| File name: | RxSLTR32.exe |
| Full analysis: | https://app.any.run/tasks/b7bd6d98-3186-4eeb-b25f-42ea2e62b070 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2019, 22:29:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7A89206D45C6874D4B606FF252ECF983 |
| SHA1: | F22EB819F9BD4D526BEC42EA5F1B5A017C5E893E |
| SHA256: | 4C87E6AB5C7C71E20F741BDADB76815E7AE3130AC70CCAB56347FF7AF8AE096B |
| SSDEEP: | 24576:6mlO8itrXZ+Pc01vuyx5J3pJ1HDrPvpyLZ+L8JJrLiTykf0Nu9nQUYy8SjaqQnH4:x6Z4Jvr7ZDrPvpw+LKJHOykceCy8SEnY |
MALICIOUS
Application was dropped or rewritten from another process
- Elevate.exe (PID: 1628)
- grep.exe (PID: 3736)
- swReg.exe (PID: 2564)
- swReg.exe (PID: 2168)
- swReg.exe (PID: 2972)
- swReg.exe (PID: 4040)
- swReg.exe (PID: 3236)
- grep.exe (PID: 3584)
- swReg.exe (PID: 588)
- grep.exe (PID: 2896)
- grep.exe (PID: 2144)
- swReg.exe (PID: 2952)
- grep.exe (PID: 3572)
- swSC.exe (PID: 3476)
- grep.exe (PID: 880)
- grep.exe (PID: 2212)
- MoveFile.exe (PID: 3200)
- swReg.exe (PID: 2140)
- grep.exe (PID: 2416)
- grep.exe (PID: 3200)
- grep.exe (PID: 2780)
- grep.exe (PID: 3128)
- swReg.exe (PID: 3296)
- MoveFile.exe (PID: 3652)
- swReg.exe (PID: 4076)
- swReg.exe (PID: 2660)
- swReg.exe (PID: 3788)
- swReg.exe (PID: 2756)
- swReg.exe (PID: 2316)
- swReg.exe (PID: 2404)
- swReg.exe (PID: 2560)
- swReg.exe (PID: 3036)
- swReg.exe (PID: 3612)
- swReg.exe (PID: 2296)
- swReg.exe (PID: 2540)
- swReg.exe (PID: 3244)
- swReg.exe (PID: 3668)
- swReg.exe (PID: 3844)
- swReg.exe (PID: 2708)
- swReg.exe (PID: 3224)
- swReg.exe (PID: 2712)
- swReg.exe (PID: 2800)
- swReg.exe (PID: 3768)
- swReg.exe (PID: 3404)
- swReg.exe (PID: 3636)
- swReg.exe (PID: 2864)
- swReg.exe (PID: 3240)
- swReg.exe (PID: 2312)
- swReg.exe (PID: 2152)
- swReg.exe (PID: 3704)
- swReg.exe (PID: 2412)
- swReg.exe (PID: 3060)
- swReg.exe (PID: 3836)
- swReg.exe (PID: 3928)
- swReg.exe (PID: 2300)
- grep.exe (PID: 2404)
- grep.exe (PID: 2812)
- grep.exe (PID: 3316)
- swReg.exe (PID: 2868)
- swReg.exe (PID: 3140)
- swReg.exe (PID: 3812)
- swReg.exe (PID: 2292)
- swReg.exe (PID: 2948)
- swReg.exe (PID: 3536)
- swReg.exe (PID: 3840)
- swReg.exe (PID: 3056)
- swReg.exe (PID: 676)
- swReg.exe (PID: 2856)
- SetRegTime.exe (PID: 3892)
- SetRegTime.exe (PID: 2852)
- swReg.exe (PID: 3228)
- swReg.exe (PID: 1492)
- swReg.exe (PID: 2524)
- swReg.exe (PID: 3732)
- SetRegTime.exe (PID: 3112)
- SetRegTime.exe (PID: 3260)
- rxRepl.exe (PID: 2532)
- MessageBox.exe (PID: 2056)
- swSC.exe (PID: 4080)
- grep.exe (PID: 3820)
- swReg.exe (PID: 3720)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3472)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3964)
- schtasks.exe (PID: 2672)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Elevate.exe (PID: 1628)
- cmd.exe (PID: 3472)
- cmd.exe (PID: 3448)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 3824)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2660)
- cmd.exe (PID: 2568)
Reads internet explorer settings
- RxSLTR32.exe (PID: 3000)
Executable content was dropped or overwritten
- RxSLTR32.exe (PID: 3000)
Application launched itself
- cmd.exe (PID: 3472)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2800)
- cmd.exe (PID: 4020)
Starts application with an unusual extension
- cmd.exe (PID: 3472)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:11 15:54:06+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 188928 |
| InitializedDataSize: | 569856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1cec9 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.9.11319 |
| ProductVersionNumber: | 3.0.9.11319 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | WinRAR: self-extracting module |
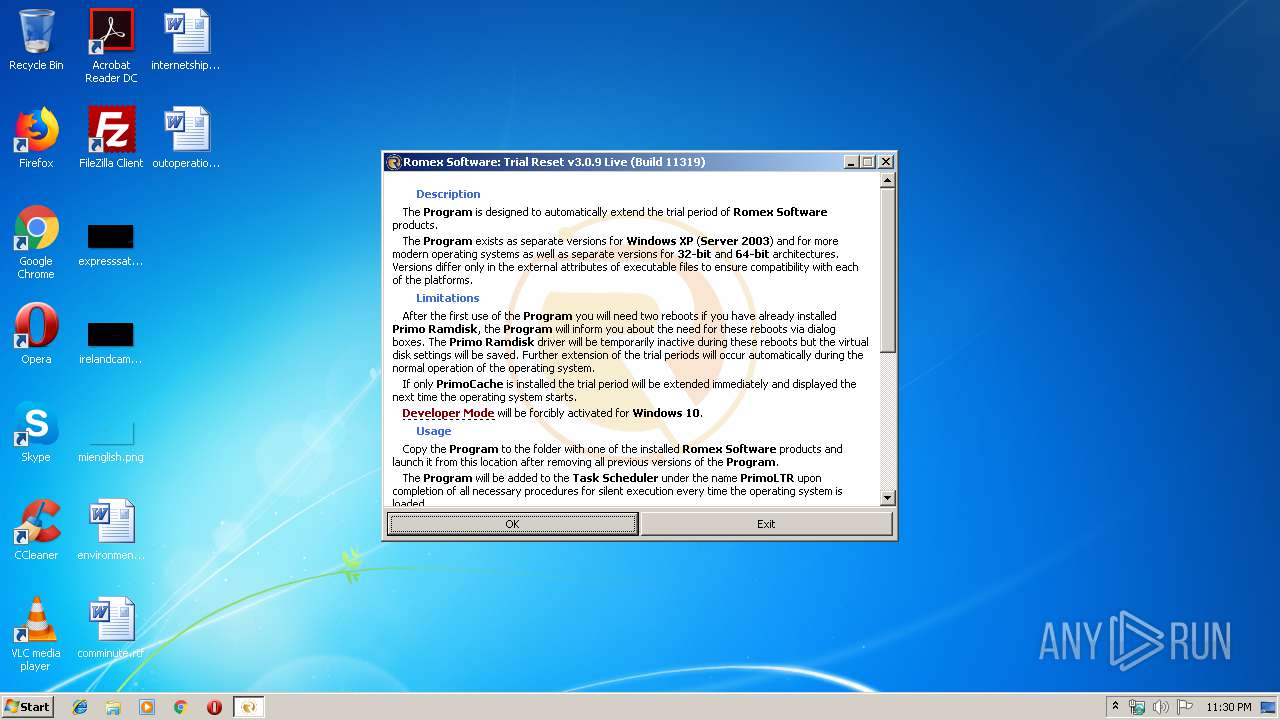
| CompanyName: | Romex Software |
| FileDescription: | Romex Software: Trial Reset |
| FileVersion: | 3.0.9.11319 |
| InternalName: | PrimoLTR.cmd |
| LegalCopyright: | © 2019 Romex Software. All rights reserved. |
| LegalTrademarks: | PrimoCache (formerly FancyCache) & Primo Ramdisk (formerly VSuite Ramdisk) |
| OriginalFileName: | RxSLTR32.exe |
| ProductName: | PrimoCache 1.0.1–3.0.9 & Primo Ramdisk 5.7.0–6.3.1 |
| ProductVersion: | 3.0.9.11319 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Aug-2017 13:54:06 |
| Detected languages: |
|
| Debug artifacts: |
|
| Comments: | WinRAR: модуль самораспаковки |
| CompanyName: | Romex Software |
| FileDescription: | Romex Software: Trial Reset |
| FileVersion: | 3.0.9.11319 |
| InternalName: | PrimoLTR.cmd |
| LegalCopyright: | © Romex Software, 2019. Все права защищены. |
| LegalTrademarks: | PrimoCache (ранее FancyCache) и Primo Ramdisk (ранее VSuite Ramdisk) |
| OriginalFilename: | RxSLTR32.exe |
| ProductName: | PrimoCache 1.0.1–3.0.9 и Primo Ramdisk 5.7.0–6.3.1 |
| ProductVersion: | 3.0.9.11319 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 11-Aug-2017 13:54:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002E1CB | 0x0002E200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.69428 |
.rdata | 0x00030000 | 0x000098A0 | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.12106 |
.data | 0x0003A000 | 0x0001F290 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.23719 |
.gfids | 0x0005A000 | 0x000000E8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.05507 |
.rsrc | 0x0005B000 | 0x0007E8D8 | 0x0007EA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.72927 |
.reloc | 0x000DA000 | 0x00001F58 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.62297 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.37648 | 1860 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 4.16926 | 1864 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.24672 | 3240 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 4.23242 | 7336 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 6.91017 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 7.11007 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 3.66634 | 508 | UNKNOWN | Russian - Russia | RT_STRING |
8 | 3.71728 | 582 | UNKNOWN | Russian - Russia | RT_STRING |
9 | 3.74776 | 476 | UNKNOWN | Russian - Russia | RT_STRING |
10 | 3.48875 | 172 | UNKNOWN | Russian - Russia | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
Total processes
146
Monitored processes
111
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" DELETE "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce" /v "PrimoLTR" | C:\Users\admin\AppData\Local\Temp\PrimoLTR\swReg.exe | — | cmd.exe | |||||||||||
User: admin Company: SteelWerX Integrity Level: HIGH Description: SteelWerX Command Line Registry Editor Exit code: 1 Version: 3.0.0.5 Modules
| |||||||||||||||
| 676 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" ACL HKLM\SYSTEM\ControlSet002\Services\Eventlog\System\{a257d54e-6769-4397-b2d2-9f75024b3156} /OA /I REMOVE /P /GE:F | C:\Users\admin\AppData\Local\Temp\PrimoLTR\swReg.exe | — | cmd.exe | |||||||||||
User: admin Company: SteelWerX Integrity Level: HIGH Description: SteelWerX Command Line Registry Editor Exit code: 1 Version: 3.0.0.5 Modules
| |||||||||||||||
| 880 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\grep.exe" -F "STOPPED" | C:\Users\admin\AppData\Local\Temp\PrimoLTR\grep.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" ACL HKLM\SYSTEM\Setup\SetuprmHashStatus\{26ACDB38-4812-4393-B91C-A315EB60E8B7} /OA /I REMOVE /P /GE:F | C:\Users\admin\AppData\Local\Temp\PrimoLTR\swReg.exe | — | cmd.exe | |||||||||||
User: admin Company: SteelWerX Integrity Level: HIGH Description: SteelWerX Command Line Registry Editor Exit code: 1 Version: 3.0.0.5 Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\Elevate.exe" -u -c -w Set "SfxName=C:\Users\admin\AppData\Local\Temp\RxSLTR32.exe" & Set "SfxPar=" & PrimoLTR.cmd | C:\Users\admin\AppData\Local\Temp\PrimoLTR\Elevate.exe | — | RxSLTR32.exe | |||||||||||
User: admin Company: code.kliu.org Integrity Level: MEDIUM Description: Command-Line UAC Elevation Utility Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 1688 | C:\Windows\system32\cmd.exe /S /D /c" Call "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" QUERY "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "CurrentMajorVersionNumber"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
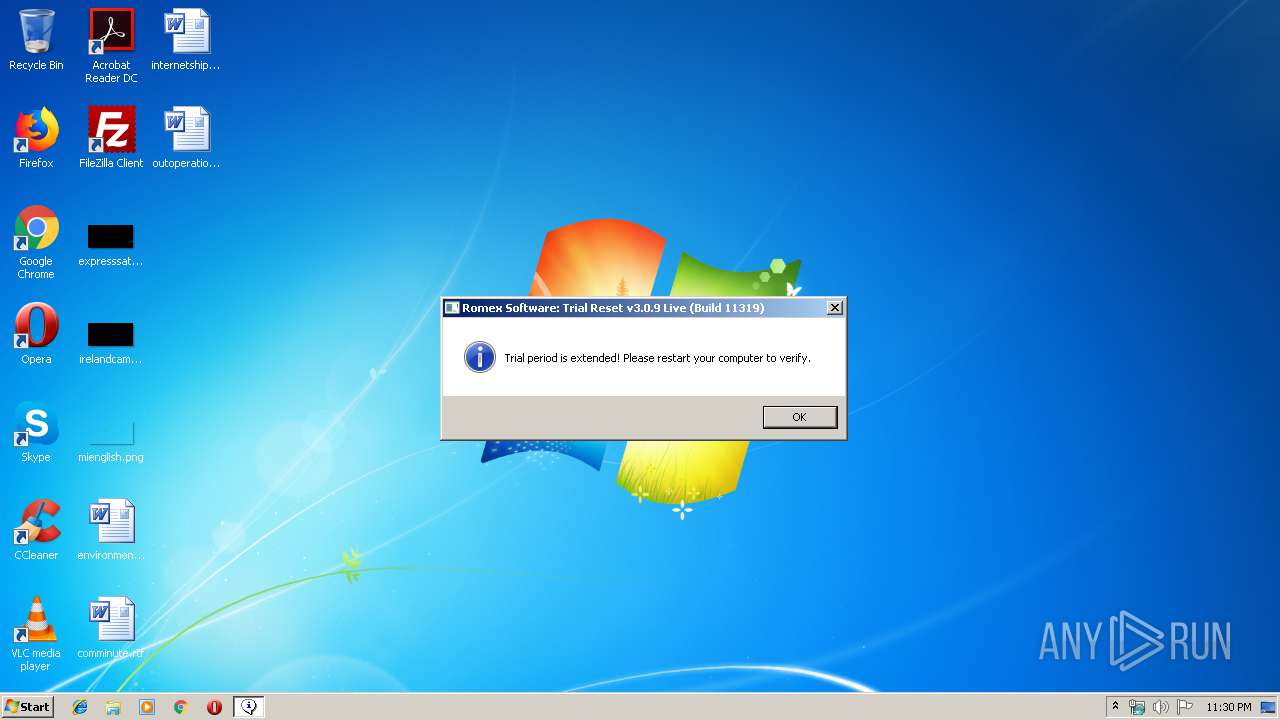
| 2056 | MessageBox.exe /C:Romex Software: Trial Reset v3.0.9 Live (Build 11319) /M:Trial period is extended! Please restart your computer to verify. /T:4160 | C:\Users\admin\AppData\Local\Temp\PrimoLTR\MessageBox.exe | — | cmd.exe | |||||||||||
User: admin Company: Optimum X Integrity Level: HIGH Description: Displays a custom MessageBox from command-line parameters. Exit code: 0 Version: 1.10 Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" QUERY "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "CurrentMajorVersionNumber" | C:\Users\admin\AppData\Local\Temp\PrimoLTR\swReg.exe | — | cmd.exe | |||||||||||
User: admin Company: SteelWerX Integrity Level: HIGH Description: SteelWerX Command Line Registry Editor Exit code: 1 Version: 3.0.0.5 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\grep.exe" -F "REG_DWORD" | C:\Users\admin\AppData\Local\Temp\PrimoLTR\grep.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\AppData\Local\Temp\PrimoLTR\swreg.exe" LINK ADD HKLM\SYSTEM\ControlSet002\Services\Eventlog\System\RxDeliveryStamp\{57C7DD3D-2E9C-4F3B-A270-391E8AEDF0C4} HKLM\SYSTEM\ControlSet001\Services\Eventlog\System\RxDeliveryStamp\{57C7DD3D-2E9C-4F3B-A270-391E8AEDF0C4} /temp | C:\Users\admin\AppData\Local\Temp\PrimoLTR\swReg.exe | — | cmd.exe | |||||||||||
User: admin Company: SteelWerX Integrity Level: HIGH Description: SteelWerX Command Line Registry Editor Exit code: 0 Version: 3.0.0.5 Modules
| |||||||||||||||
Total events
669
Read events
647
Write events
16
Delete events
6
Modification events
| (PID) Process: | (3000) RxSLTR32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) RxSLTR32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1628) Elevate.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1628) Elevate.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3200) MoveFile.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Movefile |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3652) MoveFile.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Movefile |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3612) swReg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2864) swReg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} |
| Operation: | write | Name: | SymbolicLinkValue |
Value: \Registry\Machine\SYSTEM\ControlSet002\Services\Eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} | |||
| (PID) Process: | (3240) swReg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\services\eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} |
| Operation: | write | Name: | SymbolicLinkValue |
Value: \Registry\Machine\SYSTEM\ControlSet001\Services\Eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} | |||
| (PID) Process: | (3636) swReg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\services\eventlog\System\RxDeliveryStamp\{201F15C8-ED72-4791-BABB-9DF121A43398} |
| Operation: | delete key | Name: | |
Value: | |||
Executable files
19
Suspicious files
0
Text files
53
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\PsExec.exe | executable | |
MD5:AEEE996FD3484F28E5CD85FE26B6BDCD | SHA256:F8DBABDFA03068130C277CE49C60E35C029FF29D9E3C74C362521F3FB02670D5 | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\PrimoLTR.cmd | text | |
MD5:829691EC731E7DBE353EC6FE85A3829E | SHA256:8BB551314E83B520FA491F09DABEA58B81B84F0CF97CAB1824BC612E2279B8CF | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\Ln.exe | executable | |
MD5:EDECD7CC63D7D92A47CD9C7B9E07A26A | SHA256:0285D8D2033F81FB62ED14D30CB3A23DF18F249CD33530C948BDE35DA4C5B4F3 | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\RxDS.hiv | hiv | |
MD5:1148616D6DD96CF703F30E85D13B0A87 | SHA256:04B20FF4B458A9ECDBFA26E0433DFF2953DDDACB1531FF8446B2900E41CF9C79 | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\MoveEx.exe | executable | |
MD5:FE1200C71152EC5DABD6D344BE3E107C | SHA256:8D2DE2D69CF62CF3206BA785461D33E47E951F7BF14BE1A3FA81522149079DDB | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\MoveFile.exe | executable | |
MD5:5789A1D0CF66DA36827A48F720181E16 | SHA256:CD1BA0EBE12D024D93AB01D95E8540355C1618C6DF65CB5B3A1FA01EE350D0F3 | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\HideExec.exe | executable | |
MD5:CEF18E9D1F9A4EAB3F9BB259AC81EBDE | SHA256:DA32038F37082D1DD8351FFFEDBA645CDE1DEF69B14D0D8F635029109861E76B | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\RxSLTR.xml | xml | |
MD5:94404ED2DEFE94C9E95A28767631071D | SHA256:2A6493BB893466D73F14F4F3175A52F12C2B221F414DA72535CF6C70B7BDED2D | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\RegBack.exe | executable | |
MD5:4FCA9D80849972AFFD18862B1DFE4974 | SHA256:318ED02315CE8114F22831B2F63FBA00A7B43C6FDF35EEE81AC136DC1810305D | |||
| 3000 | RxSLTR32.exe | C:\Users\admin\AppData\Local\Temp\PrimoLTR\Elevate.exe | executable | |
MD5:792825AB602FD208A5FD5521DC61AEB9 | SHA256:90C5F6D2369C794E819757A2287A3DC5BBEA107E7AB8FADE32FF33E198870C7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report