| File name: | MSDisplay_Windows_V2.0.1.7.3.exe |
| Full analysis: | https://app.any.run/tasks/dc5a52e6-dc2f-43a5-b624-43dcff57cfb2 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2025, 13:01:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 44B238973B55B2D863BC8608140AF84D |
| SHA1: | 598B1428A52E61ABEBCFEBCC3E7FC991F35837B9 |
| SHA256: | 4C0008A6DA0B5BEAA05F3AB33E822FD49FBF581BB3235FD4279743048DDEB927 |
| SSDEEP: | 98304:1SiOZA6Qt4iHcpmjVdTL8Bs+ba+46pratD8Qcf:eiHcQVdX82i5rxQcf |
MALICIOUS
Changes the autorun value in the registry
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
SUSPICIOUS
Executable content was dropped or overwritten
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 4408)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- devcon.exe (PID: 664)
- drvinst.exe (PID: 1512)
- drvinst.exe (PID: 1328)
- drvinst.exe (PID: 7148)
- devcon.exe (PID: 1912)
- devcon.exe (PID: 736)
- drvinst.exe (PID: 5984)
- drvinst.exe (PID: 6108)
- devcon.exe (PID: 6576)
- drvinst.exe (PID: 736)
- drvinst.exe (PID: 1388)
- devcon.exe (PID: 7196)
- drvinst.exe (PID: 7268)
- drvinst.exe (PID: 7308)
Reads security settings of Internet Explorer
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
- devcon.exe (PID: 1912)
- devcon.exe (PID: 736)
- devcon.exe (PID: 6576)
- devcon.exe (PID: 7196)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Reads the Windows owner or organization settings
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
The process drops C-runtime libraries
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Process drops legitimate windows executable
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Drops a system driver (possible attempt to evade defenses)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- devcon.exe (PID: 664)
- drvinst.exe (PID: 1512)
- drvinst.exe (PID: 1328)
- devcon.exe (PID: 1912)
- drvinst.exe (PID: 7148)
Creates files in the driver directory
- drvinst.exe (PID: 1512)
- drvinst.exe (PID: 1328)
- drvinst.exe (PID: 7148)
- drvinst.exe (PID: 5984)
- drvinst.exe (PID: 6108)
- drvinst.exe (PID: 736)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 7268)
- drvinst.exe (PID: 7308)
Creates or modifies Windows services
- drvinst.exe (PID: 7148)
- drvinst.exe (PID: 6108)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 7308)
Executes as Windows Service
- WUDFHost.exe (PID: 6676)
- WUDFHost.exe (PID: 856)
- WUDFHost.exe (PID: 744)
- WUDFHost.exe (PID: 7820)
- WUDFHost.exe (PID: 7372)
- WUDFHost.exe (PID: 7436)
- WUDFHost.exe (PID: 7500)
- WUDFHost.exe (PID: 7984)
- WUDFHost.exe (PID: 8080)
INFO
Checks supported languages
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 4408)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- devcon.exe (PID: 664)
- devcon.exe (PID: 1912)
- drvinst.exe (PID: 1512)
- drvinst.exe (PID: 1328)
- drvinst.exe (PID: 7148)
- devcon.exe (PID: 736)
- drvinst.exe (PID: 5984)
- devcon.exe (PID: 6576)
- drvinst.exe (PID: 6108)
- drvinst.exe (PID: 736)
- drvinst.exe (PID: 1388)
- devcon.exe (PID: 7196)
- drvinst.exe (PID: 7268)
- drvinst.exe (PID: 7308)
- devcon.exe (PID: 7600)
- WinUsbDisplay.exe (PID: 7180)
Create files in a temporary directory
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 4408)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- devcon.exe (PID: 664)
- devcon.exe (PID: 1912)
- devcon.exe (PID: 736)
- devcon.exe (PID: 6576)
- devcon.exe (PID: 7196)
Process checks computer location settings
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Reads the computer name
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- drvinst.exe (PID: 1512)
- devcon.exe (PID: 1912)
- devcon.exe (PID: 664)
- drvinst.exe (PID: 7148)
- drvinst.exe (PID: 1328)
- devcon.exe (PID: 736)
- drvinst.exe (PID: 5984)
- drvinst.exe (PID: 6108)
- devcon.exe (PID: 6576)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 736)
- devcon.exe (PID: 7196)
- drvinst.exe (PID: 7308)
- drvinst.exe (PID: 7268)
- WinUsbDisplay.exe (PID: 7180)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
Detects InnoSetup installer (YARA)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 4408)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
The sample compiled with chinese language support
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Compiled with Borland Delphi (YARA)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 4408)
- MSDisplay_Windows_V2.0.1.7.3.exe (PID: 6632)
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 4996)
Creates files in the program directory
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- WinUsbDisplay.exe (PID: 7180)
The sample compiled with english language support
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- devcon.exe (PID: 664)
- drvinst.exe (PID: 1512)
- drvinst.exe (PID: 1328)
- devcon.exe (PID: 1912)
- drvinst.exe (PID: 7148)
Creates a software uninstall entry
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
Creates files or folders in the user directory
- MSDisplay_Windows_V2.0.1.7.3.tmp (PID: 6424)
- WinUsbDisplay.exe (PID: 7180)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1512)
- devcon.exe (PID: 1912)
- drvinst.exe (PID: 1328)
- devcon.exe (PID: 736)
- drvinst.exe (PID: 5984)
- devcon.exe (PID: 6576)
- drvinst.exe (PID: 736)
- devcon.exe (PID: 7196)
- drvinst.exe (PID: 7268)
Reads the software policy settings
- drvinst.exe (PID: 1512)
- devcon.exe (PID: 1912)
- drvinst.exe (PID: 1328)
- devcon.exe (PID: 736)
- drvinst.exe (PID: 5984)
- devcon.exe (PID: 6576)
- drvinst.exe (PID: 736)
- devcon.exe (PID: 7196)
- drvinst.exe (PID: 7268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:03 08:09:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 126464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.1.7 |
| ProductVersionNumber: | 2.0.1.7 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | MS |
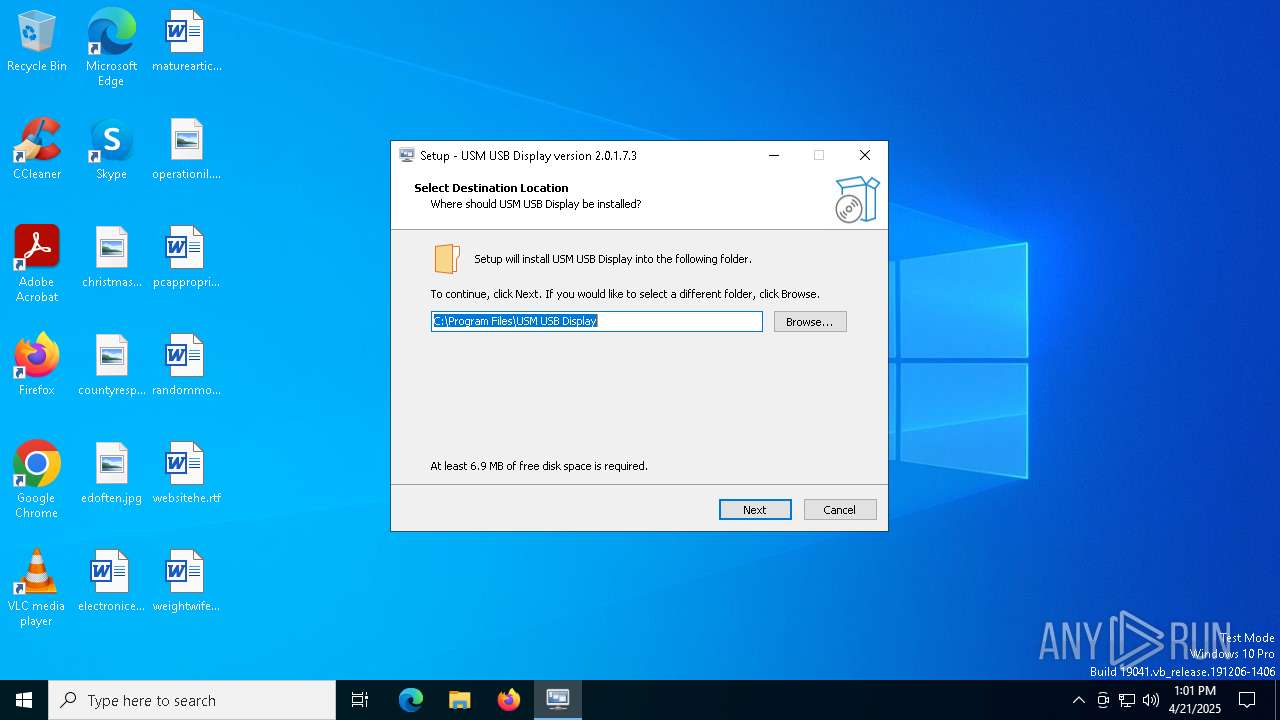
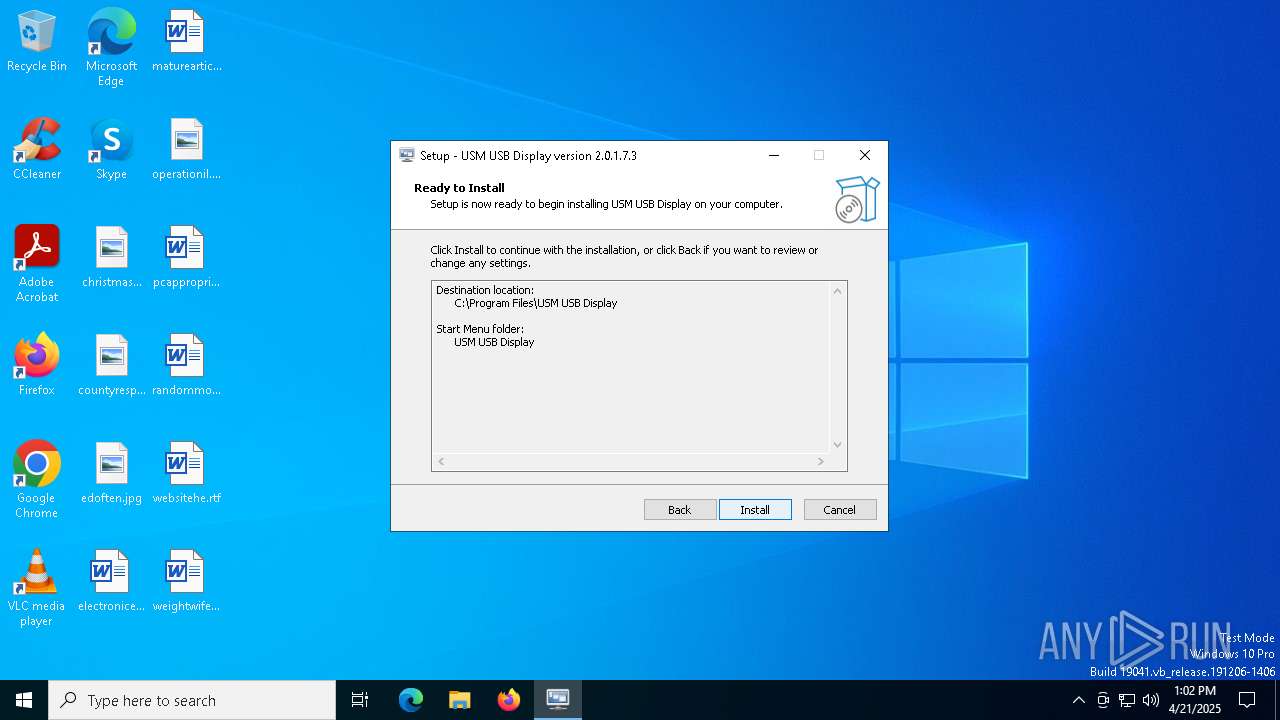
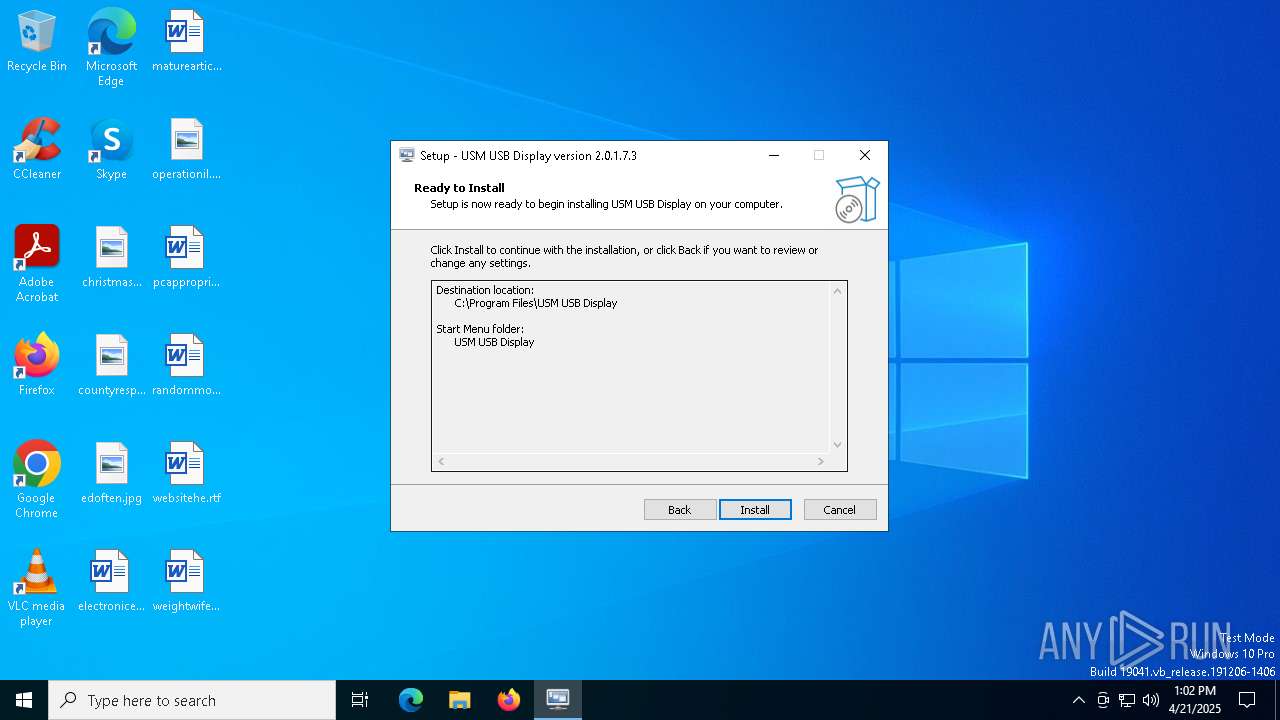
| FileDescription: | USM USB Display Setup |
| FileVersion: | 2.0.1.7.3 |
| LegalCopyright: | Copyright © USM 2022 |
| OriginalFileName: | |
| ProductName: | USM USB Display |
| ProductVersion: | 2.0.1.7.3 |
Total processes
169
Monitored processes
37
Malicious processes
12
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\USM USB Display\tool\x64\devcon.exe" dp_add "C:\Program Files\USM USB Display\lib_usb\MSUSBDisplay.inf" USB\VID_534D&PID_6021&MI_03 | C:\Program Files\USM USB Display\tool\x64\devcon.exe | MSDisplay_Windows_V2.0.1.7.3.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10586.0 (th2_release.151029-1700) Modules
| |||||||||||||||
| 736 | "C:\Program Files\USM USB Display\tool\x64\devcon.exe" update "C:\Program Files\USM USB Display\idd\indirectdisplaydriver0\indirectdisplaydriver0.inf" MS\IddBus | C:\Program Files\USM USB Display\tool\x64\devcon.exe | MSDisplay_Windows_V2.0.1.7.3.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10586.0 (th2_release.151029-1700) Modules
| |||||||||||||||
| 736 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{05871f59-1437-6b47-9280-89b8c63c2206}\indirectdisplaydriver1.inf" "9" "4f6a6593f" "00000000000001C4" "WinSta0\Default" "00000000000001F0" "208" "c:\program files\usm usb display\idd\indirectdisplaydriver1" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | "C:\Windows\System32\WUDFHost.exe" -HostGUID:{193a1820-d9ac-4997-8c55-be817523f6aa} -IoEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-6fa1b04f-7c36-439b-b5df-47088699ce44 -SystemEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-4e255144-0b71-4d3e-806b-b96027b84258 -IoCancelEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-33081948-4963-4a69-9219-763203cf5abe -NonStateChangingEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-fa0d32df-e1ad-4c39-a02b-7d0698db74ee -LifetimeId:be1a7d53-3a12-4504-8079-c9d8bbedbe3e -DeviceGroupId:IddSampleDriverGroup1 -HostArg:0 | C:\Windows\System32\WUDFHost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Driver Foundation - User-mode Driver Framework Host Process Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Windows\System32\WUDFHost.exe" -HostGUID:{193a1820-d9ac-4997-8c55-be817523f6aa} -IoEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-5e95eee1-6ef2-4c75-a974-de115ed37a1a -SystemEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-2cf316c3-a26e-4027-8d75-dd7caa2c4b7c -IoCancelEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-e293d389-4018-4d7c-957f-53886d615bcb -NonStateChangingEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-38535b72-622b-4b90-8e1e-ed9f0b52f8fd -LifetimeId:e9bf87ee-997c-4f6a-b929-d0502625c786 -DeviceGroupId:IddSampleDriverGroup -HostArg:0 | C:\Windows\System32\WUDFHost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Driver Foundation - User-mode Driver Framework Host Process Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{4bc500f7-d1c7-8f43-8dc1-705dcab0d44e}\indirectdisplaybus.inf" "9" "45a813563" "00000000000001C4" "WinSta0\Default" "00000000000001F4" "208" "c:\program files\usm usb display\idd\indirectdisplaybus" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | DrvInst.exe "2" "211" "MS\IDDBUS1\1&79F5D87&0&02" "C:\WINDOWS\INF\oem8.inf" "oem8.inf:c14ce8840c48fa1f:MyDevice_Install:10.52.13.68:ms\iddbus1," "4f6a6593f" "00000000000001F4" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0deeb76a-b40a-d243-9426-c5ea552801ec}\MSUSBDisplay.inf" "9" "42202a2d7" "00000000000001E0" "WinSta0\Default" "00000000000001F0" "208" "C:\Program Files\USM USB Display\lib_usb" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 627
Read events
29 478
Write events
123
Delete events
26
Modification events
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Usb Display |
Value: C:\Program Files\USM USB Display\WinUsbDisplay.exe | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\SERVICES\dfmirage\DEVICE0 |
| Operation: | write | Name: | Attach.ToDesktop |
Value: 0 | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\WinUsbDisplay\Server |
| Operation: | write | Name: | LogLevel |
Value: 1 | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.0 | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\USM USB Display | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\USM USB Display\ | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: USM USB Display | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (6424) MSDisplay_Windows_V2.0.1.7.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{509DC88F-BC75-4AED-B511-9892EAD1AE48}}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Uninstall USM USB Display | |||
Executable files
104
Suspicious files
81
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Users\admin\AppData\Local\Temp\is-7JBMO.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\is-JB4CV.tmp | executable | |
MD5:F70F3B35A5543365775F3EBD2C541F3E | SHA256:11F90454A71419F60612999B4B5BD4E3A5D6CA4543D37CBFC08245B224DC7A77 | |||
| 6632 | MSDisplay_Windows_V2.0.1.7.3.exe | C:\Users\admin\AppData\Local\Temp\is-9PQ2Q.tmp\MSDisplay_Windows_V2.0.1.7.3.tmp | executable | |
MD5:3656DEEFA846EB33067D66B624232474 | SHA256:BB181EF25D05ADB3D5FFFCBADB3BF3696EF27DACD2356C29E043726F9BA50083 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\is-MJ156.tmp | executable | |
MD5:7FC50D24FBF0186FF7C1734511C640C1 | SHA256:F5B3848E09E3C9AF9E764FCA6AB61E22D374707A964739373FE9692B58E9A1B4 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\config.ini | text | |
MD5:AB5BD4D46AA4F19ED52961F81635AD76 | SHA256:A1C6CEDAB9EC5850C98D5FED2CB0A2253FBBCCA7B8C5974F57F34FBDE4DC3C3F | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\libusb0.dll | executable | |
MD5:A969E398CC9319DD9BD9EEDCAE288DA7 | SHA256:3165D5E9212E9C4F009A594F67BD9E6D899B026CE1E3B0D6EBB994F423D6B1D1 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\logo.ico | image | |
MD5:2098EF97358FBBDFAE0206BBCB4E2234 | SHA256:DE96747834EF6ED07618AA7EB89F643444F3BA01140EED263468C08A0B7BF8FE | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\is-F9E8B.tmp | executable | |
MD5:10BB929E9FD8B028738B46F4D3EA741E | SHA256:8817EAF691058E091E3A240547B74C3E396DAFF1312F66971274C1D30C55BDE1 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\is-NE2H9.tmp | text | |
MD5:7F4207EA1304993E8533B7A58F3A51B0 | SHA256:EE8078A7D68D5F9B702C1F5E322D67227A6512E75247D9E950D497E753C62565 | |||
| 6424 | MSDisplay_Windows_V2.0.1.7.3.tmp | C:\Program Files\USM USB Display\msvcr120.dll | executable | |
MD5:7FC50D24FBF0186FF7C1734511C640C1 | SHA256:F5B3848E09E3C9AF9E764FCA6AB61E22D374707A964739373FE9692B58E9A1B4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.130:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.130:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.130:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5964 | svchost.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |