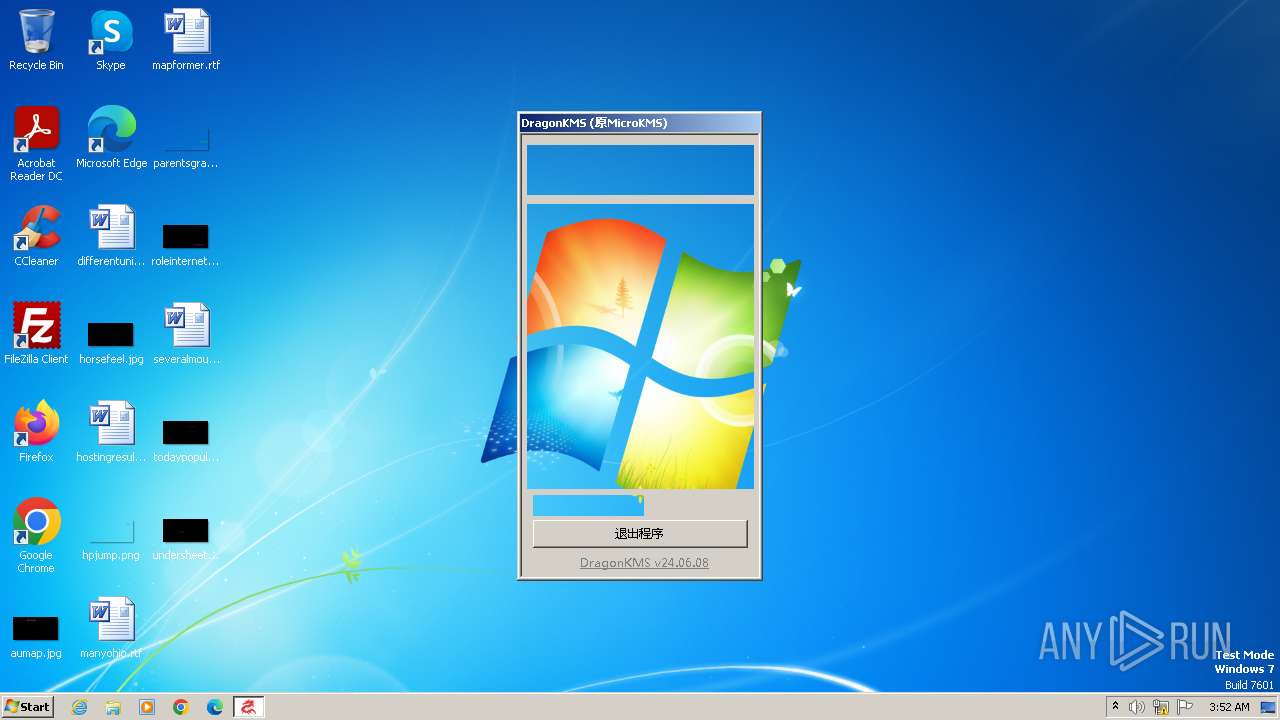
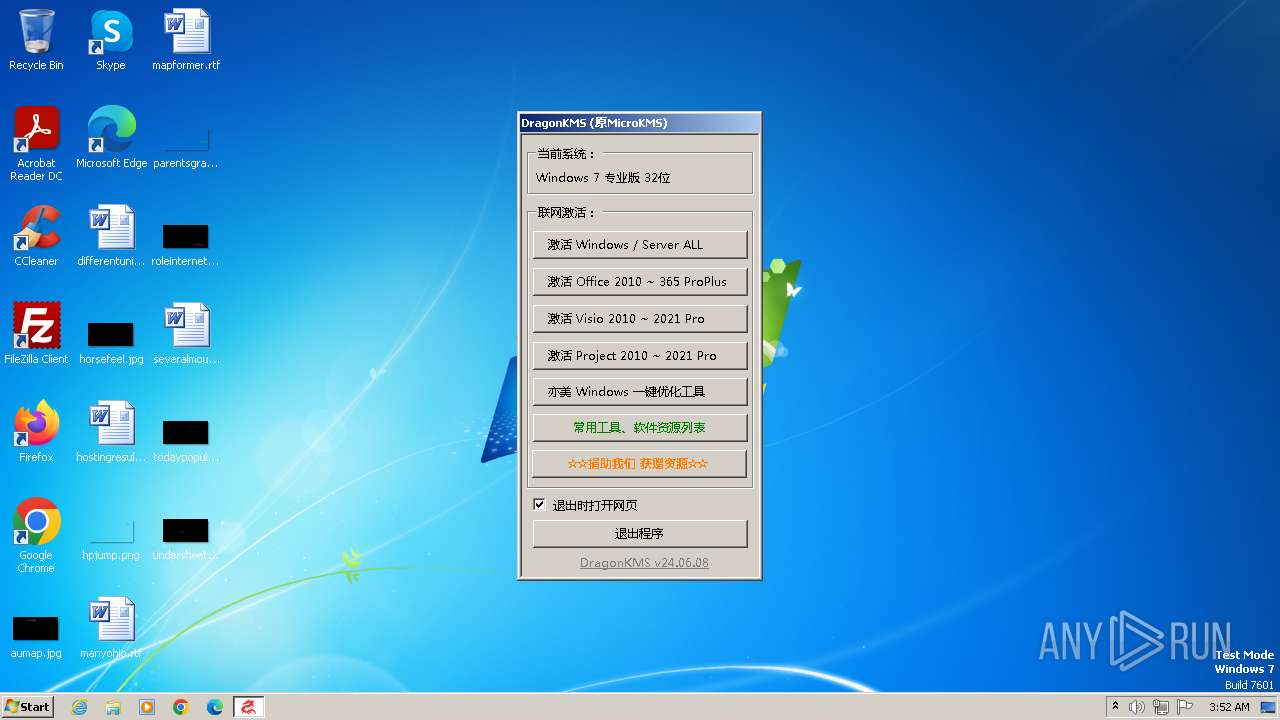
| File name: | DragonKMS v24.06.08.exe |
| Full analysis: | https://app.any.run/tasks/6d212553-9b0c-476c-abf3-10cd1e88fc5b |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2024, 02:52:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 8A99D79C4AA086978E3B3933E4C5A9A5 |
| SHA1: | B083B5A74DAFAAF2348CF527D1B03BA9995C208F |
| SHA256: | 4BB880FDA08F132E7DBF1B87DD9999C6E79FA738B017A42FF443442F9695A159 |
| SSDEEP: | 3072:lnGm+BwrSdsHuxgbCF0v2ZIDq1fkhojAROnM9K7iVE/Gp3uDmJQw0C1K01rT/eeh:IqKi3333PM |
MALICIOUS
Drops the executable file immediately after the start
- DragonKMS v24.06.08.exe (PID: 4084)
Opens a text file (SCRIPT)
- cscript.exe (PID: 1592)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
SUSPICIOUS
Reads the Internet Settings
- DragonKMS v24.06.08.exe (PID: 4084)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1592)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 2044)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1592)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1592)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
Starts CMD.EXE for commands execution
- DragonKMS v24.06.08.exe (PID: 4084)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1592)
The process executes VB scripts
- cmd.exe (PID: 2044)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1592)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
- cscript.exe (PID: 1592)
Creates file in the systems drive root
- cmd.exe (PID: 2044)
INFO
Reads the machine GUID from the registry
- DragonKMS v24.06.08.exe (PID: 4084)
Checks supported languages
- DragonKMS v24.06.08.exe (PID: 4084)
- wmpnscfg.exe (PID: 1136)
Reads the computer name
- DragonKMS v24.06.08.exe (PID: 4084)
- wmpnscfg.exe (PID: 1136)
Reads product name
- DragonKMS v24.06.08.exe (PID: 4084)
Disables trace logs
- DragonKMS v24.06.08.exe (PID: 4084)
Manual execution by a user
- wmpnscfg.exe (PID: 1136)
Reads Environment values
- DragonKMS v24.06.08.exe (PID: 4084)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1592)
- cscript.exe (PID: 2024)
- cscript.exe (PID: 1424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2039:03:17 18:08:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 603648 |
| InitializedDataSize: | 104448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9545a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 24.6.8.0 |
| ProductVersionNumber: | 24.6.8.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | 分享也是一种美,亦是美网络。 |
| CompanyName: | - |
| FileDescription: | DragonKMS |
| FileVersion: | 24.06.08 |
| InternalName: | DragonKMS.exe |
| LegalCopyright: | 这是一款免费软件。 |
| LegalTrademarks: | - |
| OriginalFileName: | DragonKMS.exe |
| ProductName: | DragonKMS |
| ProductVersion: | 24.06.08 |
| AssemblyVersion: | 24.6.8.0 |
Total processes
45
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1136 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | cscript C:\Windows\System32\slmgr.vbs /ato | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1592 | cscript C:\Windows\System32\slmgr.vbs /skms 121.37.146.102 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2024 | cscript C:\Windows\System32\slmgr.vbs /ipk FJ82H-XT6CR-J8D7P-XQJJ2-GPDD4 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2044 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | DragonKMS v24.06.08.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\DragonKMS v24.06.08.exe" | C:\Users\admin\AppData\Local\Temp\DragonKMS v24.06.08.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DragonKMS Exit code: 3221226540 Version: 24.06.08 Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\AppData\Local\Temp\DragonKMS v24.06.08.exe" | C:\Users\admin\AppData\Local\Temp\DragonKMS v24.06.08.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: DragonKMS Version: 24.06.08 Modules
| |||||||||||||||
Total events
2 307
Read events
2 295
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4084) DragonKMS v24.06.08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonKMS v24_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | DragonKMS v24.06.08.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/go/DragonKMS/DragonKMS.html | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4084 | DragonKMS v24.06.08.exe | 116.255.154.157:80 | www.yishimei.cn | CHINA UNICOM China169 Backbone | CN | unknown |
308 | sppsvc.exe | 121.37.146.102:1688 | — | Huawei Cloud Service data center | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.yishimei.cn |
| unknown |