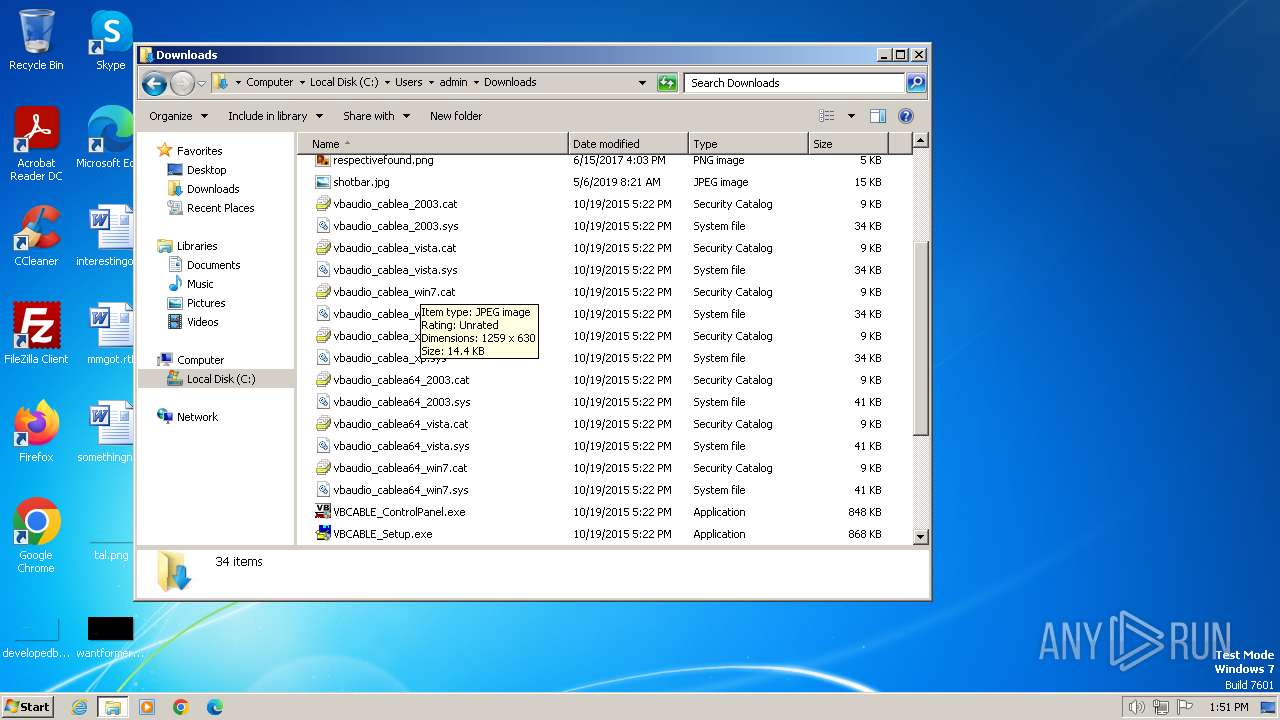
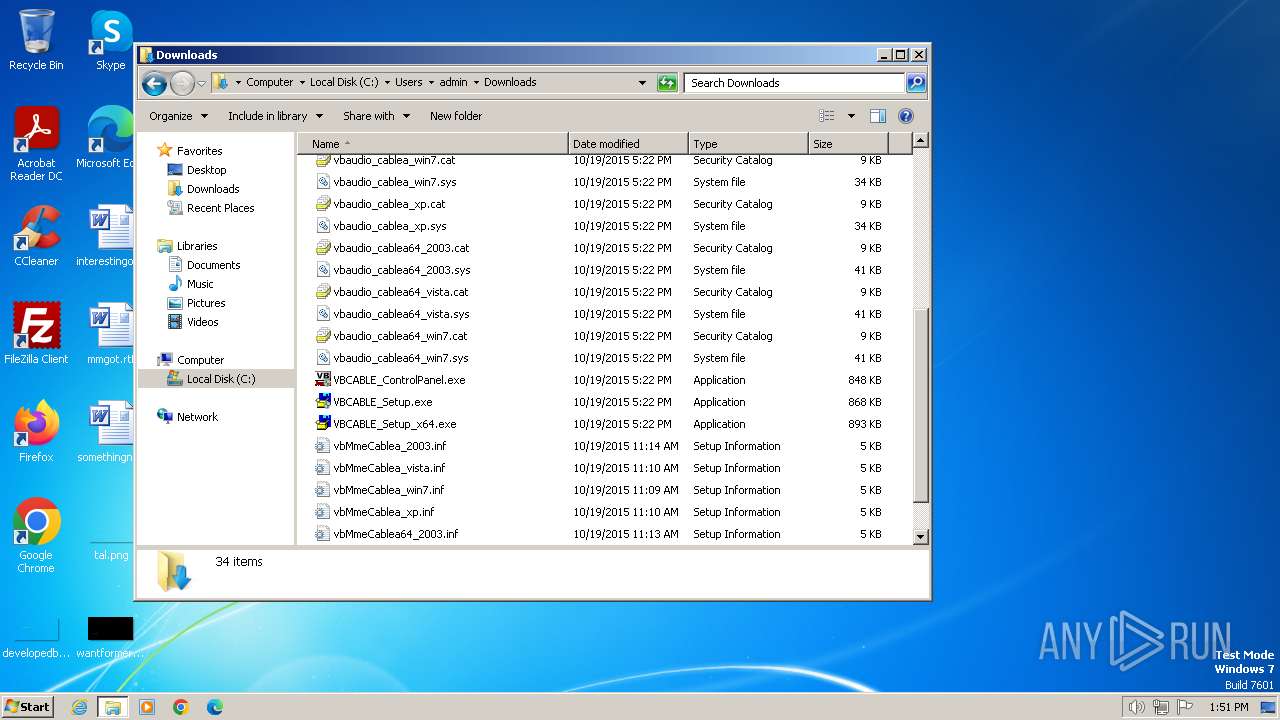
| File name: | VBCABLE_A_B_Driver_Pack43.zip |
| Full analysis: | https://app.any.run/tasks/cd0b6362-15af-47e4-a662-569760c1861e |
| Verdict: | Malicious activity |
| Analysis date: | December 22, 2023, 13:50:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 094F53B935B5B8C15175D1D4DAAB8F1E |
| SHA1: | 7DD0329EC5D32CC1127EBD62EF1A36F2FDB981D1 |
| SHA256: | 4D23903C4AA4D9E2C4F320A7989D071AF9FA822D852814AEEB3F905E03128FD0 |
| SSDEEP: | 98304:cDRVYD+AYKZ9sYbFdIk/5lsCLABGyYI3ioupXNe6NeEqWbMcVcSfmLvvZRnAJhPL:oLNhQ9gu |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 664)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1404)
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Reads security settings of Internet Explorer
- VBCABLE_Setup.exe (PID: 2432)
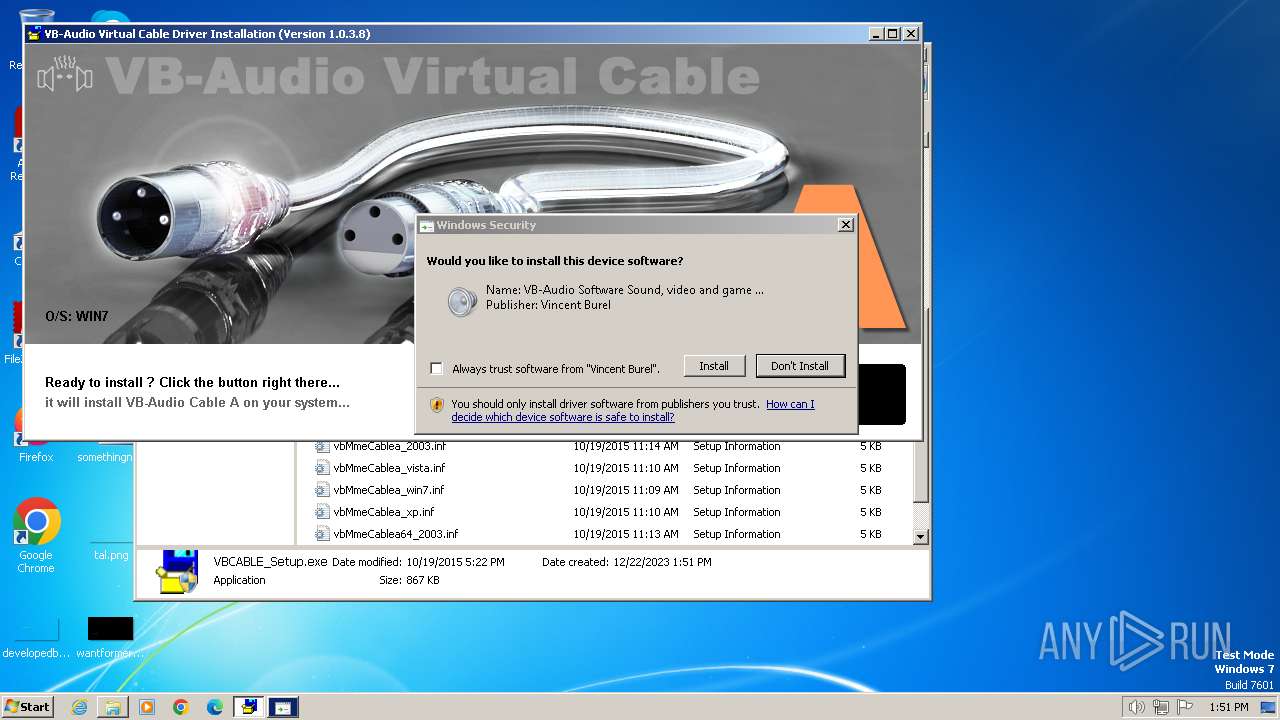
Checks Windows Trust Settings
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Reads settings of System Certificates
- VBCABLE_Setup.exe (PID: 2432)
- rundll32.exe (PID: 552)
Creates files in the driver directory
- drvinst.exe (PID: 664)
INFO
Application launched itself
- WinRAR.exe (PID: 2184)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2184)
- WinRAR.exe (PID: 1404)
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Manual execution by a user
- explorer.exe (PID: 2268)
- VBCABLE_Setup.exe (PID: 2328)
- VBCABLE_Setup.exe (PID: 2432)
Checks supported languages
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Reads the computer name
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Reads the machine GUID from the registry
- VBCABLE_Setup.exe (PID: 2432)
- drvinst.exe (PID: 664)
Create files in a temporary directory
- VBCABLE_Setup.exe (PID: 2432)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 552)
Executes as Windows Service
- VSSVC.exe (PID: 680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2015:10:19 16:33:54 |
| ZipCRC: | 0xddadde54 |
| ZipCompressedSize: | 1087106 |
| ZipUncompressedSize: | 1087106 |
| ZipFileName: | VBCABLE_B_Driver_Pack43.zip |
Total processes
47
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{1306230b-ddfb-326e-aca7-6969d7348d72} Global\{32541860-c44d-5a2a-611d-fb57deb3a044} C:\Windows\System32\DriverStore\Temp\{159a2e61-230b-1306-98c6-1521fb889129}\vbmmecablea_win7.inf C:\Windows\System32\DriverStore\Temp\{159a2e61-230b-1306-98c6-1521fb889129}\vbaudio_cablea_win7.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{759f3b78-9716-51fe-43d1-cd3abf9cd105}\vbmmecablea_win7.inf" "0" "66a81b357" "00000330" "WinSta0\Default" "000004BC" "208" "c:\users\admin\downloads" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa2184.4209\VBCABLE_A_Driver_Pack43.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\VBCABLE_A_B_Driver_Pack43.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2268 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
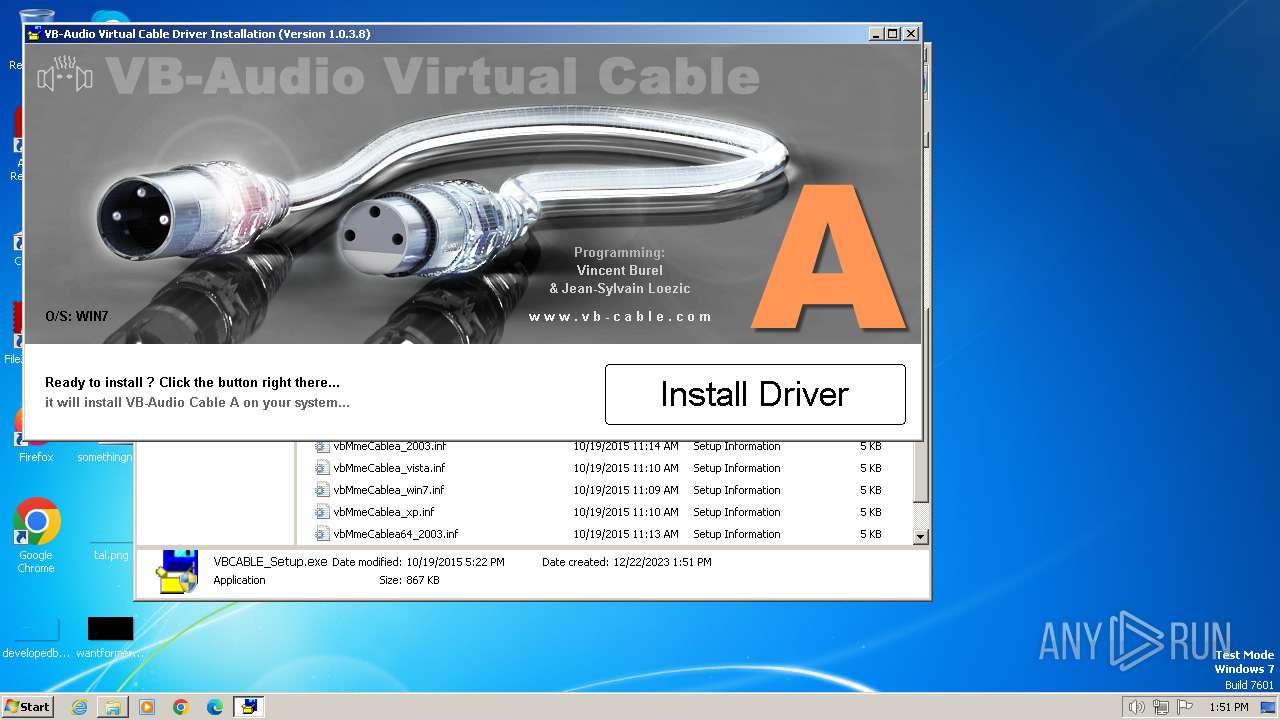
| 2328 | "C:\Users\admin\Downloads\VBCABLE_Setup.exe" | C:\Users\admin\Downloads\VBCABLE_Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: VB-AUDIO Software Integrity Level: MEDIUM Description: VB-AUDIO Virtual Cable Installer Exit code: 3221226540 Version: 1, 0, 3, 8 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Downloads\VBCABLE_Setup.exe" | C:\Users\admin\Downloads\VBCABLE_Setup.exe | explorer.exe | ||||||||||||
User: admin Company: VB-AUDIO Software Integrity Level: HIGH Description: VB-AUDIO Virtual Cable Installer Exit code: 0 Version: 1, 0, 3, 8 Modules
| |||||||||||||||
Total events
13 041
Read events
12 940
Write events
101
Delete events
0
Modification events
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
20
Suspicious files
14
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbMmeCablea64_win7.inf | ini | |
MD5:B6B8E6AFAD30C1C101D6CF3AB8C89127 | SHA256:7F07AD455C2C726F00374CFB0F2DF81939A5588E43835E3EB751062BDC53B70B | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea_2003.sys | executable | |
MD5:ABEDE3FF6C0BE2D3C96C91C945D0A5EA | SHA256:73333853C5B438CA111781FE3A397C27AC02874BED2F98657A4873AF4F3BC264 | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\readme.txt | text | |
MD5:67DE05DF45E547B434294B954C2DB7C4 | SHA256:C802624D64DEA7F7B333E4464D3EC9B8BB2C6DA2CC1BD2D3A56889CF60ED77A7 | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea_vista.cat | cat | |
MD5:082BB4F183483230C1CE3B7525AA3979 | SHA256:A1861115A107E5085E25C0706A3E1D76942599CFF18A2FD2F8FBE59E6E1EAD64 | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea_win7.cat | cat | |
MD5:BD868706619EF599BE18C207CFD2DD7B | SHA256:9EAB8BF838C6593FEB1547C032018656A72CF83A11EE260675529F0684EC9E9C | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2184.4209\VBCABLE_A_Driver_Pack43.zip | compressed | |
MD5:7266CEC4ED6B388180AD96F906CBF186 | SHA256:CC22E1BA821563A34CE1B7035FF136BE694BEEB9AAEC8934E6FD1B0E86CF05AA | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\pin_out.ico | image | |
MD5:65B15B7DAF75FF7FCF5DB697C2AEF97A | SHA256:06899AB8DA336563EC1FBF2B67F2A7EC6E56F1FAB10157F01B93860BA0C8FB46 | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea_2003.cat | cat | |
MD5:E9C5FBE24EFA70BD6954D5D97B4E4F50 | SHA256:AFA56498E777E3C9F21011549826D3246692A8229C7C9BDB0CD3E8F70360449D | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea_win7.sys | executable | |
MD5:E3D414CEF03470338A1F2C4A81917AF3 | SHA256:4ACC9A4E2E720EA91C7C662BA97FF945F10C6AB24341BD56FFA9BF8DB9250D58 | |||
| 1404 | WinRAR.exe | C:\Users\admin\Downloads\vbaudio_cablea64_2003.sys | executable | |
MD5:8D02577B426006CABA38104B99250FD9 | SHA256:0E3211EB286BBBBBA9AABE9106F688E45F6A18D59B2562B275C3CB7E66793FF6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |