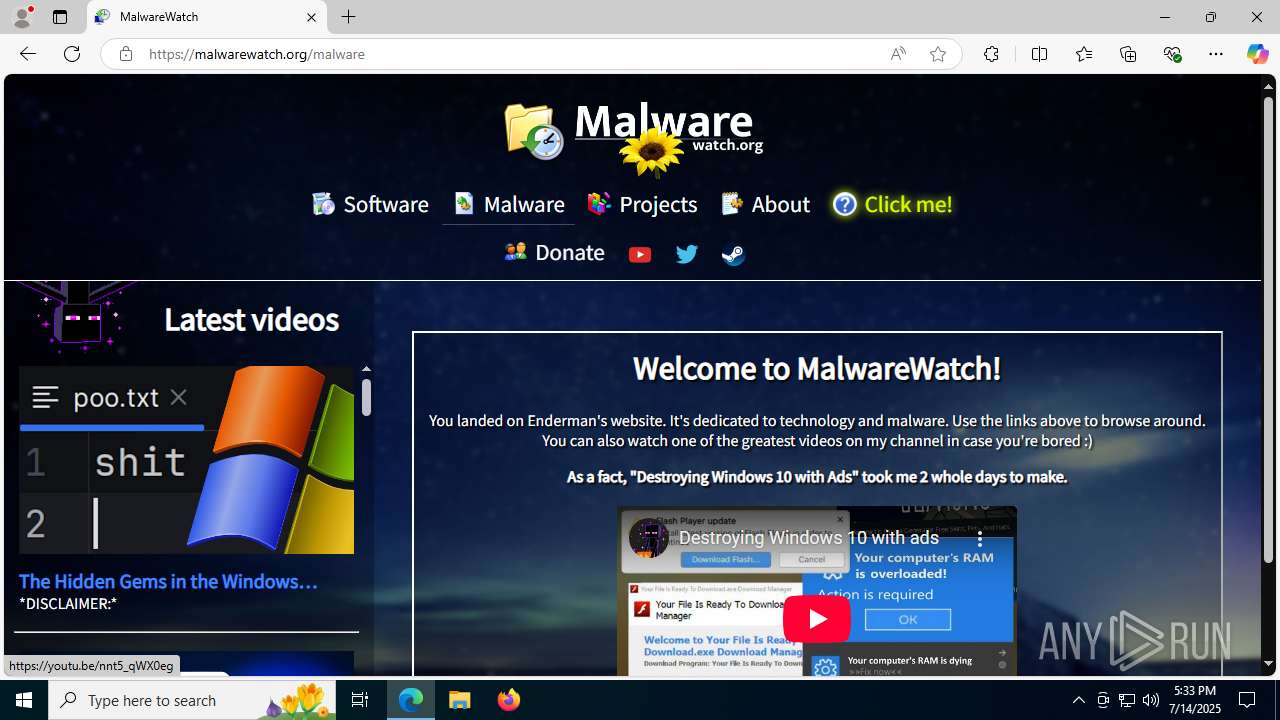
| URL: | enderman.ch |
| Full analysis: | https://app.any.run/tasks/dcbddf43-4811-45a2-a3c1-fb18a3150f5b |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 17:33:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BFFAD2DF753F349825DB8F60F0029AE3 |
| SHA1: | F05F2A2F4DA354DC2CF91D4C64B0B9C276F5FBD7 |
| SHA256: | 4CFA948C8CE7B47B826EBEC296DBFD880647B2BC17E758AB759E6F07D2D77929 |
| SSDEEP: | 3:u2XIie:uwVe |
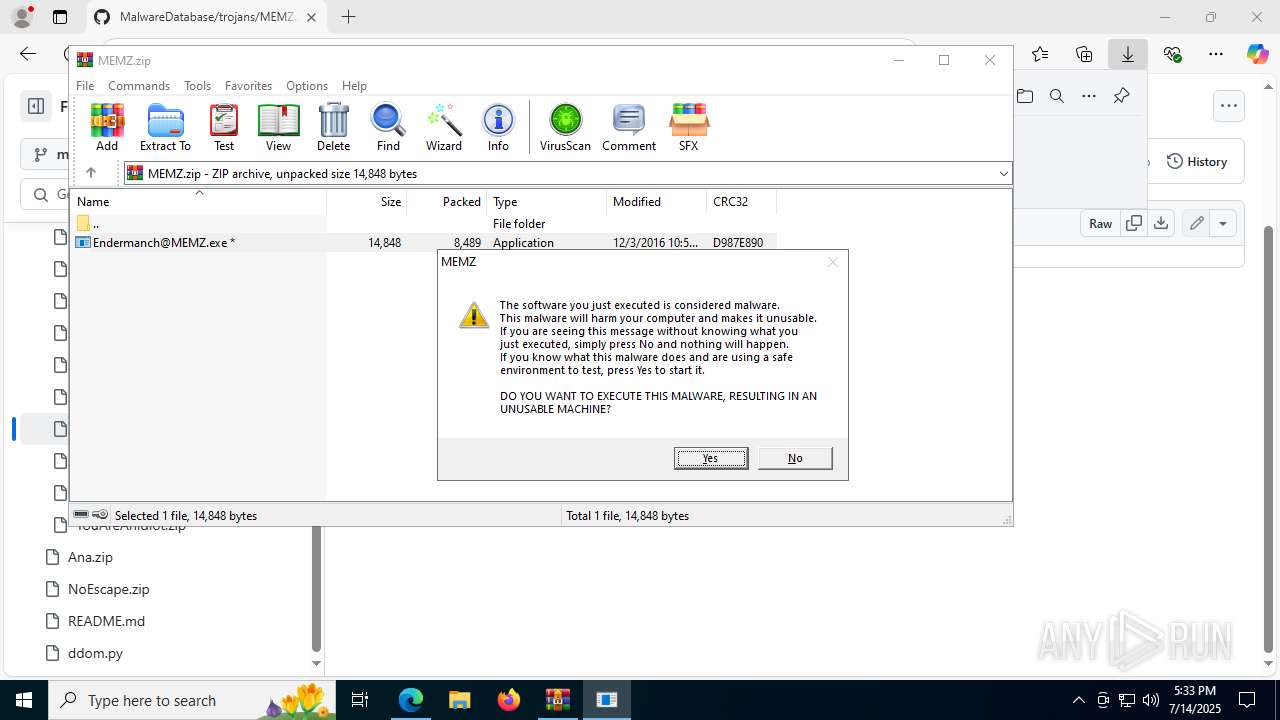
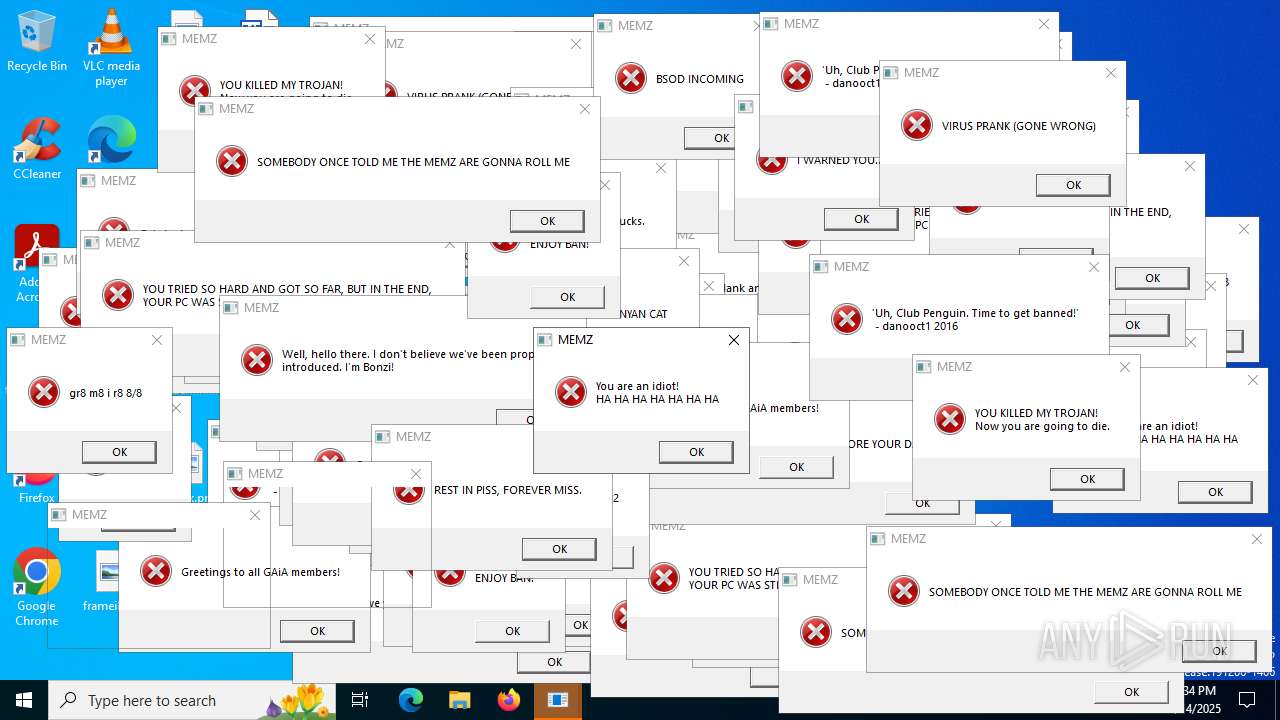
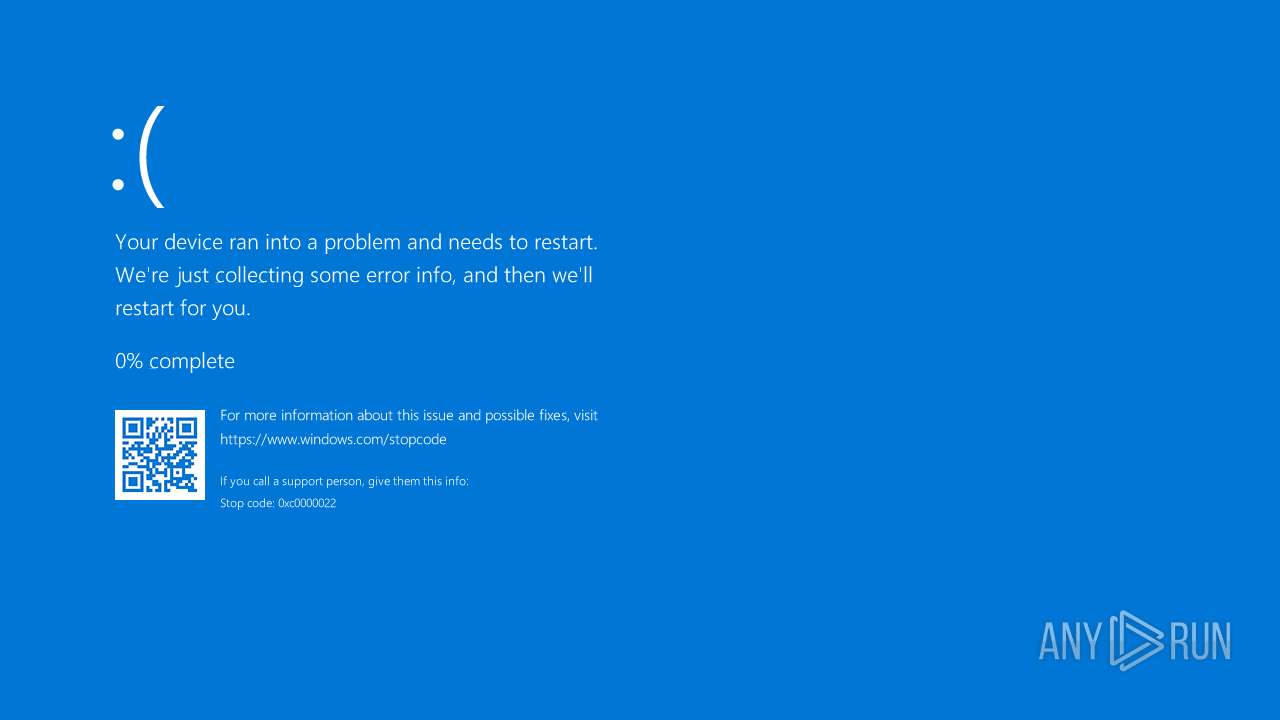
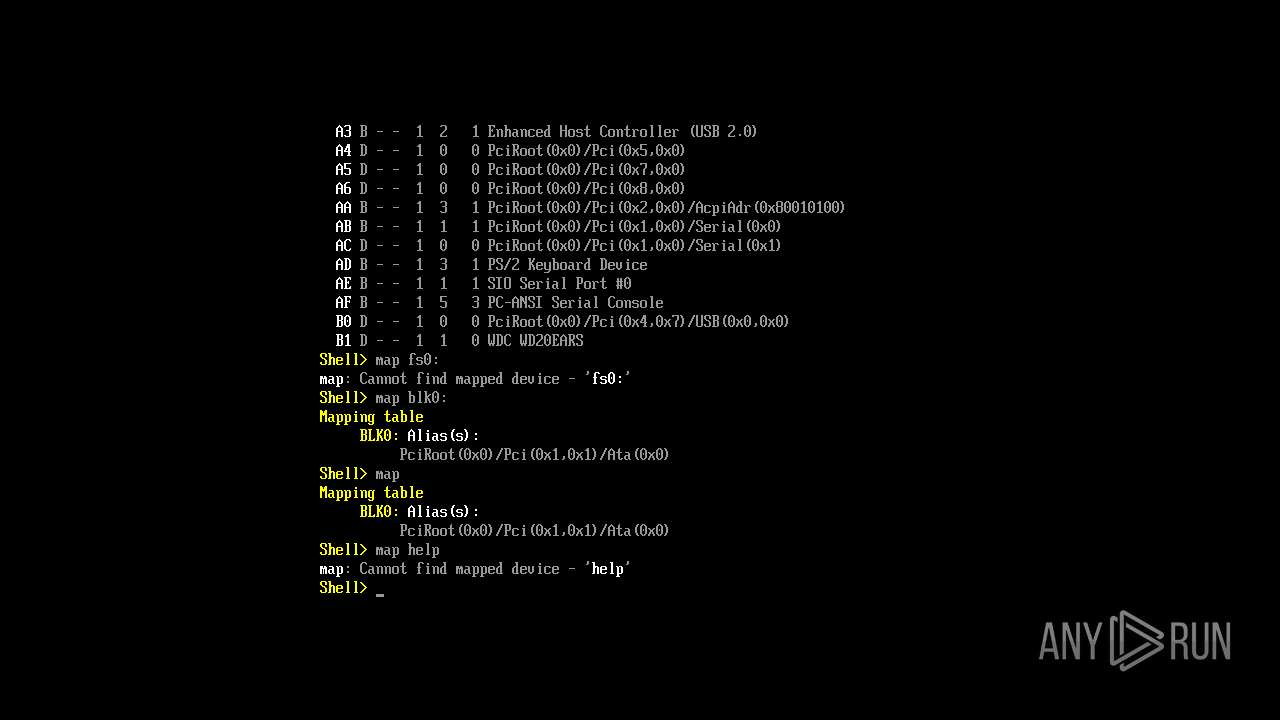
MALICIOUS
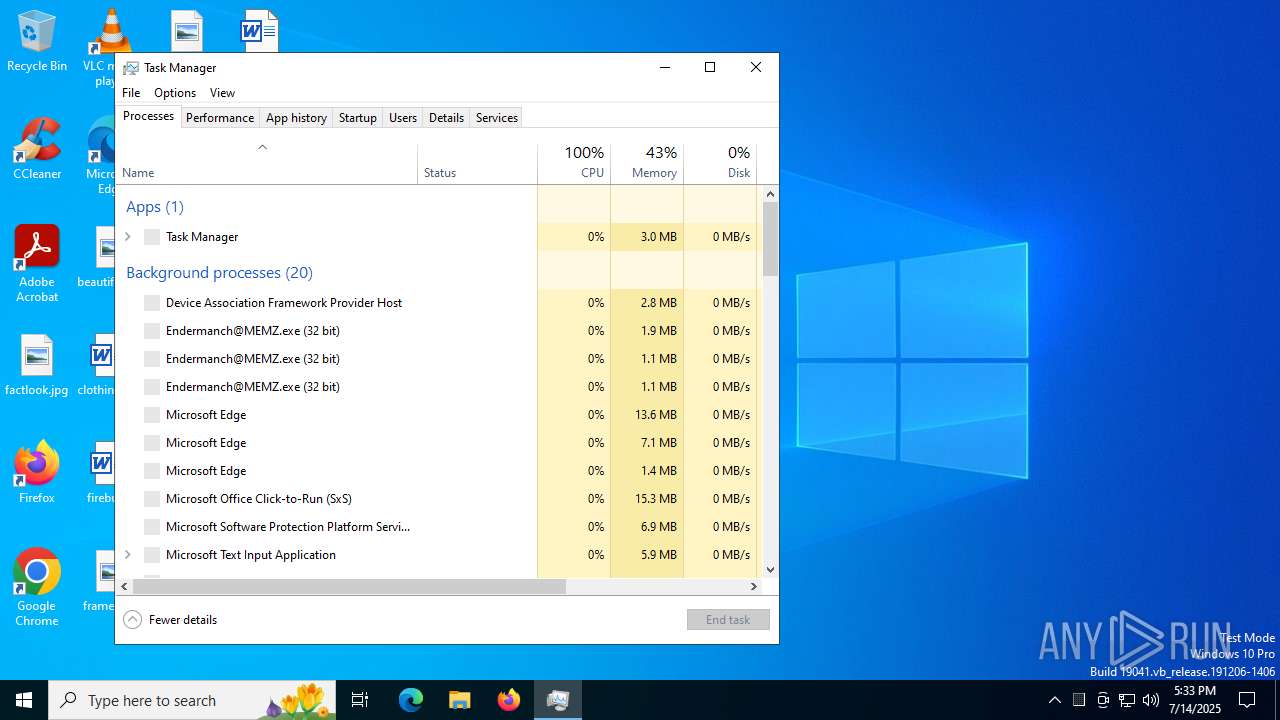
MEMZ has been detected (YARA)
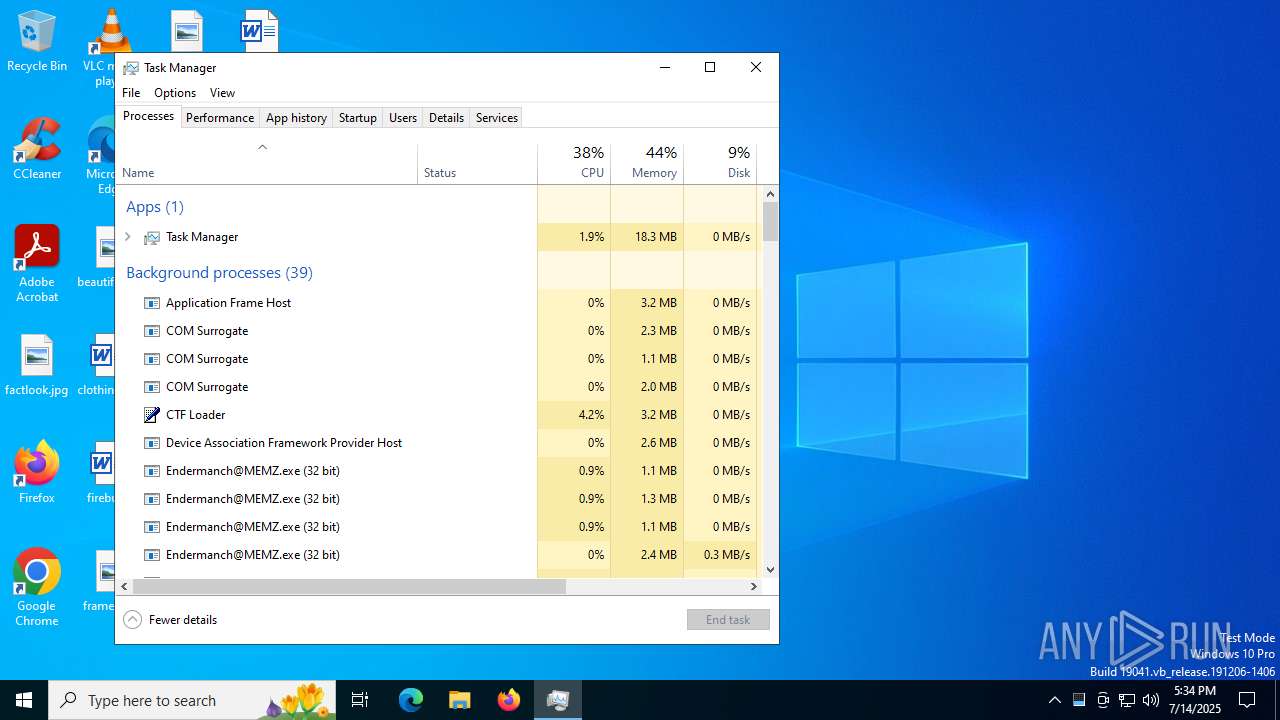
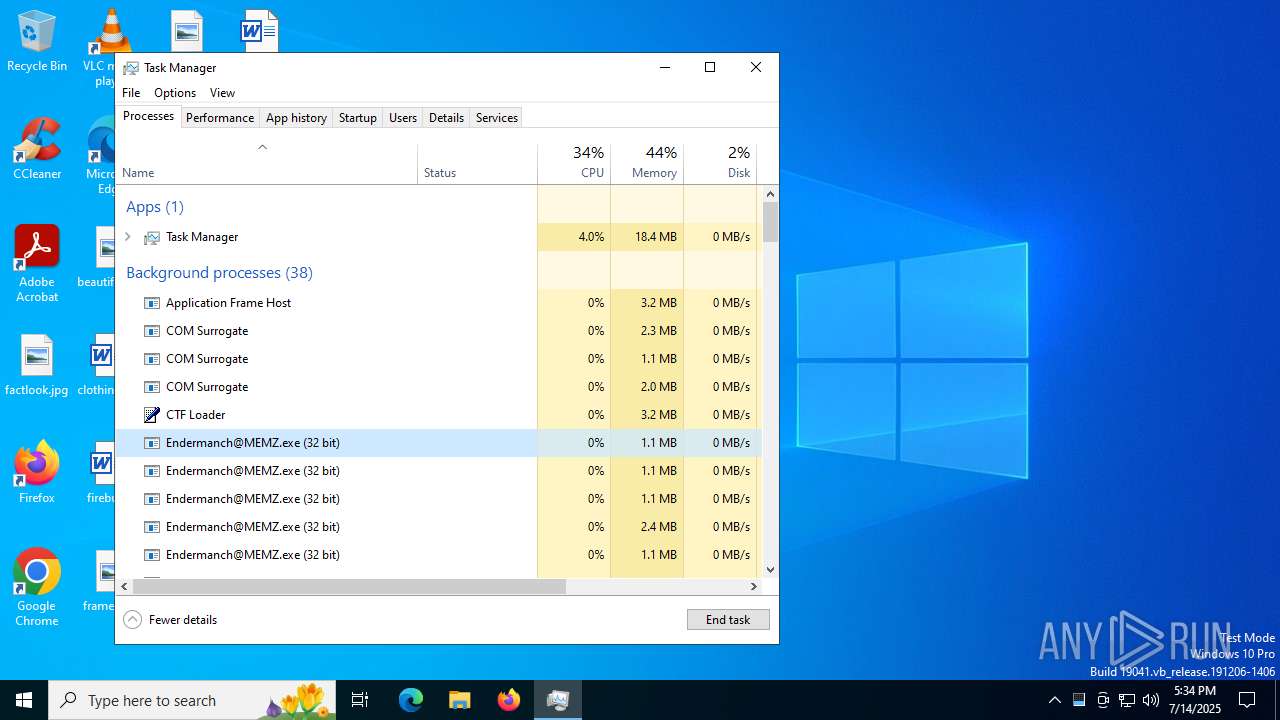
- Endermanch@MEMZ.exe (PID: 4828)
- Endermanch@MEMZ.exe (PID: 6368)
- Endermanch@MEMZ.exe (PID: 1028)
- Endermanch@MEMZ.exe (PID: 640)
- Endermanch@MEMZ.exe (PID: 1164)
- Endermanch@MEMZ.exe (PID: 3952)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7880)
- Endermanch@MEMZ.exe (PID: 5920)
- Endermanch@MEMZ.exe (PID: 6368)
Application launched itself
- Endermanch@MEMZ.exe (PID: 5920)
Creates file in the systems drive root
- Endermanch@MEMZ.exe (PID: 6368)
- notepad.exe (PID: 4804)
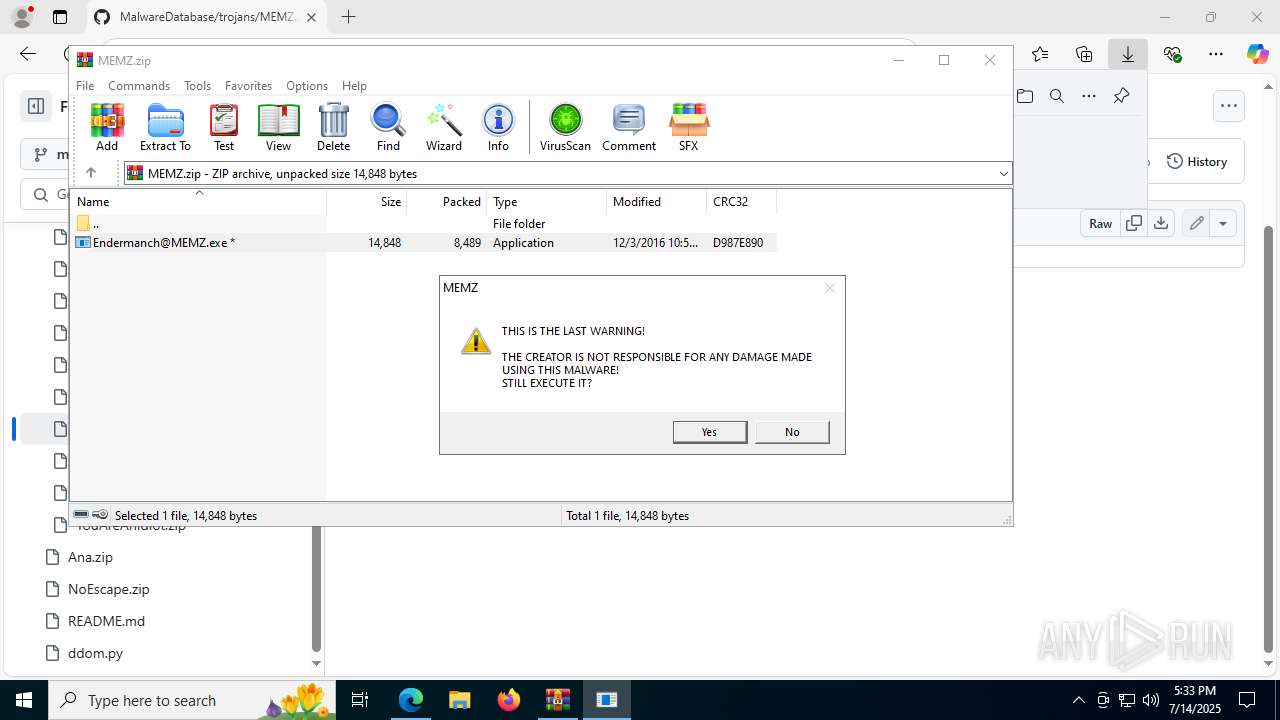
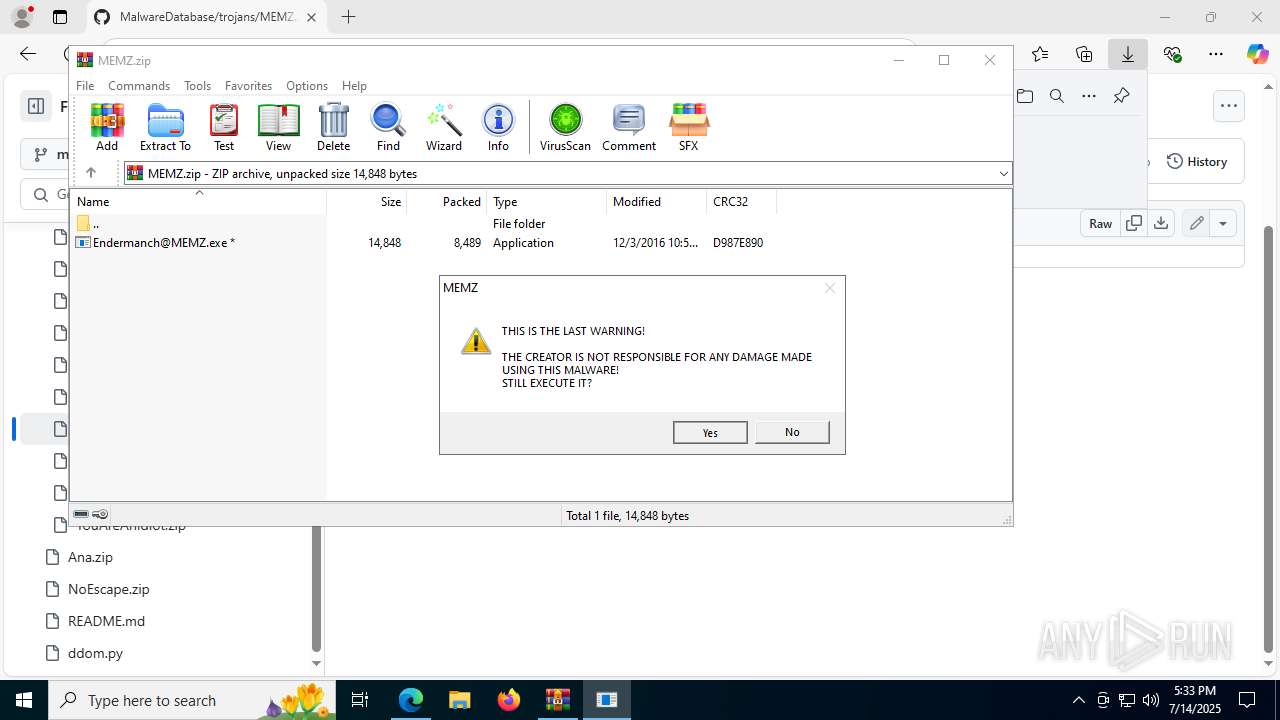
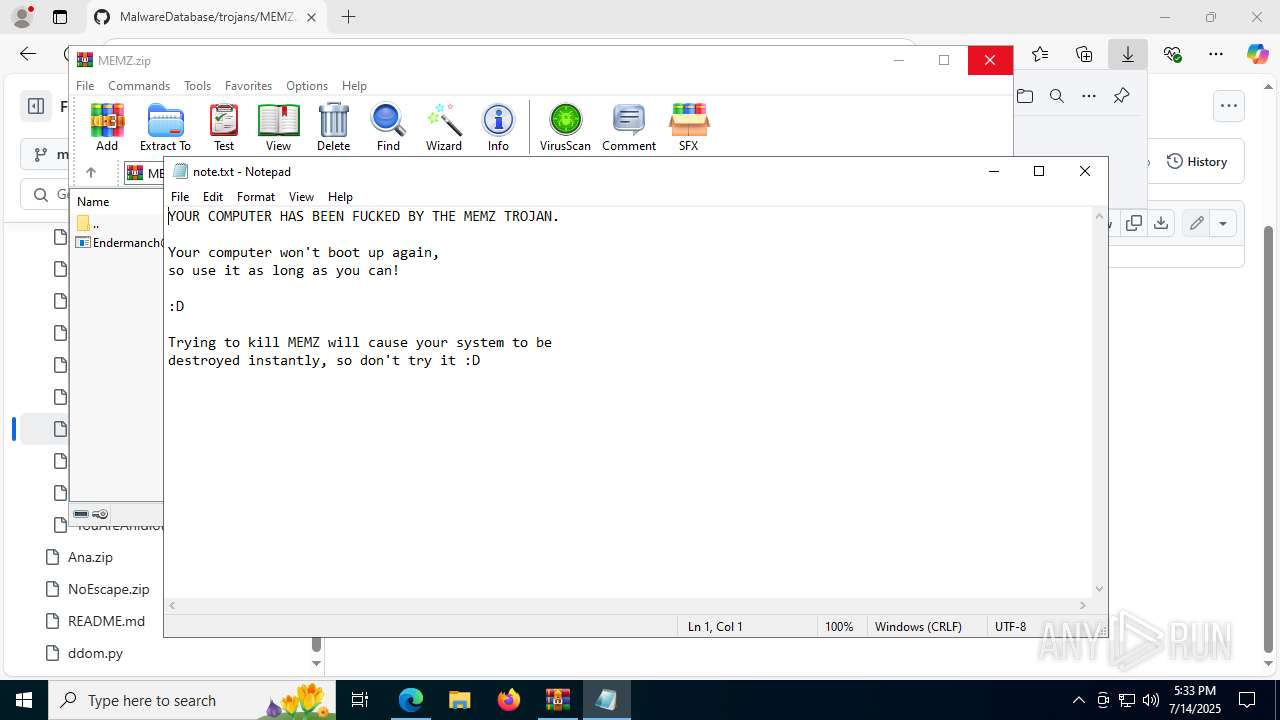
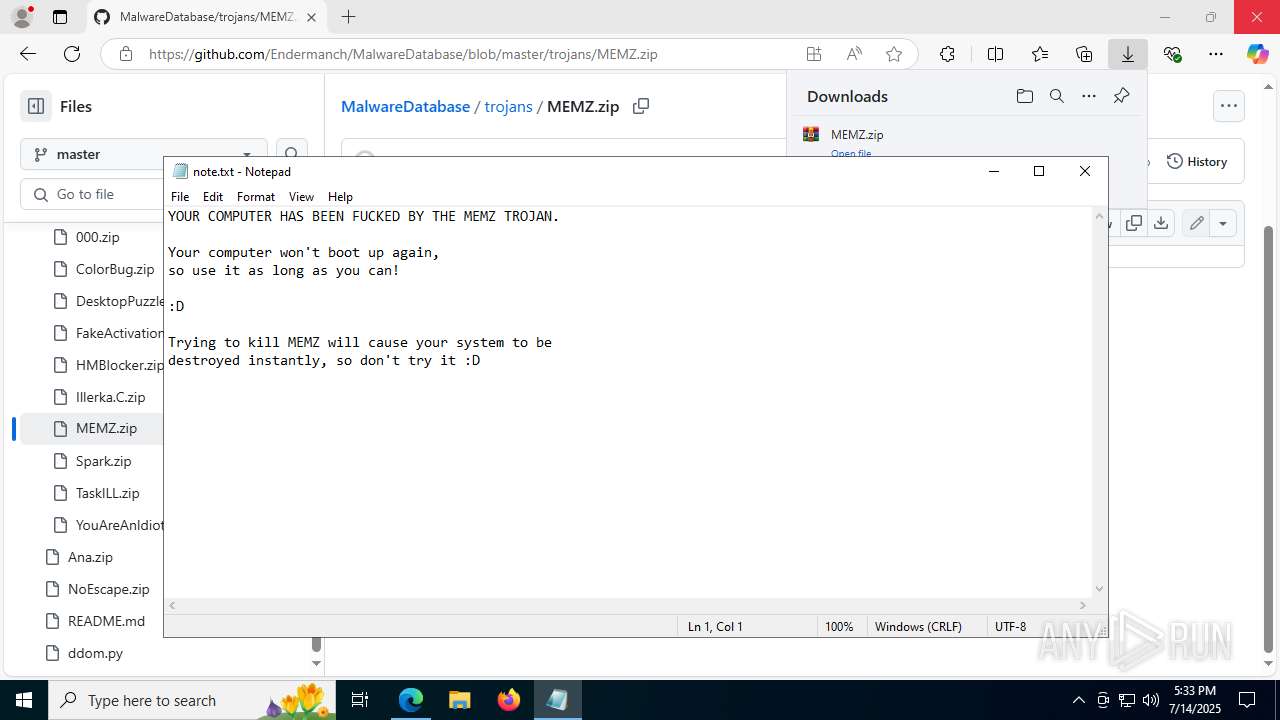
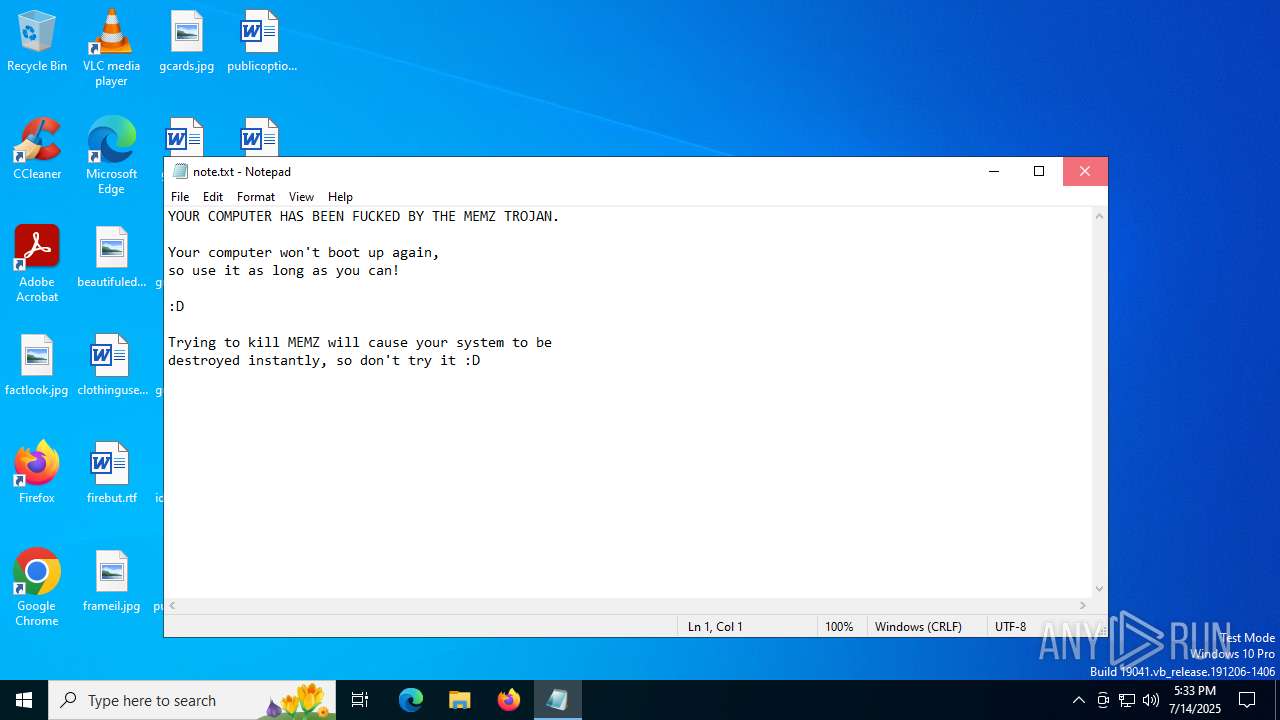
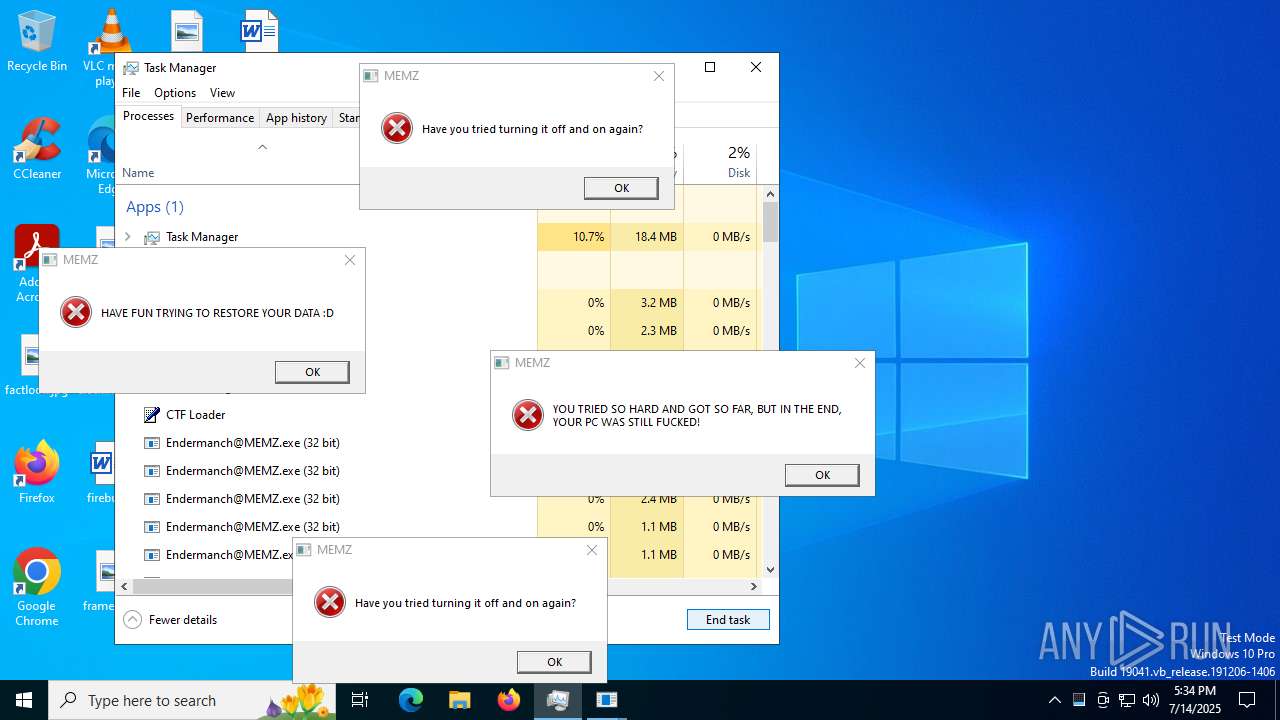
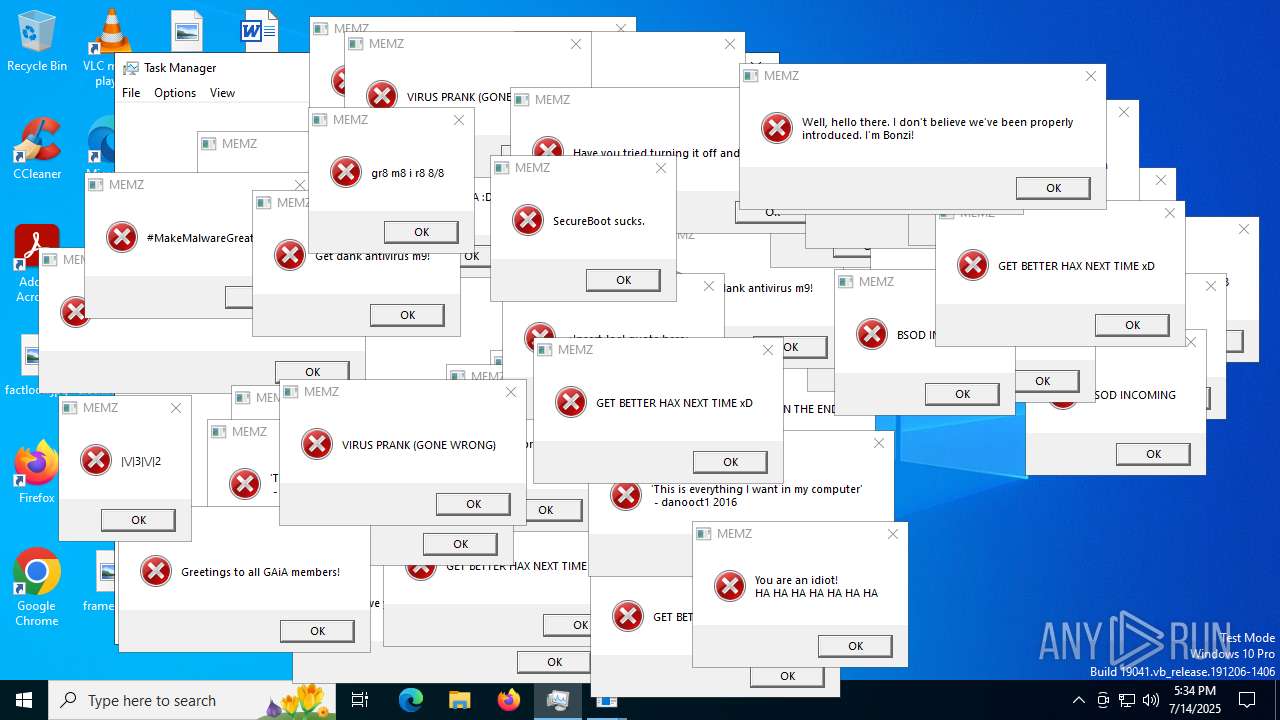
Start notepad (likely ransomware note)
- Endermanch@MEMZ.exe (PID: 6368)
There is functionality for taking screenshot (YARA)
- Endermanch@MEMZ.exe (PID: 4828)
- Endermanch@MEMZ.exe (PID: 3952)
- Endermanch@MEMZ.exe (PID: 6368)
- Endermanch@MEMZ.exe (PID: 1028)
- Endermanch@MEMZ.exe (PID: 1164)
- Endermanch@MEMZ.exe (PID: 640)
INFO
Application launched itself
- msedge.exe (PID: 1356)
- msedge.exe (PID: 7704)
Reads Environment values
- identity_helper.exe (PID: 4020)
- identity_helper.exe (PID: 6812)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1356)
Checks supported languages
- identity_helper.exe (PID: 4020)
- Endermanch@MEMZ.exe (PID: 5920)
- Endermanch@MEMZ.exe (PID: 4828)
- Endermanch@MEMZ.exe (PID: 1164)
- Endermanch@MEMZ.exe (PID: 3952)
- Endermanch@MEMZ.exe (PID: 640)
- Endermanch@MEMZ.exe (PID: 1028)
- Endermanch@MEMZ.exe (PID: 6368)
- identity_helper.exe (PID: 6812)
Reads the computer name
- identity_helper.exe (PID: 4020)
- Endermanch@MEMZ.exe (PID: 5920)
- Endermanch@MEMZ.exe (PID: 6368)
- identity_helper.exe (PID: 6812)
- Endermanch@MEMZ.exe (PID: 1028)
- Endermanch@MEMZ.exe (PID: 4828)
- Endermanch@MEMZ.exe (PID: 640)
- Endermanch@MEMZ.exe (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7880)
Process checks computer location settings
- Endermanch@MEMZ.exe (PID: 5920)
- Endermanch@MEMZ.exe (PID: 6368)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4804)
- Taskmgr.exe (PID: 7928)
- mmc.exe (PID: 7472)
- mmc.exe (PID: 7484)
Manual execution by a user
- Taskmgr.exe (PID: 7652)
- Taskmgr.exe (PID: 7928)
Reads the machine GUID from the registry
- Endermanch@MEMZ.exe (PID: 1028)
- Endermanch@MEMZ.exe (PID: 6368)
- Endermanch@MEMZ.exe (PID: 1164)
- Endermanch@MEMZ.exe (PID: 640)
- Endermanch@MEMZ.exe (PID: 4828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
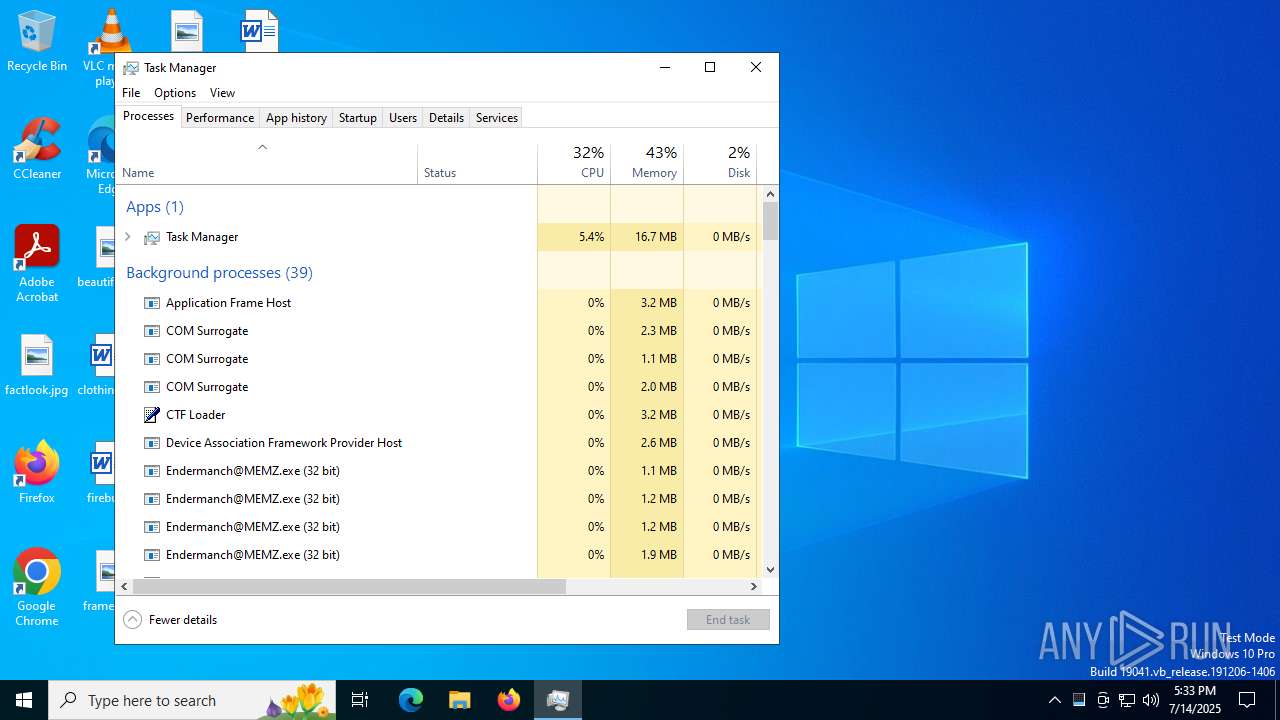
Total processes
192
Monitored processes
53
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe | Endermanch@MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43c2f208,0x7ffc43c2f214,0x7ffc43c2f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe | Endermanch@MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXb7880.22016\Endermanch@MEMZ.exe | Endermanch@MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "enderman.ch" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3668,i,6080757057467169692,4493580294328186001,262144 --variations-seed-version --mojo-platform-channel-handle=3768 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2436,i,1661260781233513629,3801687493142231575,262144 --variations-seed-version --mojo-platform-channel-handle=2428 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2788,i,1661260781233513629,3801687493142231575,262144 --variations-seed-version --mojo-platform-channel-handle=2808 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2980 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --always-read-main-dll --field-trial-handle=5088,i,1661260781233513629,3801687493142231575,262144 --variations-seed-version --mojo-platform-channel-handle=5128 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2764,i,6080757057467169692,4493580294328186001,262144 --variations-seed-version --mojo-platform-channel-handle=2644 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
12 395
Read events
12 323
Write events
70
Delete events
2
Modification events
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 24421D567D982F00 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {62132564-C45E-4435-9E35-4FF5FC32A0DF} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AEB7C150-615E-4AF7-B4E4-8A4EEEAE1C31} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {76346B48-B6BC-4D14-B08F-983328AC6F9E} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E9A534C6-DB4B-4DB5-AB03-8D9B4EE834BE} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B33D543A-9475-4695-A34A-EC5C2E151351} | |||
Executable files
1
Suspicious files
282
Text files
125
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF175544.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF175553.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF175553.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF175563.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF175563.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
118
DNS requests
119
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3752 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:S4WpC10J2I-kj99C7zBxkT2PNdDFcuibzsDUkLIB7j4&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4916 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3752 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3752 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3752 | msedge.exe | 104.21.28.75:443 | enderman.ch | CLOUDFLARENET | — | unknown |
3752 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3752 | msedge.exe | 92.123.104.53:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
enderman.ch |
| unknown |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.iconify.design |
| unknown |
api.unisvg.com |
| unknown |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
mmc.exe | |
mmc.exe | "C:\Windows\System32\devmgmt.msc" "C:\Windows\System32\devmgmt.msc" |