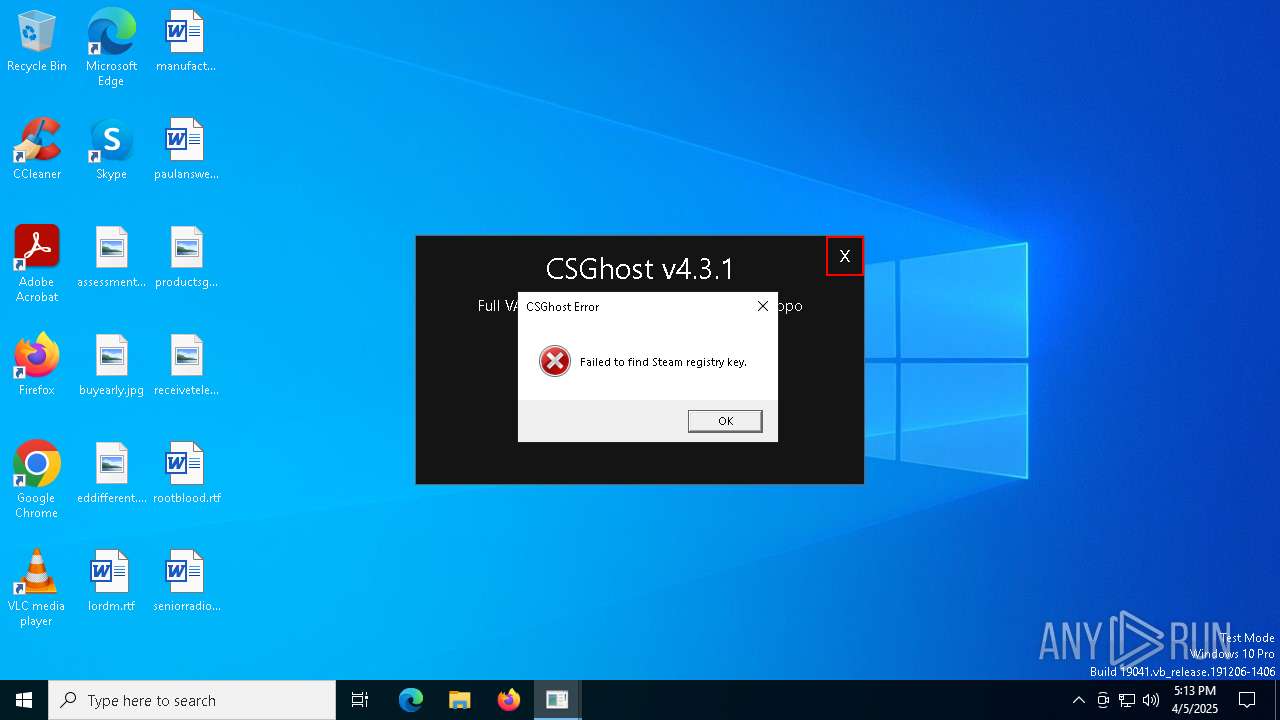
| File name: | CSGhost-v4.3.1_[unknowncheats.me]_.exe |
| Full analysis: | https://app.any.run/tasks/319ea2e1-3e3b-4f31-b22e-c24dd67c32aa |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 17:13:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 5B7C939E660AF3A678AF8C48D416F3FD |
| SHA1: | B751C3ED92F2B33693C63610A27F57616C59B6C6 |
| SHA256: | 4D512DEC8B02A8779F892ED6A07D6464625FD0EBCE4FF1A0C1CB356784DD2D9C |
| SSDEEP: | 3072:PYMEWromwPS5jVRhR6O0XnoCDj2W6EWNfynxjpY0DLIS3JTu:PFSPw6roCPAOLIIu |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 5680)
SUSPICIOUS
Application launched itself
- Skype.exe (PID: 456)
Uses REG/REGEDIT.EXE to modify registry
- Skype.exe (PID: 456)
Reads security settings of Internet Explorer
- Skype.exe (PID: 456)
Detected use of alternative data streams (AltDS)
- Skype.exe (PID: 456)
INFO
Creates files or folders in the user directory
- Skype.exe (PID: 456)
- Skype.exe (PID: 6468)
- Skype.exe (PID: 1912)
Checks supported languages
- Skype.exe (PID: 456)
- CSGhost-v4.3.1_[unknowncheats.me]_.exe (PID: 5972)
- Skype.exe (PID: 4452)
- Skype.exe (PID: 1912)
- Skype.exe (PID: 6740)
- Skype.exe (PID: 6468)
- Skype.exe (PID: 1628)
Manual execution by a user
- mspaint.exe (PID: 6644)
- mspaint.exe (PID: 6148)
- Skype.exe (PID: 456)
Reads the computer name
- CSGhost-v4.3.1_[unknowncheats.me]_.exe (PID: 5972)
- Skype.exe (PID: 456)
- Skype.exe (PID: 4452)
- Skype.exe (PID: 1912)
- Skype.exe (PID: 6468)
Reads CPU info
- Skype.exe (PID: 456)
Checks proxy server information
- Skype.exe (PID: 456)
Process checks computer location settings
- Skype.exe (PID: 456)
- Skype.exe (PID: 1628)
- Skype.exe (PID: 6468)
Create files in a temporary directory
- Skype.exe (PID: 456)
Reads the software policy settings
- Skype.exe (PID: 456)
- slui.exe (PID: 5864)
Reads the machine GUID from the registry
- Skype.exe (PID: 456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:12:01 08:23:32+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 49152 |
| InitializedDataSize: | 64000 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbd0c |
| OSVersion: | 6 |
| ImageVersion: | 4 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
157
Monitored processes
27
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe" | C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Version: 8.104.0.207 Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop" --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files (x86)\Microsoft\Skype for Desktop\resources\app.asar" --no-sandbox --no-zygote --enable-blink-features --disable-blink-features --autoplay-policy=no-user-gesture-required --disable-background-timer-throttling --ms-disable-indexeddb-transaction-timeout --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=4144 --field-trial-handle=2216,i,11399702278414096916,10664374911138591023,131072 --enable-features=WinUseBrowserSpellChecker,WinUseHybridSpellChecker,WinrtGeolocationImplementation --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Version: 8.104.0.207 Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop" --mojo-platform-channel-handle=2204 --field-trial-handle=2216,i,11399702278414096916,10664374911138591023,131072 --enable-features=WinUseBrowserSpellChecker,WinUseHybridSpellChecker,WinrtGeolocationImplementation --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Version: 8.104.0.207 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\reg.exe QUERY "HKLM\Software\Microsoft\Windows\CurrentVersion\App Paths\msedge.exe" /ve | C:\Windows\SysWOW64\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 922
Read events
6 844
Write events
58
Delete events
20
Modification events
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Ribbon |
| Operation: | write | Name: | QatItems |
Value: <siq:customUI xmlns:siq="http://schemas.microsoft.com/windows/2009/ribbon/qat"><siq:ribbon minimized="false"><siq:qat position="0"><siq:sharedControls><siq:control idQ="siq:20002" visible="false" argument="0"/><siq:control idQ="siq:20003" visible="false" argument="0"/><siq:control idQ="siq:20004" visible="true" argument="0"/><siq:control idQ="siq:20014" visible="false" argument="0"/><siq:control idQ="siq:20017" visible="false" argument="0"/><siq:control idQ="siq:20019" visible="false" argument="0"/><siq:control idQ="siq:31001" visible="true" argument="0"/><siq:control idQ="siq:31002" visible="true" argument="0"/></siq:sharedControls></siq:qat></siq:ribbon></siq:customUI> | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Recent File List |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Recent File List |
| Operation: | write | Name: | File1 |
Value: C:\Users\admin\Desktop\assessmentkids.png | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPWidth |
Value: 0 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPHeight |
Value: 0 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbXPos |
Value: 0 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbYPos |
Value: 0 | |||
| (PID) Process: | (6644) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbWidth |
Value: 0 | |||
Executable files
0
Suspicious files
40
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\48CLGFY3YRLEUYP54SS8.temp | binary | |
MD5:4A73869FADBCD20D92FCA46C804331C7 | SHA256:A45EC1B5CC37784380A9955FB2B3F9E5E80574A39A0FF9A21118BC032F56E18A | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\settings.dat | binary | |
MD5:9D0439A794AA96ABD6AFF504C86C7F31 | SHA256:5DBC3A5DAF431973E245D83AB51B128E9C4CC2F3ECD61C45C88DB161ACC25B7B | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b916037c1e115fe0.customDestinations-ms | binary | |
MD5:4A73869FADBCD20D92FCA46C804331C7 | SHA256:A45EC1B5CC37784380A9955FB2B3F9E5E80574A39A0FF9A21118BC032F56E18A | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Partitions\91bff33a-fcbd-4d5b-af85-2ca334efbf50\Local Storage\leveldb\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Partitions\91bff33a-fcbd-4d5b-af85-2ca334efbf50\Code Cache\wasm\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\IndexedDB\file__0.indexeddb.leveldb\LOG.old | text | |
MD5:D9CF6AAE805A20C96EF6414D030D6CE8 | SHA256:6AFE86308EA331969317D933883AAB0D08EF96B7F14F54E45C0145D4D757DCD5 | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Partitions\91bff33a-fcbd-4d5b-af85-2ca334efbf50\Code Cache\wasm\index-dir\temp-index | binary | |
MD5:562E6160881DBC0CFCA2E04A055B1E57 | SHA256:DAABAD0CC000C9BE314329FE971F7C70A08107A826381701DECD2EFA4406EADE | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Partitions\91bff33a-fcbd-4d5b-af85-2ca334efbf50\Code Cache\wasm\index-dir\the-real-index | binary | |
MD5:562E6160881DBC0CFCA2E04A055B1E57 | SHA256:DAABAD0CC000C9BE314329FE971F7C70A08107A826381701DECD2EFA4406EADE | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Partitions\91bff33a-fcbd-4d5b-af85-2ca334efbf50\Code Cache\js\index-dir\temp-index | binary | |
MD5:1D4AC718B40F57F5950BD1C231DDB945 | SHA256:EE88059E2087F556233C63283E2E702EF2C53712DC3AE52F3EEA36DABAF5DD05 | |||
| 456 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\IndexedDB\file__0.indexeddb.blob\1\00\2 | binary | |
MD5:93FC9375C8CA27F4135D95818282D6C6 | SHA256:6E8B23EA10EAD4FB08B554856DFA520EF685E67B94879AB2270FC89CAC73EAB1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
33
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4696 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4696 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4696 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4696 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |