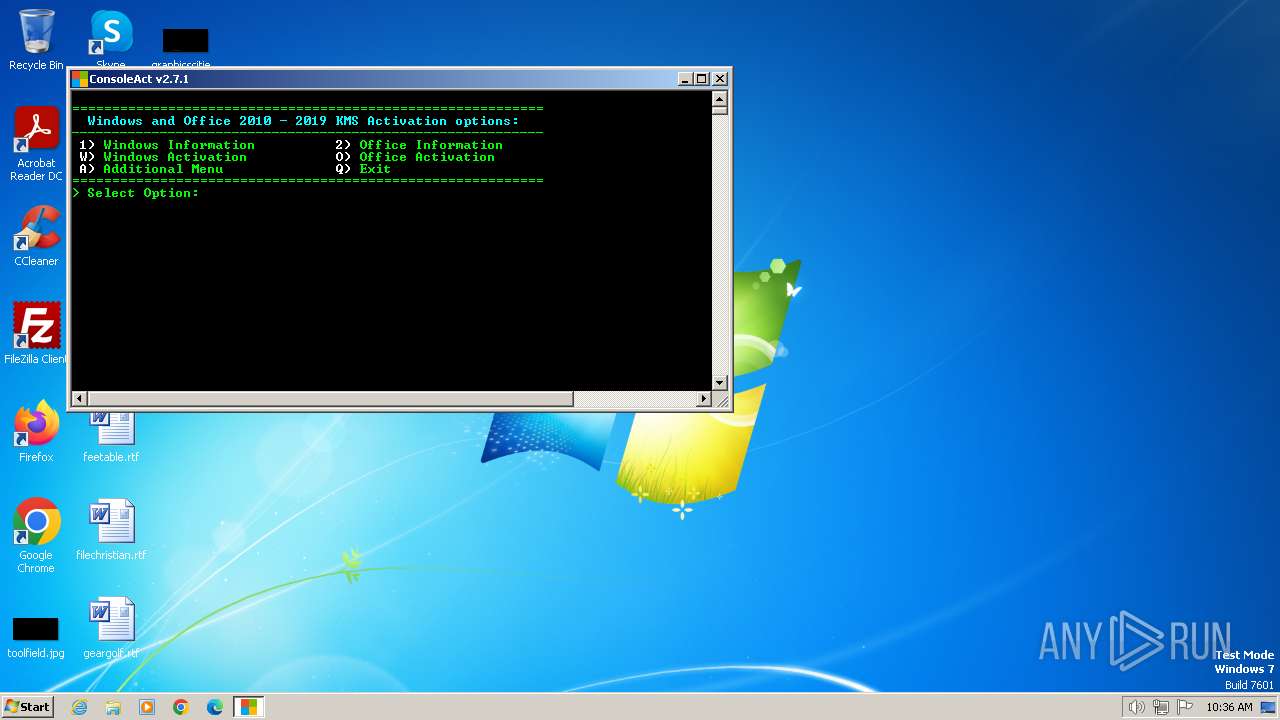
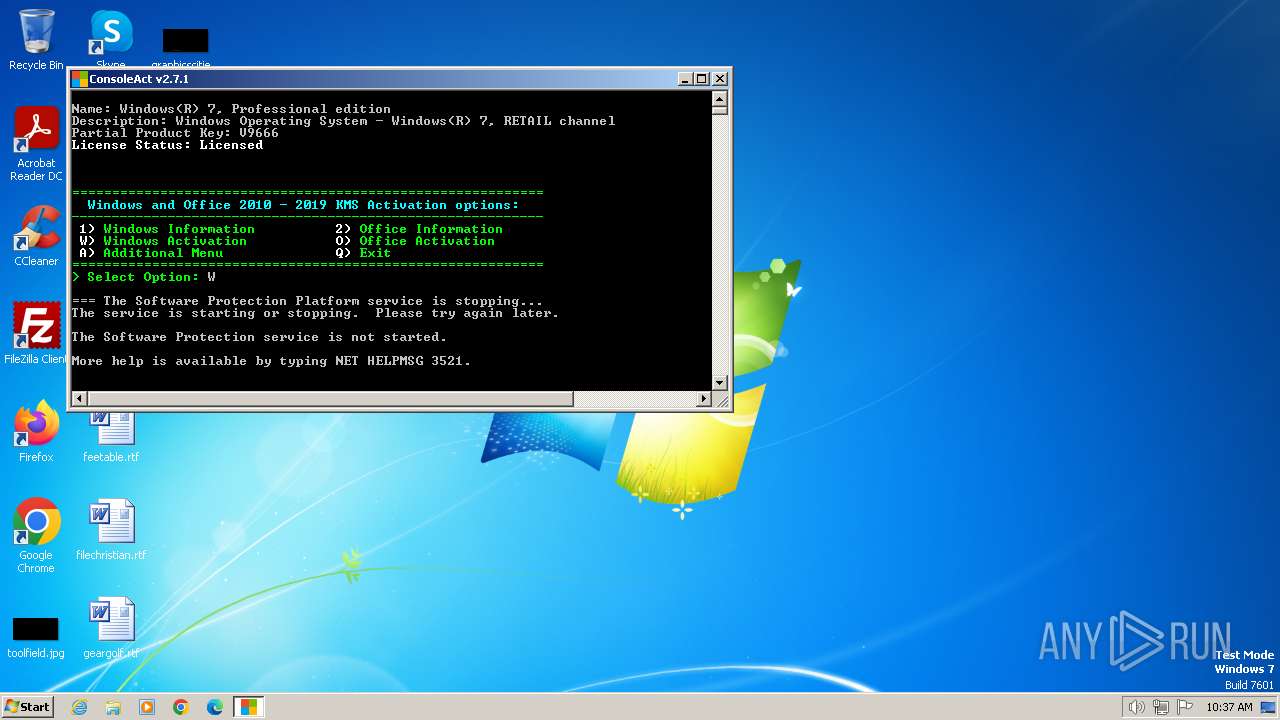
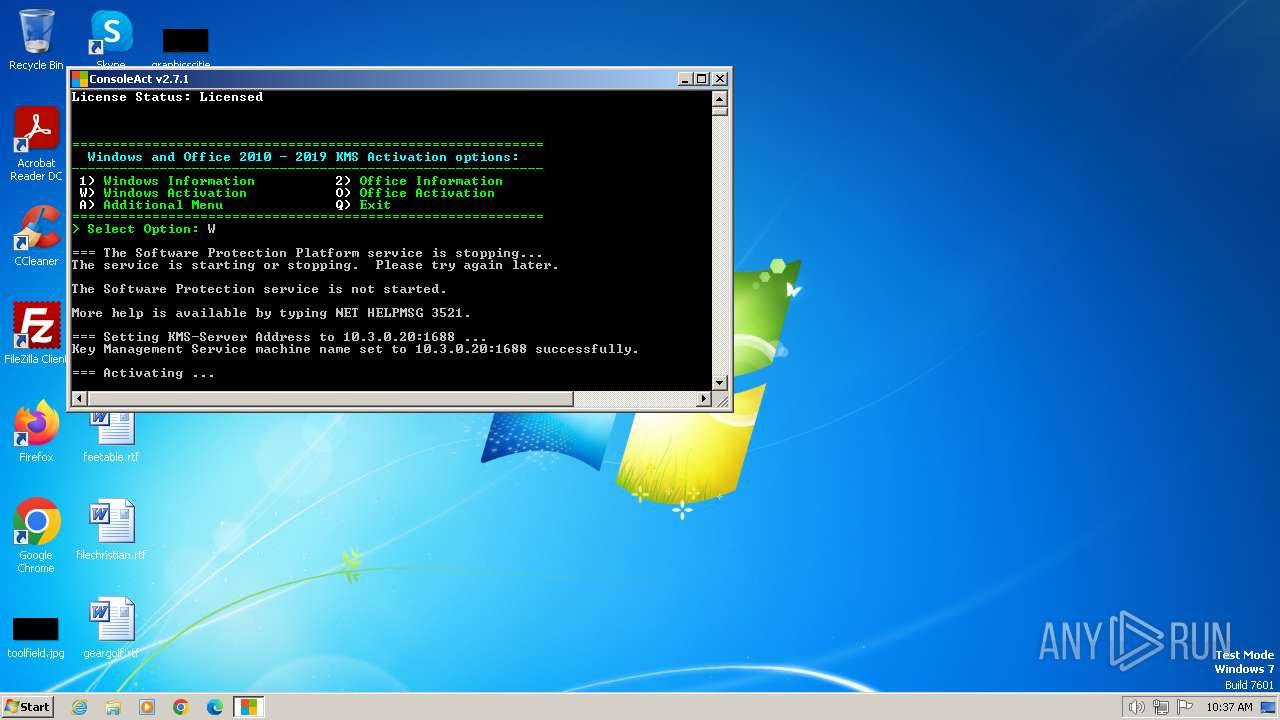
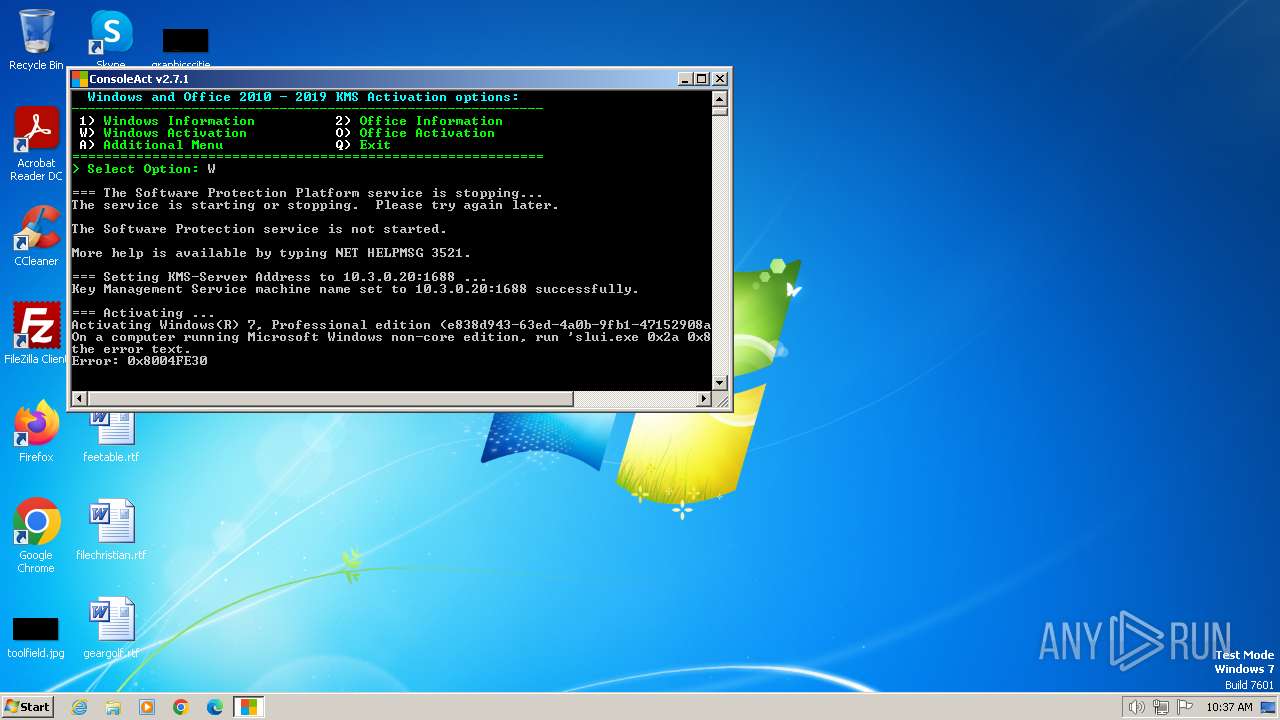
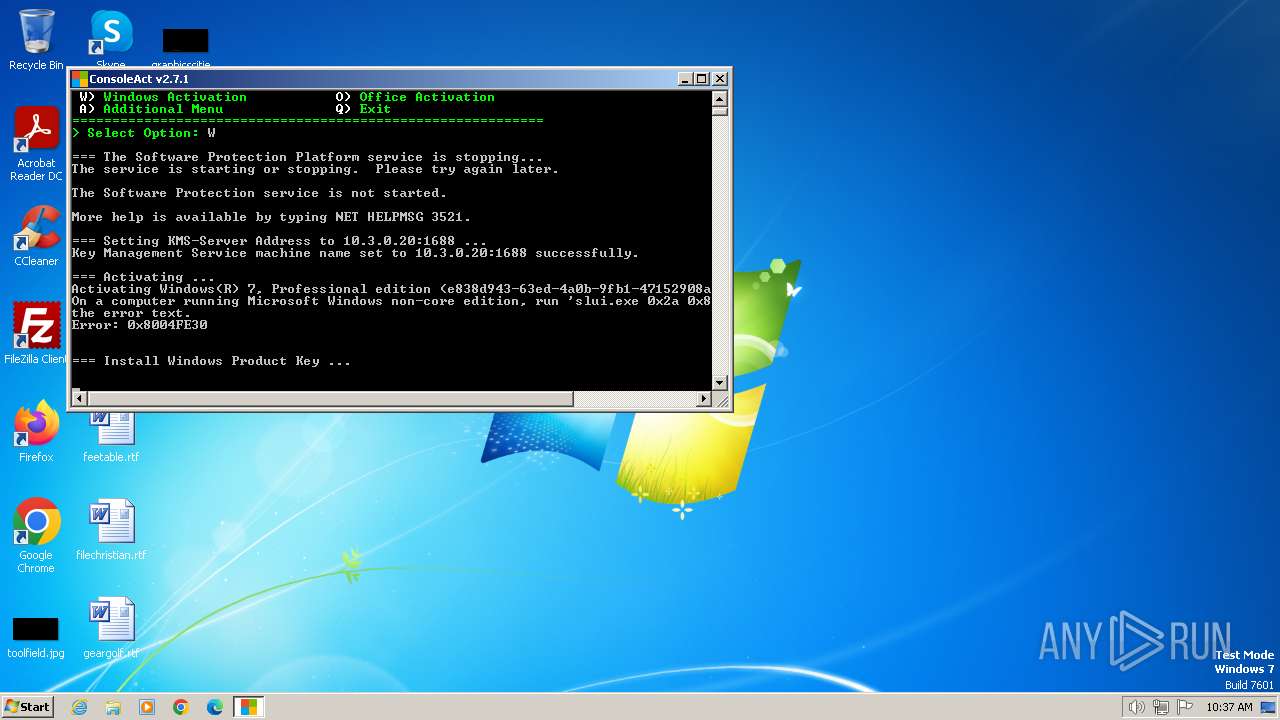
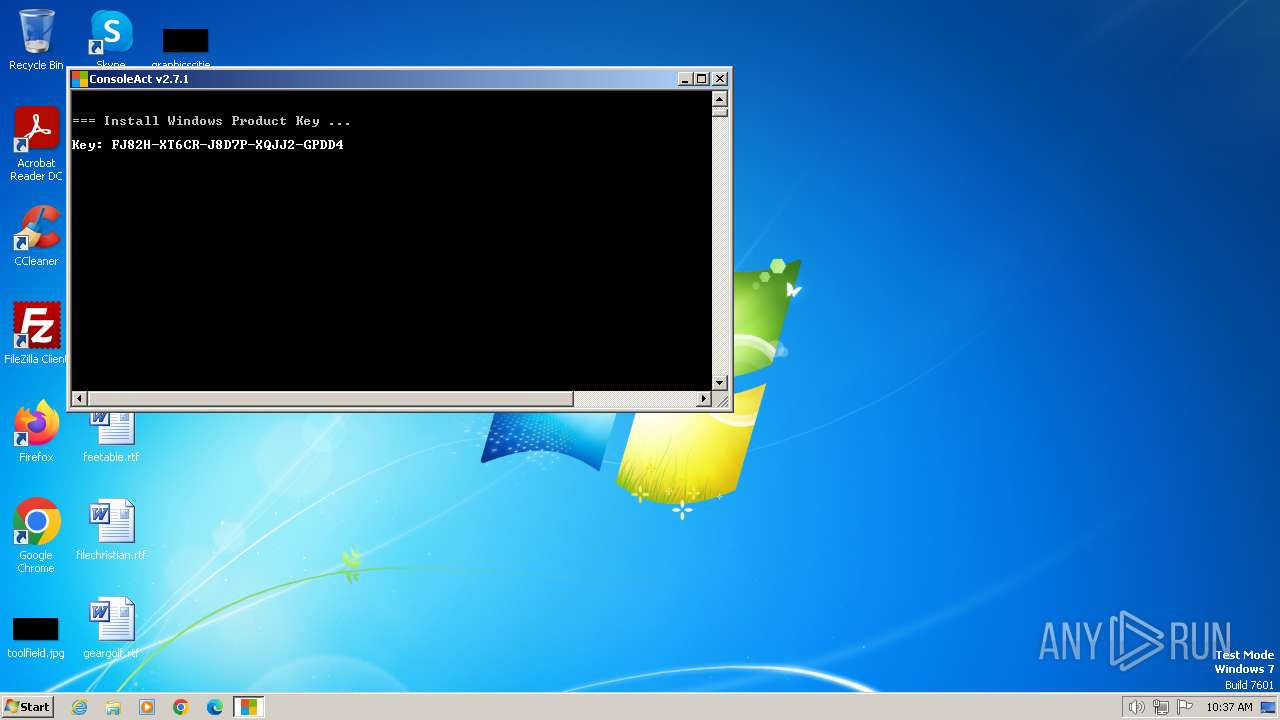
| File name: | ConsoleAct.exe |
| Full analysis: | https://app.any.run/tasks/897f63f1-d098-4a90-aa68-b2d270e7853a |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2024, 09:36:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 76E5BCF6DEE4810DC778FDFC58F6B9B4 |
| SHA1: | 582A238D3A3BF0C7A6DF7BAE46C33F50ACFF80BB |
| SHA256: | 4B72DA0D5FC4A86F2ADD2D3EA558161A8009ECA49C178A82615AE7C3BD1E21EC |
| SSDEEP: | 98304:L0CXKUx8Mnyr7aJoj/0Fdfoj/167D7gcDMCU:za |
MALICIOUS
Drops the executable file immediately after the start
- ConsoleAct.exe (PID: 2416)
Starts NET.EXE for service management
- cmd.exe (PID: 1556)
- cmd.exe (PID: 2744)
- net.exe (PID: 2780)
- net.exe (PID: 2336)
- cmd.exe (PID: 2536)
- net.exe (PID: 3868)
- cmd.exe (PID: 2376)
- net.exe (PID: 2292)
- net.exe (PID: 2032)
- cmd.exe (PID: 2960)
- net.exe (PID: 1496)
- cmd.exe (PID: 3516)
Creates a writable file in the system directory
- ConsoleAct.exe (PID: 2416)
Opens a text file (SCRIPT)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 560)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 1028)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 840)
- cmd.exe (PID: 1696)
- cmd.exe (PID: 1740)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 1496)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 3496)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 924)
- cmd.exe (PID: 2036)
- cmd.exe (PID: 2912)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 2880)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 560)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Hides command output
- cmd.exe (PID: 2528)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2152)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 560)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Starts SC.EXE for service management
- cmd.exe (PID: 2528)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3072)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 2856)
- cmd.exe (PID: 1340)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 3544)
- cmd.exe (PID: 1576)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 604)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 3348)
- ConsoleAct.exe (PID: 2416)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 1428)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 1808)
- cmd.exe (PID: 2016)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 3540)
- cmd.exe (PID: 3036)
- cmd.exe (PID: 2528)
- cmd.exe (PID: 568)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 3700)
- cmd.exe (PID: 2328)
- cmd.exe (PID: 3956)
- cmd.exe (PID: 1832)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3256)
- cmd.exe (PID: 3860)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 3204)
- cmd.exe (PID: 1044)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 1124)
- cmd.exe (PID: 1628)
- cmd.exe (PID: 268)
- cmd.exe (PID: 3612)
- cmd.exe (PID: 3408)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 1192)
Executable content was dropped or overwritten
- ConsoleAct.exe (PID: 2416)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3712)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 2540)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 560)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 560)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 560)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3084)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 560)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Starts CMD.EXE for commands execution
- ConsoleAct.exe (PID: 2416)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 1740)
- cmd.exe (PID: 3056)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 952)
- cmd.exe (PID: 2612)
Accesses system date via WMI (SCRIPT)
- cscript.exe (PID: 560)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2652)
INFO
Checks supported languages
- ConsoleAct.exe (PID: 2416)
Reads product name
- ConsoleAct.exe (PID: 2416)
Reads Environment values
- ConsoleAct.exe (PID: 2416)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3084)
- cscript.exe (PID: 3644)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 116)
- cscript.exe (PID: 848)
- cscript.exe (PID: 1976)
- cscript.exe (PID: 3128)
- cscript.exe (PID: 1220)
- cscript.exe (PID: 560)
- cscript.exe (PID: 1852)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3932)
- cscript.exe (PID: 3732)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 2864)
- cscript.exe (PID: 844)
- cscript.exe (PID: 2296)
Reads Microsoft Office registry keys
- reg.exe (PID: 2844)
- reg.exe (PID: 3240)
- reg.exe (PID: 240)
- reg.exe (PID: 2544)
- reg.exe (PID: 2820)
- reg.exe (PID: 2764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:04:27 00:34:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 737792 |
| InitializedDataSize: | 1253376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.7.1.0 |
| ProductVersionNumber: | 2.7.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| OriginalFileName: | ConsoleAct.exe |
| LegalCopyright: | MSFree Inc., Ratiborus |
Total processes
248
Monitored processes
200
Malicious processes
35
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /ckms-domain | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 240 | reg.exe add "HKLM\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform" /f /v "KeyManagementServiceName" /t REG_SZ /d 10.3.0.20 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | "C:\Windows\System32\cmd.exe" /c reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "KMS_RenewalInterval" /t REG_DWORD /d 10080 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 548 | schtasks.exe /delete /f /tn "\Microsoft\Windows\SoftwareProtectionPlatform\SvcTrigger" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /dlv All | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 560 | reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "GlobalFlag" /t REG_DWORD /d 256 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Windows\System32\cmd.exe" /c reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe" /f /v "KMS_Emulation" /t REG_DWORD /d 1 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 604 | "C:\Windows\System32\cmd.exe" /c reg.exe add "HKLM\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform" /f /v "KeyManagementServicePort" /t REG_SZ /d 1688 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 764 | reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v "KMS_Emulation" /t REG_DWORD /d 1 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 840 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /sdns 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 725
Read events
11 418
Write events
295
Delete events
12
Modification events
| (PID) Process: | (2416) ConsoleAct.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (4024) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (2432) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (980) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
| (PID) Process: | (3324) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_RenewalInterval |
Value: 10080 | |||
| (PID) Process: | (2000) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
| (PID) Process: | (2044) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (4028) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (3224) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
| (PID) Process: | (2204) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osppsvc.exe |
| Operation: | write | Name: | KMS_RenewalInterval |
Value: 10080 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | ConsoleAct.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:E30B53AEDCB0C17DB66D5B3B3EB9A4BA | SHA256:66FAE80DC13273D3C8FEC2ACB8C0FB1F658D53E34D28CDA4986048B8D1DEA8F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3604 | WmiPrvSE.exe | POST | 404 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=88339 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3604 | WmiPrvSE.exe | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |