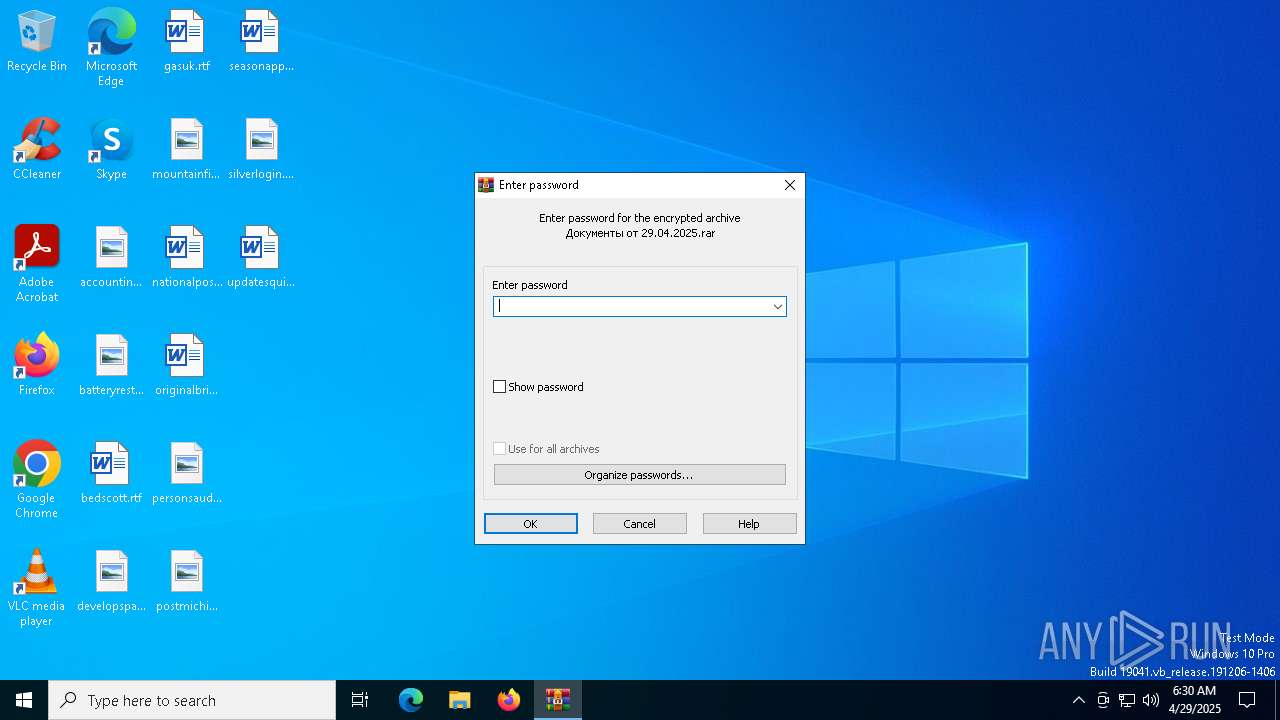
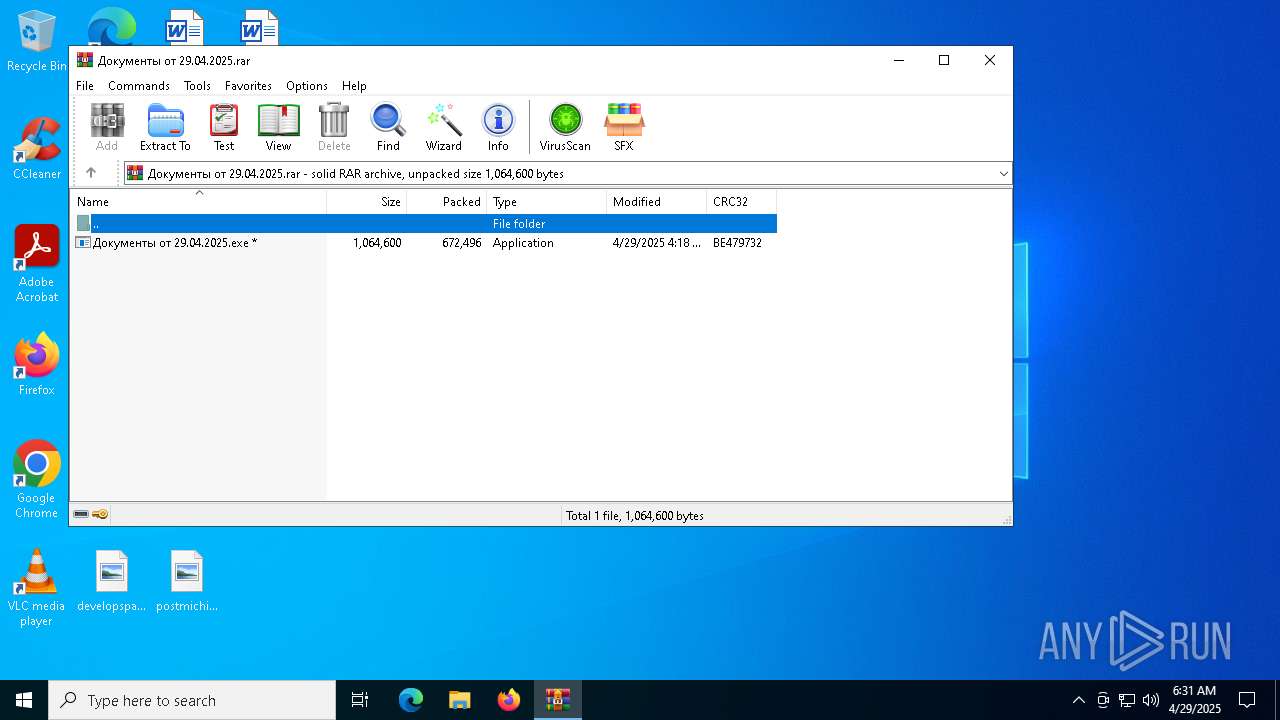
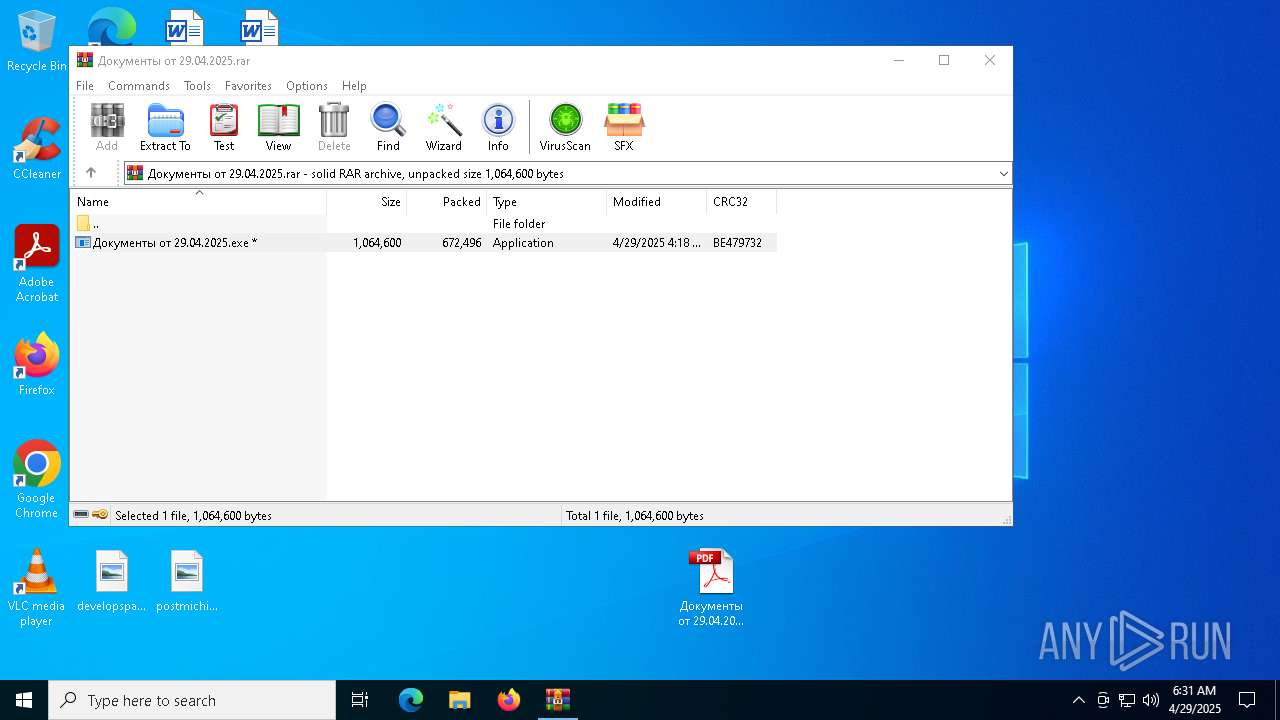
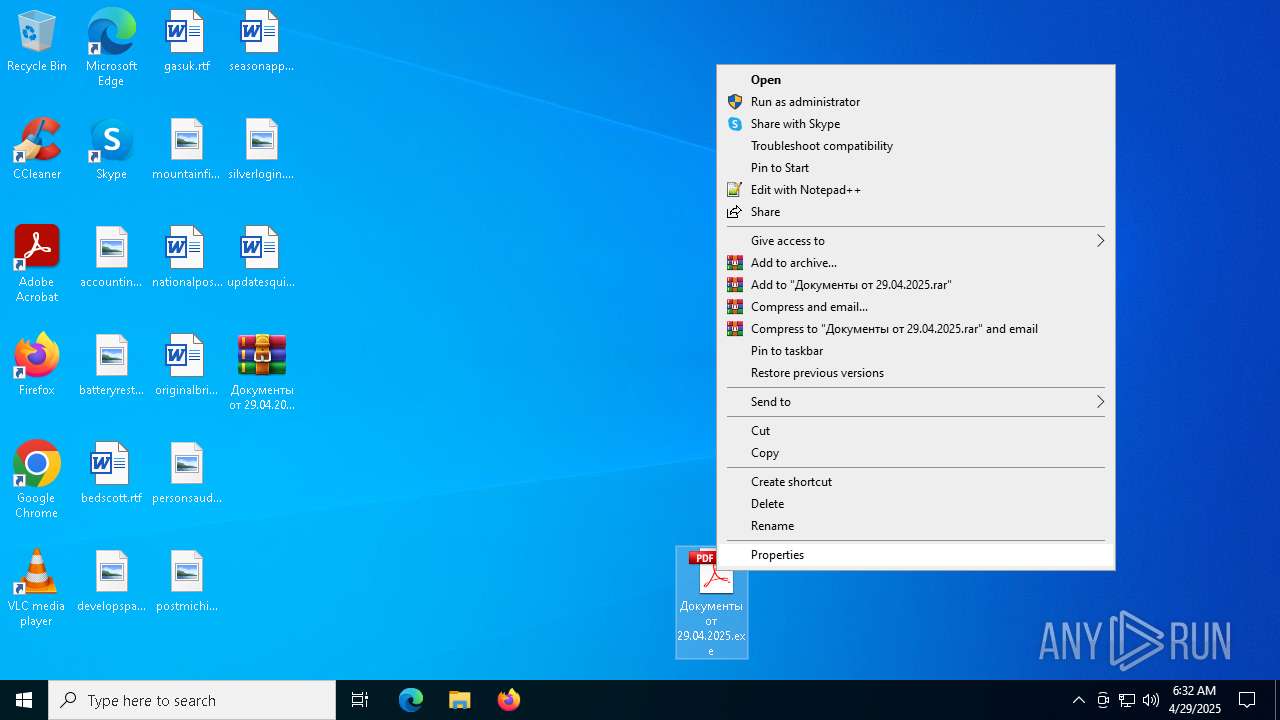
| File name: | Документы от 29.04.2025.rar |
| Full analysis: | https://app.any.run/tasks/2e60bff3-377a-43dd-8697-7d38d4c4c08e |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 06:30:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 91E85F333CE0A8547F438C98F158E685 |
| SHA1: | B8996B7AE9779C6D37D42250E39B7D04A0443C13 |
| SHA256: | 4B884EF88B610061F154FA7E98F49FE708F8A6646CA00A002E441AF4033E7F98 |
| SSDEEP: | 24576:ZrUq9Jxn9wj0vmIbGLkNEcBDbRu27v9UBE3oo3CuUcBM7sGB/cn8bxvNH:dUq9Jxn9wj0vpbGLk6cBDbRu27v9UBEu |
MALICIOUS
Executing a file with an untrusted certificate
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
SUSPICIOUS
Executes application which crashes
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7328)
Manual execution by a user
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
Reads the computer name
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
Checks supported languages
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
Reads the machine GUID from the registry
- Документы от 29.04.2025.exe (PID: 3884)
- Документы от 29.04.2025.exe (PID: 1272)
Creates files or folders in the user directory
- WerFault.exe (PID: 6032)
- WerFault.exe (PID: 5772)
Reads the software policy settings
- slui.exe (PID: 7488)
- slui.exe (PID: 1116)
Checks proxy server information
- slui.exe (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
142
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\Desktop\Документы от 29.04.2025.exe" | C:\Users\admin\Desktop\Документы от 29.04.2025.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3762504530 Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\Desktop\Документы от 29.04.2025.exe" | C:\Users\admin\Desktop\Документы от 29.04.2025.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3762504530 Modules
| |||||||||||||||
| 5772 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1272 -s 1276 | C:\Windows\SysWOW64\WerFault.exe | — | Документы от 29.04.2025.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3884 -s 1300 | C:\Windows\SysWOW64\WerFault.exe | — | Документы от 29.04.2025.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Документы от 29.04.2025.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7456 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7488 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 786
Read events
5 761
Write events
22
Delete events
3
Modification events
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Документы от 29.04.2025.rar | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
1
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_ADVVZV3XZWT4XRMQ_2bc37148df531a393affca896f7cdda810f14380_c3ac41ce_631d5c8e-e7a5-48fe-afa4-257a0e84b619\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6032 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Документы от 29.04.2025.exe.3884.dmp | — | |
MD5:— | SHA256:— | |||
| 5772 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_ADVVZV3XZWT4XRMQ_2bc37148df531a393affca896f7cdda810f14380_c3ac41ce_dee0eb4a-fa23-412e-a40b-ca6cdb041e09\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5772 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Документы от 29.04.2025.exe.1272.dmp | — | |
MD5:— | SHA256:— | |||
| 5772 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2284.tmp.dmp | binary | |
MD5:7AF425512EDBD0140C12CA6B3F2AA507 | SHA256:5DF3F43BADBDE8334AEB989DF42C5476EFC037E457C1AFCE7640B660C20424D3 | |||
| 6032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER923B.tmp.WERInternalMetadata.xml | binary | |
MD5:CBEE7E945B0179F9649EE7BB055A3683 | SHA256:3183320E6BC4D8AD0FDDF50FA99A18DB7E67223E0931DC4B032F17167B816FAB | |||
| 6032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9046.tmp.dmp | binary | |
MD5:6D378BDC0E80A27C93F9954FA016B47B | SHA256:A8BBBD2D5D75ABAE9EC20323598EBF5ABE37631AF75FA5331DC81862968AE921 | |||
| 6032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER92AA.tmp.xml | xml | |
MD5:1274D3F14CFE42677C8F43E7C6FD8356 | SHA256:EEA2C186658F89233878B59116824479CEAD71C34A7CCCBDB03D2E1F1FD0C1D9 | |||
| 5772 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2321.tmp.WERInternalMetadata.xml | binary | |
MD5:FB51798B3506006244D4D9C4C956F5C9 | SHA256:69381A1B2A28D087AF389E481D1B7FA60BCCF42282B31CBA6B169CEEF08644A7 | |||
| 5772 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2341.tmp.xml | xml | |
MD5:0019784AC75C917DF888CA83DFBC8C11 | SHA256:45CE92098B9FF28D2DFA9E48DFD840BED58FE179EBFC2723F879DAD70C8FE706 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8016 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |