| URL: | https://www.dpbolvw.net/click-7603392-12788914 |
| Full analysis: | https://app.any.run/tasks/84bac7c5-ed27-48d4-807d-c0471c2a67be |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2024, 18:40:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 31B2857FE390FA36C4CB293E654FA9E8 |
| SHA1: | ABE5252C1F5DF7840A6AA5BAFD0B39C1FA227C60 |
| SHA256: | 4BDF054C370C3C00EC632F71618DBA3C609F71F268F1443A2024992CC4AC1617 |
| SSDEEP: | 3:N8DSLOQ/qJM2Q8MdLR:2OLTqJMnj |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.dpbolvw.net/click-7603392-12788914" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
24 576
Read events
24 428
Write events
100
Delete events
48
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090110 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090110 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
64
Text files
109
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\349D186F1CB5682FA0194D4F3754EF36_669BD570D18920164FD74B39F24B4A98 | binary | |
MD5:FD7675E43F2B8A1AFA25FFB9DC6B14E9 | SHA256:E88249525E2B2D77491FB175A542C7E20800CA5D1F87CDC9C837545AD524E0B1 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\offers[1].htm | html | |
MD5:303BA87CBBC3DA000B0B289B714B4905 | SHA256:BC5A87030401A439A81F1ACD7780583C2F7AD645A0F21580EE6FF57DD77FA3E4 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:8278EC273D463EB04301F506944E41C9 | SHA256:426D8AD1919C4895CD3555D1B91453717E11FDD492F3BBA5C4919AAE12A80D58 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\hoverIntent[1].js | text | |
MD5:1A27531C68DF91EC891A075B0832C2E8 | SHA256:719875309A034313C742EDFA43B78177BA49971A941B961CA9DD360EAB569C8E | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\349D186F1CB5682FA0194D4F3754EF36_2BB370AA3C57189636EEBD702A05DBB2 | binary | |
MD5:882EEB1BB3D84E06CD2131689BDB449D | SHA256:74B5030FD8ECC5083ACF2725BA8627A69270AAFDF644D67513302D5B2EF78230 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\grid[1].css | text | |
MD5:2DD4CC08B6D91593DE7F34E342F156E1 | SHA256:CEBE8A03AF2133A81102FD2AD9686F0412BA1178511C7AA3D63F802BEDA0BB3B | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery.nivo.slider.pack[1].js | text | |
MD5:7F8710242A543E500BFD193AE458DB3D | SHA256:2BC715B86C77B54108AF299FCAFBDDD5CA24EB71AA3C769B5623938D2D5CB2AE | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | der | |
MD5:04CFB1E63AF021BE20C8C4B5742631FF | SHA256:EF694C57F3EC9B3F20B22064F9BF9DA8387175E5D9D89D252E023F94E9235F52 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\349D186F1CB5682FA0194D4F3754EF36_2BB370AA3C57189636EEBD702A05DBB2 | binary | |
MD5:0ED5BAC52C775586EEB45044B55CD97C | SHA256:8986EF3D4F864FC5AA54E5FFF46F6A8104460ADF617AFF30AE172728155D42EB | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\modernizr-1.7.min[1].js | text | |
MD5:52B8FD529E8142BDB6C4F9E7F55AAEC0 | SHA256:954E385ECD6ED2AB0CB91DC0333EA1B3CF1BDCFE309D4857E7181324CB8DC25B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
130
DNS requests
48
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c70275e956f241e7 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDBiHCRREcGS96IilTg%3D%3D | unknown | binary | 1.40 Kb | unknown |
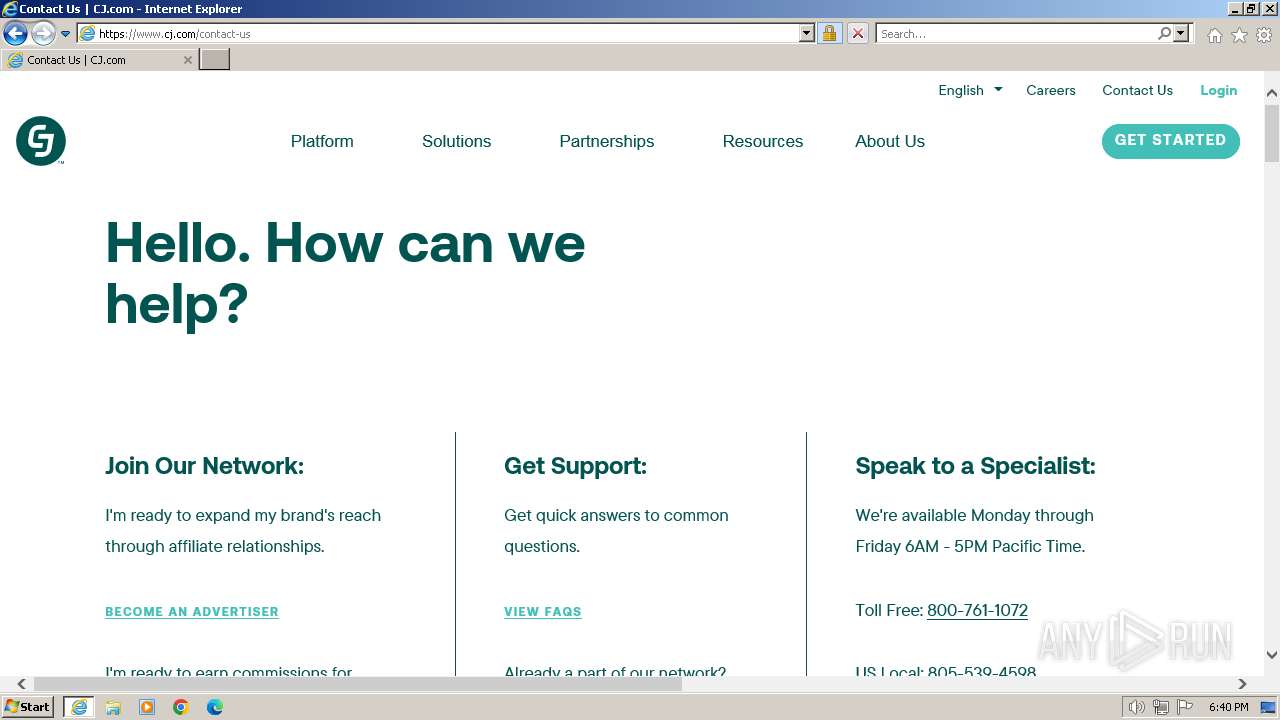
2044 | iexplore.exe | GET | — | 159.127.40.213:80 | http://members.cj.com/expired.jsp?utm_source=cjcom&utm_campaign=tello_cj_affiliates&utm_medium=cpa&src=cjcom&mdm=cpa&cmg=tello_cj_affiliates&PID=7603392&CID=4344425&LID=12788914&SID=&cjevent=d15ec4abd1b111ee818500020a18b8f8 | unknown | — | — | unknown |
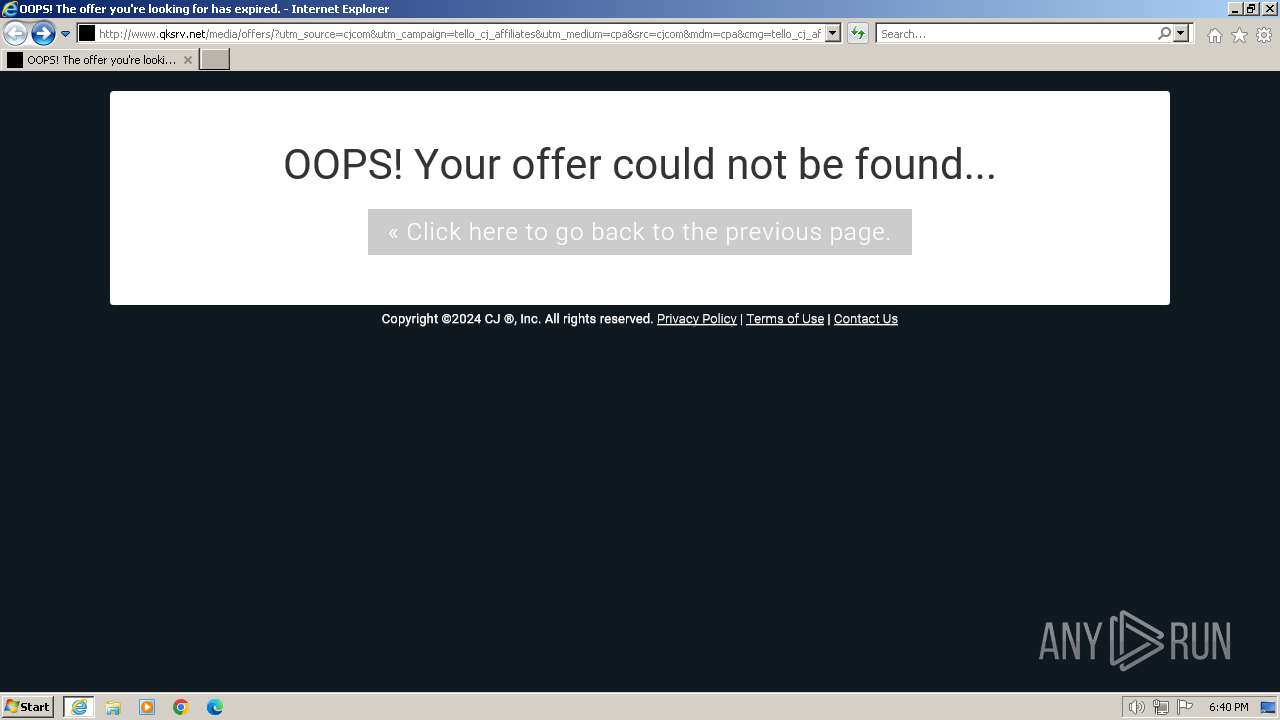
2044 | iexplore.exe | GET | 200 | 89.207.16.75:80 | http://www.qksrv.net/media/offers/?utm_source=cjcom&utm_campaign=tello_cj_affiliates&utm_medium=cpa&src=cjcom&mdm=cpa&cmg=tello_cj_affiliates&PID=7603392&CID=4344425&LID=12788914&SID=&cjevent=d15ec4abd1b111ee818500020a18b8f8 | unknown | html | 3.12 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDHN0C436%2BcTV%2F8qqtQ%3D%3D | unknown | binary | 1.40 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 89.207.16.75:80 | http://www.qksrv.net/media/offers/css/reset.css | unknown | text | 1.71 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 89.207.16.75:80 | http://www.qksrv.net/media/offers/js/jquery.js | unknown | text | 70.4 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 89.207.16.75:80 | http://www.qksrv.net/media/offers/js/modernizr-1.7.min.js | unknown | text | 8.81 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 89.207.16.75:80 | http://www.qksrv.net/media/offers/css/css3.css | unknown | text | 2.46 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2044 | iexplore.exe | 89.207.16.75:443 | www.dpbolvw.net | Conversant LLC | NL | unknown |
2044 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2044 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
2044 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
2044 | iexplore.exe | 159.127.40.213:80 | members.cj.com | VALUECLICK | US | unknown |
2044 | iexplore.exe | 159.127.40.213:443 | members.cj.com | VALUECLICK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dpbolvw.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
cj.dotomi.com |
| whitelisted |
www.emjcd.com |
| whitelisted |
members.cj.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.qksrv.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2044 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
2044 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |