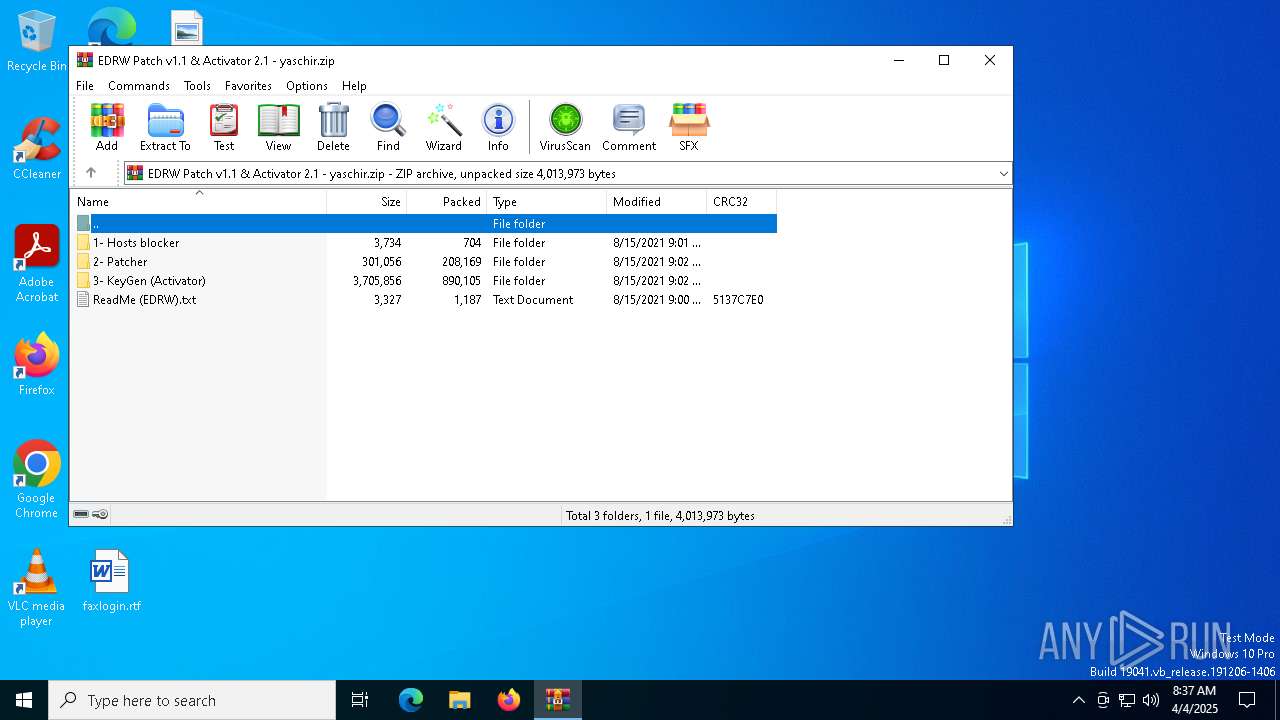
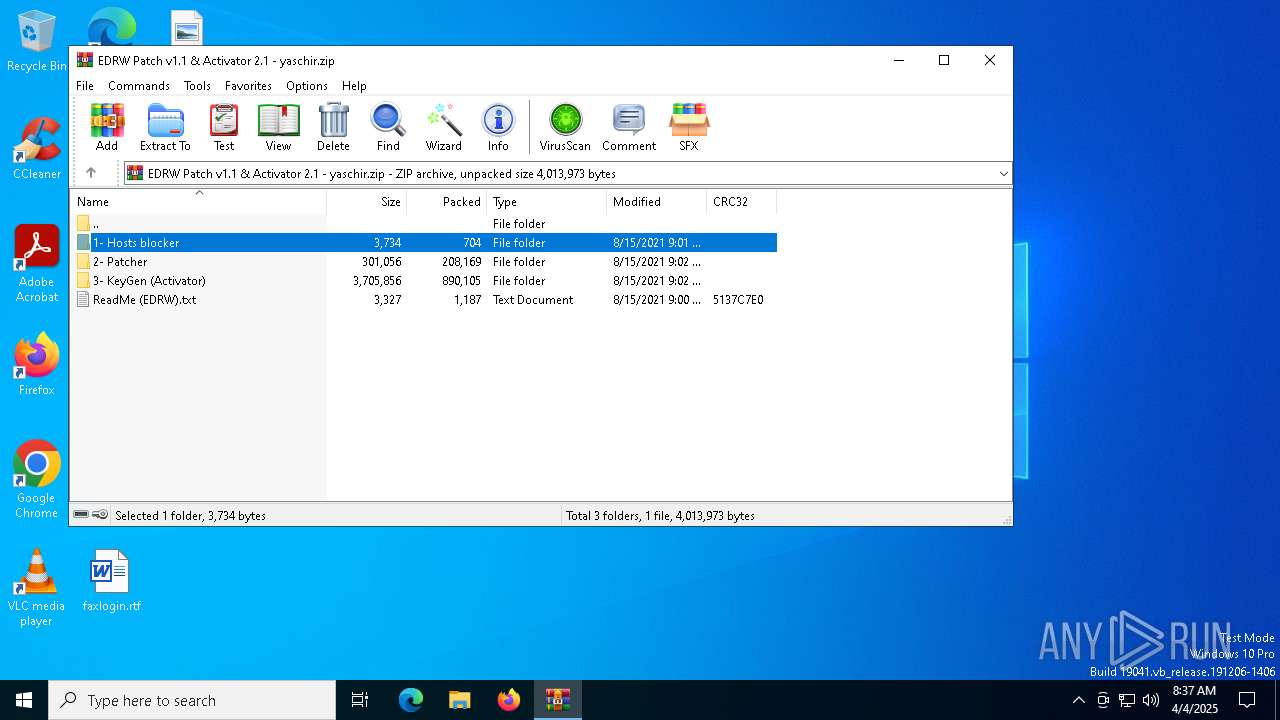
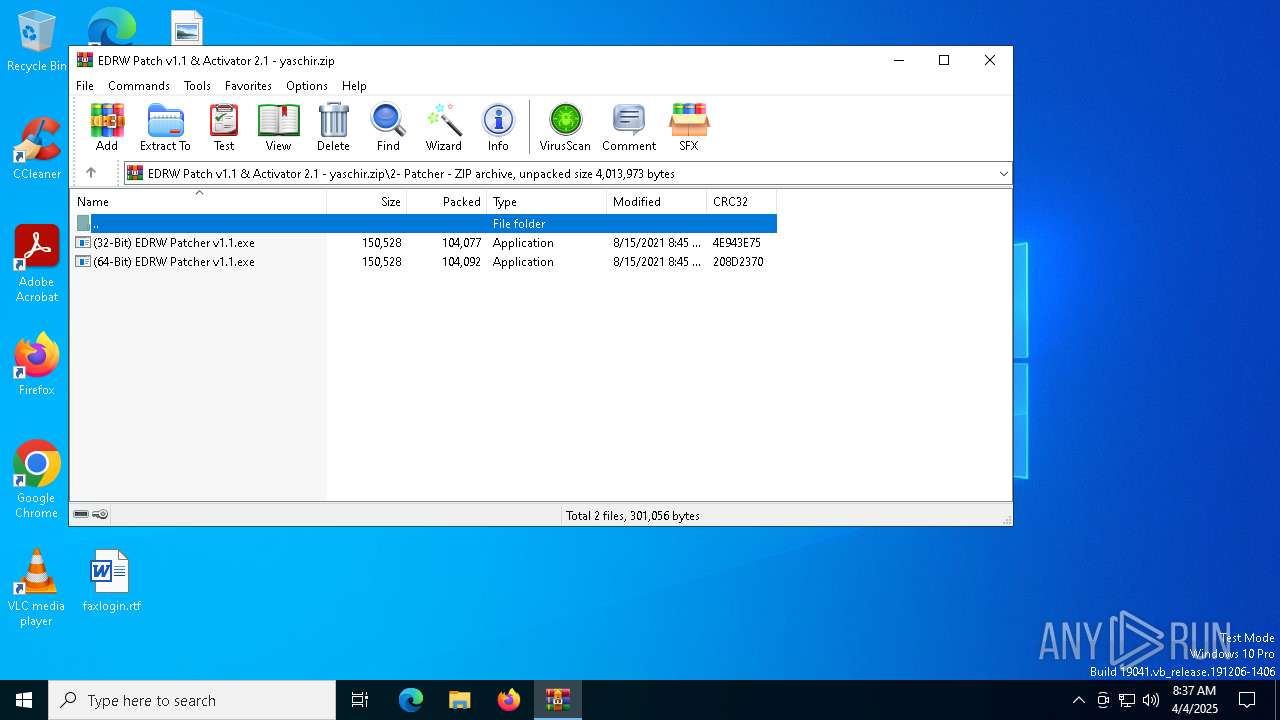
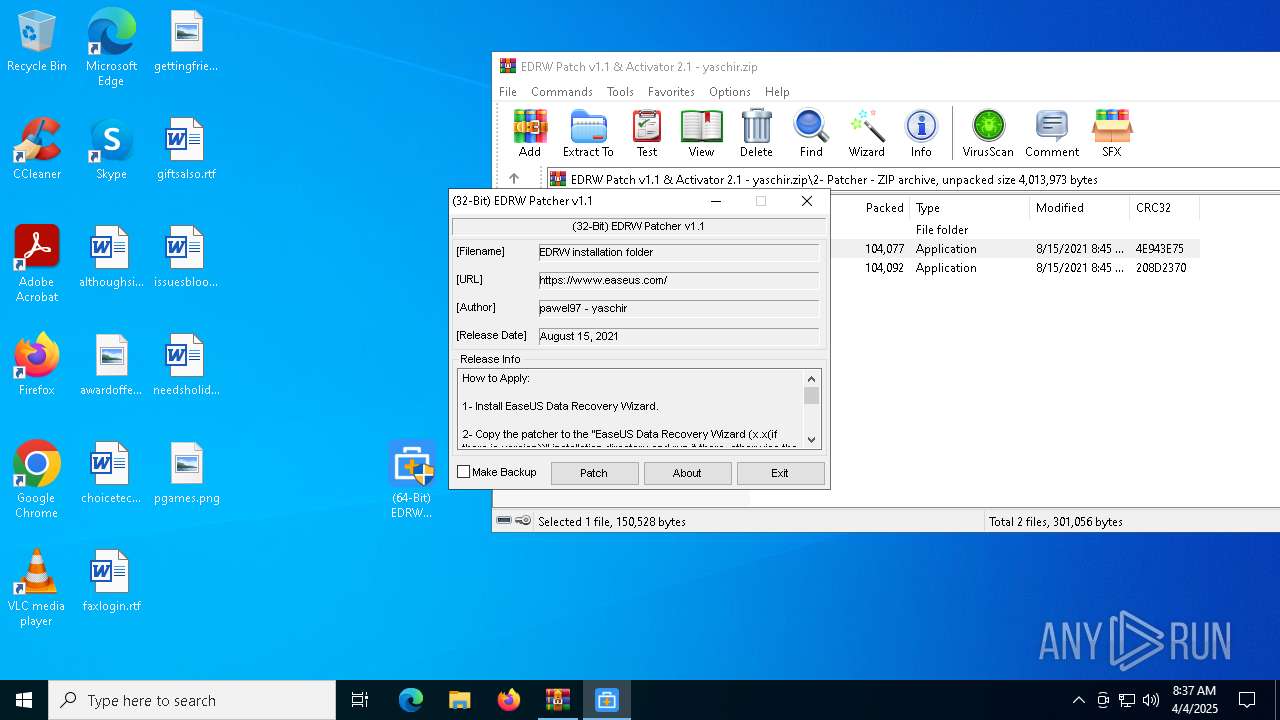
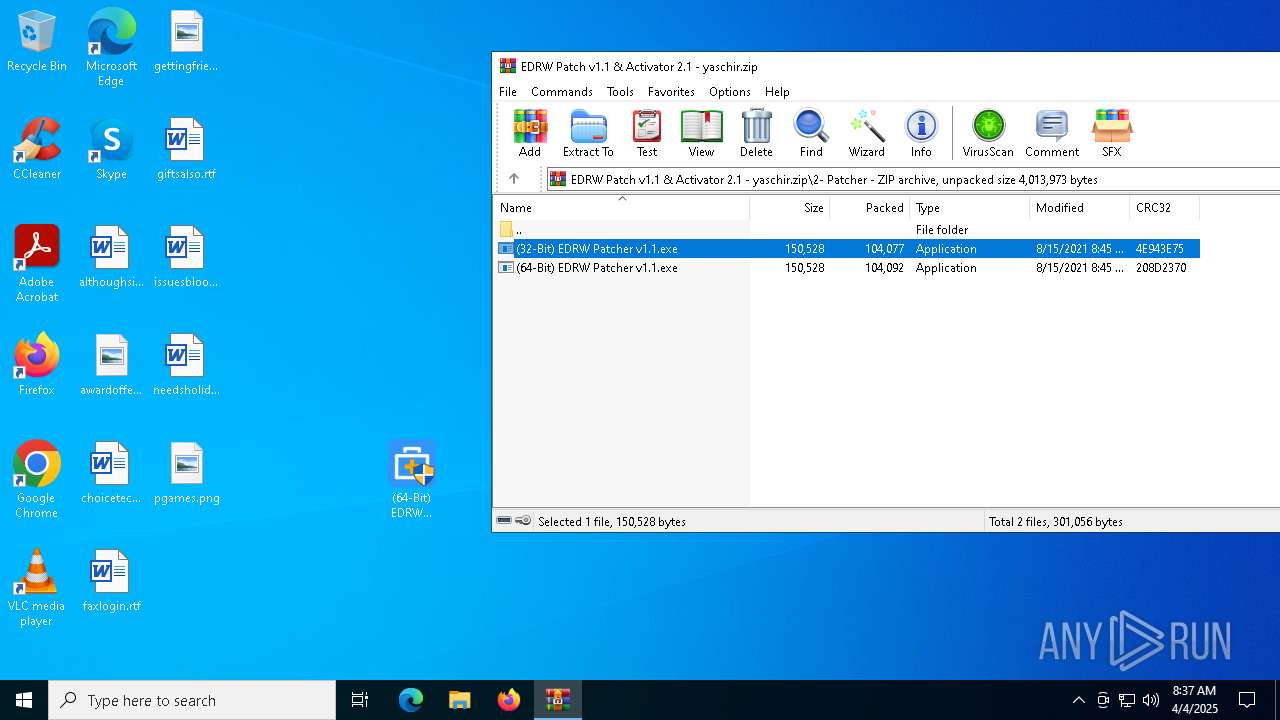
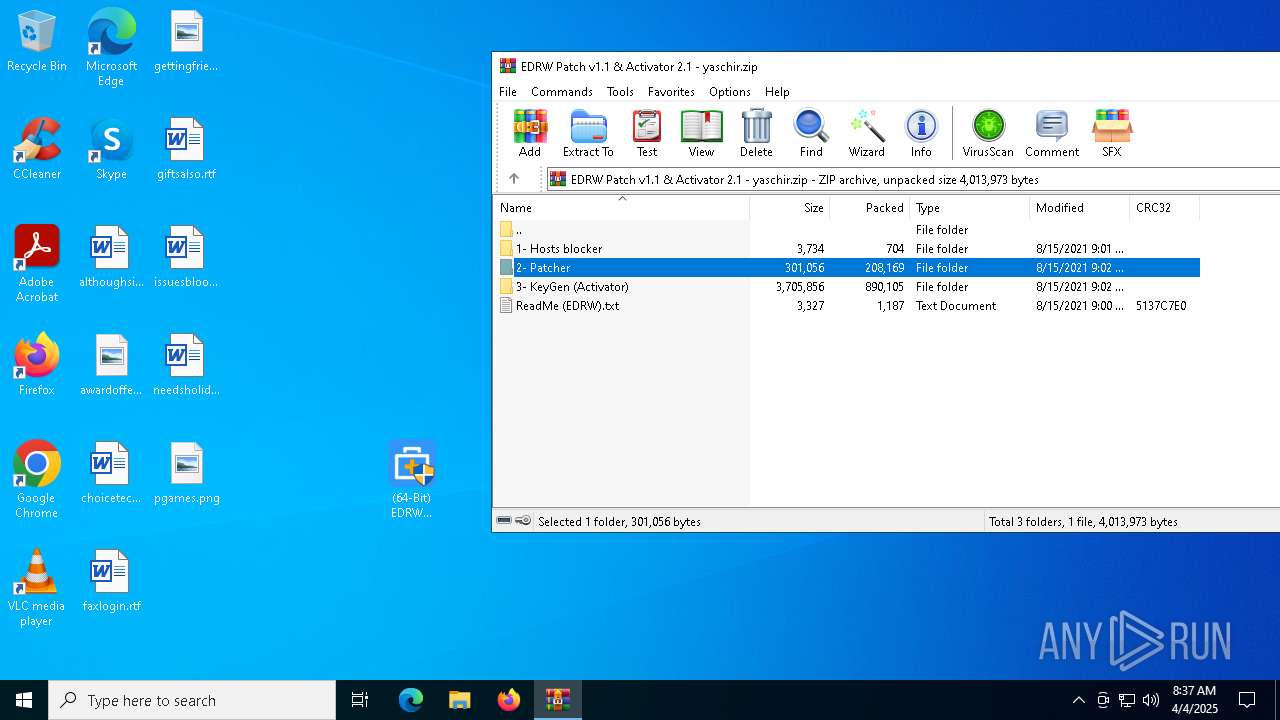
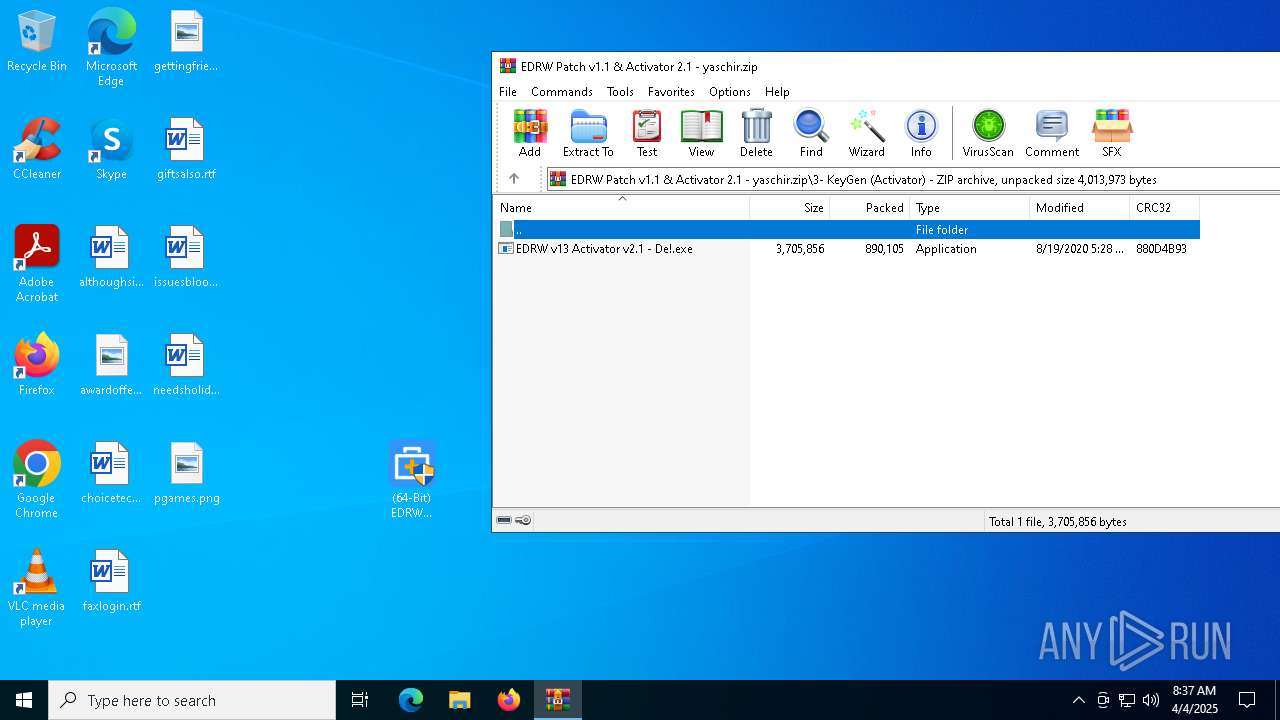
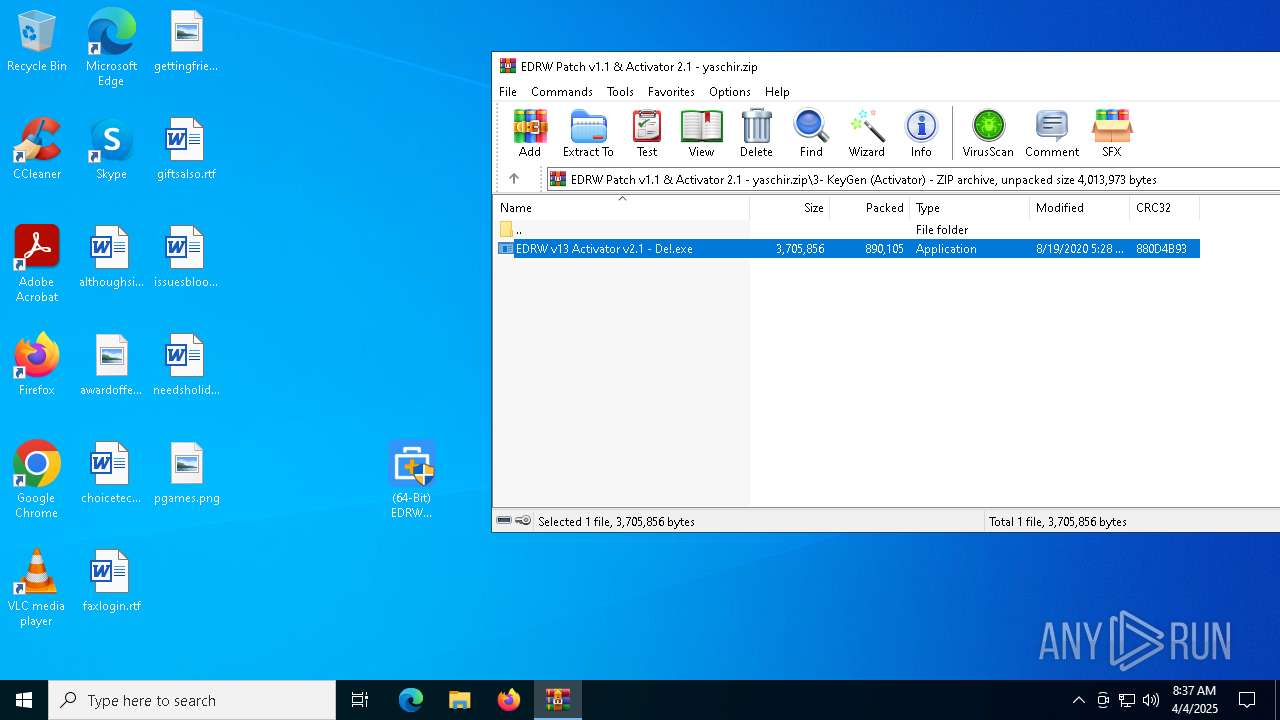
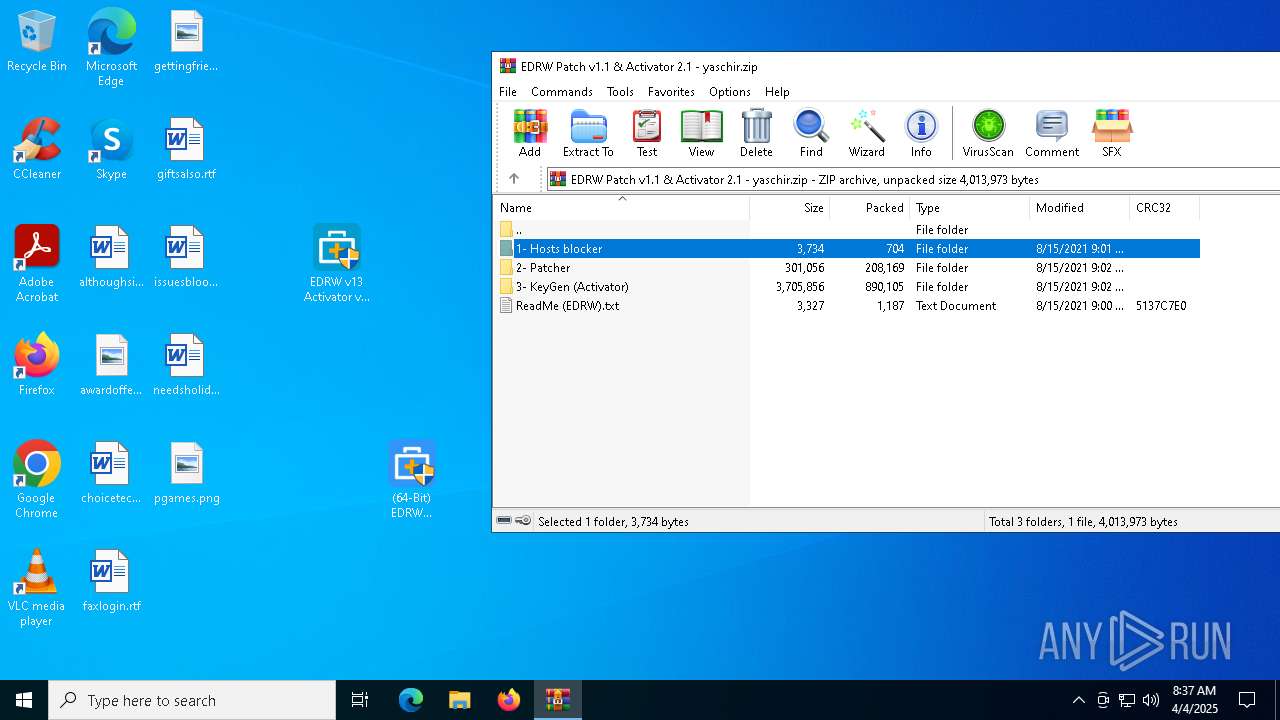
| File name: | EDRW Patch v1.1 & Activator 2.1 - yaschir.zip |
| Full analysis: | https://app.any.run/tasks/6974fbfe-43e5-417c-ad66-97fab44cb3d9 |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 08:37:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 92DE5DBC76CA5302D92B725B0F7FC9C2 |
| SHA1: | 52B42EF3C9B86334133F9B916C1BB934822BBD72 |
| SHA256: | 4B929EFE2753988A399F16C24A26A9610FB9EEFFA05D641FDAAE8213E907AA9D |
| SSDEEP: | 49152:4l/8zqTyaZifBml/8zLpwlYu/32enMkJZCYuO8EZF7vuAh1BT+MVmczBfanu5nLt:4R8zqTyjgR8zLYYY32yMVSH7f1BT+MVh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- (32-Bit) EDRW Patcher v1.1.exe (PID: 6744)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5668)
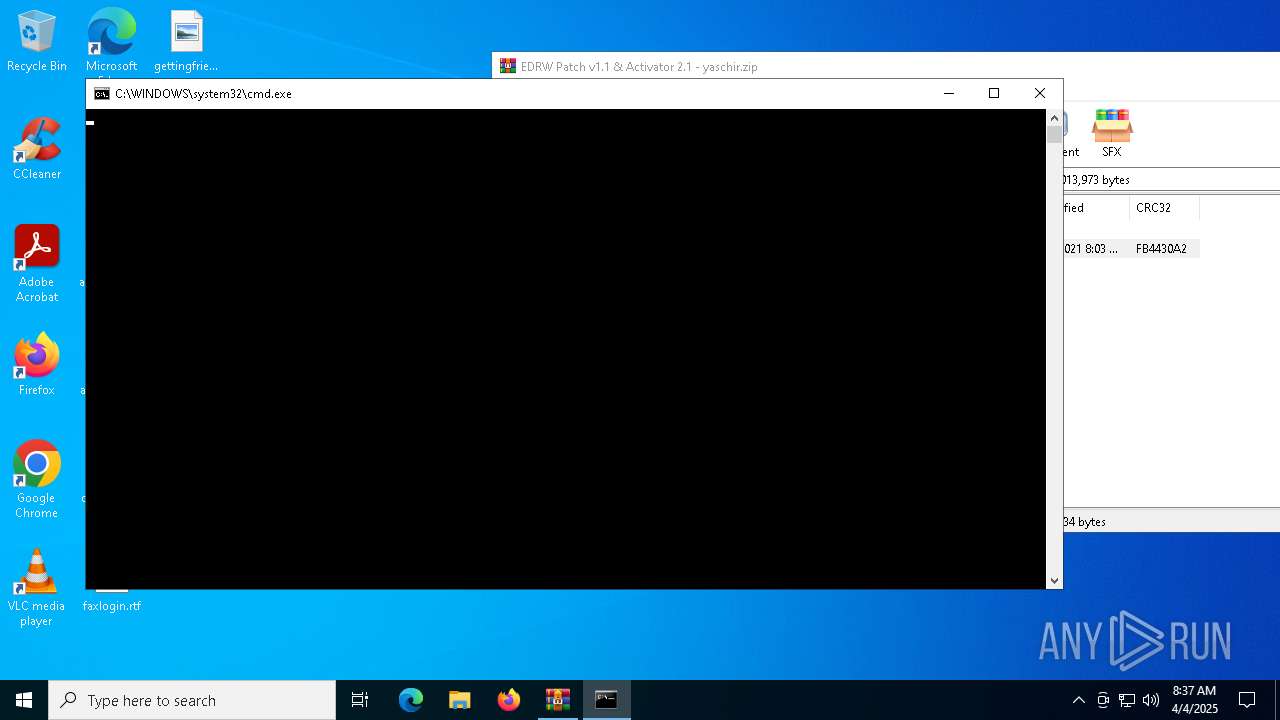
Executing commands from a ".bat" file
- cmd.exe (PID: 4608)
- WinRAR.exe (PID: 5668)
- wscript.exe (PID: 6640)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5668)
- cmd.exe (PID: 4608)
- wscript.exe (PID: 6640)
Application launched itself
- cmd.exe (PID: 4608)
The process executes VB scripts
- cmd.exe (PID: 4608)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6640)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1512)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1512)
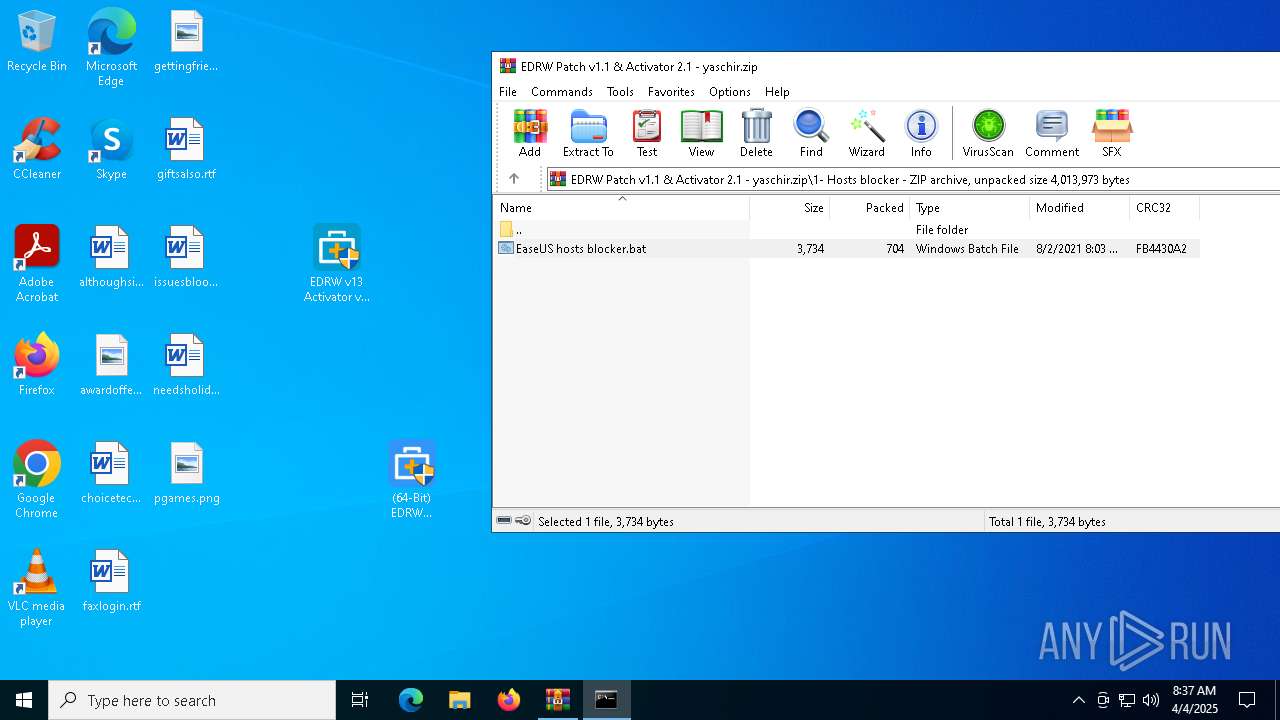
Modifies hosts file to alter network resolution
- cmd.exe (PID: 1512)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 1512)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5668)
Create files in a temporary directory
- (32-Bit) EDRW Patcher v1.1.exe (PID: 6744)
Checks supported languages
- (32-Bit) EDRW Patcher v1.1.exe (PID: 6744)
Reads the computer name
- (32-Bit) EDRW Patcher v1.1.exe (PID: 6744)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:08:16 00:00:12 |
| ZipCRC: | 0x5137c7e0 |
| ZipCompressedSize: | 1187 |
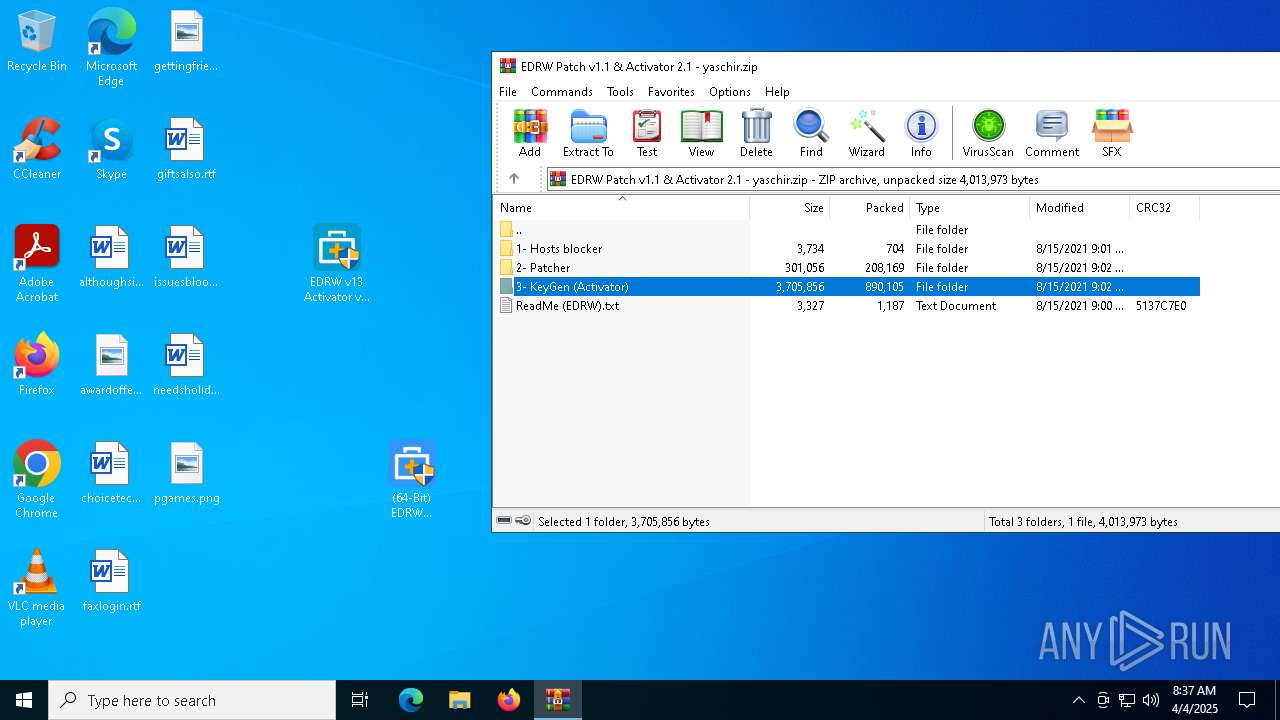
| ZipUncompressedSize: | 3327 |
| ZipFileName: | ReadMe (EDRW).txt |
Total processes
161
Monitored processes
33
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\2- Patcher\(32-Bit) EDRW Patcher v1.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\2- Patcher\(32-Bit) EDRW Patcher v1.1.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1088 | FIND /C /I "buy.easeus.com" C:\WINDOWS\system32\drivers\etc\hosts | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\Windows\System32\cmd.exe" /k cd "C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.17705\" && "C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.17705\EaseUS hosts blocker.bat" "" | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | FIND /C /I "api.easeus.com" C:\WINDOWS\system32\drivers\etc\hosts | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | FIND /C /I "www.easeus.com.cn" C:\WINDOWS\system32\drivers\etc\hosts | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | FIND /C /I "order.easeus.com" C:\WINDOWS\system32\drivers\etc\hosts | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | fltmc | C:\Windows\System32\fltMC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | cmd /u /c echo Set UAC = CreateObject("Shell.Application") : UAC.ShellExecute "cmd.exe", "/k cd ""C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.17705\"" && ""C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.17705\EaseUS hosts blocker.bat"" """"", "", "runas", 1 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 923
Read events
4 904
Write events
19
Delete events
0
Modification events
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EDRW Patch v1.1 & Activator 2.1 - yaschir.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4608) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE401000033000000A40500001C020000 | |||
Executable files
6
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5668.16111\2- Patcher\(64-Bit) EDRW Patcher v1.1.exe | executable | |
MD5:087406E501B283F538D66C98B7EA1991 | SHA256:04491956A8B8993E031D632304FF57667BC4C77885DA153E75454FF2E25DBC1D | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\2- Patcher\(32-Bit) EDRW Patcher v1.1.exe | executable | |
MD5:D0D44869D0B87FD8E960951687417CC9 | SHA256:8A66E54EB6A022EEB9063BF8182D3D1DEE11AA6990742E25CCD64CC5B7DBE3B0 | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\2- Patcher\(64-Bit) EDRW Patcher v1.1.exe | executable | |
MD5:087406E501B283F538D66C98B7EA1991 | SHA256:04491956A8B8993E031D632304FF57667BC4C77885DA153E75454FF2E25DBC1D | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\ReadMe (EDRW).txt | text | |
MD5:5590D164C5A5933C6D76CB7C51EC3C61 | SHA256:D95DD67969972258D255169D95F5EB948494C8E1C092E1FCFD69DDA1C5CE98FE | |||
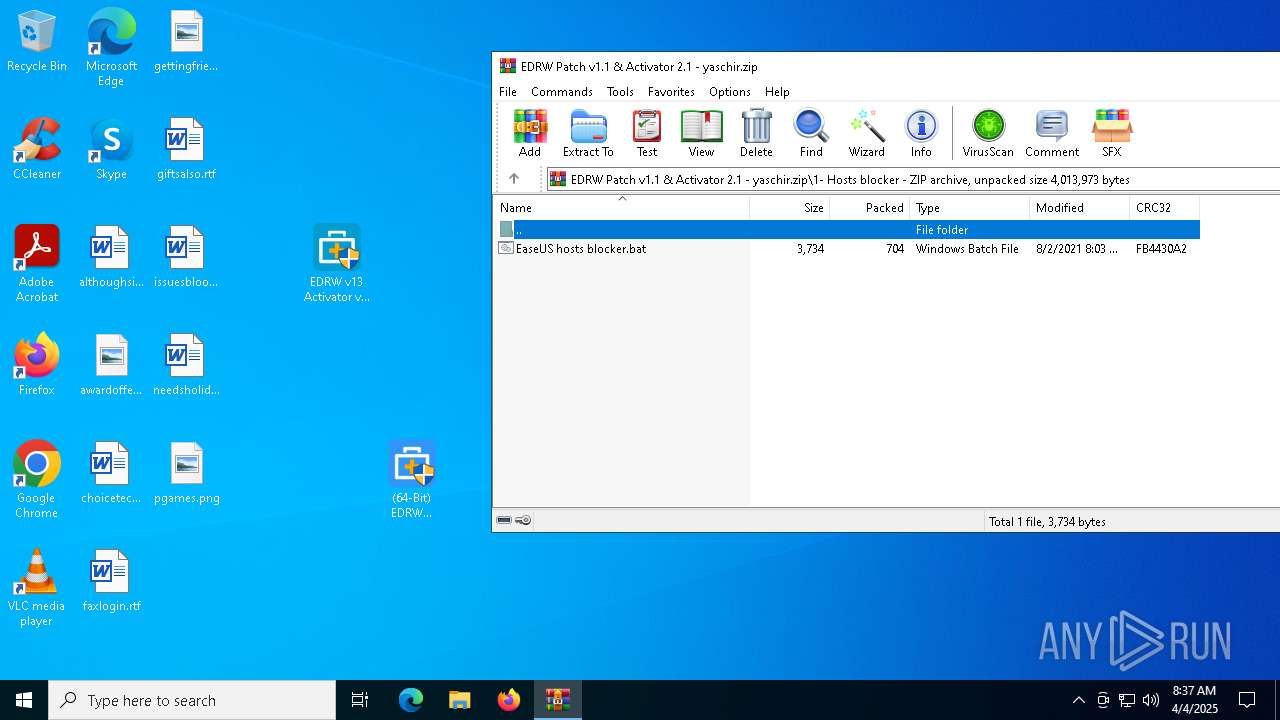
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\1- Hosts blocker\EaseUS hosts blocker.bat | text | |
MD5:A20BEF352C605997B09E2DA7BCA1F16E | SHA256:0124F42AC03A8F0CCACB35CF2E57D8CE96A323D66FBE4EBE06AD1DEF2E4D3B20 | |||
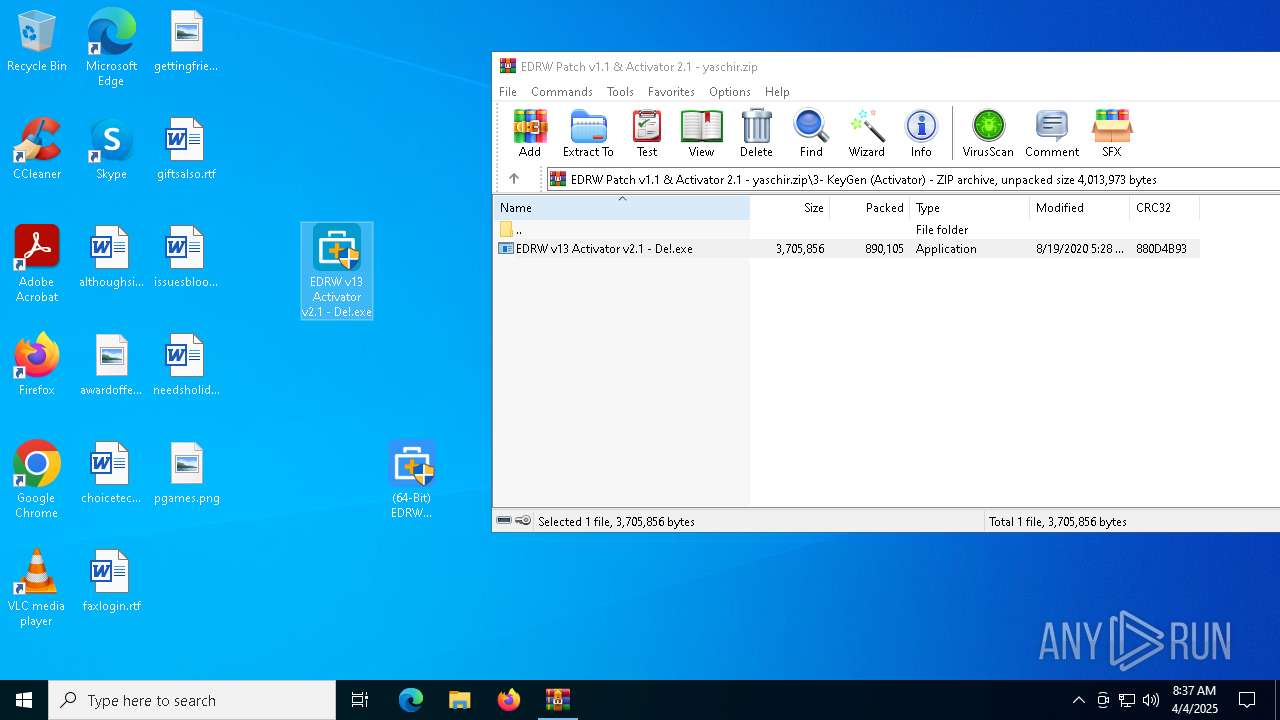
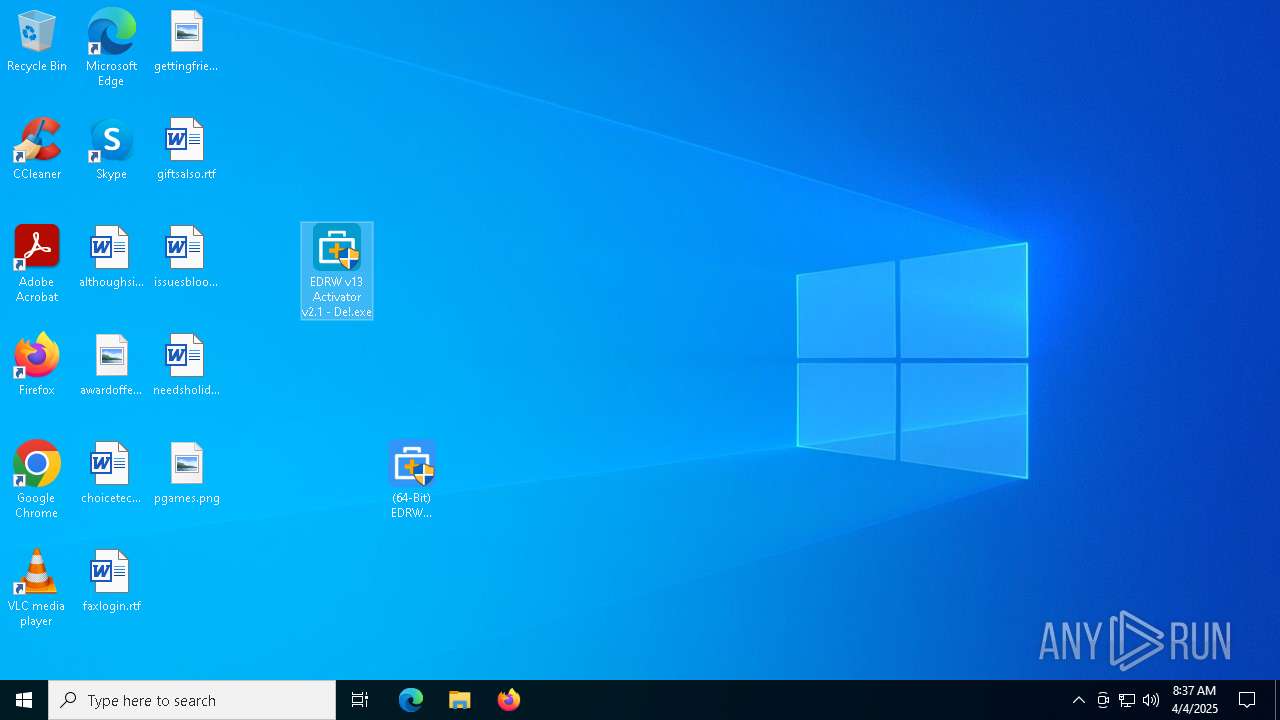
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5668.17248\3- KeyGen (Activator)\EDRW v13 Activator v2.1 - De!.exe | executable | |
MD5:284182F0388FE891ED6B6A1DA5B4196E | SHA256:10BADD3B49C88AC87CE720C47CCD79F0DB4F8125D63B52D328E554FB549C44A8 | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.17705\EaseUS hosts blocker.bat | text | |
MD5:A20BEF352C605997B09E2DA7BCA1F16E | SHA256:0124F42AC03A8F0CCACB35CF2E57D8CE96A323D66FBE4EBE06AD1DEF2E4D3B20 | |||
| 4608 | cmd.exe | C:\Users\admin\AppData\Local\Temp\GetAdmin.vbs | binary | |
MD5:693F2E8FB39643680DF883D41E535C5F | SHA256:E4EF22ABD7867272706F0BFDC59000DA06309B34CFF2F65429CB8DF3C2CC7759 | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5668.16658\3- KeyGen (Activator)\EDRW v13 Activator v2.1 - De!.exe | executable | |
MD5:284182F0388FE891ED6B6A1DA5B4196E | SHA256:10BADD3B49C88AC87CE720C47CCD79F0DB4F8125D63B52D328E554FB549C44A8 | |||
| 6744 | (32-Bit) EDRW Patcher v1.1.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:4D9AB4032AFF2644CE0D1E54D3DE1D7D | SHA256:F9585DE5B2442E841FABB7F4A61DFAFE28849FBECE57A372A9110137ECC4A6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
960 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
960 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.10.31.115:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
960 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |