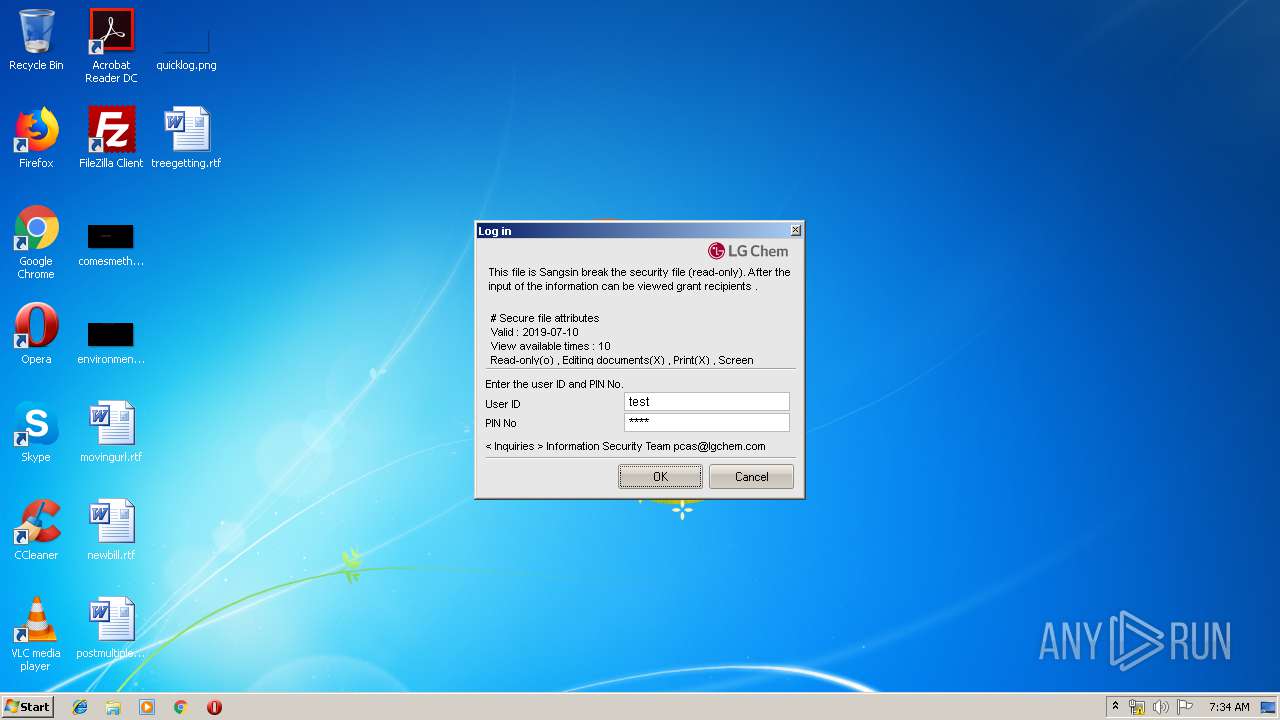
| File name: | LGCMAIL_image001.exe |
| Full analysis: | https://app.any.run/tasks/39c14cd0-1259-45e0-a775-50d77007985c |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2019, 06:33:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1C4447F79A5724B0BF806B9E274F408F |
| SHA1: | 562836788FD6A8D425712602AB37212EE375C8DE |
| SHA256: | 4BF3F0633322A8C977FF5FCB8697A4466771D7413A685B8DF842069C1639AC4A |
| SSDEEP: | 393216:zLqV+jYDJ1eaSvjXS4Hgfo/EWKPLxl+wbk9PSkS459mE+:zLqV+jAQhrS4HgAEWKVl+8kB7mE+ |
MALICIOUS
Application was dropped or rewritten from another process
- instdrvOT.Exe (PID: 988)
- SetupTmp.Exe (PID: 3236)
Registers / Runs the DLL via REGSVR32.EXE
- SetupTmp.tmp (PID: 2964)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2604)
- LGCMAIL_image001.exe (PID: 2804)
- regsvr32.exe (PID: 1872)
SUSPICIOUS
Creates files in the Windows directory
- LGCMAIL_image001.exe (PID: 2804)
- SetupTmp.tmp (PID: 2964)
Executable content was dropped or overwritten
- LGCMAIL_image001.exe (PID: 2804)
- SetupTmp.tmp (PID: 2964)
- SetupTmp.Exe (PID: 3236)
Checks supported languages
- LGCMAIL_image001.exe (PID: 2804)
Creates files in the program directory
- LGCMAIL_image001.exe (PID: 2804)
Removes files from Windows directory
- SetupTmp.tmp (PID: 2964)
Creates files in the driver directory
- SetupTmp.tmp (PID: 2964)
Creates COM task schedule object
- regsvr32.exe (PID: 2604)
INFO
Application was dropped or rewritten from another process
- SetupTmp.tmp (PID: 2964)
- chkosbe.exe (PID: 2672)
Loads dropped or rewritten executable
- SetupTmp.tmp (PID: 2964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (47.8) |
|---|---|---|
| .exe | | | InstallShield setup (25.1) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (18.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
| .exe | | | Win32 Executable (generic) (2.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:24 10:58:27+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2187264 |
| InitializedDataSize: | 151552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9bec |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.99 |
| ProductVersionNumber: | 4.0.0.99 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | MyGuard |
| CompanyName: | ITM SYSTEM.,LTD |
| FileDescription: | MyGuard |
| LegalCopyright: | ITM SYSTEM.,LTD |
| LegalTrademarks: | MyGuard |
| ProductName: | MyGuard |
| FileVersion: | 4.00.0099 |
| ProductVersion: | 4.00.0099 |
| InternalName: | SetNTmpl |
| OriginalFileName: | SetNTmpl.exe |
Total processes
46
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\mscomctl.ocx" | C:\Windows\system32\regsvr32.exe | — | SetupTmp.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Windows\system32\instdrvOT.Exe" | C:\Windows\system32\instdrvOT.Exe | — | SetupTmp.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1672 | "cacls" "C:\ProgramData\CryptorPlus" /T /C /E /P Everyone:F | C:\Windows\system32\cacls.exe | — | SetupTmp.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1872 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\HexUniControls42.ocx" | C:\Windows\system32\regsvr32.exe | — | SetupTmp.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\AppData\Local\Temp\LGCMAIL_image001.exe" | C:\Users\admin\AppData\Local\Temp\LGCMAIL_image001.exe | — | explorer.exe | |||||||||||
User: admin Company: ITM SYSTEM.,LTD Integrity Level: MEDIUM Description: MyGuard Exit code: 3221226540 Version: 4.00.0099 Modules
| |||||||||||||||
| 2604 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\conmenuOT.dll" | C:\Windows\system32\regsvr32.exe | — | SetupTmp.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\is-NQENN.tmp\chkosbe.exe" | C:\Users\admin\AppData\Local\Temp\is-NQENN.tmp\chkosbe.exe | — | SetupTmp.tmp | |||||||||||
User: admin Company: ITM SYSTEM.,LTD Integrity Level: HIGH Description: MyGuard Exit code: 0 Version: 3.00.0192 Modules
| |||||||||||||||
| 2804 | "C:\Users\admin\AppData\Local\Temp\LGCMAIL_image001.exe" | C:\Users\admin\AppData\Local\Temp\LGCMAIL_image001.exe | explorer.exe | ||||||||||||
User: admin Company: ITM SYSTEM.,LTD Integrity Level: HIGH Description: MyGuard Exit code: 0 Version: 4.00.0099 Modules
| |||||||||||||||
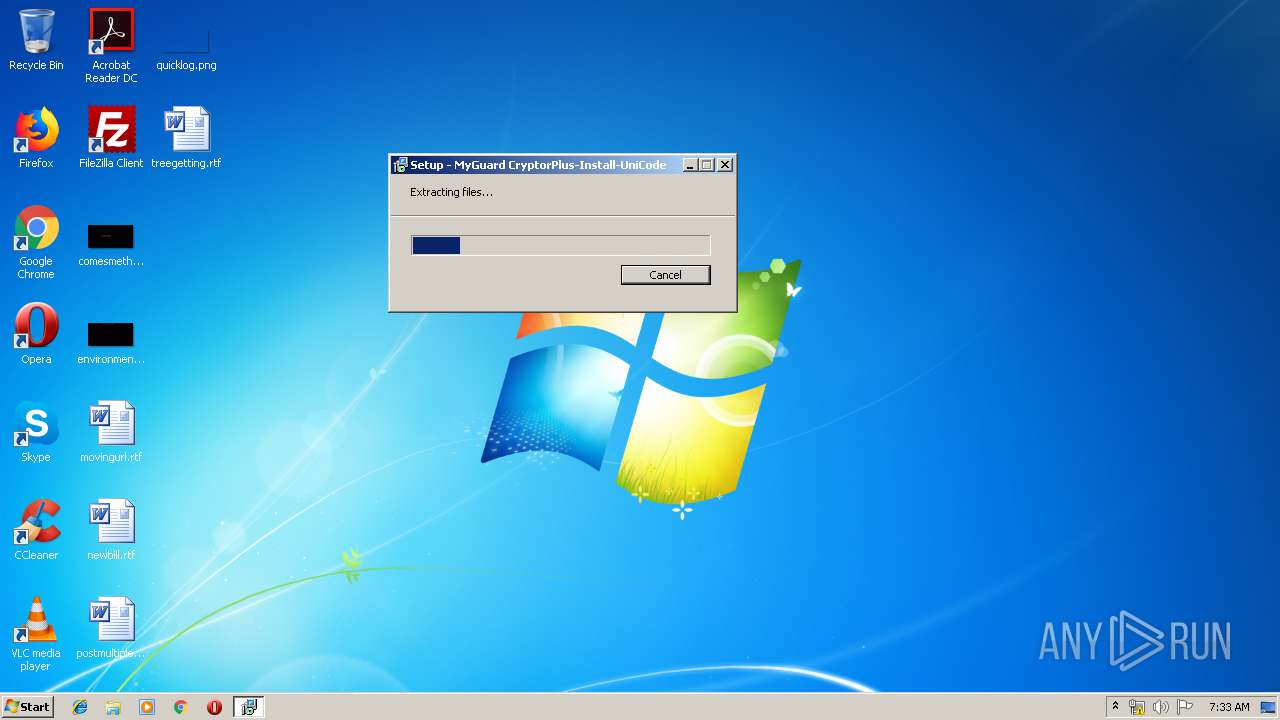
| 2964 | "C:\Users\admin\AppData\Local\Temp\is-RTA8N.tmp\SetupTmp.tmp" /SL5="$50146,9734113,54272,C:\ProgramData\MyGuard\SetupTmp.Exe" /Silent | C:\Users\admin\AppData\Local\Temp\is-RTA8N.tmp\SetupTmp.tmp | SetupTmp.Exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3236 | "C:\ProgramData\MyGuard\SetupTmp.Exe" /Silent | C:\ProgramData\MyGuard\SetupTmp.Exe | LGCMAIL_image001.exe | ||||||||||||
User: admin Company: ITM System, Inc. Integrity Level: HIGH Description: MyGuard CryptorPlus-Install-UniCode Setup Exit code: 0 Version: 4.0.1.3 Modules
| |||||||||||||||
Total events
3 125
Read events
555
Write events
2 496
Delete events
74
Modification events
| (PID) Process: | (2804) LGCMAIL_image001.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2804) LGCMAIL_image001.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\system32\unicows.dll |
Value: 1 | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\system32\HexUniControls42.ocx |
Value: 1 | |||
| (PID) Process: | (2672) chkosbe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | CorrectOS |
Value: FALSE | |||
| (PID) Process: | (2672) chkosbe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | CorrectOS |
Value: TRUE | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\system32\XceedZip.dll |
Value: 1 | |||
| (PID) Process: | (2964) SetupTmp.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\system32\VB6KO.DLL |
Value: 1 | |||
Executable files
57
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2672 | chkosbe.exe | C:\Users\admin\AppData\Local\Temp\~DF9DC97DC01FB3A4A1.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-8SKAI.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-4SV0U.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-TA6A5.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-K7BME.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-Q6JB6.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-H5173.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-14KNR.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-AL55U.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | SetupTmp.tmp | C:\Windows\system32\is-769FK.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
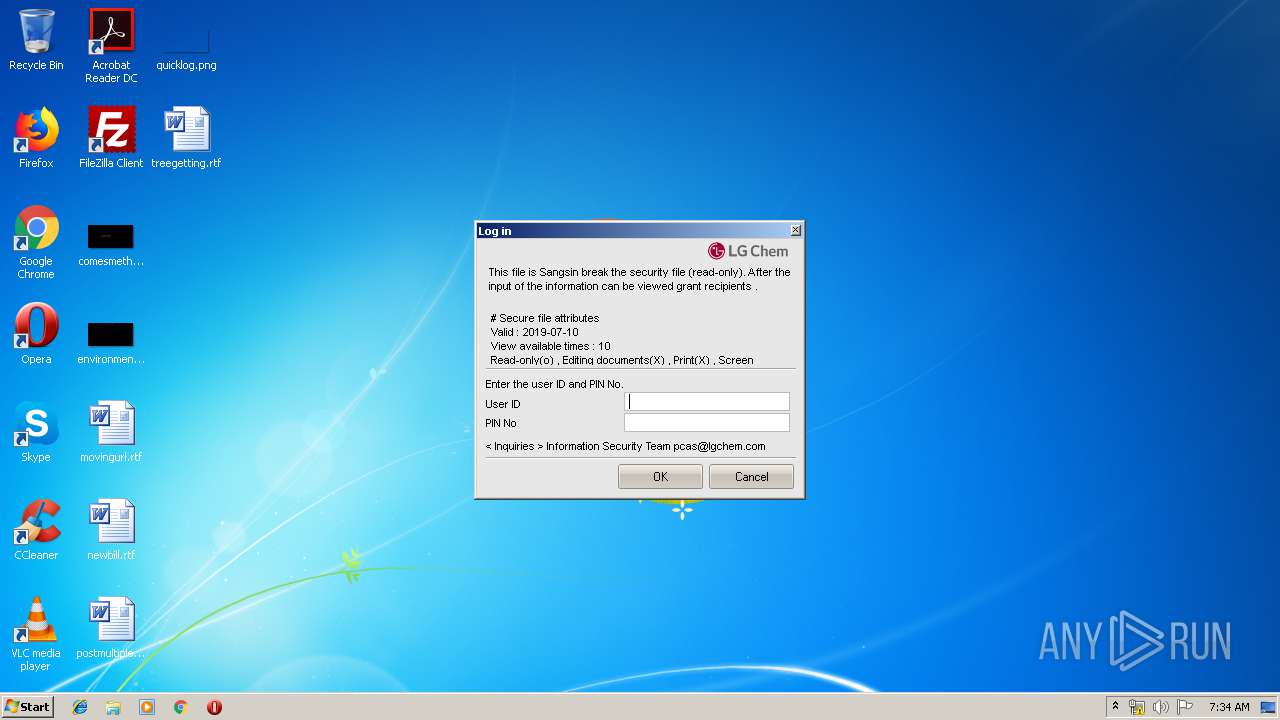
2804 | LGCMAIL_image001.exe | POST | 200 | 203.247.130.70:80 | http://cowork.lgchem.com/cp/approval.do?mod=authUser&DOC_NO=20190610102958361834&USER_ID=test&PASSWD=397379656d656d6d696d38346d3073306d746d6769677930386d38736569656d&j_language=en&log={"DOC_NO":"20190610102958361834","USER_ID":"test","IP_ADDR":"192.168.100.111","MAC_ADDR":"5254004A04AF","WORKGROUP":"WORKGROUP","WORK_TYPE":"LOGIN","Message":"","COUNTRY_CD":"ENU","PC_LOGIN_ID":"admin"} | KR | text | 52 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2804 | LGCMAIL_image001.exe | 203.247.130.70:80 | cowork.lgchem.com | LG CNS | KR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cowork.lgchem.com |
| suspicious |
Threats
Process | Message |
|---|---|
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 03=13710568 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 04=11235656 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 05=11235656 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 0503 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 0504 G_CP_COMPANYTYPE=LGCHEM |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 06 G_CP_LOADINGIMG=1 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 07 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 08 |
LGCMAIL_image001.exe | [test] Mod_CP::CheckPropBag_01 sTART 09 |