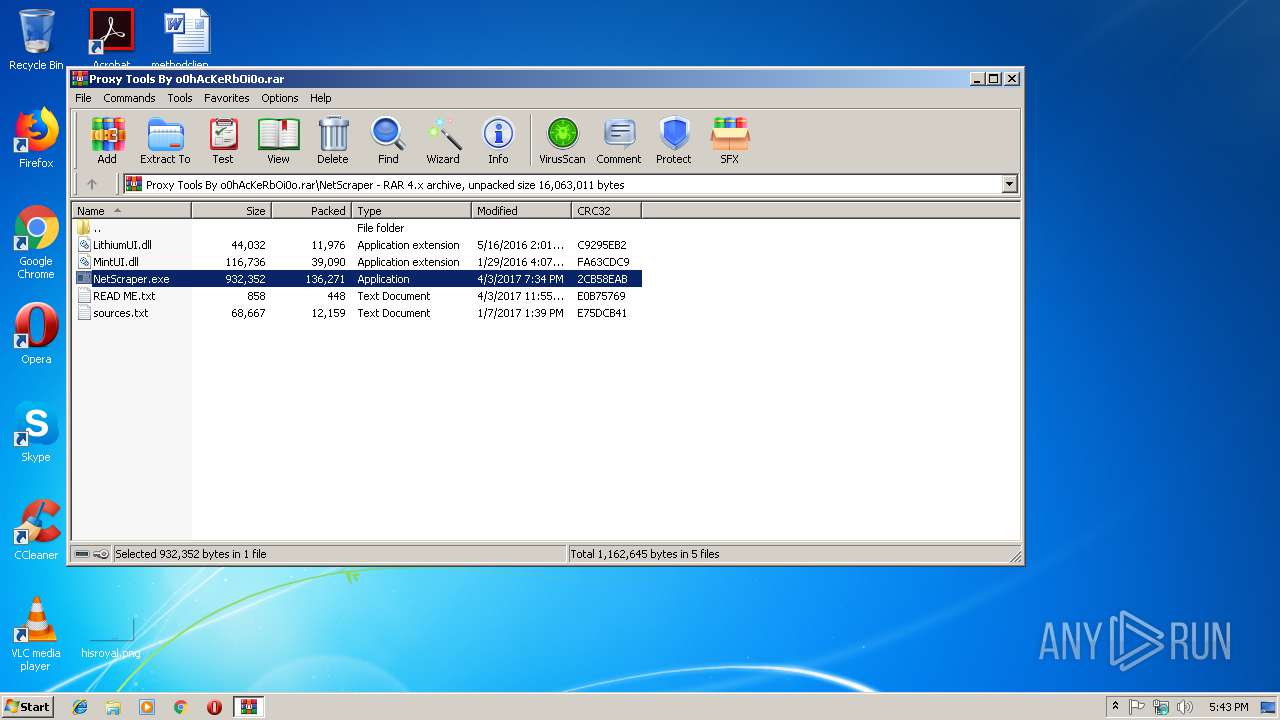
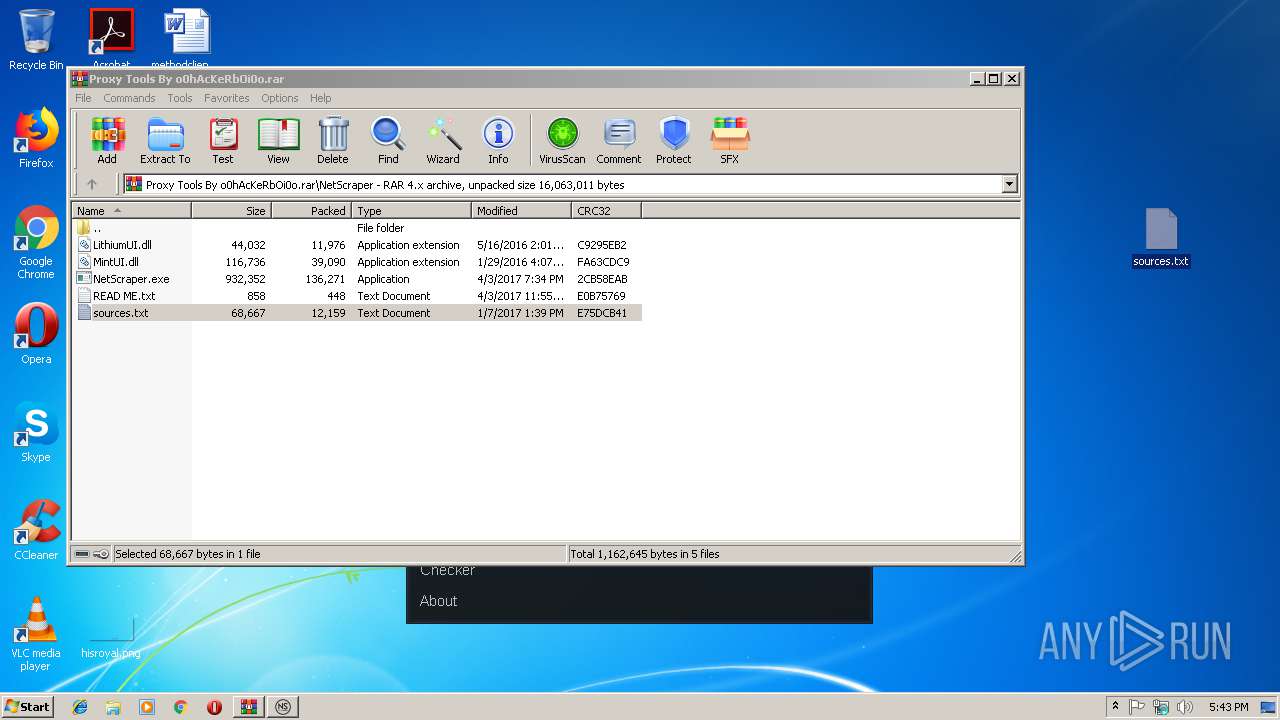
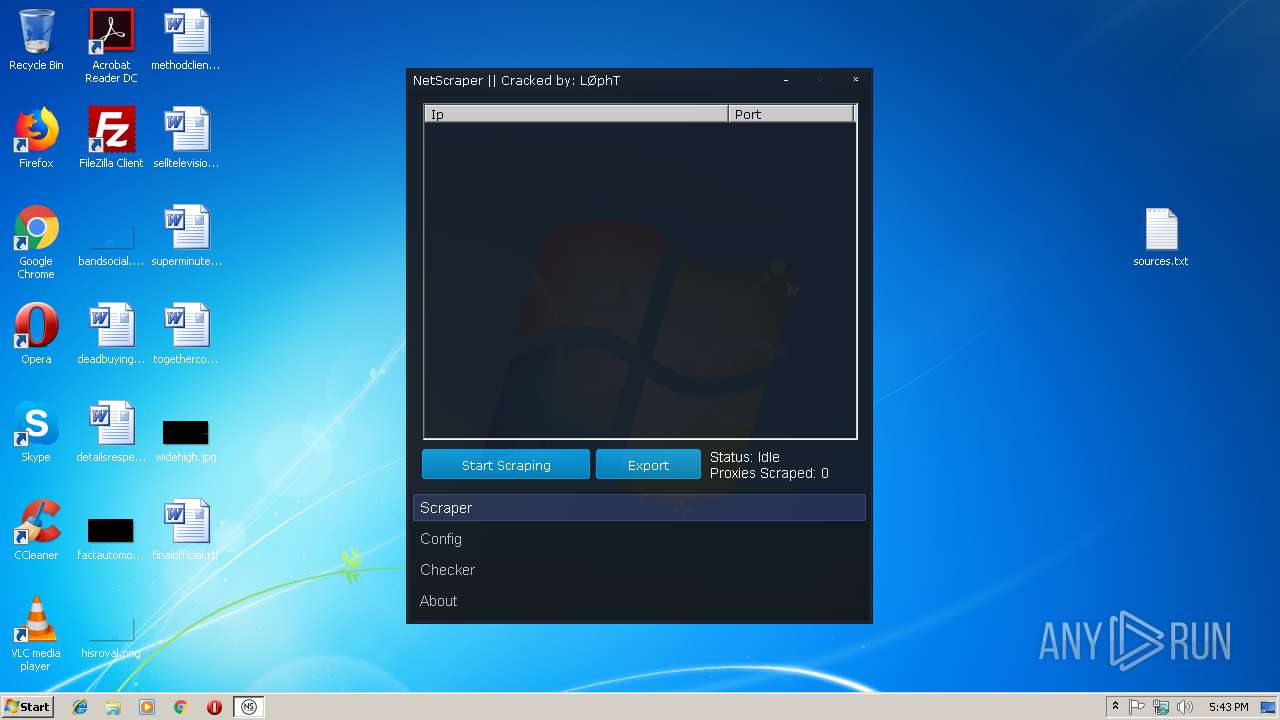
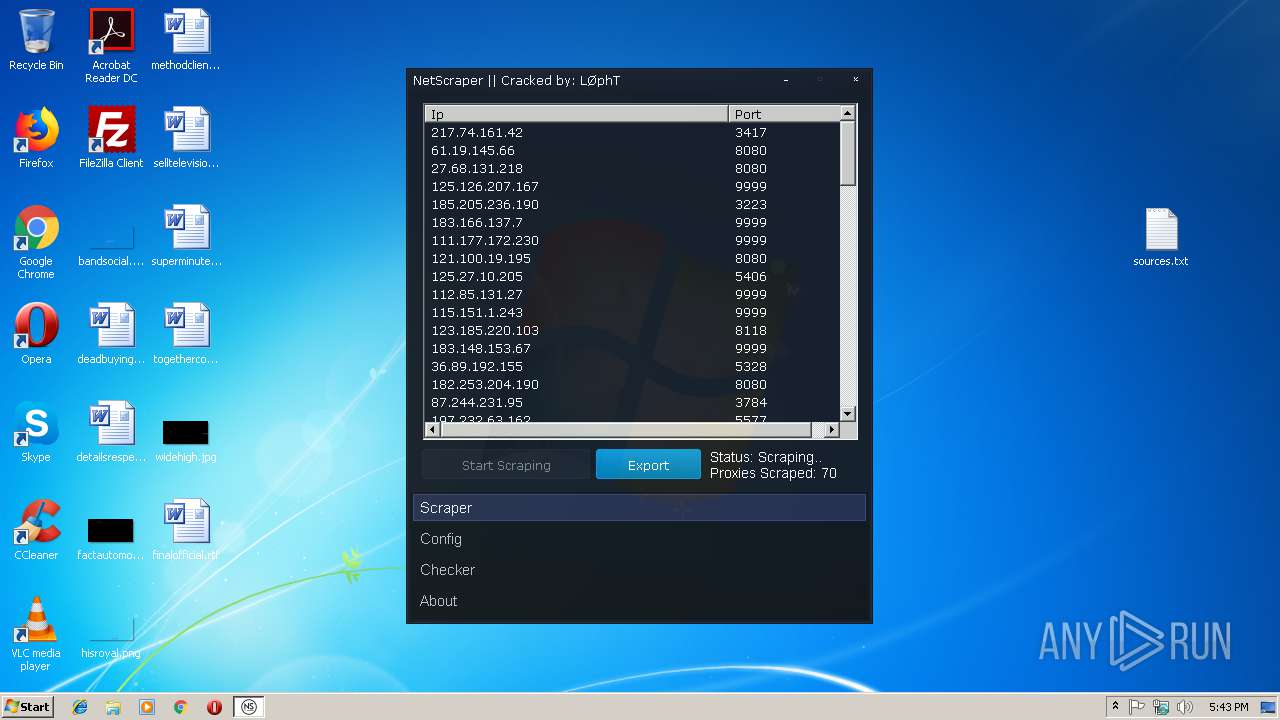
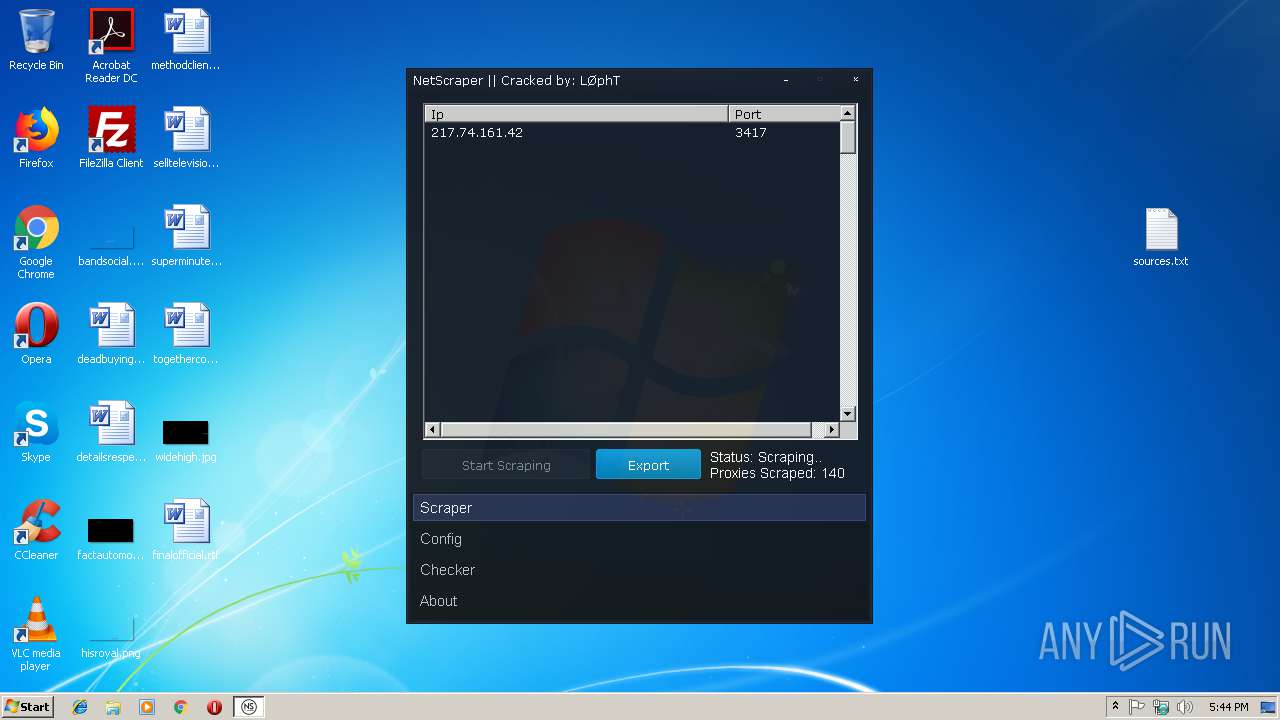
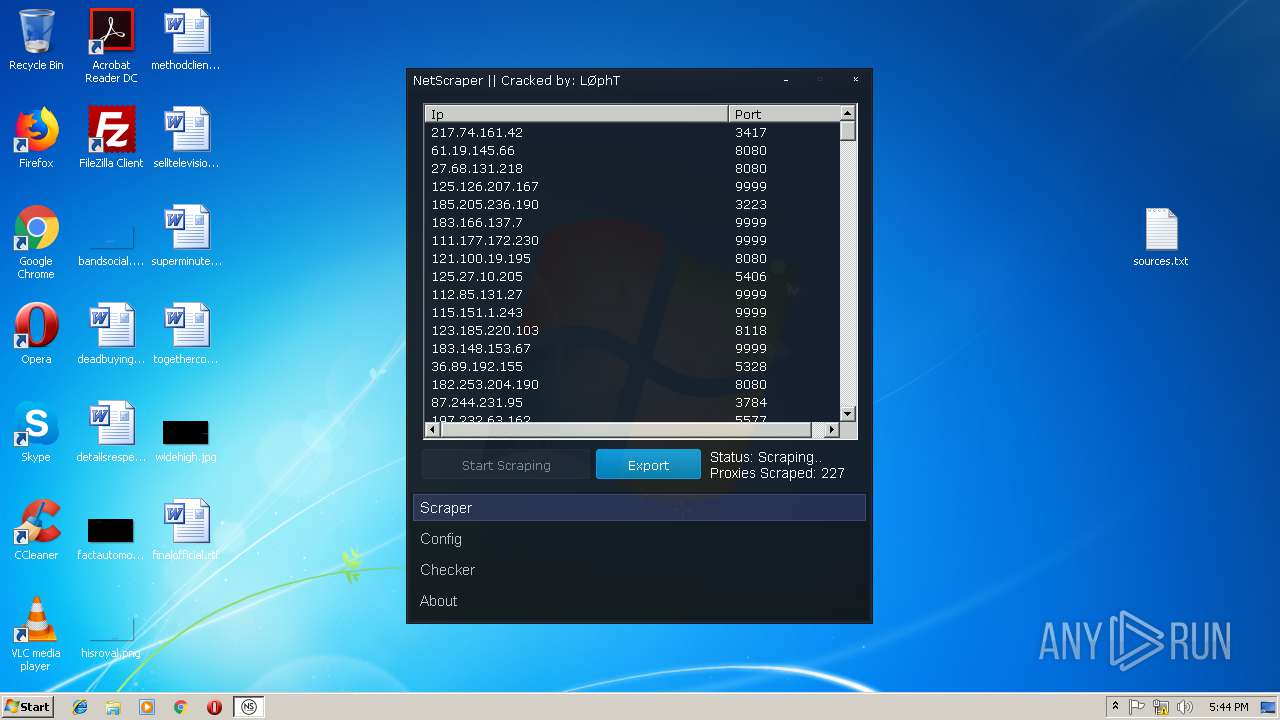
| File name: | Proxy Tools By o0hAcKeRbOi0o.rar |
| Full analysis: | https://app.any.run/tasks/314394a6-de5f-4012-bb66-452e49cba2bf |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2019, 17:42:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 141ACFAF9507C1F7CD370DA9070B7400 |
| SHA1: | AE3CFD5FCB129EE30F0983C673407165011D49EB |
| SHA256: | 4D722E1FF9D657A3A838388491551CDC056FAD8360D0D5E859E1426EB2F8ADB7 |
| SSDEEP: | 98304:2n1yXF9PH+NE4iLLo52aFMJc8s8qIs6WTl1LX2:V19/Fbn82a6QCWjLG |
MALICIOUS
Loads dropped or rewritten executable
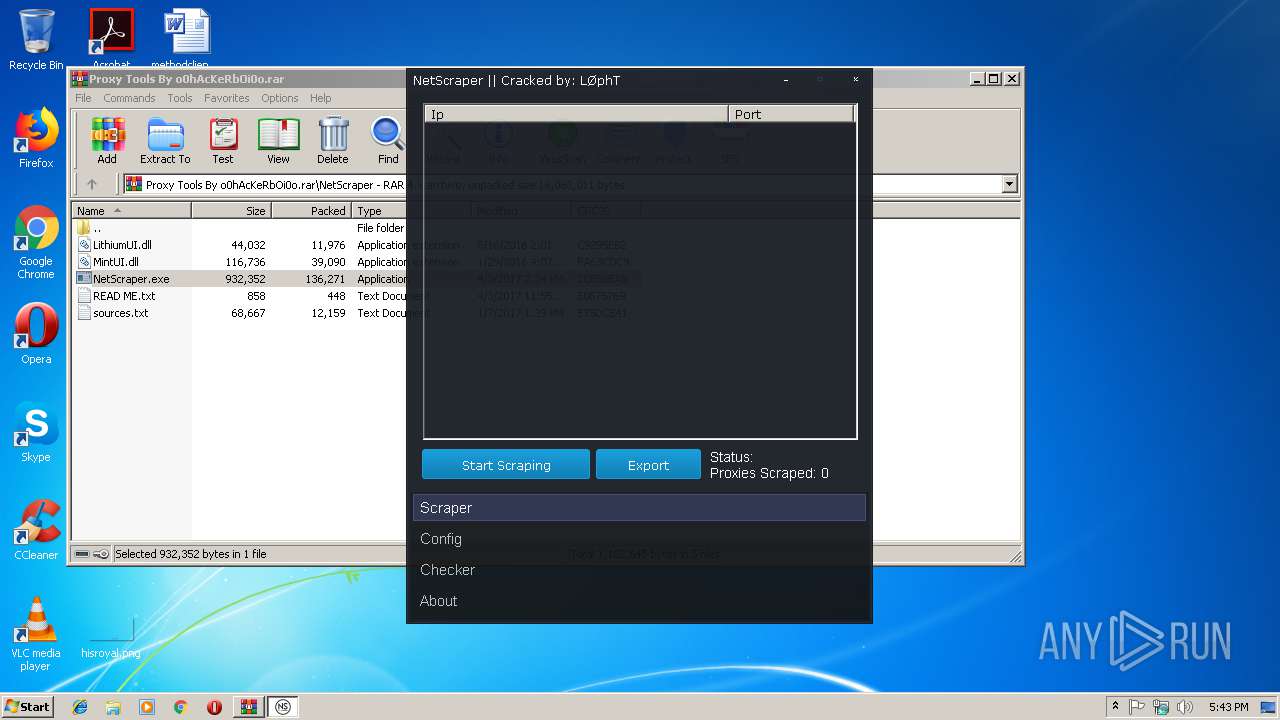
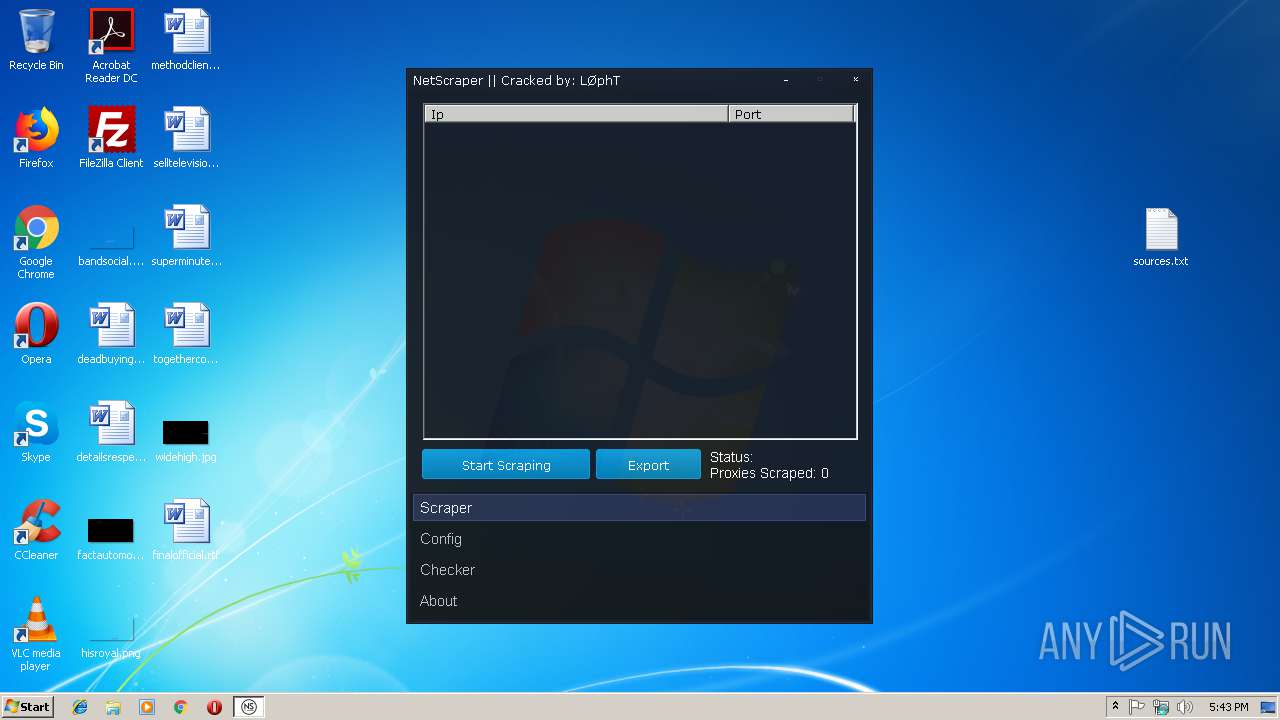
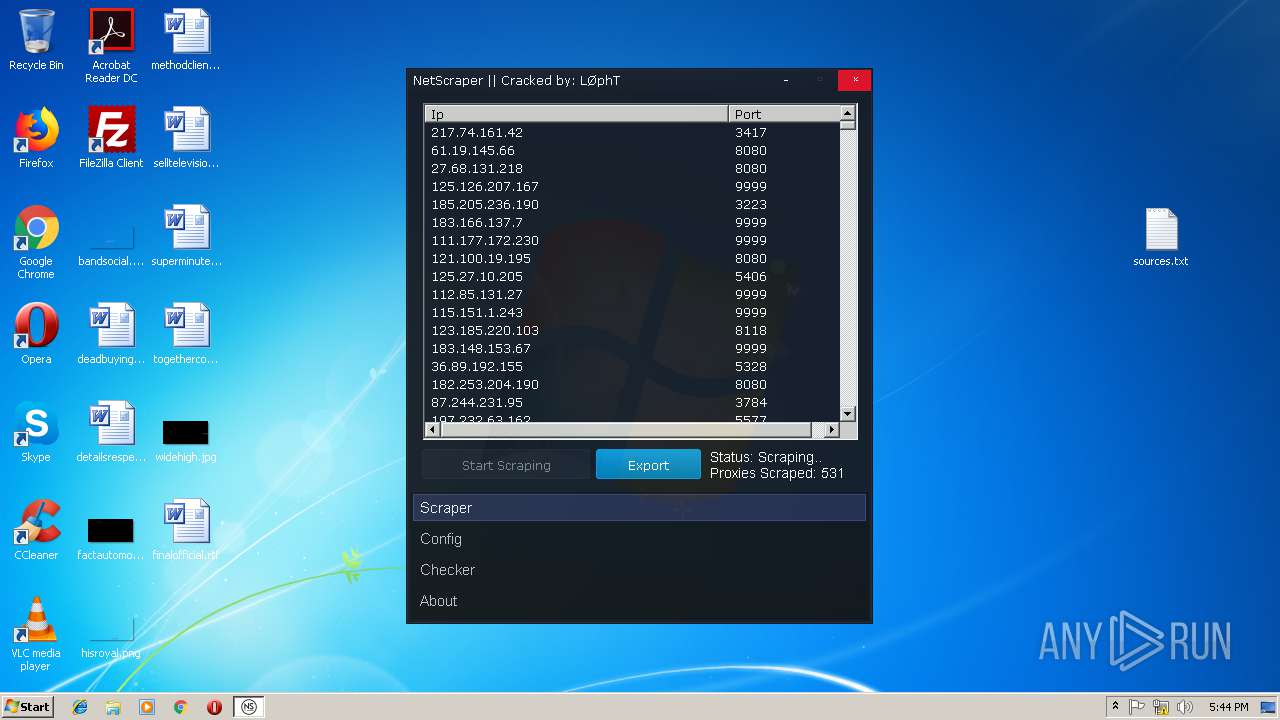
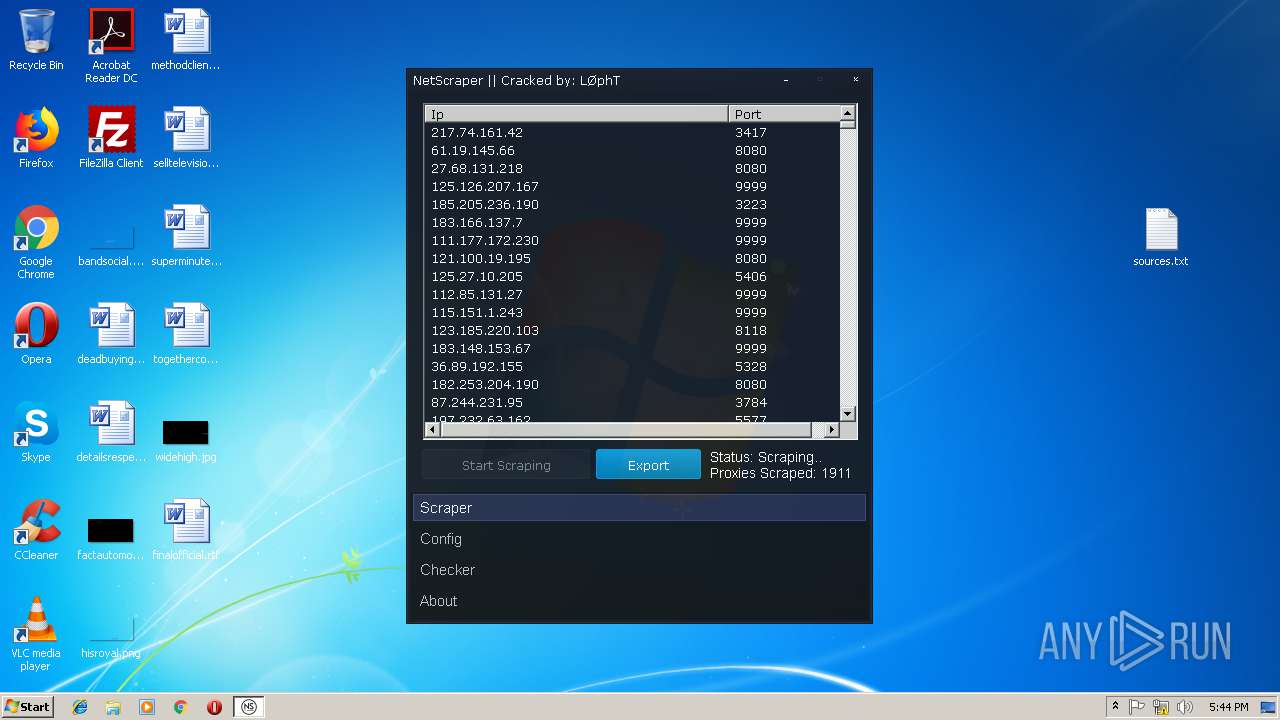
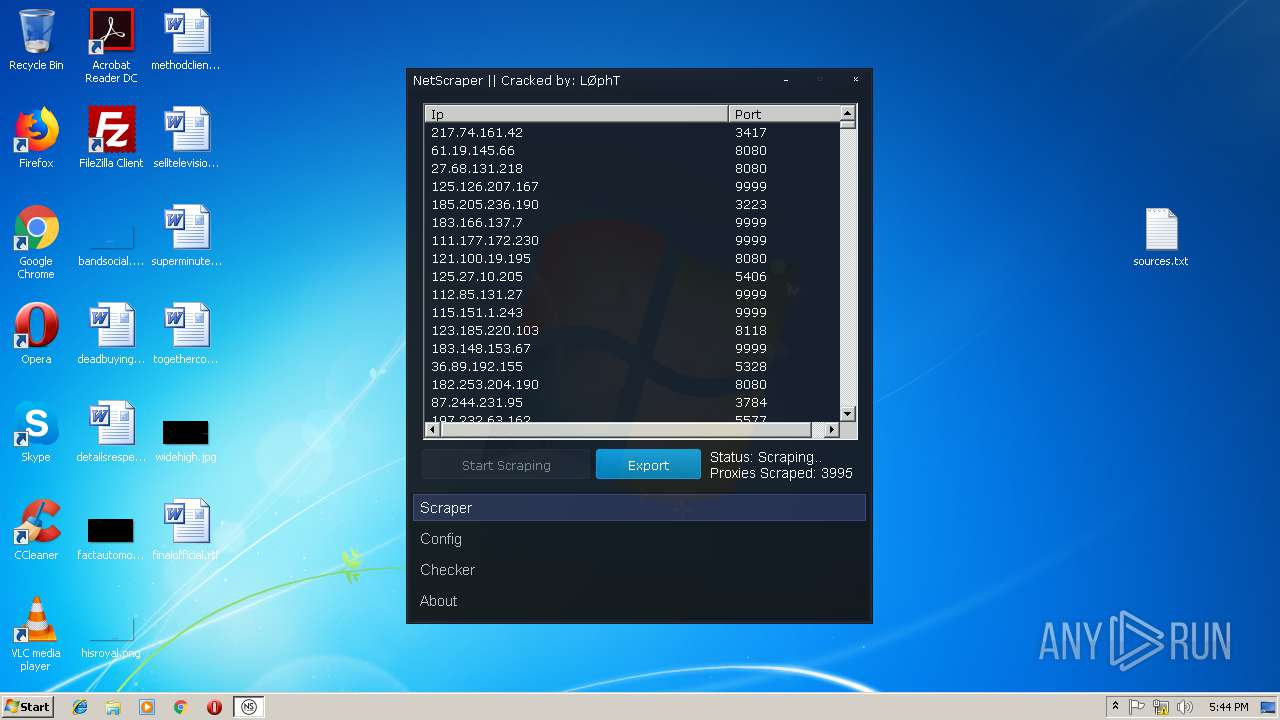
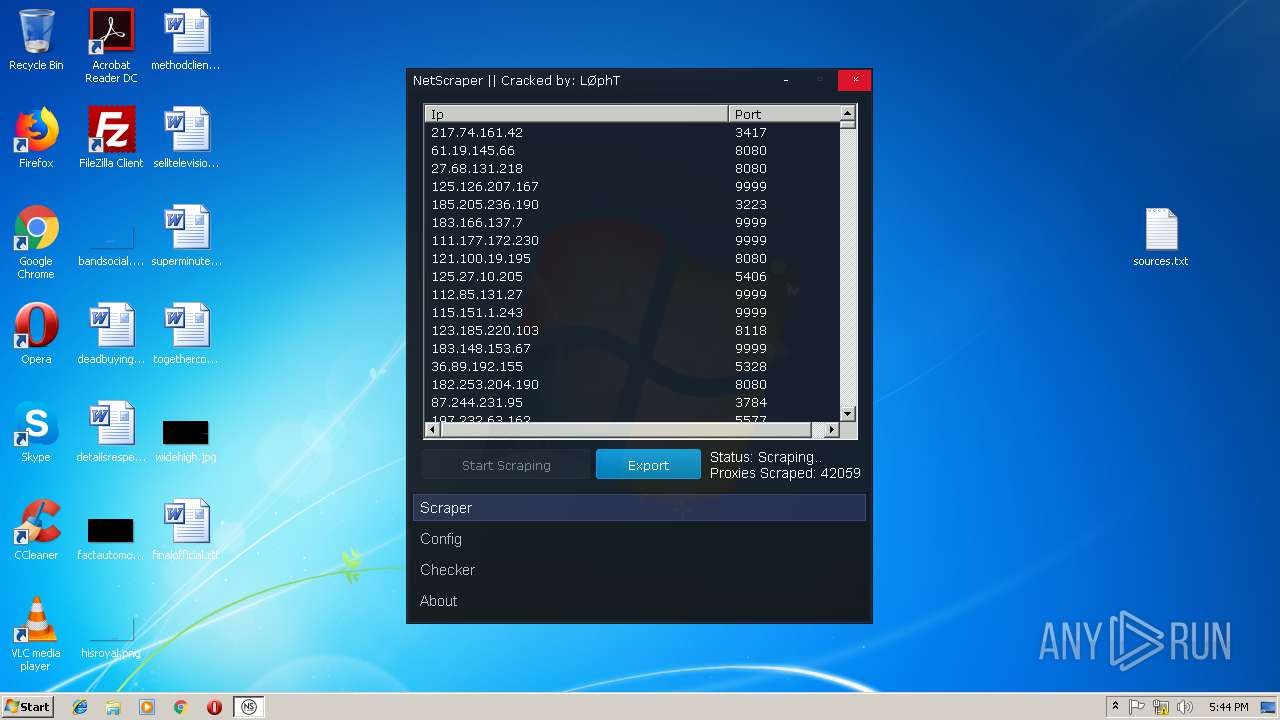
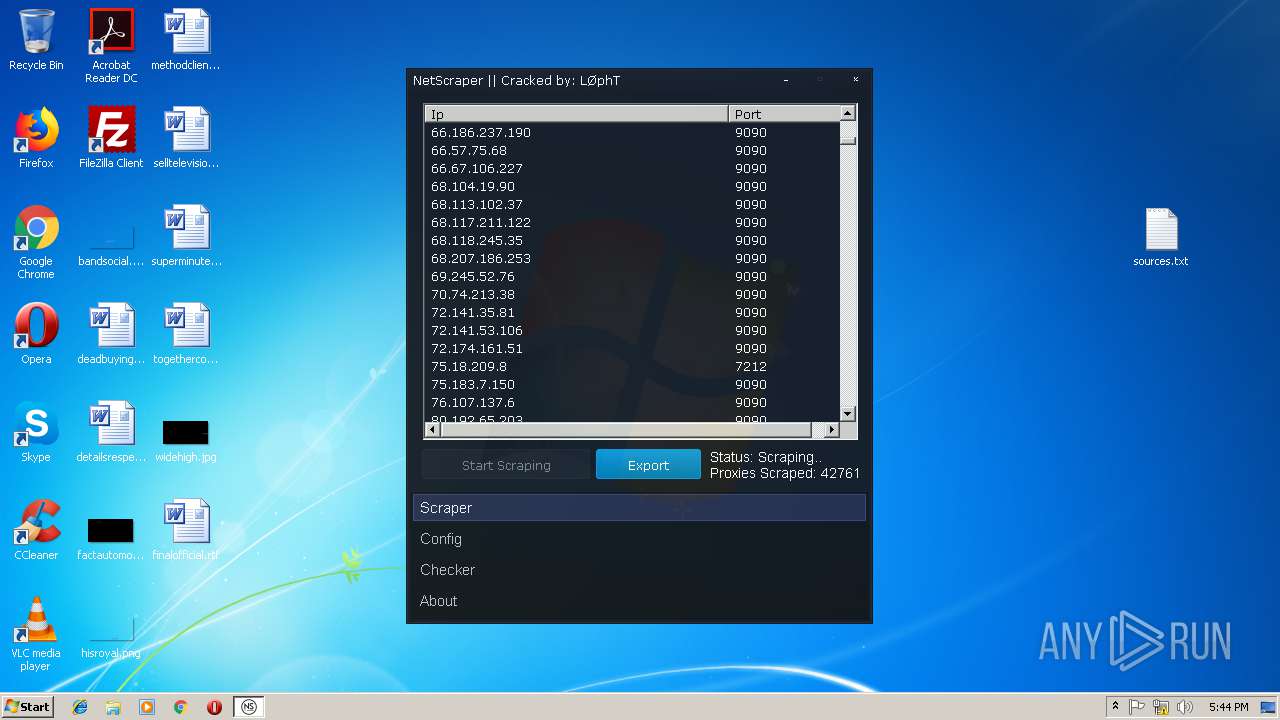
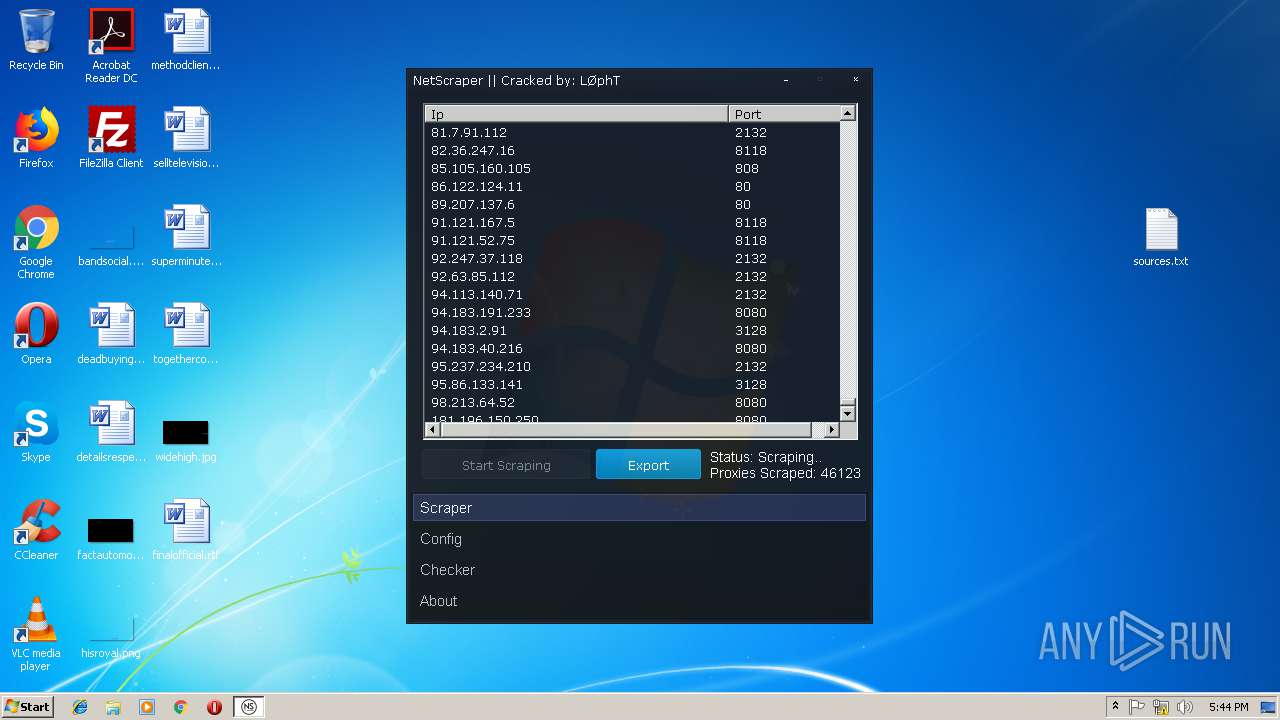
- NetScraper.exe (PID: 3508)
Application was dropped or rewritten from another process
- NetScraper.exe (PID: 3508)
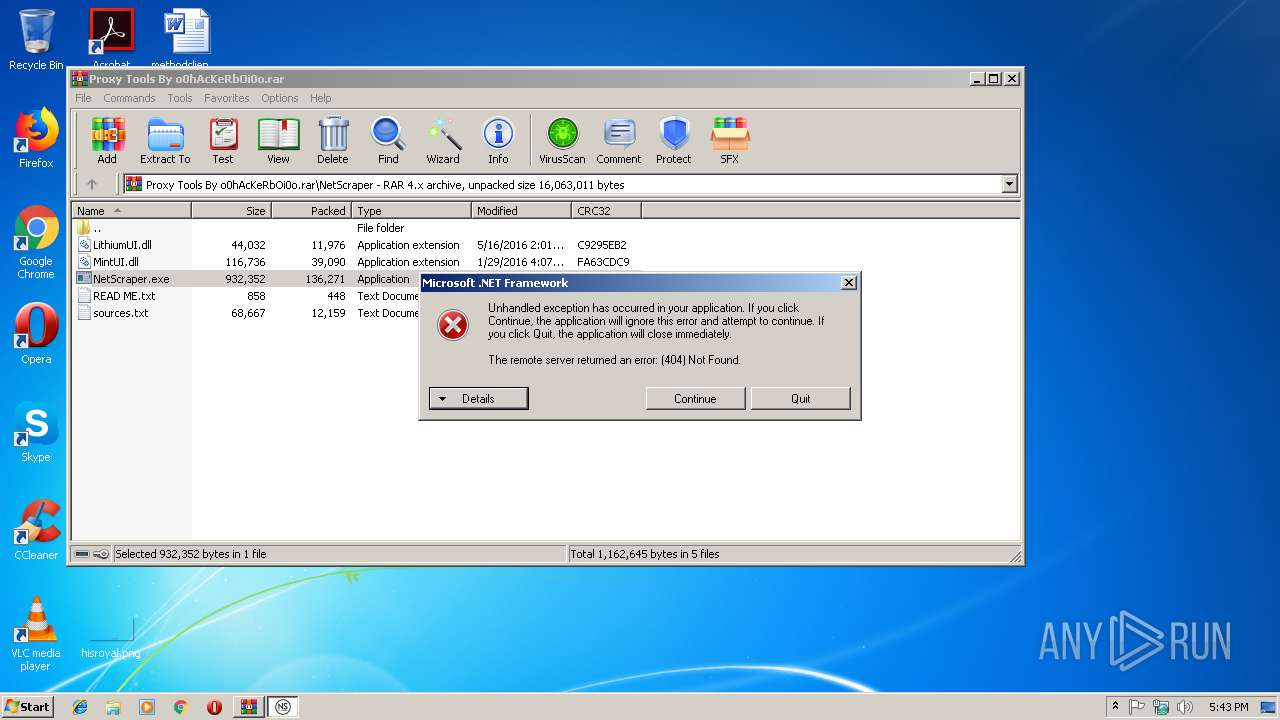
Connects to CnC server
- NetScraper.exe (PID: 3508)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3088)
Reads Internet Cache Settings
- NetScraper.exe (PID: 3508)
INFO
Reads settings of System Certificates
- NetScraper.exe (PID: 3508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 17880 |
|---|---|
| UncompressedSize: | 368097 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2012:08:13 21:16:13 |
| PackingMethod: | Normal |
| ArchivedFileName: | Gather Proxy 8.9\Data\agents.txt |
Total processes
32
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Proxy Tools By o0hAcKeRbOi0o.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3508 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\NetScraper\NetScraper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\NetScraper\NetScraper.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: NetScraper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 160
Read events
1 009
Write events
150
Delete events
1
Modification events
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Proxy Tools By o0hAcKeRbOi0o.rar | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
15
Suspicious files
0
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Data\geo.mmdb | — | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Data\configs.gp | text | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Gather Proxy.exe | executable | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\FacebookAPIClass.dll | executable | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\megaprox.txt | text | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\proxies.txt | text | |
MD5:— | SHA256:— | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Data\agents.txt | text | |
MD5:8520DC38FF84C55CEFA74D492D271DA4 | SHA256:FC73F46883AECB0AC9C944A2756CA2CF1AC0E60F963D92700C0DD62EADC3D72B | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Data\country.txt | text | |
MD5:F349544550AB3FA73C515A02B1E28A46 | SHA256:3E1DF9E1B2BCDD9223B8092D216F22472685788255441144F935795193454E24 | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Gather Proxy.exe.config | xml | |
MD5:365E8A1FAE1391145F187F048680FC08 | SHA256:40A15F3B0184FB80CC36F771B589D2338CDA22EBC2F0EF0711E0C69B4DBCE4CC | |||
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3088.30772\Gather Proxy 8.9\Data\autosp.ini | text | |
MD5:0AB7386476BFD6E6A7FDCAA91DA04D4F | SHA256:BA4DB1C4843A36822F68556D4F2AC5B815F3E7B063D28D8905FD6084B594EC40 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
392
TCP/UDP connections
211
DNS requests
197
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3508 | NetScraper.exe | GET | 200 | 104.27.143.11:80 | http://www.forumproxyleecher.com/liststat.php | US | html | 15.9 Kb | malicious |
3508 | NetScraper.exe | GET | 404 | 73.133.210.28:80 | http://notepad.win/updates.txt | US | html | 209 b | malicious |
3508 | NetScraper.exe | GET | 301 | 172.217.18.97:80 | http://vip-socks24.blogspot.com/feeds/posts/default | US | html | 227 b | whitelisted |
3508 | NetScraper.exe | GET | 200 | 72.52.4.90:80 | http://ww1.proxylistchecker.org/?sub1=49233a70-27db-11e9-875e-7865bc56ba45 | US | html | 70.7 Kb | malicious |
3508 | NetScraper.exe | GET | 200 | 109.201.133.56:80 | http://proxylistchecker.org/proxylists.php?t=&p=35 | NL | html | 320 b | suspicious |
3508 | NetScraper.exe | GET | 301 | 92.48.97.11:80 | http://samair.ru/proxy/proxy-27.htm | GB | html | 241 b | malicious |
3508 | NetScraper.exe | GET | 404 | 172.217.18.97:80 | http://irc-proxies24.blogspot.com/feeds/posts/default | US | html | 3.13 Kb | whitelisted |
3508 | NetScraper.exe | GET | 200 | 172.217.18.179:80 | http://www.vipsocks24.net/feeds/posts/default | US | xml | 42.4 Kb | whitelisted |
3508 | NetScraper.exe | GET | 301 | 92.48.97.11:80 | http://samair.ru/proxy/proxy-25.htm | GB | html | 241 b | malicious |
3508 | NetScraper.exe | GET | 301 | 92.48.97.11:80 | http://samair.ru/proxy/proxy-26.htm | GB | html | 241 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3508 | NetScraper.exe | 172.217.18.179:80 | www.vipsocks24.net | Google Inc. | US | whitelisted |
3508 | NetScraper.exe | 73.133.210.28:80 | notepad.win | Comcast Cable Communications, LLC | US | suspicious |
3508 | NetScraper.exe | 92.48.97.11:80 | samair.ru | Simply Transit Ltd | GB | malicious |
3508 | NetScraper.exe | 172.217.18.97:80 | vip-socks24.blogspot.com | Google Inc. | US | whitelisted |
3508 | NetScraper.exe | 104.27.143.11:80 | www.forumproxyleecher.com | Cloudflare Inc | US | shared |
3508 | NetScraper.exe | 69.64.54.126:80 | nntime.com | server4you Inc. | US | malicious |
— | — | 109.201.133.56:80 | proxylistchecker.org | NForce Entertainment B.V. | NL | unknown |
3508 | NetScraper.exe | 185.209.23.43:80 | 50na50.net | NovoServe B.V. | NL | suspicious |
3508 | NetScraper.exe | 185.209.23.43:443 | 50na50.net | NovoServe B.V. | NL | suspicious |
3508 | NetScraper.exe | 134.119.217.244:80 | spys.ru | velia.net Internetdienste GmbH | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad.win |
| malicious |
vip-socks24.blogspot.com |
| whitelisted |
www.forumproxyleecher.com |
| malicious |
proxylistchecker.org |
| suspicious |
samair.ru |
| malicious |
premproxy.com |
| unknown |
ww1.proxylistchecker.org |
| malicious |
www.vipsocks24.net |
| whitelisted |
www.my-proxy.com |
| unknown |
irc-proxies24.blogspot.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .cf Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3508 | NetScraper.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
1060 | svchost.exe | Misc activity | ET MALWARE All Numerical .cn Domain Likely Malware Related |
1060 | svchost.exe | Misc activity | ET MALWARE All Numerical .cn Domain Likely Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3508 | NetScraper.exe | A Network Trojan was detected | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Misc activity | ET MALWARE All Numerical .cn Domain Likely Malware Related |
3508 | NetScraper.exe | A Network Trojan was detected | ET CNC Zeus Tracker Reported CnC Server group 23 |
1060 | svchost.exe | Misc activity | ET MALWARE All Numerical .cn Domain Likely Malware Related |