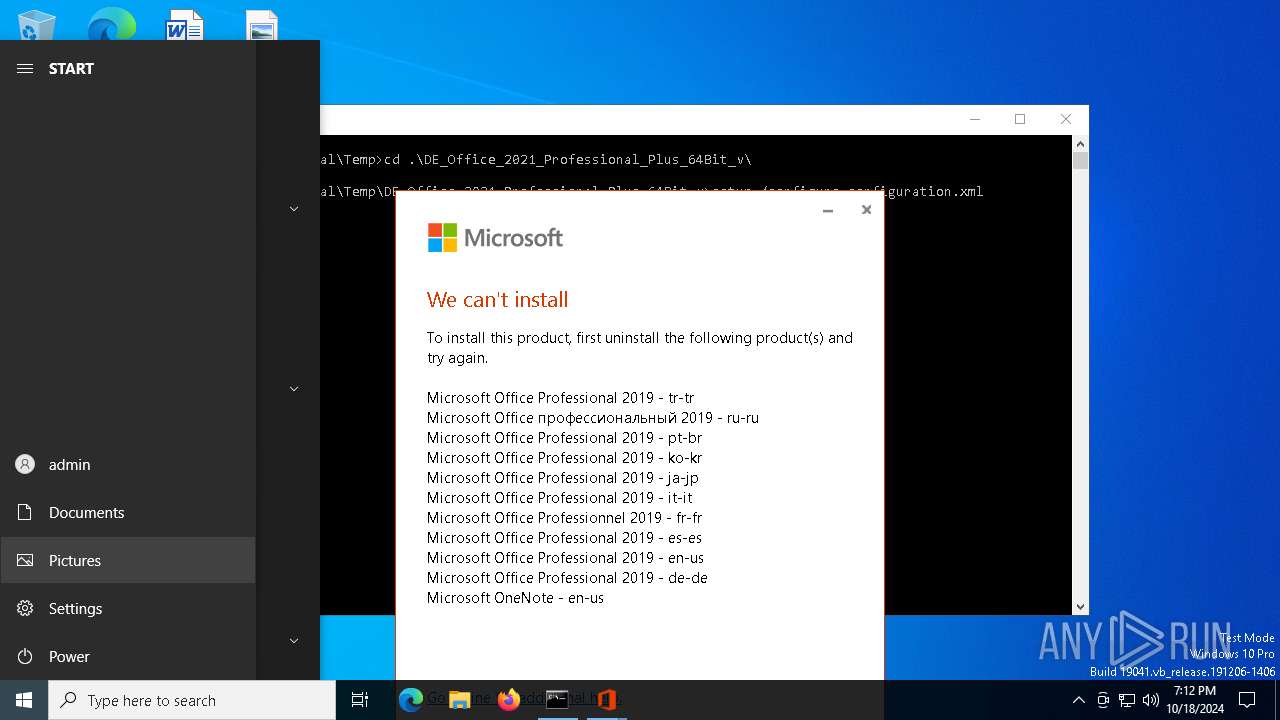
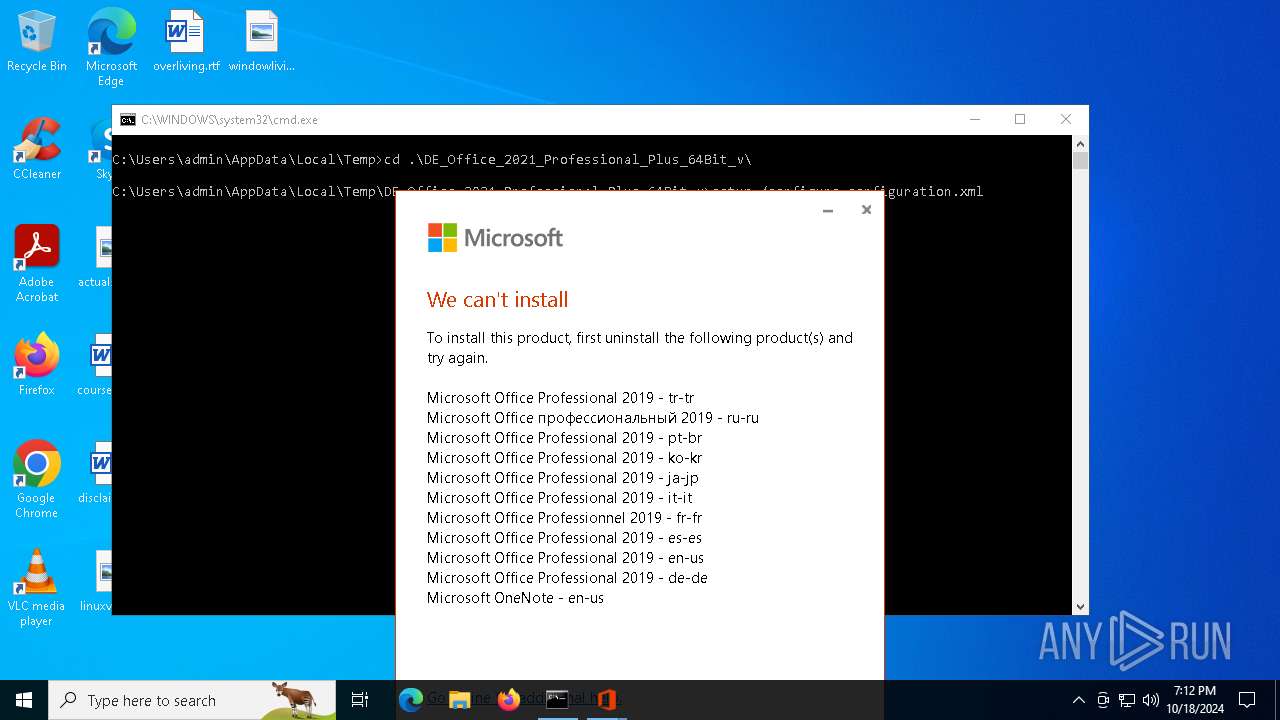
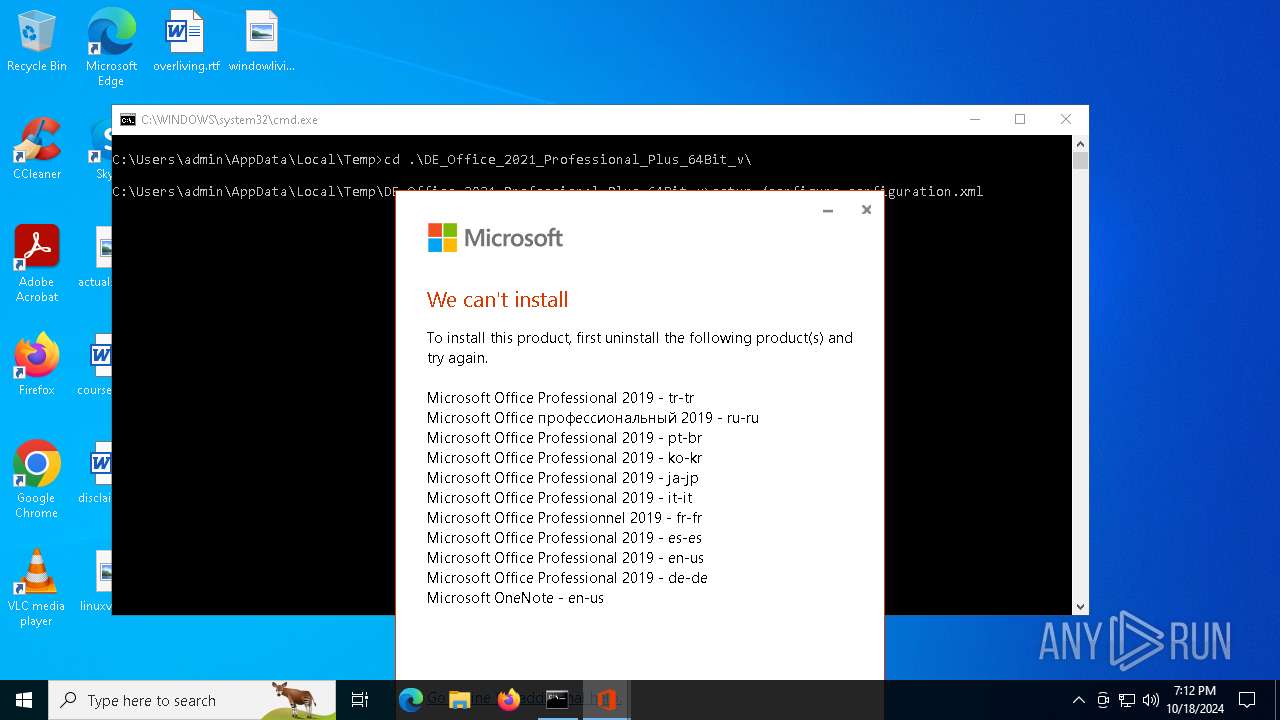
| File name: | DE_Office_2021_Professional_Plus_64Bit_v.exe |
| Full analysis: | https://app.any.run/tasks/5ad89982-1d2f-4062-8882-e4e3d724b838 |
| Verdict: | Malicious activity |
| Analysis date: | October 18, 2024, 19:12:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B93B58C3DE7050CBCA7714B846A605F7 |
| SHA1: | 6C65B97A39BD17C0E1A898EA9F6816D7EA4D2ECA |
| SHA256: | 4D4E94C0BE77CAF3755473B0CA5DBAA280C9DDC7330566B1539CD830664043CC |
| SSDEEP: | 98304:SFrKdIQsO8d5Q3AnI0g5h0Dh1Qc2oU66ooHf/Y+7aqmZN59GIg2hjYybZStNehDO:SQQ5yiNI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Reads Microsoft Outlook installation path
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Reads Internet Explorer settings
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
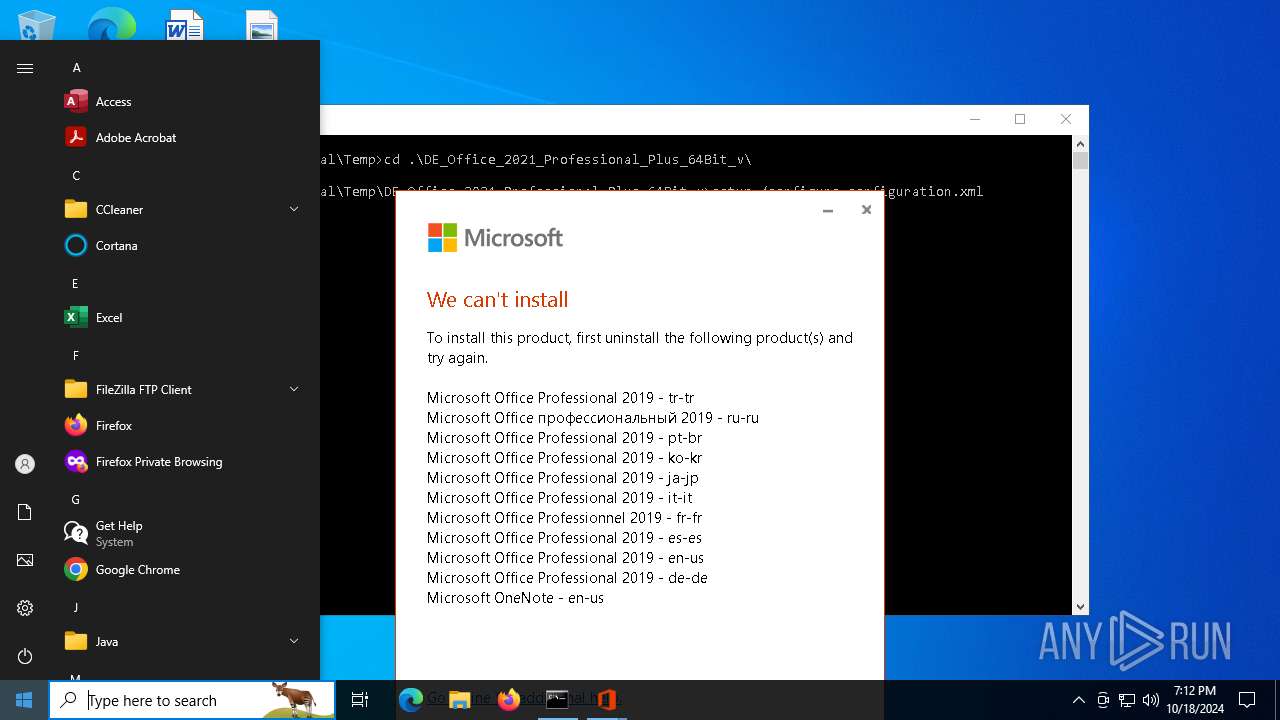
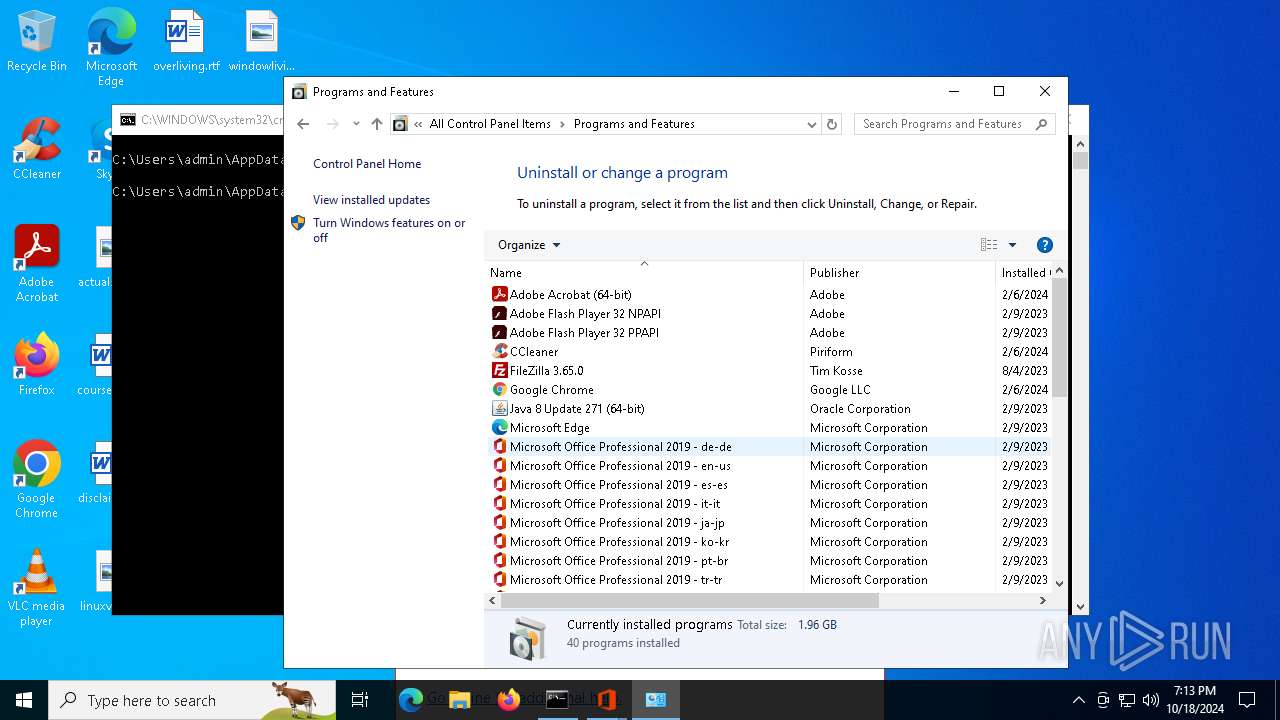
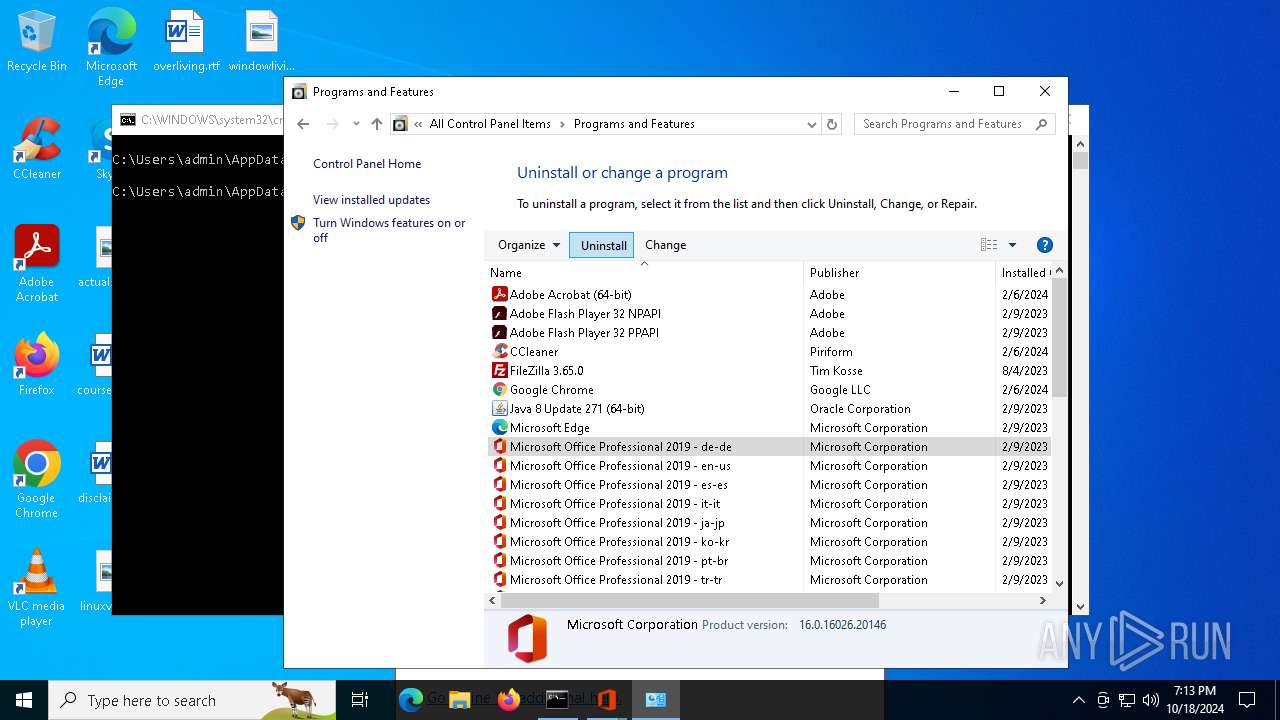
Process drops legitimate windows executable
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Executable content was dropped or overwritten
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Executing commands from a ".bat" file
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Starts CMD.EXE for commands execution
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
The executable file from the user directory is run by the CMD process
- setup.exe (PID: 3852)
Starts a Microsoft application from unusual location
- setup.exe (PID: 3852)
- setup.exe (PID: 5168)
Application launched itself
- setup.exe (PID: 3852)
The process bypasses the loading of PowerShell profile settings
- setup.exe (PID: 5168)
Starts POWERSHELL.EXE for commands execution
- setup.exe (PID: 5168)
INFO
Reads the computer name
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Checks supported languages
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Checks proxy server information
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Create files in a temporary directory
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
The process uses the downloaded file
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Process checks computer location settings
- DE_Office_2021_Professional_Plus_64Bit_v.exe (PID: 6436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201216 |
| InitializedDataSize: | 257024 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ec40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
190
Monitored processes
16
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1884 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile "$package = Get-AppxPackage Microsoft.Office.Desktop -allUsers; if (!$package) { $Error.Add(\"Package is not installed\")}; if ($error.Count -eq 0) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '1' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '0' -Encoding ascii; Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch' -InputObject $error -Encoding ascii;} " | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
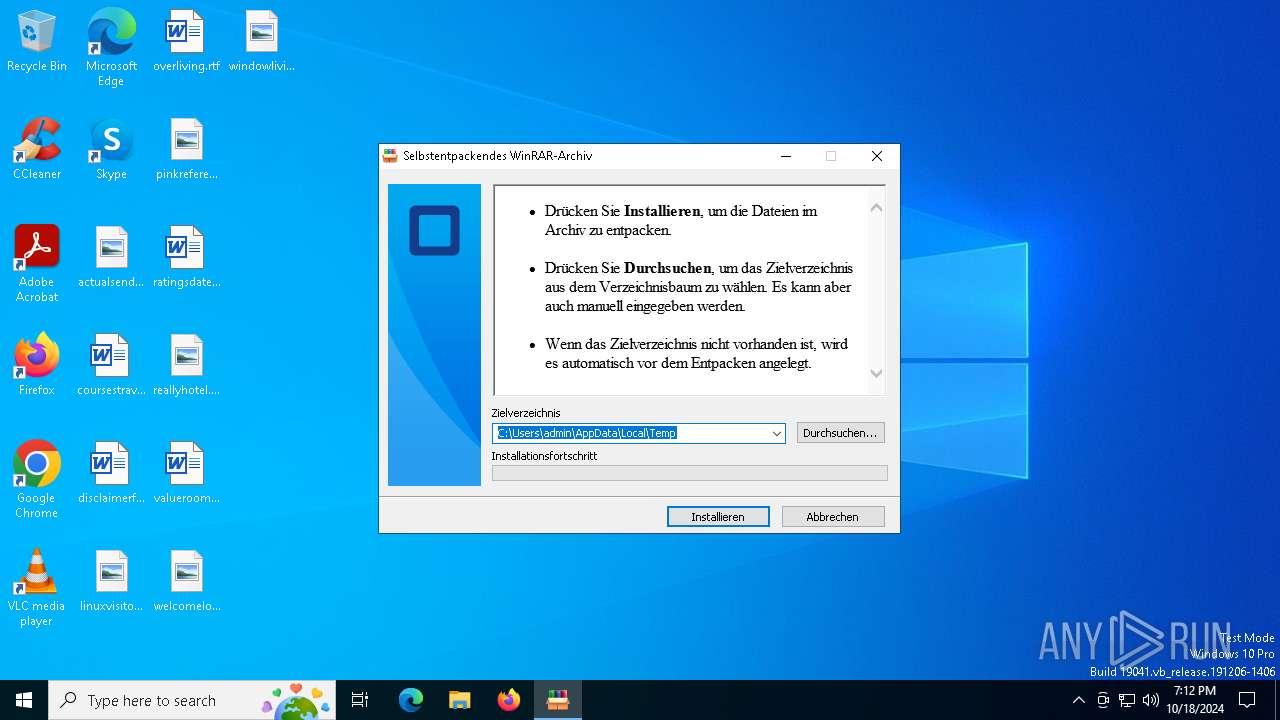
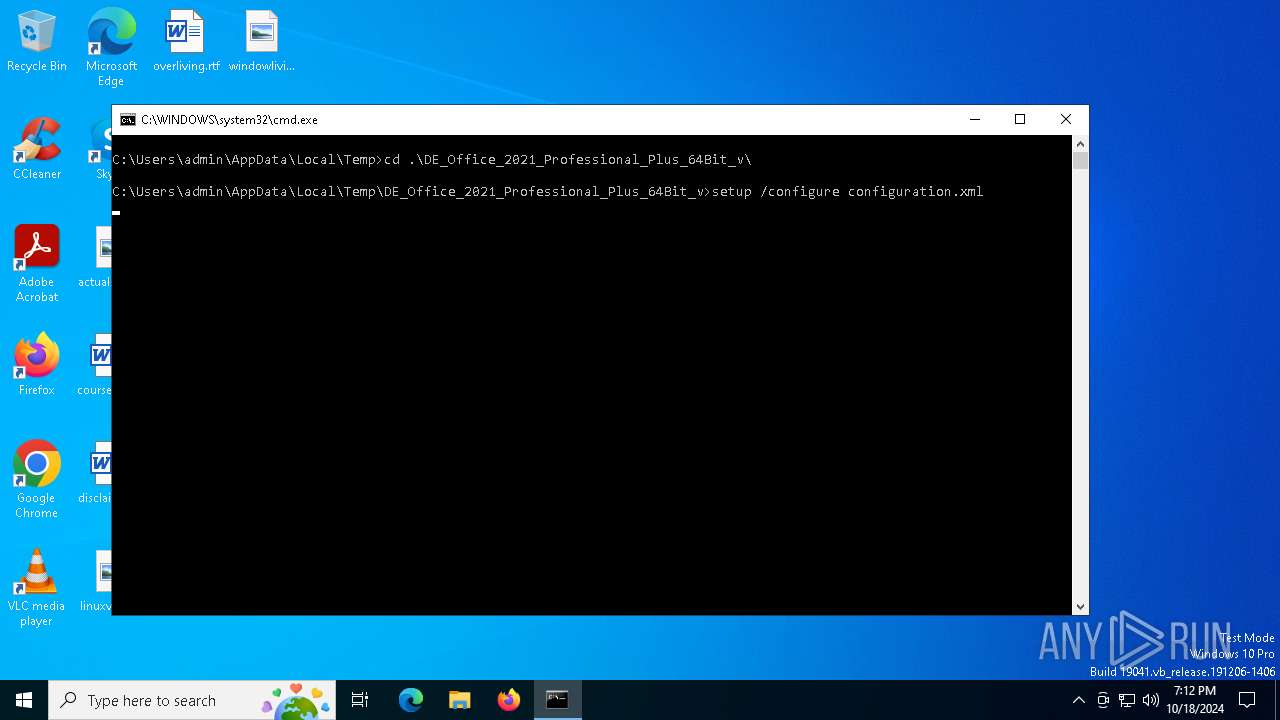
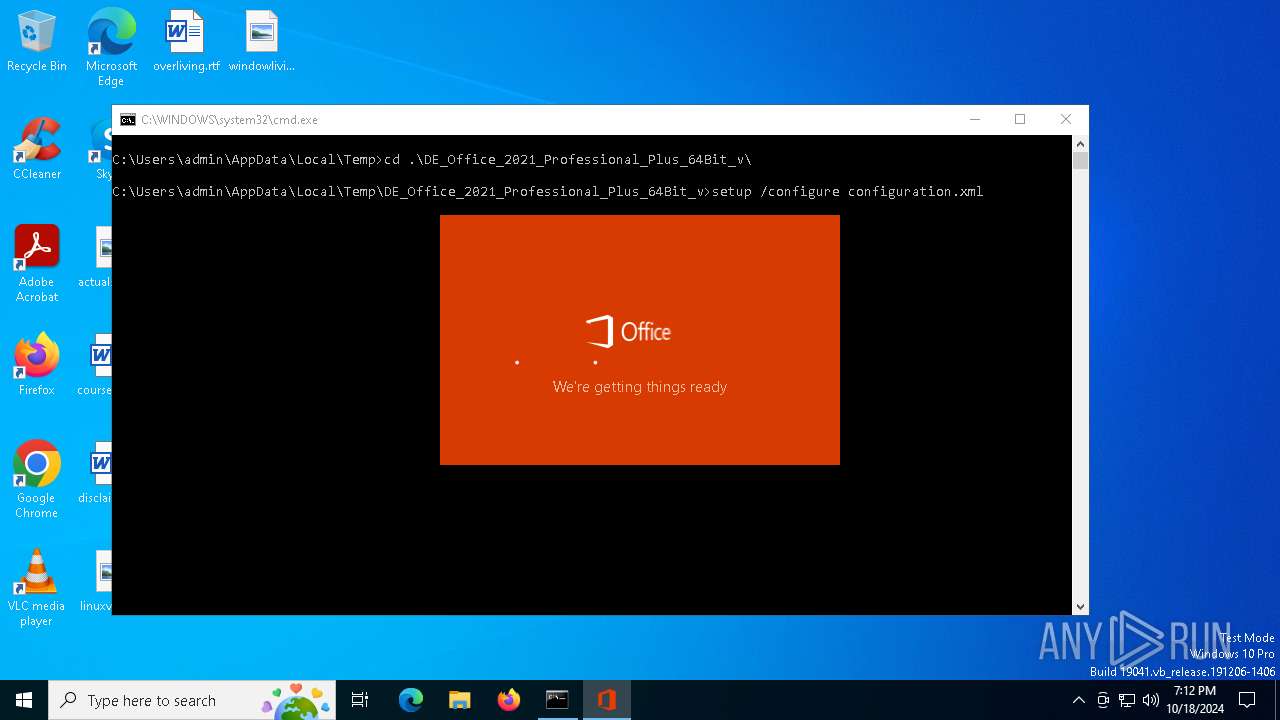
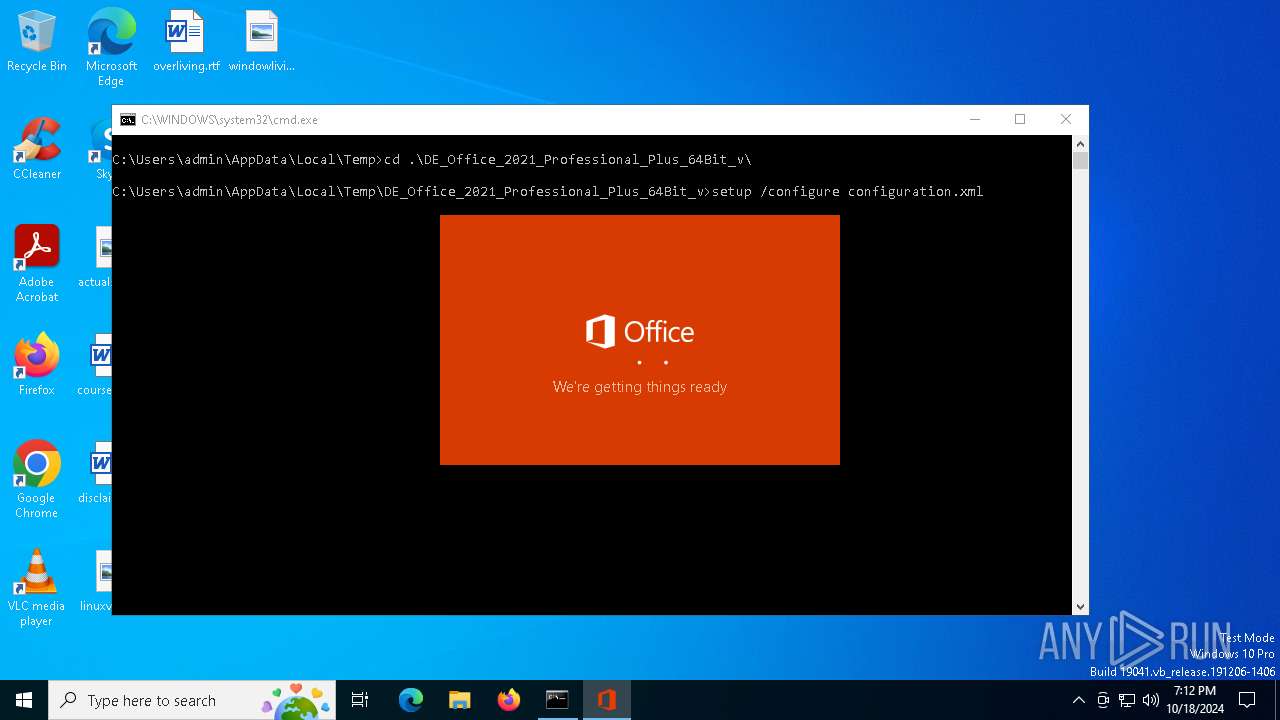
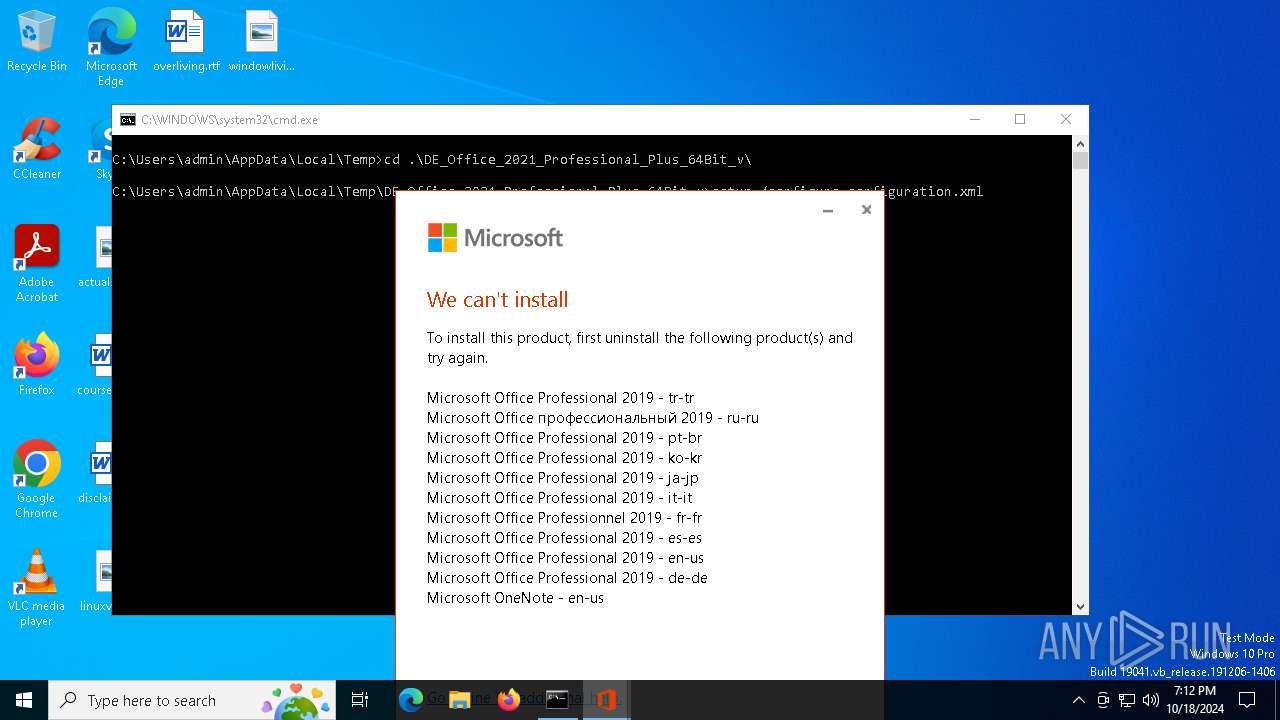
| 3852 | setup /configure configuration.xml | C:\Users\admin\AppData\Local\Temp\DE_Office_2021_Professional_Plus_64Bit_v\setup.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Version: 16.0.14326.20384 Modules
| |||||||||||||||
| 3960 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile "$package = Get-AppxPackage Microsoft.Office.Desktop -allUsers; if (!$package) { $Error.Add(\"Package is not installed\")}; if ($error.Count -eq 0) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '1' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '0' -Encoding ascii; Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch' -InputObject $error -Encoding ascii;} " | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5168 | "C:\Users\admin\AppData\Local\Temp\DE_Office_2021_Professional_Plus_64Bit_v\setup.exe" ELEVATED sid=S-1-5-21-1693682860-607145093-2874071422-1001 /configure configuration.xml | C:\Users\admin\AppData\Local\Temp\DE_Office_2021_Professional_Plus_64Bit_v\setup.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Version: 16.0.14326.20384 Modules
| |||||||||||||||
| 5276 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6408 | InspectorOfficeGadget.exe isinstalled --displayname "Microsoft.Office.Desktop" --logfile "C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch" | C:\Program Files\Common Files\microsoft shared\ClickToRun\InspectorOfficeGadget.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: InspectorOfficeGadget Exit code: 4294967293 Version: 16.0.15726.20000 Modules
| |||||||||||||||
| 6416 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 614
Read events
26 397
Write events
109
Delete events
108
Modification events
| (PID) Process: | (6436) DE_Office_2021_Professional_Plus_64Bit_v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6436) DE_Office_2021_Professional_Plus_64Bit_v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6436) DE_Office_2021_Professional_Plus_64Bit_v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6436) DE_Office_2021_Professional_Plus_64Bit_v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (6436) DE_Office_2021_Professional_Plus_64Bit_v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (3852) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3852) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (3852) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (3852) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (3852) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
Executable files
1
Suspicious files
1
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6436 | DE_Office_2021_Professional_Plus_64Bit_v.exe | C:\Users\admin\AppData\Local\Temp\DE_Office_2021_Professional_Plus_64Bit_v\setup.exe | executable | |
MD5:C43FA7C24D8F0DEC0C1E55DBFF369FD6 | SHA256:AAE9C94BC546D208868BC04A823AD6A716B1B4D3AD7010263B0690082E3B8DA8 | |||
| 6436 | DE_Office_2021_Professional_Plus_64Bit_v.exe | C:\Users\admin\AppData\Local\Temp\DE_Office_2021_Professional_Plus_64Bit_v\Click To Run.bat | text | |
MD5:AD3ED1D41F9B51F7F203D56597C05958 | SHA256:413B8E555D8F42C56D22D6843708F7BFCB0BBEDB4F833BF3C89880665925BD14 | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ox44aqg4.4q0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch | text | |
MD5:BD3457E50947D4280734E74B51B5B68D | SHA256:23D647979BC5DC186DE5BA3E00A222A912AB8E4782EB6407EFA70E29E95979F5 | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sjchjjmq.vca.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch | text | |
MD5:21438EF4B9AD4FC266B6129A2F60DE29 | SHA256:13BF7B3039C63BF5A50491FA3CFD8EB4E699D1BA1436315AEF9CBE5711530354 | |||
| 1884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t0bkxpph.pfc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6408 | InspectorOfficeGadget.exe | C:\Users\admin\AppData\Local\Temp\office.validateerror.scratch | text | |
MD5:A57CDED3959AB84E99F1A878EA0B1965 | SHA256:077A892BE8D50992E22DD50ADEADF0F1341230C7F41E720A188C72BF0CB5D12D | |||
| 6436 | DE_Office_2021_Professional_Plus_64Bit_v.exe | C:\Users\admin\AppData\Local\Temp\start.bat | text | |
MD5:523AE06179B3B0FE540991FA7CA42EBB | SHA256:B9E5C13F03D90D9A918C0C13BCAD26CF5C25C732807B9023574129AB78051395 | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:16B18E1C3B7837E5A737D4E33B28B045 | SHA256:7D1D680742B9C4A6CE7BFBCBB3165F2A1FF60A0DBEF319CBD8118DF53C4F65F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
89
DNS requests
65
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6260 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6260 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5596 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6908 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3852 | setup.exe | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6944 | svchost.exe | 23.48.23.145:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |