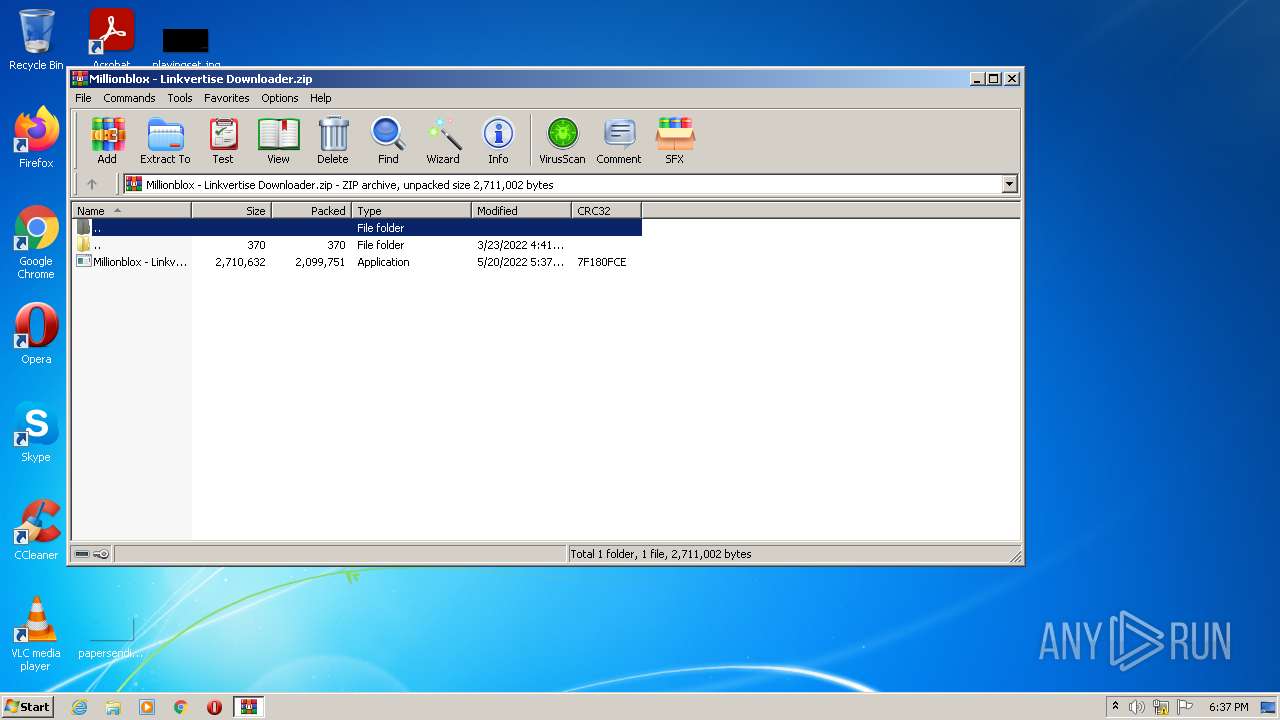
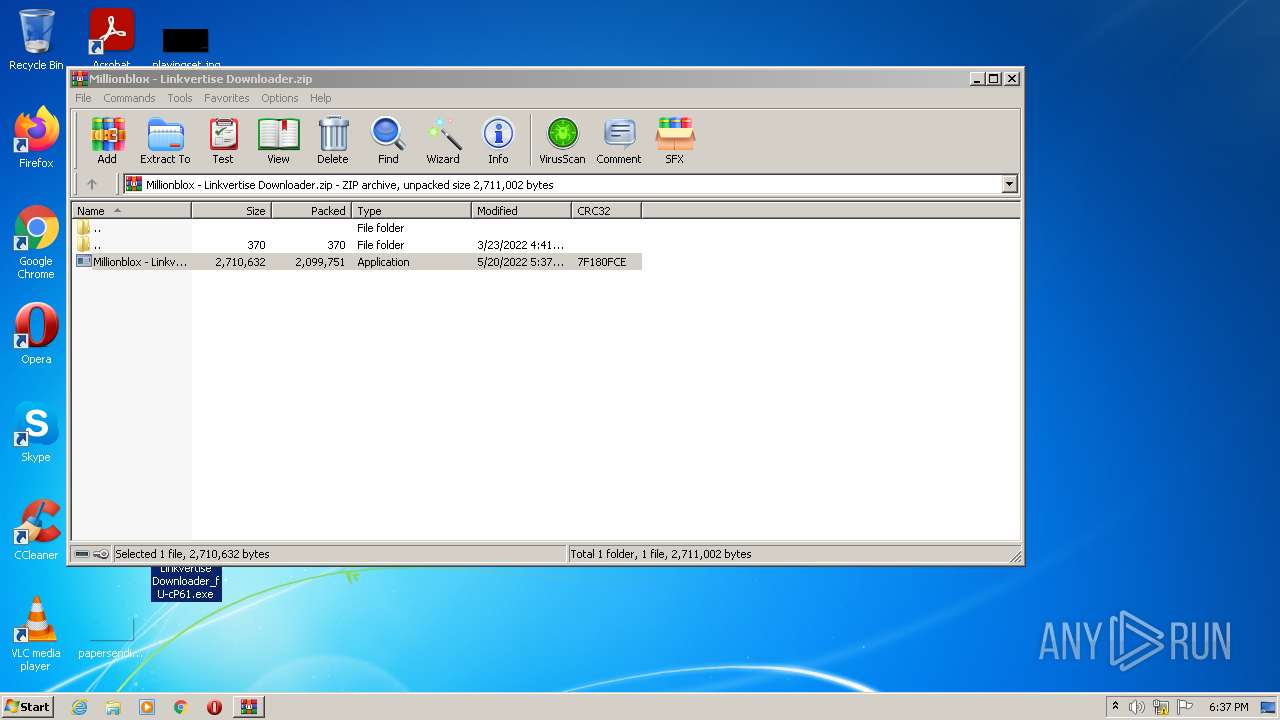
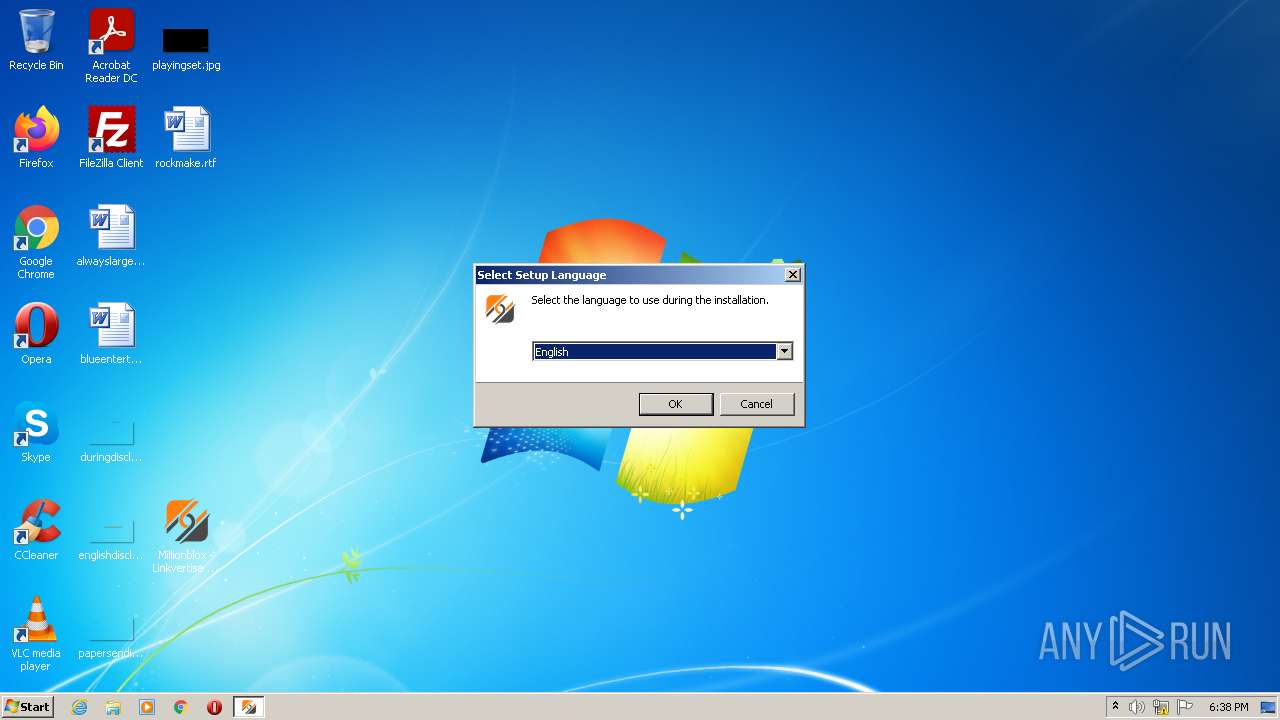
| File name: | Millionblox - Linkvertise Downloader.zip |
| Full analysis: | https://app.any.run/tasks/005081b4-4bad-43df-b70d-9410066f73f3 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 17:37:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 89A1FCDC66AB5EAB63DF366F61280ED0 |
| SHA1: | 590F168716D34BF71429467ED215F3AA2DACB1EF |
| SHA256: | 4E209BF17FF38C6D7E83F7FAF07C90CC75048A369D630D0FBB60225F3B4FCE03 |
| SSDEEP: | 49152:+tQcRavvL7pyhNCLvKOFICf+kGnlZ8LscgtyIqGEx:hvxyhN2vFx+XlZ84HbqBx |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 2864)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 2988)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Application was dropped or rewritten from another process
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 2988)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2864)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 1668)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 2988)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Reads the computer name
- WinRAR.exe (PID: 2864)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 1668)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2864)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 2988)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2864)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 2988)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Reads the Windows organization settings
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Reads Windows owner or organization settings
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Starts Internet Explorer
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2940)
INFO
Manual execution by user
- Millionblox - Linkvertise Downloader_fU-cP61.exe (PID: 4012)
Application was dropped or rewritten from another process
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 1668)
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Reads settings of System Certificates
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 2596)
Loads dropped or rewritten executable
- Millionblox - Linkvertise Downloader_fU-cP61.tmp (PID: 3248)
Checks supported languages
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 2940)
- NOTEPAD.EXE (PID: 2032)
Application launched itself
- iexplore.exe (PID: 2596)
Reads the computer name
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 2940)
Changes internet zones settings
- iexplore.exe (PID: 2596)
Checks Windows Trust Settings
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 2596)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2940)
Reads internet explorer settings
- iexplore.exe (PID: 2940)
Changes settings of System certificates
- iexplore.exe (PID: 2940)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2596)
Reads the date of Windows installation
- iexplore.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | .. / |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:03:23 16:41:23 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
47
Monitored processes
8
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1668 | "C:\Users\admin\AppData\Local\Temp\is-F7EKU.tmp\Millionblox - Linkvertise Downloader_fU-cP61.tmp" /SL5="$3012E,1785071,899584,C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe" | C:\Users\admin\AppData\Local\Temp\is-F7EKU.tmp\Millionblox - Linkvertise Downloader_fU-cP61.tmp | — | Millionblox - Linkvertise Downloader_fU-cP61.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
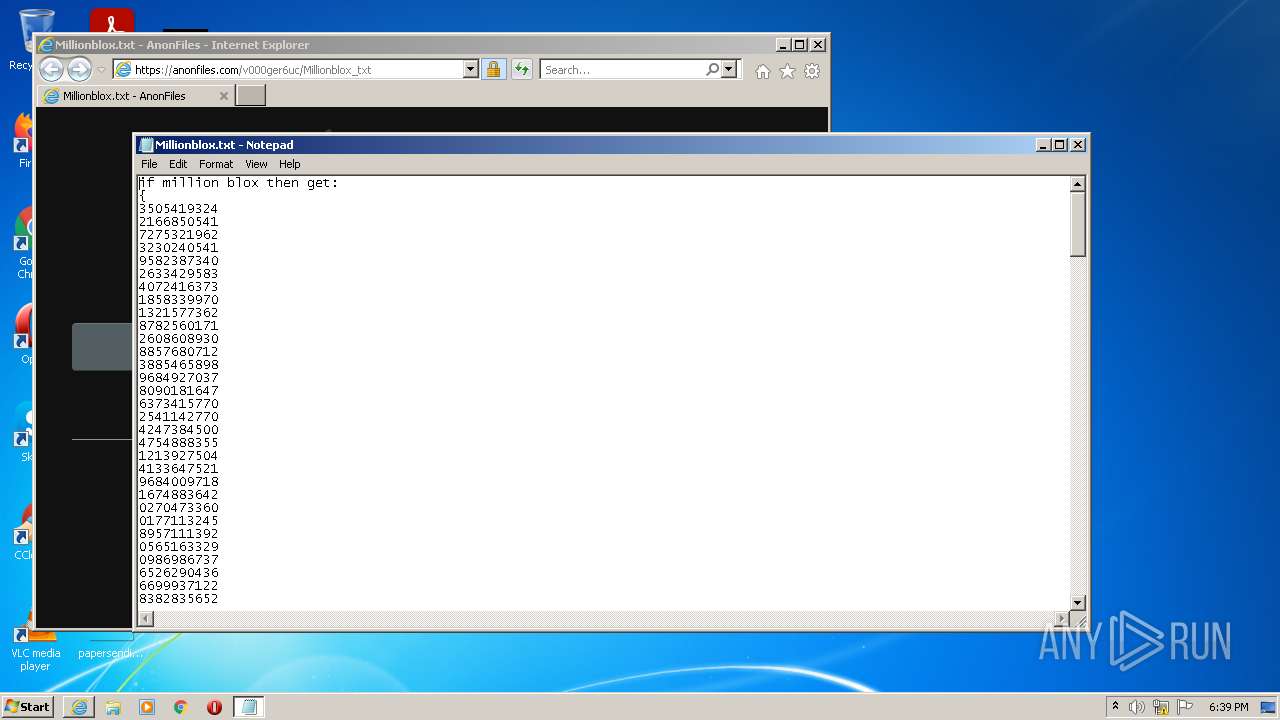
| 2032 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Millionblox.txt | C:\Windows\system32\NOTEPAD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Internet Explorer\iexplore.exe" https://anonfiles.com/v000ger6uc/Millionblox_txt | C:\Program Files\Internet Explorer\iexplore.exe | Millionblox - Linkvertise Downloader_fU-cP61.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Millionblox - Linkvertise Downloader.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2596 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
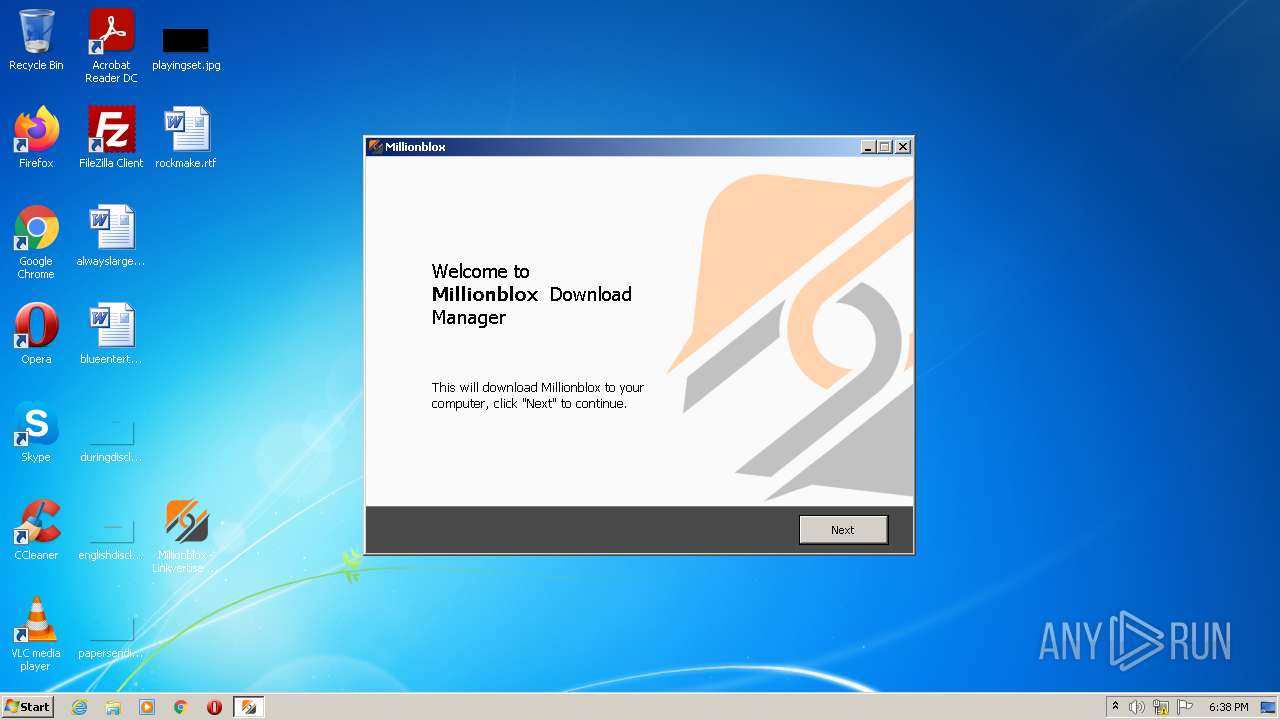
| 2988 | "C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe" /SPAWNWND=$30128 /NOTIFYWND=$3012E | C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe | Millionblox - Linkvertise Downloader_fU-cP61.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Linkvertise GmbH & Co. KG Exit code: 0 Version: 2.0.0.13 Modules
| |||||||||||||||
| 3248 | "C:\Users\admin\AppData\Local\Temp\is-1BPP9.tmp\Millionblox - Linkvertise Downloader_fU-cP61.tmp" /SL5="$40134,1785071,899584,C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe" /SPAWNWND=$30128 /NOTIFYWND=$3012E | C:\Users\admin\AppData\Local\Temp\is-1BPP9.tmp\Millionblox - Linkvertise Downloader_fU-cP61.tmp | Millionblox - Linkvertise Downloader_fU-cP61.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4012 | "C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe" | C:\Users\admin\Desktop\Millionblox - Linkvertise Downloader_fU-cP61.exe | Explorer.EXE | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Linkvertise GmbH & Co. KG Exit code: 0 Version: 2.0.0.13 Modules
| |||||||||||||||
Total events
28 502
Read events
28 335
Write events
162
Delete events
5
Modification events
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Millionblox - Linkvertise Downloader.zip | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
18
Text files
37
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.43327\Millionblox - Linkvertise Downloader_fU-cP61.exe | executable | |
MD5:— | SHA256:— | |||
| 3248 | Millionblox - Linkvertise Downloader_fU-cP61.tmp | C:\Users\admin\AppData\Local\Temp\is-LLKVN.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab48A1.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar48A0.tmp | cat | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab489F.tmp | compressed | |
MD5:— | SHA256:— | |||
| 4012 | Millionblox - Linkvertise Downloader_fU-cP61.exe | C:\Users\admin\AppData\Local\Temp\is-F7EKU.tmp\Millionblox - Linkvertise Downloader_fU-cP61.tmp | executable | |
MD5:74FAD5C6CD2D3AF1FA257B5E9531993A | SHA256:8DC40627FA4C09F7FD6DF78E3AD03D7DB3767010E15418DBA24E63754DCBC59B | |||
| 3248 | Millionblox - Linkvertise Downloader_fU-cP61.tmp | C:\Users\admin\AppData\Local\Temp\is-LLKVN.tmp\is-2THS7.tmp | image | |
MD5:DB6C259CD7B58F2F7A3CCA0C38834D0E | SHA256:494169CDD9C79EB4668378F770BFA55D4B140F23A682FF424441427DFAB0CED2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2940 | iexplore.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7f489d6beef6ebd2 | US | compressed | 60.0 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?36d797131d42325a | US | compressed | 60.0 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 67.27.158.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?edb2485dccd2de63 | US | compressed | 60.0 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 184.24.77.63:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNu0fhzwLRxYIjzRdYSnQiCNw%3D%3D | US | der | 503 b | shared |
2940 | iexplore.exe | GET | 200 | 52.222.206.73:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHophRq39F1meVBmQbb%2F1x0%3D | US | der | 1.40 Kb | whitelisted |
2596 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 18.66.107.194:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 493 b | whitelisted |
2940 | iexplore.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0701859344d4fe90 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3248 | Millionblox - Linkvertise Downloader_fU-cP61.tmp | 18.66.107.75:443 | d17kz3i6hbr7d3.cloudfront.net | Massachusetts Institute of Technology | US | suspicious |
2940 | iexplore.exe | 45.154.253.152:443 | anonfiles.com | — | — | suspicious |
2940 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2940 | iexplore.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
2940 | iexplore.exe | 67.27.158.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
2940 | iexplore.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2940 | iexplore.exe | 184.24.77.63:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
2940 | iexplore.exe | 108.138.24.89:443 | djv99sxoqpv11.cloudfront.net | BellSouth.net Inc. | US | unknown |
2940 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
2940 | iexplore.exe | 108.138.2.195:80 | o.ss2.us | BellSouth.net Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d17kz3i6hbr7d3.cloudfront.net |
| whitelisted |
anonfiles.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
vjs.zencdn.net |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
ocsp2.globalsign.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |