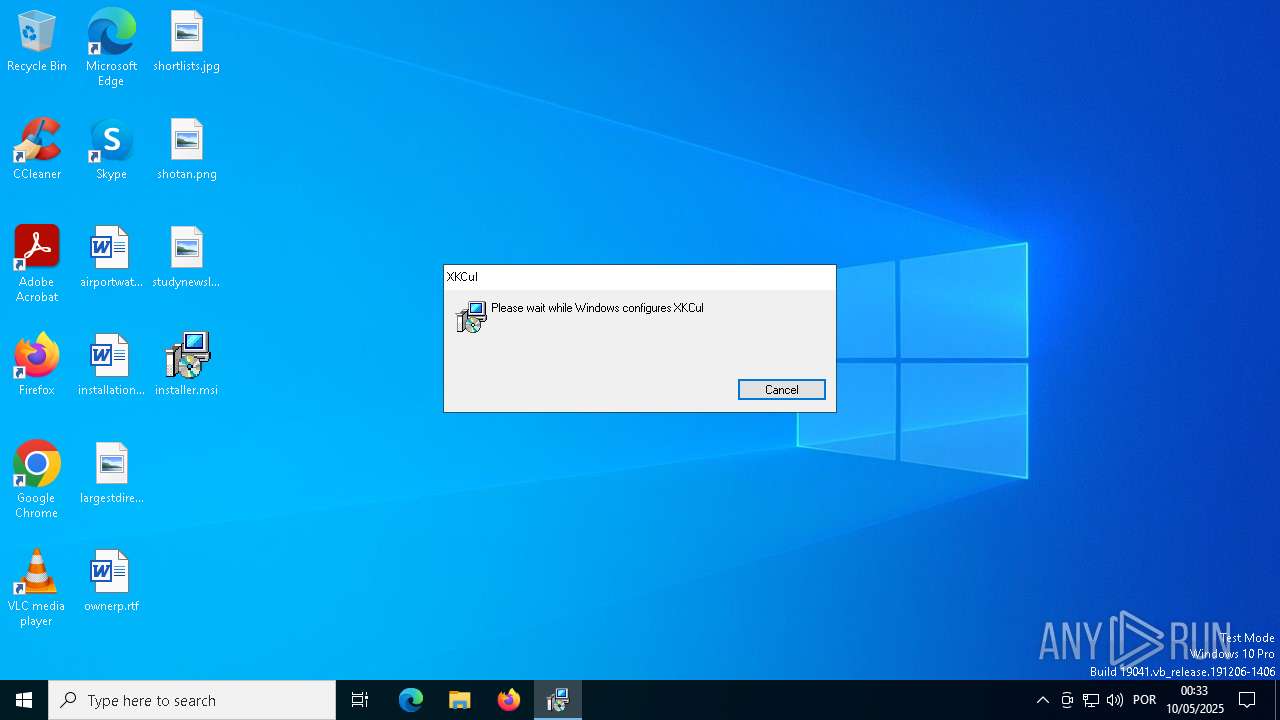
| File name: | installer.msi |
| Full analysis: | https://app.any.run/tasks/dd334329-4c52-4dc7-a7f0-6a800eeed7ce |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 03:32:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: XKCul, Author: nmweYOYspv, Keywords: Installer, Comments: This installer database contains the logic and data required to install XKCul., Template: Intel;1033, Revision Number: {5EF3F2C7-20CC-4C6B-9383-256B027B0519}, Create Time/Date: Thu May 8 12:53:08 2025, Last Saved Time/Date: Thu May 8 12:53:08 2025, Number of Pages: 200, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | C9F15A59C155B934A6A59802F8FF6AE7 |
| SHA1: | FFA38CF8F2EB664241A39A78CEBE55075F8D734B |
| SHA256: | 4C7A463B08571D7329206265BB1583250FBFC2D3EC9CF69B120C91F3049DB7E3 |
| SSDEEP: | 196608:QXFimfDj/fzO6FOXxRVF3A1xEv2dOip/ZkTko:QsUDjXS6FOXxRvA1J/ZkIo |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 4200)
Bypass execution policy to execute commands
- powershell.exe (PID: 2344)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3768)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 4200)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 4200)
The process executes Powershell scripts
- msiexec.exe (PID: 4200)
There is functionality for taking screenshot (YARA)
- ASCTray.exe (PID: 6632)
Executes application which crashes
- ASCTray.exe (PID: 6632)
The process executes via Task Scheduler
- SecureBootEncodeUEFI.exe (PID: 4180)
- PLUGScheduler.exe (PID: 2264)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 6744)
- msiexec.exe (PID: 4200)
Reads the computer name
- msiexec.exe (PID: 4200)
Checks supported languages
- msiexec.exe (PID: 4200)
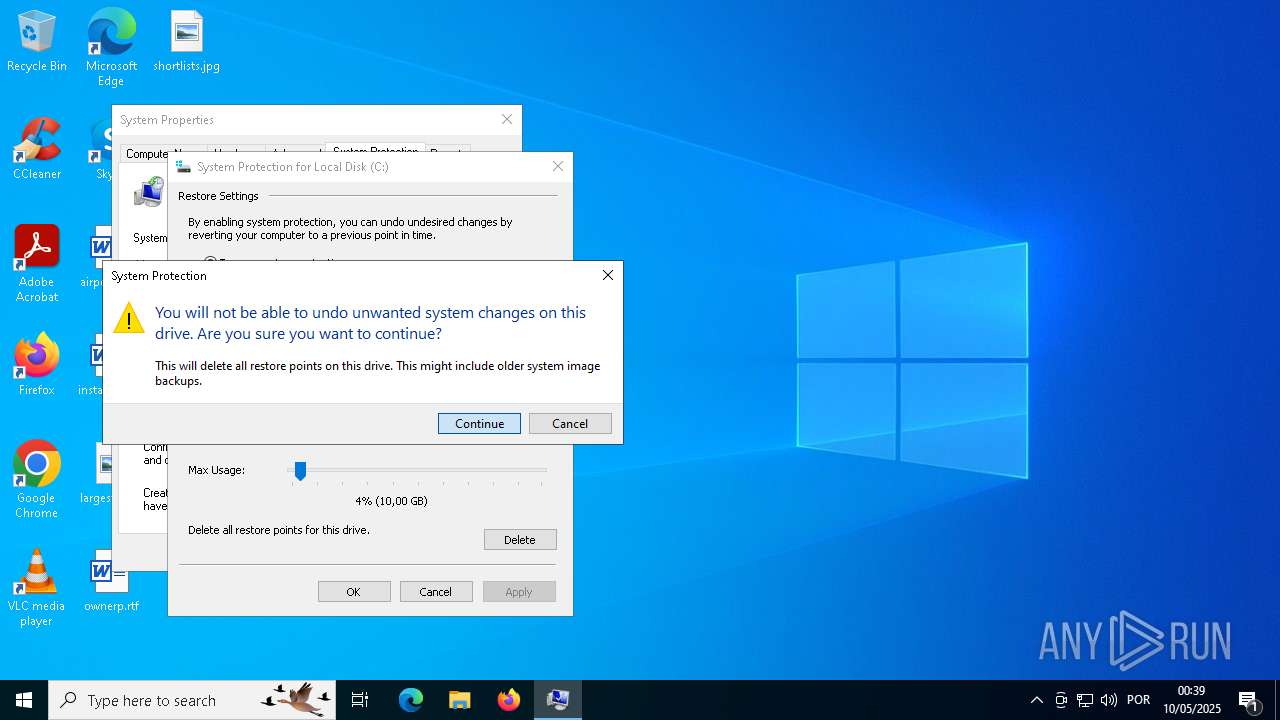
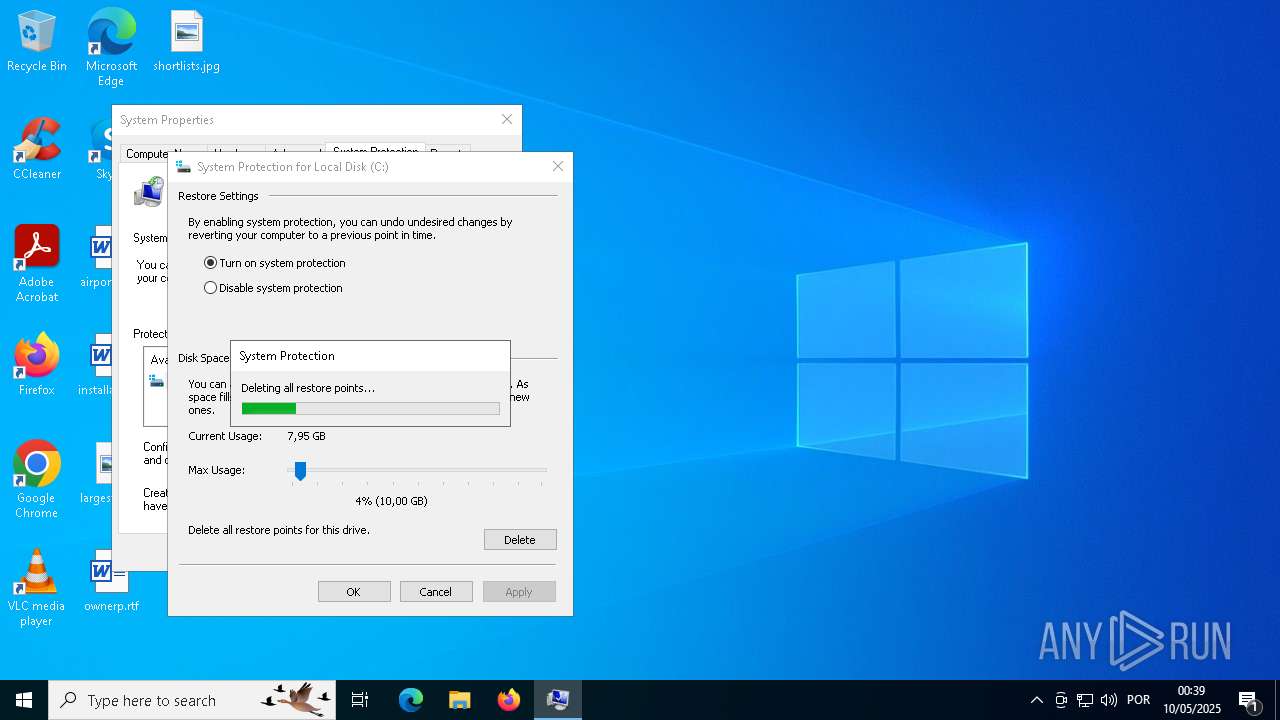
Manages system restore points
- SrTasks.exe (PID: 3332)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4200)
Compiled with Borland Delphi (YARA)
- ASCTray.exe (PID: 6632)
Manual execution by a user
- control.exe (PID: 6624)
Encodes the UEFI Secure Boot certificates
- SecureBootEncodeUEFI.exe (PID: 4180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | XKCul |
| Author: | nmweYOYspv |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install XKCul. |
| Template: | Intel;1033 |
| RevisionNumber: | {5EF3F2C7-20CC-4C6B-9383-256B027B0519} |
| CreateDate: | 2025:05:08 12:53:08 |
| ModifyDate: | 2025:05:08 12:53:08 |
| Pages: | 200 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
445
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | "C:\ProgramData\Obit-3091\DiskDefrag_16933.exe" | C:\ProgramData\Obit-3091\DiskDefrag_16933.exe | — | powershell.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Advanced SystemCare Disk Defrag Exit code: 0 Version: 1.0.0.11 Modules
| |||||||||||||||
| 1880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SecureBootEncodeUEFI.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\ProgramData\Obit-3091\ASCTray.exe" /diskdefrag | C:\ProgramData\Obit-3091\ASCTray.exe | — | DiskDefrag_16933.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Advanced SystemCare Tray Exit code: 0 Version: 18.0.0.1034 Modules
| |||||||||||||||
| 2264 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | powershell.exe -NoProfile -ExecutionPolicy Bypass -File ".\run_hidden.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3768 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6632 -s 1148 | C:\Windows\SysWOW64\WerFault.exe | — | ASCTray.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\WINDOWS\system32\SecureBootEncodeUEFI.exe" | C:\Windows\System32\SecureBootEncodeUEFI.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Secure Boot UEFI Encoder Exit code: 3221225728 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 553
Read events
13 255
Write events
280
Delete events
18
Modification events
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000514ABB3B5CC1DB016810000004170000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000514ABB3B5CC1DB016810000004170000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000931F113C5CC1DB016810000004170000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000931F113C5CC1DB016810000004170000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000074AE1A3C5CC1DB016810000004170000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000E5611F3C5CC1DB016810000004170000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000F054A73C5CC1DB016810000004170000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002C1BAC3C5CC1DB0168100000A8120000E80300000100000000000000000000001A8A99984B365E48AF9C7DD09FC3D66A00000000000000000000000000000000 | |||
| (PID) Process: | (3768) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000085FFB73C5CC1DB01B80E0000001A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
13
Suspicious files
68
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4200 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4200 | msiexec.exe | C:\Windows\Installer\112b14.msi | — | |
MD5:— | SHA256:— | |||
| 4200 | msiexec.exe | C:\ProgramData\Obit-3091\asas.dmp | — | |
MD5:— | SHA256:— | |||
| 4200 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:0A432208C992CFEA514CC557968D6062 | SHA256:5BC578A9B88DB0530FD082E37A997410CDF26BDBF1BA1645CA99E8EDA71F21A5 | |||
| 4200 | msiexec.exe | C:\Windows\Installer\MSI2D76.tmp | binary | |
MD5:1E2D66D3E59EA47F1137EFE3687BC312 | SHA256:17F863319EB2C72B58994373A0197D90D71887D2F93D1ABA44C54ED70EBDD6B3 | |||
| 4200 | msiexec.exe | C:\Windows\Installer\112b16.msi | — | |
MD5:— | SHA256:— | |||
| 4200 | msiexec.exe | C:\ProgramData\Obit-3091\rtl120.bpl | executable | |
MD5:4F2040ADD9F5B541DB07A2E866E2C5CA | SHA256:B3DEE68AF7B2805F6CF74976B60564DCC7D6D38444078D32CDCA99EE1BB5BB22 | |||
| 4200 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{98998a1a-364b-485e-af9c-7dd09fc3d66a}_OnDiskSnapshotProp | binary | |
MD5:FCDC1AB1792FBFDDBE142C426C6853B6 | SHA256:BE9BA596FBF6263087CB95AA4D7B437FB062FF438F0C70F97D30AA8E4973DB00 | |||
| 4200 | msiexec.exe | C:\Windows\Temp\~DF95068F8595813EC3.TMP | binary | |
MD5:0A432208C992CFEA514CC557968D6062 | SHA256:5BC578A9B88DB0530FD082E37A997410CDF26BDBF1BA1645CA99E8EDA71F21A5 | |||
| 4200 | msiexec.exe | C:\ProgramData\Obit-3091\SQLite3.dll | executable | |
MD5:017DB2D24CA200CBCB6DBA6BB0464554 | SHA256:8123BB90D7BEB8D2814F9602A0273467402BDFF13E67C8442D0509438F28462A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
251
TCP/UDP connections
204
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
856 | SIHClient.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
856 | SIHClient.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
856 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
856 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
856 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 40.69.42.241:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
856 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
856 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2028 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
856 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |