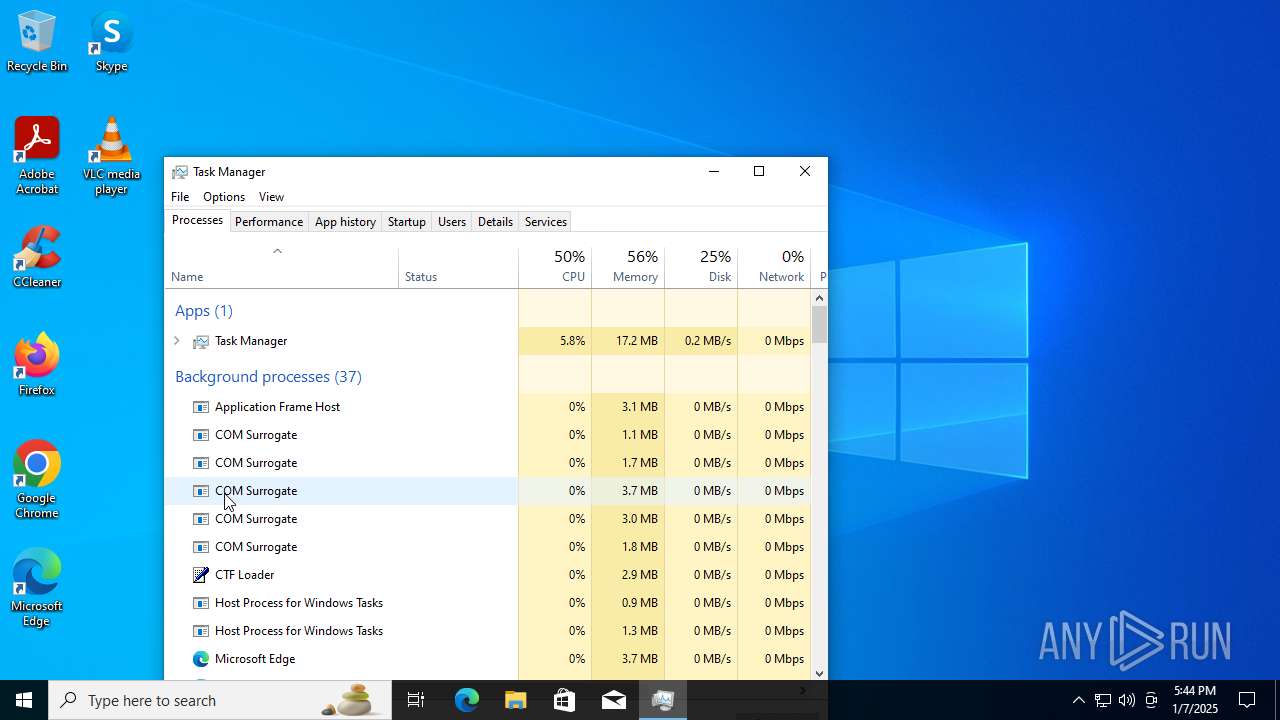
| File name: | ViraLock.exe |
| Full analysis: | https://app.any.run/tasks/bd2b4508-4095-4a6e-8c61-f89fdc35944a |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2025, 17:40:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | image/bmp |
| File info: | PC bitmap, Windows 3.x format, 48 x 48 x 24, resolution 3779 x 3779 px/m, cbSize 6968, bits offset 54 |
| MD5: | 76E08B93985D60B82DDB4A313733345C |
| SHA1: | 273EFFBAC9E1DC901A3F0EE43122D2BDB383ADBF |
| SHA256: | 4DC0A8AFBF4DBB1A67B9292BB028B7F744F3029B0083C36307B1F84A00692A89 |
| SSDEEP: | 192:+jcU93o+u1PhhSf0LtRnd+Hf3mix7JpAJTs1Ckg9:Vs3ncZLPkHf3m0JpANbkg9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- LockApp.exe (PID: 4244)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 1292)
Reads Internet Explorer settings
- FirstLogonAnim.exe (PID: 7396)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 7784)
Application launched itself
- ie4uinit.exe (PID: 7784)
- setup.exe (PID: 2132)
- setup.exe (PID: 5268)
- setup.exe (PID: 5804)
- setup.exe (PID: 8960)
- setup.exe (PID: 8416)
- OneDriveSetup.exe (PID: 4968)
Changes internet zones settings
- ie4uinit.exe (PID: 7784)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 7864)
Executable content was dropped or overwritten
- OneDriveSetup.exe (PID: 9728)
The process drops C-runtime libraries
- OneDriveSetup.exe (PID: 9728)
Process drops legitimate windows executable
- msedge.exe (PID: 556)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 3000)
- BackgroundTransferHost.exe (PID: 6872)
- ie4uinit.exe (PID: 7864)
- WWAHost.exe (PID: 1460)
- FirstLogonAnim.exe (PID: 7396)
- BackgroundTransferHost.exe (PID: 8840)
- OneDriveSetup.exe (PID: 4968)
Reads the computer name
- LockApp.exe (PID: 4244)
- PLUGScheduler.exe (PID: 1292)
- setup.exe (PID: 2132)
- SearchApp.exe (PID: 9308)
Checks supported languages
- LockApp.exe (PID: 4244)
- PLUGScheduler.exe (PID: 1292)
- setup.exe (PID: 3876)
- setup.exe (PID: 2132)
- setup.exe (PID: 5268)
- setup.exe (PID: 5804)
- setup.exe (PID: 9156)
- StartMenuExperienceHost.exe (PID: 10184)
- setup.exe (PID: 9092)
- SearchApp.exe (PID: 9308)
- OneDrive.exe (PID: 10300)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 6872)
- SearchApp.exe (PID: 9308)
- BackgroundTransferHost.exe (PID: 8840)
Manual execution by a user
- FirstLogonAnim.exe (PID: 7396)
- ie4uinit.exe (PID: 7784)
- unregmp2.exe (PID: 7724)
- chrmstp.exe (PID: 7284)
- setup.exe (PID: 2132)
- unregmp2.exe (PID: 8168)
- OneDriveSetup.exe (PID: 4968)
- fsquirt.exe (PID: 1076)
- msedge.exe (PID: 8708)
- wab.exe (PID: 8548)
- firefox.exe (PID: 8688)
- Taskmgr.exe (PID: 1044)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 6872)
- SearchApp.exe (PID: 9308)
- OneDriveSetup.exe (PID: 4968)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6872)
Local mutex for internet shortcut management
- ie4uinit.exe (PID: 7784)
Creates files in the program directory
- chrmstp.exe (PID: 7284)
- chrmstp.exe (PID: 7024)
- setup.exe (PID: 8960)
- setup.exe (PID: 8416)
Application launched itself
- chrmstp.exe (PID: 7284)
- chrmstp.exe (PID: 7024)
- msedge.exe (PID: 8080)
- firefox.exe (PID: 8688)
- firefox.exe (PID: 8508)
Process checks computer location settings
- setup.exe (PID: 5268)
- SearchApp.exe (PID: 9308)
- StartMenuExperienceHost.exe (PID: 10184)
Reads Microsoft Office registry keys
- setup.exe (PID: 2132)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 10184)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 9308)
The sample compiled with english language support
- OneDriveSetup.exe (PID: 9728)
The sample compiled with chinese language support
- OneDriveSetup.exe (PID: 9728)
The sample compiled with portuguese language support
- OneDriveSetup.exe (PID: 9728)
Executable content was dropped or overwritten
- msedge.exe (PID: 556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bmp | | | Windows Bitmap (v3) (50) |
|---|---|---|
| .bmp | | | Windows Bitmap (49.9) |
EXIF
Composite
| ImageSize: | 48x48 |
|---|---|
| Megapixels: | 0.002 |
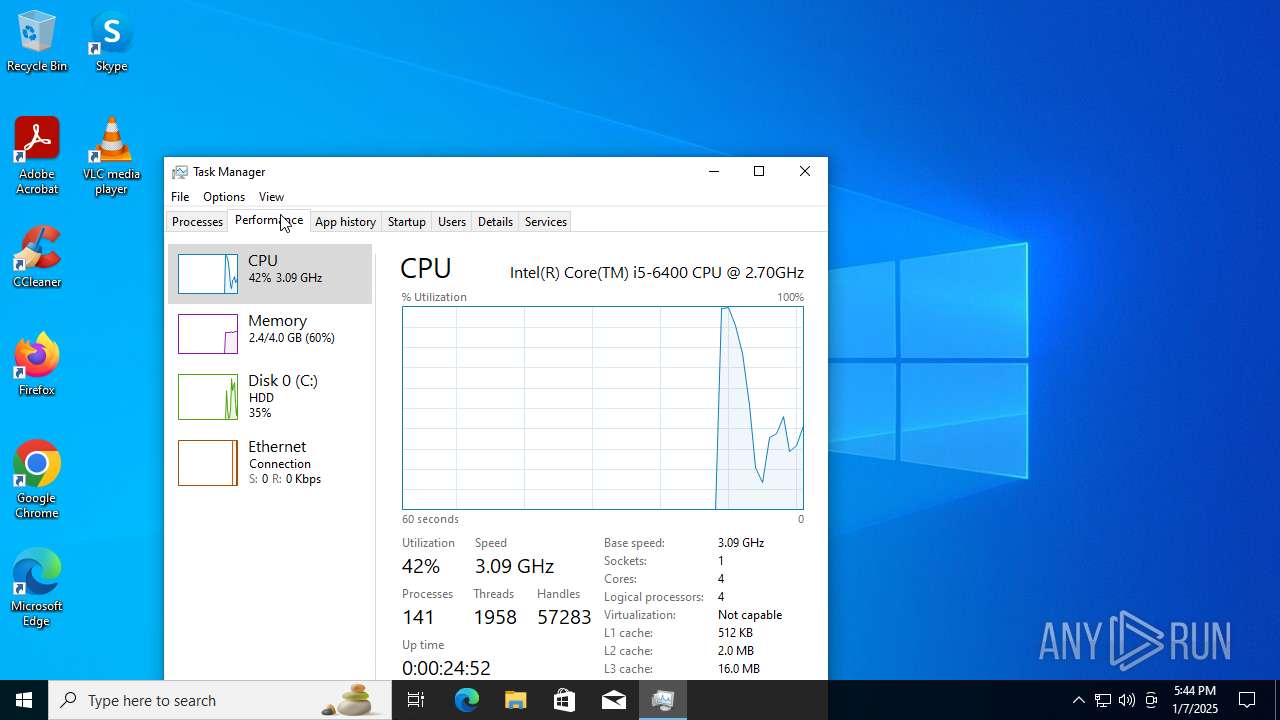
Total processes
326
Monitored processes
101
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\DllHost.exe /Processid:{CA8C87C1-929D-45BA-94DB-EF8E6CB346AD} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5340 --field-trial-handle=2096,i,11394327520799330964,9464023134388429761,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 628 | "C:\Program Files\Google\Chrome\Application\122.0.6261.70\Installer\chrmstp.exe" --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x2c4,0x2c8,0x2cc,0x2a0,0x2d0,0x7ff7bbf117e8,0x7ff7bbf117f4,0x7ff7bbf11800 | C:\Program Files\Google\Chrome\Application\122.0.6261.70\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1044 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\Windows\System32\fsquirt.exe" -Register | C:\Windows\System32\fsquirt.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1460 | "C:\WINDOWS\system32\wwahost.exe" -ServerName:App.wwa | C:\Windows\System32\WWAHost.exe | — | svchost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft WWA Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\Administrator\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\Administrator\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x28c,0x290,0x294,0x284,0x29c,0x7ff81c7a5fd8,0x7ff81c7a5fe4,0x7ff81c7a5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1073807364 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2132 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe" --configure-user-settings --verbose-logging --system-level --msedge --channel=stable | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Installer Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
66 620
Read events
65 331
Write events
1 241
Delete events
48
Modification events
| (PID) Process: | (6256) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000033000000A00400007502000000000000 | |||
| (PID) Process: | (3000) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3000) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3000) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6872) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6872) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6872) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7724) unregmp2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Keyboard\Native Media Players\WMP |
| Operation: | write | Name: | AppName |
Value: Windows Media Player | |||
| (PID) Process: | (7724) unregmp2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Keyboard\Native Media Players\WMP |
| Operation: | write | Name: | ExePath |
Value: C:\Program Files\Windows Media Player\wmplayer.exe | |||
| (PID) Process: | (7724) unregmp2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Player\Settings |
| Operation: | write | Name: | Client ID |
Value: {F1C7D8FB-FD67-4662-8251-79828E90088E} | |||
Executable files
242
Suspicious files
1 011
Text files
680
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.026.etl | etl | |
MD5:B787593A02A4E0A601164A65952D0CB9 | SHA256:3594AD496D8E1771BCC3E8B6F68B4C2B4190A9A331FB43F068A7DF4E1894E2CF | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | binary | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | binary | |
MD5:868E79A00A8204448B2FFC4F4D5C08EA | SHA256:148FE324431CB4C826BCF0436147D946AC389A877732612CF40629048B8517DC | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:673727AF7C6805E869C9F8BE1E468F4A | SHA256:6B16B7DE97F397BCEC36EB3F18C7B64CD3DB6D2974DDF319A251CE27B80D837B | |||
| 6872 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\29181626-1d29-4586-851a-987c7dce6a90.down_data | — | |
MD5:— | SHA256:— | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | binary | |
MD5:B53B2070E686FFB1FBC8B06994E7C8D7 | SHA256:A3ABD06F4E40CB700B1908AB6BCD2E27455E13EF076E0BF2345BB2FA369EF802 | |||
| 1292 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
87
TCP/UDP connections
179
DNS requests
196
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1616 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7068 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7068 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6648 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1684 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
1684 | svchost.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |