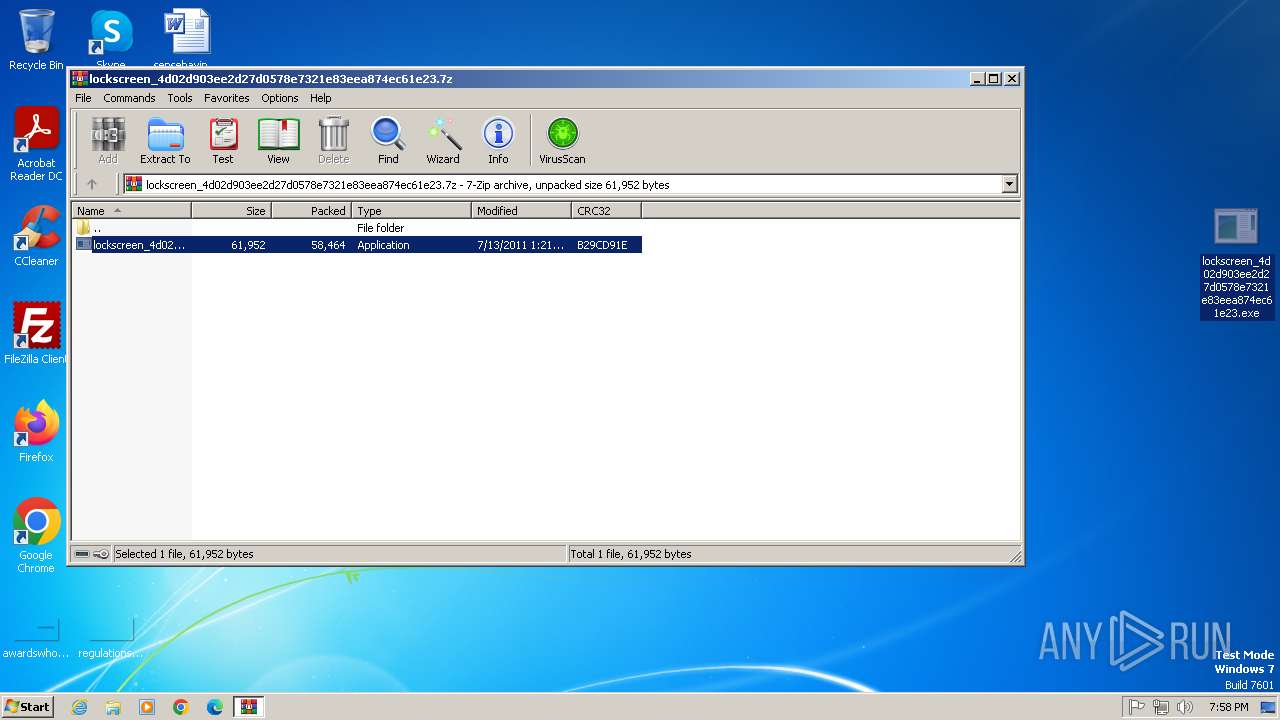
| File name: | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.7z |
| Full analysis: | https://app.any.run/tasks/379c1b5b-9e5f-4bad-a074-1a8feb24bbad |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 18:57:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 80803BDB3EAFE0BF6D2378944D82B166 |
| SHA1: | D8507933F2F075F52B333646289C8BAFCE58E18E |
| SHA256: | 4B643D6C6B3518E25E079B5B8F324ED6F8B7C491845EFDE347FD10F42C4A2E5C |
| SSDEEP: | 1536:Alr2nRrXQnxuFx/y52utWrs63nvYdA7NNg+k6xzYEWZ:AliRraIFxahcPncK1xzJWZ |
MALICIOUS
Changes the autorun value in the registry
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
SUSPICIOUS
Reads security settings of Internet Explorer
- firefox.exe (PID: 1504)
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
There is functionality for taking screenshot (YARA)
- firefox.exe (PID: 1504)
Reads the Internet Settings
- firefox.exe (PID: 1504)
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Starts itself from another location
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Starts CMD.EXE for commands execution
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Executing commands from a ".bat" file
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Executable content was dropped or overwritten
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
INFO
Manual execution by a user
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Reads the computer name
- firefox.exe (PID: 1504)
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
Reads the machine GUID from the registry
- firefox.exe (PID: 1504)
Checks supported languages
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
- firefox.exe (PID: 1504)
Creates files or folders in the user directory
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
The sample compiled with english language support
- lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe (PID: 2516)
- WinRAR.exe (PID: 2472)
Checks proxy server information
- firefox.exe (PID: 1504)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2011:07:13 00:21:48+00:00 |
| ArchivedFileName: | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe |
Total processes
43
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1504 | "C:\Users\admin\AppData\Local\Mozilla\Firefox\firefox.exe" | C:\Users\admin\AppData\Local\Mozilla\Firefox\firefox.exe | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2100 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\unlnk.bat" " | C:\Windows\System32\cmd.exe | — | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\Desktop\lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe" | C:\Users\admin\Desktop\lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 053
Read events
3 995
Write events
52
Delete events
6
Modification events
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.7z | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | C:\Users\admin\Desktop\unlnk.bat | text | |
MD5:B28CFA17CDE1FDCFBFE7C3AAFE177C85 | SHA256:44BA5A2D2D781106FAB4EE16F82C68647CEF1C18AA8B43CE55B45D451187FEA4 | |||
| 2472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2472.29783\lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | executable | |
MD5:8319AA38ACA634550EECFE04B3594ABF | SHA256:9A83A1C668FC060E019D2D74C47B799774F51639C8E843B62CD3E2AA6DE2A0F0 | |||
| 2516 | lockscreen_4d02d903ee2d27d0578e7321e83eea874ec61e23.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\firefox.exe | executable | |
MD5:8319AA38ACA634550EECFE04B3594ABF | SHA256:9A83A1C668FC060E019D2D74C47B799774F51639C8E843B62CD3E2AA6DE2A0F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
12
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://jaculatebliley.info/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://panizagyrose.com/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://gimmiraestrang.info/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://dismayedcorallo.info/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://yarukulakonica.info/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://smuggestbusting.info/ | unknown | — | — | unknown |
1504 | firefox.exe | POST | 404 | 49.13.77.253:80 | http://daiglernylghaus.info/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1504 | firefox.exe | 49.13.77.253:80 | panizagyrose.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
panizagyrose.com |
| unknown |
daiglernylghaus.info |
| unknown |
gimmiraestrang.info |
| unknown |
jaculatebliley.info |
| unknown |
yarukulakonica.info |
| unknown |
dismayedcorallo.info |
| unknown |
smuggestbusting.info |
| unknown |