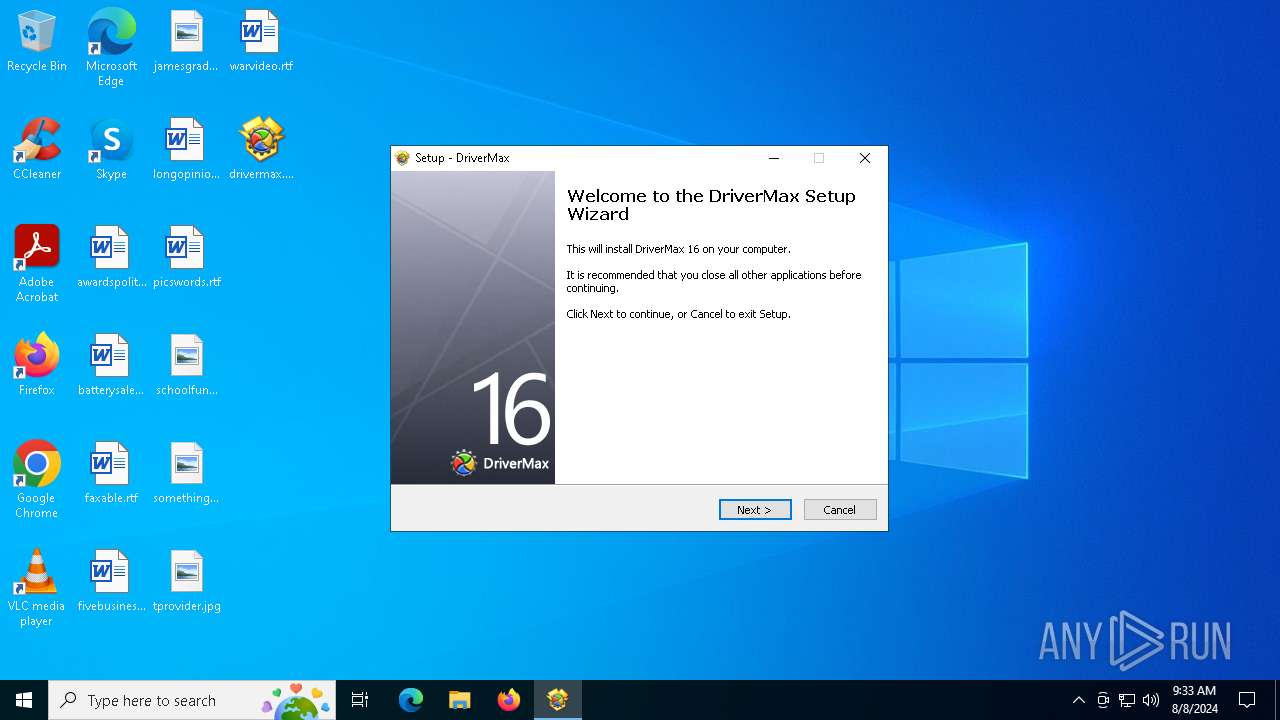
| File name: | drivermax.exe |
| Full analysis: | https://app.any.run/tasks/756ecf3e-a134-4180-a2aa-3a16a4de88b9 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 09:33:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 08B1C00831EB994402598FBDE8231E97 |
| SHA1: | D68B9FEE5DD2F544032C54C3B37E5AAC0909957A |
| SHA256: | 4CA6B1F38A4486882F3416BCED3A1B9462BF55869A5A3CCE43FD57C4AA20A478 |
| SSDEEP: | 98304:igXnkfOwNL25WTrw3D8KehdAZG7DB0uKh2LqXJ5Y7ZVevMT2/K/O5F+AvHhwHAJ4:lin1Z983ez3b |
MALICIOUS
Drops the executable file immediately after the start
- drivermax.exe (PID: 6520)
- drivermax.exe (PID: 6620)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
Connects to the CnC server
- drivermax.tmp (PID: 6644)
Changes the autorun value in the registry
- drivermax.tmp (PID: 6644)
SUSPICIOUS
Reads security settings of Internet Explorer
- drivermax.tmp (PID: 6540)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 8152)
Executable content was dropped or overwritten
- drivermax.exe (PID: 6520)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 6620)
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 6456)
Reads the Windows owner or organization settings
- drivermax.tmp (PID: 6644)
Process drops legitimate windows executable
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 6580)
Checks for external IP
- svchost.exe (PID: 2256)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 8152)
Uses TASKKILL.EXE to kill process
- drivermax.tmp (PID: 6644)
Reads the date of Windows installation
- drivermax.tmp (PID: 6540)
Checks Windows Trust Settings
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 8152)
Adds/modifies Windows certificates
- drivermax.exe (PID: 840)
Searches for installed software
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 6456)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 6384)
- dxdiag.exe (PID: 6568)
Checks for Java to be installed
- java.exe (PID: 4316)
- java.exe (PID: 1168)
Starts CMD.EXE for commands execution
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
There is functionality for taking screenshot (YARA)
- innostp.exe (PID: 6236)
- drivermax.exe (PID: 6580)
There is functionality for communication over UDP network (YARA)
- drivermax.exe (PID: 6580)
Drops a system driver (possible attempt to evade defenses)
- drivermax.exe (PID: 6580)
- drivermax.exe (PID: 6456)
Application launched itself
- drivermax.exe (PID: 6580)
INFO
Reads the computer name
- drivermax.tmp (PID: 6540)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- innostp.exe (PID: 6236)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
- innostp.exe (PID: 6672)
- innostp.exe (PID: 2456)
- drivermax.exe (PID: 8152)
- identity_helper.exe (PID: 7348)
Checks supported languages
- drivermax.tmp (PID: 6540)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 6520)
- stop_dmx.exe (PID: 4280)
- drivermax.exe (PID: 6620)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6456)
- innostp.exe (PID: 6236)
- drivermax.exe (PID: 6580)
- innostp.exe (PID: 6672)
- innostp.exe (PID: 2456)
- java.exe (PID: 4316)
- java.exe (PID: 1168)
- identity_helper.exe (PID: 7348)
- drivermax.exe (PID: 8152)
Create files in a temporary directory
- drivermax.exe (PID: 6620)
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 6520)
- java.exe (PID: 4316)
- java.exe (PID: 1168)
Reads the software policy settings
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6456)
- drivermax.exe (PID: 6580)
- dxdiag.exe (PID: 6568)
- dxdiag.exe (PID: 6384)
- drivermax.exe (PID: 8152)
Checks proxy server information
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- dxdiag.exe (PID: 6384)
Creates files in the program directory
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6580)
- dxdiag.exe (PID: 6384)
- dxdiag.exe (PID: 6568)
- cmd.exe (PID: 6756)
- java.exe (PID: 4316)
- cmd.exe (PID: 5880)
Creates files or folders in the user directory
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- drivermax.exe (PID: 6580)
- dxdiag.exe (PID: 6384)
- drivermax.exe (PID: 6456)
Reads the machine GUID from the registry
- drivermax.tmp (PID: 6644)
- drivermax.exe (PID: 840)
- innostp.exe (PID: 6236)
- drivermax.exe (PID: 6580)
- innostp.exe (PID: 6672)
- drivermax.exe (PID: 6456)
- innostp.exe (PID: 2456)
- drivermax.exe (PID: 8152)
Creates a software uninstall entry
- drivermax.tmp (PID: 6644)
Process checks computer location settings
- drivermax.tmp (PID: 6540)
Reads Microsoft Office registry keys
- drivermax.tmp (PID: 6644)
- msedge.exe (PID: 6440)
- msedge.exe (PID: 5064)
Manual execution by a user
- msedge.exe (PID: 5064)
Application launched itself
- msedge.exe (PID: 5064)
- msedge.exe (PID: 6440)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 6384)
- dxdiag.exe (PID: 6568)
Reads Environment values
- identity_helper.exe (PID: 7348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (74.3) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.6) |
| .scr | | | Windows screen saver (8.8) |
| .exe | | | Win32 Executable (generic) (3) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 382976 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
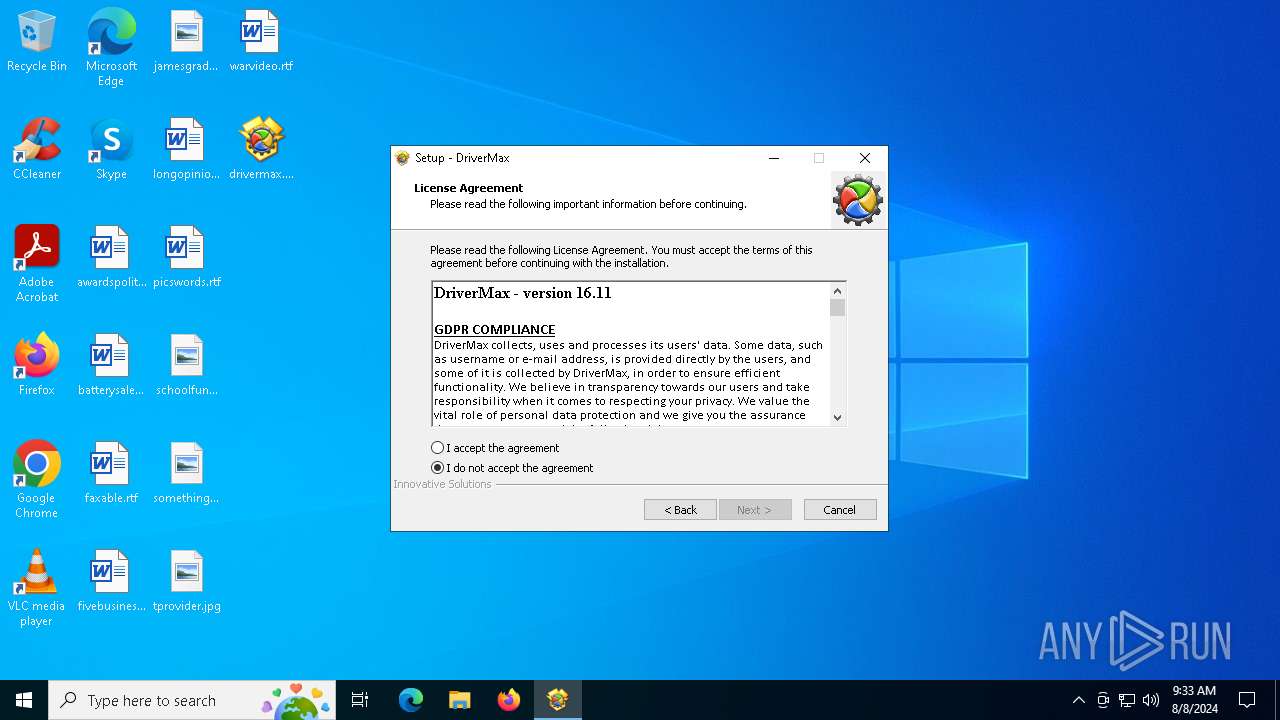
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Innovative Solutions |
| FileDescription: | DriverMax Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | DriverMax |
| ProductVersion: | 16.14.0.9 |
Total processes
223
Monitored processes
100
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6708 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 840 | "C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax.exe" -LANGUAGE | C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax.exe | drivermax.tmp | ||||||||||||
User: admin Company: Innovative Solutions Integrity Level: HIGH Description: DriverMax Exit code: 0 Version: 16.14.0.9 Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "Taskkill.exe" /IM stop_dmx.exe /F | C:\Windows\SysWOW64\taskkill.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\\Common Files\Oracle\Java\javapath\java.exe" -version | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=4036 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4780 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5396 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1372 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2788 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1536 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3036 --field-trial-handle=2372,i,8895696691646240009,7420409971150158167,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
70 687
Read events
70 019
Write events
582
Delete events
86
Modification events
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | Affiliate |
Value: Inno | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | fc |
Value: NP | |||
| (PID) Process: | (6644) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | lc |
Value: NP | |||
Executable files
135
Suspicious files
444
Text files
165
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6644 | drivermax.tmp | C:\Users\admin\AppData\Local\Temp\is-ONQHF.tmp\analytics_v2.dll | executable | |
MD5:9997F8936AC3187262ED21E681A6F254 | SHA256:E53317E0ECD2B26D4901D4E29914B4BB3F3097AAF5485D5B0A2D58E1340B45EC | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-P2HTQ.tmp | executable | |
MD5:DDA56268C2B003EA0ECF68982E950F9E | SHA256:61E4D3ED79FD304D8D8E9588A4E4ACDD9193FE44955A3E1CF3BF60A2B8351138 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\Readme\is-CSFTO.tmp | text | |
MD5:7FABABD2AAE7365FAB3366D0EA8B5C09 | SHA256:B835321246B4EBE6B3640F50A320C6FB8F0B26331664B72007D2CEBA64369773 | |||
| 6620 | drivermax.exe | C:\Users\admin\AppData\Local\Temp\is-B5262.tmp\drivermax.tmp | executable | |
MD5:AB126F7F9FF2E7902FF2BBDC1A6D3158 | SHA256:89D0CFA56BACC7981227BF45E2983DD6BFF5BAA359EBF756EF2B171B5668E515 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-O85S2.tmp | executable | |
MD5:FEA887BCC3A342B2FACB566B7F7E5FCE | SHA256:087A5E4CBE8278E364703EA78F7EE57BC85D6C24A361529940634957FE18D1C5 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\innostp.exe | executable | |
MD5:024814EF497C4CEE55663912E1C35DD0 | SHA256:0C6053EF6722F3770CE474CFD5039296BC5F59E4C8A23670BA19B3D2F4A48B10 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\unins000.exe | executable | |
MD5:DDA56268C2B003EA0ECF68982E950F9E | SHA256:61E4D3ED79FD304D8D8E9588A4E4ACDD9193FE44955A3E1CF3BF60A2B8351138 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\Readme\license.rtf | text | |
MD5:7FABABD2AAE7365FAB3366D0EA8B5C09 | SHA256:B835321246B4EBE6B3640F50A320C6FB8F0B26331664B72007D2CEBA64369773 | |||
| 6644 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-PTR8N.tmp | executable | |
MD5:024814EF497C4CEE55663912E1C35DD0 | SHA256:0C6053EF6722F3770CE474CFD5039296BC5F59E4C8A23670BA19B3D2F4A48B10 | |||
| 6644 | drivermax.tmp | C:\Users\admin\AppData\Local\Temp\is-ONQHF.tmp\folder-images-icon.bmp | image | |
MD5:D393253B0477CCE0D1E2F6E96E1339E9 | SHA256:171092952FE01BACAFEEA6B4C7CF90AF0CA98EB251834F9B9E3E702DC878FA61 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
148
TCP/UDP connections
130
DNS requests
97
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
840 | drivermax.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
840 | drivermax.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDA5ml5aITsG9Y8TP4w%3D%3D | unknown | — | — | whitelisted |
840 | drivermax.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
6644 | drivermax.tmp | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
6580 | drivermax.exe | GET | 200 | 168.119.201.56:80 | http://www.drivermax.com/promo8//Inno/_v5.xml | unknown | — | — | whitelisted |
6580 | drivermax.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | OPTIONS | 503 | 23.48.23.26:443 | https://bzib.nelreports.net/api/report?cat=bingbusiness | unknown | — | — | unknown |
6456 | drivermax.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
— | — | POST | 204 | 142.250.181.238:443 | https://www.google-analytics.com/mp/collect?api_secret=j_--kIeEReK9Q1WaFVRUnw&measurement_id=G-FR85445GJW | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4088 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5112 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6644 | drivermax.tmp | 34.117.59.81:80 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
6644 | drivermax.tmp | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4088 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ipinfo.io |
| shared |
www.google-analytics.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.drivermax.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6644 | drivermax.tmp | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6644 | drivermax.tmp | Misc activity | ET ADWARE_PUP Drivermax Utility Checkin Activity |
6644 | drivermax.tmp | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
840 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
6456 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
6580 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
4008 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
4008 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |