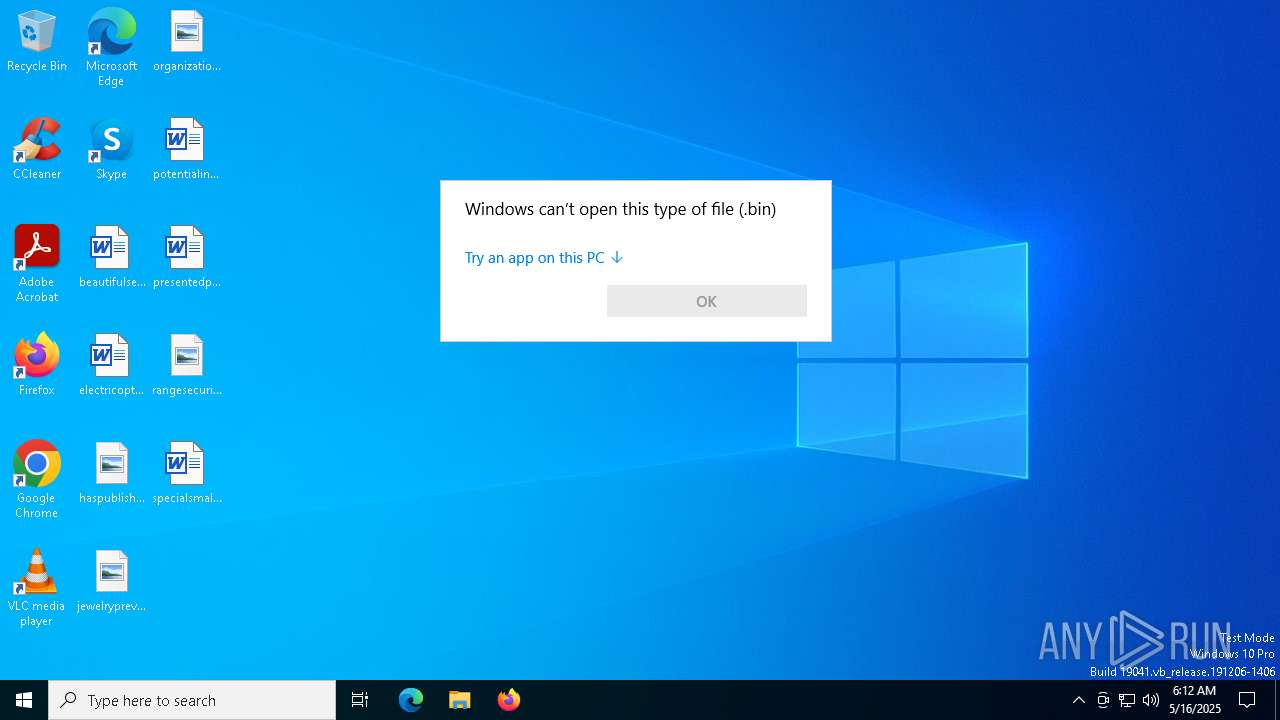
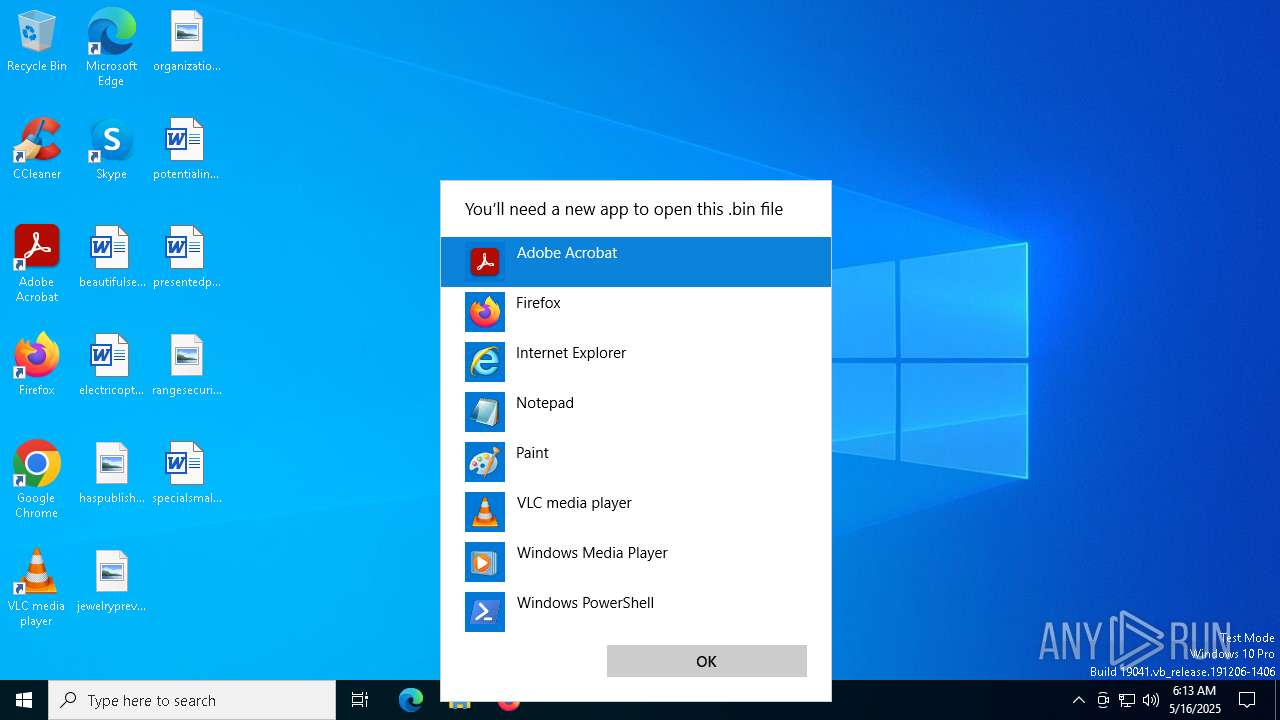
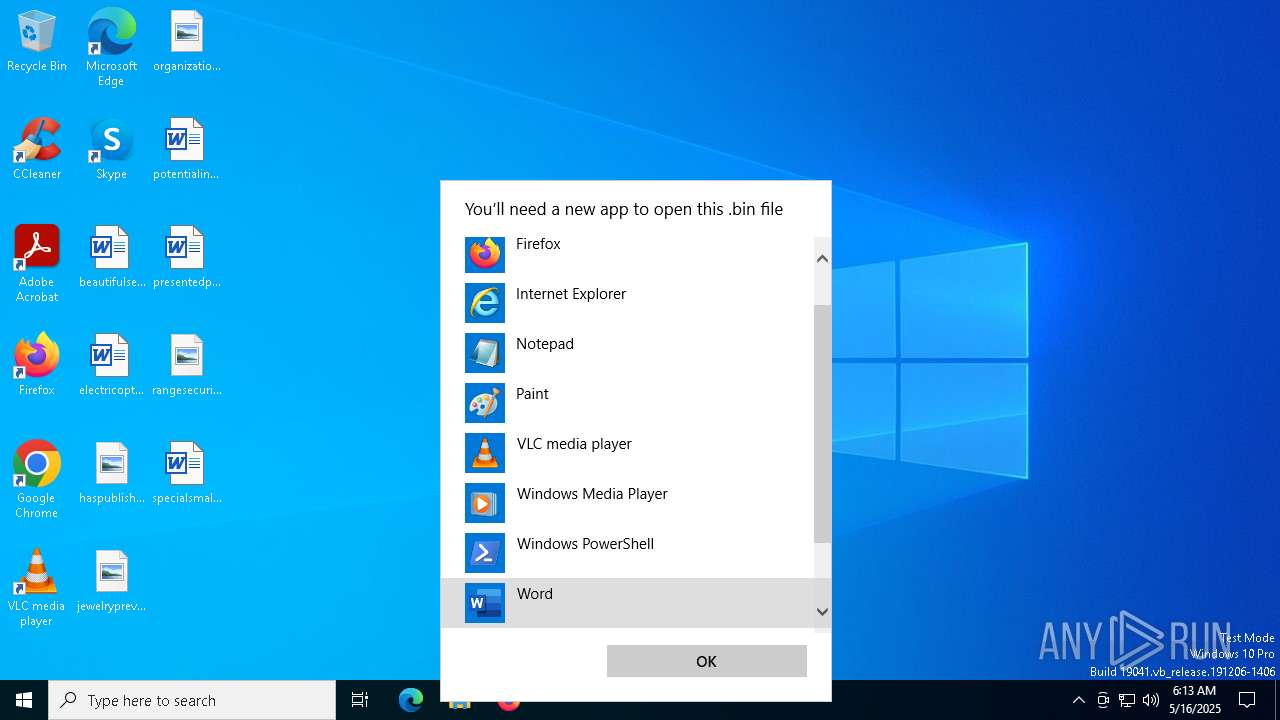
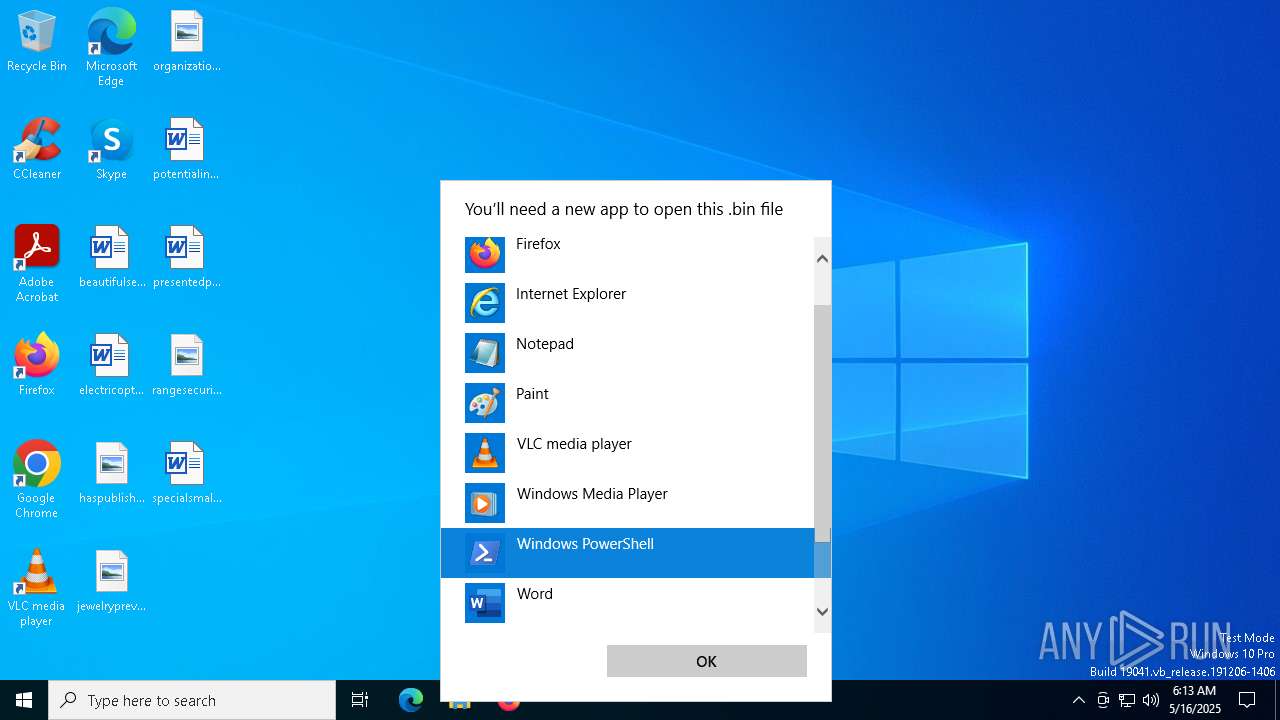
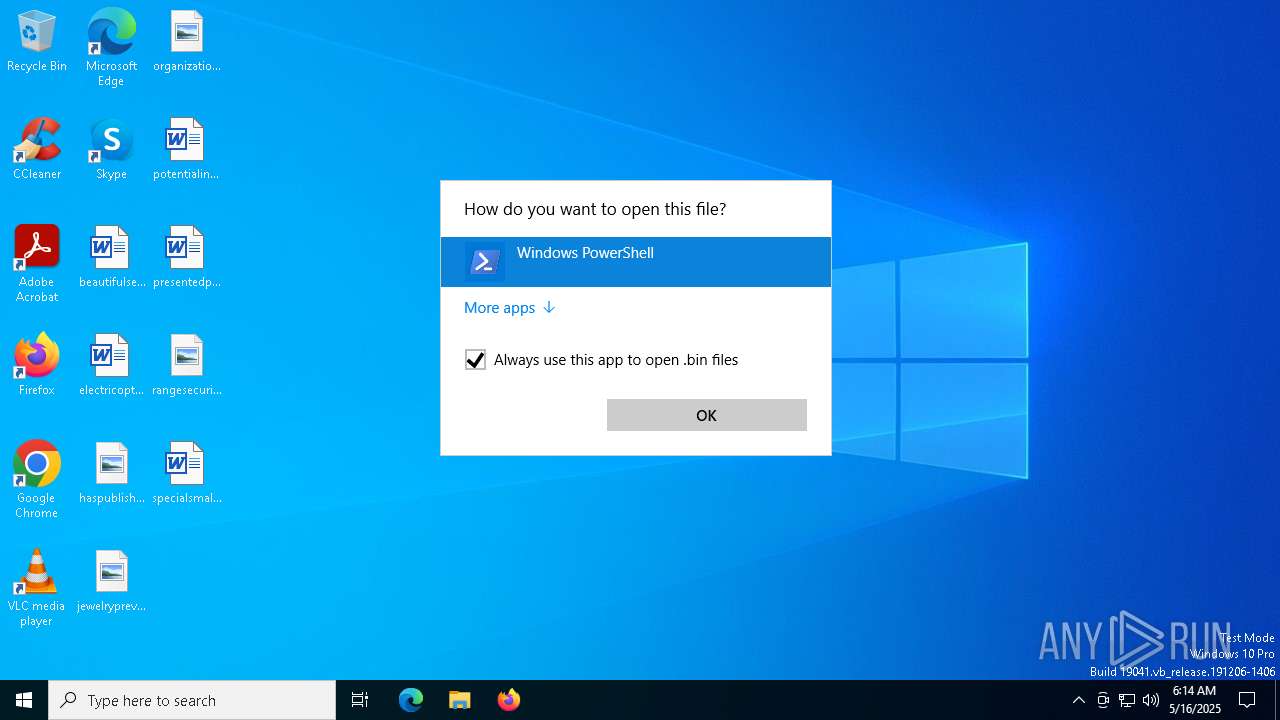
| File name: | 2020-06-03-Word-doc-with-macro-for-Valak.bin |
| Full analysis: | https://app.any.run/tasks/bd40aefd-75fc-4187-bfda-967ed16e4330 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 06:12:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 4D4994030DB743C270956B50C765CADE |
| SHA1: | D5BAF0693E9988E4194621F736DB00E643F4A458 |
| SHA256: | 4C0D7B112DFD99C751A85AD9539152C413EDE7E5D976F75AE13A8B46EBF53E66 |
| SSDEEP: | 3072:zXokxE5Et2foxdPDKZWF5OFaLzIzZjPgWjnxgueBVNng:1t4kPDPF4gHIzxTnK/6 |
MALICIOUS
Drops known malicious document
- OpenWith.exe (PID: 5552)
SUSPICIOUS
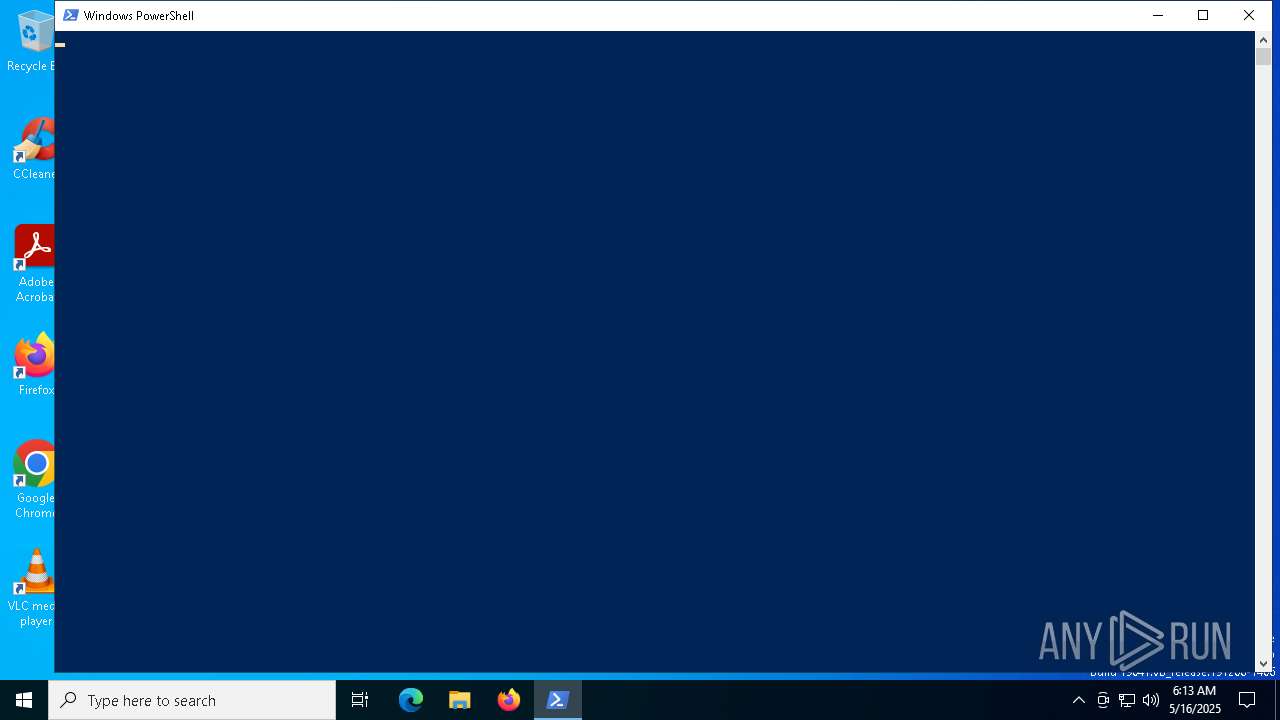
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 5552)
- OpenWith.exe (PID: 5384)
- powershell.exe (PID: 5960)
- powershell.exe (PID: 976)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 2568)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 4212)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 5352)
- powershell.exe (PID: 924)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 2896)
- powershell.exe (PID: 6228)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 7052)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2960)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 5332)
- powershell.exe (PID: 4436)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 3800)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 5256)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 2516)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 5308)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 132)
- powershell.exe (PID: 6192)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 6228)
- powershell.exe (PID: 4844)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 968)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 2100)
- powershell.exe (PID: 1116)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 968)
- powershell.exe (PID: 2984)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 5960)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 516)
- powershell.exe (PID: 1628)
- powershell.exe (PID: 6712)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 780)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 4400)
- powershell.exe (PID: 2984)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 7104)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 1660)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1504)
- powershell.exe (PID: 976)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 1168)
- powershell.exe (PID: 132)
- powershell.exe (PID: 7012)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1664)
- powershell.exe (PID: 4868)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 976)
- powershell.exe (PID: 6004)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 4528)
- powershell.exe (PID: 6276)
- powershell.exe (PID: 6080)
Application launched itself
- powershell.exe (PID: 5960)
- powershell.exe (PID: 976)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 2568)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 4212)
- powershell.exe (PID: 5352)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 924)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 2896)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 6228)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 7052)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 5332)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 2960)
- powershell.exe (PID: 960)
- powershell.exe (PID: 4436)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 2516)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 3800)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 5256)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 5308)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 132)
- powershell.exe (PID: 6192)
- powershell.exe (PID: 6228)
- powershell.exe (PID: 4844)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 968)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 2100)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 1116)
- powershell.exe (PID: 968)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 2984)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 516)
- powershell.exe (PID: 1628)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 6712)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 5960)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 780)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 4400)
- powershell.exe (PID: 2984)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 7104)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1504)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 976)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1168)
- powershell.exe (PID: 7012)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 6276)
- powershell.exe (PID: 976)
- powershell.exe (PID: 1664)
- powershell.exe (PID: 4868)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 6004)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 4528)
- powershell.exe (PID: 6080)
INFO
An automatically generated document
- OpenWith.exe (PID: 5552)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5552)
- OpenWith.exe (PID: 5384)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5552)
- OpenWith.exe (PID: 5384)
Reads the software policy settings
- slui.exe (PID: 4244)
- slui.exe (PID: 2984)
Checks proxy server information
- slui.exe (PID: 2984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x7df6b578 |
| ZipCompressedSize: | 427 |
| ZipUncompressedSize: | 1637 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 4 |
| Paragraphs: | - |
| ScaleCrop: | No |
| Manager: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | admin |
| RevisionNumber: | 2 |
| CreateDate: | 2020:06:03 09:47:00Z |
| ModifyDate: | 2020:06:03 09:47:00Z |
| Category: | - |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | ciifwq |
| Description: | - |
Total processes
366
Monitored processes
237
Malicious processes
1
Suspicious processes
57
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-03-Word-doc-with-macro-for-Valak.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-03-Word-doc-with-macro-for-Valak.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-03-Word-doc-with-macro-for-Valak.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-03-Word-doc-with-macro-for-Valak.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
545 837
Read events
545 716
Write events
121
Delete events
0
Modification events
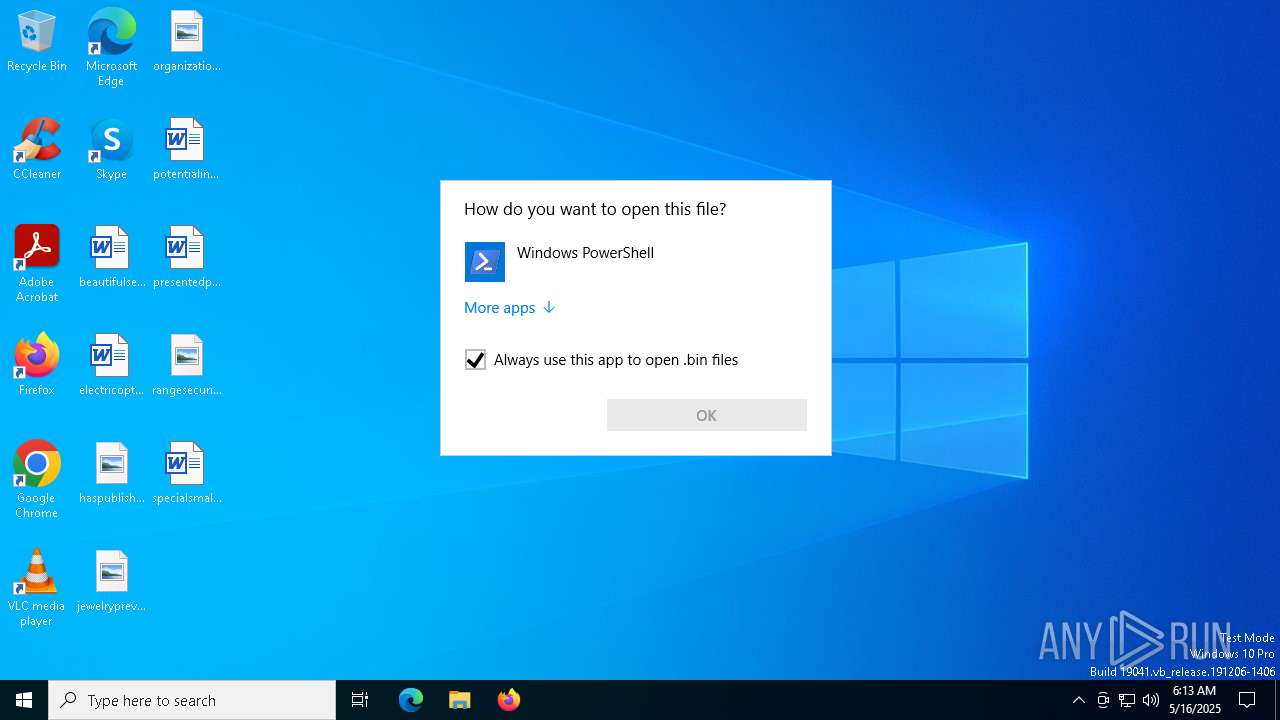
| (PID) Process: | (5384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (5384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | ProgId |
Value: Applications\powershell.exe | |||
| (PID) Process: | (5384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | Hash |
Value: 75XkTvDUczU= | |||
| (PID) Process: | (5384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (5384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (5960) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (4380) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (6208) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (2568) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
Executable files
0
Suspicious files
349
Text files
232
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CP6BWPQBTFDFC03493W8.temp | binary | |
MD5:BC1652A0BCBEDB4CFA74D973757469AC | SHA256:B1FC4C38A77E48610FCBB829C3E5BBC4877FA59670D433CEF12E93CFCF4E8C47 | |||
| 6768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_v1hfh40z.du1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5960 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\25A11PQXOH9XB5BPACN7.temp | binary | |
MD5:5FFD6A6DC6260834D1518970C3D8DC51 | SHA256:E4737D672AE9B131BF9DD35CA04205B48F50CA4F37E253EBBBBBA466EDB43CC6 | |||
| 6768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:BC1652A0BCBEDB4CFA74D973757469AC | SHA256:B1FC4C38A77E48610FCBB829C3E5BBC4877FA59670D433CEF12E93CFCF4E8C47 | |||
| 6768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_24fpsn55.sul.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_o3j0gvih.glc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ntxonyf4.ac4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5960 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF12911c.TMP | binary | |
MD5:BC1652A0BCBEDB4CFA74D973757469AC | SHA256:B1FC4C38A77E48610FCBB829C3E5BBC4877FA59670D433CEF12E93CFCF4E8C47 | |||
| 5960 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:5FFD6A6DC6260834D1518970C3D8DC51 | SHA256:E4737D672AE9B131BF9DD35CA04205B48F50CA4F37E253EBBBBBA466EDB43CC6 | |||
| 5960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lj25trxj.bbd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
46
DNS requests
18
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
920 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
920 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
198.187.3.20.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |