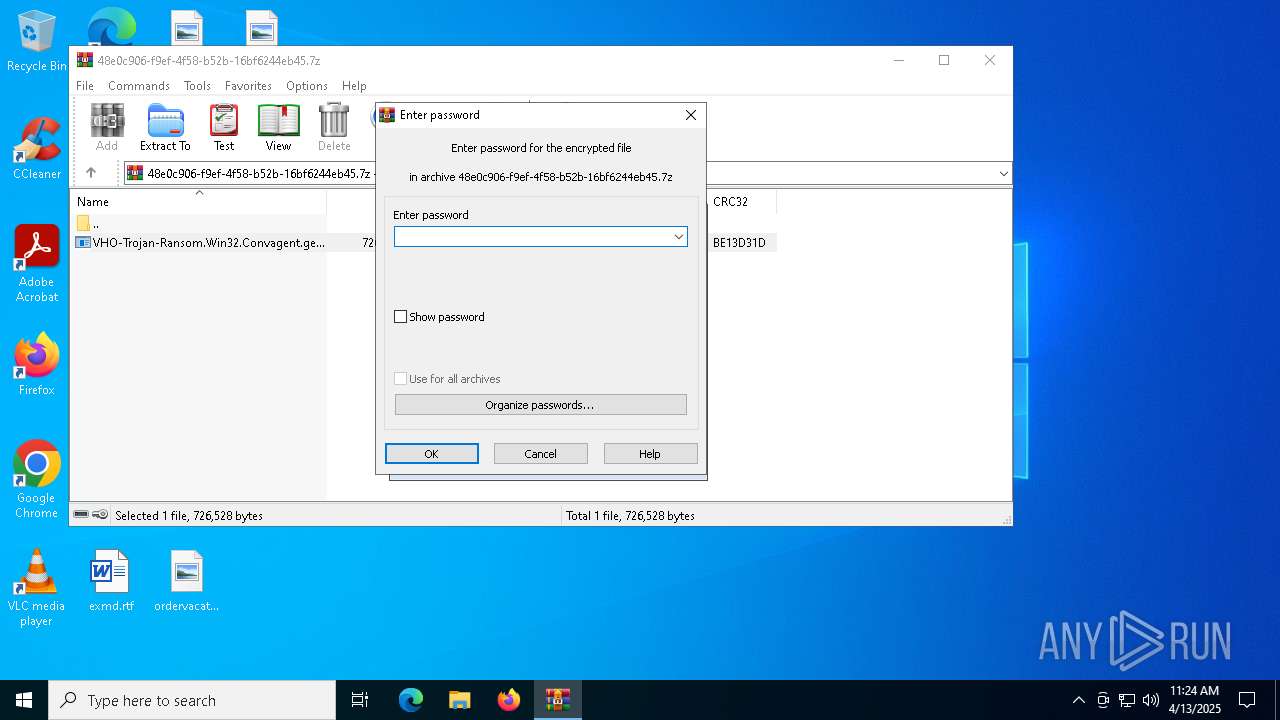
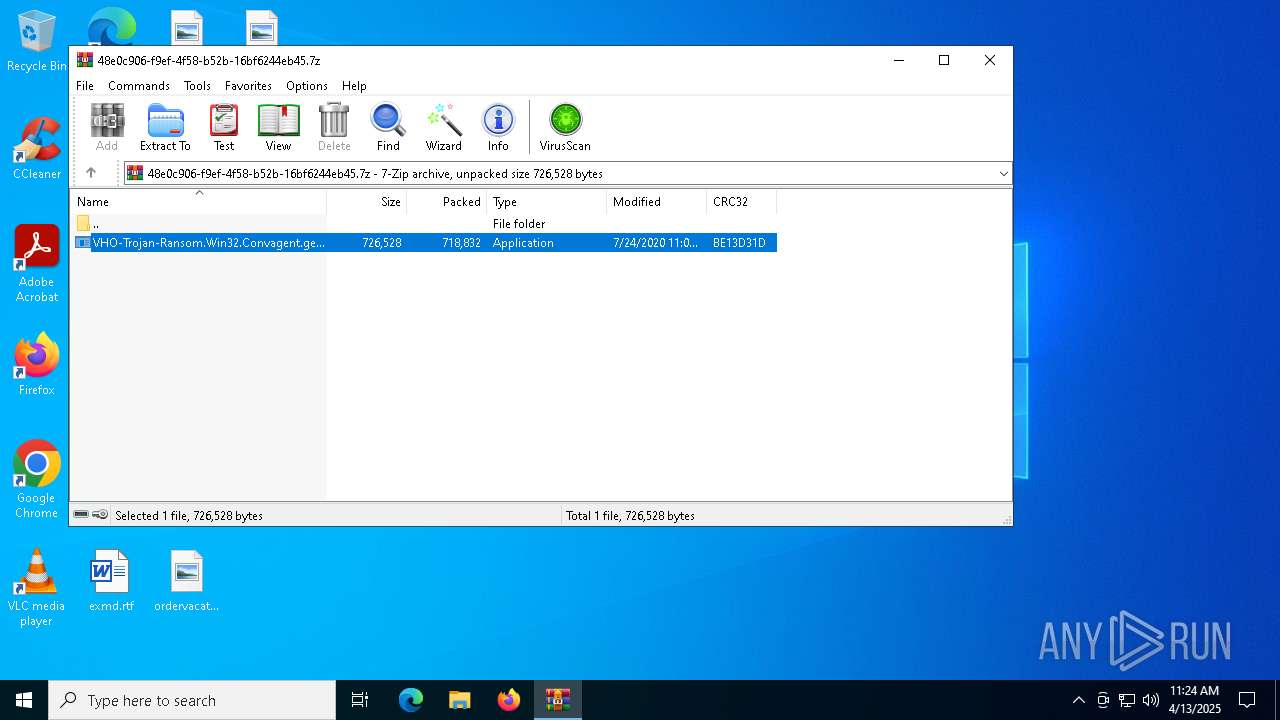
| File name: | VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.7z |
| Full analysis: | https://app.any.run/tasks/48e0c906-f9ef-4f58-b52b-16bf6244eb45 |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2025, 11:24:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A6096E8EEE2DE80465E8DBC0805BEEBE |
| SHA1: | 8E9E667501BD8A912DA868592C0864A83C358127 |
| SHA256: | 4CA7858F157FDCE2C806C3BC00E590F0559A7EC00D27184458CCA97E1DE343FA |
| SSDEEP: | 24576:l1YVkJm7Bxl4qPpBvjHOPiDz52IVETKiePCP3r6PHZQ6wKp6EwuKyAa5L2EWT:l2VkJm7Bxl4qPpBvjHOPiDz52IVETKiH |
MALICIOUS
Disables Windows Defender
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
UAC/LUA settings modification
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Starts NET.EXE for service management
- cmd.exe (PID: 7916)
- net.exe (PID: 8188)
- net.exe (PID: 2236)
- net.exe (PID: 2140)
- net.exe (PID: 632)
- net.exe (PID: 5392)
Deletes shadow copies
- cmd.exe (PID: 7992)
SUSPICIOUS
Starts CMD.EXE for commands execution
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7852)
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Windows service management via SC.EXE
- sc.exe (PID: 6048)
- sc.exe (PID: 6816)
- sc.exe (PID: 5800)
- sc.exe (PID: 7052)
Creates files in the driver directory
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Executes as Windows Service
- VSSVC.exe (PID: 7448)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 7860)
INFO
Manual execution by a user
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Reads the computer name
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
- ShellExperienceHost.exe (PID: 7852)
The sample compiled with german language support
- WinRAR.exe (PID: 4628)
Checks supported languages
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
- ShellExperienceHost.exe (PID: 7852)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4628)
Process checks computer location settings
- VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe (PID: 7752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:07:24 23:00:44+00:00 |
| ArchivedFileName: | VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe |
Total processes
163
Monitored processes
34
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | net stop NetBackup BMR MTFTP Service /y | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | wmic shadowcopy delete | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749908 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\system32\net1 stop mfewc /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | net stop mfewc /y | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\system32\net1 stop BMR Boot Service /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | net stop McAfeeDLPAgentService /y | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\system32\net1 stop NetBackup BMR MTFTP Service /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | C:\WINDOWS\system32\net1 stop McAfeeDLPAgentService /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
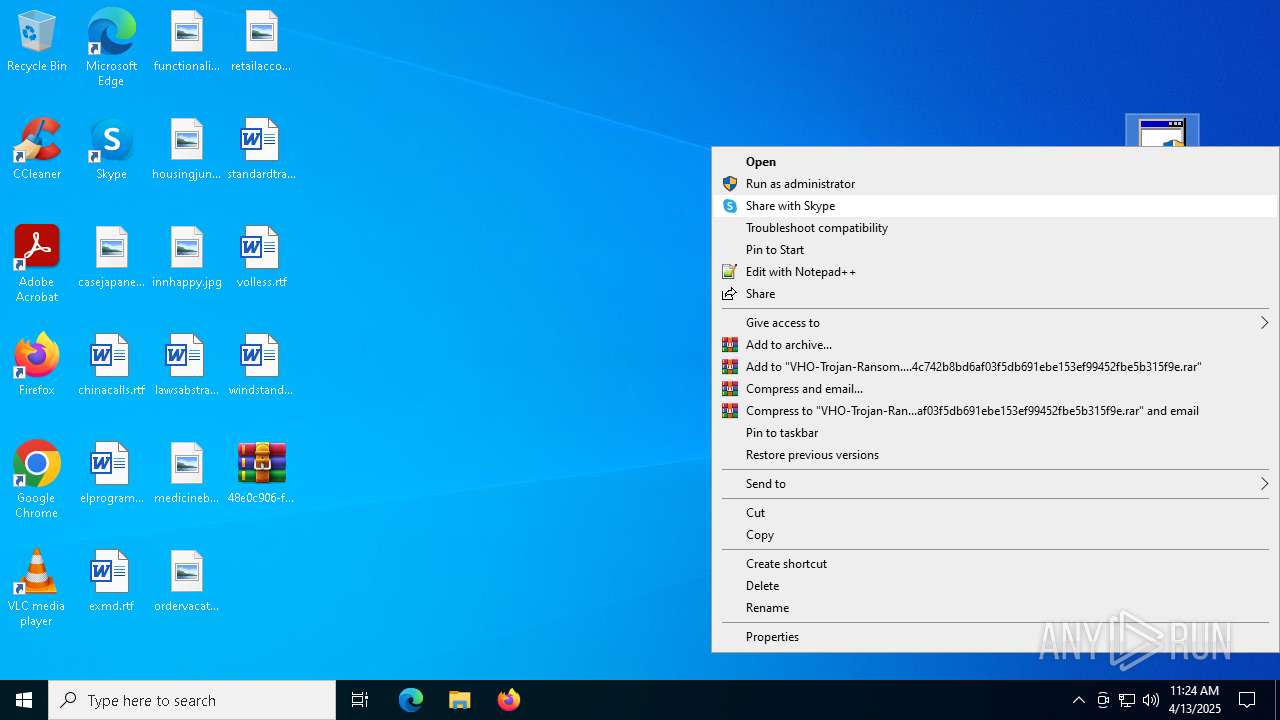
| 4628 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\48e0c906-f9ef-4f58-b52b-16bf6244eb45.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5392 | net stop BMR Boot Service /y | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 178
Read events
4 138
Write events
40
Delete events
0
Modification events
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\48e0c906-f9ef-4f58-b52b-16bf6244eb45.7z | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4628.26720\VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe | executable | |
MD5:8AB4B4A5BB74F22137E45A15879C9F9B | SHA256:A7A64650030F5D2225D4C742B8BD6AF03F5DB691EBE153EF99452FBE5B315F9E | |||
| 7752 | VHO-Trojan-Ransom.Win32.Convagent.gen-a7a64650030f5d2225d4c742b8bd6af03f5db691ebe153ef99452fbe5b315f9e.exe | C:\Windows\System32\drivers\etc\host | text | |
MD5:1721DD2411428A6CB86973D86419CD6D | SHA256:BFB93C4DA0828E5C59679B4DCAF9425CAB7EA8F87B11A3E4D44FF34F18BE1B1B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2292 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
df4gd65fg4565f4d56.000webhostapp.com |
| shared |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
2196 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
2196 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |