| File name: | ArmouryCrateInstaller.exe |
| Full analysis: | https://app.any.run/tasks/bd616895-c5ee-4cba-8353-33bd006bc9d4 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2024, 07:31:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 350ADD77EC579BBBDE55F5CD84E5104F |
| SHA1: | 7497FD58BF6F80EFDB8D569C1771FFE9BEC21977 |
| SHA256: | 4D05106479102D0AC3B774FB5287DEE09A785CB27F9C64884D46631E2F52337F |
| SSDEEP: | 98304:wWBAn6mYHT6Gl2Bn8uSM1ytXp17JKR7jLVW0Whm9T5DfUqbBiKhOFYMLlt1DM8nJ:w36 |
MALICIOUS
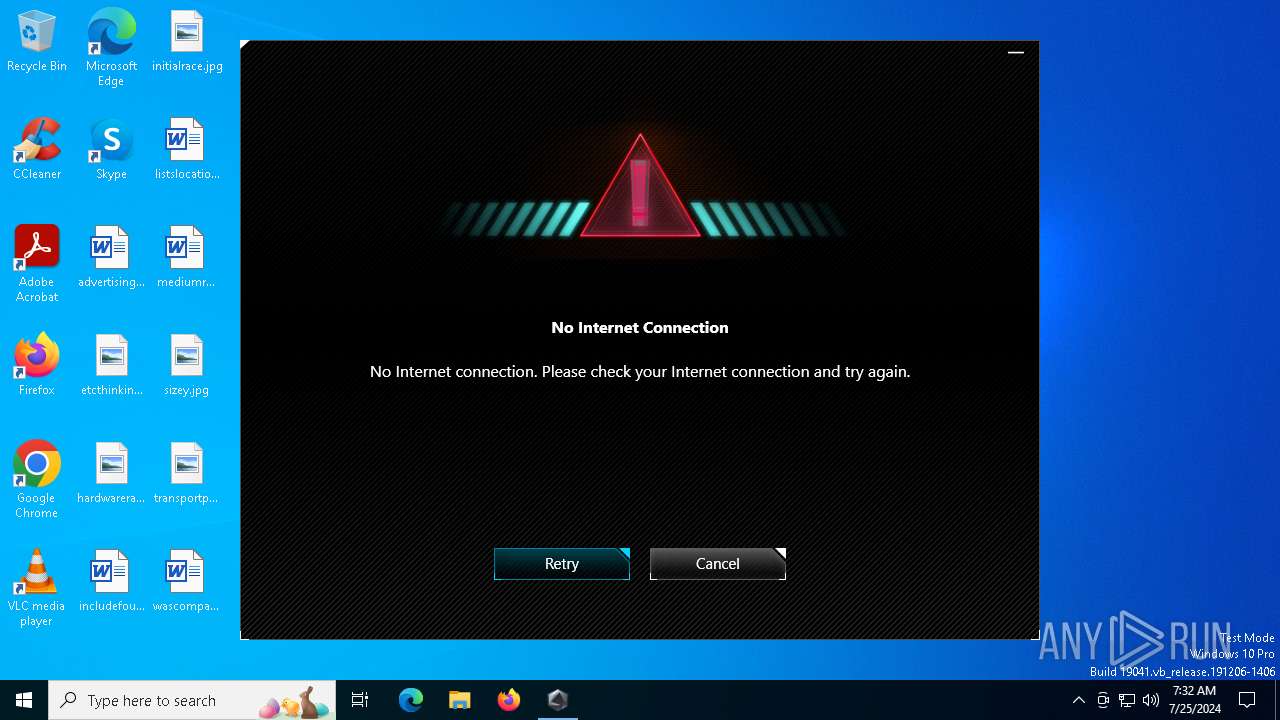
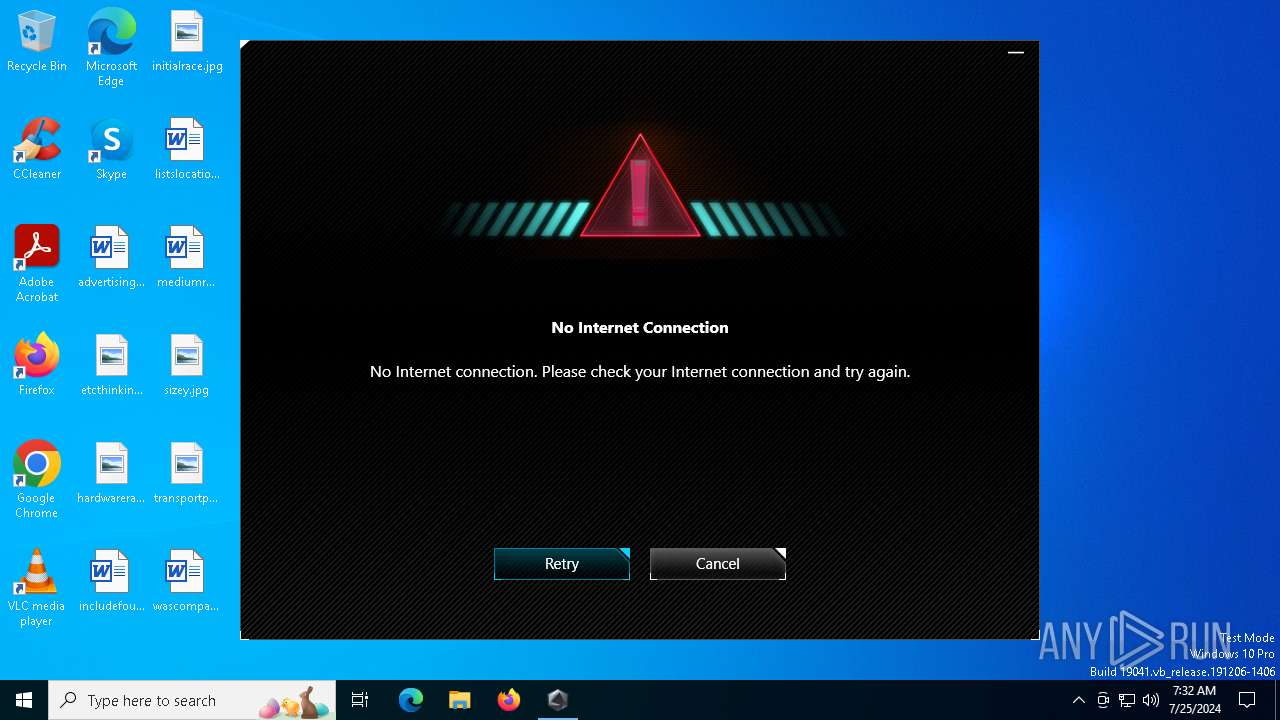
Drops the executable file immediately after the start
- ArmouryCrateInstaller.exe (PID: 4880)
SUSPICIOUS
Creates file in the systems drive root
- ArmouryCrateInstaller.exe (PID: 4880)
- conhost.exe (PID: 4044)
Executable content was dropped or overwritten
- ArmouryCrateInstaller.exe (PID: 4880)
Reads the date of Windows installation
- ArmouryCrateInstaller.exe (PID: 4880)
Reads security settings of Internet Explorer
- ArmouryCrateInstaller.exe (PID: 4880)
- Armoury Crate Installer.exe (PID: 4360)
- Armoury Crate Installer.exe (PID: 6604)
- Armoury Crate Installer.exe (PID: 4116)
- Armoury Crate Installer.exe (PID: 6956)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6448)
- cmd.exe (PID: 1756)
- cmd.exe (PID: 6544)
Executes as Windows Service
- AsusROGLSLService.exe (PID: 2192)
Starts CMD.EXE for commands execution
- ArmouryCrateInstaller.exe (PID: 4880)
INFO
Checks supported languages
- ArmouryCrateInstaller.exe (PID: 4880)
- Armoury Crate Installer.exe (PID: 4360)
- Armoury Crate Installer.exe (PID: 6956)
- AsusROGLSLService.exe (PID: 2192)
- Armoury Crate Installer.exe (PID: 6604)
- Armoury Crate Installer.exe (PID: 4116)
- AsusROGLSLService.exe (PID: 3968)
- AsusROGLSLService.exe (PID: 7080)
Creates files in the program directory
- ArmouryCrateInstaller.exe (PID: 4880)
- AsusROGLSLService.exe (PID: 3968)
- Armoury Crate Installer.exe (PID: 4360)
- Armoury Crate Installer.exe (PID: 6956)
- Armoury Crate Installer.exe (PID: 6604)
- Armoury Crate Installer.exe (PID: 4116)
Reads the computer name
- ArmouryCrateInstaller.exe (PID: 4880)
- AsusROGLSLService.exe (PID: 3968)
- AsusROGLSLService.exe (PID: 7080)
- AsusROGLSLService.exe (PID: 2192)
- Armoury Crate Installer.exe (PID: 4360)
- Armoury Crate Installer.exe (PID: 6956)
- Armoury Crate Installer.exe (PID: 6604)
- Armoury Crate Installer.exe (PID: 4116)
Process checks computer location settings
- ArmouryCrateInstaller.exe (PID: 4880)
Reads the machine GUID from the registry
- Armoury Crate Installer.exe (PID: 4360)
- Armoury Crate Installer.exe (PID: 6956)
- Armoury Crate Installer.exe (PID: 6604)
- Armoury Crate Installer.exe (PID: 4116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (83) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (9) |
| .exe | | | Generic Win/DOS Executable (3.9) |
| .exe | | | DOS Executable Generic (3.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:01:17 13:47:38+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 398848 |
| InitializedDataSize: | 3752960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x37c24 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.2.11.2 |
| ProductVersionNumber: | 3.2.11.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral 2 |
| CharacterSet: | Unicode |
| CompanyName: | ASUS |
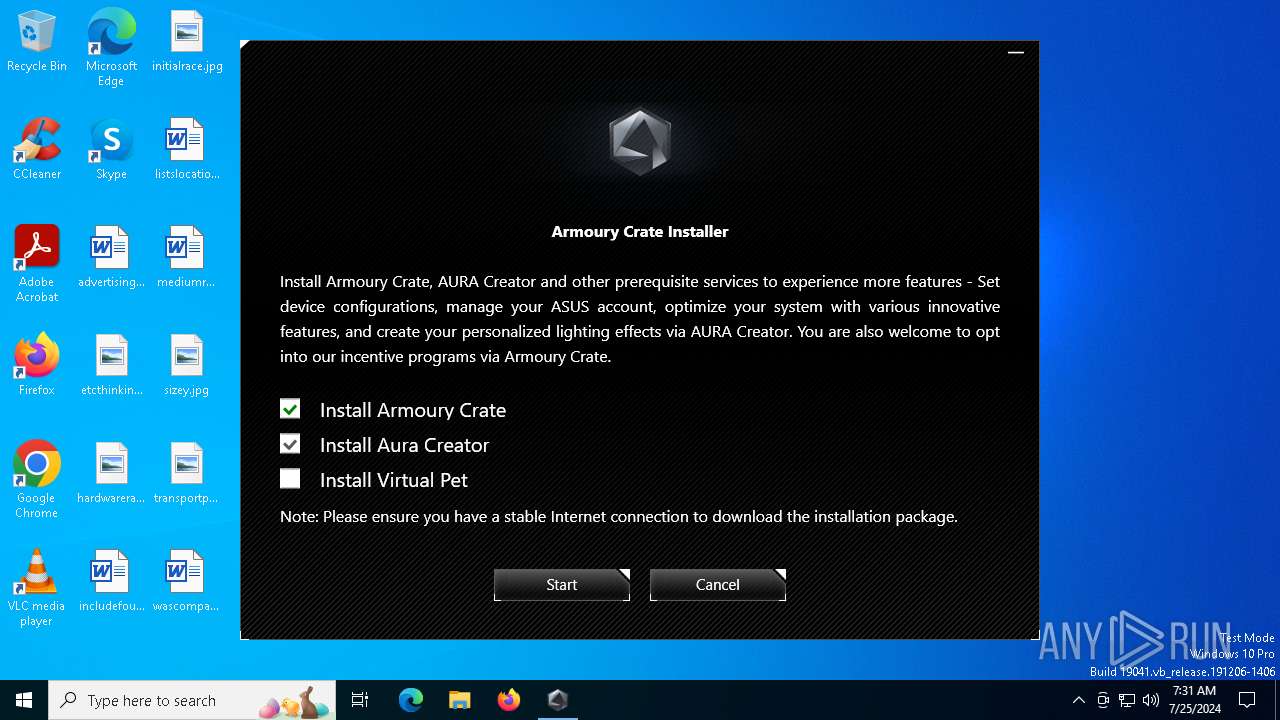
| FileDescription: | The installer for Armoury Crate and Aura Creator. |
| FileVersion: | 3.2.11.2 |
| LegalCopyright: | Copyright (C) 2019 |
| OriginalFileName: | ArmouryCrateInstaller.exe |
| ProductVersion: | 3.2.11.2 |
Total processes
142
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\ArmouryCrateInstaller.exe" | C:\ArmouryCrateInstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: ASUS Integrity Level: MEDIUM Description: The installer for Armoury Crate and Aura Creator. Exit code: 3221226540 Version: 3.2.11.2 Modules
| |||||||||||||||
| 1756 | C:\WINDOWS\system32\cmd.exe /c Powershell "(get-appxpackage -Name B9ECED6F.ArmouryCrateSE).Version" | C:\Windows\System32\cmd.exe | — | ArmouryCrateInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusROGLSLService.exe" -runservice | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusROGLSLService.exe | services.exe | ||||||||||||
User: SYSTEM Company: ASUS Integrity Level: SYSTEM Version: 2.3.11.0 Modules
| |||||||||||||||
| 2616 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3968 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusROGLSLService.exe" -remove | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusROGLSLService.exe | — | ArmouryCrateInstaller.exe | |||||||||||
User: admin Company: ASUS Integrity Level: HIGH Exit code: 0 Version: 2.3.11.0 Modules
| |||||||||||||||
| 4044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ArmouryCrateInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4116 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe" -roglsloaderstart -win armourycrate -networkerror | C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe | — | AsusROGLSLService.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Armoury Crate Installer Version: 2.3.11.2 Modules
| |||||||||||||||
| 4248 | Powershell "(get-appxpackage -Name B9ECED6F.ArmouryCrateSE).Version" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4360 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe" -roglsloaderstart -win armourycrate -acinstaller | C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe | — | AsusROGLSLService.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Armoury Crate Installer Exit code: 21858 Version: 2.3.11.2 Modules
| |||||||||||||||
| 4880 | "C:\ArmouryCrateInstaller.exe" | C:\ArmouryCrateInstaller.exe | explorer.exe | ||||||||||||
User: admin Company: ASUS Integrity Level: HIGH Description: The installer for Armoury Crate and Aura Creator. Exit code: 0 Version: 3.2.11.2 Modules
| |||||||||||||||
Total events
20 486
Read events
20 465
Write events
19
Delete events
2
Modification events
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | ACInstallPath |
Value: C: | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | InstallFinish |
Value: 0 | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | delete value | Name: | aaiu |
Value: | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | delete value | Name: | InstallerSilentMode |
Value: | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4880) ArmouryCrateInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7080) AsusROGLSLService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | aaiu |
Value: 0 | |||
| (PID) Process: | (4360) Armoury Crate Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Left |
Value: 0 | |||
Executable files
9
Suspicious files
1
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | AsusROGLSLService.exe | C:\ProgramData\ASUS\ALL\ACLoader\AsusROGLSLService.log | text | |
MD5:DC7A87483870EB6EFB7DBE6CE61C9BBF | SHA256:C918FE217F8B637E9E6F25F1FB20B45141E977F513F30D7032A8B6F12EF7D94A | |||
| 4880 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe | executable | |
MD5:F0CDCAF5152EFDE0DB8B6D962F9D7C6B | SHA256:F2E5C2982BBFAFB9B97DEB17A3D1499768E6A26AA3BAB4CF512ABF033F694AE2 | |||
| 3968 | AsusROGLSLService.exe | C:\ProgramData\ASUS\ALL\ACLoader\ArmouryCrateInstaller.log | text | |
MD5:71AABCFE654232FEF3867EE55D5638CC | SHA256:E2394A391138304E19B37D01BE0011E3A19A445700E0F17A2ADD9B9B2C47BAF4 | |||
| 4880 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsZip.dll | executable | |
MD5:964068210EDCB3631F02E45856EB291E | SHA256:4CF079D4D7A154CD93F65934B5D115F07AF8F25EE24930E6CC606DFB0AEA2A4E | |||
| 4880 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\Newtonsoft.Json.dll | executable | |
MD5:081D9558BBB7ADCE142DA153B2D5577A | SHA256:B624949DF8B0E3A6153FDFB730A7C6F4990B6592EE0D922E1788433D276610F3 | |||
| 6056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5kythodp.is0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4880 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\CheckTool.exe | executable | |
MD5:12AB05AE37EF47DA353EFF14D5A81382 | SHA256:87D2FF260502B5C954C1BB4B867264BD5343451260151070A8B56225A8B4986E | |||
| 6056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zbx2keio.jqe.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4880 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusROGLSLService.exe | executable | |
MD5:12D2B87765FA26B2FCE79C806F4EB2EA | SHA256:43A0C9E2B294656EFF305EC8A247D647BC3B85542F2FE1EC424D7FDC822A5F07 | |||
| 6056 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:8FBC791747280AD0113BBDE4A8DF1B1D | SHA256:37878E09E57EA184973E2A953AA9B354E69621A6BDB437B61E574E1CB100CE31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4012 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4512 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.178:443 | — | Akamai International B.V. | DE | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4512 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6176 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
AsusROGLSLService.exe | Failed to get baseboard manufacturer via WMI, get via registry. |