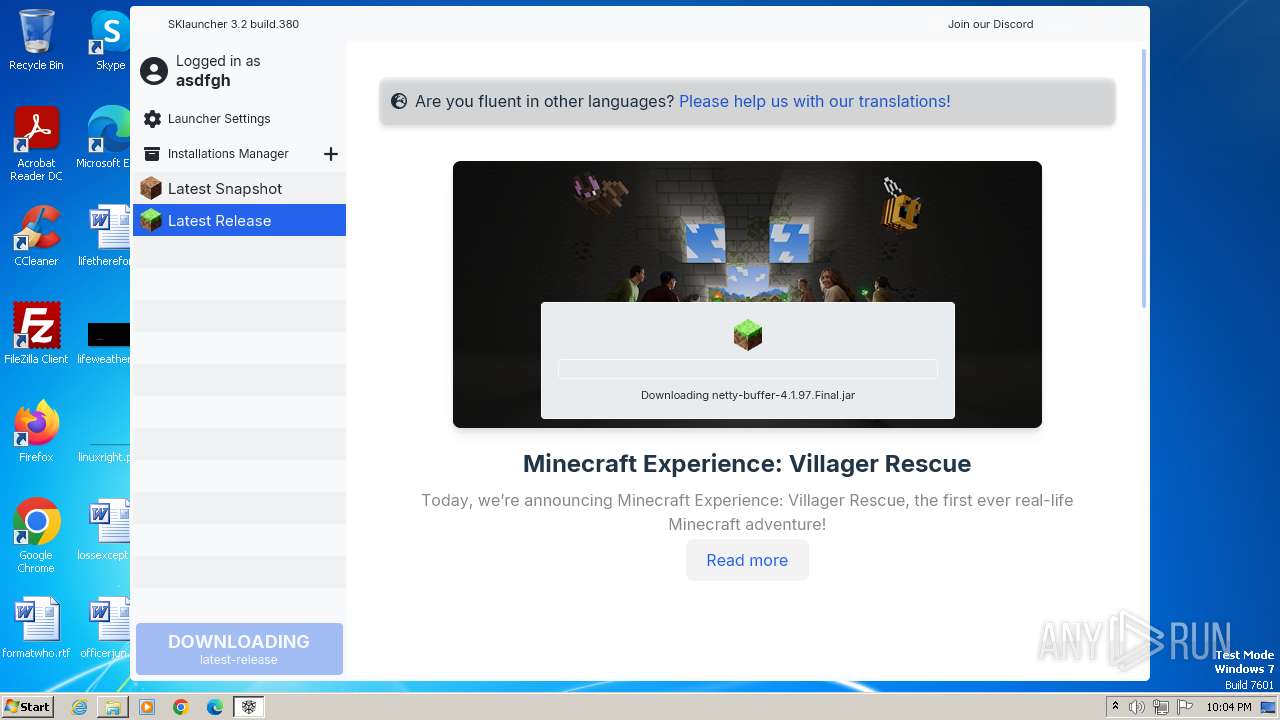
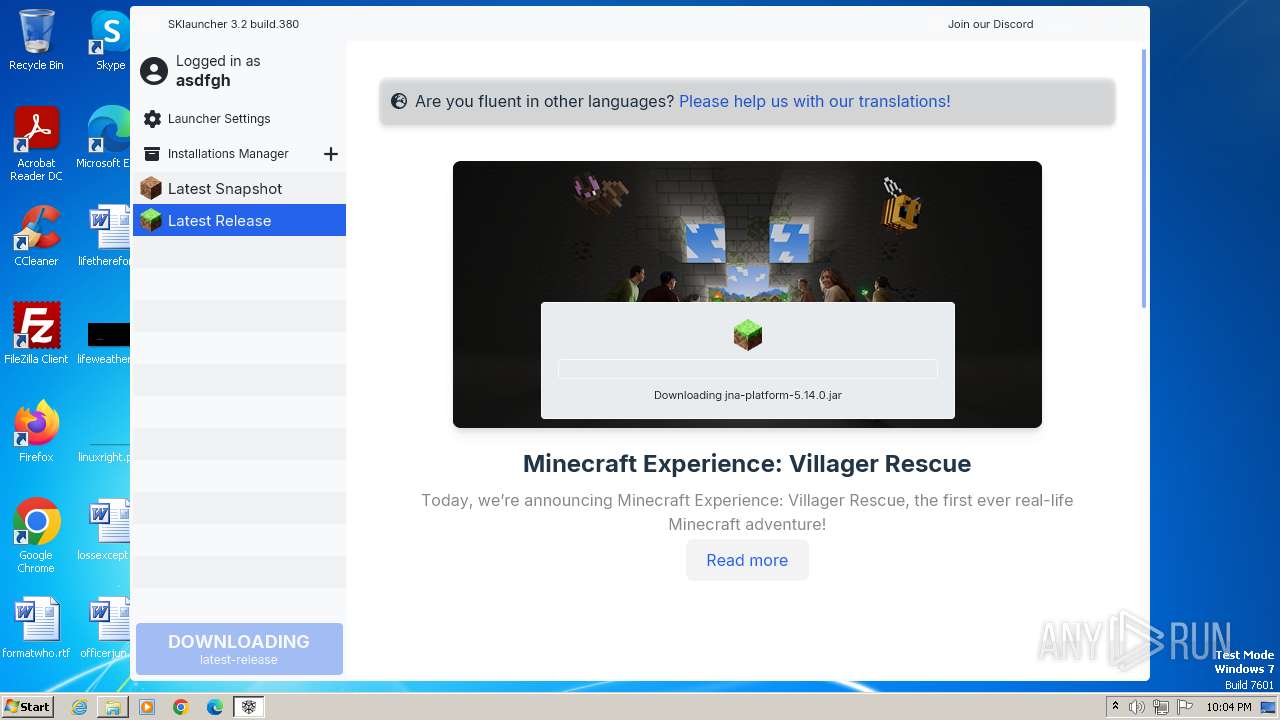
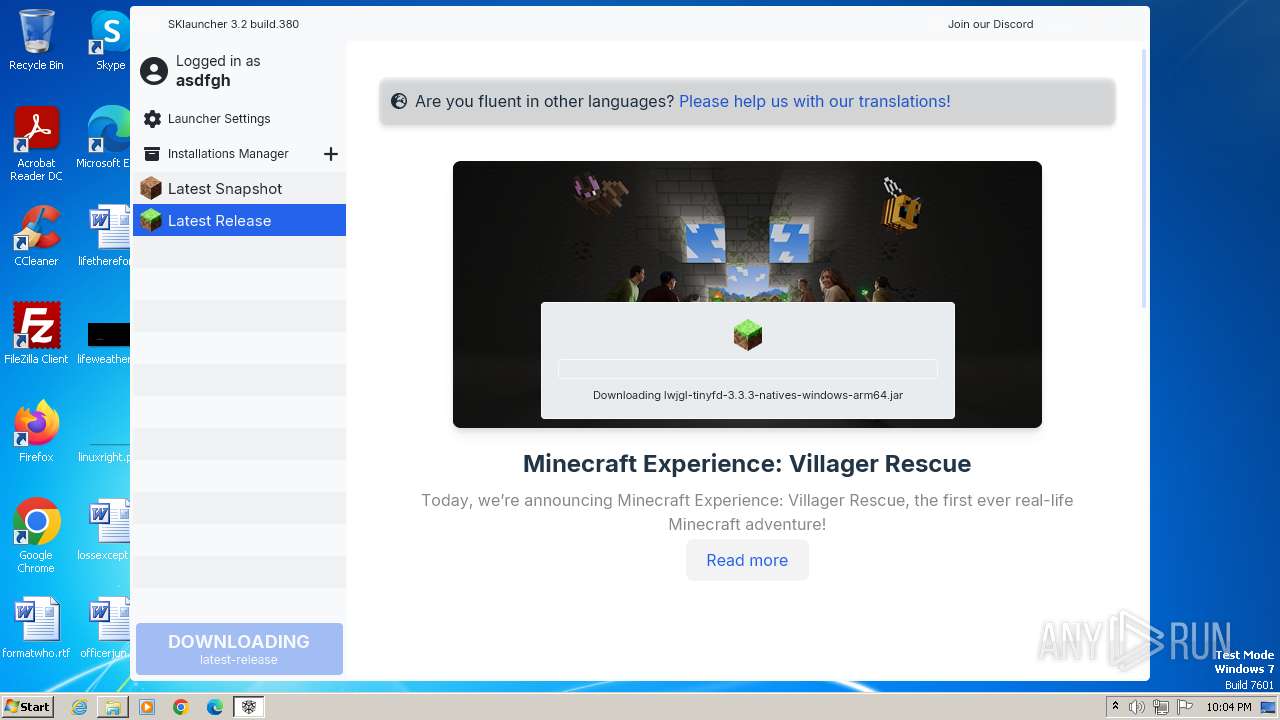
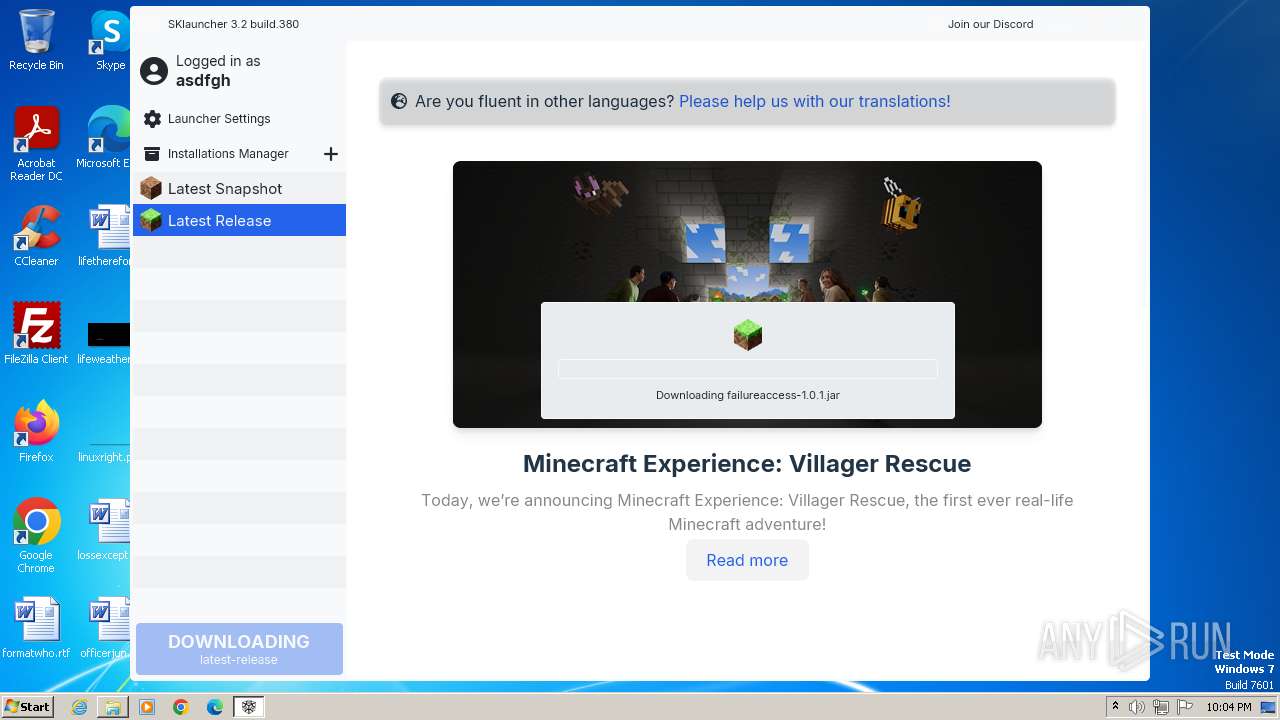
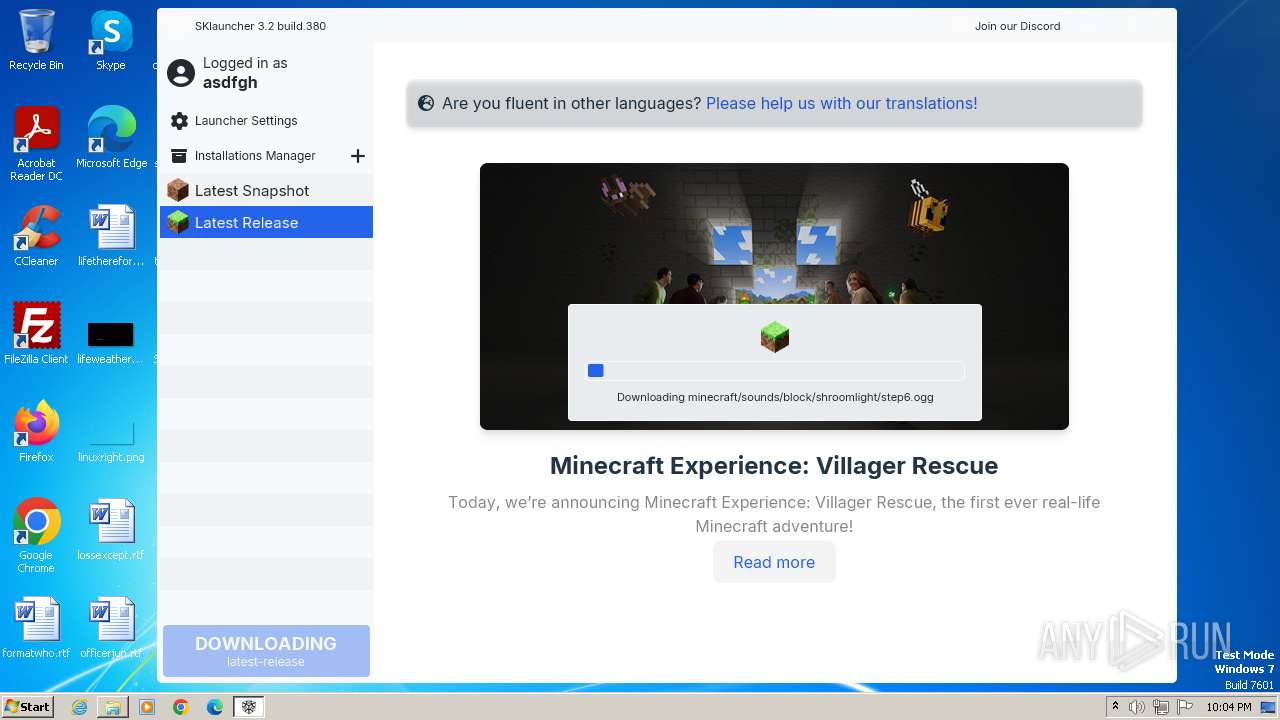
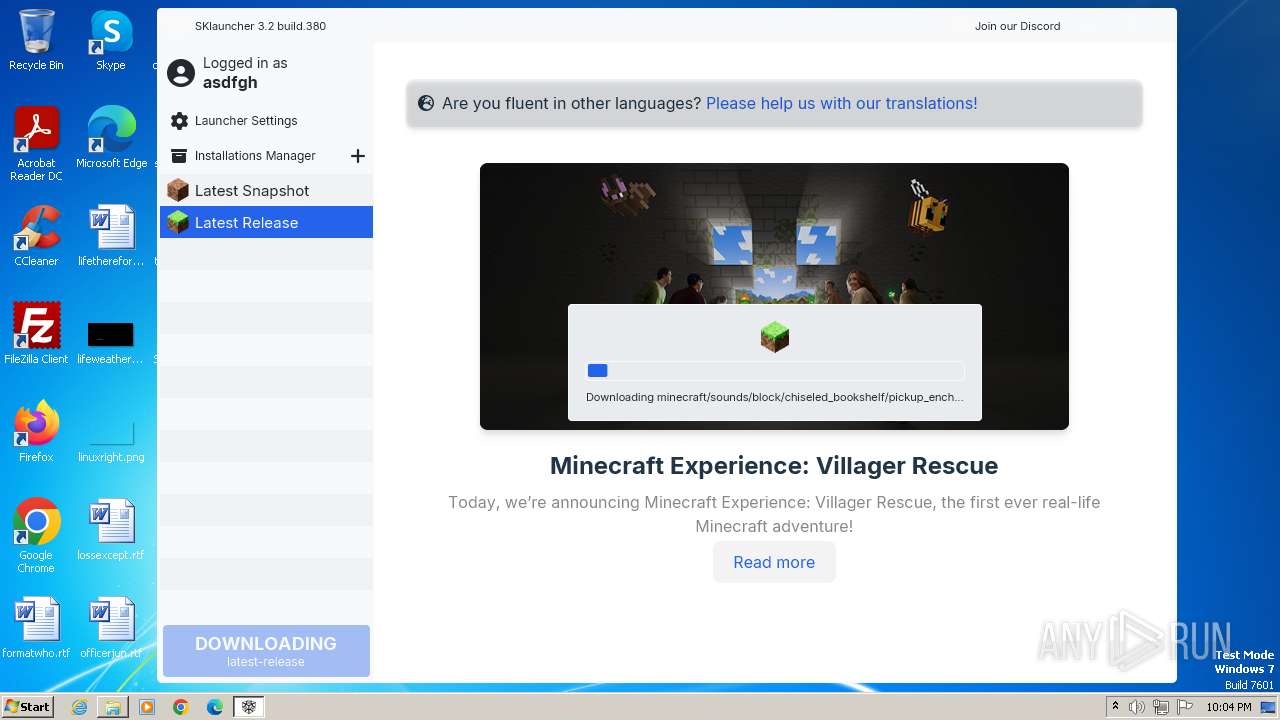
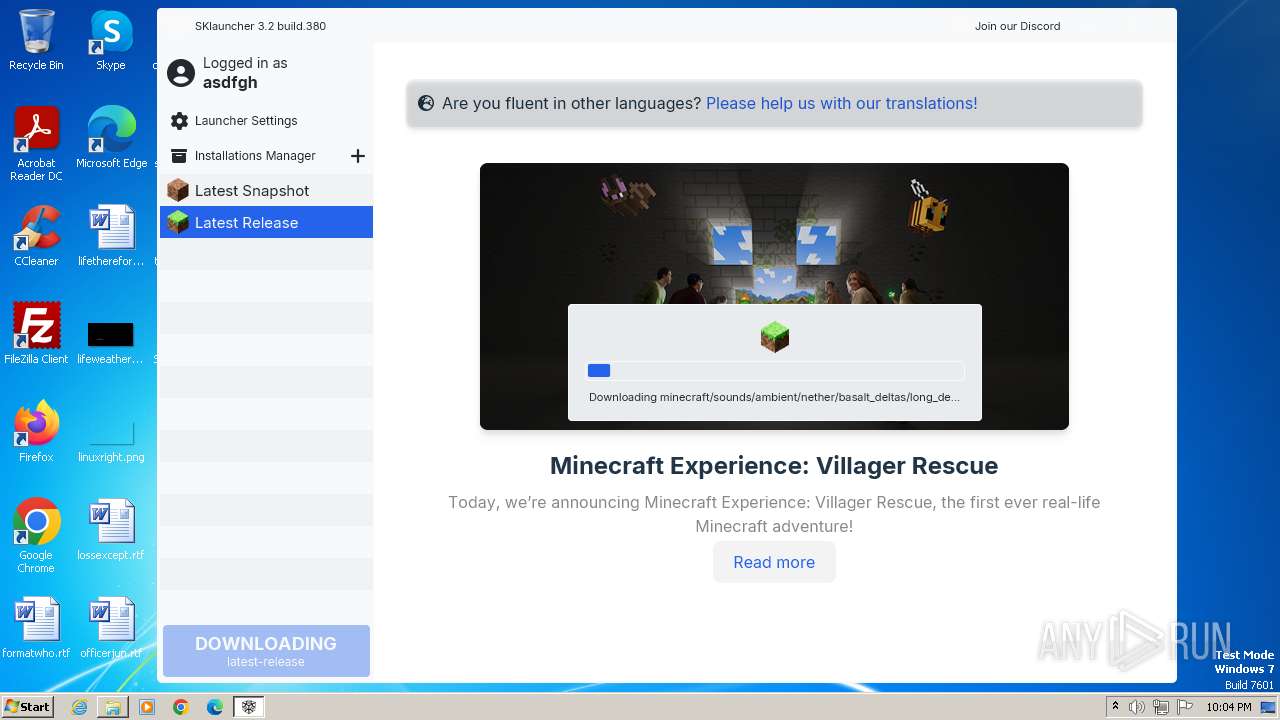
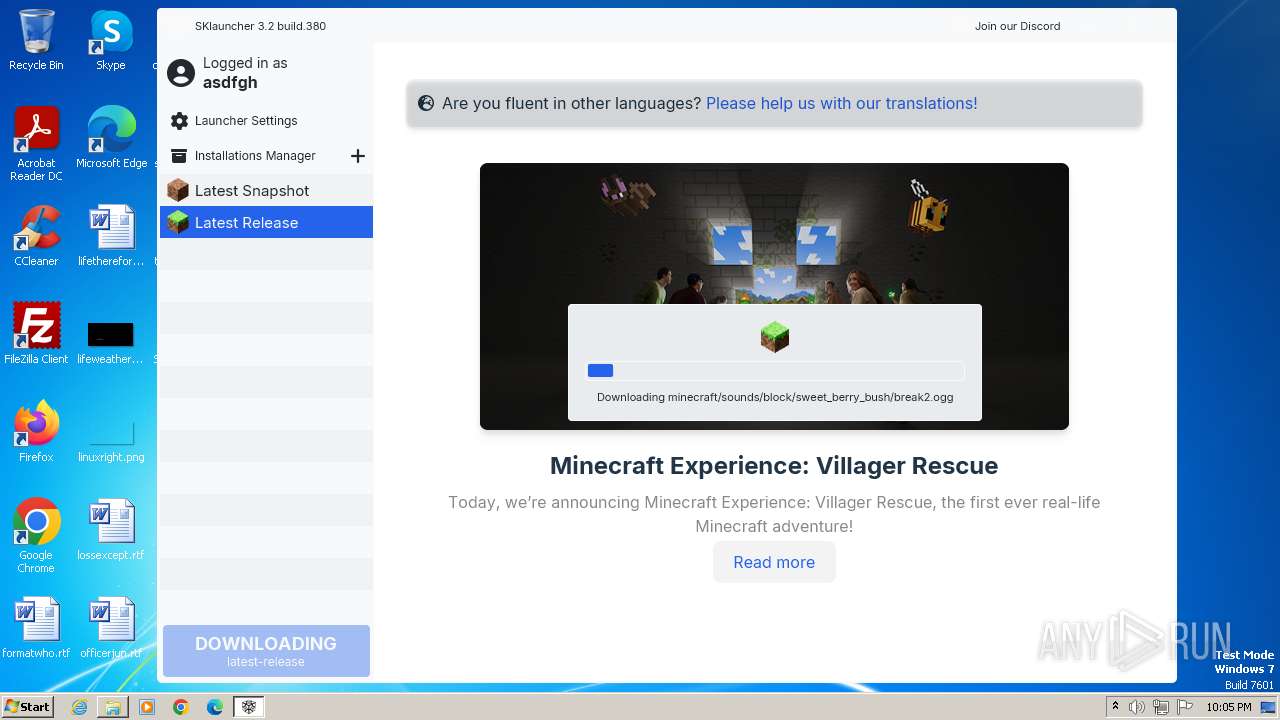
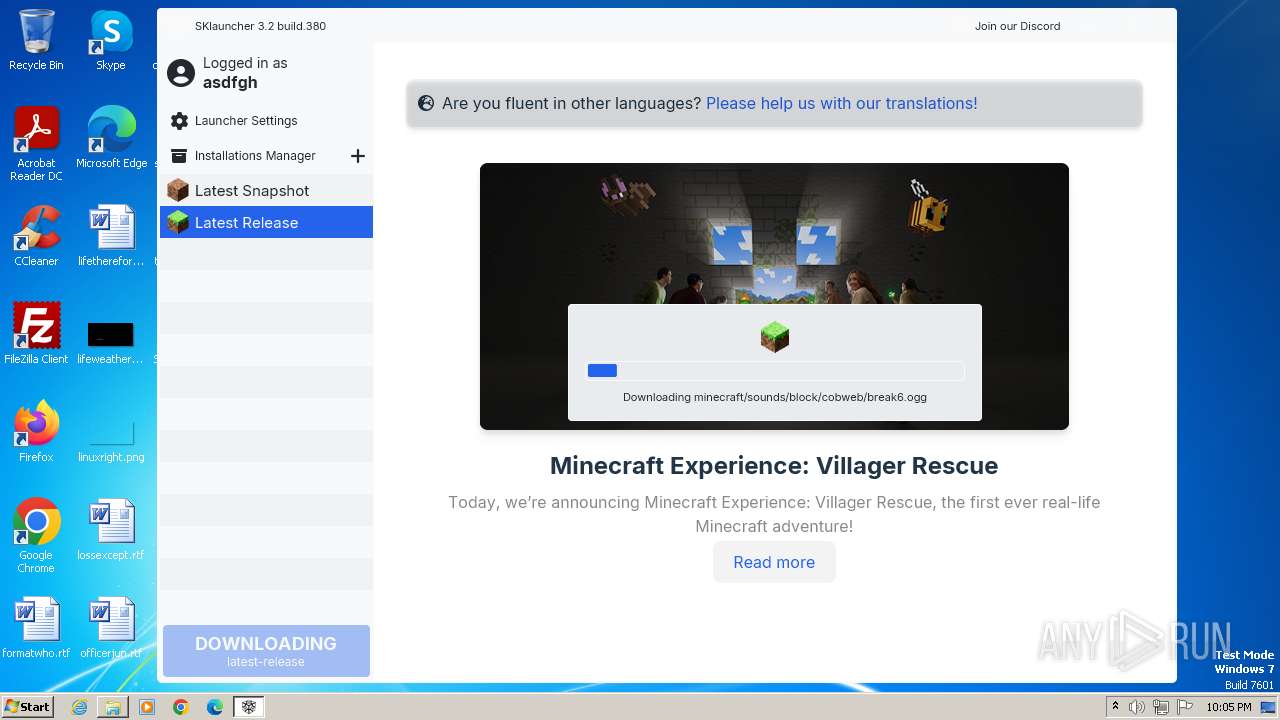
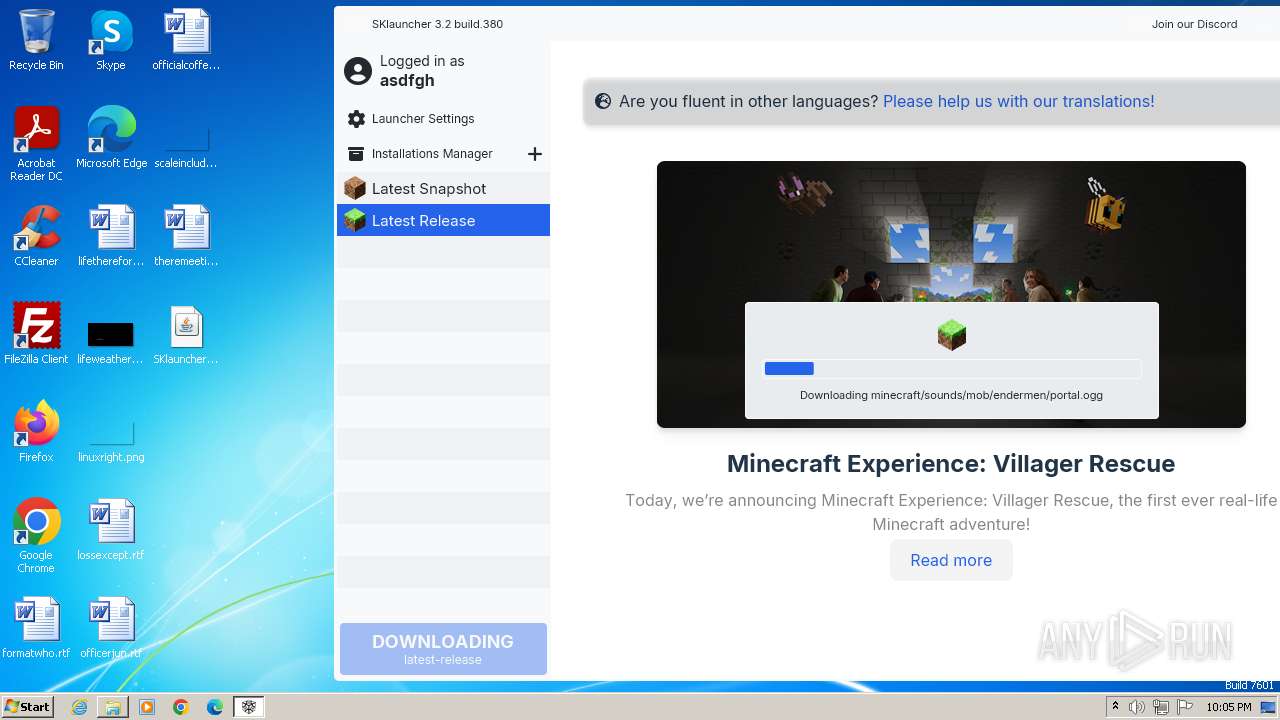
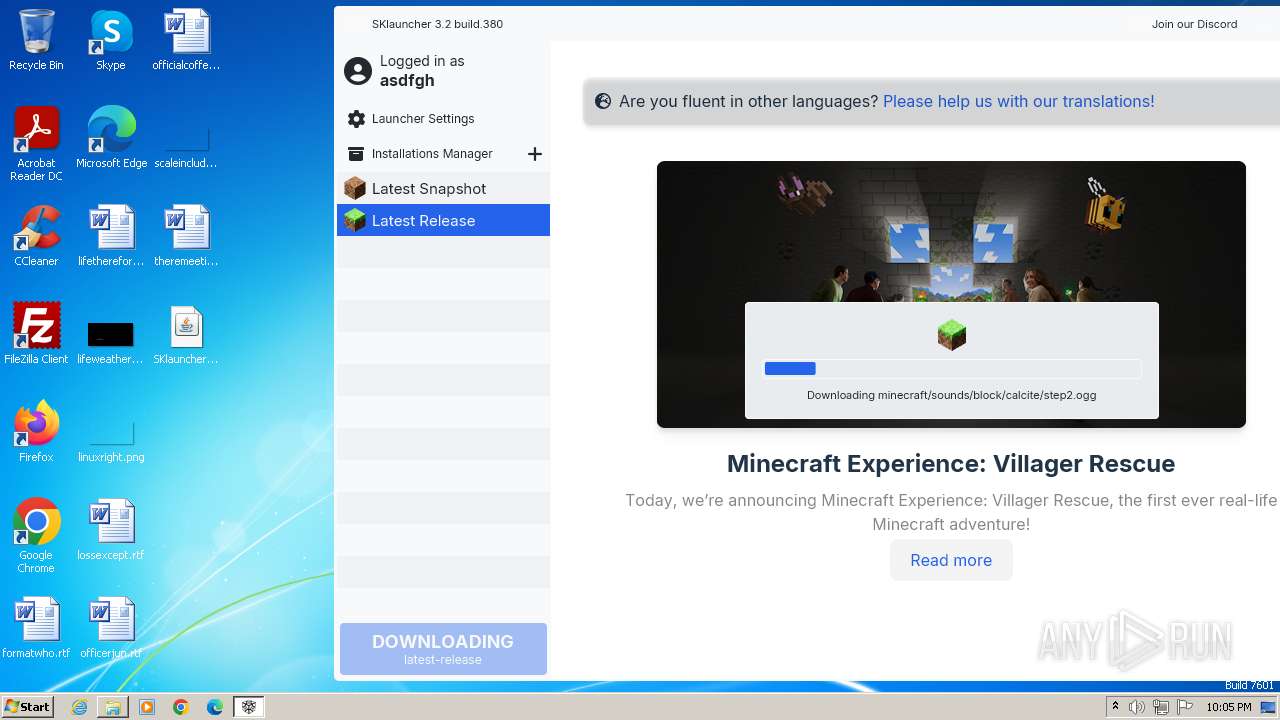
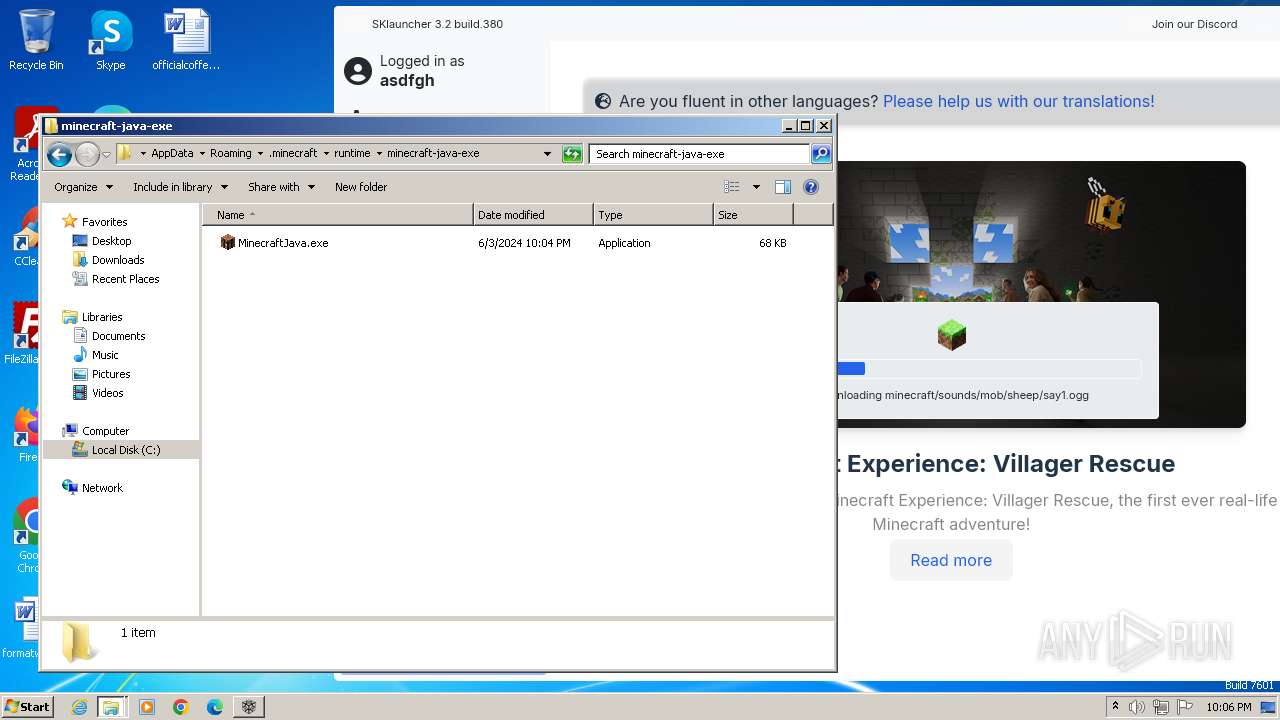
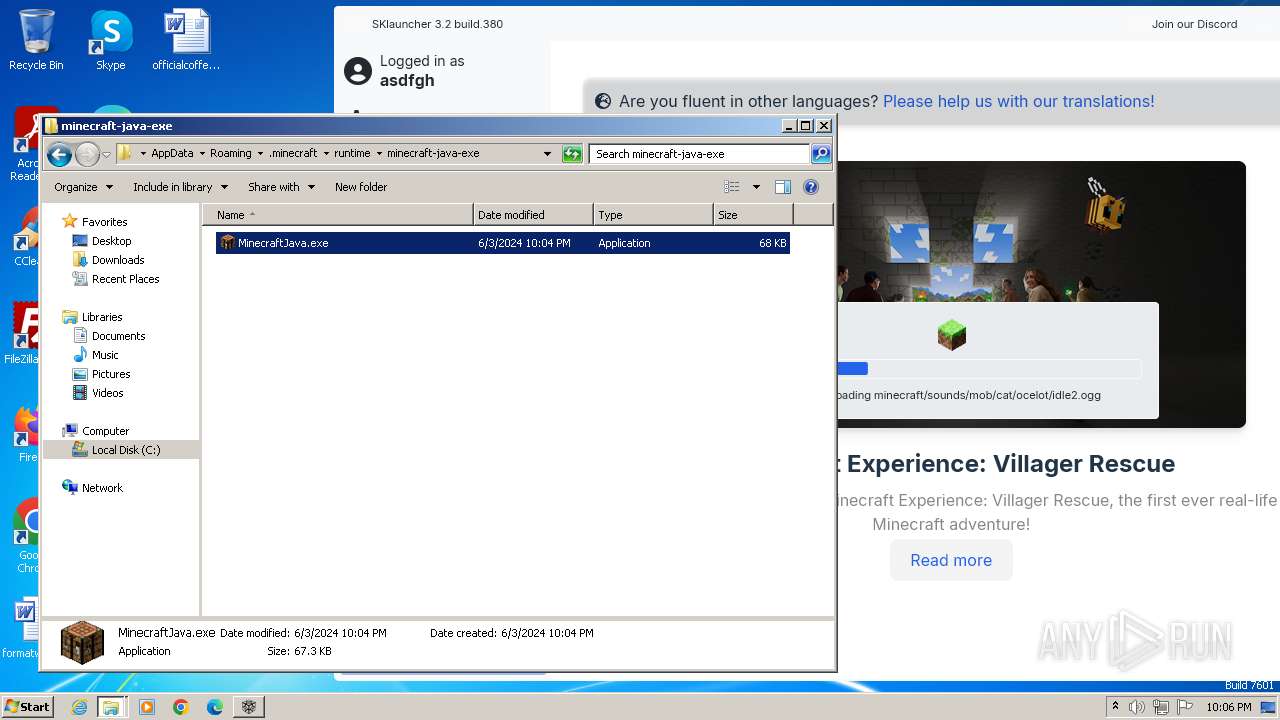
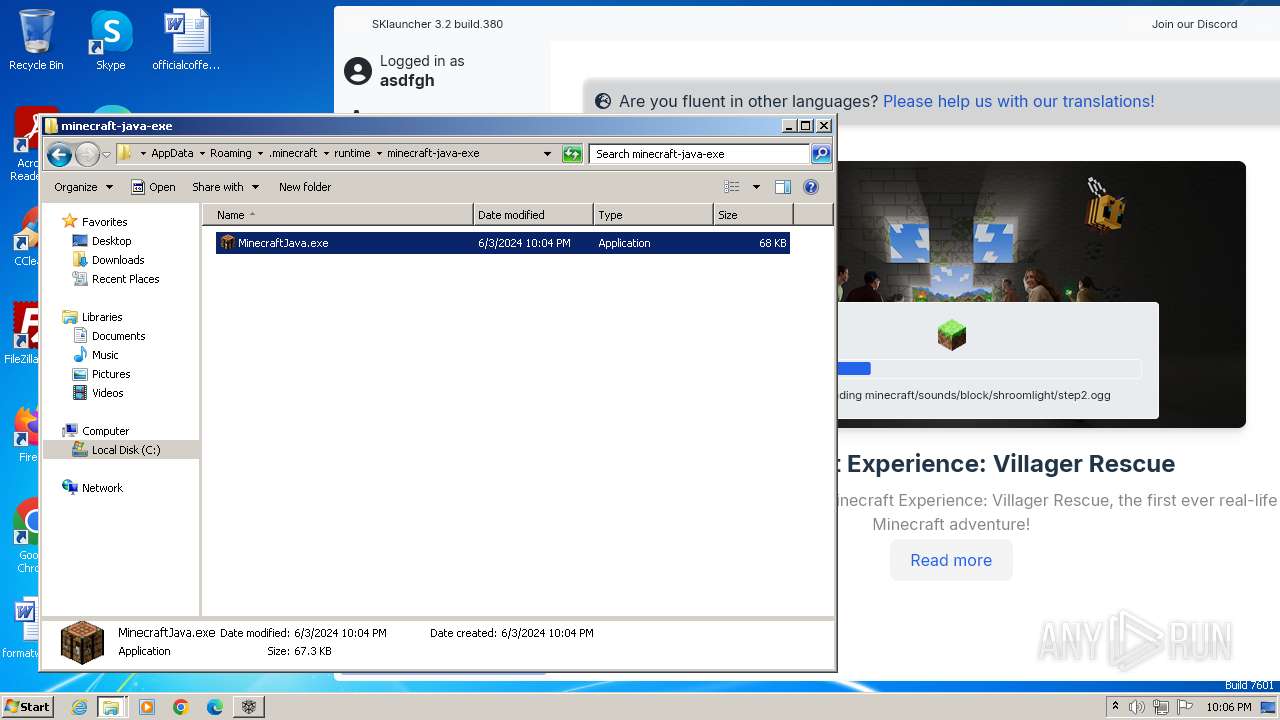
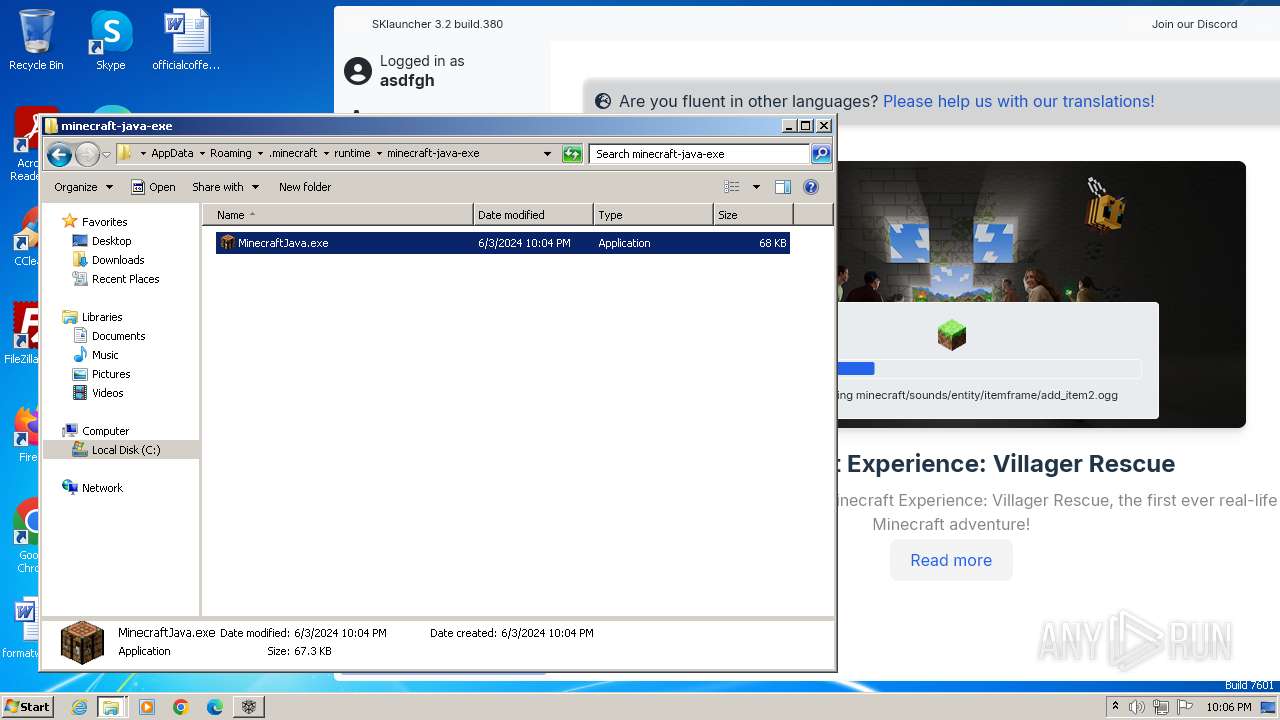
| File name: | SKlauncher-3.2.8.jar |
| Full analysis: | https://app.any.run/tasks/3747112e-6c15-4e26-9fa5-c22ccc61dbc7 |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2024, 21:02:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=deflate |
| MD5: | 3F6AE53541622BFD30D2D6A850A1C7FC |
| SHA1: | FDF2493EBB654889B16E87DE32BA353905B3F8A3 |
| SHA256: | 4BC59DACFA6A02B5E825CCB4D545E6749393B30783459637C5075A6C2B60BC68 |
| SSDEEP: | 49152:WLEmVnVgdzyad3ySXmnET2MgvHG7+y+Z3iqN5FfdUz3Ser27hDjFj9qiFxdYRTdW:PmVYeCyMmEivmWwqN3fdUmeoj9qiJWhW |
MALICIOUS
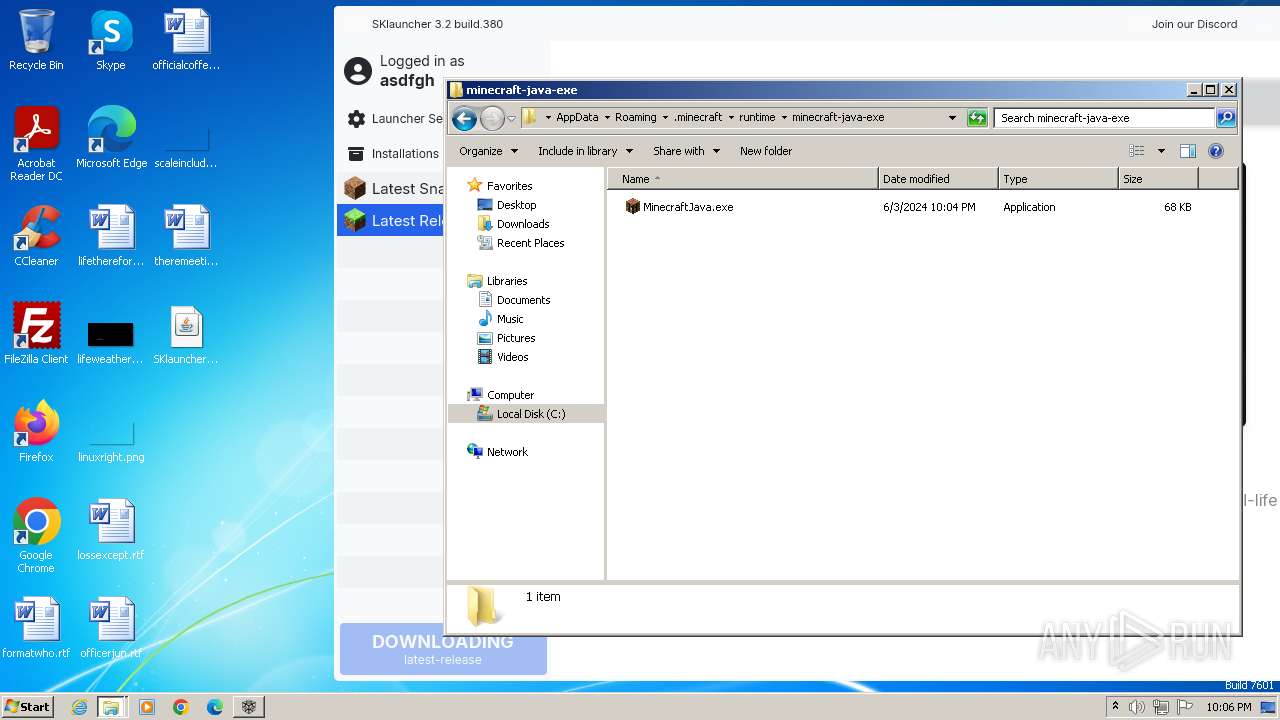
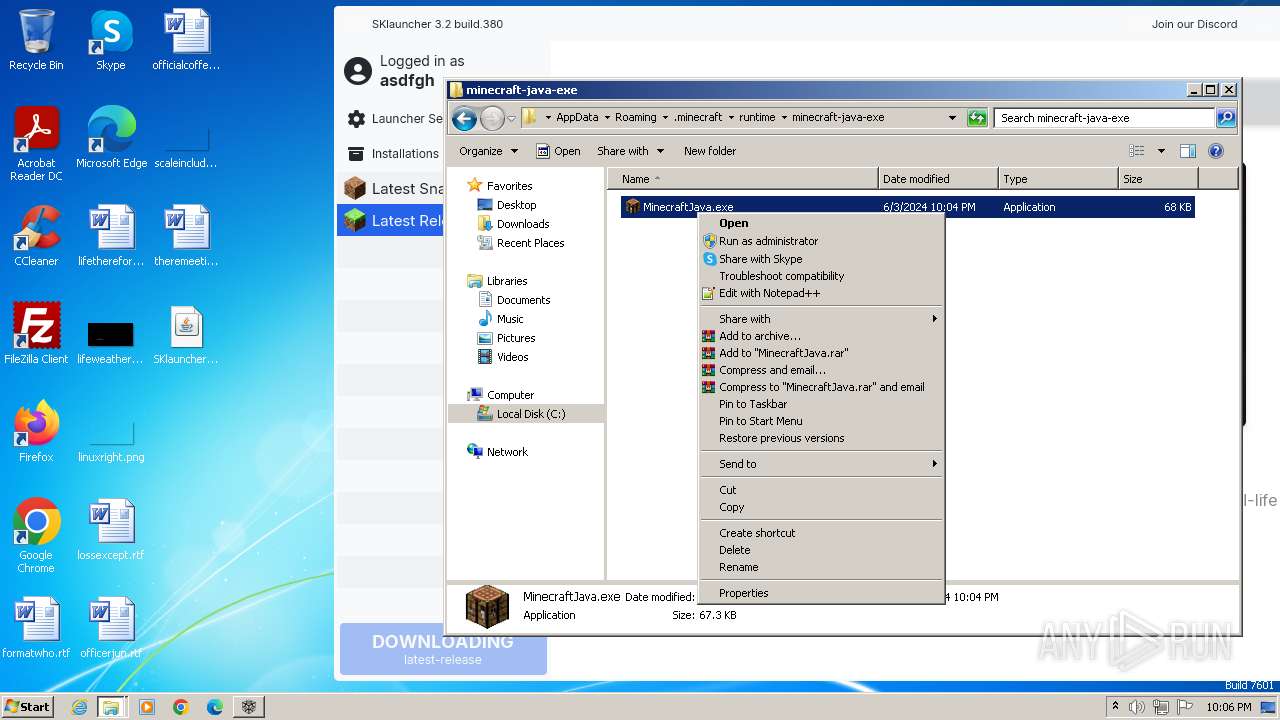
Drops the executable file immediately after the start
- javaw.exe (PID: 1652)
SUSPICIOUS
Checks for Java to be installed
- java.exe (PID: 3972)
Executable content was dropped or overwritten
- javaw.exe (PID: 1652)
INFO
Creates files in the program directory
- java.exe (PID: 3972)
Checks supported languages
- javaw.exe (PID: 1652)
- java.exe (PID: 3972)
- wmpnscfg.exe (PID: 2336)
Manual execution by a user
- explorer.exe (PID: 2108)
- javaw.exe (PID: 1652)
- wmpnscfg.exe (PID: 2336)
- explorer.exe (PID: 2808)
Create files in a temporary directory
- java.exe (PID: 3972)
- javaw.exe (PID: 1652)
Creates files or folders in the user directory
- javaw.exe (PID: 1652)
Reads the computer name
- javaw.exe (PID: 1652)
- wmpnscfg.exe (PID: 2336)
Reads the machine GUID from the registry
- javaw.exe (PID: 1652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:04:07 23:15:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | META-INF/ |
Total processes
49
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1652 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\SKlauncher-3.2.8.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2108 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2284 | reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v AppsUseLightTheme | C:\Windows\System32\reg.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2808 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Common Files\Oracle\Java\javapath\java.exe" -cp C:\Users\admin\Desktop\SKlauncher-3.2.8.jar | C:\Program Files\Common Files\Oracle\Java\javapath_target_52116515\java.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4068 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 128
Read events
2 126
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1652) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
46
Suspicious files
1 621
Text files
22
Unknown types
99
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1652 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\sklauncher\sklauncher-fx.jar.xz | — | |
MD5:— | SHA256:— | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio518879011541996765.tmp | image | |
MD5:4BC22D05B225A34A3DDB4F17D2469B77 | SHA256:FACE76C9C4FAD9476A1D80483D41772C805808A1383012B1C22065E30D32EDE6 | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio6613989175752475885.tmp | image | |
MD5:8EE50698797304540FC85117D67FE39A | SHA256:90F1E2BCC7B6C2E9B5ACBF3211ECB0B58F9E36B4F3DB56ACFC07F2A3577B644A | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF2290917484577911839.tmp | binary | |
MD5:118ABBE34A2979B66D6838805C56B7CD | SHA256:D054D998AE12BE33820B100E0ED3923D513FA5C79C6D4E7CA1953AFEB262EA9B | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio394726617383718027.tmp | image | |
MD5:4BC22D05B225A34A3DDB4F17D2469B77 | SHA256:FACE76C9C4FAD9476A1D80483D41772C805808A1383012B1C22065E30D32EDE6 | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF2627710311497524359.tmp | pi2 | |
MD5:FDB50E0D48CDCF775FA1AC0DC3C33BD4 | SHA256:64F8BE6E55C37E32EF03DA99714BF3AA58B8F2099BFE4F759A7578E3B8291123 | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF6730186834965428537.tmp | binary | |
MD5:FF5FDC6F42C720A3EBD7B60F6D605888 | SHA256:1936D24CB0F4CE7006E08C6EF4243D2E42A7B45F2249F8FE54D92F76A317DFD1 | |||
| 3972 | java.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:269EF8DB621022181FCDE5F4F3F3BE3D | SHA256:D9375817E77065E62BA9D9CC6553435CE4B691CE1760E478D0CA4B71D4C3FD1B | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\sklauncher\sklauncher_data.bin | text | |
MD5:F579158E1B0BA1000239E45A9C67CC85 | SHA256:27AED4CA0122CCC3B17D457722B8921C32BC2844251C1CEA5481E4852FA10CA8 | |||
| 1652 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF8612958439133600321.tmp | binary | |
MD5:4B1FFAD3C0075AF22674765FF1EE2F56 | SHA256:FE3714926082AC5764327E3B67AE52CB6F0CF6B8C4221C064A6CACF821079414 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
63
DNS requests
19
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1652 | javaw.exe | 188.114.96.3:443 | files.skmedix.pl | CLOUDFLARENET | NL | unknown |
1652 | javaw.exe | 188.114.97.3:443 | files.skmedix.pl | CLOUDFLARENET | NL | unknown |
1652 | javaw.exe | 13.107.246.44:443 | piston-meta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1652 | javaw.exe | 172.217.16.200:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
1652 | javaw.exe | 104.21.234.235:443 | rsms.me | CLOUDFLARENET | — | unknown |
1652 | javaw.exe | 104.16.80.73:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
files.skmedix.pl |
| unknown |
piston-meta.mojang.com |
| unknown |
meta.skmedix.pl |
| unknown |
beta.skmedix.pl |
| unknown |
rsms.me |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
launchercontent.mojang.com |
| whitelisted |
region1.analytics.google.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |