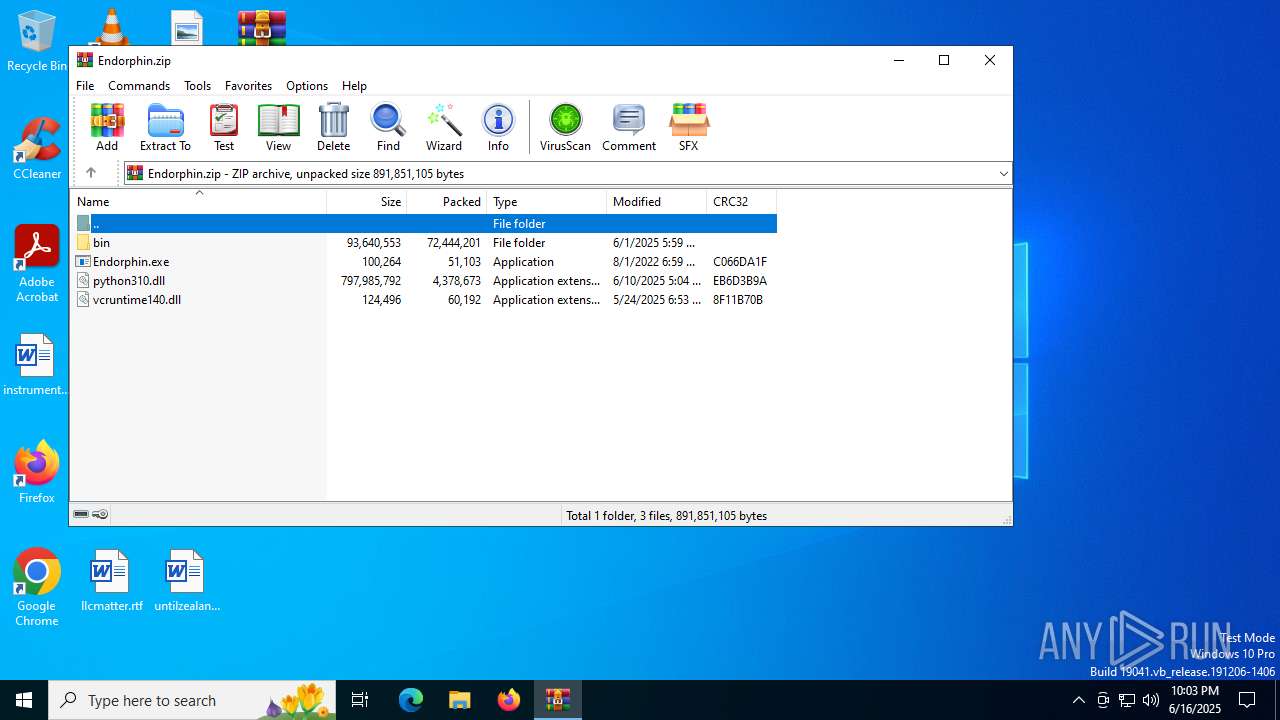
| File name: | Endorphin.zip |
| Full analysis: | https://app.any.run/tasks/c8794b17-8834-4353-9557-5ca12becf553 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2025, 22:02:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3980372D95941C723A2620BA0375F844 |
| SHA1: | D5F510E7191F4BC78AA7E1437E4F54231A754779 |
| SHA256: | 4CA7A0B6900931784C1CC59FBB7E433500E5C53FE14FBBDAC1CA861B66E347A1 |
| SSDEEP: | 786432:vftLxklXN9LElc/fHPSC+LTwWPlF2Uaze9rq3AbdJZiFWF6Ju:XtlkWlcD+IWPL/azaq3AbdJwWFIu |
MALICIOUS
No malicious indicators.SUSPICIOUS
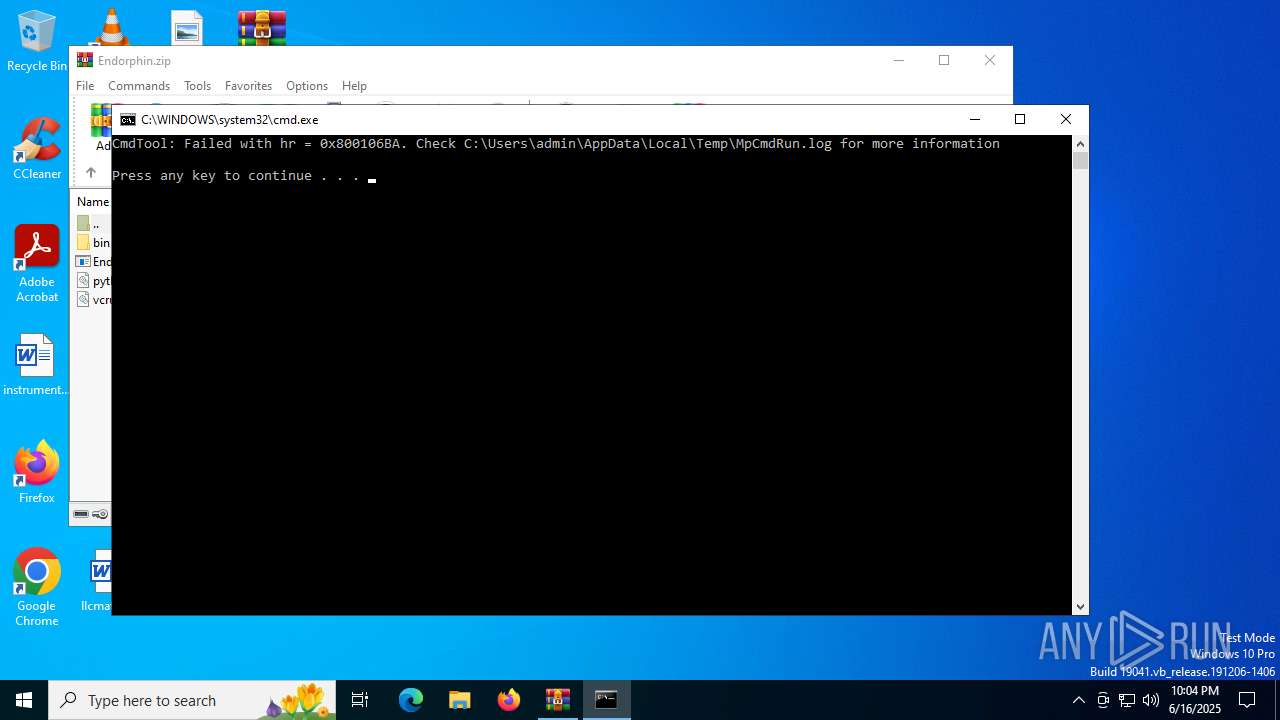
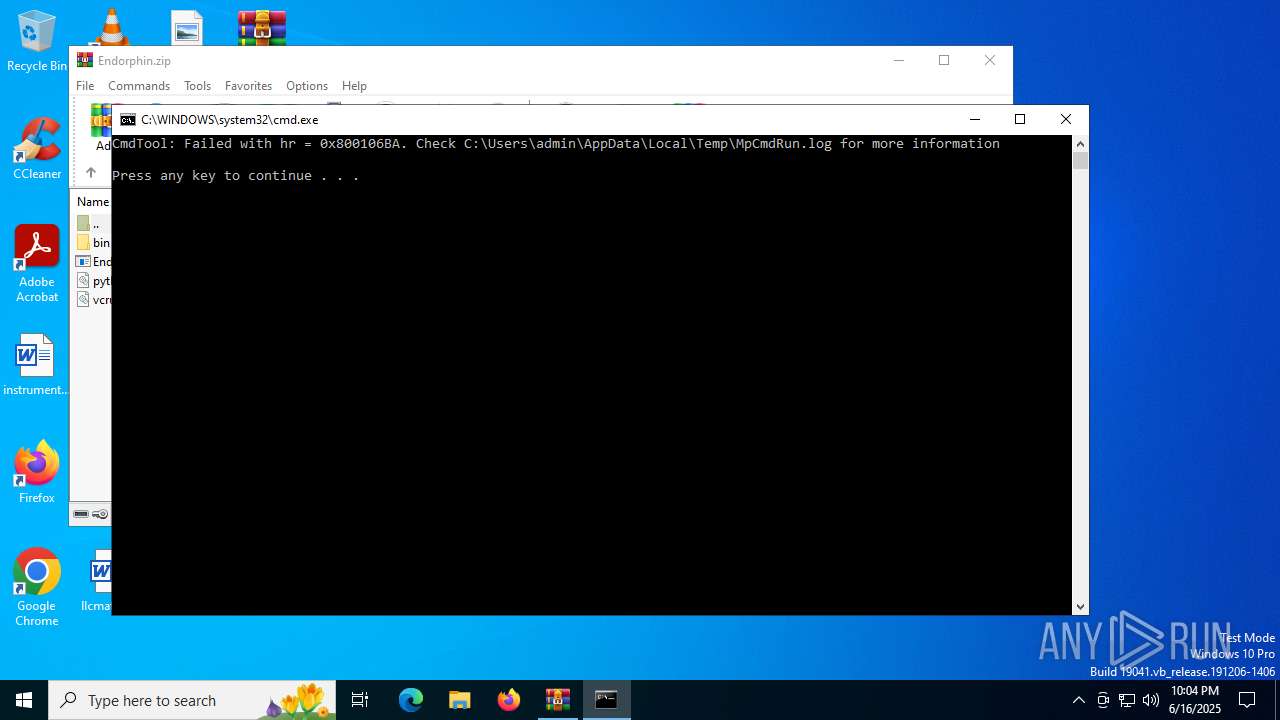
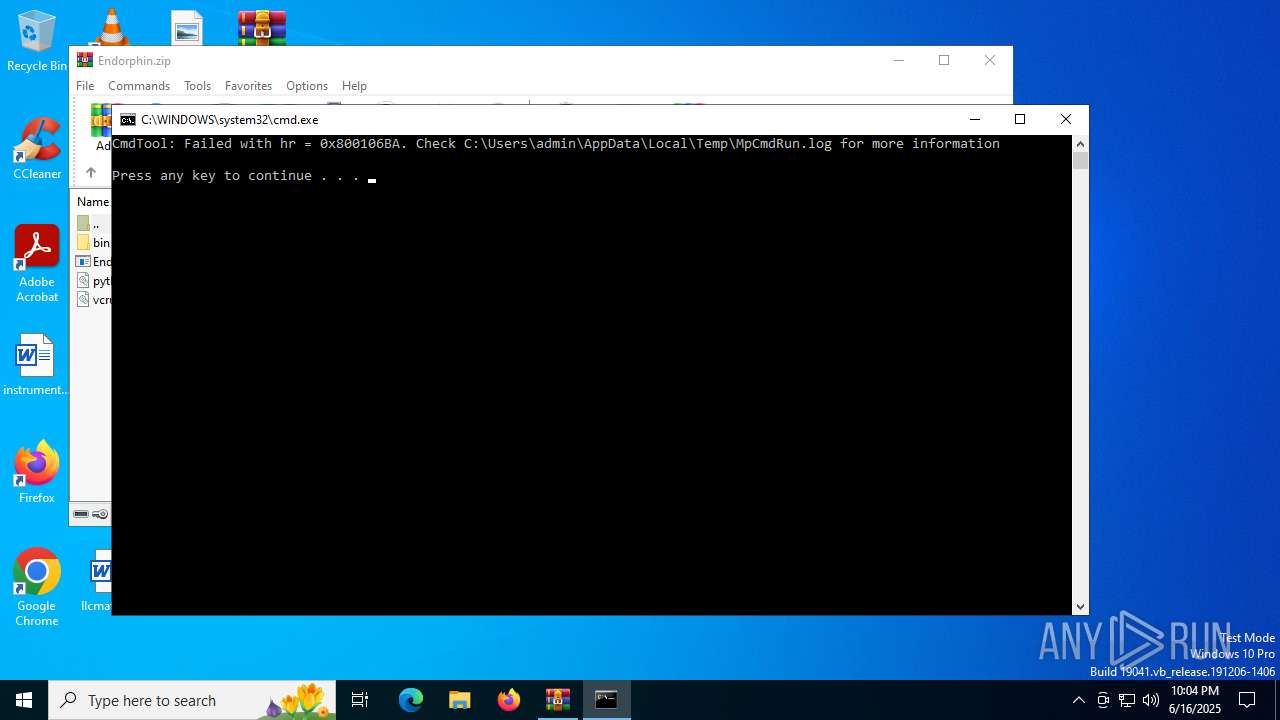
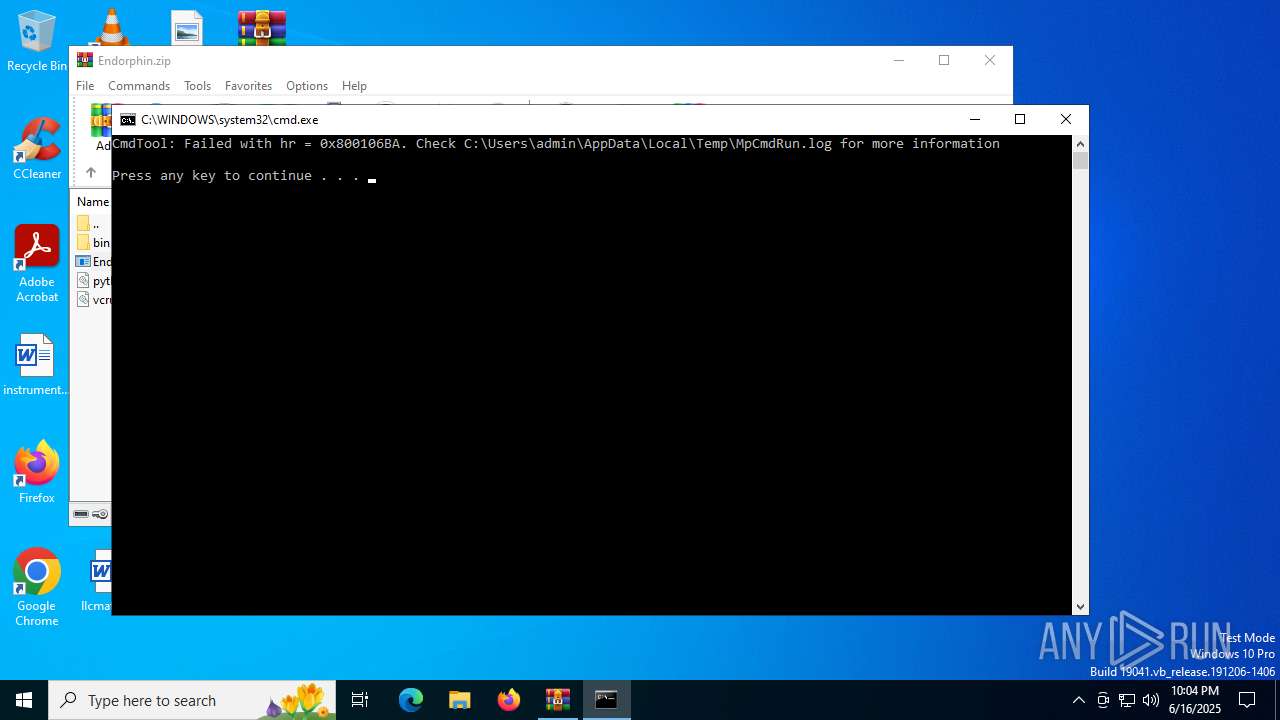
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6128)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6128)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6128)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6128)
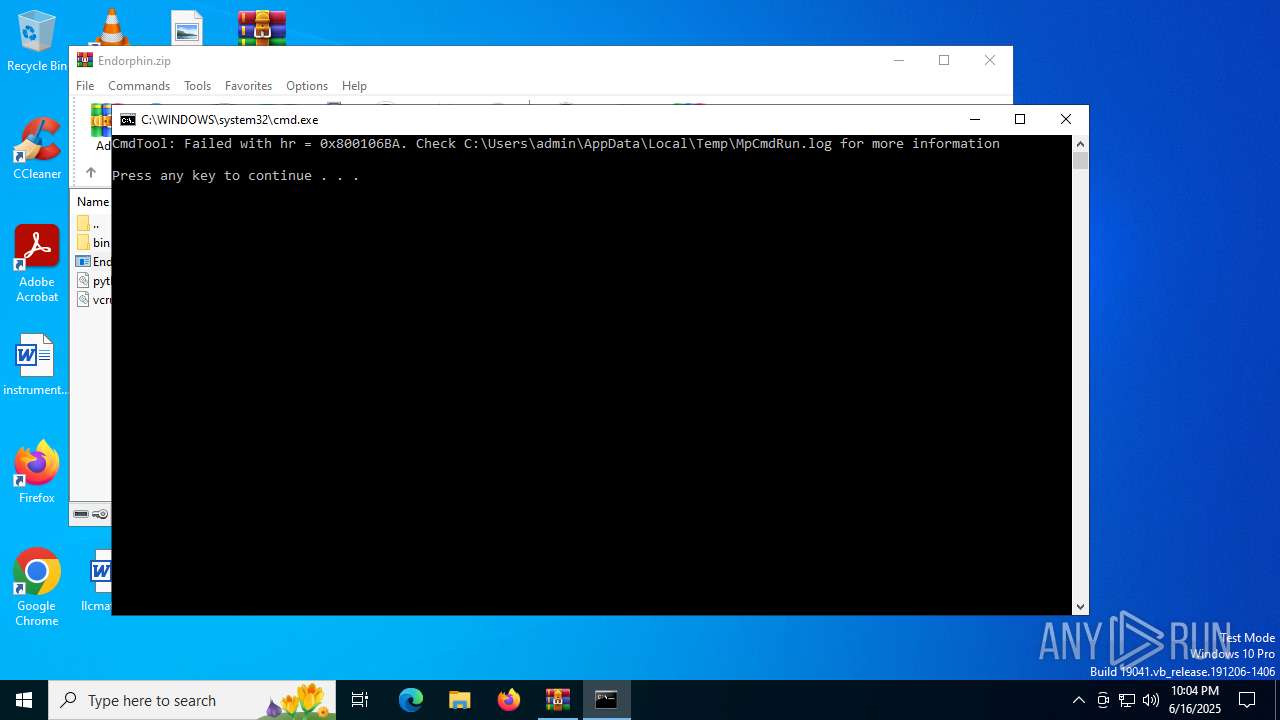
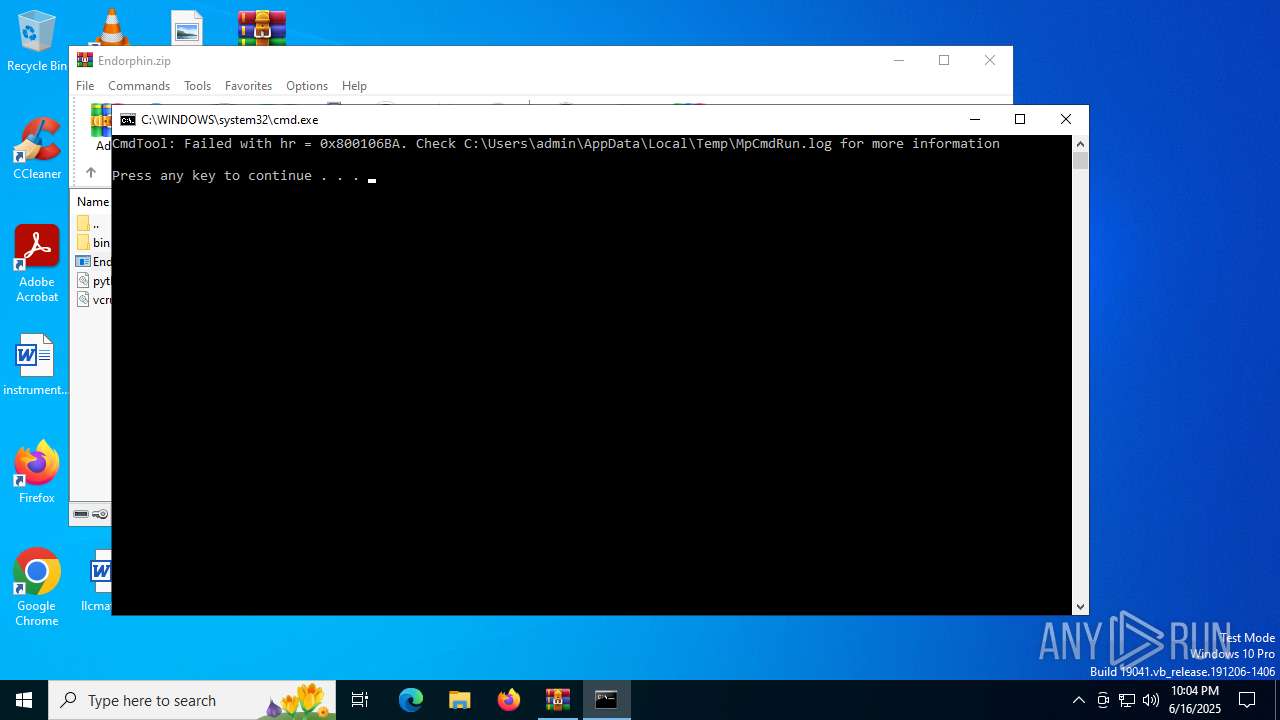
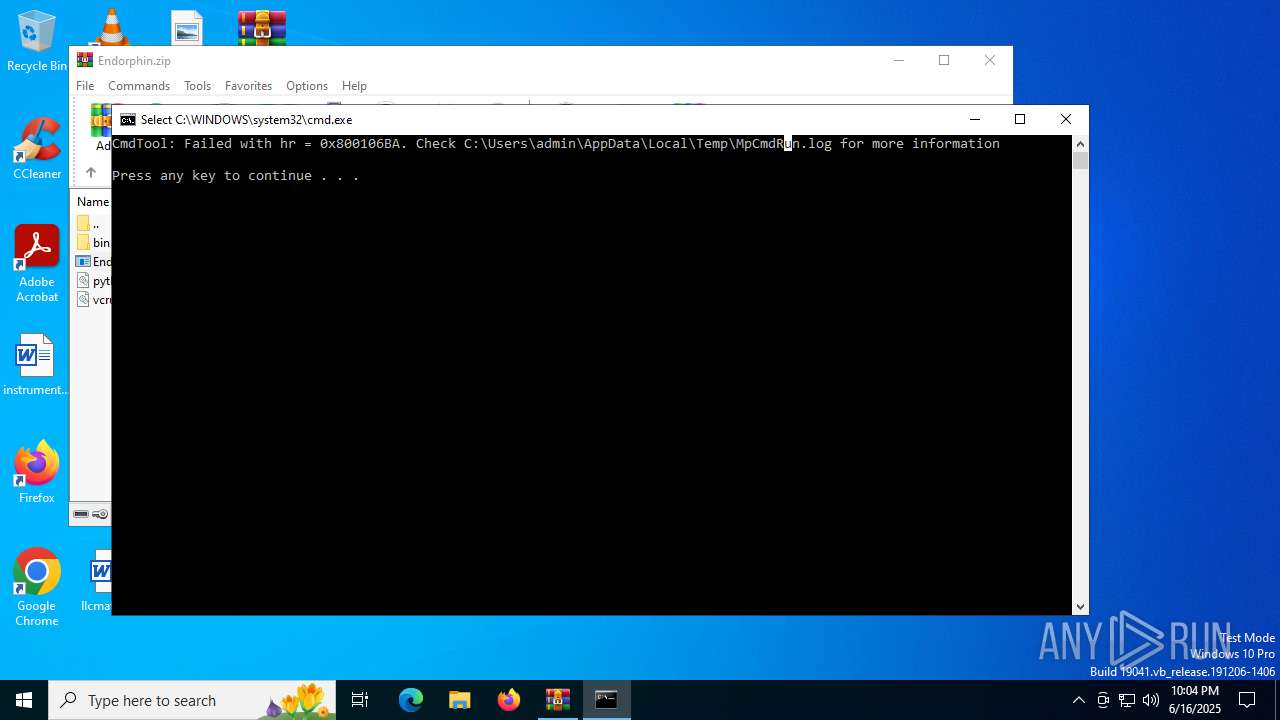
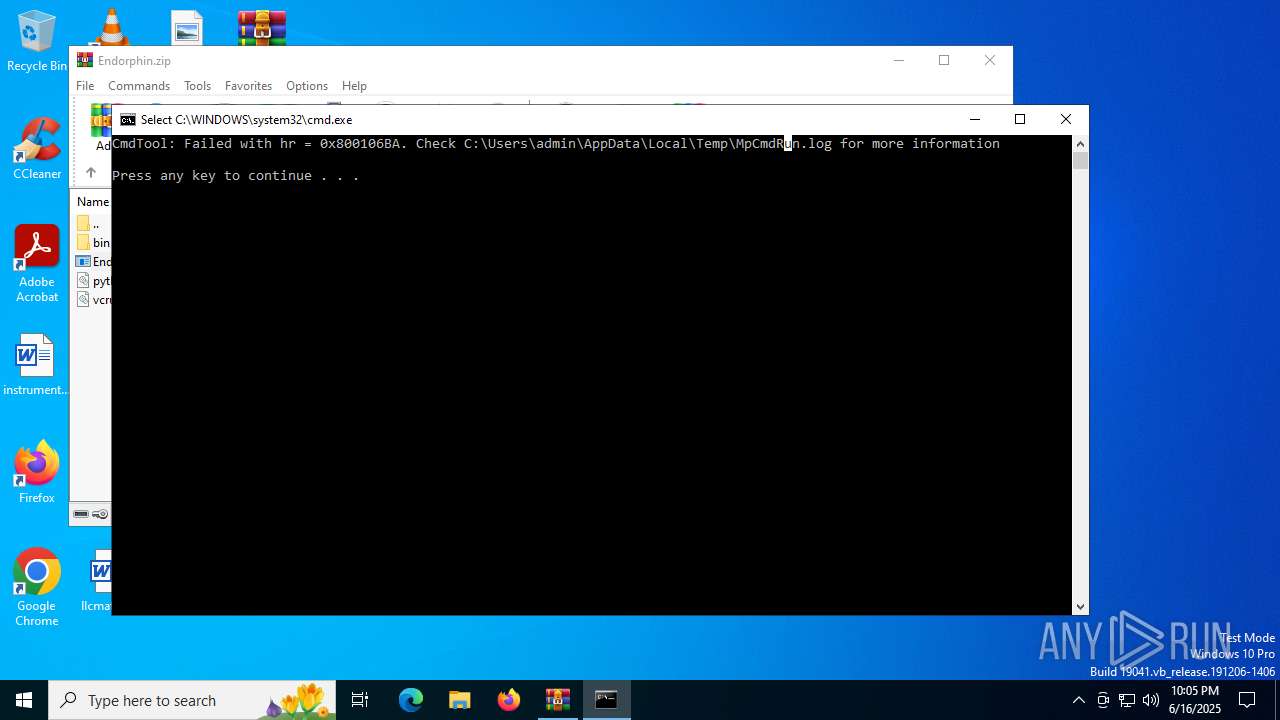
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6128)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6128)
Reads the computer name
- MpCmdRun.exe (PID: 2216)
Checks supported languages
- MpCmdRun.exe (PID: 2216)
The sample compiled with english language support
- WinRAR.exe (PID: 6128)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2216)
Reads the software policy settings
- slui.exe (PID: 3636)
Checks proxy server information
- slui.exe (PID: 3636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:08:01 13:59:58 |
| ZipCRC: | 0xc066da1f |
| ZipCompressedSize: | 51103 |
| ZipUncompressedSize: | 100264 |
| ZipFileName: | Endorphin.exe |
Total processes
132
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2216 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3636 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Rar$Scan58773.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6128 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Endorphin.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 093
Read events
5 084
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Endorphin.zip | |||
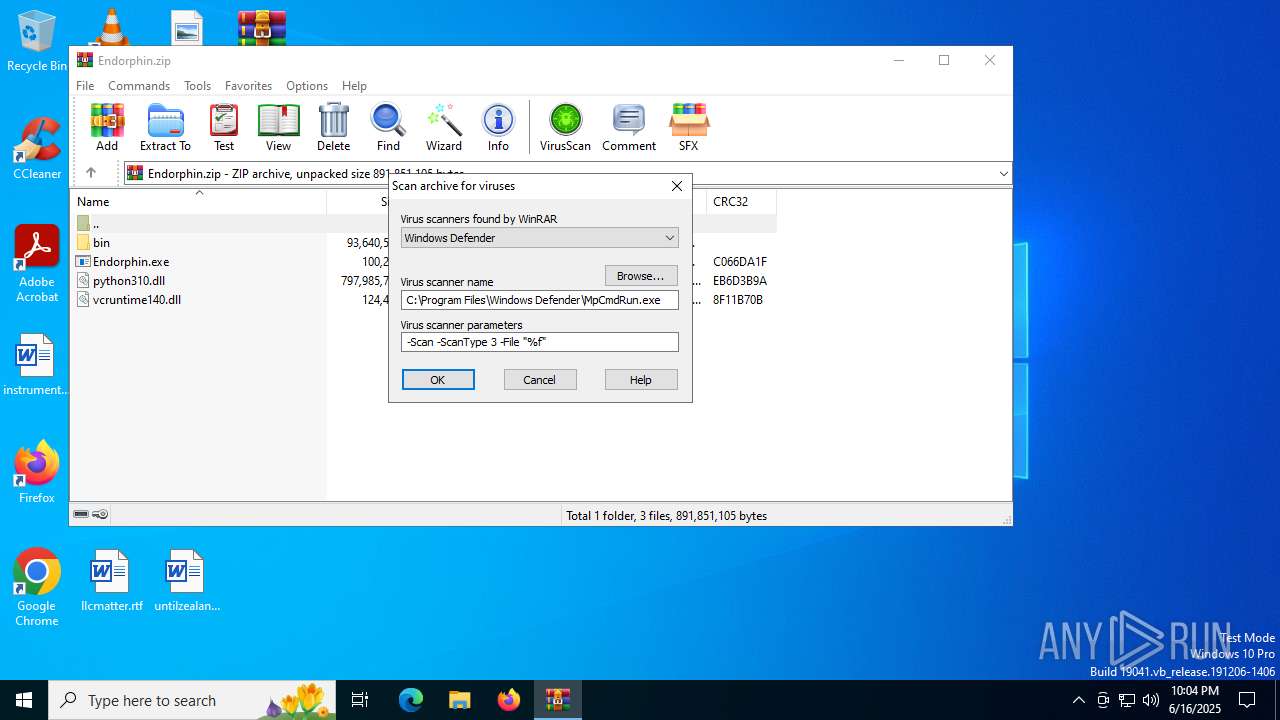
| (PID) Process: | (6128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
133
Suspicious files
10
Text files
274
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\python310.dll | — | |
MD5:— | SHA256:— | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\api-ms-win-crt-stdio-l1-1-0.dll | executable | |
MD5:306608A878089CB38602AF693BA0485B | SHA256:3B59A50457F6B6EAA6D35E42722D4562E88BCD716BAE113BE1271EAD0FEB7AF3 | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:9151E83B4FDFA88353B7A97AE7792678 | SHA256:6C0E0D22B65329F4948FCF36C8048A54CCCCBF6C05B330B2C1A686F3E686EED0 | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\Endorphin.exe | executable | |
MD5:7AA94603BE1F83C51661DF24C0F88EC3 | SHA256:CB893F43012C270C23043563282E012F2552F7C2996F8951CB5672B197511BAB | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\java-runtime-gamma\windows\de.qm | binary | |
MD5:AFABAFB8D5375FD28D5BDEFE543541B8 | SHA256:47D9566871C51C9D9DAA1FDED81A649376B30EAB2AF63D9C1687814D7DF4A8DD | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\api-ms-win-crt-locale-l1-1-0.dll | executable | |
MD5:EBC168D7D3EA7C6192935359B6327627 | SHA256:C048A3D7AB951DCE1D6D3F5F497B50353F640A1787C6C65677A13C55C8E99983 | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\java-runtime-gamma\dsengine.dll | executable | |
MD5:EB8F0AE9D91BA8F6CF4B7001B071727E | SHA256:4F037A4378C5C507E3330C6A18874E4600E5EABA8FD2887B61FBEEB6CA4B64C7 | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\java-runtime-gamma\000129.ldb | binary | |
MD5:A5AC95FD722C2B84322F3CB51716A95F | SHA256:F916A657CDB5ABEF575E399E50BE48D14737B23970F9AEBCA5A356E6A45CE1A1 | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\java-runtime-gamma\windows\java-runtime-gamma\bin\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:2A8065DC6E6E60FB90B4B3F9E6BA7288 | SHA256:55E5F10D0DD9C85FF1C6DC7798E46B3A4422FB7EBC583BB00D06A7DF2494397B | |||
| 6128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6128.25868\Endorphin.zip\bin\java-runtime-gamma\windows\java-runtime-gamma\bin\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:ECDD006AAE56427C3555740F1ABFA8D6 | SHA256:13BC8B3F90DA149030897B8F9F08D71E5D1561E3AE604472A82F58DAB2B103F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1508 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1508 | RUXIMICS.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1508 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1508 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 104.85.1.163:80 | www.microsoft.com | AKAMAI-AS | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |