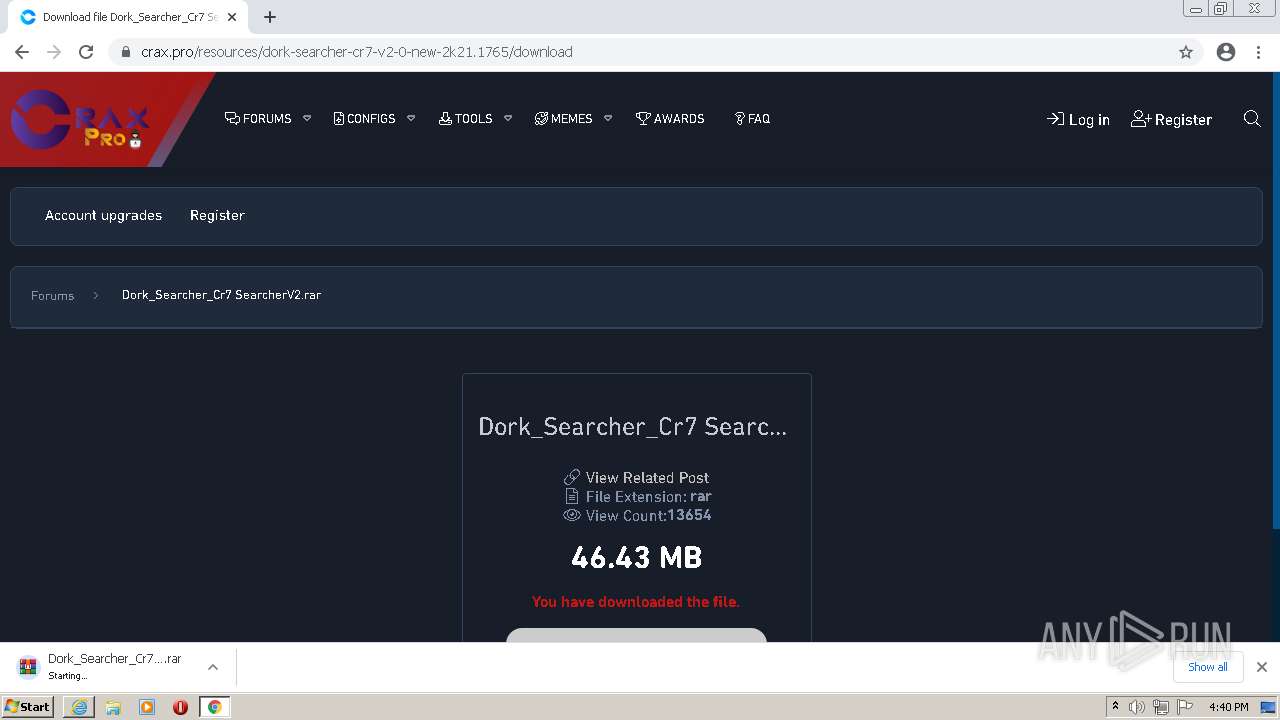
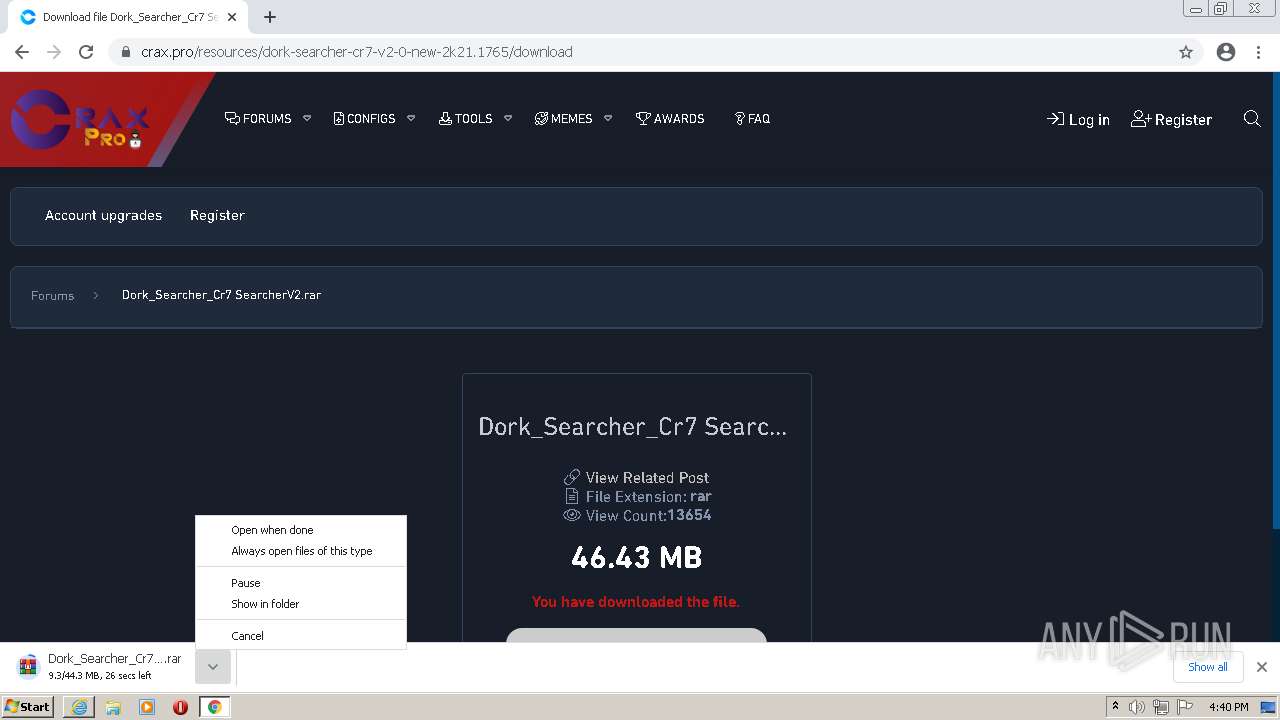
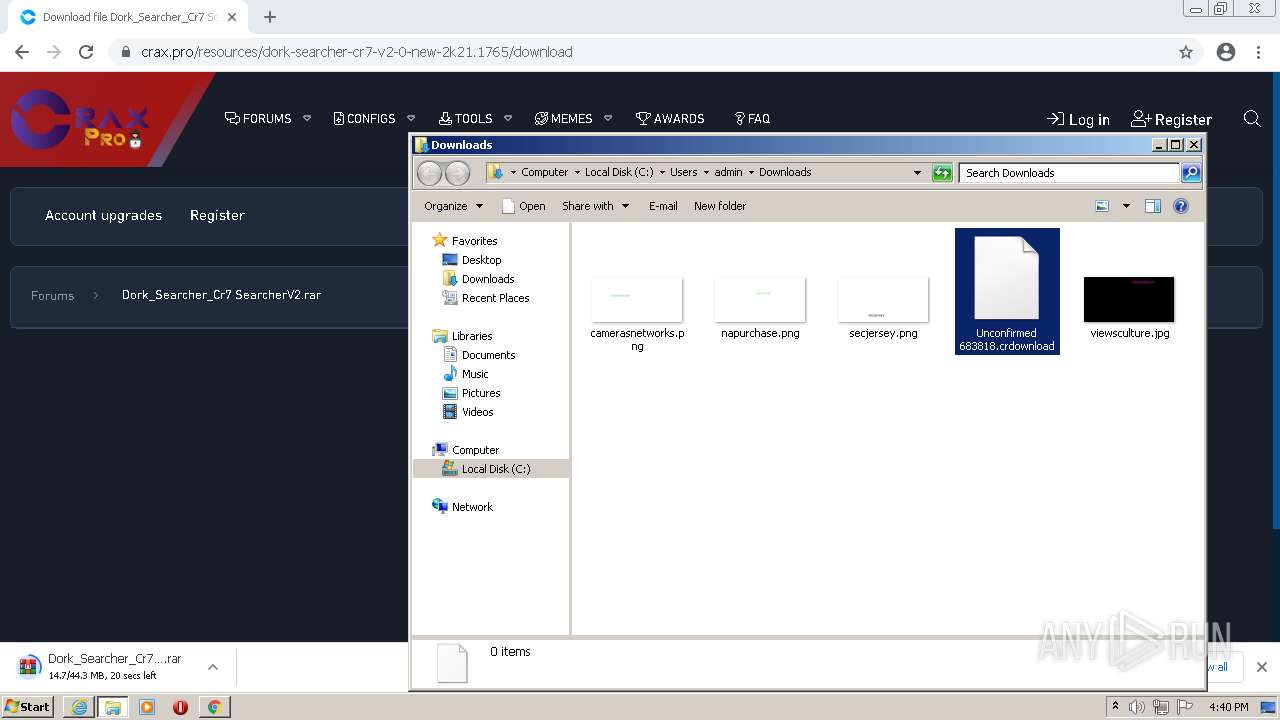
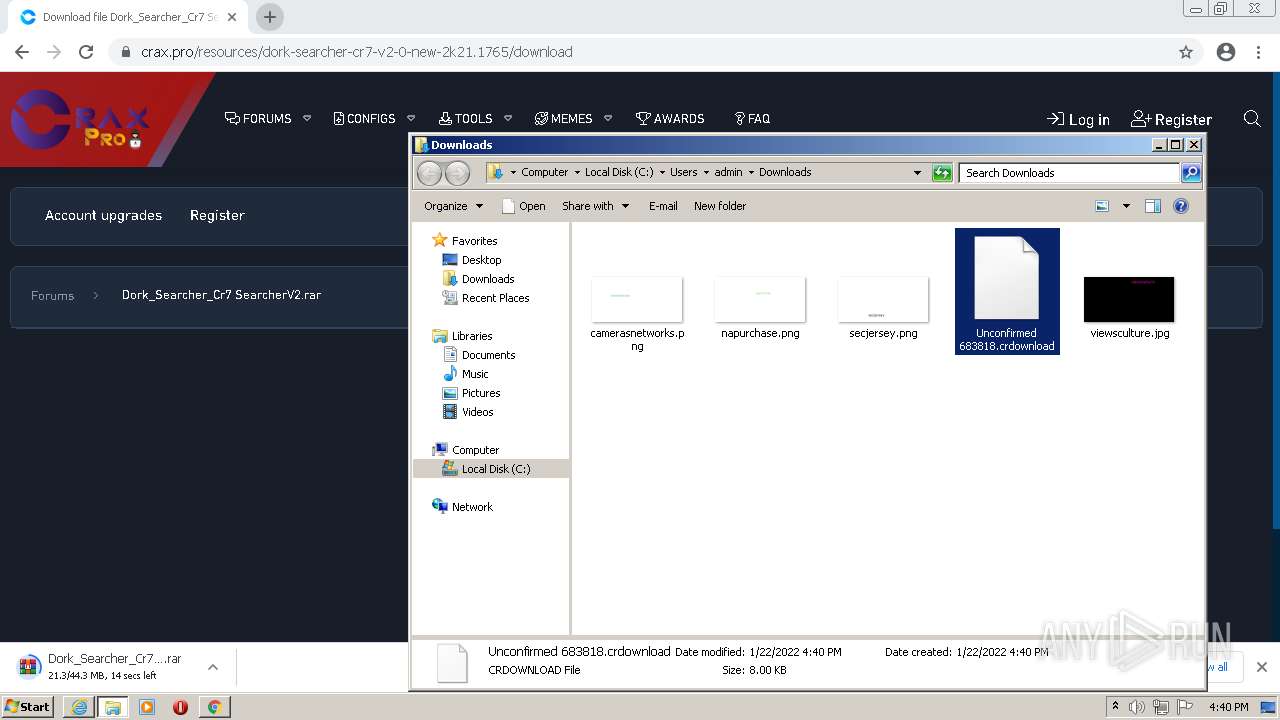
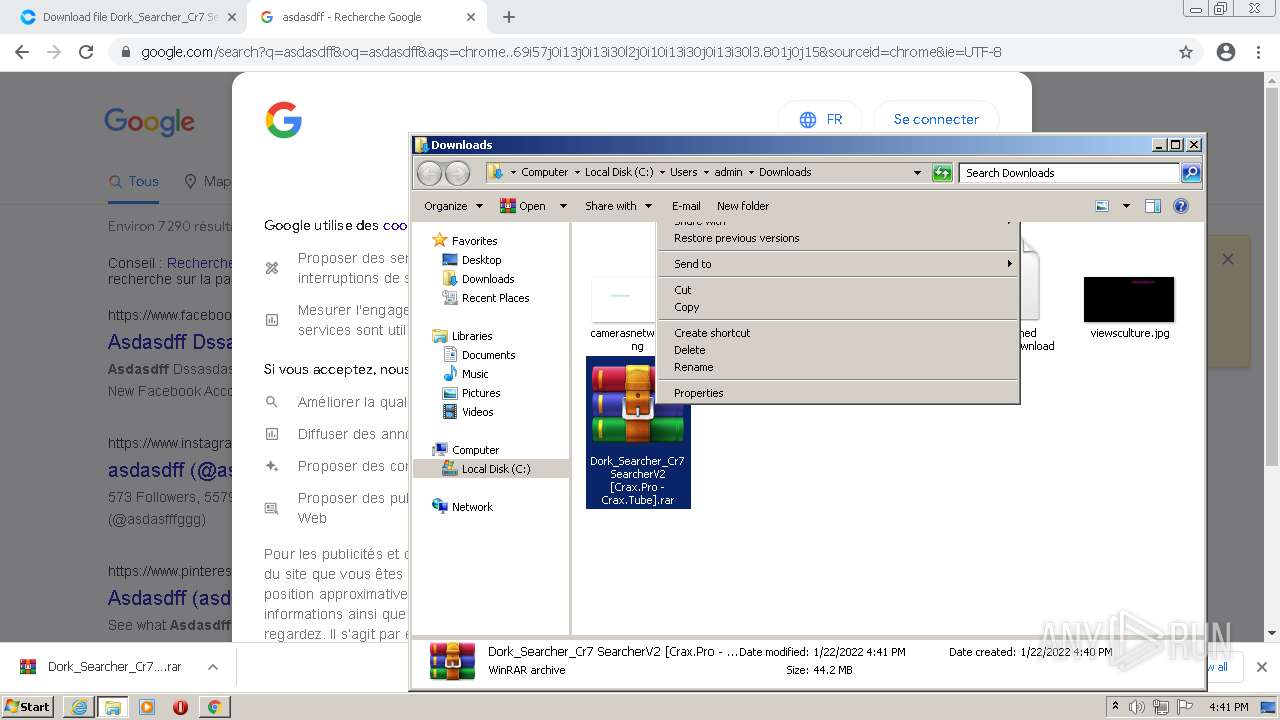
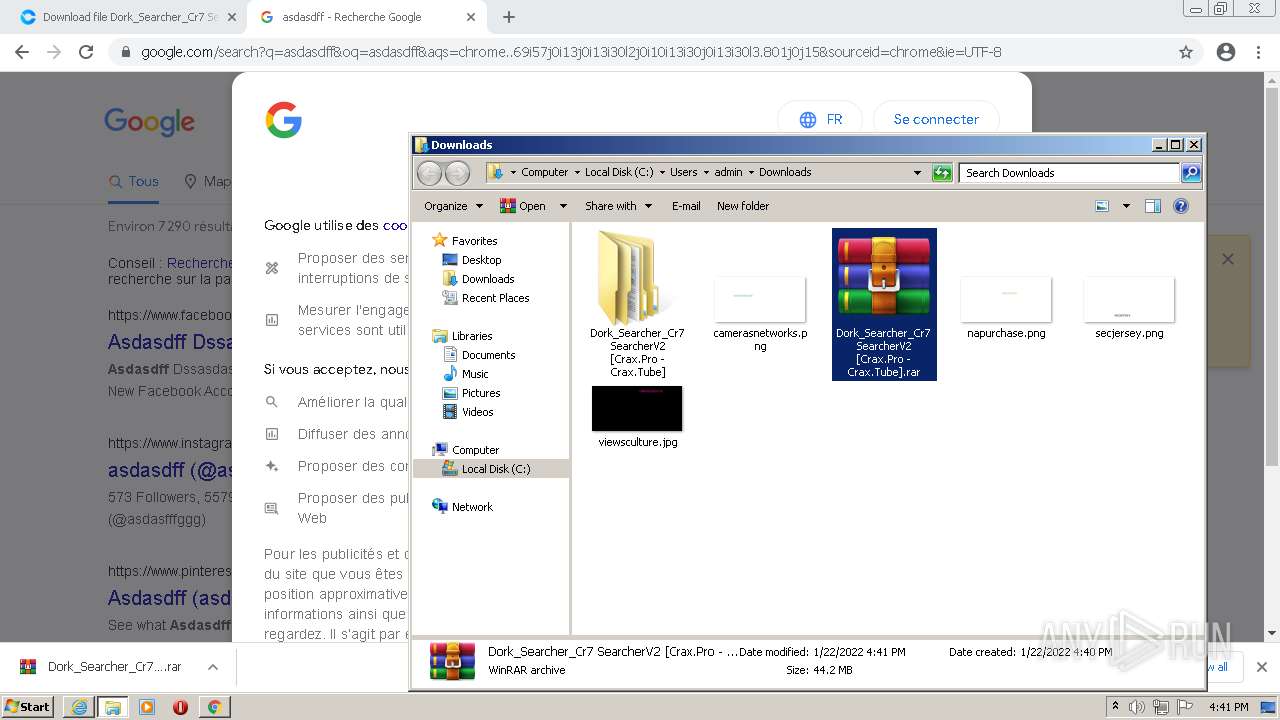
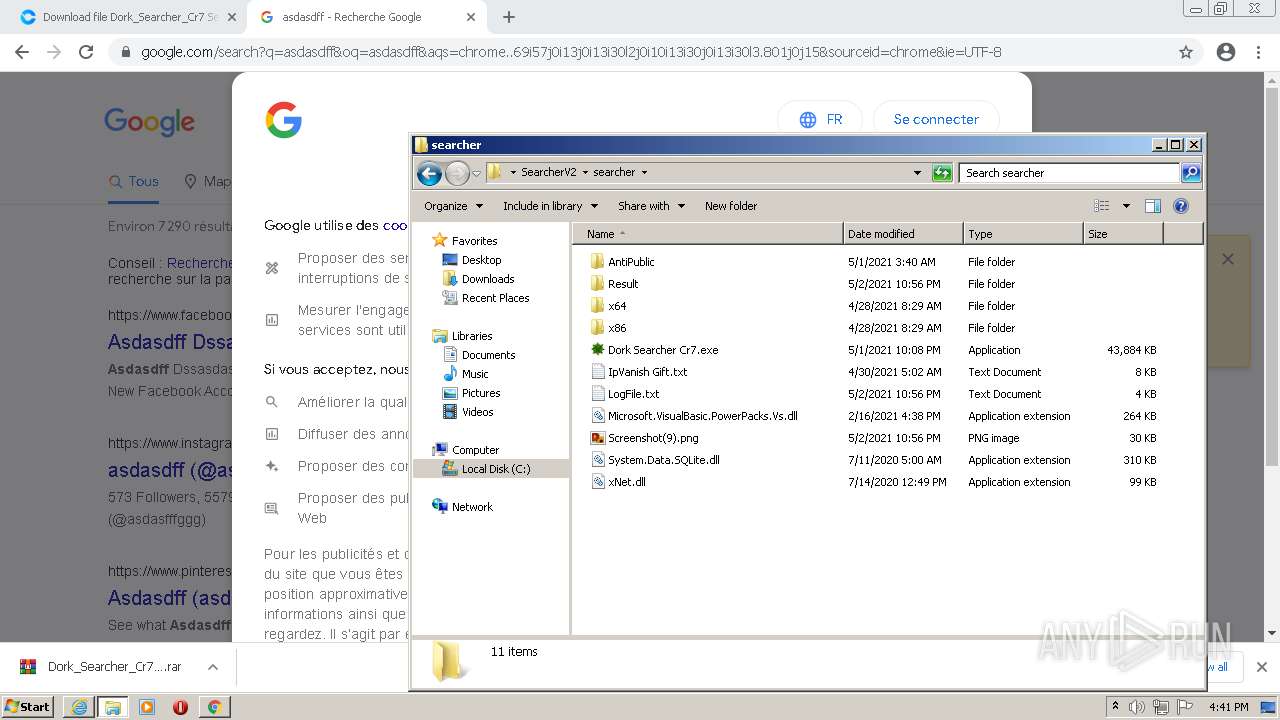
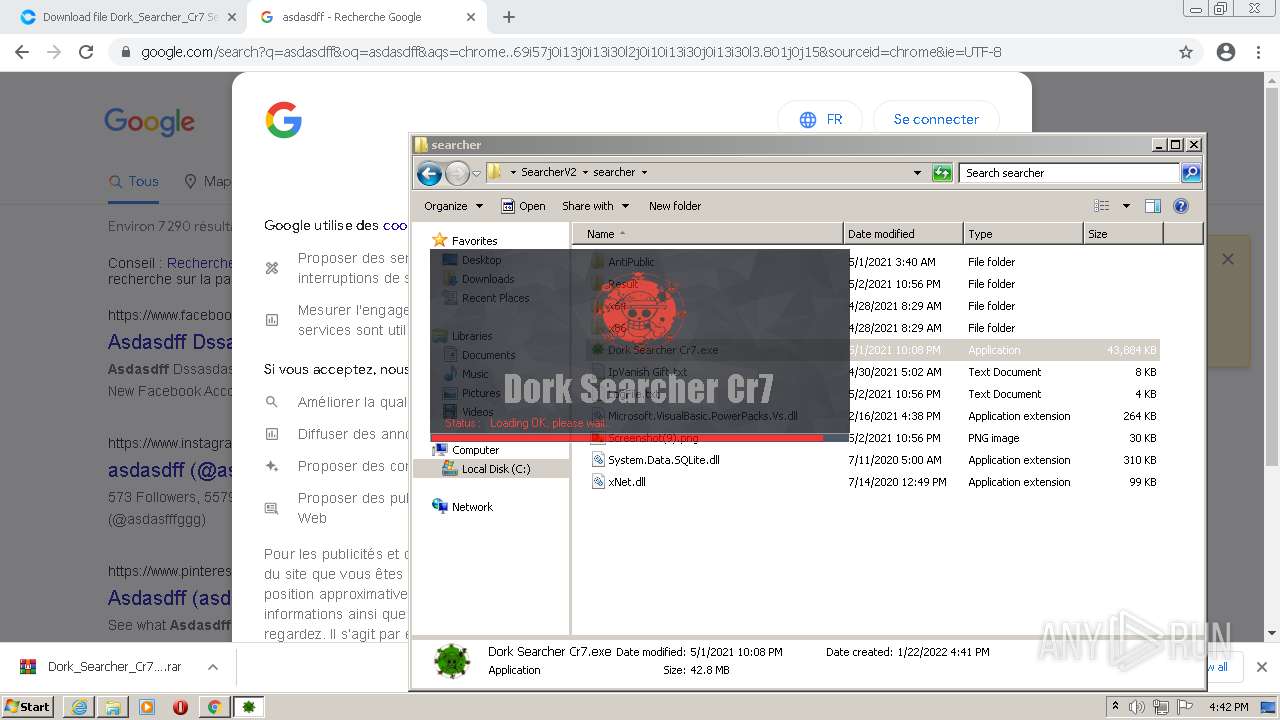
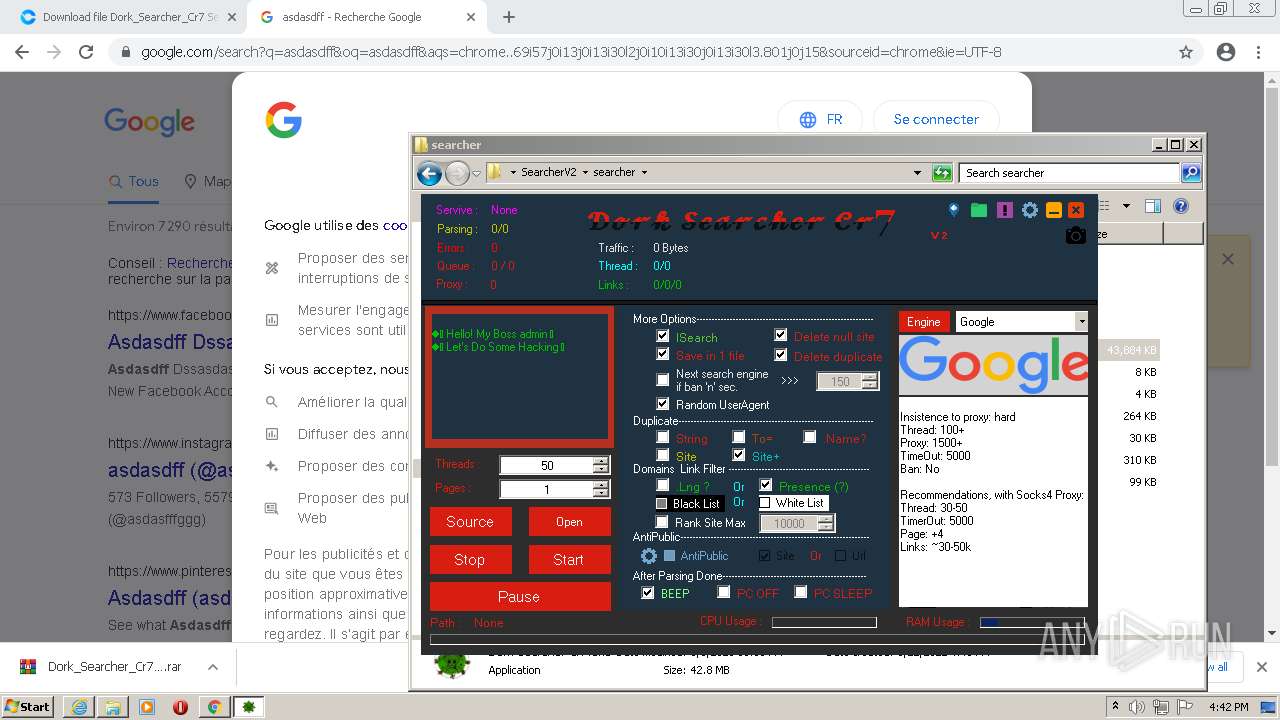
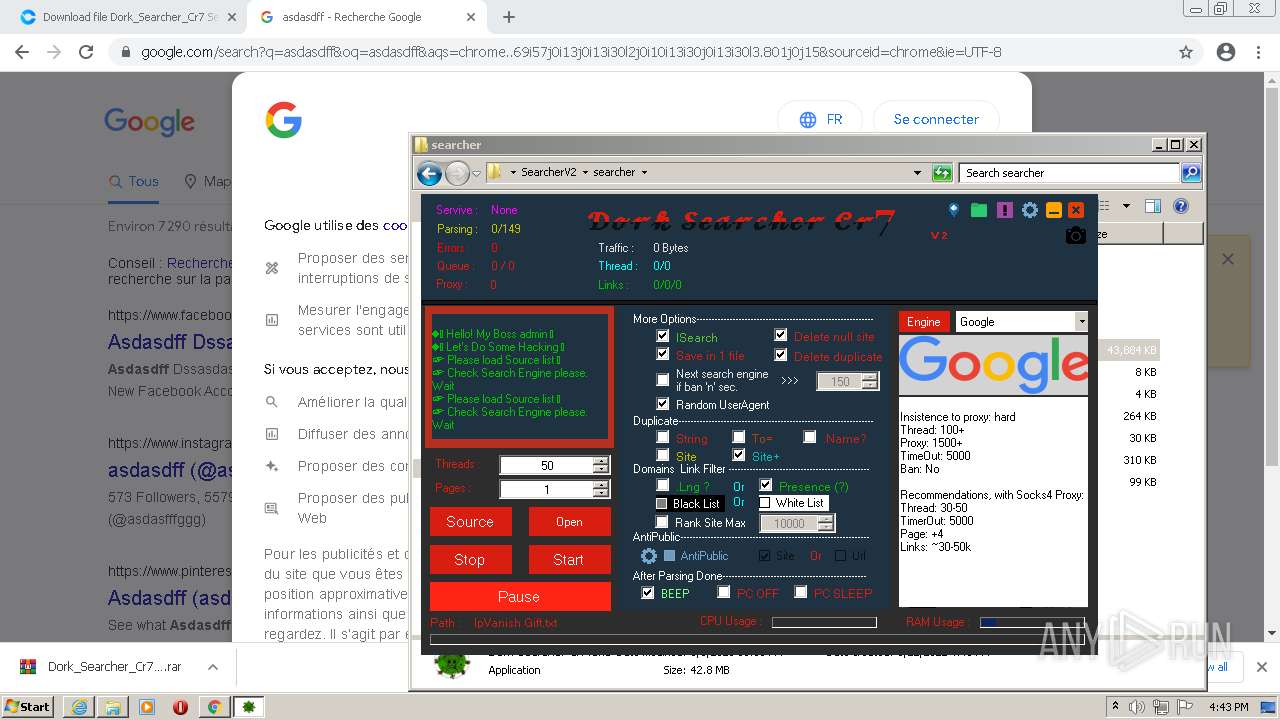
| URL: | https://crax.pro/resources/dork-searcher-cr7-v2-0-new-2k21.1765/download |
| Full analysis: | https://app.any.run/tasks/e1a70554-e9c6-4027-8399-c2ee85aa8aa3 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2022, 16:39:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D8AF8C4553AF2B390395808C93BFE206 |
| SHA1: | 86FED16CB25E9F5C1048C163E1A9E4FB9B1C7EF9 |
| SHA256: | 4D342FD2DCFC95BCA02ADE938D66FFCAD047CD92263C2514E700F438F7DFAA51 |
| SSDEEP: | 3:N8KnFtUXainG7XBQKBKS/:2KnFtUXajTBQK8S/ |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3960)
- chrome.exe (PID: 2856)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2248)
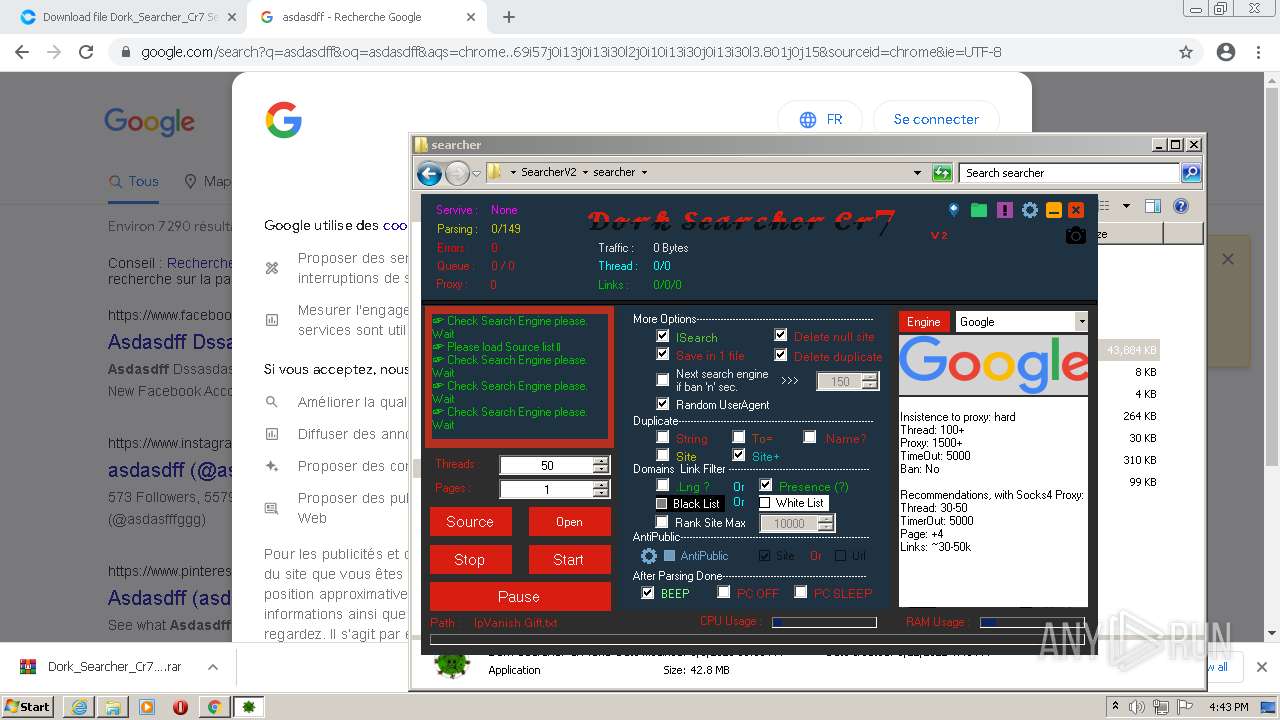
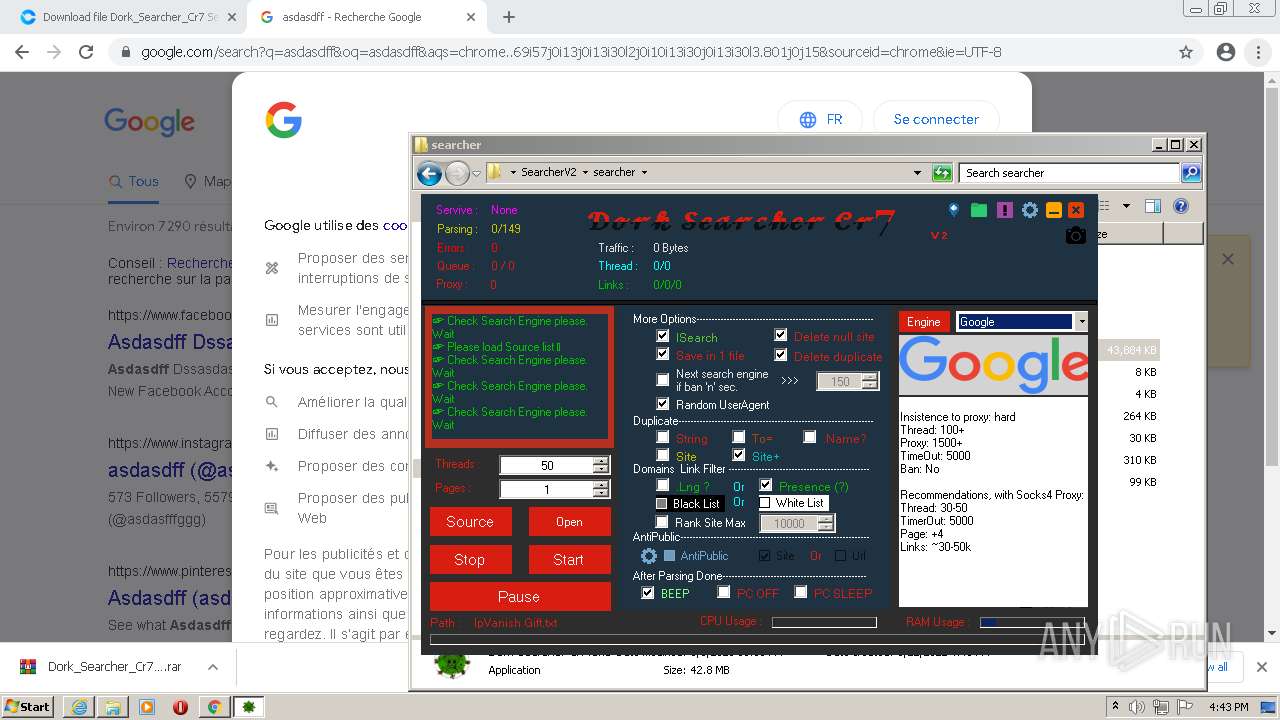
- Dork Searcher Cr7.exe (PID: 2868)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2504)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2836)
Reads the computer name
- WinRAR.exe (PID: 3960)
- Dork Searcher Cr7.exe (PID: 2868)
Checks supported languages
- WinRAR.exe (PID: 3960)
- Dork Searcher Cr7.exe (PID: 2868)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3960)
- chrome.exe (PID: 2856)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3960)
- chrome.exe (PID: 2856)
Reads Environment values
- Dork Searcher Cr7.exe (PID: 2868)
INFO
Reads the computer name
- iexplore.exe (PID: 2824)
- chrome.exe (PID: 2836)
- iexplore.exe (PID: 2504)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 1168)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 492)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 2580)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 4076)
Checks supported languages
- iexplore.exe (PID: 2824)
- chrome.exe (PID: 1548)
- chrome.exe (PID: 2836)
- iexplore.exe (PID: 2504)
- chrome.exe (PID: 1168)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 2052)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 600)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 2632)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 492)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 2580)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 3552)
- chrome.exe (PID: 576)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 3780)
- chrome.exe (PID: 1784)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 3584)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 2360)
- chrome.exe (PID: 520)
- chrome.exe (PID: 4076)
- chrome.exe (PID: 392)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 272)
- chrome.exe (PID: 2640)
- chrome.exe (PID: 2856)
- chrome.exe (PID: 1188)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 3856)
Creates files in the user directory
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 2824)
Reads settings of System Certificates
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2504)
- chrome.exe (PID: 1168)
Changes settings of System certificates
- iexplore.exe (PID: 2824)
Application launched itself
- chrome.exe (PID: 2836)
- iexplore.exe (PID: 2824)
Checks Windows Trust Settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2504)
Reads internet explorer settings
- iexplore.exe (PID: 2504)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2824)
Manual execution by user
- chrome.exe (PID: 2836)
- WinRAR.exe (PID: 3960)
- Dork Searcher Cr7.exe (PID: 2868)
Reads the hosts file
- chrome.exe (PID: 2836)
- chrome.exe (PID: 1168)
Changes internet zones settings
- iexplore.exe (PID: 2824)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2836)
Reads the date of Windows installation
- chrome.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
45
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3212 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4000 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3232 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3984 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2368 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2856 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1352 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=880 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e4ed988,0x6e4ed998,0x6e4ed9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1080,13454362246088615240,3650123205174687129,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2760 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
32 720
Read events
32 328
Write events
378
Delete events
14
Modification events
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937006 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937006 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
6
Suspicious files
221
Text files
285
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1DCEC4C238E19B7FBA7F1B0350A3F02E | der | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\v1[1].js | text | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\M56O3PGB.txt | text | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1DCEC4C238E19B7FBA7F1B0350A3F02E | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\IK4J2AUE.txt | text | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\KPKPOFMP.txt | text | |
MD5:— | SHA256:— | |||
| 2836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EC335F-B14.pma | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
91
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.70 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.69 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.4 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 178 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | iexplore.exe | 2.16.186.27:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
2824 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2504 | iexplore.exe | 172.67.68.83:443 | crax.pro | — | US | unknown |
2504 | iexplore.exe | 2.16.106.233:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2824 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1168 | chrome.exe | 142.250.185.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1168 | chrome.exe | 142.250.186.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
1168 | chrome.exe | 142.250.181.228:443 | www.google.com | Google Inc. | US | whitelisted |
2824 | iexplore.exe | 172.67.68.83:443 | crax.pro | — | US | unknown |
1168 | chrome.exe | 142.250.185.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crax.pro |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |