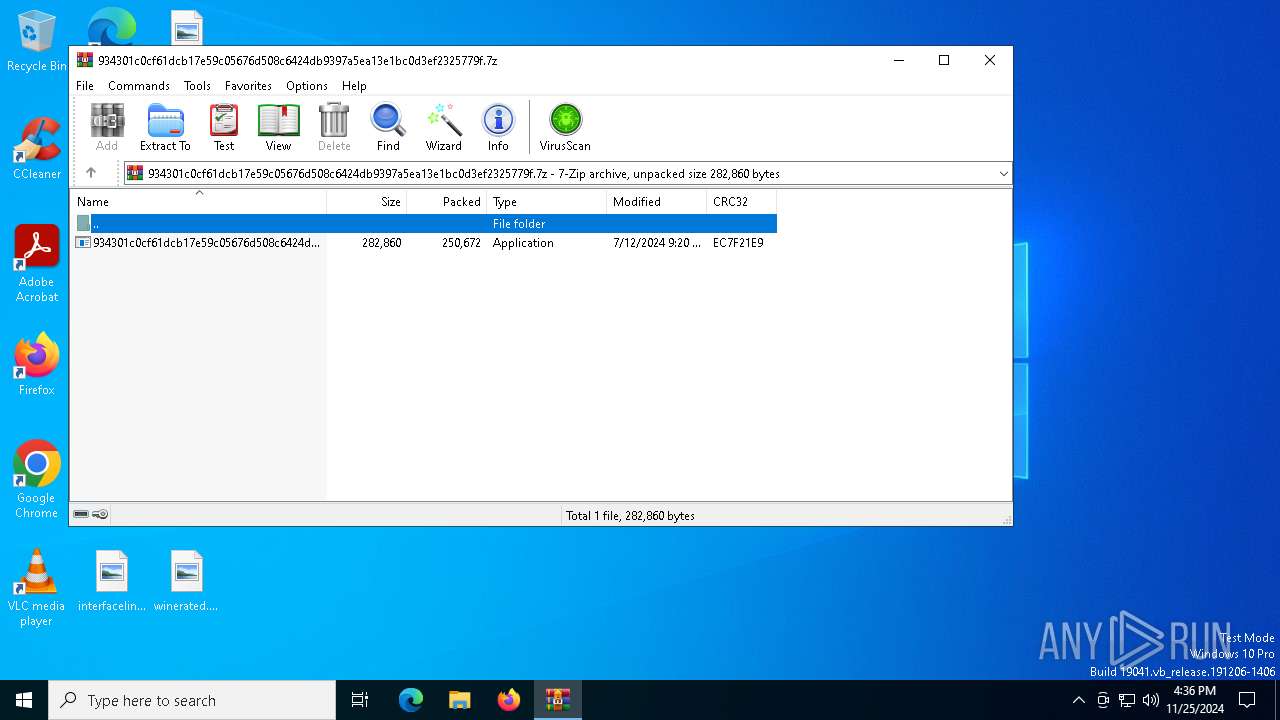
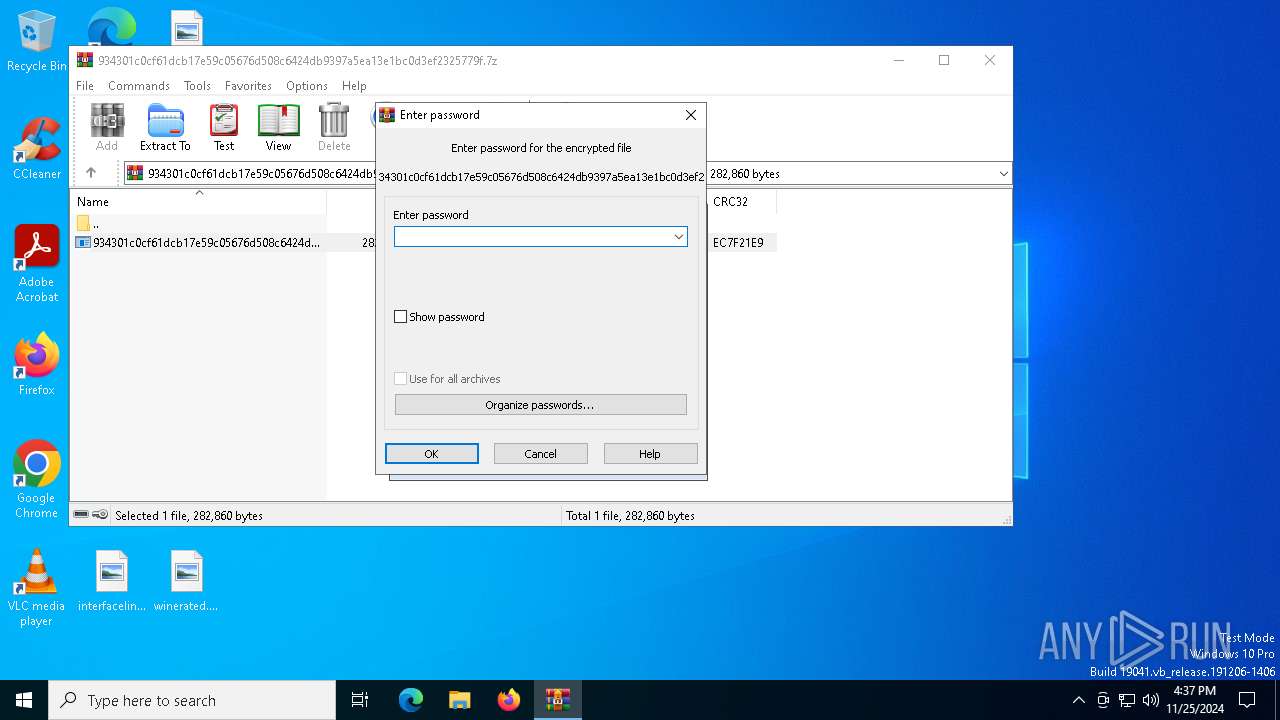
| File name: | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.7z |
| Full analysis: | https://app.any.run/tasks/e4d3771f-28da-43b2-ac5e-4193cb4101c3 |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2024, 16:36:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 12FEEC7118A2631E385DB02141062E16 |
| SHA1: | 4EC266F0A6866CC309DF827D20CA9F03377D7386 |
| SHA256: | 4B612CD92DFCD128CBCC41F4C0D7F10A033CD4053AEF06C0D64F7E17348AE844 |
| SSDEEP: | 6144:5fS2XtCWAE0Bl2rs3/cHcDodVnnZF3HZjZHgRsoxKlBiIqfs5Fb:5S2XtCWI2sUHc2nZZZjI/YlBhHb |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6240)
Starts CMD.EXE for self-deleting
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 4400)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 5752)
- eventcreate.exe (PID: 1512)
- eventcreate.exe (PID: 4876)
- eventcreate.exe (PID: 4008)
Application launched itself
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 5752)
- eventcreate.exe (PID: 1512)
- eventcreate.exe (PID: 4008)
- eventcreate.exe (PID: 4876)
Executable content was dropped or overwritten
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 5752)
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 4400)
- eventcreate.exe (PID: 4876)
- eventcreate.exe (PID: 1512)
- eventcreate.exe (PID: 4008)
Starts itself from another location
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 4400)
Hides command output
- cmd.exe (PID: 6436)
Starts CMD.EXE for commands execution
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 4400)
The process executes via Task Scheduler
- eventcreate.exe (PID: 4008)
- eventcreate.exe (PID: 1512)
Checks for external IP
- svchost.exe (PID: 2192)
- eventcreate.exe (PID: 1596)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6436)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6436)
INFO
Manual execution by a user
- 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe (PID: 5752)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:07:12 21:20:12+00:00 |
| ArchivedFileName: | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe |
Total processes
140
Monitored processes
14
Malicious processes
2
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe" | C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe" | C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe | eventcreate.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe" | C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 4400 | "C:\Users\admin\Desktop\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe" | C:\Users\admin\Desktop\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4516 | "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe" | C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe | — | eventcreate.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 4876 | "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe" | C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\eventcreate.exe | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5404 | taskkill /t /f /im "934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe" | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5752 | "C:\Users\admin\Desktop\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe" | C:\Users\admin\Desktop\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 112
Read events
3 080
Write events
32
Delete events
0
Modification events
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.7z | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
7
Suspicious files
21
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6240.44285\934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | executable | |
MD5:32559ED7885B5BD32DEDB03CC244D55B | SHA256:934301C0CF61DCB17E59C05676D508C6424DB9397A5EA13E1BC0D3EF2325779F | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\BitFrequency.mm | text | |
MD5:C593BC1CA9F04F16EA5EEF58BAEBAC50 | SHA256:78748624D055829446B9A963BF3B19B3DB2428EAC192ACFA2027C1C80FB3F774 | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\Bibliomania.fh5 | binary | |
MD5:87A1BE58CBDD87C3FBE6AEF78C458EF4 | SHA256:97C282799F83F5D4D1825F4E87BC07861100D0D8AA330F1B9D99D7C168462168 | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\CommonMessages_fr.xml | xml | |
MD5:B734C3F8BD71D9A7BDC6B95BEF93CE90 | SHA256:89DEF78B70F8D8B07F1FC794CAF8F6BCF92FFC58893EE1DAF099A574B50D346D | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\EngineLoggerConfig.xml | text | |
MD5:3C776D54E30C91AB5003DB046C369C05 | SHA256:B346158E5F2F3F9AE59F06D6129034F71740DC2482187A73BFE857FE8A093002 | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\default.table.frame.xml | html | |
MD5:11131B301360CB35DD6F0F6B9B837239 | SHA256:A92EA20DCE28D0175239282B5D2C440A778C98956D08BCE52CB3E4FC15CAB16B | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\but-next.png | image | |
MD5:505F381EBC020405DE2F29DFB0FC2218 | SHA256:78D2571AAD9E004F9FB31672C8195492722BCD42D88EC8ADD5D81A4F8AED8DEA | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\dsfroot.inf | binary | |
MD5:A9525C72B61CA351D7ADC155866F3331 | SHA256:44F7115E9C4A02F1A1D712BA719094C5E68F7850BD9247DC14D381AC53AD1C19 | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Local\Temp\nsh1A01.tmp\System.dll | executable | |
MD5:CA332BB753B0775D5E806E236DDCEC55 | SHA256:DF5AE79FA558DC7AF244EC6E53939563B966E7DBD8867E114E928678DBD56E5D | |||
| 5752 | 934301c0cf61dcb17e59c05676d508c6424db9397a5ea13e1bc0d3ef2325779f.exe | C:\Users\admin\AppData\Roaming\EUC-V | ps | |
MD5:2AE28D03E6F74FC3C034E3610CAA5280 | SHA256:DF632351D3735A6305DC56D28BFC361F5C028F6B366EBB887480DF32421201DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
2 081
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6152 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1596 | eventcreate.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | shared |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6916 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6916 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.177:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4652 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
1596 | eventcreate.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |