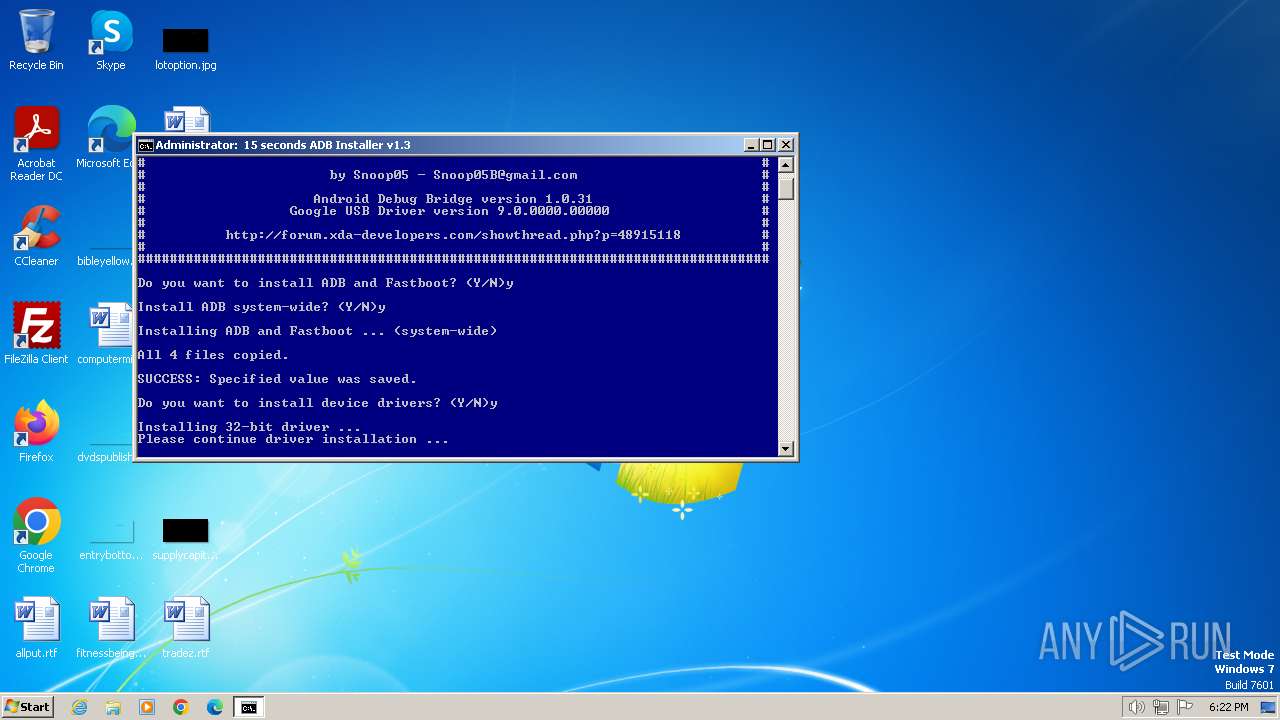
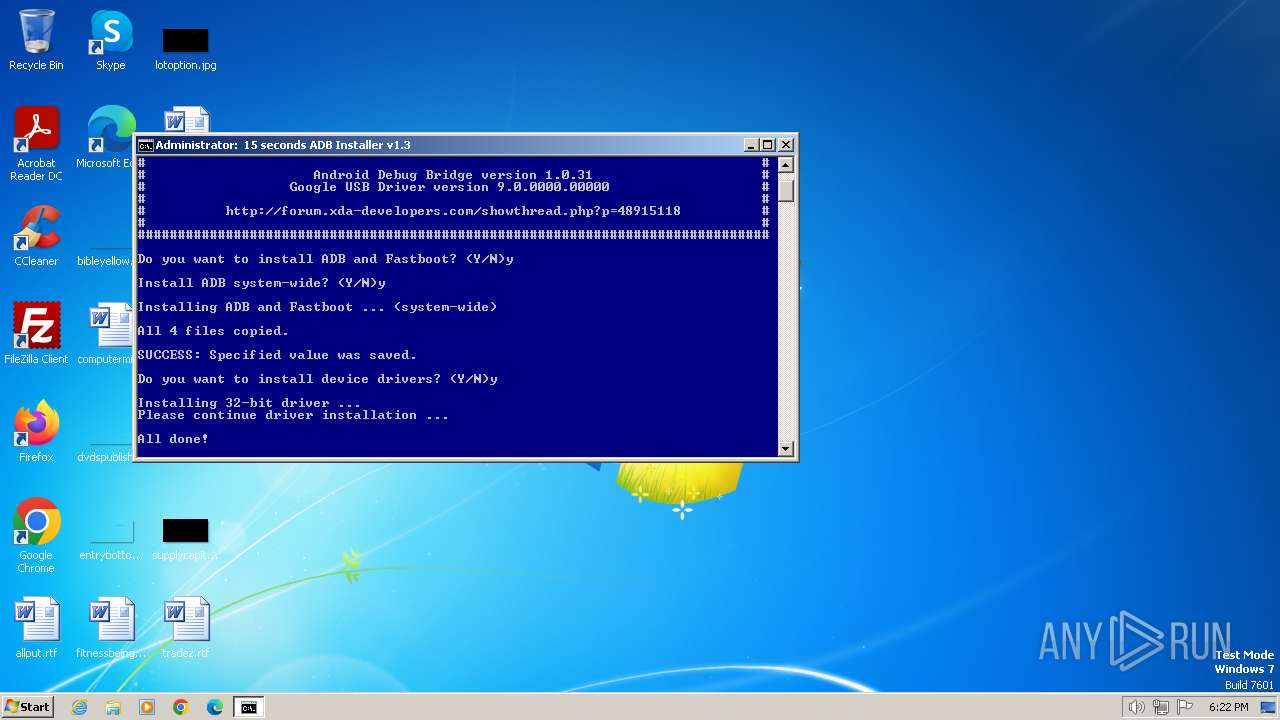
| File name: | adb-setup-1.3.exe |
| Full analysis: | https://app.any.run/tasks/e9c76109-a87f-4889-b1f2-0338ac2ee695 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 18:22:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | A7027B44B7036BB12935AA0BDE764CD2 |
| SHA1: | 40F4C73EA92137361A11511A4C0A52AC8D99D345 |
| SHA256: | 4D479E6615ABAA7B443F5638AE7A2B2D3F92D53BCA9B7BC3B7FC452ABD5BD409 |
| SSDEEP: | 196608:NQhcmavTsC9iOAMYX9mecGxxcSLPZ7ztCawWooDRiuDALqHRBP8RatWRw:+hczTsLMWkecz2Zf6KQuxx11tEw |
MALICIOUS
Drops the executable file immediately after the start
- adb-setup-1.3.exe (PID: 3668)
- adb-setup-1.3.exe (PID: 2844)
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Creates a writable file in the system directory
- drvinst.exe (PID: 3488)
SUSPICIOUS
Reads security settings of Internet Explorer
- adb-setup-1.3.exe (PID: 3668)
- adb-setup-1.3.exe (PID: 2752)
Application launched itself
- adb-setup-1.3.exe (PID: 2844)
- adb-setup-1.3.exe (PID: 3668)
Reads the Internet Settings
- adb-setup-1.3.exe (PID: 3668)
- adb-setup-1.3.exe (PID: 2752)
Process drops legitimate windows executable
- adb-setup-1.3.exe (PID: 2844)
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Starts CMD.EXE for commands execution
- adb-setup-1.3.exe (PID: 2752)
Executable content was dropped or overwritten
- adb-setup-1.3.exe (PID: 2844)
- xcopy.exe (PID: 4060)
- xcopy.exe (PID: 1692)
- xcopy.exe (PID: 2120)
- xcopy.exe (PID: 3092)
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Executing commands from a ".bat" file
- adb-setup-1.3.exe (PID: 2752)
The executable file from the user directory is run by the CMD process
- DPInst_x86.exe (PID: 2420)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1876)
Starts a Microsoft application from unusual location
- DPInst_x86.exe (PID: 2420)
Creates files in the driver directory
- drvinst.exe (PID: 3488)
Checks Windows Trust Settings
- drvinst.exe (PID: 3488)
Reads settings of System Certificates
- rundll32.exe (PID: 1824)
Executes as Windows Service
- VSSVC.exe (PID: 796)
Creates a software uninstall entry
- DPInst_x86.exe (PID: 2420)
INFO
Checks supported languages
- adb-setup-1.3.exe (PID: 3668)
- adb-setup-1.3.exe (PID: 2752)
- adb-setup-1.3.exe (PID: 2844)
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Reads the computer name
- adb-setup-1.3.exe (PID: 3668)
- adb-setup-1.3.exe (PID: 2752)
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Create files in a temporary directory
- adb-setup-1.3.exe (PID: 2844)
- DPInst_x86.exe (PID: 2420)
Drops the executable file immediately after the start
- xcopy.exe (PID: 2120)
- xcopy.exe (PID: 1692)
- xcopy.exe (PID: 3092)
- xcopy.exe (PID: 4060)
Reads the machine GUID from the registry
- DPInst_x86.exe (PID: 2420)
- drvinst.exe (PID: 3488)
Reads the software policy settings
- rundll32.exe (PID: 1824)
- drvinst.exe (PID: 3488)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:31 00:38:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 57344 |
| InitializedDataSize: | 307200 |
| UninitializedDataSize: | 389120 |
| EntryPoint: | 0x6ce00 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| InternalName: | - |
| ProductName: | 15 seconds ADB Installer |
| OriginalFileName: | - |
| FileVersion: | 1.3 |
| ProductVersion: | 1.3 |
| Comments: | - |
| PrivateBuild: | - |
| SpecialBuild: | - |
Total processes
59
Monitored processes
20
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | PING localhost -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | PING localhost -n 3 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | FC /b adb\adb.exe C:\adb\adb.exe | C:\Windows\System32\fc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS 5 File Compare Utility Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | xcopy adb\AdbWinUsbApi.dll C:\adb\ /y /q | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{4e1f11f9-ad74-51ac-2ded-5c6b1033e70d} Global\{2752b98d-7311-3df3-fdde-7b356e9b5366} C:\Windows\System32\DriverStore\Temp\{289cb3d3-c3e5-5f52-74ad-ac514b846310}\android_winusb.inf C:\Windows\System32\DriverStore\Temp\{289cb3d3-c3e5-5f52-74ad-ac514b846310}\androidwinusb86.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\install.bat" " | C:\Windows\System32\cmd.exe | — | adb-setup-1.3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2120 | xcopy adb\AdbWinApi.dll C:\adb\ /y /q | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | driver\DPInst_x86 /f | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\DPInst_x86.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 2752 | "C:\Users\admin\AppData\Local\Temp\adb-setup-1.3.exe" -sfxwaitall:0 "install.bat" | C:\Users\admin\AppData\Local\Temp\adb-setup-1.3.exe | — | adb-setup-1.3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.3 Modules
| |||||||||||||||
Total events
15 869
Read events
15 654
Write events
212
Delete events
3
Modification events
| (PID) Process: | (3668) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3668) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3668) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3668) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2752) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2752) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2752) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2752) adb-setup-1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3960) setx.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Environment |
| Operation: | write | Name: | PATH |
Value: C:\Program Files\Common Files\Oracle\Java\javapath;C:\ProgramData\Oracle\Java\javapath;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Program Files\PowerShell\7\;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\adb | |||
| (PID) Process: | (2420) DPInst_x86.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
26
Suspicious files
10
Text files
6
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\android_winusb.inf | binary | |
MD5:91EEEFEBF7F96222E8084D8483F0CB85 | SHA256:576E8AF6052501591AB726F64D1E77AD3B6BA03E9FD9A70542A46F16992BD773 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\i386\NOTICE.txt | text | |
MD5:EA7F2158B930BAF2C0FE799566489716 | SHA256:A19B767B9DDDA7306C78232E4A223D0BA966471B74DCE3C0C995307CAB5BF7B7 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\amd64\NOTICE.txt | text | |
MD5:EA7F2158B930BAF2C0FE799566489716 | SHA256:A19B767B9DDDA7306C78232E4A223D0BA966471B74DCE3C0C995307CAB5BF7B7 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\adb\fastboot.exe | executable | |
MD5:2782D10E7D3370CFEFBADAE0E8EAAA35 | SHA256:1D6142422F9A0D6D4302D826D5490B2C07FF113D9EDCFEA0EADCBACDCCB1B325 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\adb\AdbWinUsbApi.dll | executable | |
MD5:5F23F2F936BDFAC90BB0A4970AD365CF | SHA256:041C6859BB4FC78D3A903DD901298CD1ECFB75B6BE0646B74954CD722280A407 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\androidwinusba64.cat | binary | |
MD5:1DB49B8110F671821FD91E1DA29D36BF | SHA256:160C6809340675DD44AB36D32725418AF0FE5B8FD0893BBDA3660B1A92D779D5 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\adb\AdbWinApi.dll | executable | |
MD5:47A6EE3F186B2C2F5057028906BAC0C6 | SHA256:14A51482AA003DB79A400F4B15C158397FE6D57EE6606B3D633FA431A7BFDF4B | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\i386\WdfCoInstaller01009.dll | executable | |
MD5:A9970042BE512C7981B36E689C5F3F9F | SHA256:7A6BF1F950684381205C717A51AF2D9C81B203CB1F3DB0006A4602E2DF675C77 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\driver\DPInst_x64.exe | executable | |
MD5:4192A5B905374E423EC1E545599AA86E | SHA256:567F40A09F1D9E72396296AD194FA7CF48B72361D6E259D6B99DA774C2CD8981 | |||
| 2844 | adb-setup-1.3.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\adb\adb.exe | executable | |
MD5:81D188A849C8768E8F3694EB1C0E6086 | SHA256:0405EEAF5D7B54AAAA3939A87D0A64B21EDEACE5DBEADE6D8CFD6B5FAF9F7115 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |