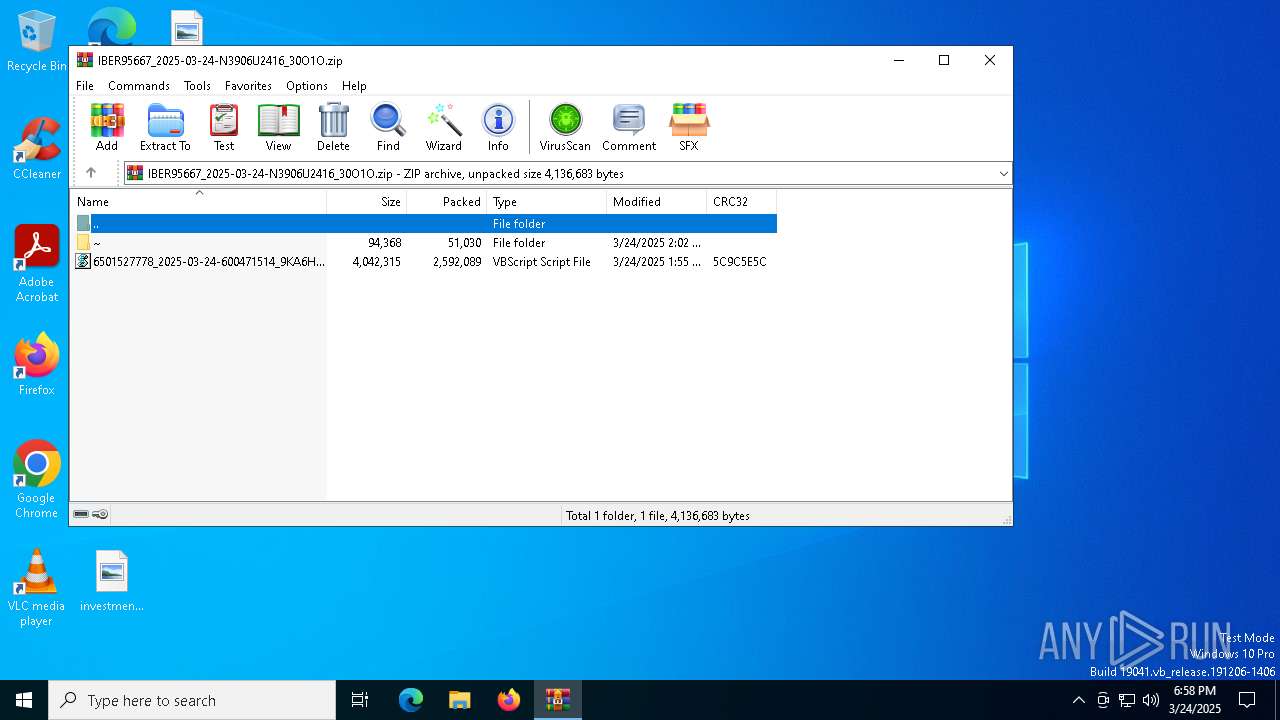
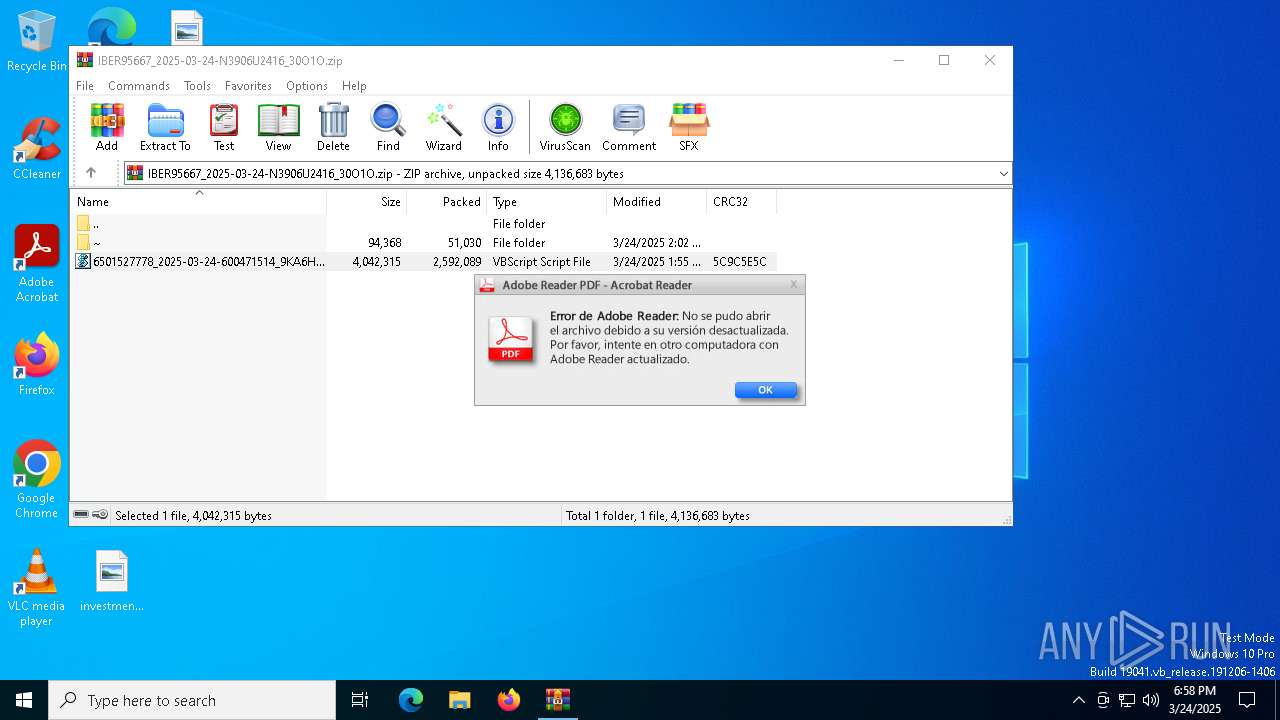
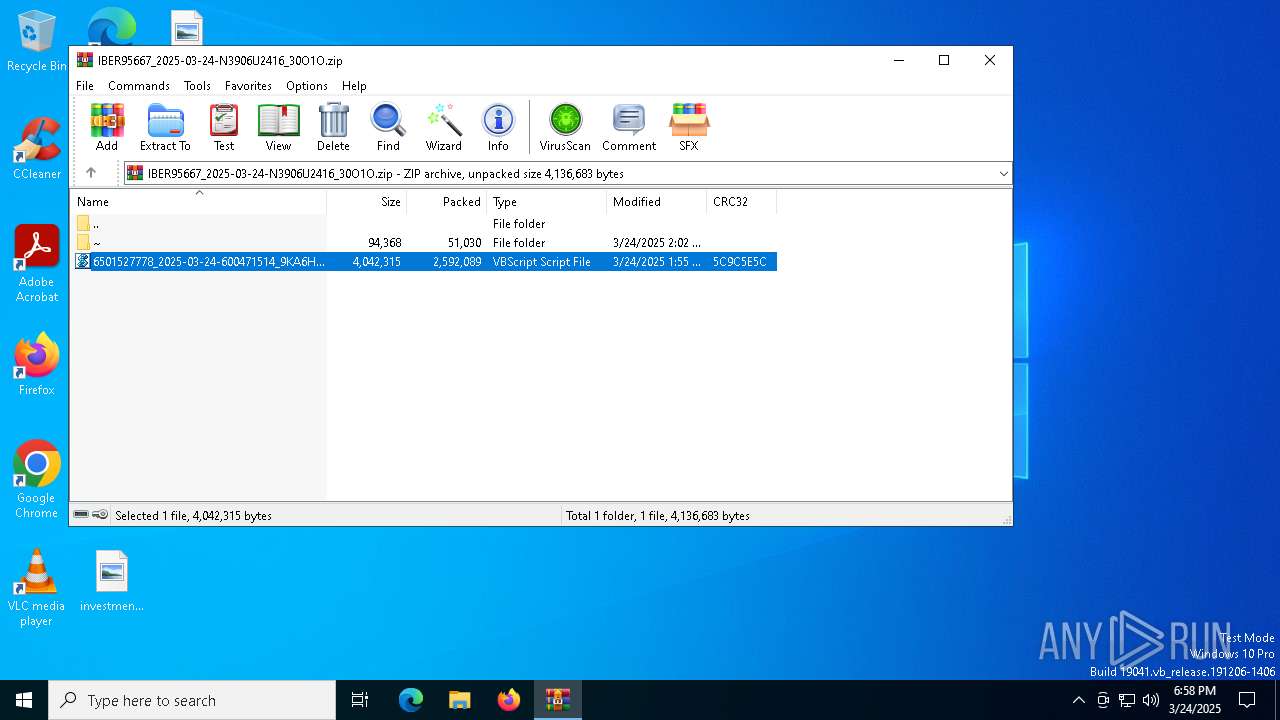
| File name: | IBER95667_2025-03-24-N3906U2416_30O1O.zip |
| Full analysis: | https://app.any.run/tasks/129cfd92-97e4-4ec6-881b-2b73da72e9b6 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 18:58:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6DE3777F479965E2EFC38E51A942111C |
| SHA1: | D945BC6DFD88FA7F6D677B9C473C106EC7A0EB93 |
| SHA256: | 4D9DC5E28920B275BD1E75BD0381262E7787836ED41ED6FB5073525BDE1F40FF |
| SSDEEP: | 98304:iBQVcsmLLTDB5TSrHKNfq7ALqh+ySLC1esG+JhRE/aESB4g+WlmQjtBv1LElNbro:DAC |
MALICIOUS
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 7472)
Deletes a file (SCRIPT)
- wscript.exe (PID: 7472)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 7352)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 7472)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7472)
Likely accesses (executes) a file from the Public directory
- qfEWdyvSEO.exe (PID: 7544)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 7472)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 7472)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 7472)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7472)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7352)
There is functionality for taking screenshot (YARA)
- qfEWdyvSEO.exe (PID: 7544)
There is functionality for communication over UDP network (YARA)
- qfEWdyvSEO.exe (PID: 7544)
Checks for external IP
- svchost.exe (PID: 2196)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7352)
The sample compiled with english language support
- wscript.exe (PID: 7472)
Reads the computer name
- qfEWdyvSEO.exe (PID: 7544)
Checks supported languages
- qfEWdyvSEO.exe (PID: 7544)
Compiled with Borland Delphi (YARA)
- qfEWdyvSEO.exe (PID: 7544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 13:55:36 |
| ZipCRC: | 0x5c9c5e5c |
| ZipCompressedSize: | 2592089 |
| ZipUncompressedSize: | 4042315 |
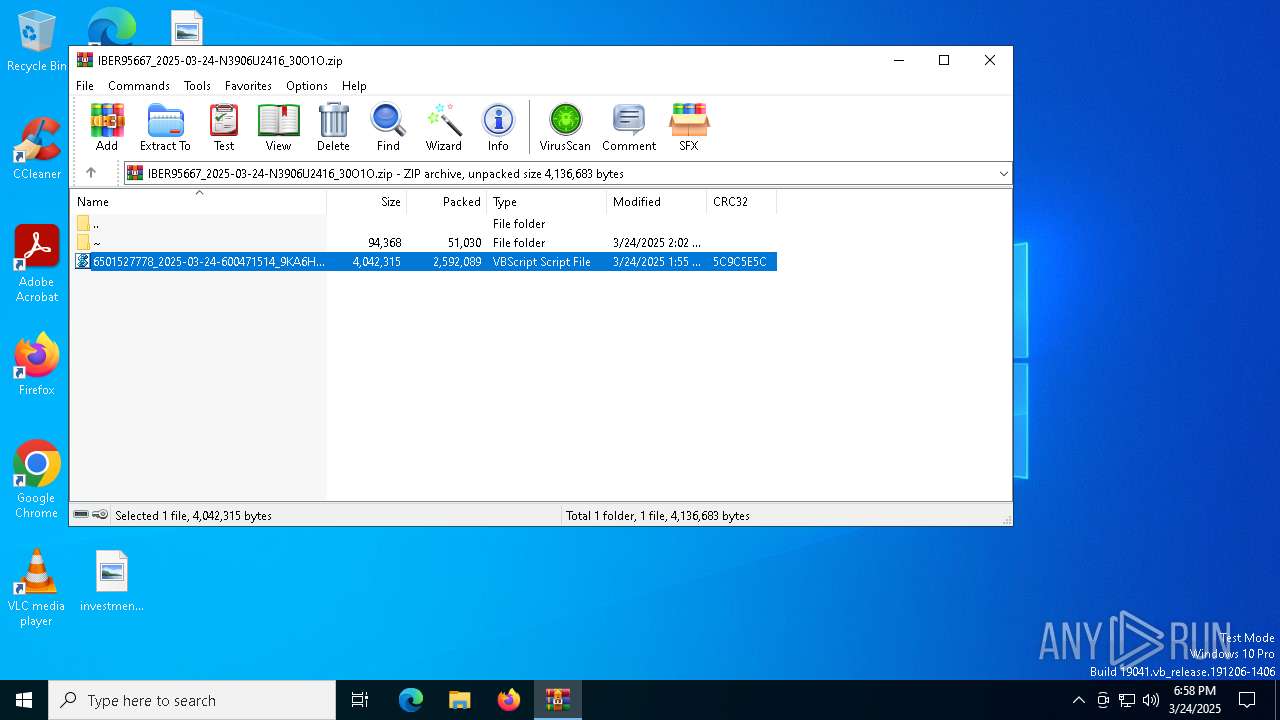
| ZipFileName: | 6501527778_2025-03-24-600471514_9KA6H.vbs |
Total processes
120
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\IBER95667_2025-03-24-N3906U2416_30O1O.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7472 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa7352.1411\6501527778_2025-03-24-600471514_9KA6H.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7544 | "C:\Users\Public\qfEWdyvSEO.exe" | C:\Users\Public\qfEWdyvSEO.exe | wscript.exe | ||||||||||||
User: admin Company: CloudBridge Solutions 8008019 Inc. Integrity Level: MEDIUM Description: Advanced Data Protection Management 8008019, 34649.10192.19702.37677, K735. Version: 34649.10192.19702.37677 Modules
| |||||||||||||||
| 7768 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 634
Read events
3 624
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IBER95667_2025-03-24-N3906U2416_30O1O.zip | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7472) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000008F1DFFB9EE9CDB01 | |||
Executable files
0
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7472 | wscript.exe | C:\Users\Public\MTETqrsot886XS71RC6M6U8ARMHXVbmlyjj.tcg | — | |
MD5:— | SHA256:— | |||
| 7472 | wscript.exe | C:\Users\Public\qfEWdyvSEO.exe | — | |
MD5:— | SHA256:— | |||
| 7472 | wscript.exe | C:\Users\Public\qfEWdyvSEO.zip | compressed | |
MD5:47761942BF8B377D85CFABCF0BC4BE07 | SHA256:FF3D25A975186C2BD991B7F74338063ECF45FE9C2F38E6D2974B0E64CB994FA5 | |||
| 7472 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:916474512B5E4D207B8E06696BD38F0C | SHA256:2754AD05CDA8430EE3D1D38AA0344C18A07E7F30F35A1F7AC3C874A1ECA55148 | |||
| 7352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7352.1411\6501527778_2025-03-24-600471514_9KA6H.vbs | binary | |
MD5:FD7FD6DF75012A1C87E97CDC5FE74244 | SHA256:B8D742E12AB2DCE7306CAEA26AC647B00AA66C5714C4C84524D0D7E35C9C63C6 | |||
| 7472 | wscript.exe | C:\Users\Public\HXdpnmMclMZPjKIUoDVLGOU.txt | text | |
MD5:AE967CB8818CE6824FB1A91D89E939FF | SHA256:EFC705A56F3373A583F9FEA00D8E6C94BB1A8EFCEC24711CCF8805CA94684259 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
22
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7544 | qfEWdyvSEO.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
5576 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ip-api.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |