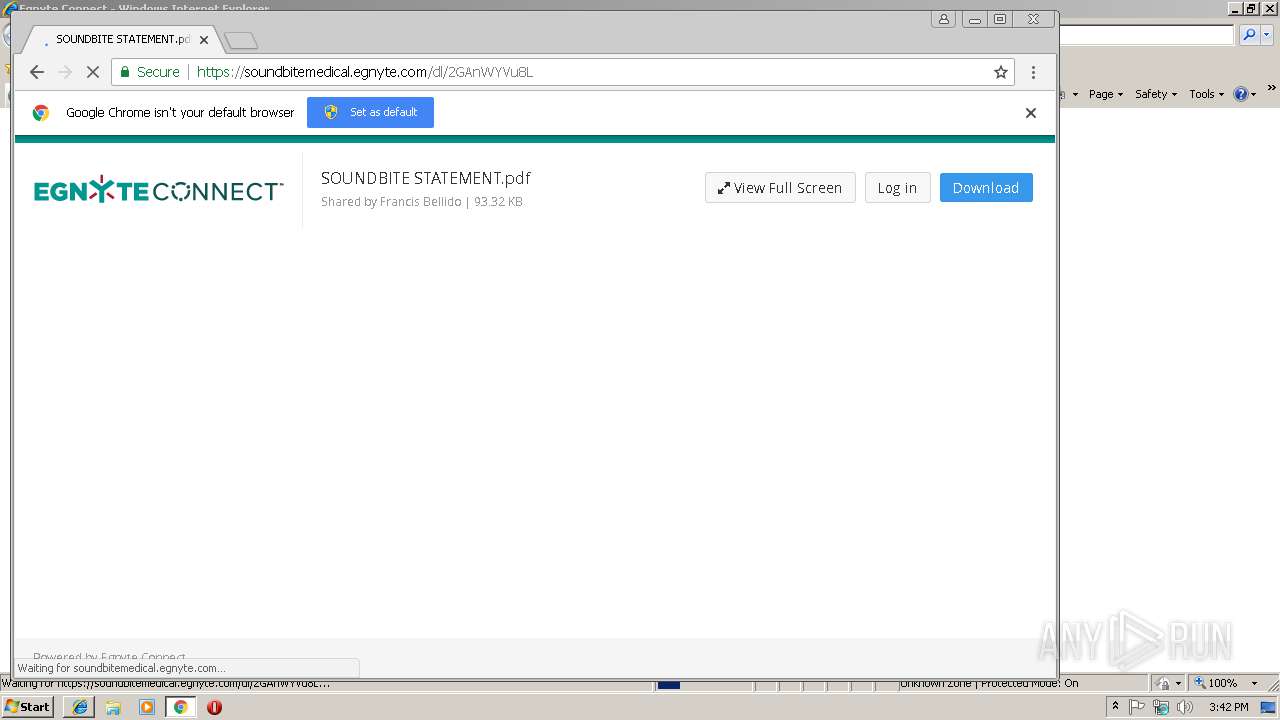
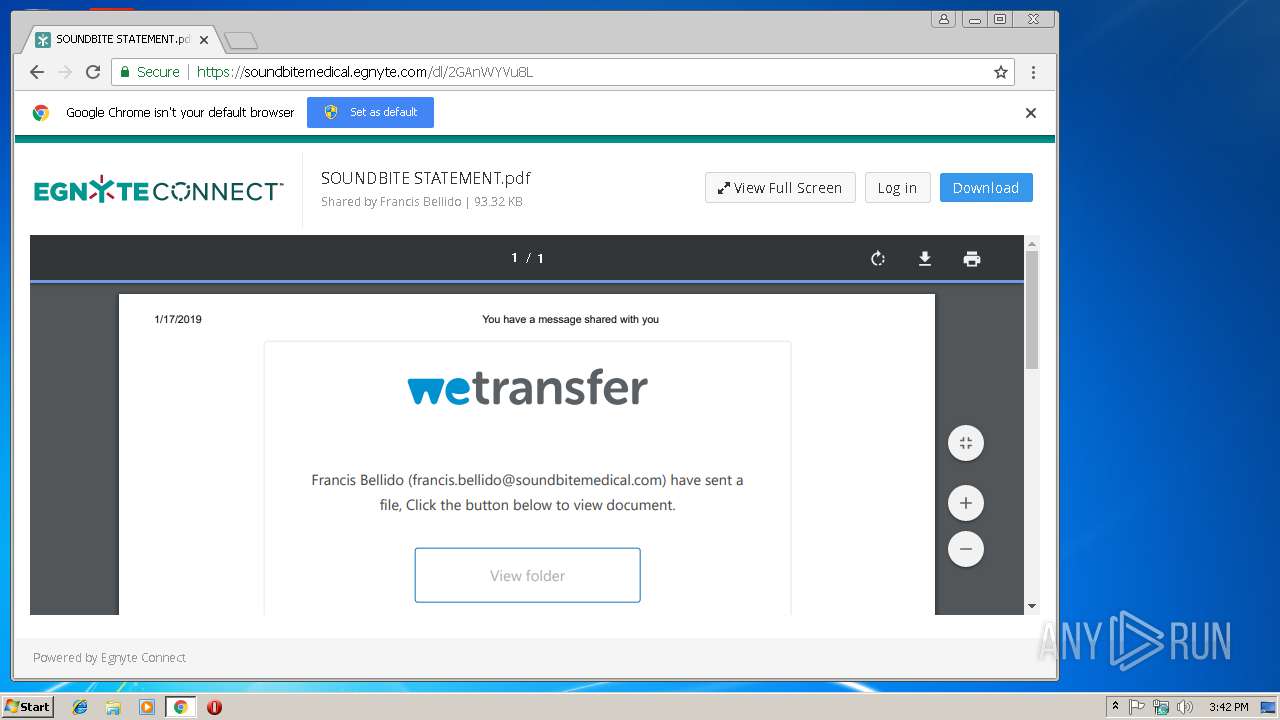
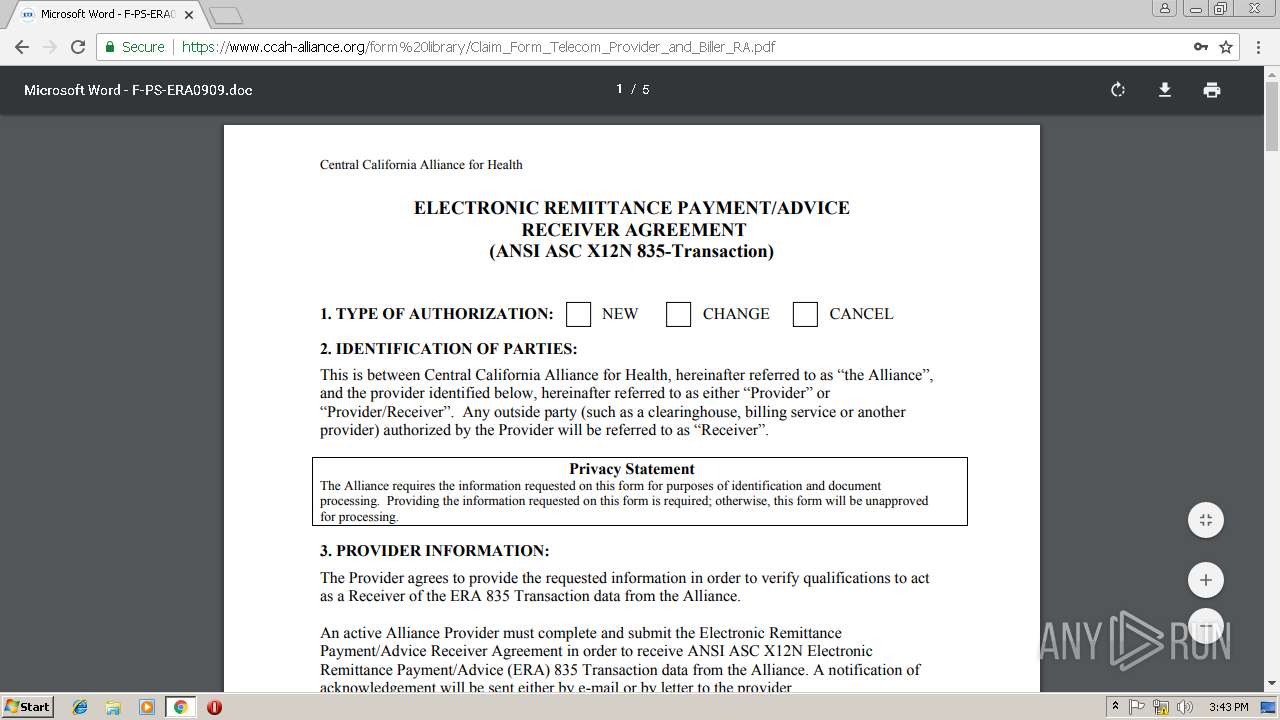
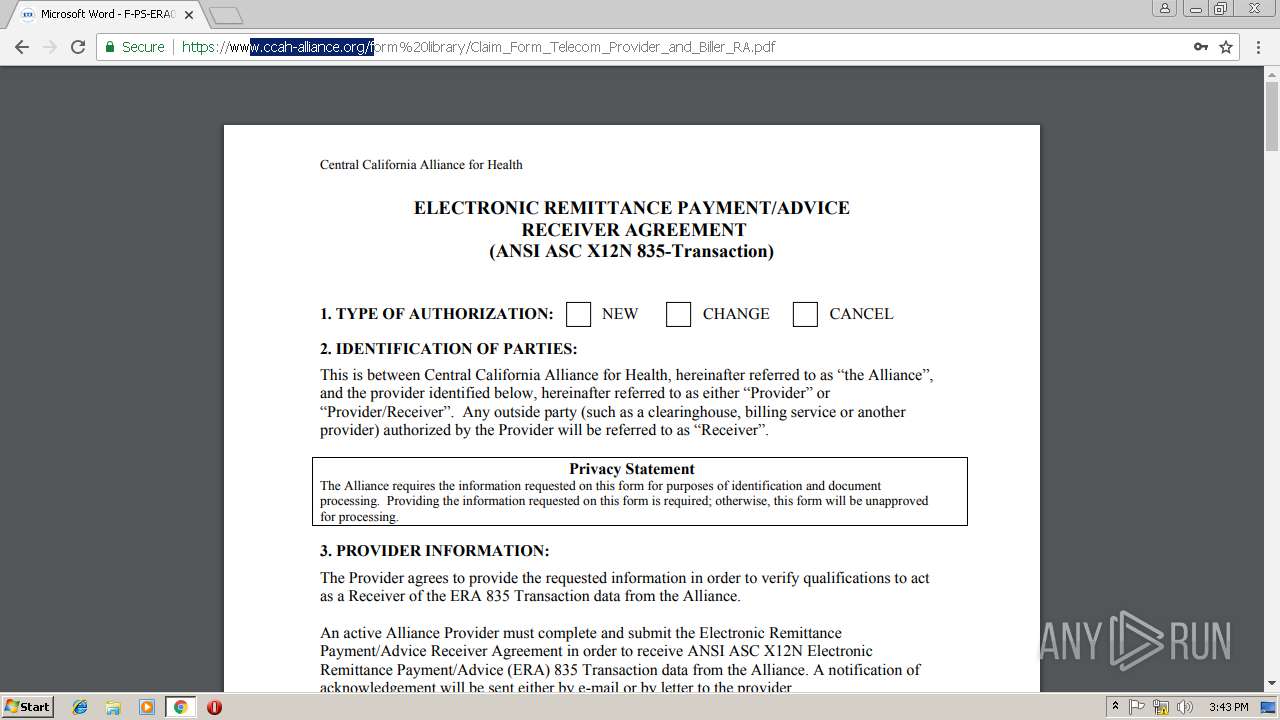
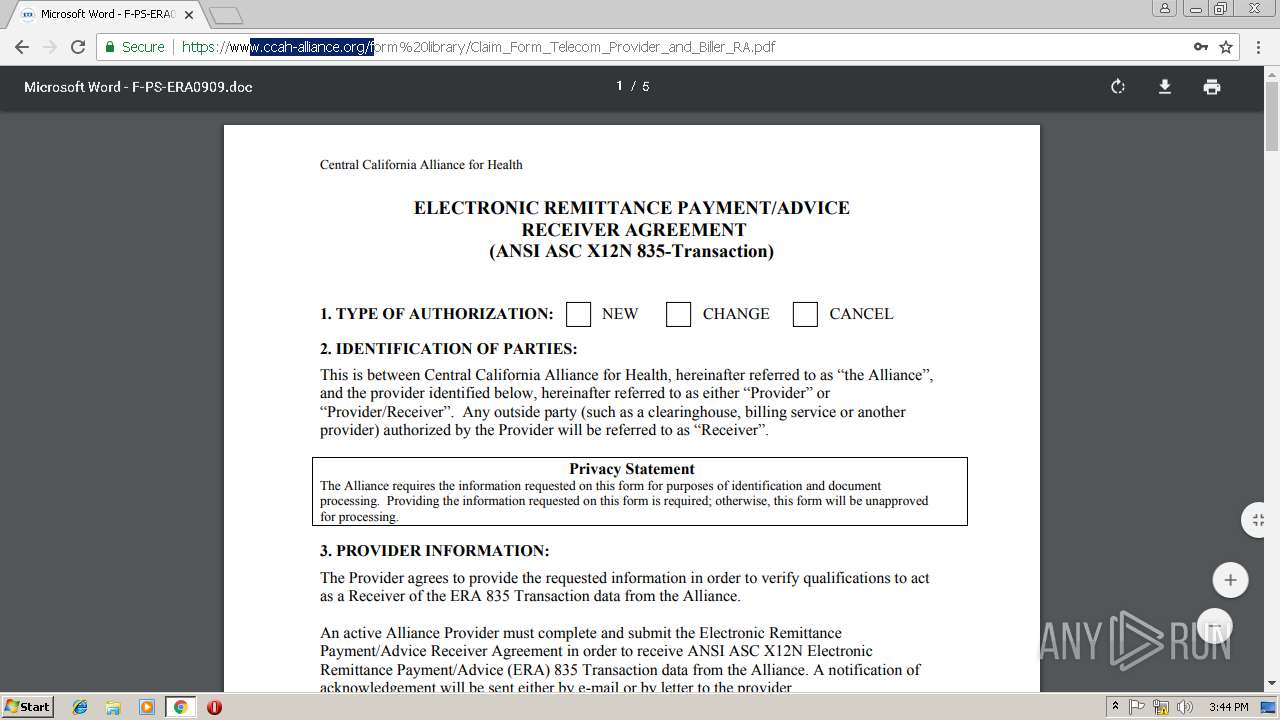
| URL: | https://soundbitemedical.egnyte.com/dl/2GAnWYVu8L |
| Full analysis: | https://app.any.run/tasks/98192934-84f3-4baf-a557-651c8e03a448 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2019, 15:41:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9154B992037F98B93163EF594823AAAC |
| SHA1: | B45A7D9266E71CDDF465541BA15398A09E1C41F4 |
| SHA256: | 4D5C77EB20DA987EEB9D9B572CFF01CCCBB51677DA1701443F3534616A9AB9A9 |
| SSDEEP: | 3:N8HeKdGEFAhaxJMiYUn:2+0FAYn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 2952)
Creates files in the user directory
- iexplore.exe (PID: 3124)
Reads Internet Cache Settings
- iexplore.exe (PID: 3124)
Reads internet explorer settings
- iexplore.exe (PID: 3124)
Application launched itself
- chrome.exe (PID: 3348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
21
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=ppapi --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --ppapi-flash-args --lang=en-US --device-scale-factor=1 --ppapi-antialiased-text-enabled=0 --ppapi-subpixel-rendering-setting=0 --service-request-channel-token=0D803A4379B3951244692750F3F1DE0A --mojo-platform-channel-handle=4168 --ignored=" --type=renderer " /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --service-pipe-token=C11335E437BC67FE477AFE26CC22E850 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C11335E437BC67FE477AFE26CC22E850 --renderer-client-id=3 --mojo-platform-channel-handle=2156 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=DEB9C25BF89F781FA164D704E280453E --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=DEB9C25BF89F781FA164D704E280453E --renderer-client-id=8 --mojo-platform-channel-handle=4084 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6d3c00b0,0x6d3c00c0,0x6d3c00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=C43D7CEC065644EA03C93DDD9F46E173 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C43D7CEC065644EA03C93DDD9F46E173 --renderer-client-id=11 --mojo-platform-channel-handle=2308 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=3B978DBF8F8D38F9C446BEAFF13C4190 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3B978DBF8F8D38F9C446BEAFF13C4190 --renderer-client-id=6 --mojo-platform-channel-handle=3532 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=DEF5FA0F18C47AF3BB8ECE722BE9674B --mojo-platform-channel-handle=3228 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=AAE0A623F61E2AC180E74602510A2A17 --mojo-platform-channel-handle=976 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,3238475376321933939,1515638116460801673,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=3E5A739513A68EB78F882BB239B8EA28 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3E5A739513A68EB78F882BB239B8EA28 --renderer-client-id=14 --mojo-platform-channel-handle=2136 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
894
Read events
774
Write events
115
Delete events
5
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {640D3E2B-1A6E-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070100040011000F0029002D00EB01 | |||
Executable files
0
Suspicious files
56
Text files
116
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\2GAnWYVu8L[1].txt | — | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@egnyte[1].txt | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\mpmanager[1].js | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\fileFolderLinks[1].css | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\font-awesome.min[1].css | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\shCoreDefault[1].css | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\jquery-1.7.2[1].js | text | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\2GAnWYVu8L[1].htm | html | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\reset[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
52
DNS requests
27
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
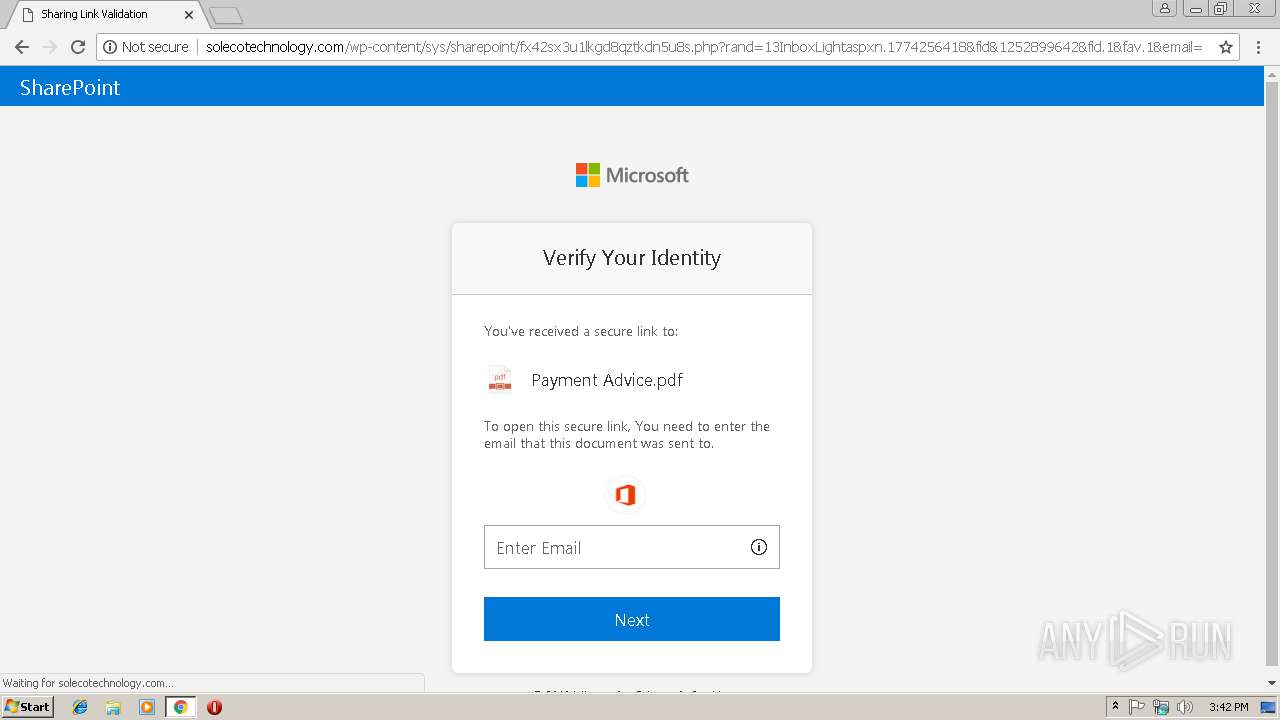
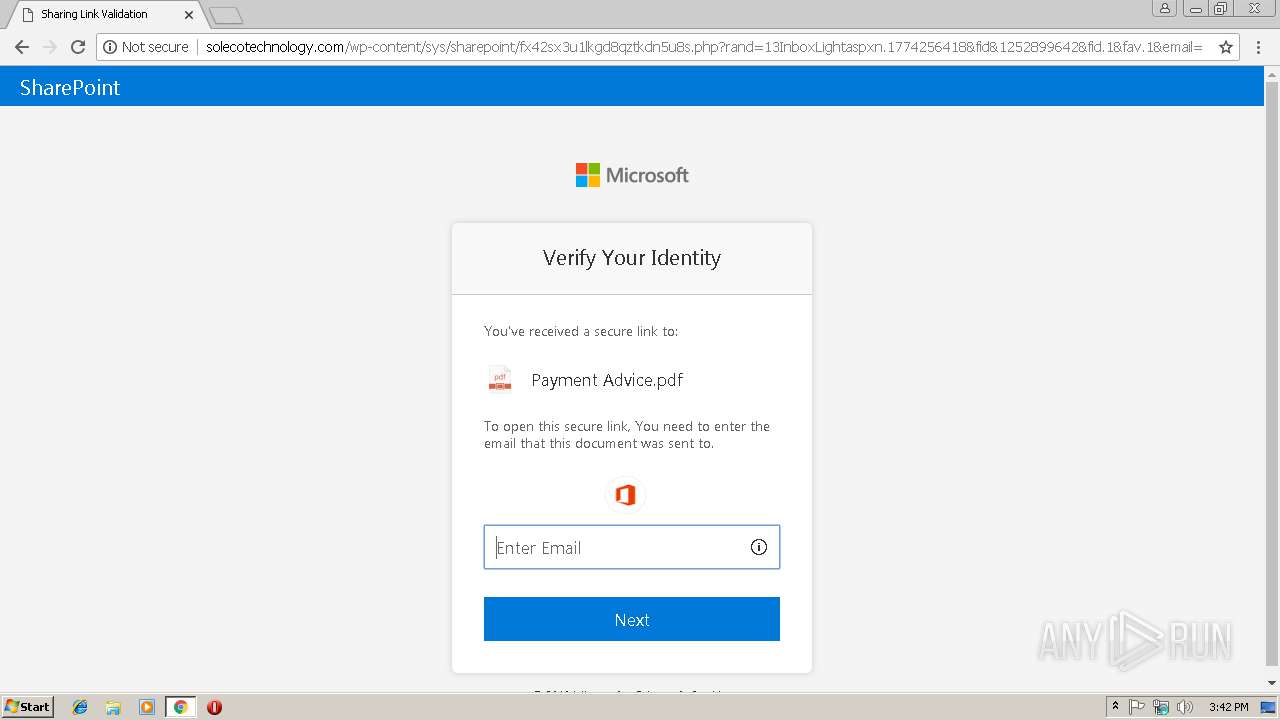
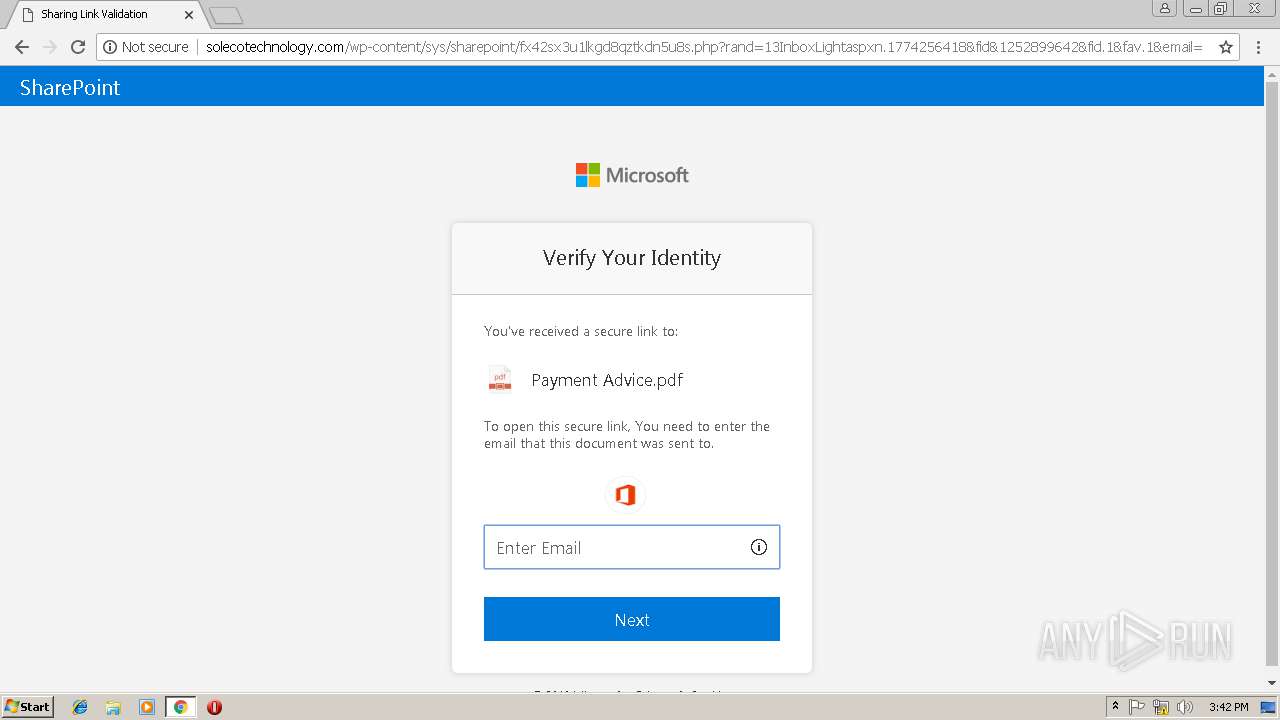
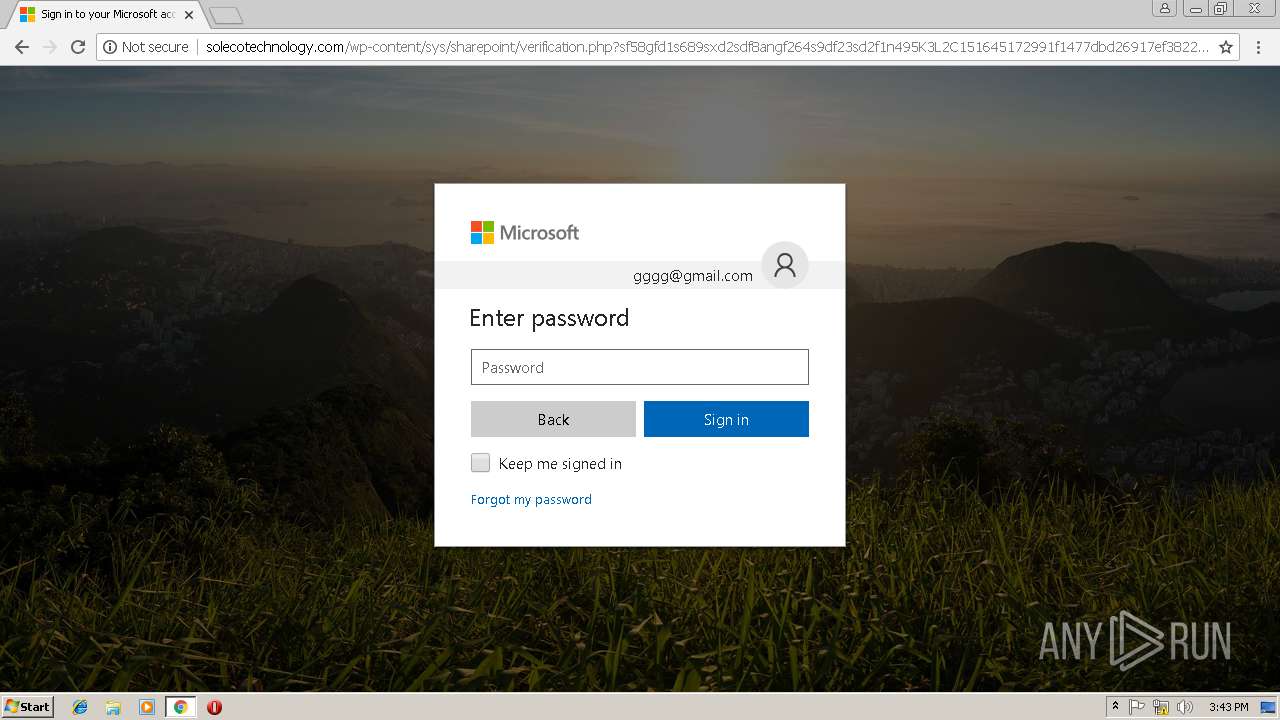
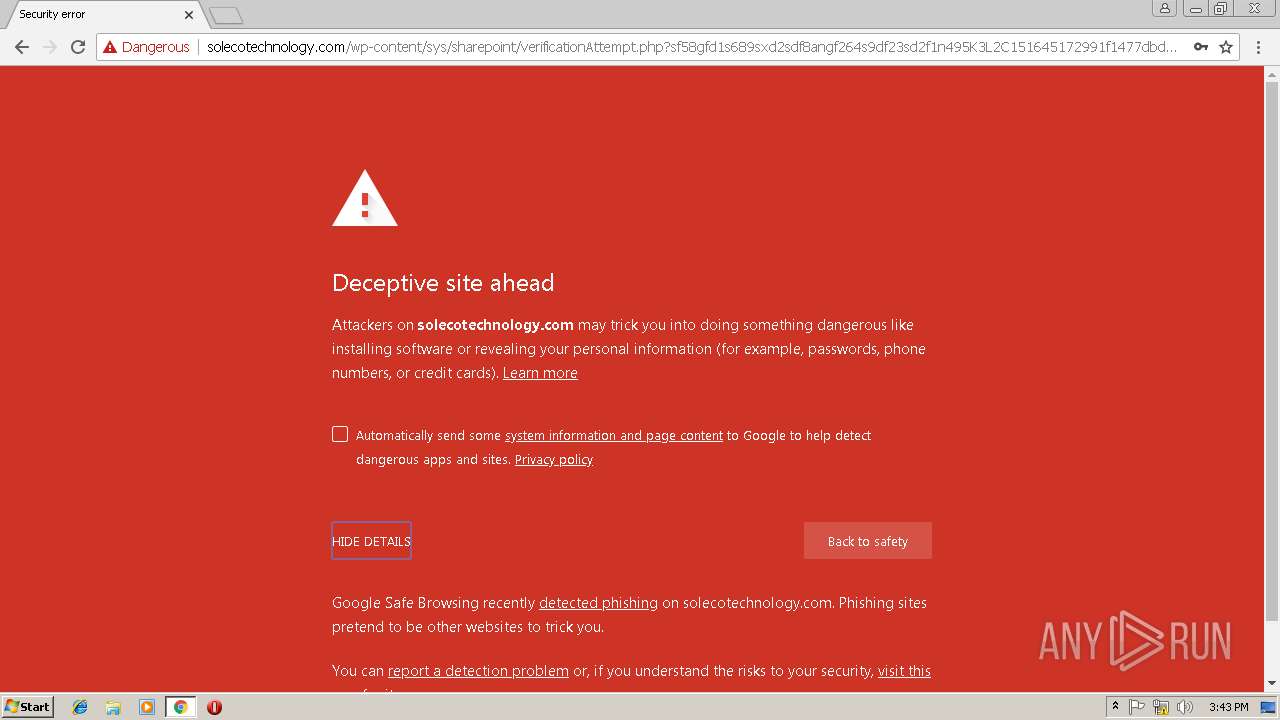
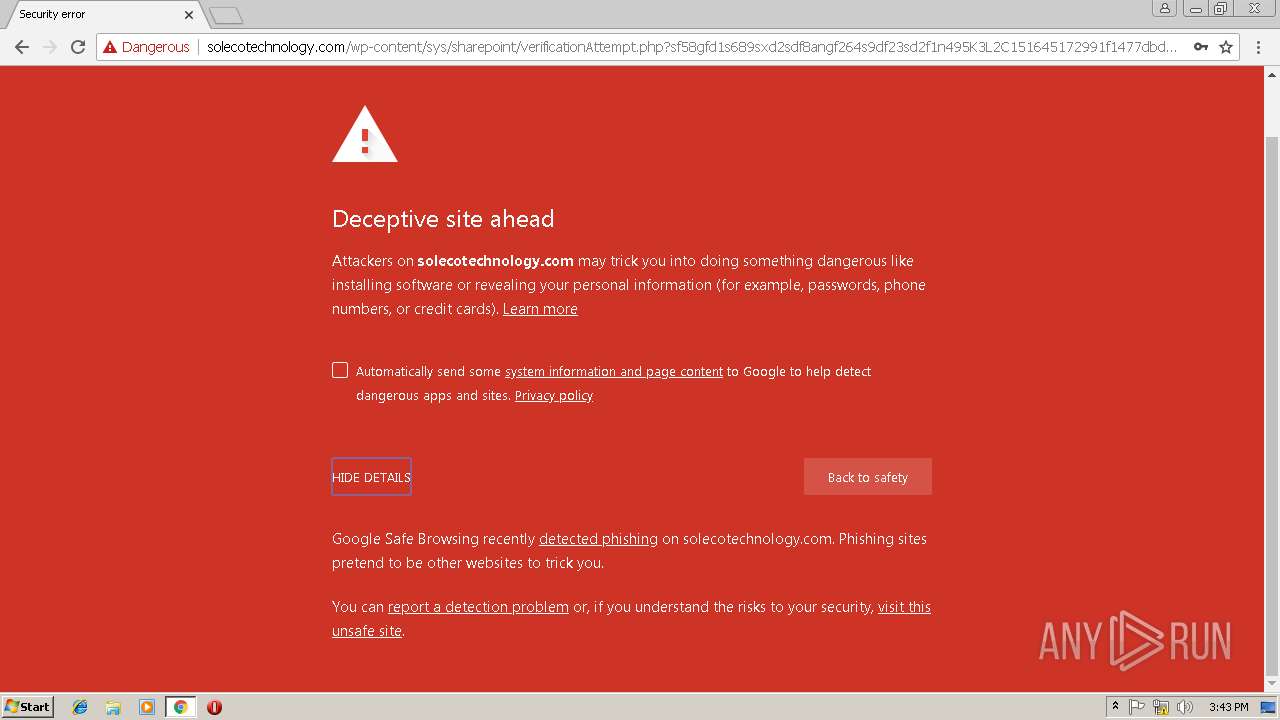
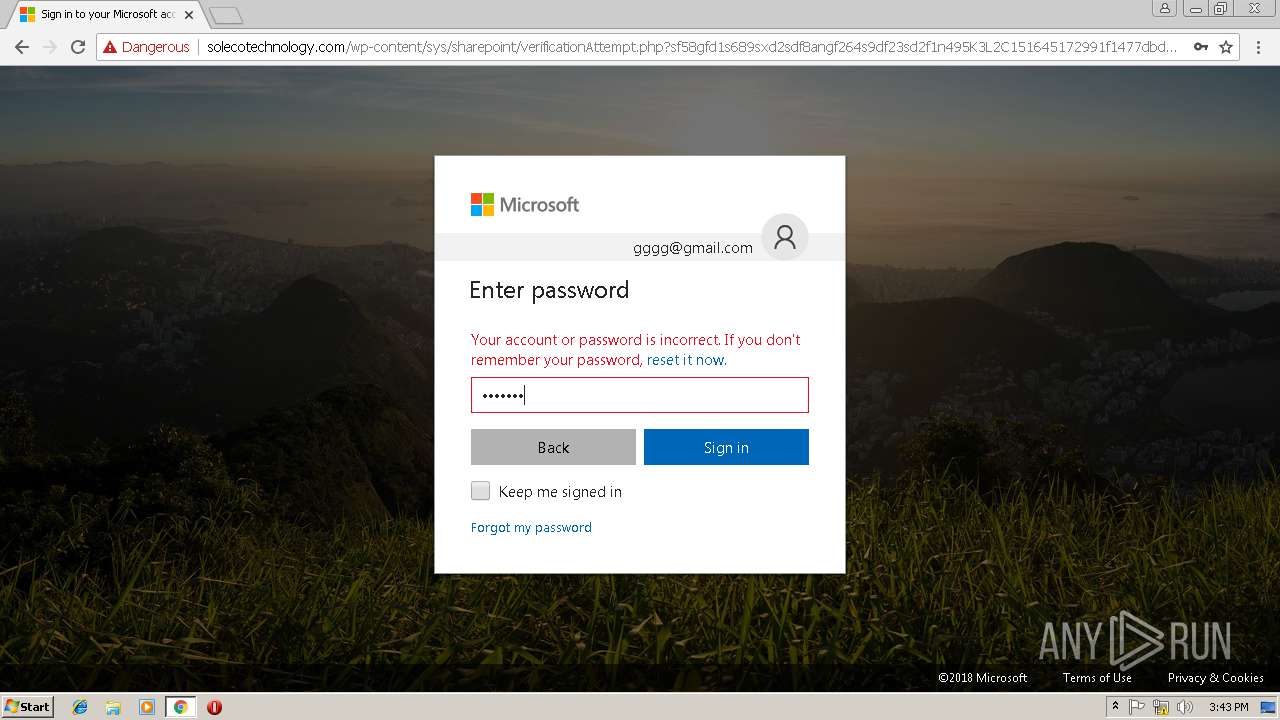
3348 | chrome.exe | GET | — | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/ | US | — | — | suspicious |
3348 | chrome.exe | GET | 302 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/ | US | — | — | suspicious |
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/files/Converged1033.css | US | text | 84.9 Kb | suspicious |
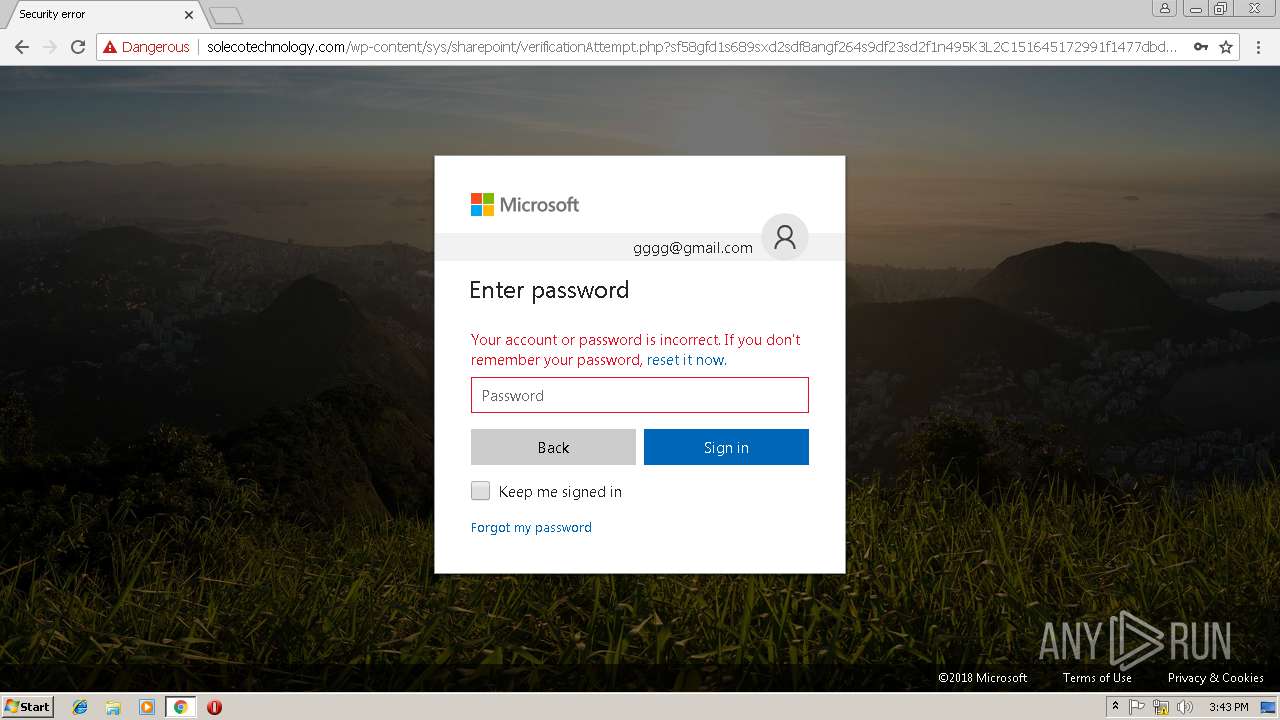
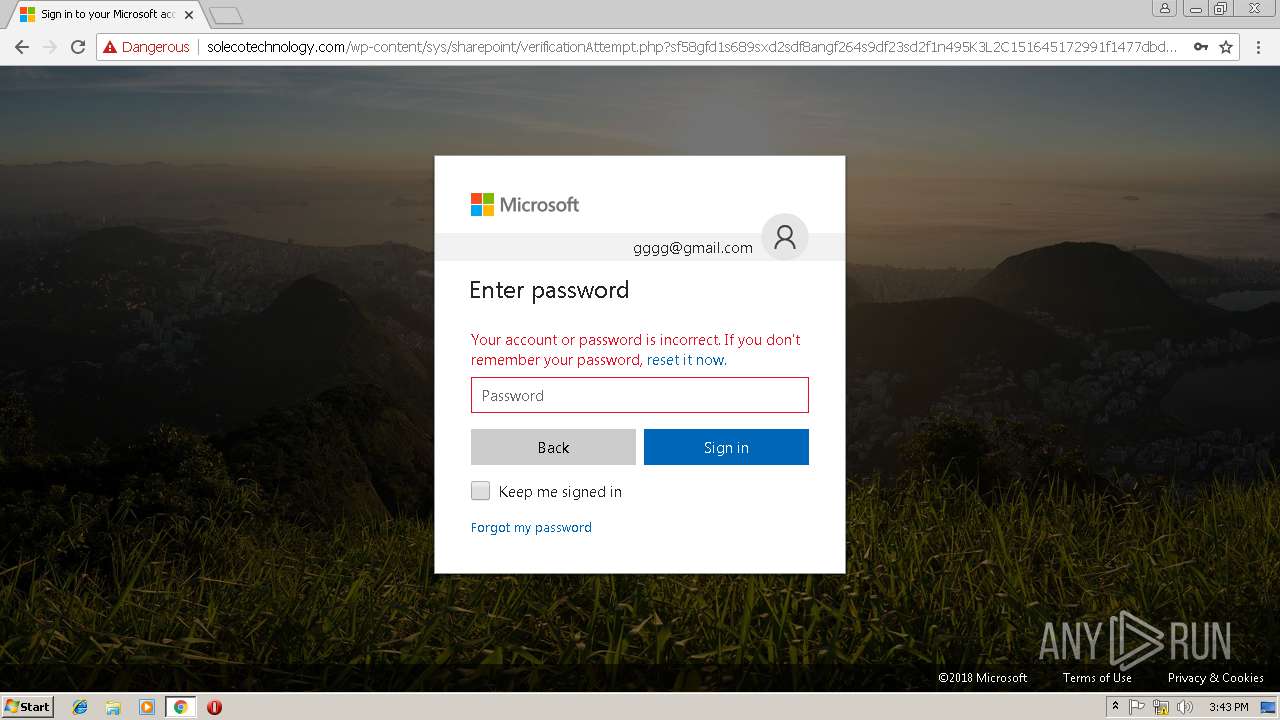
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/fx42sx3u1lkgd8qztkdn5u8s.php?rand=13InboxLightaspxn.1774256418&fid&1252899642&fid.1&fav.1&email= | US | html | 4.20 Kb | suspicious |
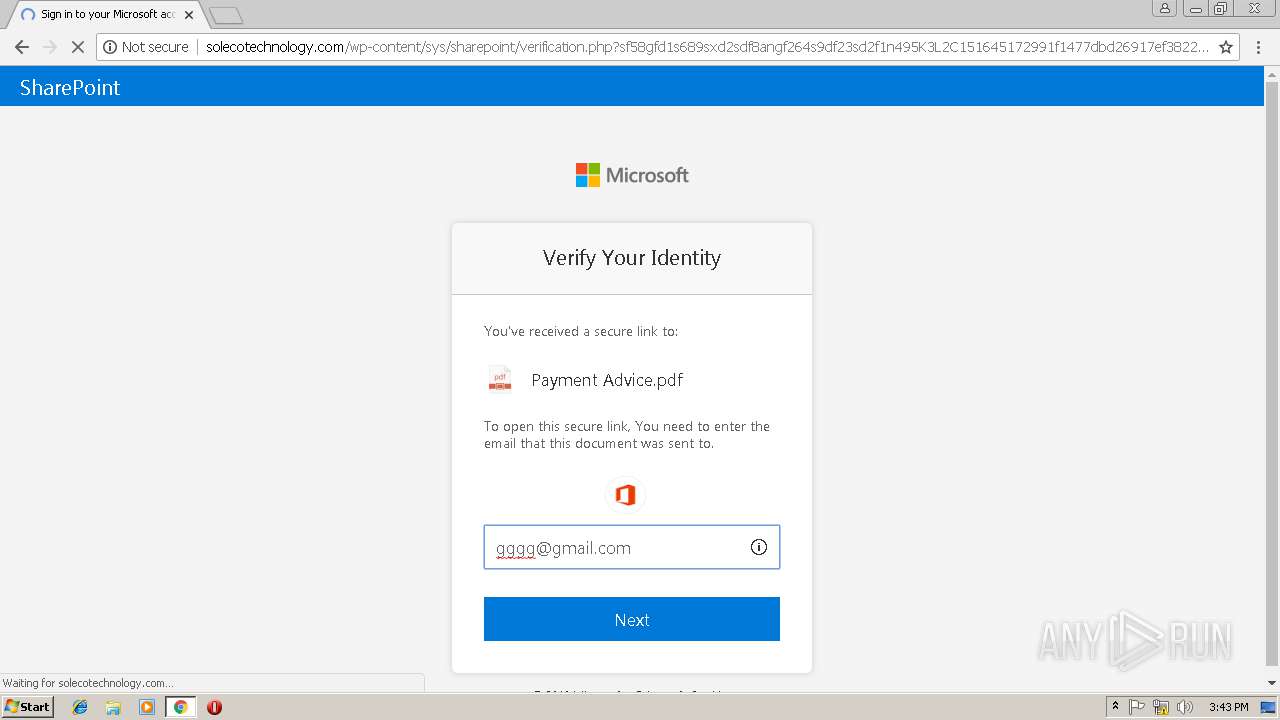
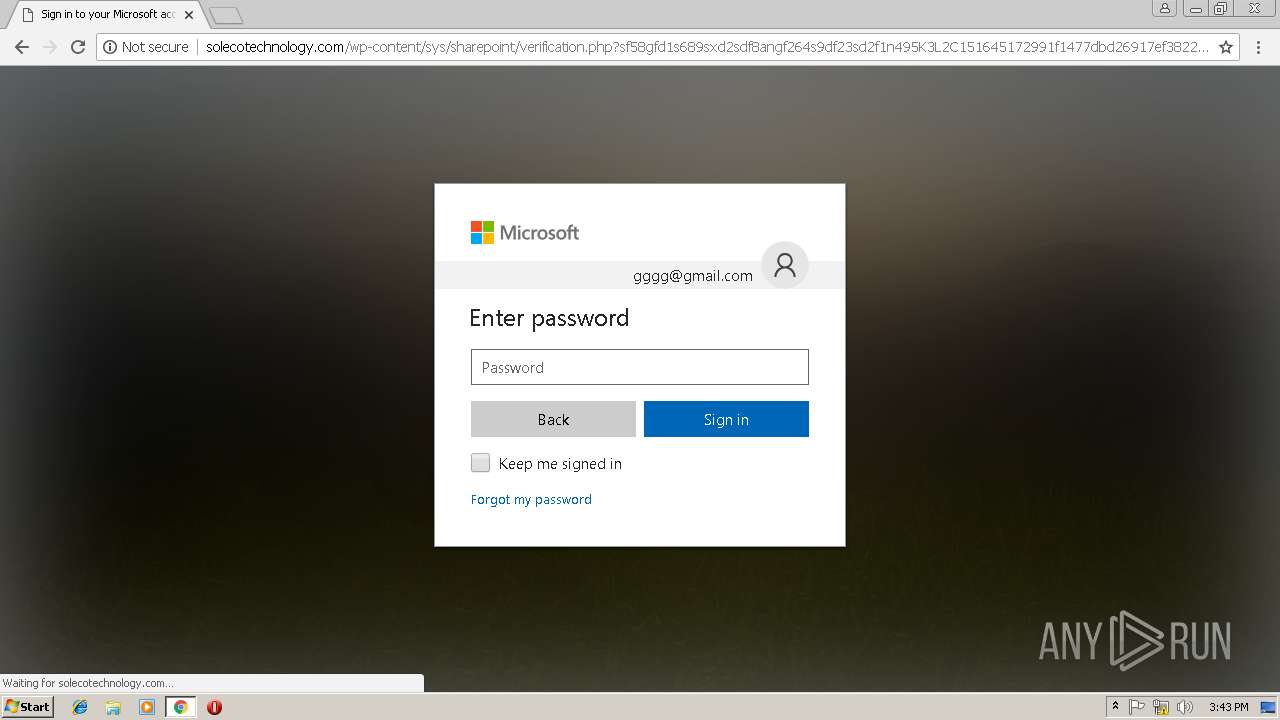
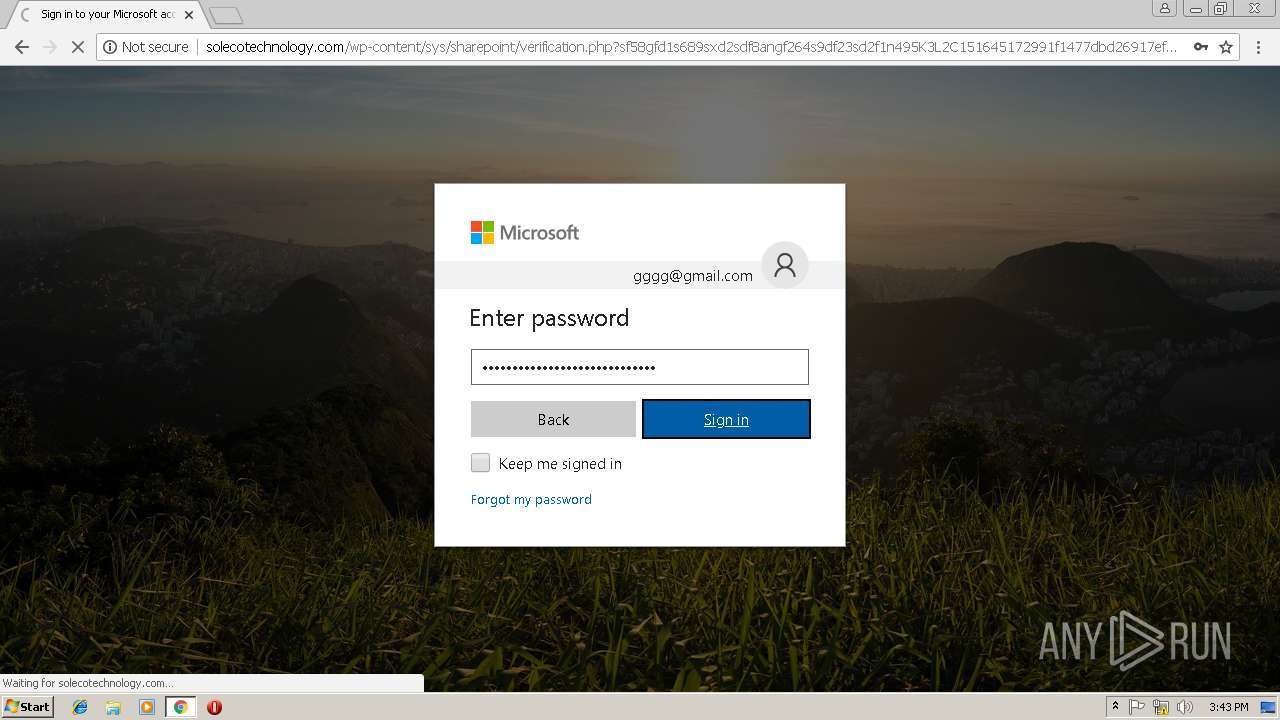
3348 | chrome.exe | POST | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/verification.php?sf58gfd1s689sxd2sdf8angf264s9df23sd2f1n495K3L2C151645172991f1477dbd26917ef3822423f62e984a91f1477dbd26917ef3822423f62e984a91f1477dbd | US | html | 9.76 Kb | suspicious |
3348 | chrome.exe | POST | 302 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/script/throwit_first.php | US | — | — | suspicious |
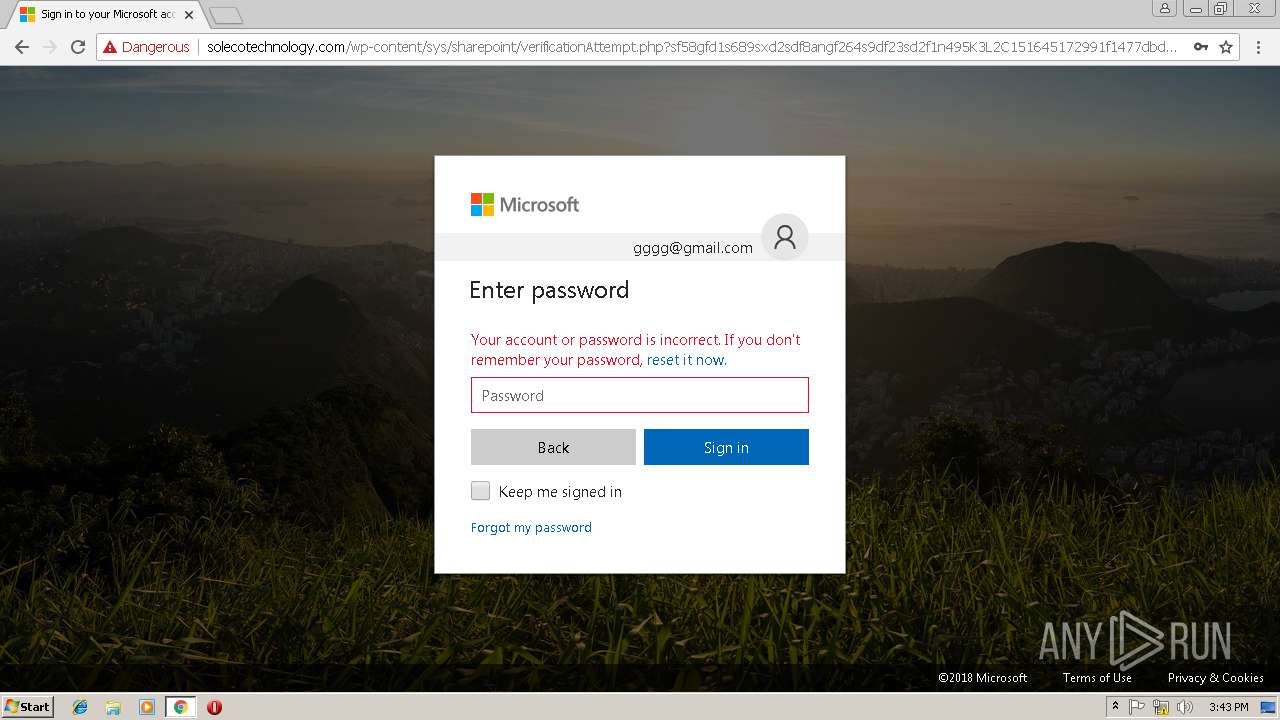
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/verificationAttempt.php?sf58gfd1s689sxd2sdf8angf264s9df23sd2f1n495K3L2C151645172991f1477dbd26917ef3822423f62e984a91f1477dbd26917ef3822423f62e984a91f1477dbd | US | html | 18.9 Kb | suspicious |
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/img/logo_strip.png | US | image | 7.36 Kb | suspicious |
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/img/logo.png | US | image | 3.25 Kb | suspicious |
3348 | chrome.exe | GET | 200 | 144.208.76.186:80 | http://solecotechnology.com/wp-content/sys/sharepoint/css/share-point.css | US | text | 15.1 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
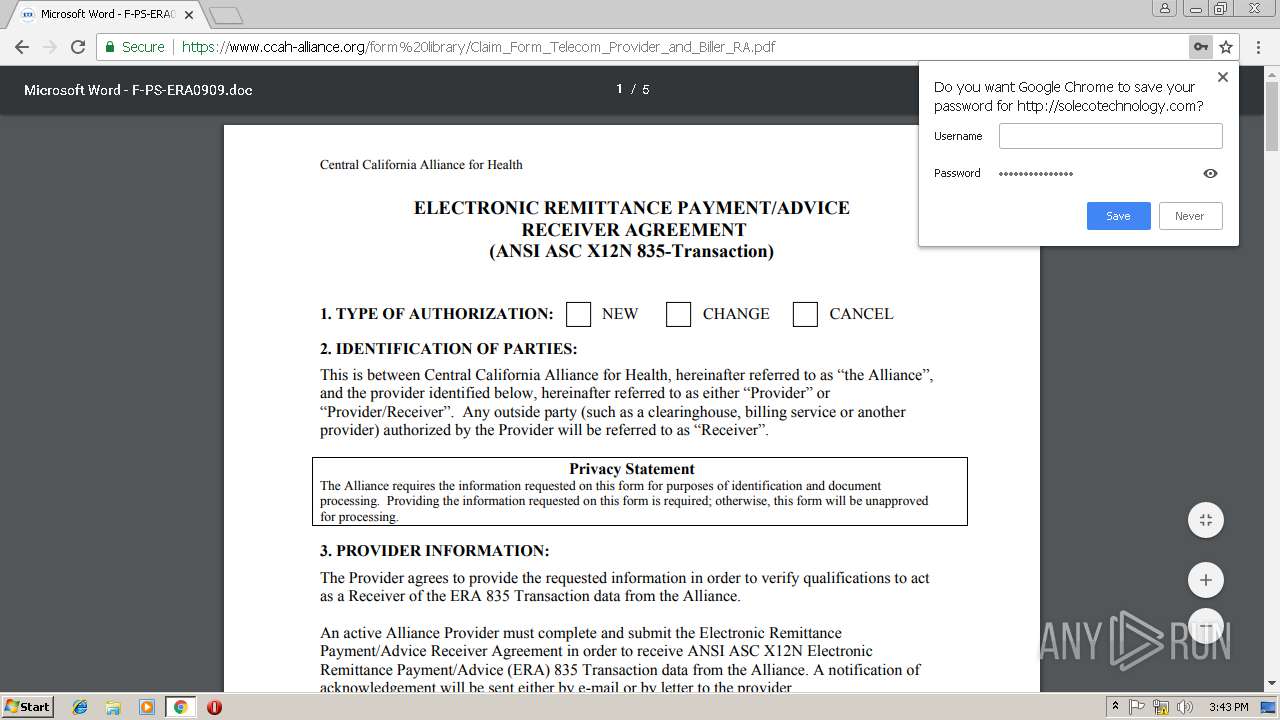
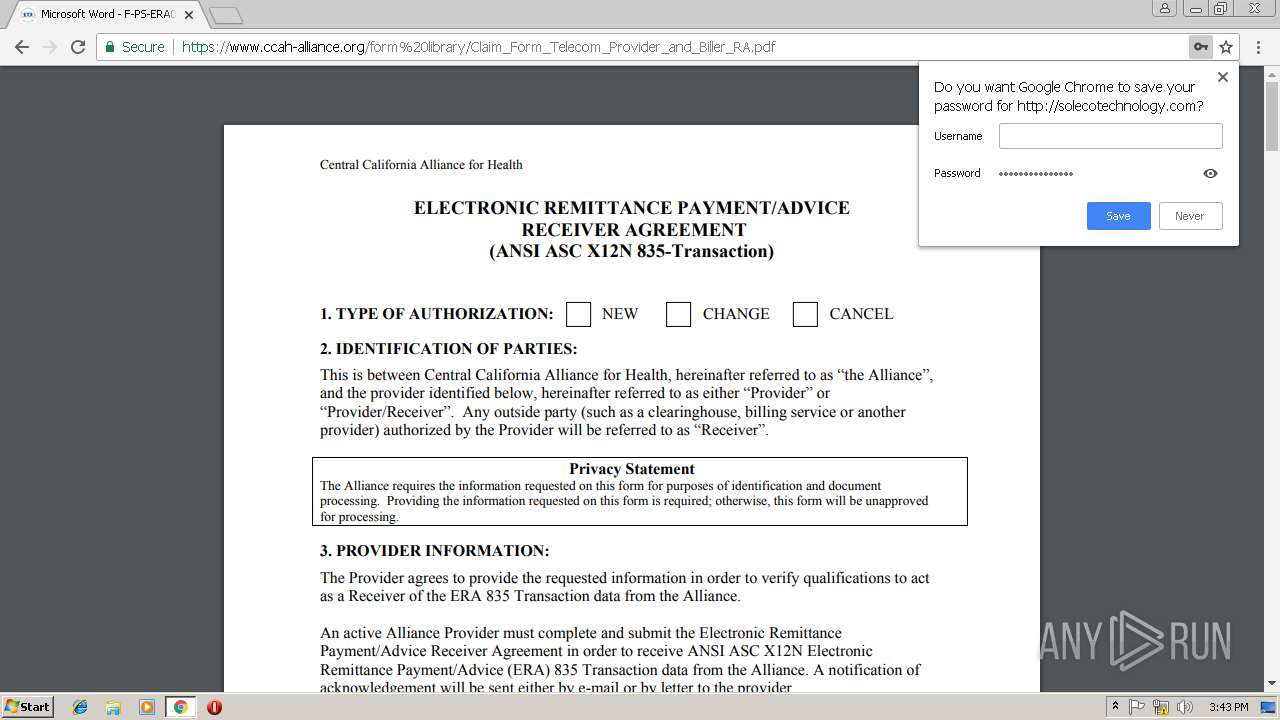
3124 | iexplore.exe | 208.83.105.12:443 | soundbitemedical.egnyte.com | Bloomip Inc. | US | unknown |
2952 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3348 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3348 | chrome.exe | 216.58.205.232:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
3348 | chrome.exe | 151.101.2.110:443 | js-agent.newrelic.com | Fastly | US | suspicious |
3348 | chrome.exe | 162.247.242.19:443 | bam.nr-data.net | New Relic | US | whitelisted |
3348 | chrome.exe | 35.186.235.23:443 | cdn.mxpnl.com | Google Inc. | US | whitelisted |
3348 | chrome.exe | 107.178.240.159:443 | api.mixpanel.com | Google Inc. | US | whitelisted |
3348 | chrome.exe | 144.208.76.186:80 | solecotechnology.com | InMotion Hosting, Inc. | US | suspicious |
3348 | chrome.exe | 208.83.105.12:443 | soundbitemedical.egnyte.com | Bloomip Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
soundbitemedical.egnyte.com |
| unknown |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
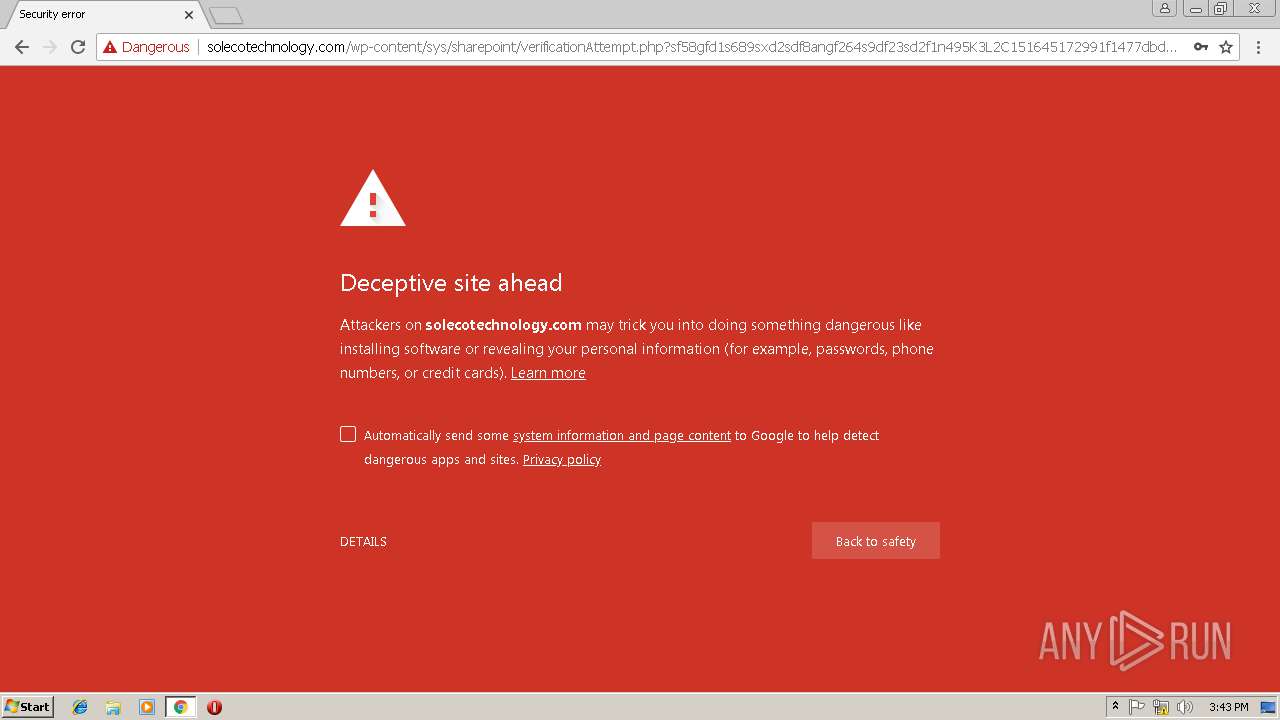
3348 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS Microsoft Live Phishing Landing |
3348 | chrome.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Microsoft Account Phishing Landing M1 2018-04-19 |
3348 | chrome.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Microsoft Account Phishing Landing 2018-08-07 |
3348 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS Microsoft Live Phishing Landing |
3348 | chrome.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Microsoft Account Phishing Landing M1 2018-04-19 |
3348 | chrome.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Microsoft Account Phishing Landing 2018-08-07 |
2 ETPRO signatures available at the full report