| File name: | Stop Moodle.exe |
| Full analysis: | https://app.any.run/tasks/9af70760-2f9c-454e-8941-63f712f99e1e |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2024, 06:24:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | C543148BC9395606C1360E2E20FE1293 |
| SHA1: | FF998F30423CC2403DF9DA6D07D5D2F1B50046CD |
| SHA256: | 4DF51798055701A531D398244D7F01F647B5DFA9C677940603D15161D2A14501 |
| SSDEEP: | 384:E2w1LxeV0ZNtMjs+beTKrukDEm8vjKTvgdohgxT:E2mLxfjgs+b3Zgx |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- Stop Moodle.exe (PID: 2728)
- b2e.exe (PID: 3612)
Executable content was dropped or overwritten
- Stop Moodle.exe (PID: 3680)
- Stop Moodle.exe (PID: 2728)
Reads the Internet Settings
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- b2e.exe (PID: 3612)
- Stop Moodle.exe (PID: 2728)
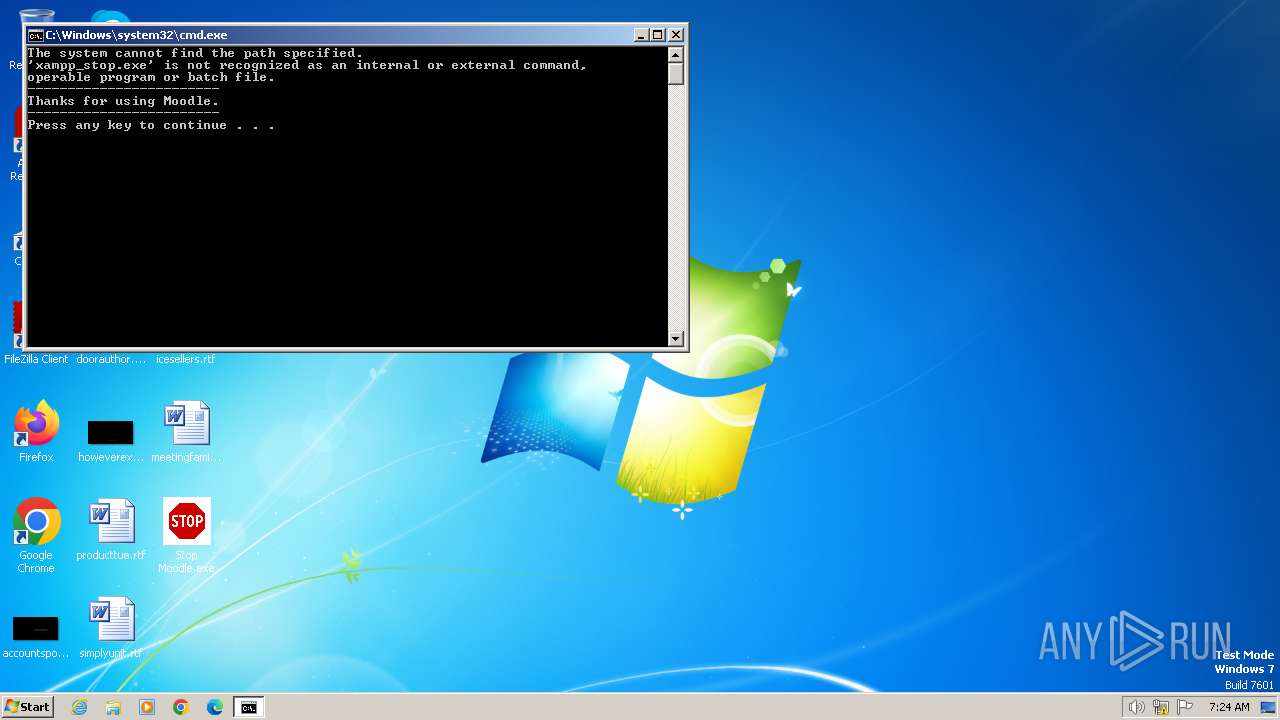
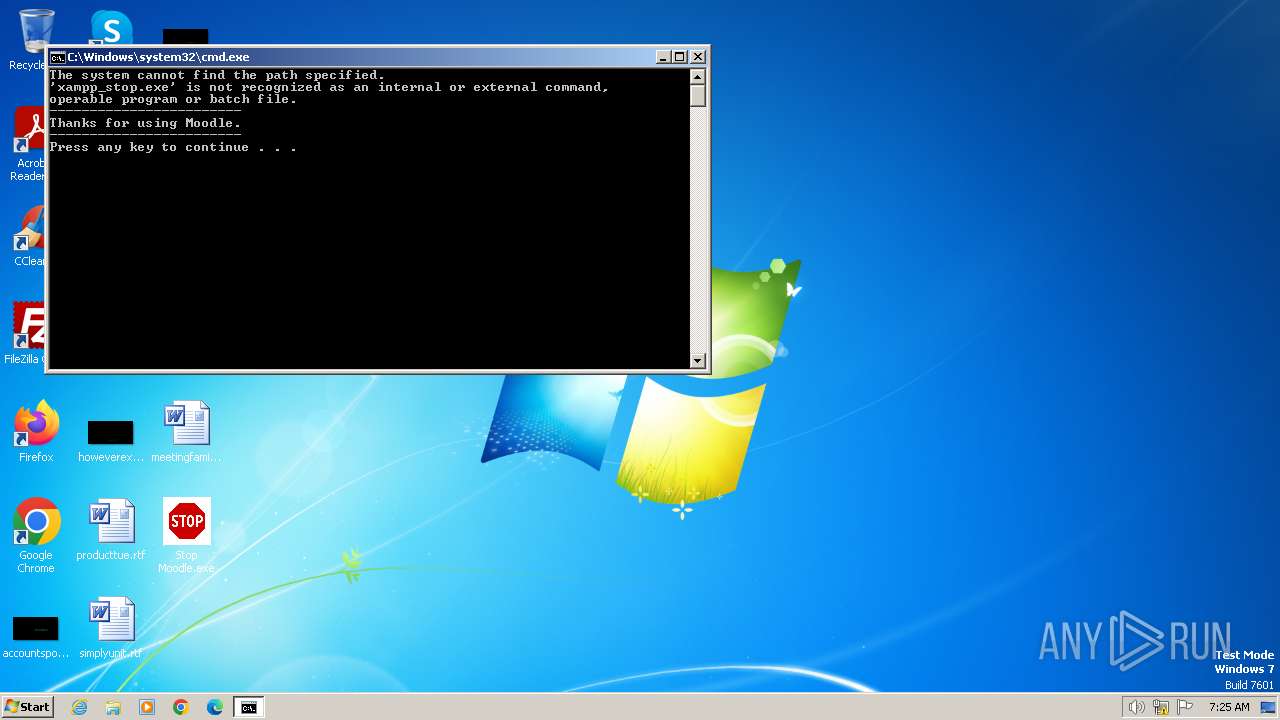
Starts CMD.EXE for commands execution
- b2e.exe (PID: 2640)
- b2e.exe (PID: 3612)
Executing commands from a ".bat" file
- b2e.exe (PID: 2640)
- b2e.exe (PID: 3612)
INFO
Reads the computer name
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- b2e.exe (PID: 3612)
- Stop Moodle.exe (PID: 2728)
Create files in a temporary directory
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- b2e.exe (PID: 3612)
- Stop Moodle.exe (PID: 2728)
Checks supported languages
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- Stop Moodle.exe (PID: 2728)
- b2e.exe (PID: 3612)
The process uses the downloaded file
- Stop Moodle.exe (PID: 3680)
- b2e.exe (PID: 2640)
- Stop Moodle.exe (PID: 2728)
- b2e.exe (PID: 3612)
Manual execution by a user
- Stop Moodle.exe (PID: 2728)
- explorer.exe (PID: 1756)
- notepad.exe (PID: 2248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.7) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.4) |
| .exe | | | DOS Executable Generic (23.4) |
| .vxd | | | VXD Driver (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:05:12 01:24:56+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 1.67 |
| CodeSize: | 8192 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 32768 |
| EntryPoint: | 0x9fa0 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 3.1 |
| Subsystem: | Windows GUI |
Total processes
52
Monitored processes
10
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\D358.tmp\batchfile.bat" " | C:\Windows\System32\cmd.exe | — | b2e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
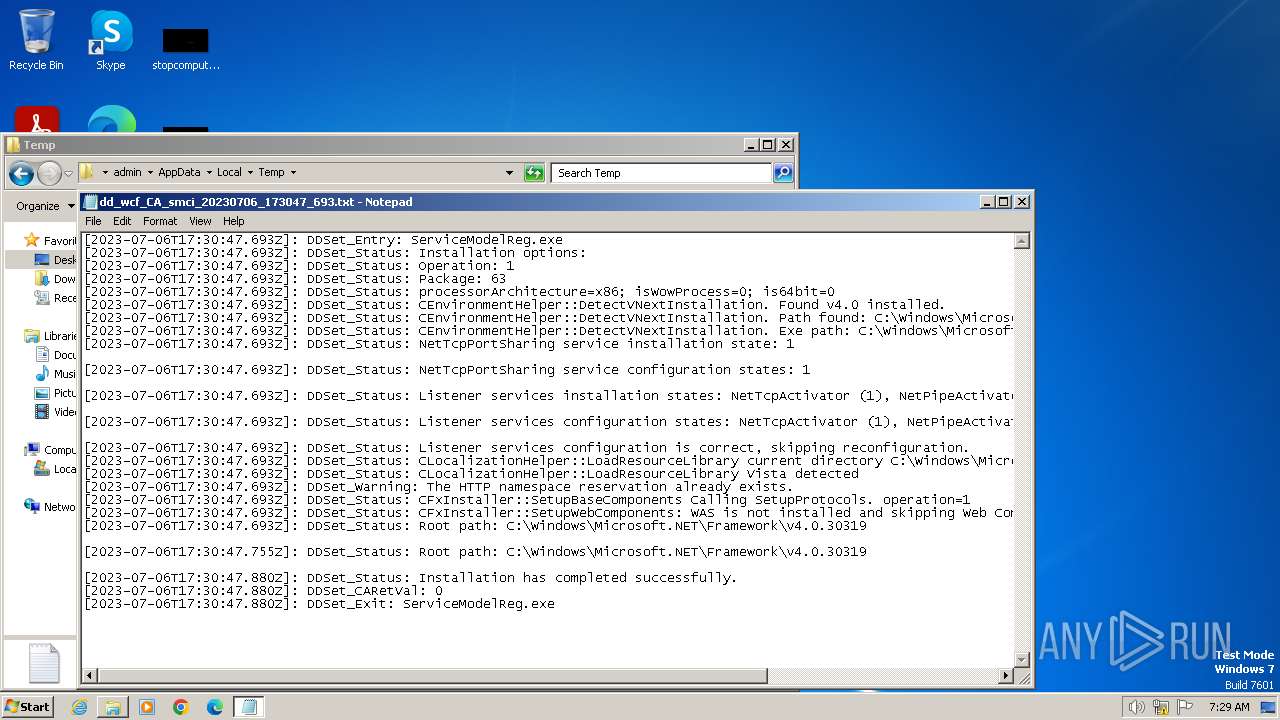
| 2248 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\dd_wcf_CA_smci_20230706_173047_693.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\selfdel0.bat" " | C:\Windows\System32\cmd.exe | — | b2e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2556 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\381D.tmp\batchfile.bat" " | C:\Windows\System32\cmd.exe | — | b2e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2640 | "C:\Users\admin\AppData\Local\Temp\D27D.tmp\b2e.exe" C:\Users\admin\AppData\Local\Temp\D27D.tmp\b2e.exe C:\Users\admin\Desktop "C:\Users\admin\Desktop\Stop Moodle.exe" | C:\Users\admin\AppData\Local\Temp\D27D.tmp\b2e.exe | — | Stop Moodle.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\Desktop\Stop Moodle.exe" | C:\Users\admin\Desktop\Stop Moodle.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 9017 Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\AppData\Local\Temp\3771.tmp\b2e.exe" C:\Users\admin\AppData\Local\Temp\3771.tmp\b2e.exe C:\Users\admin\Desktop "C:\Users\admin\Desktop\Stop Moodle.exe" | C:\Users\admin\AppData\Local\Temp\3771.tmp\b2e.exe | — | Stop Moodle.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\Stop Moodle.exe" | C:\Users\admin\Desktop\Stop Moodle.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 9017 Modules
| |||||||||||||||
| 3688 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\selfdel0.bat" " | C:\Windows\System32\cmd.exe | — | b2e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 436
Read events
1 388
Write events
48
Delete events
0
Modification events
| (PID) Process: | (3680) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3680) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3680) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3680) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2640) b2e.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2640) b2e.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2640) b2e.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2640) b2e.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2728) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2728) Stop Moodle.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2640 | b2e.exe | C:\Users\admin\AppData\Local\Temp\D358.tmp\batchfile.bat | text | |
MD5:3E0A729D8F098B7C12D469DFB4BF51EA | SHA256:50EBC7CB7415C7D1F73C8E6DD52EDF59F67A9FFCAC98002A101A1ADB450BBB6E | |||
| 3612 | b2e.exe | C:\Users\admin\AppData\Local\Temp\selfdel0.bat | text | |
MD5:78C963C5E210DA2B3B9B12B0DA9D0E73 | SHA256:1D33615CCB5E96E62798174F282955800D952198973F889C5D50BDF660B2DBBB | |||
| 3680 | Stop Moodle.exe | C:\Users\admin\AppData\Local\Temp\D27D.tmp\b2e.exe | executable | |
MD5:086A33E2ABCE74042A6C20374B7F061C | SHA256:3A829F3DC66B5D060910189447A1AD50443EA01880235D097A2BAA2169EAD15A | |||
| 3612 | b2e.exe | C:\Users\admin\AppData\Local\Temp\381D.tmp\batchfile.bat | text | |
MD5:3E0A729D8F098B7C12D469DFB4BF51EA | SHA256:50EBC7CB7415C7D1F73C8E6DD52EDF59F67A9FFCAC98002A101A1ADB450BBB6E | |||
| 2728 | Stop Moodle.exe | C:\Users\admin\AppData\Local\Temp\3771.tmp\b2e.exe | executable | |
MD5:086A33E2ABCE74042A6C20374B7F061C | SHA256:3A829F3DC66B5D060910189447A1AD50443EA01880235D097A2BAA2169EAD15A | |||
| 2640 | b2e.exe | C:\Users\admin\AppData\Local\Temp\selfdel0.bat | text | |
MD5:FC9825CFC601E1101E83AC3AD5B7E3E1 | SHA256:0DE49FFAA9A34CE663E9238847BAC4C26759D5B3675D2D9D944196EFFB8C0238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |