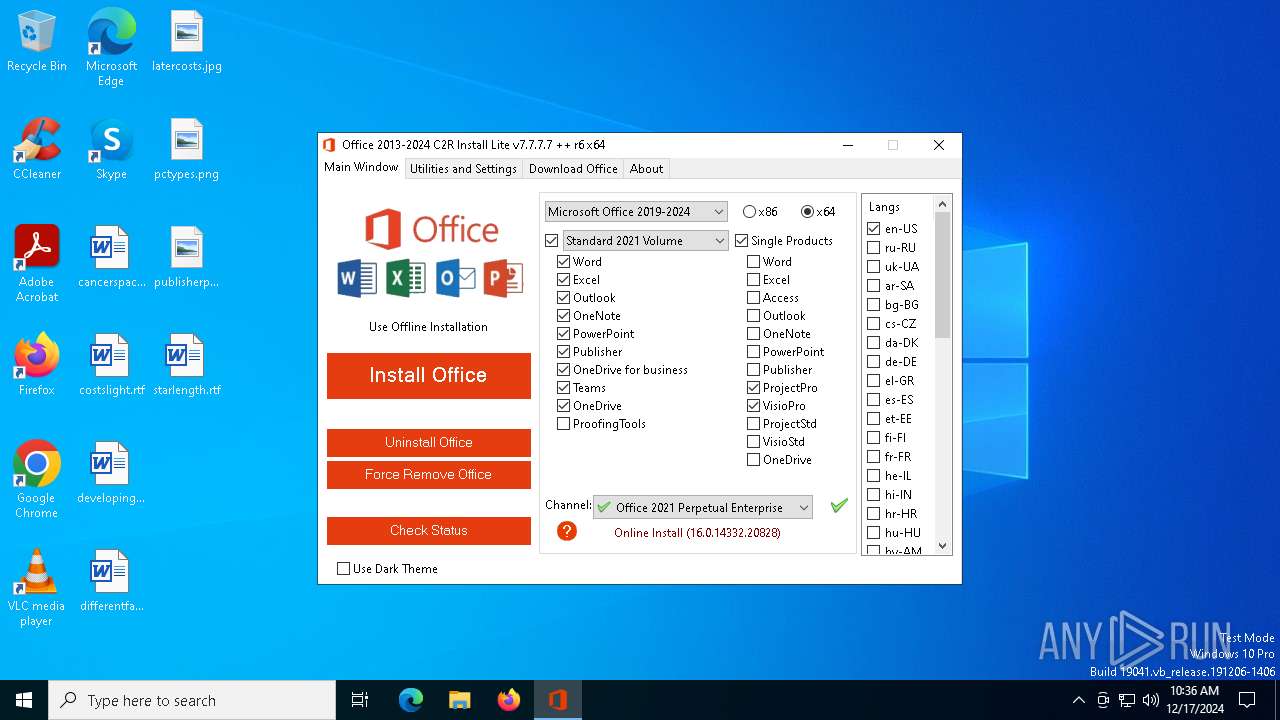
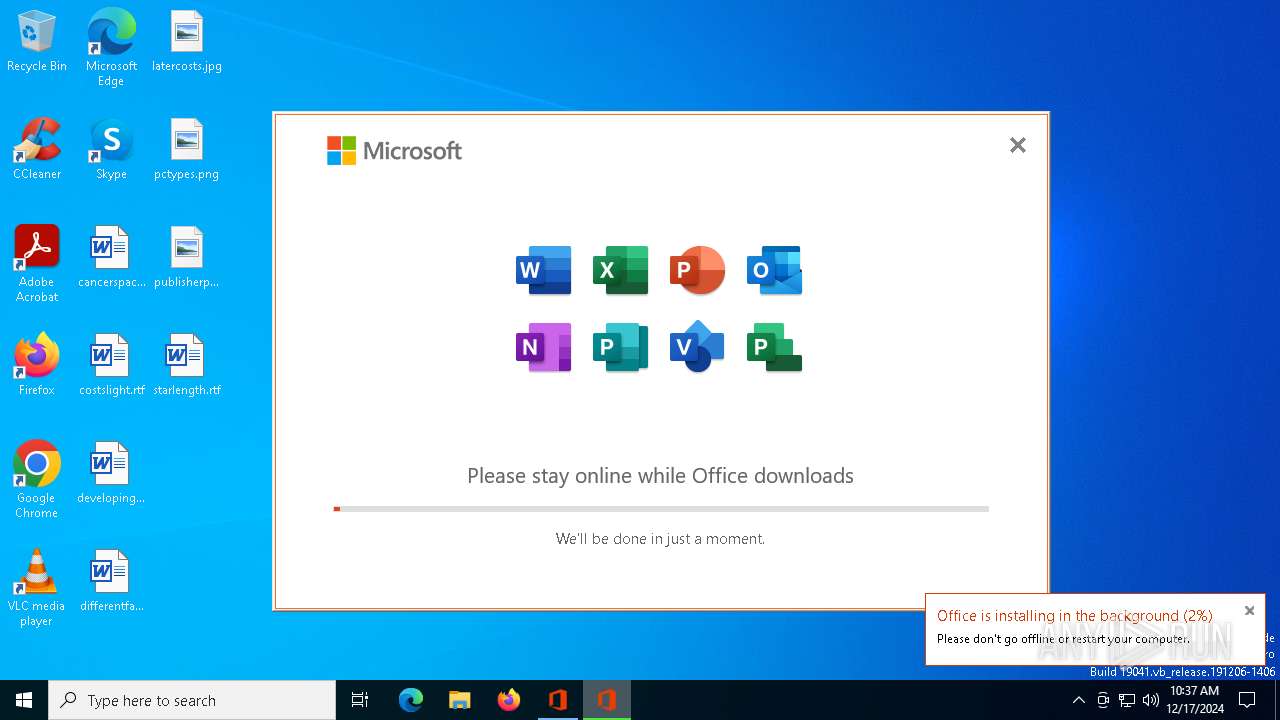
| File name: | OInstallLite_x64.exe |
| Full analysis: | https://app.any.run/tasks/644e67fa-d652-4853-899e-4d62a9419b5e |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | December 17, 2024, 10:35:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 54ED82C9A96FAB05860D449EF6AD66C1 |
| SHA1: | B870D4A6832B87C150D5609CAAF6060EDEEE31B0 |
| SHA256: | 4C3BB0D872AFD14CB7AD2ABABC48098F4D11D55F14C93BE4E26D249B41FCACEC |
| SSDEEP: | 98304:Hr70fBbzKtHucp+r4laH0hWD9yfsIB+O7xEjeA6aKJqMBOQr0W9TX62Ap4oj/Hdb:kW9l7 |
MALICIOUS
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6444)
- cmd.exe (PID: 6772)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6928)
- powershell.exe (PID: 5496)
- powershell.exe (PID: 4076)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- OInstallLite_x64.exe (PID: 6408)
Found strings related to reading or modifying Windows Defender settings
- OInstallLite_x64.exe (PID: 6408)
Executable content was dropped or overwritten
- OInstallLite_x64.exe (PID: 6408)
- files.dat (PID: 6628)
- expand.exe (PID: 6956)
Uses REG/REGEDIT.EXE to modify registry
- OInstallLite_x64.exe (PID: 6408)
Starts CMD.EXE for commands execution
- OInstallLite_x64.exe (PID: 6408)
Starts application with an unusual extension
- cmd.exe (PID: 6564)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 6628)
Process drops legitimate windows executable
- files.dat (PID: 6628)
- expand.exe (PID: 6956)
The process drops C-runtime libraries
- files.dat (PID: 6628)
- expand.exe (PID: 6956)
The process bypasses the loading of PowerShell profile settings
- OInstallLite_x64.exe (PID: 6408)
Starts POWERSHELL.EXE for commands execution
- OInstallLite_x64.exe (PID: 6408)
Executes script without checking the security policy
- powershell.exe (PID: 6928)
Probably download files using WebClient
- OInstallLite_x64.exe (PID: 6408)
Starts SC.EXE for service management
- cmd.exe (PID: 6824)
Unpacks CAB file
- expand.exe (PID: 6956)
- expand.exe (PID: 4640)
Uses TASKKILL.EXE to kill process
- OInstallLite_x64.exe (PID: 6408)
Reads security settings of Internet Explorer
- OInstallLite_x64.exe (PID: 6408)
- OfficeC2RClient.exe (PID: 5904)
Reads the date of Windows installation
- OInstallLite_x64.exe (PID: 6408)
INFO
Reads Microsoft Office registry keys
- OInstallLite_x64.exe (PID: 6408)
- OfficeClickToRun.exe (PID: 6776)
- OfficeClickToRun.exe (PID: 6656)
- OfficeC2RClient.exe (PID: 5904)
Checks supported languages
- OInstallLite_x64.exe (PID: 6408)
- files.dat (PID: 6628)
- expand.exe (PID: 6956)
- OfficeClickToRun.exe (PID: 6776)
- OfficeClickToRun.exe (PID: 6656)
Reads Environment values
- OInstallLite_x64.exe (PID: 6408)
The sample compiled with english language support
- OInstallLite_x64.exe (PID: 6408)
- files.dat (PID: 6628)
- expand.exe (PID: 6956)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6556)
- WMIC.exe (PID: 6832)
Create files in a temporary directory
- files.dat (PID: 6628)
- OInstallLite_x64.exe (PID: 6408)
- OfficeC2RClient.exe (PID: 5904)
Reads the computer name
- OInstallLite_x64.exe (PID: 6408)
Disables trace logs
- powershell.exe (PID: 6928)
- powershell.exe (PID: 5496)
- powershell.exe (PID: 4076)
Checks proxy server information
- powershell.exe (PID: 6928)
- powershell.exe (PID: 5496)
- powershell.exe (PID: 4076)
- OfficeClickToRun.exe (PID: 6656)
- OfficeClickToRun.exe (PID: 6776)
- OfficeC2RClient.exe (PID: 5904)
Reads the machine GUID from the registry
- expand.exe (PID: 6956)
- OfficeClickToRun.exe (PID: 6776)
The sample compiled with bulgarian language support
- expand.exe (PID: 6956)
Creates files in the program directory
- expand.exe (PID: 6956)
- expand.exe (PID: 4640)
- OfficeClickToRun.exe (PID: 6776)
The sample compiled with arabic language support
- expand.exe (PID: 6956)
The sample compiled with czech language support
- expand.exe (PID: 6956)
The sample compiled with spanish language support
- expand.exe (PID: 6956)
The sample compiled with german language support
- expand.exe (PID: 6956)
The sample compiled with japanese language support
- expand.exe (PID: 6956)
The sample compiled with french language support
- expand.exe (PID: 6956)
The sample compiled with Indonesian language support
- expand.exe (PID: 6956)
The sample compiled with Italian language support
- expand.exe (PID: 6956)
The sample compiled with slovak language support
- expand.exe (PID: 6956)
The sample compiled with korean language support
- expand.exe (PID: 6956)
The sample compiled with polish language support
- expand.exe (PID: 6956)
The sample compiled with russian language support
- expand.exe (PID: 6956)
The sample compiled with turkish language support
- expand.exe (PID: 6956)
The sample compiled with swedish language support
- expand.exe (PID: 6956)
The sample compiled with chinese language support
- expand.exe (PID: 6956)
The sample compiled with portuguese language support
- expand.exe (PID: 6956)
The process uses the downloaded file
- OInstallLite_x64.exe (PID: 6408)
Process checks computer location settings
- OInstallLite_x64.exe (PID: 6408)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 6776)
Creates files or folders in the user directory
- OfficeClickToRun.exe (PID: 6656)
- OfficeC2RClient.exe (PID: 5904)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 6776)
Manual execution by a user
- OfficeC2RClient.exe (PID: 5904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:04:13 05:34:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 1411584 |
| InitializedDataSize: | 10929152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.7.7.7 |
| ProductVersionNumber: | 7.7.7.7 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| ProductName: | Office 2013-2024 C2R Install Lite |
| FileDescription: | Office 2013-2024 C2R Install Lite |
Total processes
178
Monitored processes
49
Malicious processes
2
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | sc.exe stop ClickToRunSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "taskkill.exe" /t /f /IM IntegratedOffice.exe | C:\Windows\System32\taskkill.exe | — | OInstallLite_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | "C:\WINDOWS\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v KeyManagementServiceName /t REG_SZ /d kms.loli.best /f | C:\Windows\System32\reg.exe | — | OInstallLite_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3436 | "C:\WINDOWS\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v KeyManagementServicePort /t REG_SZ /d 1688 /f | C:\Windows\System32\reg.exe | — | OInstallLite_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3440 | C:\WINDOWS\system32\DllHost.exe /Processid:{338B40F9-9D68-4B53-A793-6B9AA0C5F63B} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20828/i641033.cab', 'C:\Users\admin\AppData\Local\Temp\over644176\i641033.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstallLite_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4468 | "C:\WINDOWS\System32\cmd.exe" /D /c regedit.exe -s C:\Users\admin\AppData\Local\Temp\newui.reg | C:\Windows\System32\cmd.exe | — | OInstallLite_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | "C:\WINDOWS\System32\reg.exe" add "HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v KeyManagementServicePort /t REG_SZ /d 1688 /f | C:\Windows\System32\reg.exe | — | OInstallLite_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 637
Read events
67 325
Write events
203
Delete events
109
Modification events
| (PID) Process: | (6472) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6408) OInstallLite_x64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (5592) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: kms.loli.best | |||
| (PID) Process: | (6512) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Office\16.0\Common\OfficeUpdate |
| Operation: | write | Name: | UpdateBranch |
Value: PerpetualVL2021 | |||
| (PID) Process: | (4548) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (6536) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRefresh |
Value: true | |||
| (PID) Process: | (6536) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.RibbonTouchOptimization |
Value: true | |||
| (PID) Process: | (6536) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRibbonOptionsMenu |
Value: true | |||
| (PID) Process: | (6536) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\excel |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRefresh |
Value: true | |||
| (PID) Process: | (6536) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\excel |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.RibbonTouchOptimization |
Value: true | |||
Executable files
225
Suspicious files
80
Text files
77
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5496 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over644176\i640.cab | — | |
MD5:— | SHA256:— | |||
| 6408 | OInstallLite_x64.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:46C7CEAD7726B1530BB4C096A648137E | SHA256:BF9CA6C946B42346C8E4B5B1EDCEAA9385069F680F53BEA30C9B16529C39EA8B | |||
| 6956 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:B9BC664A451424342A73A8B12918F88D | SHA256:0C5C4DFEA72595FB7AE410F8FA8DA983B53A83CE81AEA144FA20CAB613E641B7 | |||
| 6408 | OInstallLite_x64.exe | C:\Users\admin\AppData\Local\Temp\newui.reg | text | |
MD5:7FB2BDA7CA25568909EAB0B872416ADA | SHA256:92DC5F009E30E42D18B80FDCCE0E029DF6D56E387EB38E16C5585A9C5A0B41A7 | |||
| 6956 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:ADB3471F89E47CD93B6854D629906809 | SHA256:355633A84DB0816AB6A340A086FB41C65854C313BD08D427A17389C42A1E5B69 | |||
| 6956 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:19DF2B0F78DC3D8C470E836BAE85E1FF | SHA256:BD9E07BBC62CE82DBC30C23069A17FBFA17F1C26A9C19E50FE754D494E6CD0B1 | |||
| 6628 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 6628 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\cleanospp.exe | executable | |
MD5:D3467CB7B83B654C2D05407DC7BA2360 | SHA256:EDF85F4E2EF1A427B34265A22F261D664EC78DE90C3B5DA4174EF28558C8522A | |||
| 6408 | OInstallLite_x64.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:BB5569B15D68C10B7FF2D96B45825120 | SHA256:4E3B13B56BEC0E41778E6506430282BBBD75CCAA600FD4B645CE37DD95B44C8E | |||
| 6628 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:98821A7A5737D656633D10A3AFB724BD | SHA256:04BA4487F95290E0B0557B44300C18F637FBAF0872EE96E3111013B8A1539F25 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2 034
TCP/UDP connections
148
DNS requests
79
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | powershell.exe | GET | 200 | 23.48.23.64:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20828/i640.cab | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3612 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3612 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4076 | powershell.exe | GET | 200 | 23.48.23.7:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20828/i641033.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3700 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.64:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |