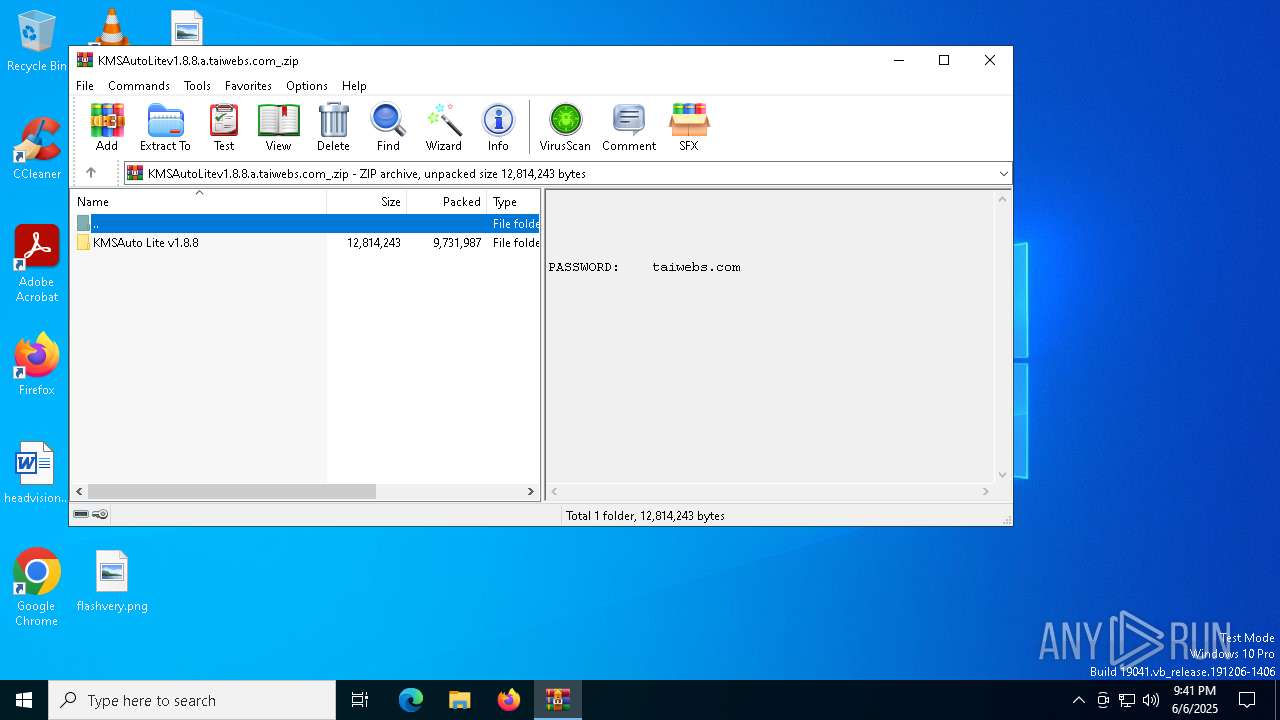
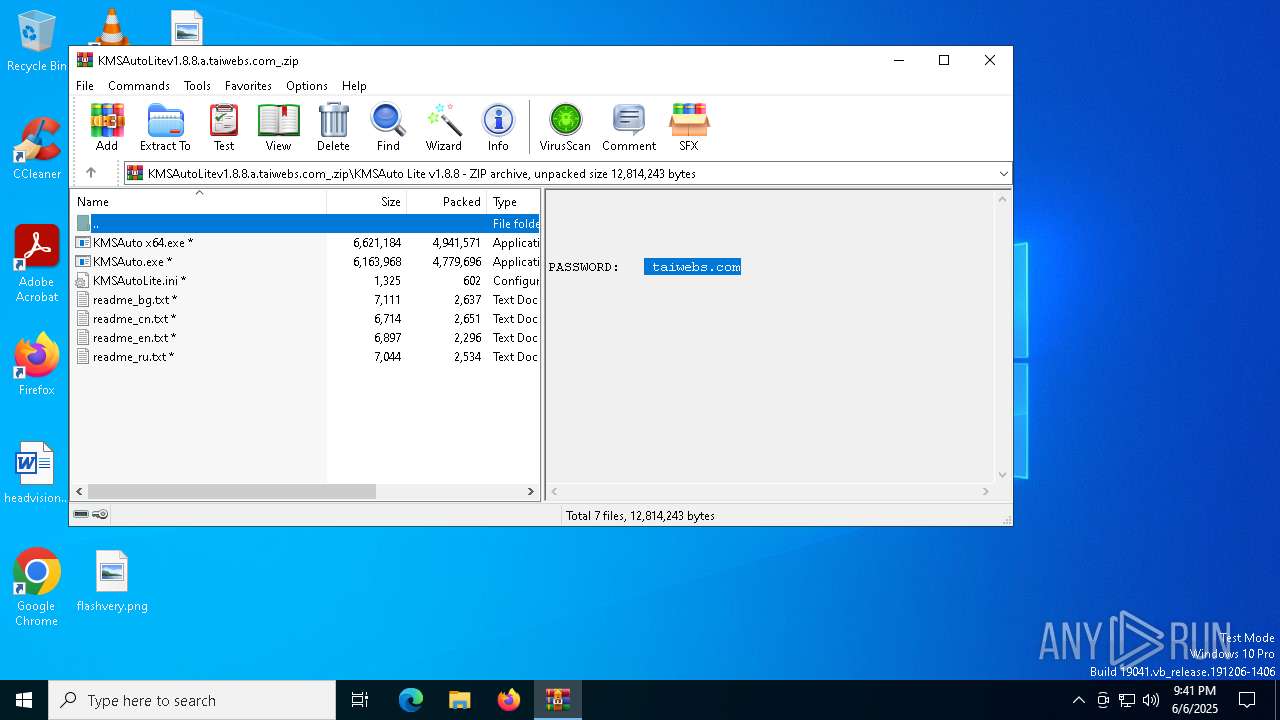
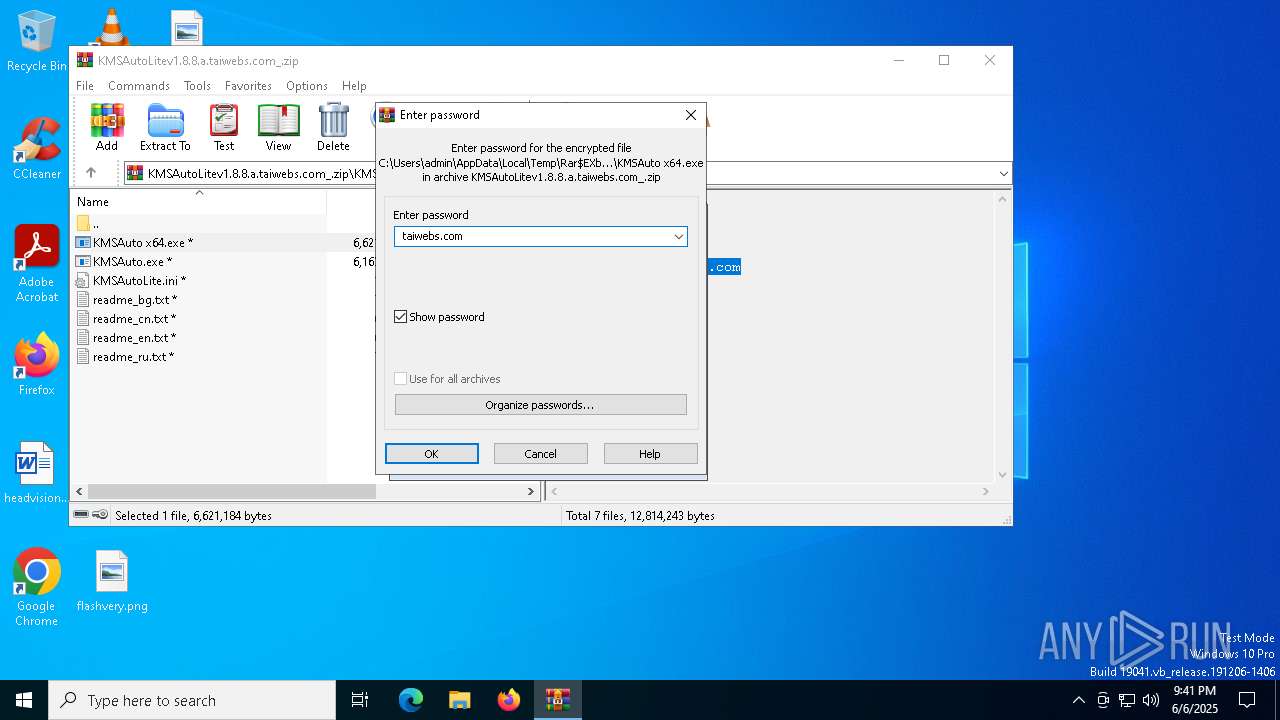
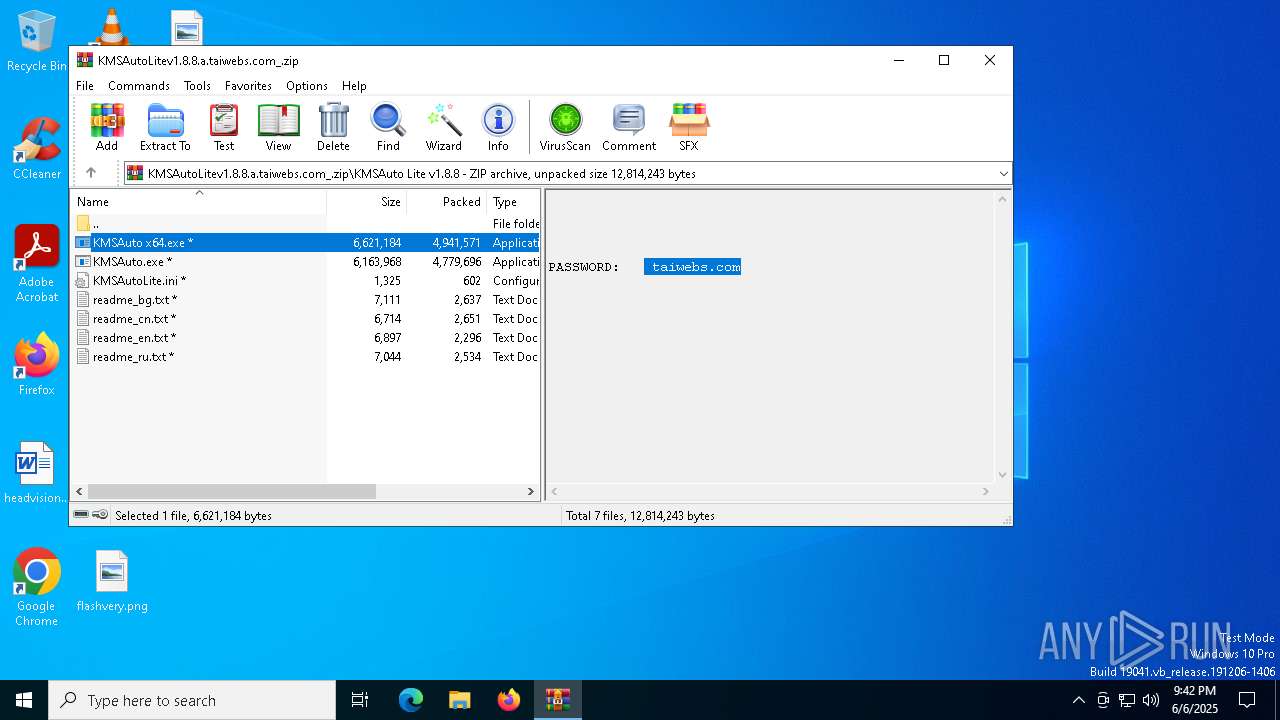
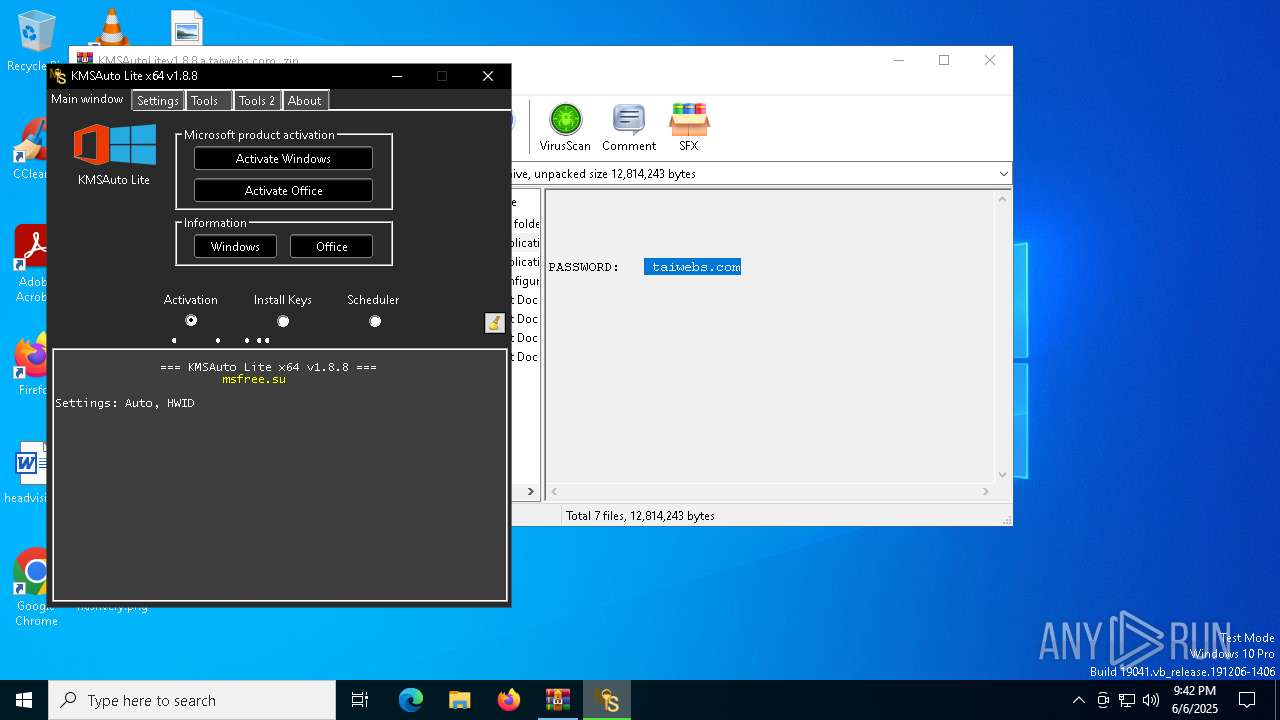
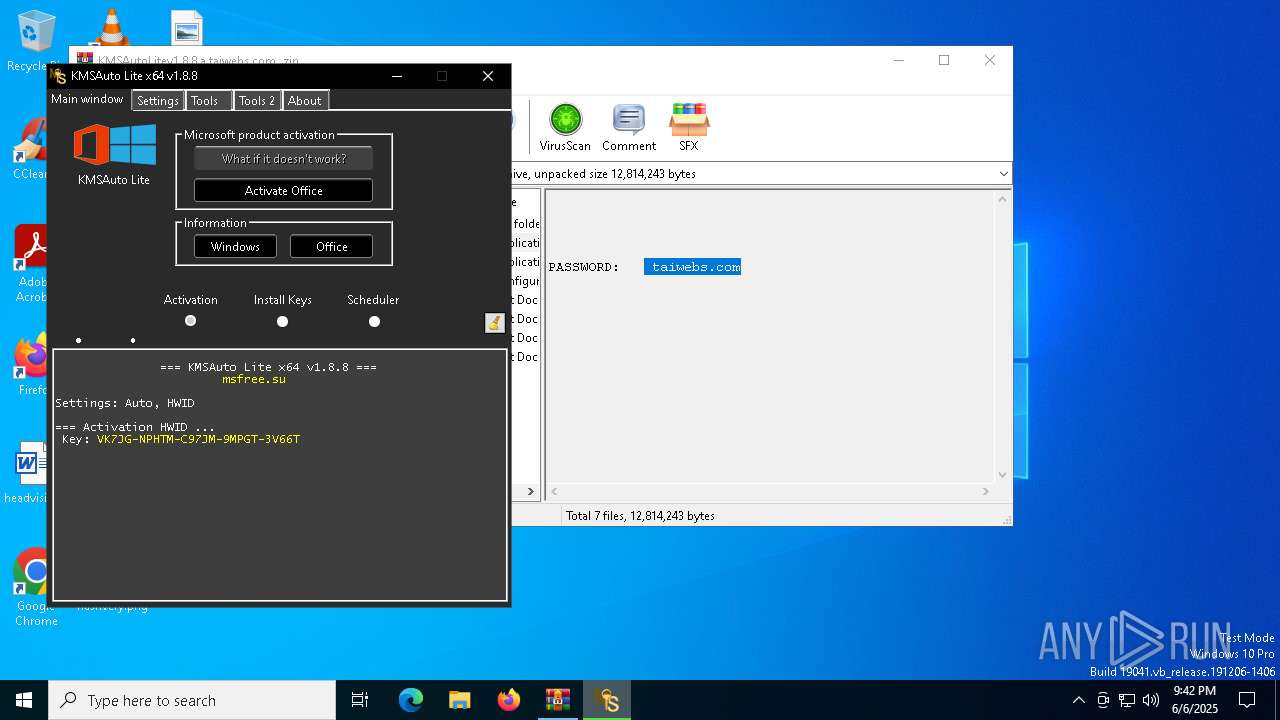
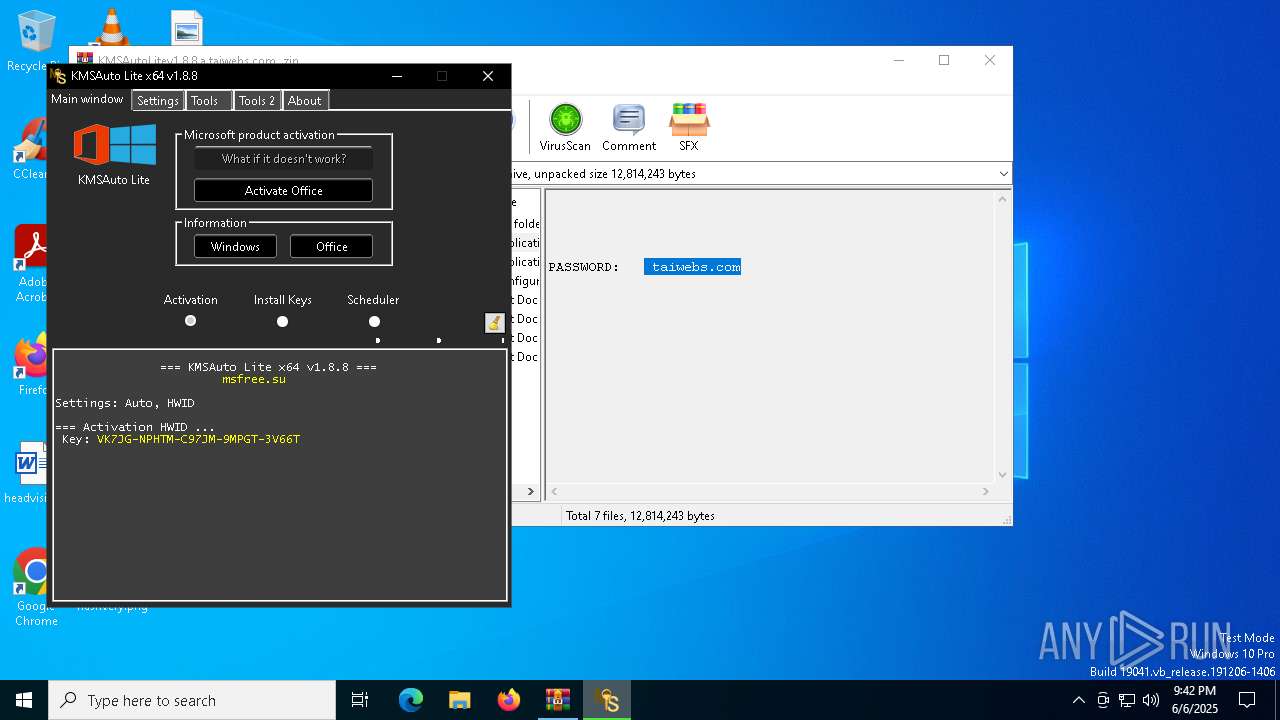
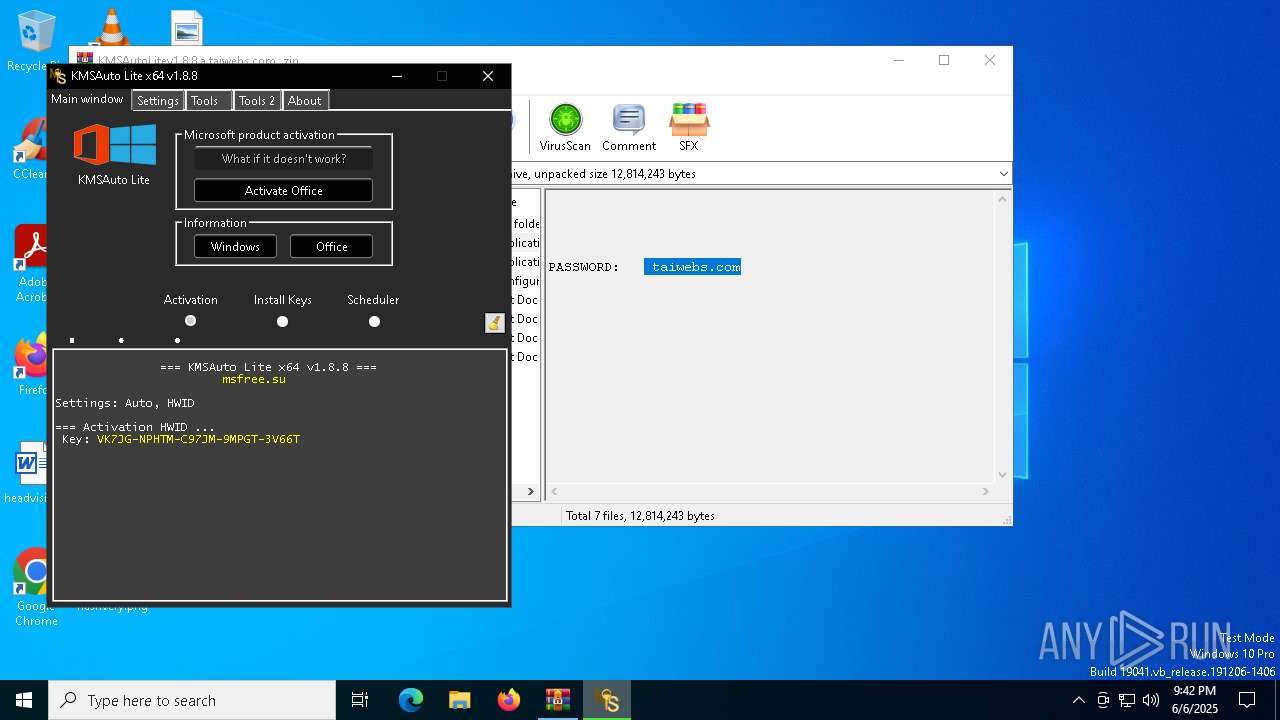
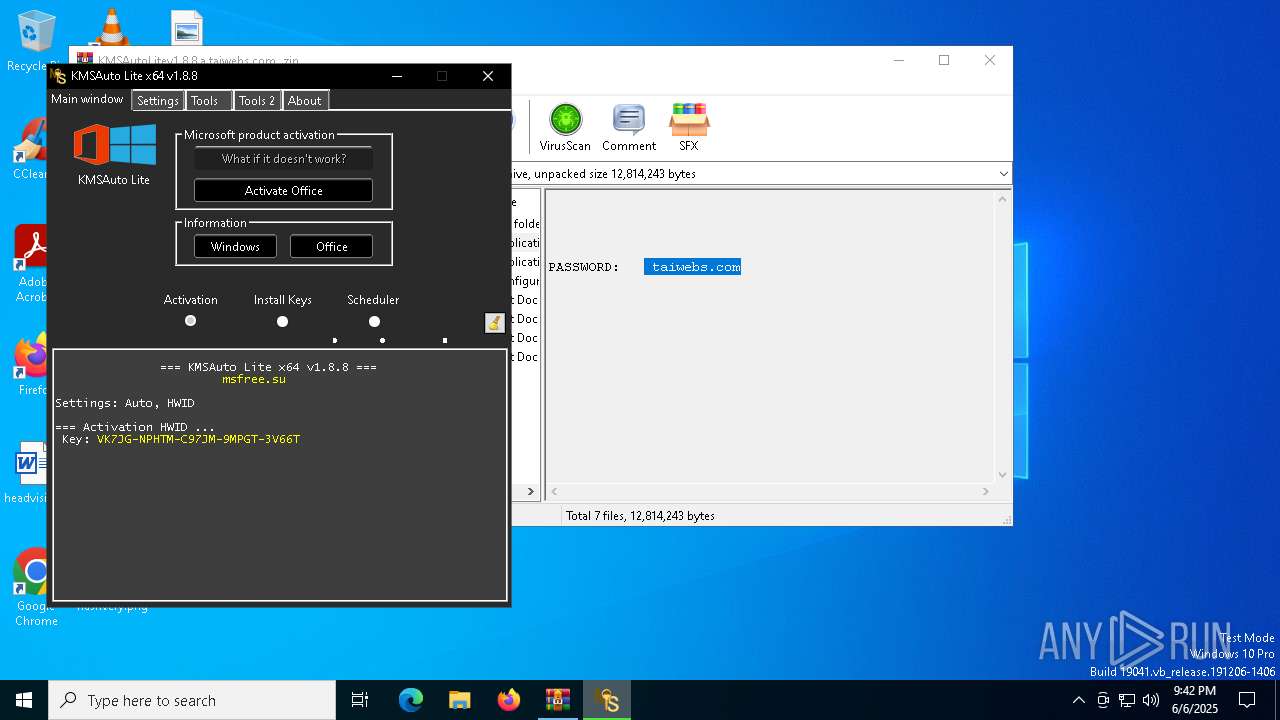
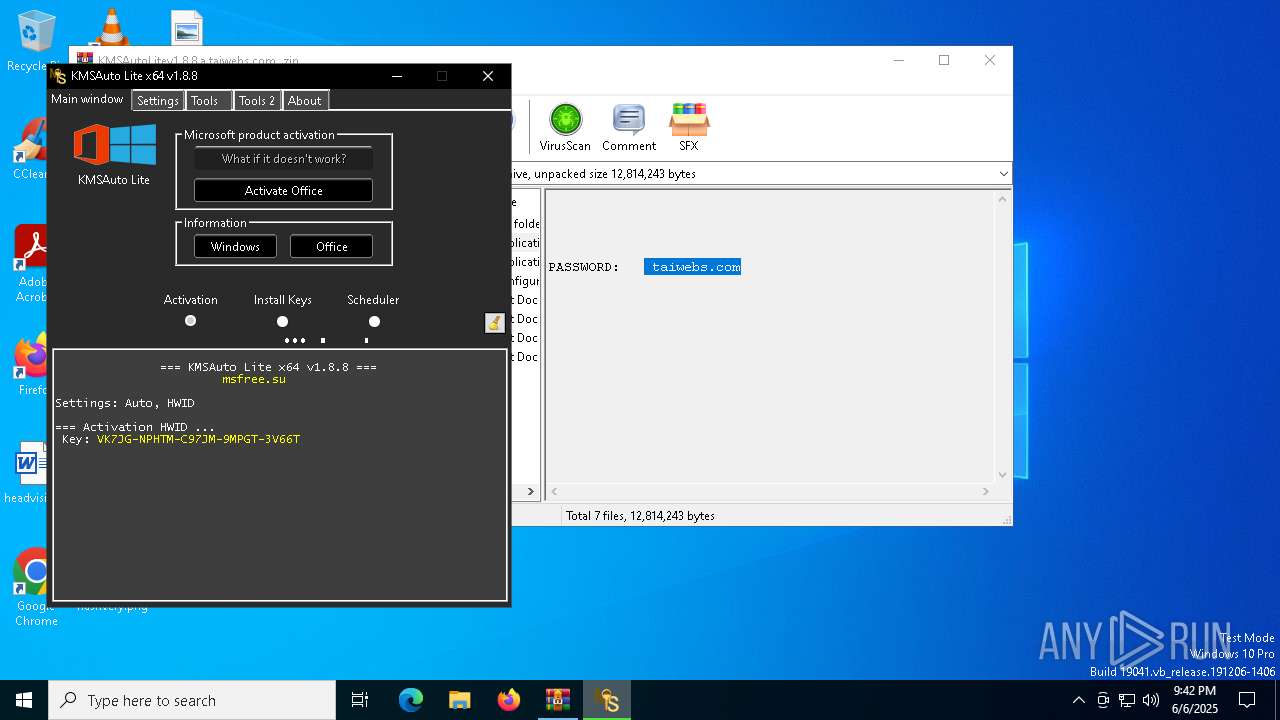
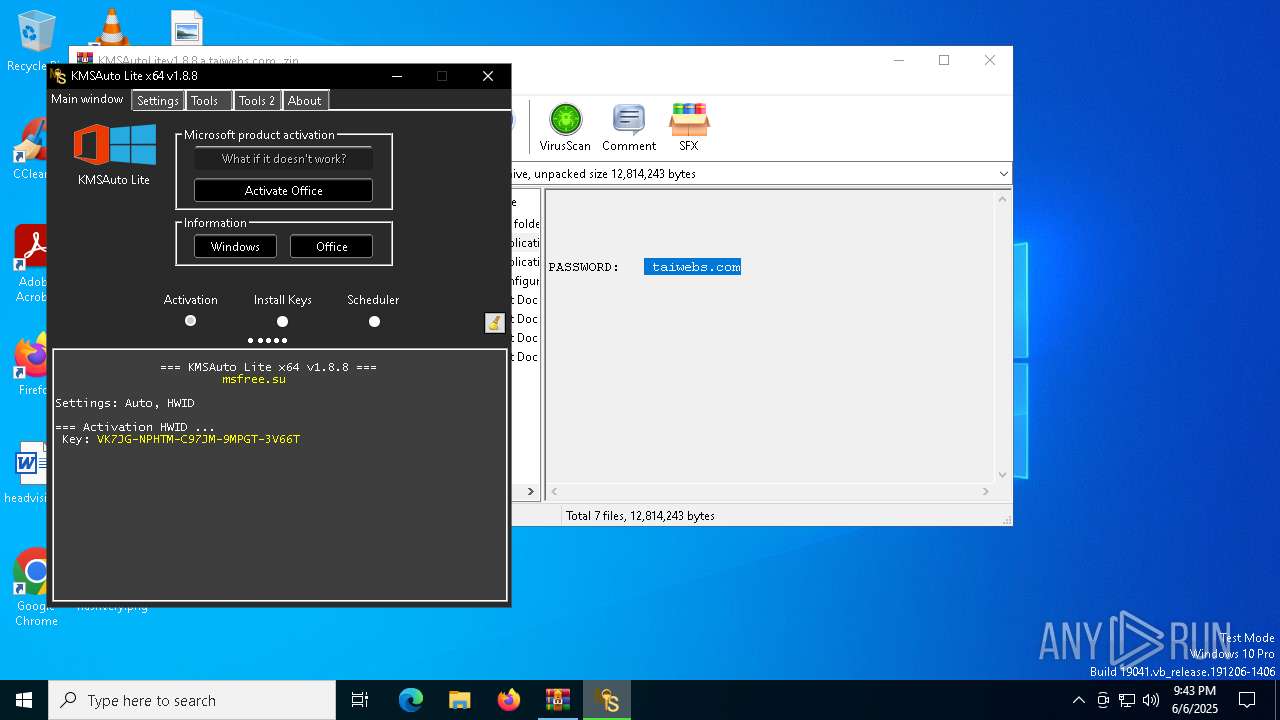
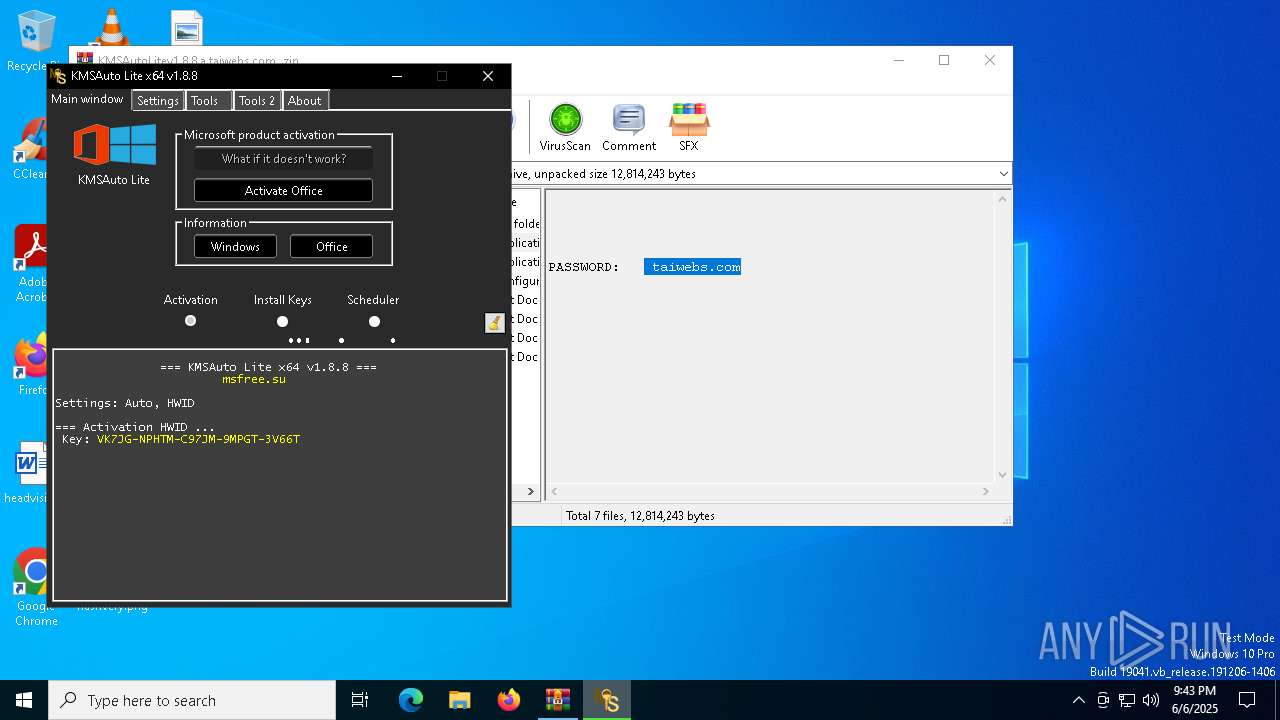
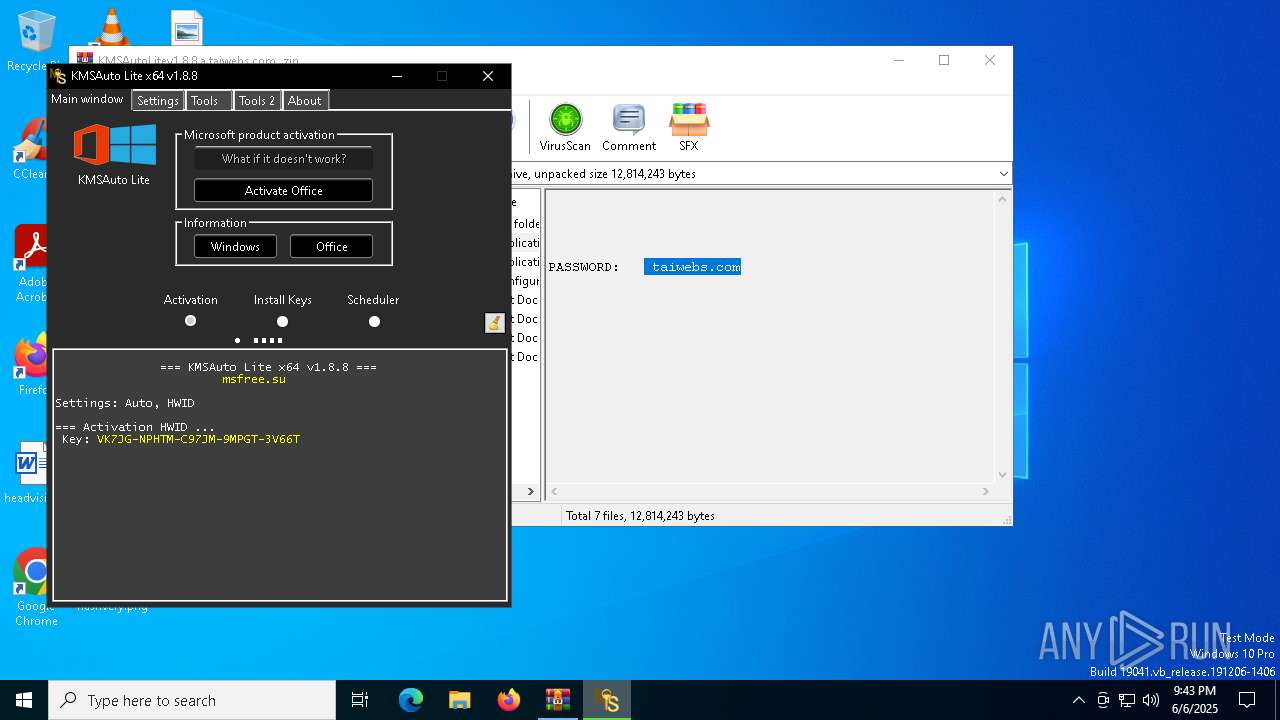
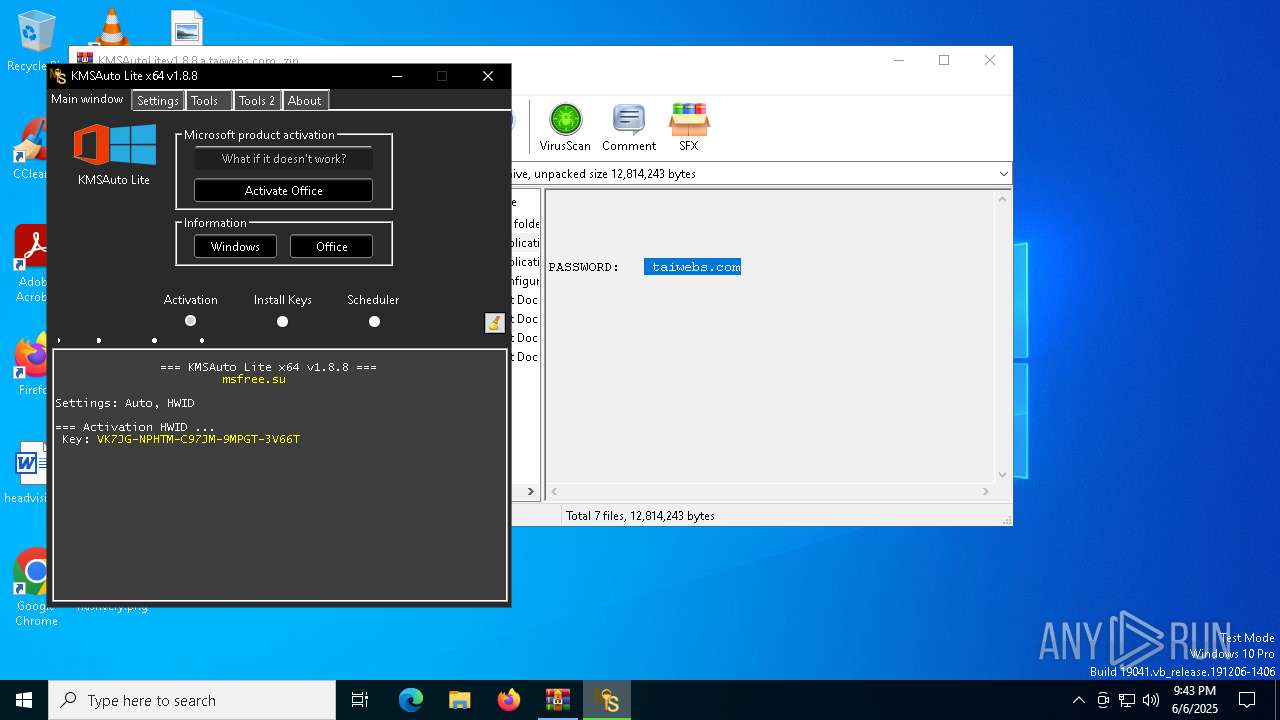
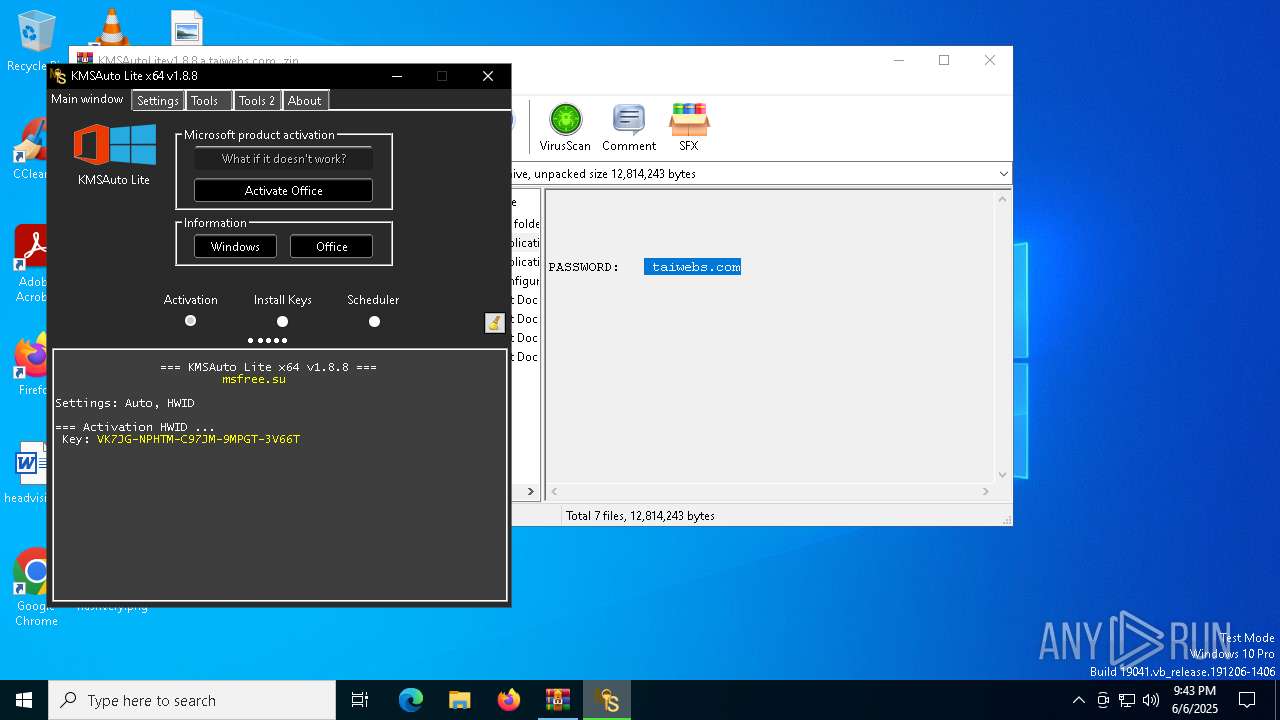
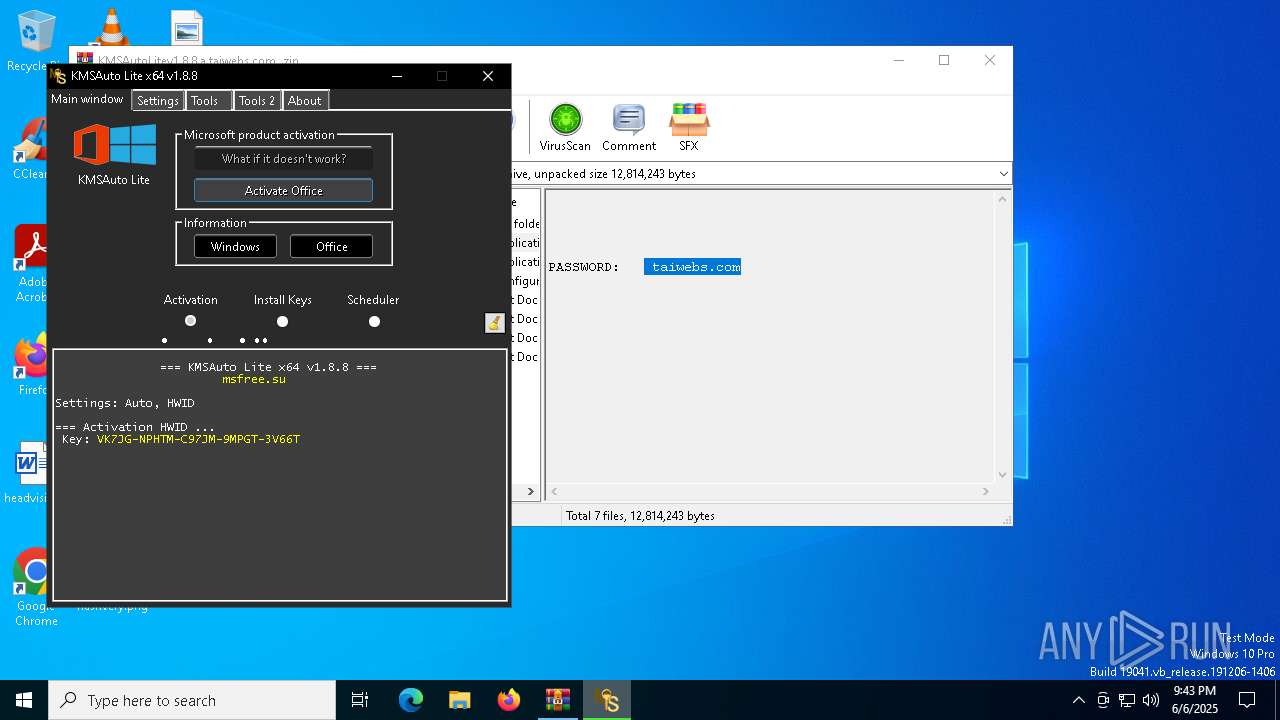
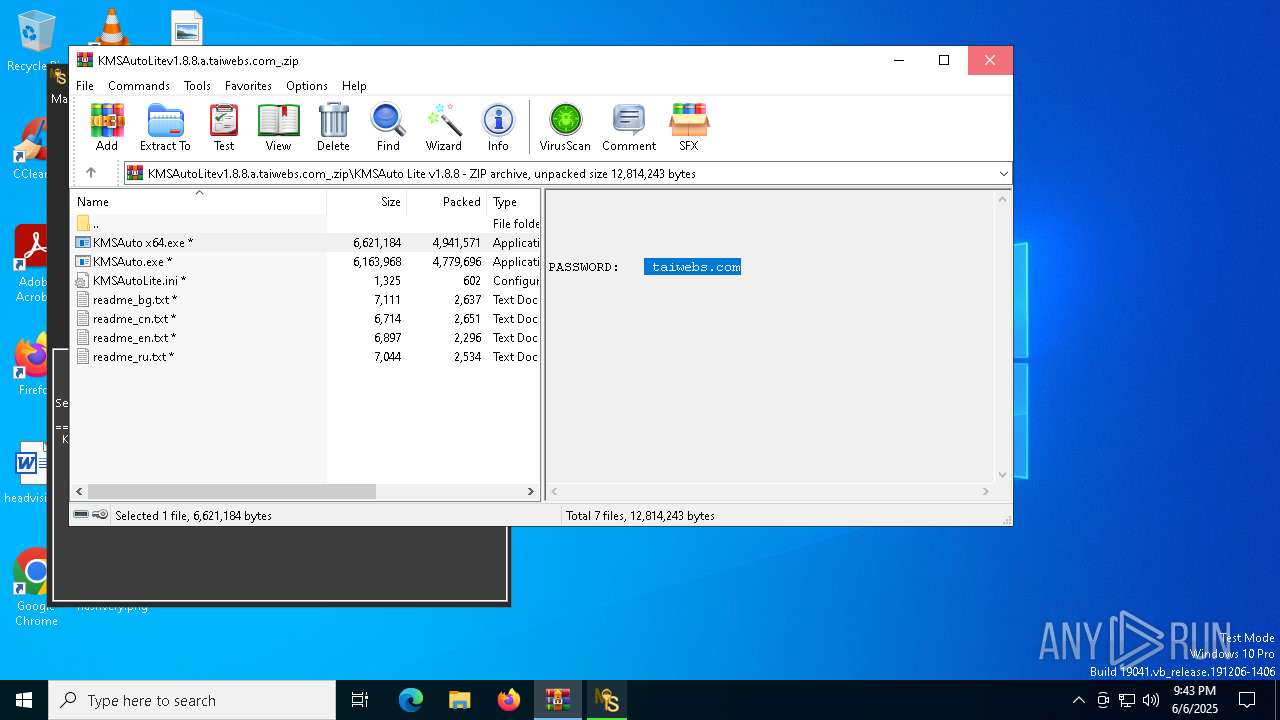
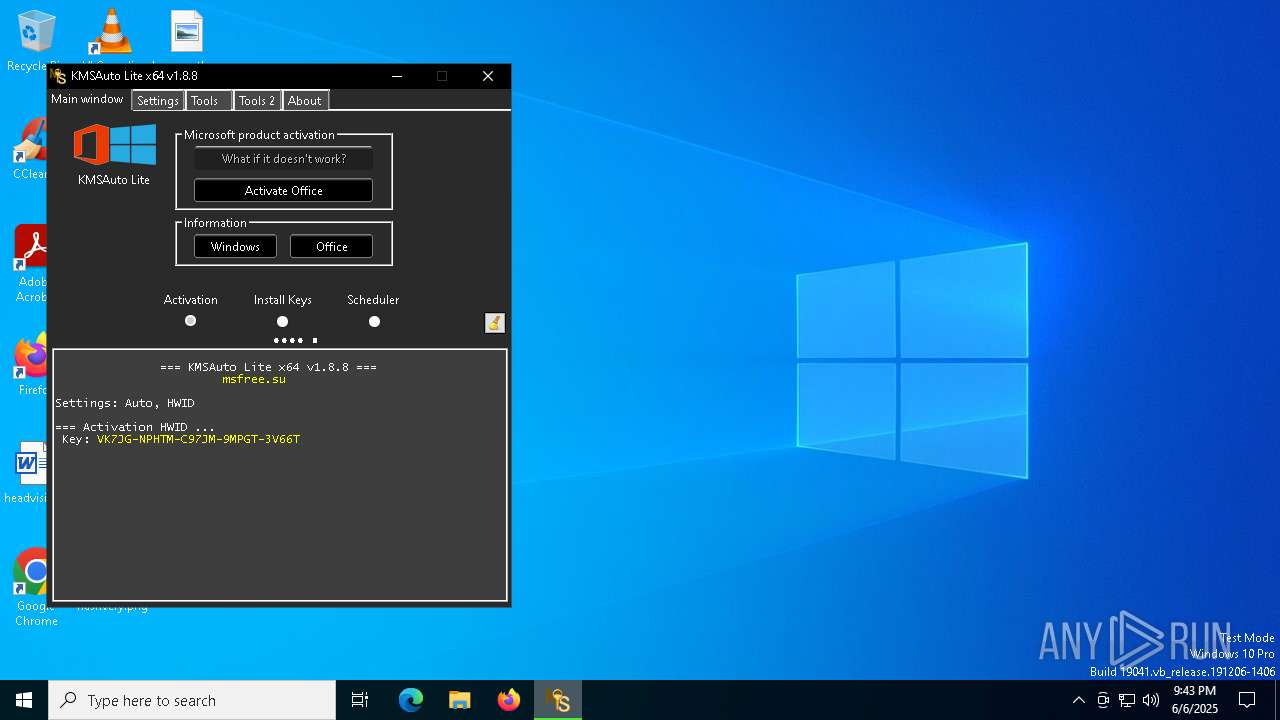
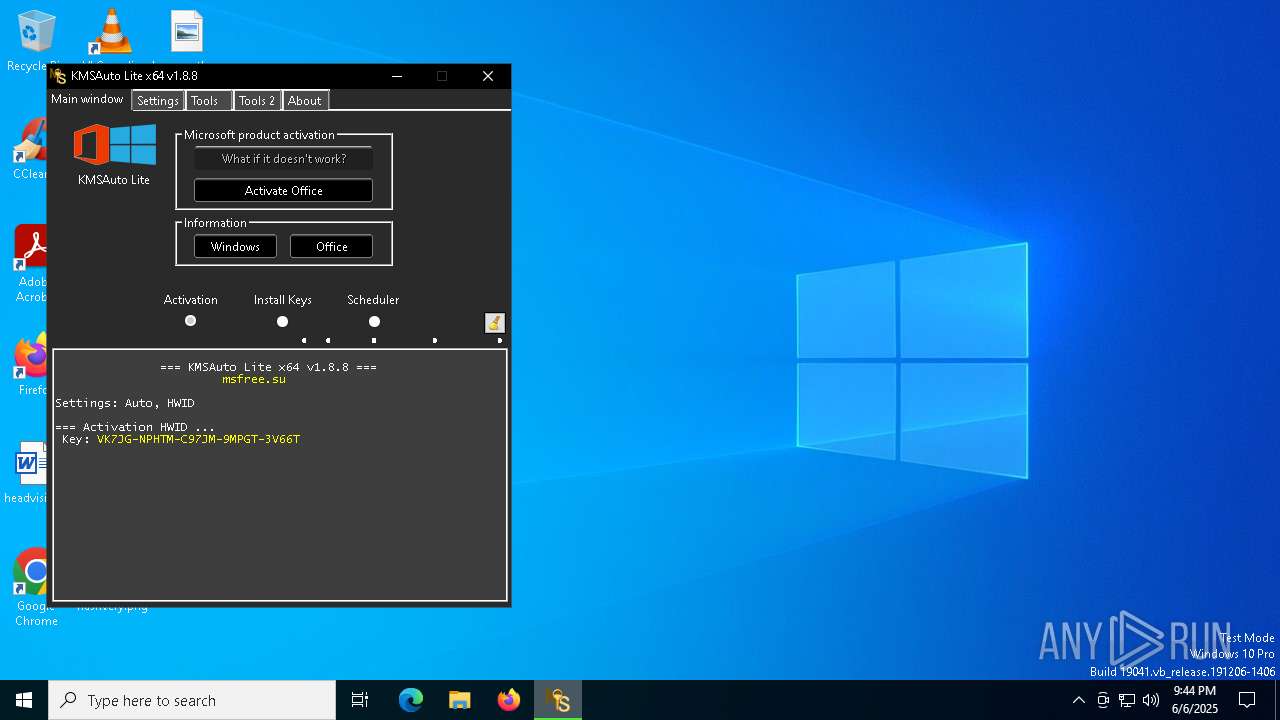
| File name: | KMSAutoLitev1.8.8.a.taiwebs.com_.zip |
| Full analysis: | https://app.any.run/tasks/975762a7-7548-46f5-b7f2-ba231c8c01e7 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2025, 21:41:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | AD3278429F3973E89BB9517A5BDFECE4 |
| SHA1: | D90EFF655C2A43DD0D484380B8F1D8896DB0A126 |
| SHA256: | 4C36216C8F2E8FB138551582313A927CA175E1502F8E84C94BF5FF5643AF18B7 |
| SSDEEP: | 98304:cke2v+M99wX2I45yr9O3f7HScA0IypEOIC8UuHfWkfmLOwgSIhhPnlORkS86oFzc:c4kUcziUnJluEWHWjs7Kv2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3364)
Windows service management via SC.EXE
- sc.exe (PID: 4560)
- sc.exe (PID: 7184)
- sc.exe (PID: 7616)
- sc.exe (PID: 7528)
- sc.exe (PID: 4724)
- sc.exe (PID: 6072)
- sc.exe (PID: 2384)
- sc.exe (PID: 6044)
- sc.exe (PID: 7260)
- sc.exe (PID: 6540)
- sc.exe (PID: 7708)
- sc.exe (PID: 7592)
- sc.exe (PID: 6892)
- sc.exe (PID: 1600)
- sc.exe (PID: 680)
- sc.exe (PID: 7716)
- sc.exe (PID: 2192)
- sc.exe (PID: 5548)
- sc.exe (PID: 5308)
- sc.exe (PID: 8160)
- sc.exe (PID: 4696)
- sc.exe (PID: 7552)
- sc.exe (PID: 6792)
- sc.exe (PID: 2664)
- sc.exe (PID: 7948)
- sc.exe (PID: 896)
- sc.exe (PID: 772)
- sc.exe (PID: 4844)
- sc.exe (PID: 632)
- sc.exe (PID: 1180)
- sc.exe (PID: 6416)
- sc.exe (PID: 7972)
- sc.exe (PID: 6496)
- sc.exe (PID: 7464)
- sc.exe (PID: 4892)
- sc.exe (PID: 3100)
- sc.exe (PID: 3396)
- sc.exe (PID: 5360)
- sc.exe (PID: 7856)
- sc.exe (PID: 4268)
- sc.exe (PID: 7344)
- sc.exe (PID: 2108)
- sc.exe (PID: 4560)
- sc.exe (PID: 4164)
- sc.exe (PID: 4988)
- sc.exe (PID: 7268)
- sc.exe (PID: 2692)
- sc.exe (PID: 960)
- sc.exe (PID: 7868)
- sc.exe (PID: 6132)
- sc.exe (PID: 7288)
- sc.exe (PID: 6792)
- sc.exe (PID: 5404)
- sc.exe (PID: 7952)
- sc.exe (PID: 7880)
- sc.exe (PID: 8152)
- sc.exe (PID: 7732)
- sc.exe (PID: 8164)
- sc.exe (PID: 8156)
- sc.exe (PID: 472)
- sc.exe (PID: 4844)
- sc.exe (PID: 6540)
- sc.exe (PID: 7904)
- sc.exe (PID: 776)
- sc.exe (PID: 6632)
- sc.exe (PID: 6656)
- sc.exe (PID: 7592)
- sc.exe (PID: 7196)
- sc.exe (PID: 5096)
- sc.exe (PID: 7976)
- sc.exe (PID: 6264)
- sc.exe (PID: 7876)
- sc.exe (PID: 7492)
- sc.exe (PID: 3008)
- sc.exe (PID: 8044)
Starts CMD.EXE for commands execution
- KMSAuto x64.exe (PID: 2416)
- cmd.exe (PID: 5988)
Starts SC.EXE for service management
- KMSAuto x64.exe (PID: 2416)
- cmd.exe (PID: 2092)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 5988)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 5024)
- cscript.exe (PID: 7264)
- cscript.exe (PID: 7376)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 5024)
- cscript.exe (PID: 7264)
- cscript.exe (PID: 7376)
Uses WMIC.EXE
- KMSAuto x64.exe (PID: 2416)
The process executes VB scripts
- cmd.exe (PID: 7252)
- cmd.exe (PID: 7784)
- cmd.exe (PID: 5988)
Executable content was dropped or overwritten
- KMSAuto x64.exe (PID: 2416)
- Dism.exe (PID: 5176)
Process drops legitimate windows executable
- KMSAuto x64.exe (PID: 2416)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5216)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 5988)
Executing commands from ".cmd" file
- KMSAuto x64.exe (PID: 2416)
- cmd.exe (PID: 5988)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4228)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 6820)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 644)
Application launched itself
- cmd.exe (PID: 5988)
- ClipUp.exe (PID: 7788)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 5988)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5988)
- cmd.exe (PID: 8132)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5988)
Hides command output
- cmd.exe (PID: 6404)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 644)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 704)
- cmd.exe (PID: 5404)
- cmd.exe (PID: 8132)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 3156)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7636)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 644)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 644)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 1072)
The process creates files with name similar to system file names
- Dism.exe (PID: 5176)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 7376)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 7604)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 5988)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4608)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5988)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3364)
Reads Environment values
- KMSAuto x64.exe (PID: 2416)
- DismHost.exe (PID: 7604)
Reads the computer name
- KMSAuto x64.exe (PID: 2416)
- DismHost.exe (PID: 7604)
Checks supported languages
- KMSAuto x64.exe (PID: 2416)
- DismHost.exe (PID: 7604)
Reads product name
- KMSAuto x64.exe (PID: 2416)
Create files in a temporary directory
- KMSAuto x64.exe (PID: 2416)
- Dism.exe (PID: 5176)
Reads security settings of Internet Explorer
- cscript.exe (PID: 5024)
- WMIC.exe (PID: 8168)
- cscript.exe (PID: 7264)
- WMIC.exe (PID: 7212)
- WMIC.exe (PID: 7424)
- WMIC.exe (PID: 5864)
- cscript.exe (PID: 7376)
- WMIC.exe (PID: 5332)
- WMIC.exe (PID: 8136)
- WMIC.exe (PID: 4700)
- WMIC.exe (PID: 1300)
The sample compiled with english language support
- KMSAuto x64.exe (PID: 2416)
- Dism.exe (PID: 5176)
Checks operating system version
- cmd.exe (PID: 5988)
UPX packer has been detected
- KMSAuto x64.exe (PID: 2416)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 924)
Creates files in the program directory
- cmd.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:05:28 23:12:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | KMSAuto Lite v1.8.8/ |
Total processes
474
Monitored processes
334
Malicious processes
4
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | reg query HKLM\SYSTEM\CurrentControlSet\Services\LicenseManager /v ErrorControl | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | sc start LicenseManager | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | reg query HKLM\SYSTEM\CurrentControlSet\Services\DoSvc /v ImagePath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | sc query BITS | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\AppData\Local\Temp\BIN\h.cmd') -split ':wpatest\:.*';iex ($f[1]);" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | sc start wlidsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 704 | C:\WINDOWS\system32\cmd.exe /c reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v EditionID 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 772 | sc start BITS | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | sc query DoSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | reg query HKLM\SYSTEM\CurrentControlSet\Services\KeyIso /v ErrorControl | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
57 475
Read events
57 443
Write events
30
Delete events
2
Modification events
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAutoLitev1.8.8.a.taiwebs.com_.zip | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (2416) KMSAuto x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
Executable files
54
Suspicious files
1
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3364.41531\KMSAuto Lite v1.8.8\readme_cn.txt | text | |
MD5:D6B1343B3529407866EBDB7027F6BEA6 | SHA256:29A8D19DF069CEF8BD36F7317F08E612E61B7C4D01C91DD7995726E994A99479 | |||
| 1472 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_umb0zbul.svl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3364.41531\KMSAuto Lite v1.8.8\readme_bg.txt | text | |
MD5:05271DECC7594F49AAE6F96A2A726C86 | SHA256:FF73697ED8A8C3118F0B57E923F288B8F9C14393E741AF7314587659C0A34C71 | |||
| 3364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3364.41531\KMSAuto Lite v1.8.8\KMSAuto x64.exe | executable | |
MD5:0FCE66D54787A891A1CB5F06C09C5065 | SHA256:A11BFCBF566428E787E685FC1ABF67474777BD4160764AC4F34096E079B8B84D | |||
| 4120 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uiu4he4r.w33.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2416 | KMSAuto x64.exe | C:\Users\admin\AppData\Local\Temp\BIN\slc.dll | executable | |
MD5:31E221D3B930629A14ED2AF067F777E3 | SHA256:32073D9D5706476785E3FBCB208B65DFF56038C6CA9A8A2B15D2AB1590CC8E04 | |||
| 4120 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_d3ntvg4f.lt3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2416 | KMSAuto x64.exe | C:\Users\admin\AppData\Local\Temp\slmgr.vbs | text | |
MD5:3903BCAB32A4A853DFA54962112D4D02 | SHA256:95FC646D222D324DB46F603A7F675C329FE59A567ED27FDAED2A572A19206816 | |||
| 6132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5a0h4l0p.mlj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3364.41531\KMSAuto Lite v1.8.8\readme_ru.txt | text | |
MD5:3D2918B86DFE71340B4C3E14D545FC79 | SHA256:CAB66CEAF2BB0D3533258414D37DCC4F7466F17B6442BCEBC5B8FA122E1C29F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.27:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2432 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2432 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
8028 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.27:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7964 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7964 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
l.root-servers.net |
| unknown |