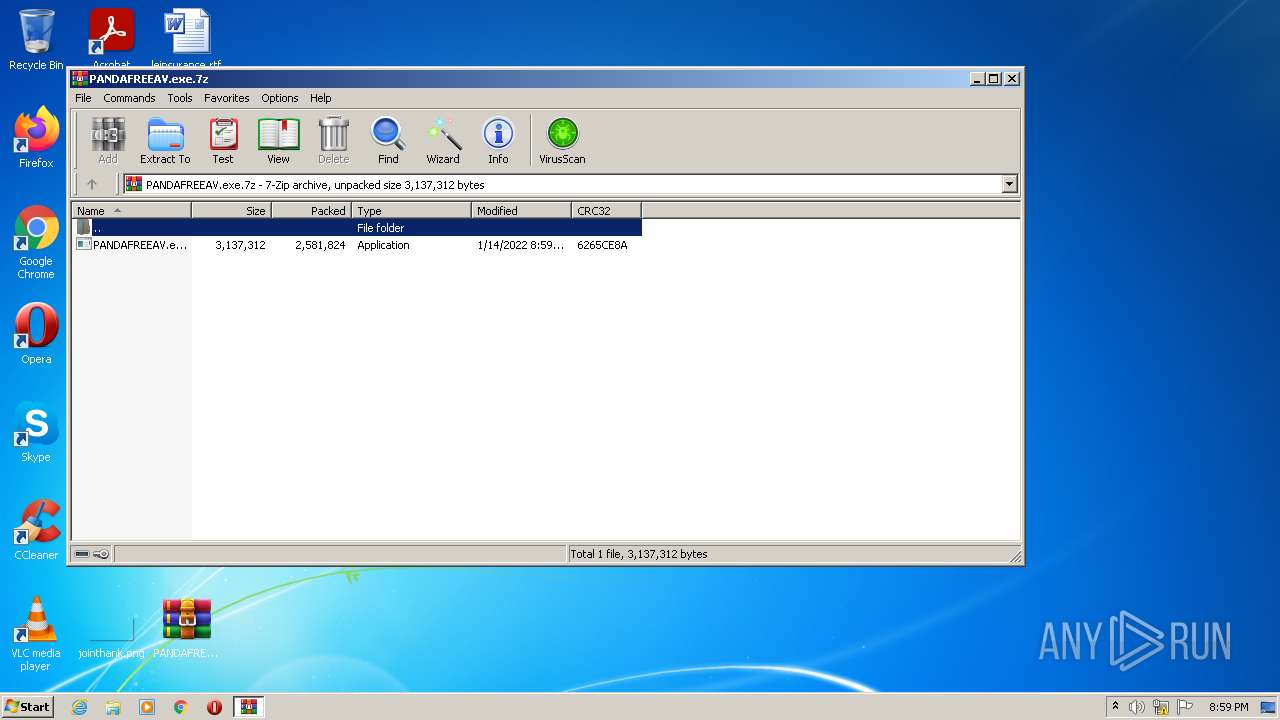
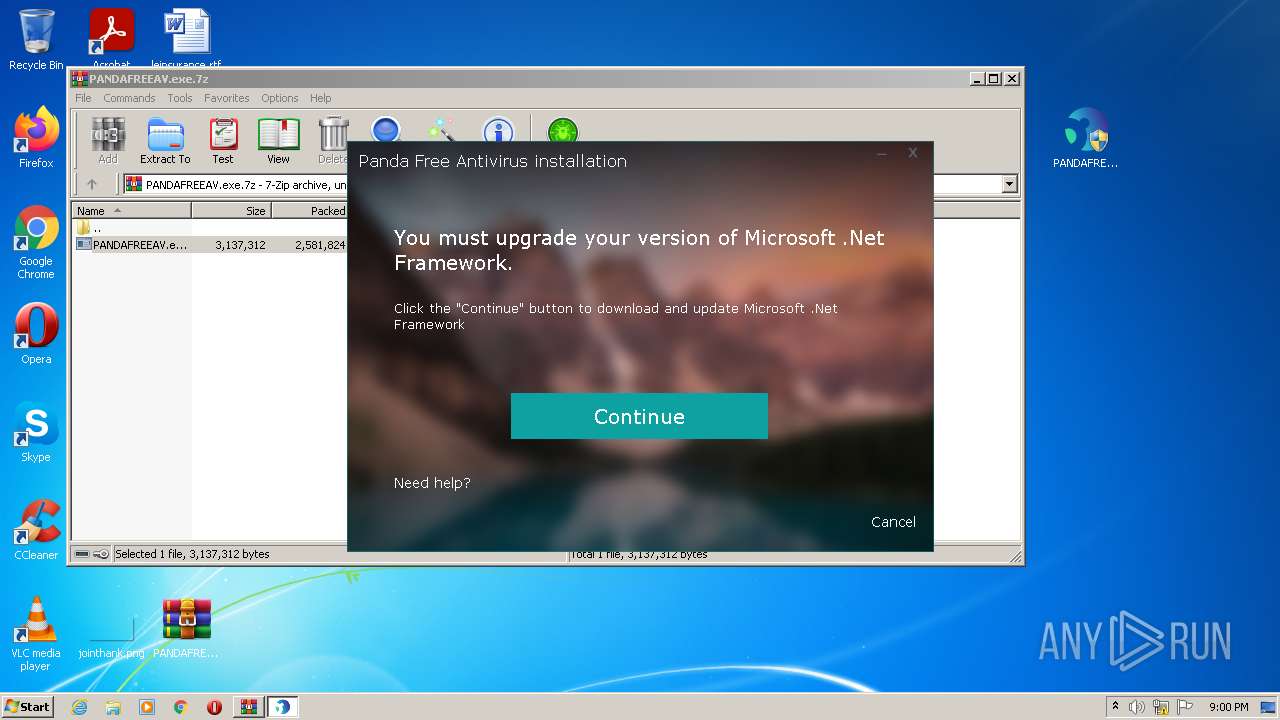
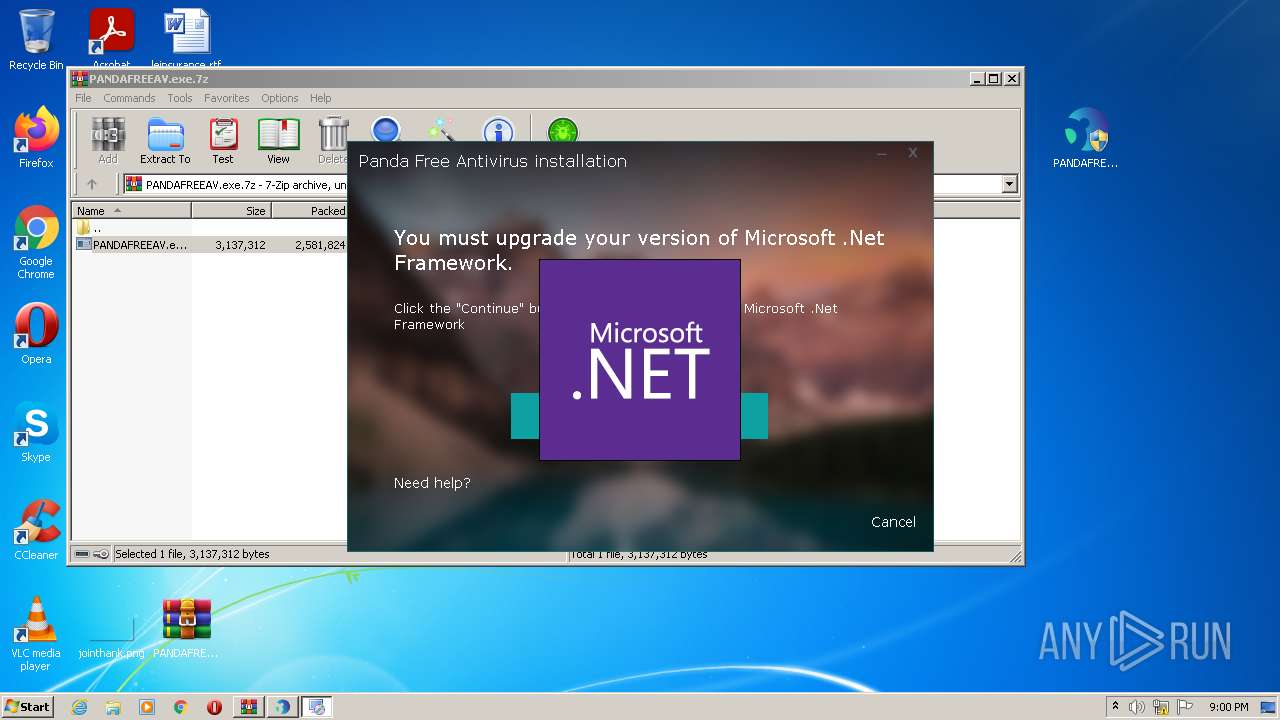
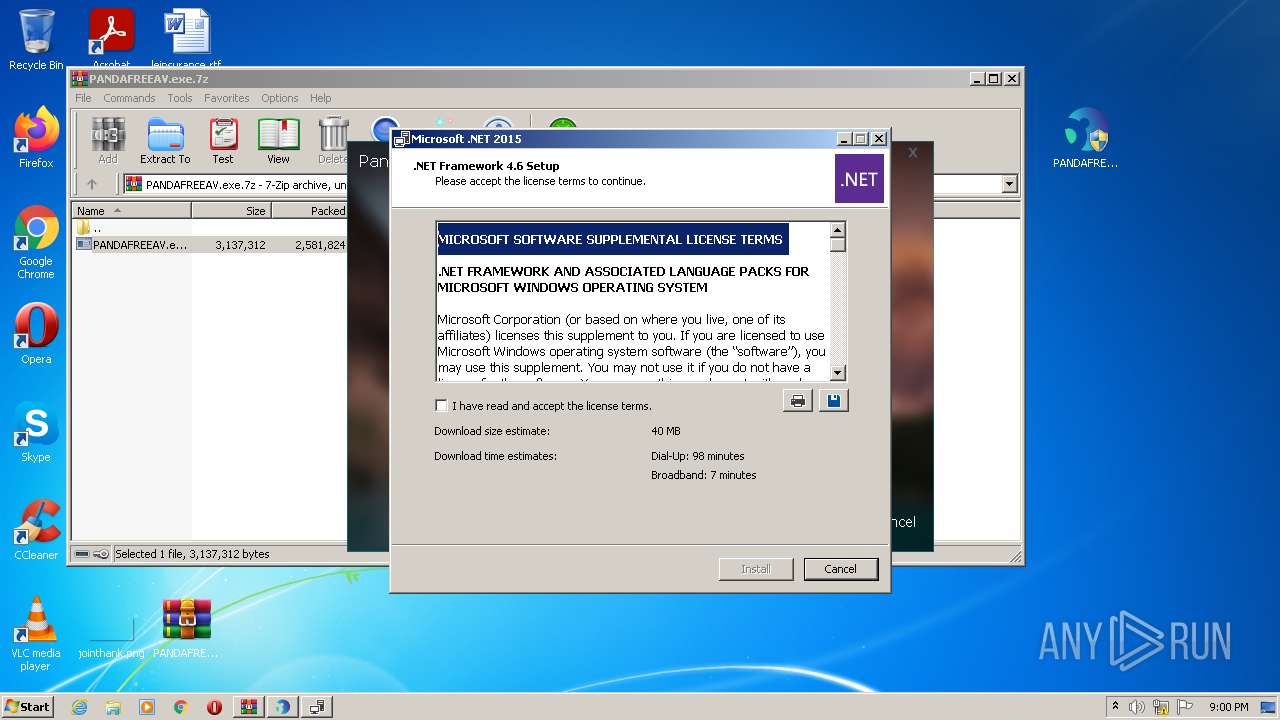
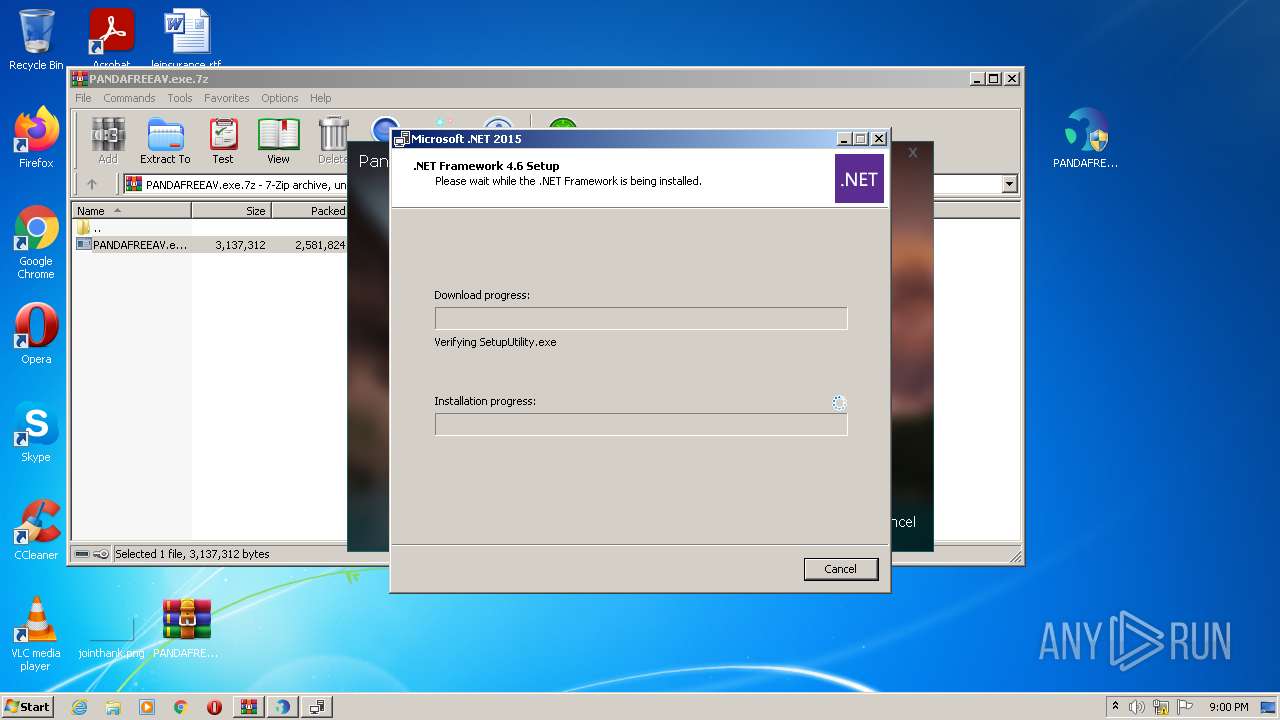
| File name: | PANDAFREEAV.exe.7z |
| Full analysis: | https://app.any.run/tasks/2a52a337-4164-474a-ae42-ad898cb3b923 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 20:59:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EE2D971CECF7C7C5B94B1DB04F324007 |
| SHA1: | 7BA348194261A903938E15265B0F73C579123E0D |
| SHA256: | 4CFBFC663343D9B814D3F34142D9732B70508FDF82C1AE15D927A13840EF0AD1 |
| SSDEEP: | 49152:bsNAb4fijC72sqTRBFrshjHk1gb/sCTB4ouI/YEeifx6Ekm1:qfi2SFTRBFIhOC14e/6tEt |
MALICIOUS
Application was dropped or rewritten from another process
- Stub.exe (PID: 3652)
- PANDAFREEAV.exe (PID: 1324)
- Setup.exe (PID: 2368)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
- PANDAFREEAV.exe (PID: 460)
- SetupUtility.exe (PID: 832)
- SetupUtility.exe (PID: 2324)
Drops executable file immediately after starts
- PANDAFREEAV.exe (PID: 460)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
Loads dropped or rewritten executable
- Setup.exe (PID: 2368)
- Stub.exe (PID: 3652)
Actions looks like stealing of personal data
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
Changes settings of System certificates
- Setup.exe (PID: 2368)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2732)
- Stub.exe (PID: 3652)
- Setup.exe (PID: 2368)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
- SetupUtility.exe (PID: 2324)
- TMP766B.tmp.exe (PID: 2684)
- SetupUtility.exe (PID: 832)
Checks supported languages
- WinRAR.exe (PID: 2732)
- Stub.exe (PID: 3652)
- PANDAFREEAV.exe (PID: 460)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
- Setup.exe (PID: 2368)
- SetupUtility.exe (PID: 832)
- SetupUtility.exe (PID: 2324)
- TMP766B.tmp.exe (PID: 2684)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2732)
- PANDAFREEAV.exe (PID: 460)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
- Stub.exe (PID: 3652)
- TMP766B.tmp.exe (PID: 2684)
- Setup.exe (PID: 2368)
Drops a file that was compiled in debug mode
- PANDAFREEAV.exe (PID: 460)
- Stub.exe (PID: 3652)
- {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe (PID: 3076)
Reads Environment values
- PANDAFREEAV.exe (PID: 460)
- Setup.exe (PID: 2368)
Reads CPU info
- Setup.exe (PID: 2368)
Creates files in the program directory
- Stub.exe (PID: 3652)
INFO
Reads settings of System Certificates
- Stub.exe (PID: 3652)
- Setup.exe (PID: 2368)
Manual execution by user
- PANDAFREEAV.exe (PID: 1324)
- PANDAFREEAV.exe (PID: 460)
Checks Windows Trust Settings
- Setup.exe (PID: 2368)
- Stub.exe (PID: 3652)
Dropped object may contain Bitcoin addresses
- Setup.exe (PID: 2368)
- SetupUtility.exe (PID: 832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
50
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Users\admin\Desktop\PANDAFREEAV.exe" | C:\Users\admin\Desktop\PANDAFREEAV.exe | Explorer.EXE | ||||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: HIGH Description: Panda Security SFX Exit code: 0 Version: 15.14.5.0 Modules
| |||||||||||||||
| 832 | SetupUtility.exe /aupause | C:\39adf1b9158926f1f694\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.0.0081.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\Desktop\PANDAFREEAV.exe" | C:\Users\admin\Desktop\PANDAFREEAV.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: MEDIUM Description: Panda Security SFX Exit code: 3221226540 Version: 15.14.5.0 Modules
| |||||||||||||||
| 2324 | SetupUtility.exe /screboot | C:\39adf1b9158926f1f694\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.0.0081.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2368 | C:\39adf1b9158926f1f694\\Setup.exe /x86 /x64 /web | C:\39adf1b9158926f1f694\Setup.exe | {E6381693-C0F2-419C-80D1-DE353CB06F20}.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 14.0.0081.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2684 | TMP766B.tmp.exe /Q /X:C:\39adf1b9158926f1f694\TMP766B.tmp.exe.tmp | C:\39adf1b9158926f1f694\TMP766B.tmp.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.6 Setup Exit code: 0 Version: 4.6.00081.00 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\PANDAFREEAV.exe.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\AppData\Local\Temp\{E6381693-C0F2-419C-80D1-DE353CB06F20}.exe" | C:\Users\admin\AppData\Local\Temp\{E6381693-C0F2-419C-80D1-DE353CB06F20}.exe | Stub.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.6 Setup Exit code: 0 Version: 4.6.00081.00 Modules
| |||||||||||||||
| 3652 | ".\Stub.exe" /c "181176" /u "http://acs.pandasoftware.com/Panda/FREEAV/181176/FREEAV.exe" /a "AFPZP1016" /p "4252" | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\Stub.exe | PANDAFREEAV.exe | ||||||||||||
User: admin Company: Panda Security, S.L. Integrity Level: HIGH Exit code: 0 Version: 5.0.38.3 Modules
| |||||||||||||||
Total events
11 425
Read events
11 360
Write events
65
Delete events
0
Modification events
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PANDAFREEAV.exe.7z | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
41
Suspicious files
8
Text files
114
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2732.15823\PANDAFREEAV.exe | executable | |
MD5:— | SHA256:— | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\img_product1.png | image | |
MD5:1714652A08968AAB7E4CCC1801E0050F | SHA256:EF693F45D5CFBE30A3F4F0081DAED414390B412DE0946CD45C14B9B218868390 | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\recorte_cloud.png | image | |
MD5:F037258F333D7967D5CB7672AE0DD4CA | SHA256:226928BD446DBF9542DBDE8D38367194DCCA65C18A552F4F26DAF30520E41822 | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\ico_ven_cancel.png | image | |
MD5:D3D94C8ACB4CE42424526DA2DCF5DF39 | SHA256:4E67660226A201929A6CF6D75CBA7681FA278D30541D412458768FF785EA886B | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\opera_dan.png | image | |
MD5:0D1A2B6C14E6351B1A92133297D565C5 | SHA256:5CB0D9BC99F4B17B9E8DE4CEE5E15C91D080B2E0F83B9FFECC8830DCA39C5ACA | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\opera_chi_tra.png | image | |
MD5:9BC154C90DF9BC76D58E182BD43809C9 | SHA256:2ABC487808A9C2F7D4C03D78D595F2A9D4FD61F1D3042F098E2D07096EF2E7CB | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\opera_eng.png | image | |
MD5:81354E9C2FD7345627769B3FE7170208 | SHA256:33D026DC50F812A41B83E0D7E5EB2B4C35D9A35E93C09B9729B8C1A67A32B8F6 | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\background.png | image | |
MD5:66F91F2B36927E1B51344BDA4B373B04 | SHA256:DAE5E3F303D3CAB68A7D920F081923BF89DD8FD1C58621C6BC3CAD8B880F1494 | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\opera_chi_sim.png | image | |
MD5:C7B6F609A1474B0CB8CF0FAF50A2285E | SHA256:1641E037E4E7C91270E4DC6359CE1D00E8A2B6BB31D143D764E221BDE5D02168 | |||
| 460 | PANDAFREEAV.exe | C:\Users\admin\AppData\Local\Temp\7zSCC1ECA71\res\opera_fre.png | image | |
MD5:B0C548A5529E5BB1C3AD451482547783 | SHA256:B819B6C483A3FF99CBF670008279EF15F7E718A376963AC8A092F3DDB88046AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
15
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | Stub.exe | GET | 200 | 40.69.210.172:80 | http://eventtrack.pandasecurity.com/track/install/details.html?ProductID=4252&Stub_Event=Start&_ei=FD8174B1-CD36-4718-9BE0-AF16DE8B9B4D&_es=1&_et=Stub&_lt=20220114210010 | IE | — | — | suspicious |
3652 | Stub.exe | GET | 200 | 40.69.210.172:80 | http://eventtrack.pandasecurity.com/track/install/details.html?Installation_Code=1034&Installation_End=ERROR&Stub_Event=End&_ei=DE61434F-0189-4DAB-9CC7-9DBAB4B1F3C3&_es=1&_et=Stub&_lt=20220114210010 | IE | — | — | suspicious |
860 | svchost.exe | HEAD | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=528231&clcid=0x409 | NL | — | — | whitelisted |
3652 | Stub.exe | GET | 200 | 40.69.210.172:80 | http://eventtrack.pandasecurity.com/track/install/details.html?Installation_Code=1035&Installation_End=ERROR&Stub_Event=End&_ei=CEC550F8-8E3D-4207-A21F-DB2F6AC746DB&_es=1&_et=Stub&_lt=20220114210010 | IE | — | — | suspicious |
860 | svchost.exe | HEAD | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=249117&clcid=0x409 | NL | — | — | whitelisted |
860 | svchost.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=528231&clcid=0x409 | NL | — | — | whitelisted |
860 | svchost.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=249117&clcid=0x409 | NL | — | — | whitelisted |
3652 | Stub.exe | GET | 301 | 104.111.243.23:80 | http://www.pandasecurity.com/Vg5sw34C5j | NL | text | 105 b | unknown |
2368 | Setup.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | US | der | 1.05 Kb | whitelisted |
2368 | Setup.exe | GET | 200 | 92.123.194.163:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 519 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3652 | Stub.exe | 92.122.255.148:443 | download.microsoft.com | GTT Communications Inc. | — | malicious |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3652 | Stub.exe | 41.63.96.0:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | ZA | suspicious |
3652 | Stub.exe | 92.122.255.148:80 | download.microsoft.com | GTT Communications Inc. | — | malicious |
860 | svchost.exe | 104.102.28.147:443 | download.microsoft.com | Akamai Technologies, Inc. | US | malicious |
860 | svchost.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3652 | Stub.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2368 | Setup.exe | 92.123.194.154:80 | crl.microsoft.com | Akamai International B.V. | — | suspicious |
3652 | Stub.exe | 2.16.107.106:80 | acs.pandasoftware.com | Akamai International B.V. | — | suspicious |
860 | svchost.exe | 104.89.38.104:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acs.pandasoftware.com |
| whitelisted |
eventtrack.pandasecurity.com |
| unknown |
www.pandasecurity.com |
| unknown |
download.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3652 | Stub.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3652 | Stub.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |