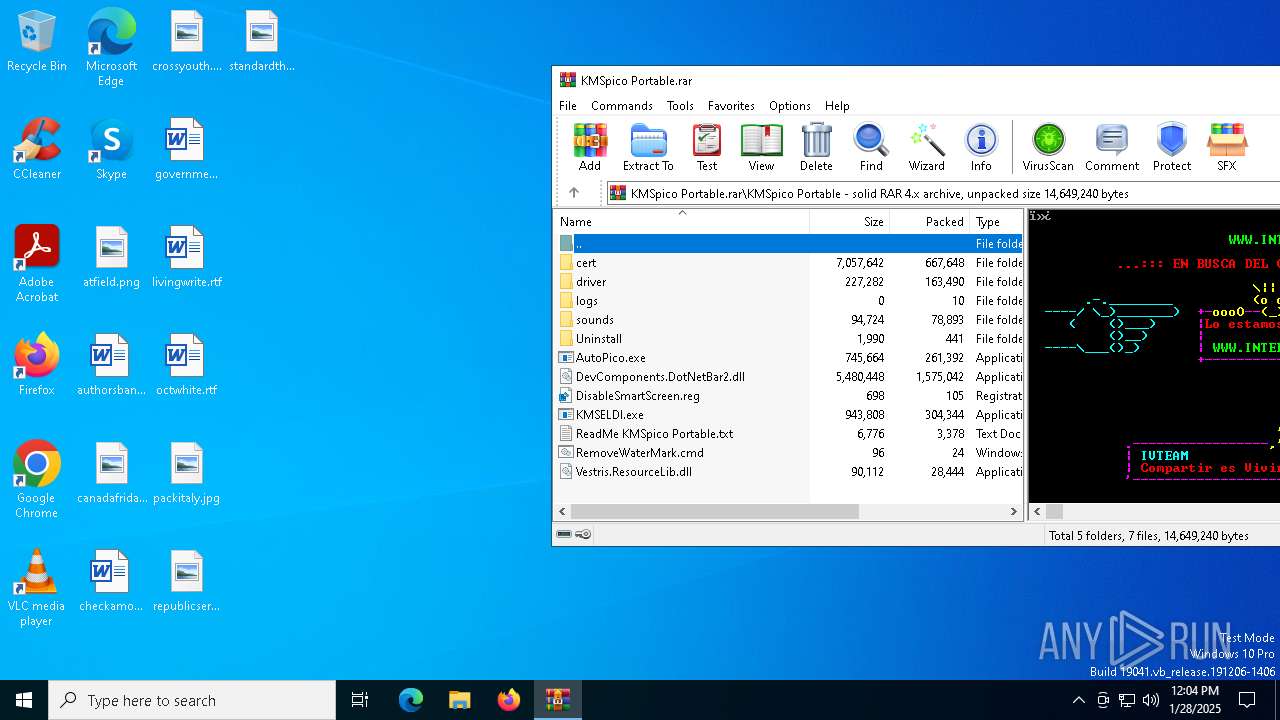
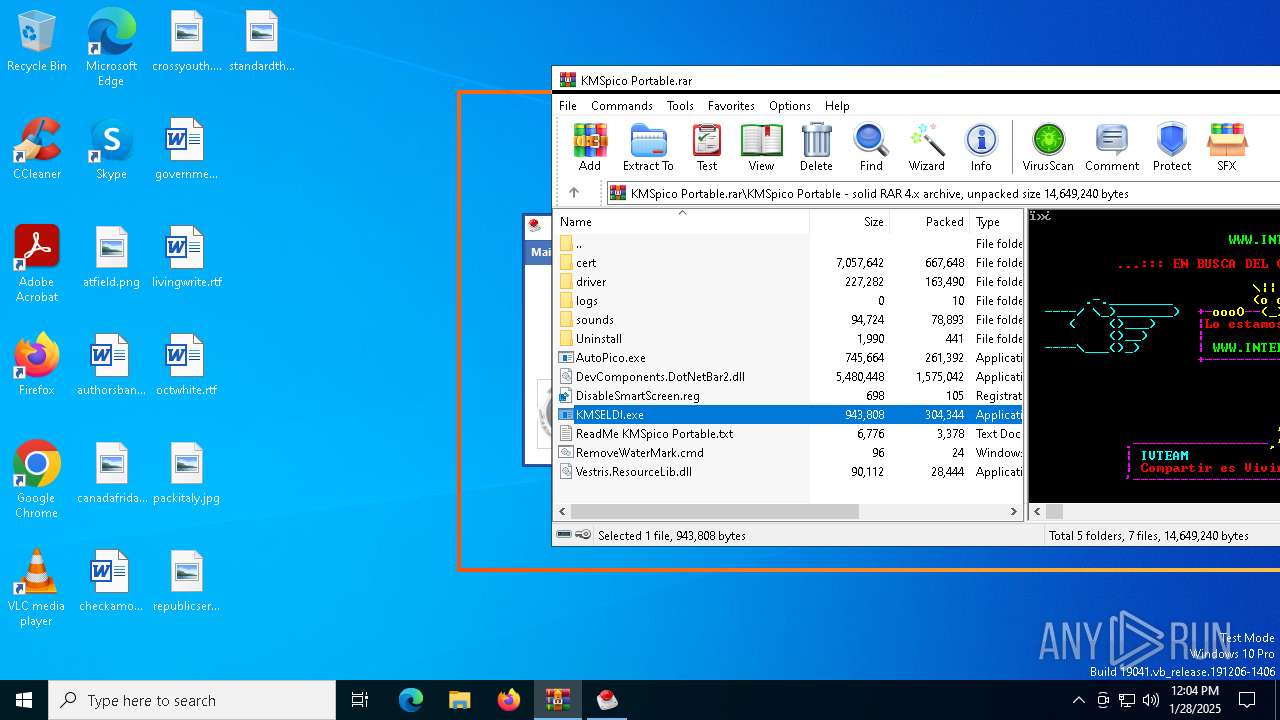
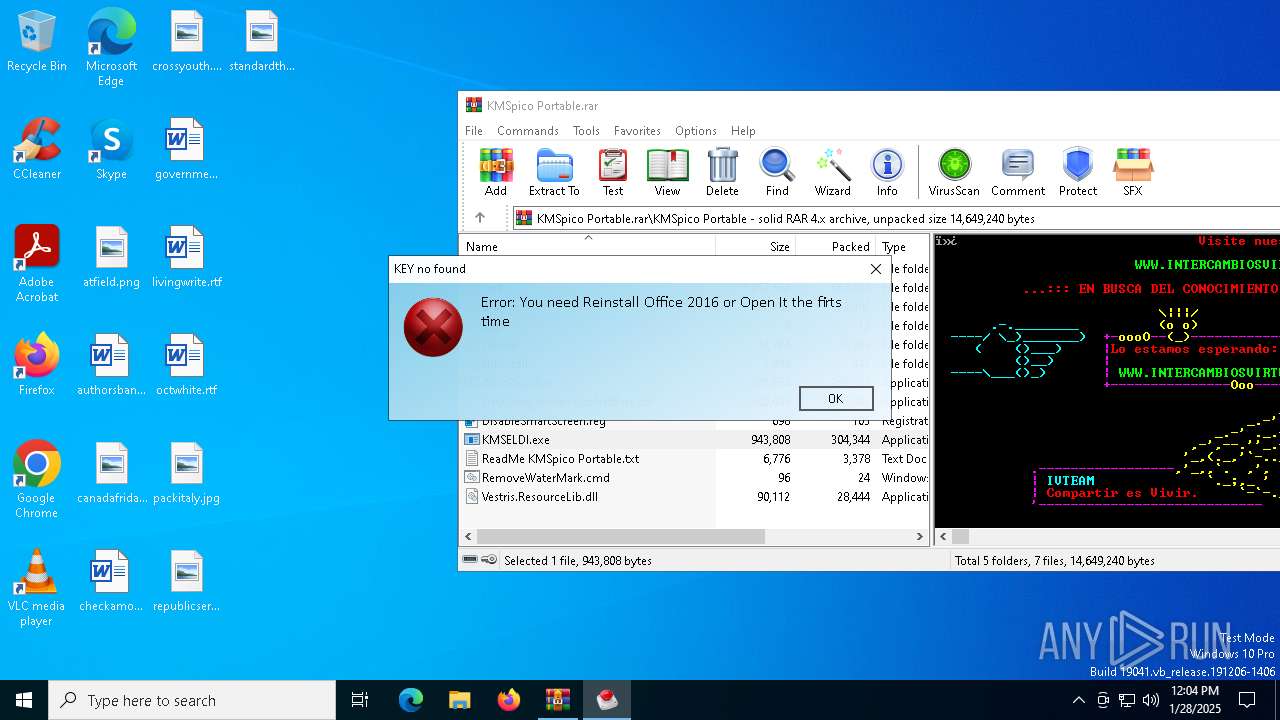
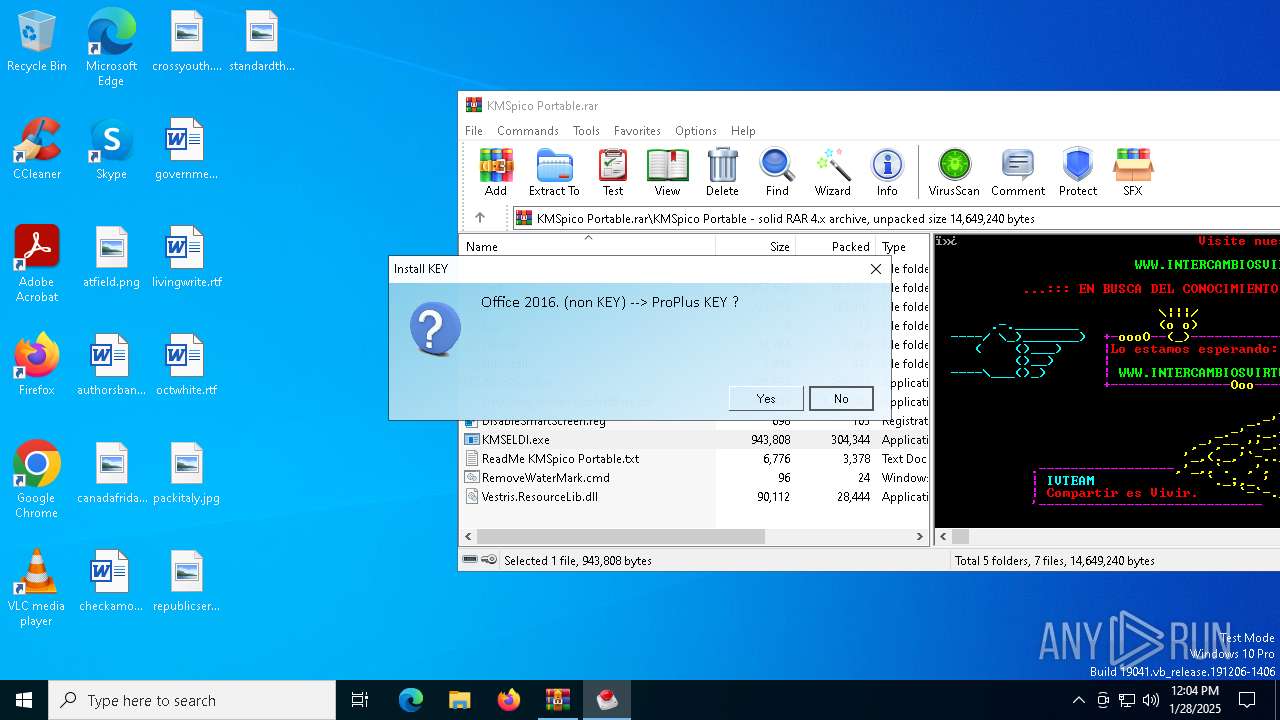
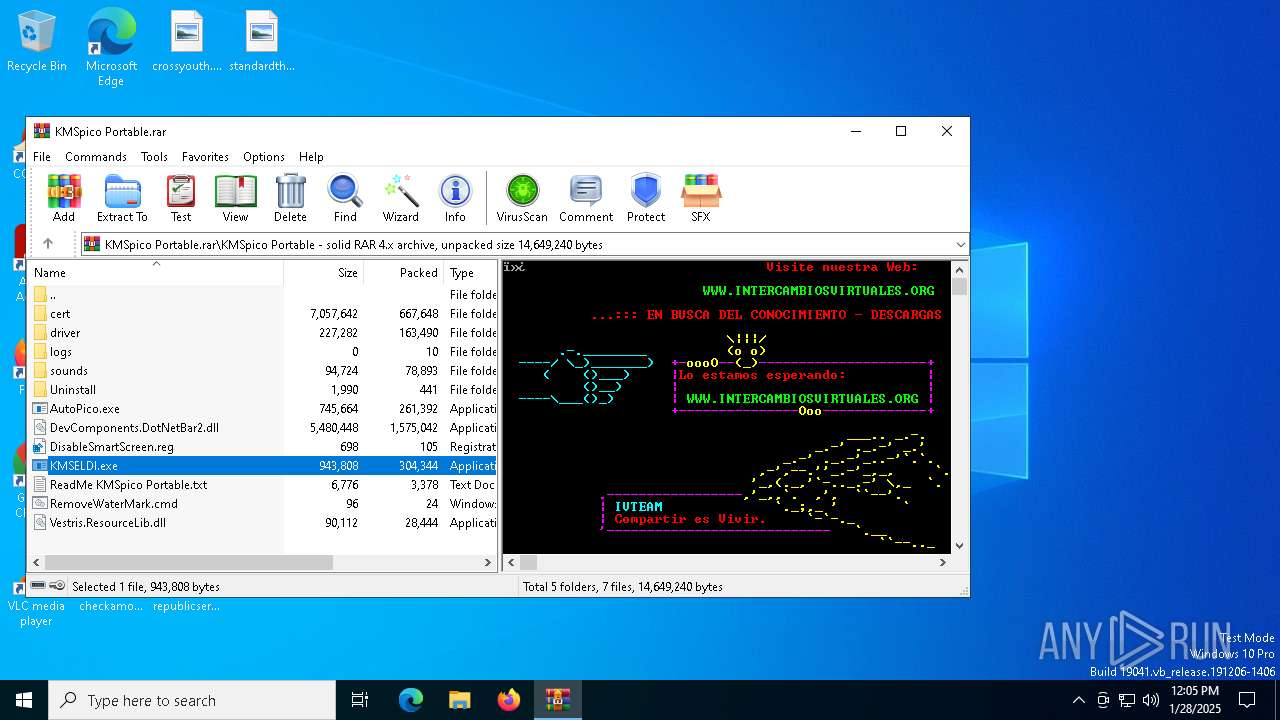
| File name: | KMSpico Portable.rar |
| Full analysis: | https://app.any.run/tasks/97101698-7861-41f5-9a52-1fae7f1001b4 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2025, 12:04:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: Solid |
| MD5: | 655F6DF21950B954EE19FDE43FB92746 |
| SHA1: | 4D328DA9C075209734B3FFA0BC951398CE0E30FC |
| SHA256: | 4C847D066D178CD4F53EB66AA6E39968ED48616631BCD62FFD6B9CE813026526 |
| SSDEEP: | 98304:LXb4Nv7ohPtwOYiKLP/fNlWvPn7Z026CTjMm8sS3GxFrY64BytEXAIFPqPM3cA+n:u2 |
MALICIOUS
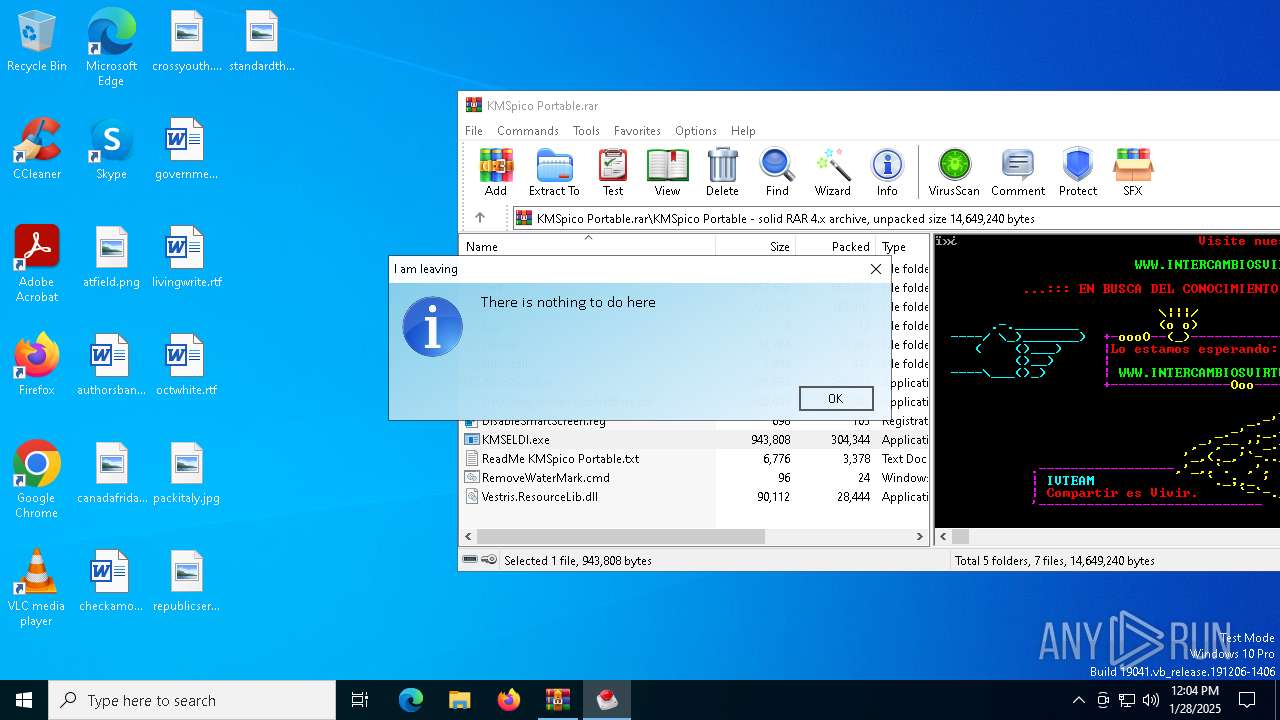
Executing a file with an untrusted certificate
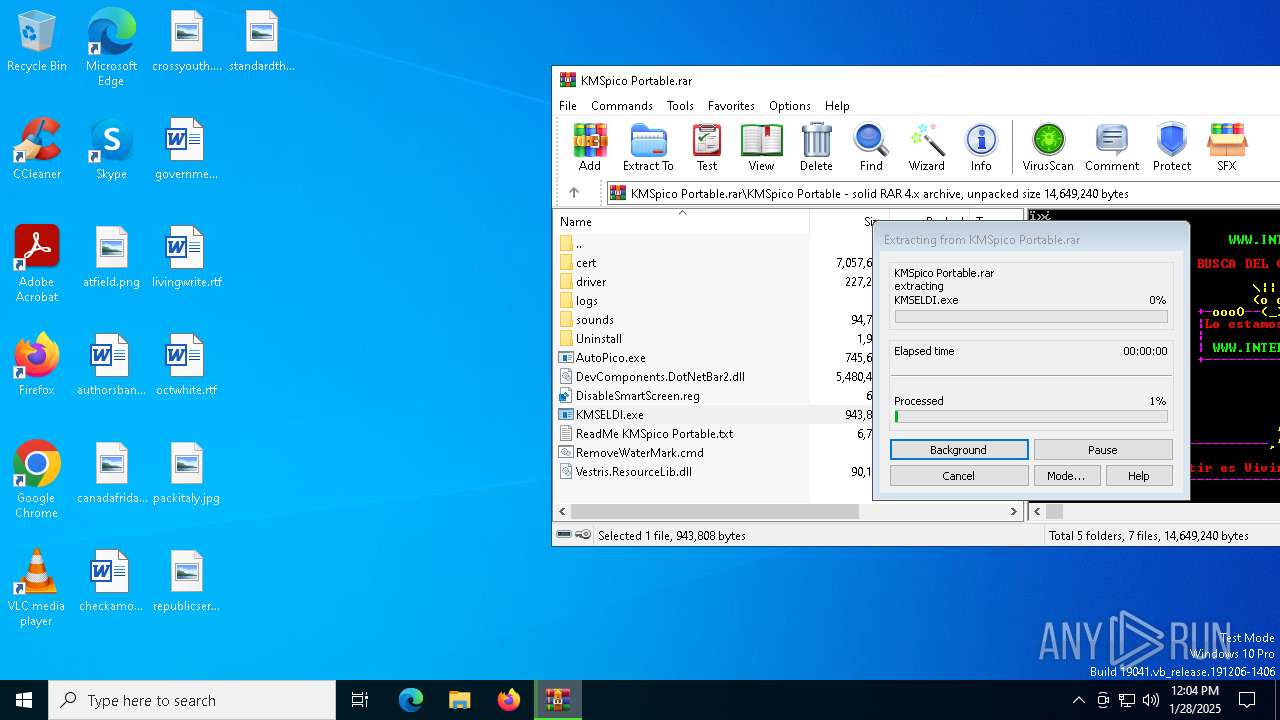
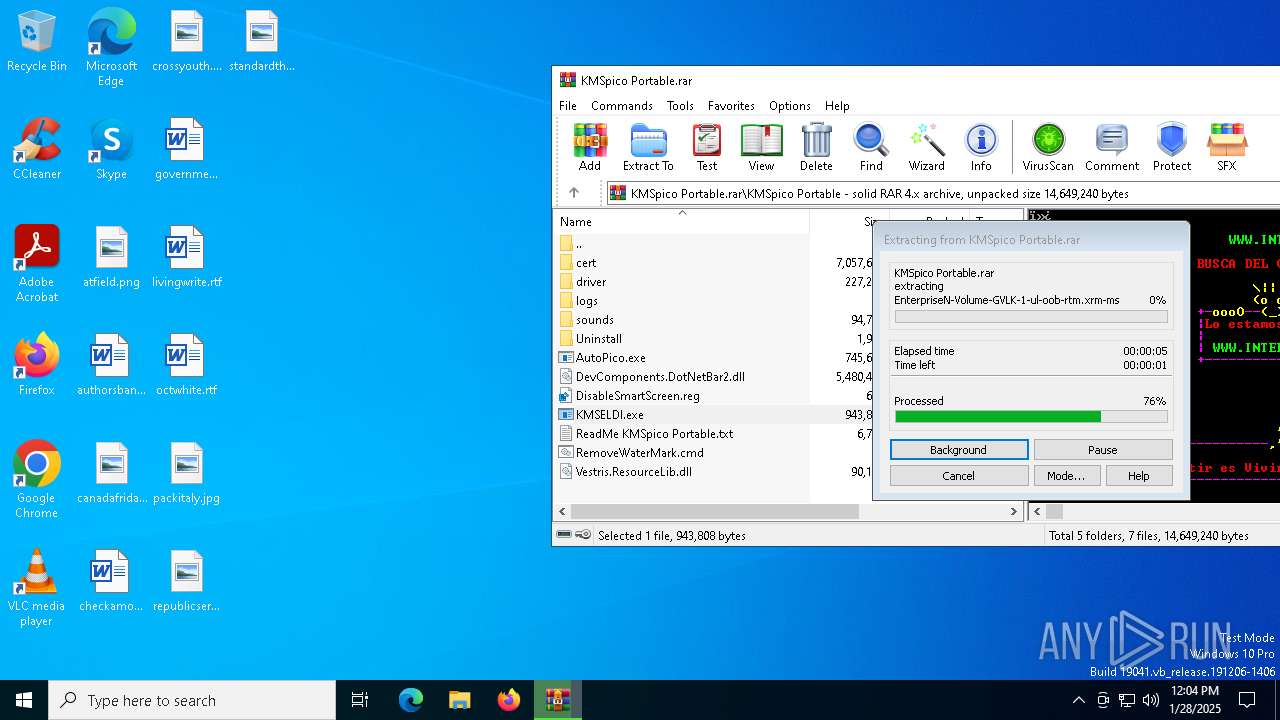
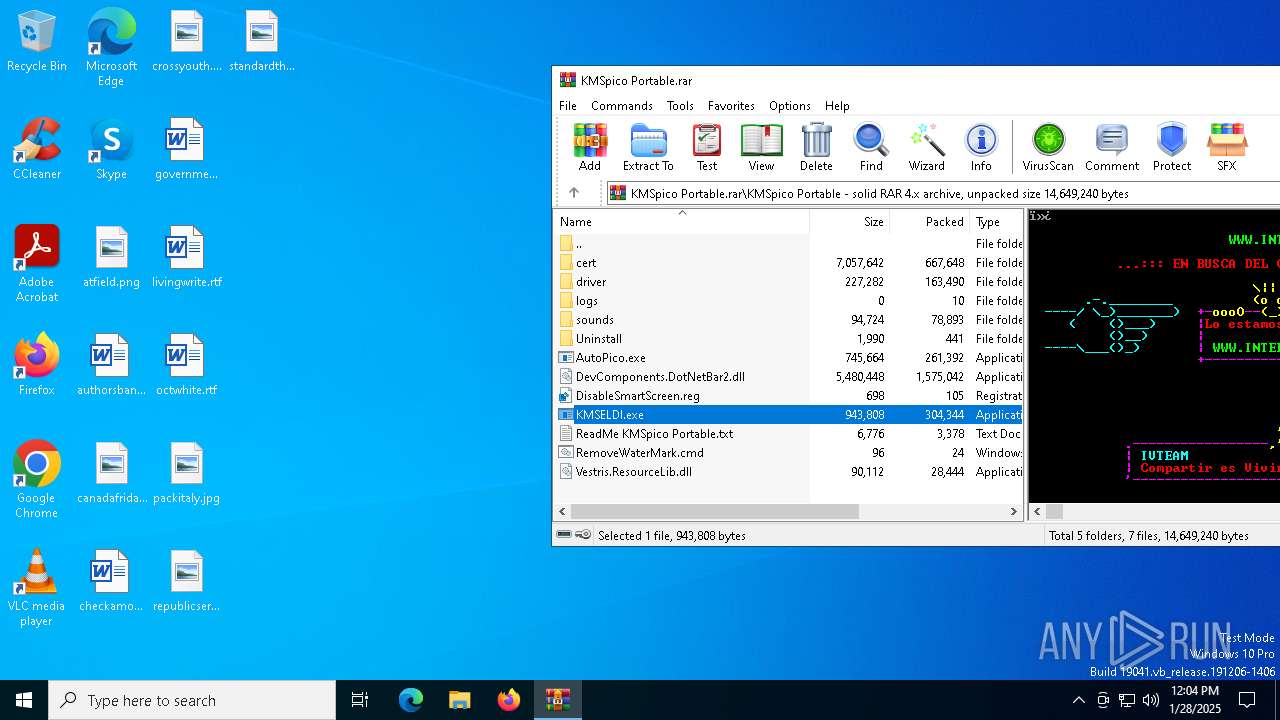
- KMSELDI.exe (PID: 6816)
- KMSELDI.exe (PID: 7008)
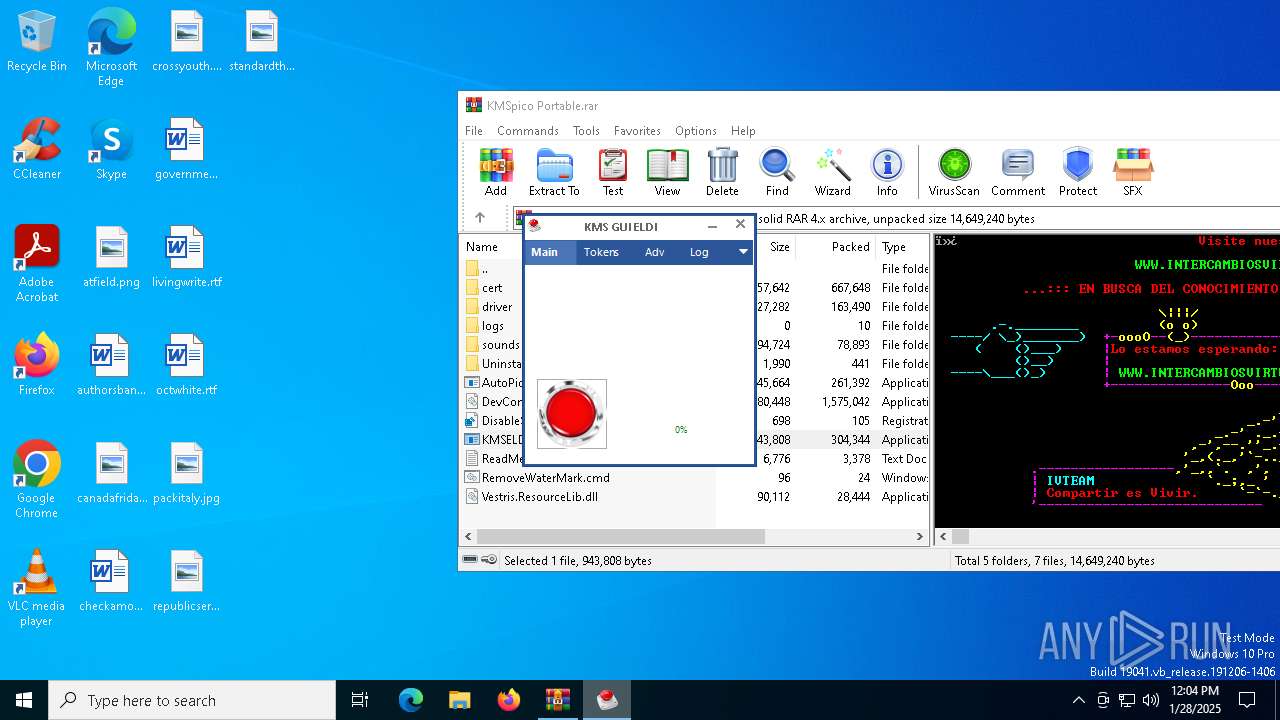
Generic archive extractor
- WinRAR.exe (PID: 6388)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6388)
Executable content was dropped or overwritten
- KMSELDI.exe (PID: 7008)
INFO
Reads product name
- KMSELDI.exe (PID: 7008)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 7008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6388)
Reads Environment values
- KMSELDI.exe (PID: 7008)
Checks supported languages
- KMSELDI.exe (PID: 7008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 3448 |
| UncompressedSize: | 6776 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:01:11 23:45:04 |
| PackingMethod: | Best Compression |
| ArchivedFileName: | KMSpico Portable\ReadMe KMSpico Portable.txt |
Total processes
134
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMSpico Portable.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6816 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\KMSELDI.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\KMSELDI.exe | — | WinRAR.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: KMS GUI ELDI Exit code: 3221226540 Version: 37.1.0.0 Modules
| |||||||||||||||
| 7008 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\KMSELDI.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\KMSELDI.exe | WinRAR.exe | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 0 Version: 37.1.0.0 Modules
| |||||||||||||||
Total events
4 636
Read events
4 562
Write events
72
Delete events
2
Modification events
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSpico Portable.rar | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7008) KMSELDI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\SECOH-QAD.exe | |||
| (PID) Process: | (7008) KMSELDI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\AudioCompressionManager\DriverCache\msacm.msg711 |
| Operation: | write | Name: | fdwSupport |
Value: 1 | |||
Executable files
7
Suspicious files
13
Text files
345
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\Uninstall\EnableSmartScreen.cmd | text | |
MD5:1306FC7DDF8FB649E1B3232FDEA0E7E8 | SHA256:C46A27E951658BB62D27496245A307713413E22762BAB12EDA98D15F6A796B88 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\cert\kmscert2010\Excel\ExcelVLReg32.reg | text | |
MD5:28BD0428CA20C5E612D7EC795BBB9EA9 | SHA256:3D1A428865F4F4FB5AFDB7CD69F0619C9A5F466EBA160F63DB8ED376C721563C | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\Uninstall\EnableSmartScreen.reg | text | |
MD5:7373D614601A1194BA33663C5547D85B | SHA256:FC8E4B0CA8392FBBEBB7D580D99A9FB03B19FBFEA04602E714B90C45D81B9116 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\Vestris.ResourceLib.dll | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\driver\tap-windows-9.21.0.exe | executable | |
MD5:05230AFDEEB13718E926FD654DE63F12 | SHA256:325222566DF55B85EEAE5247EC08BBF555BF2BDE00D14CB1A8CF323DF4A97C03 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\driver\OpenVPN.cer | binary | |
MD5:3D5FFD53BE77C32CBB147F32423C0A86 | SHA256:669C56DB590C0308EA25C4508375BB88611B06B1AE689A895DC6B19F4DF5619C | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\DisableSmartScreen.reg | text | |
MD5:98726CF4E77C2A5159801D4E888833DA | SHA256:20AEE3A1B0ECD68E642A5C8FF550D1525DF1C3F2FDA22B7DB51010947153FEBA | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\cert\kmscert2010\Access\AccessVLRegWOW.reg | text | |
MD5:50122EA723FFE7367AD811FC333594C2 | SHA256:18B8099777C8956C4299DA79A44BF9CB3ADDE96B652A0C6D063BF6C9A925B0B8 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\DevComponents.DotNetBar2.dll | executable | |
MD5:1397B23F30681F97049DF61F94F54D05 | SHA256:FA76151A783250014AC8FA55D4C833100A623FCAD1D6E2DDADCDE259F5709609 | |||
| 6388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6388.18671\KMSpico Portable\cert\kmscert2010\Access\AccessVLReg64.reg | text | |
MD5:3C688EC4EDC18A1FFA7EA020556504DB | SHA256:EE5C8D9592F48DEED26590C06756CC7EABF96ED0BEA56B8DD87EC6C80871B9B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5092 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
732 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
732 | svchost.exe | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
0.pool.ntp.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |