| File name: | c.exe |
| Full analysis: | https://app.any.run/tasks/94bce07d-0296-47f6-817c-4a59730e524c |
| Verdict: | Malicious activity |
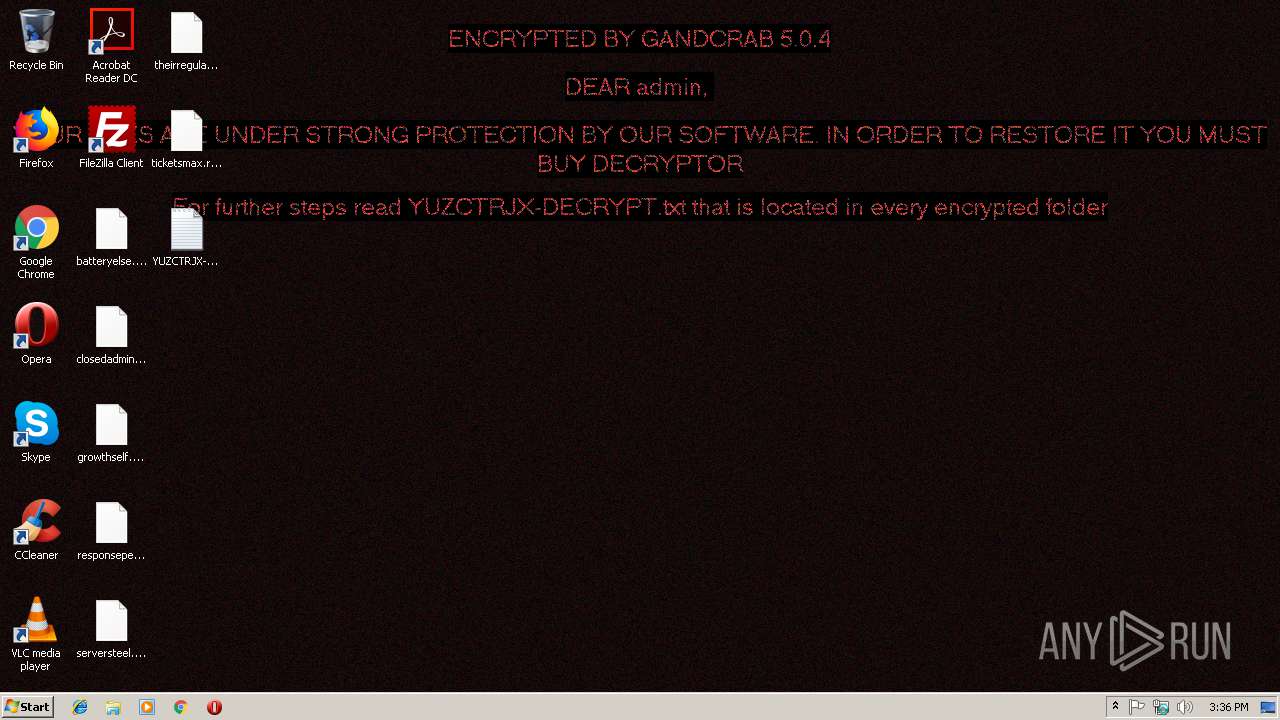
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 22, 2019, 15:35:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 24275604649AC0ABAFE99B981B914FBC |
| SHA1: | 818B0E3018AD27BE9887E9E5F4EF1971F422652C |
| SHA256: | 4B5FE7497864D07F78AF15FA3E1AA3702B303B89F9644624871D83DD0F484749 |
| SSDEEP: | 1536:JLMVCWvZ8URtqOz3d+1Qs6H9Mk2e3E2avMWC3yMgYxf6+okbdWsWjcdpKCaIxWzX:VM9ntZ3s1QJdnU2SQdf64ZZ8CaIxWec |
MALICIOUS
GandCrab keys found
- c.exe (PID: 3092)
Actions looks like stealing of personal data
- c.exe (PID: 3092)
Writes file to Word startup folder
- c.exe (PID: 3092)
Renames files like Ransomware
- c.exe (PID: 3092)
Deletes shadow copies
- c.exe (PID: 3092)
Dropped file may contain instructions of ransomware
- c.exe (PID: 3092)
Connects to CnC server
- c.exe (PID: 3092)
SUSPICIOUS
Reads the cookies of Mozilla Firefox
- c.exe (PID: 3092)
Creates files like Ransomware instruction
- c.exe (PID: 3092)
Creates files in the user directory
- c.exe (PID: 3092)
INFO
Dropped object may contain TOR URL's
- c.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:10:26 10:47:08+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 80896 |
| InitializedDataSize: | 68096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6229 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Oct-2018 08:47:08 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 26-Oct-2018 08:47:08 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00013BE4 | 0x00013C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58693 |
.rdata | 0x00015000 | 0x00006B46 | 0x00006C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.59755 |
.data | 0x0001C000 | 0x000087F4 | 0x00006A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.15553 |
.rsrc | 0x00025000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.7123 |
.reloc | 0x00026000 | 0x000013A8 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.64868 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
GDI32.dll |
KERNEL32.dll |
MPR.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
WININET.dll |
ole32.dll |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2756 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | c.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3092 | "C:\Users\admin\AppData\Local\Temp\c.exe" | C:\Users\admin\AppData\Local\Temp\c.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
121
Read events
90
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3092) c.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E00790075007A006300740072006A0078000000 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001002BBA94FB568B1BF893E5AC5FD5F15973D87F8C6345F855B1CBC21E98C6EEB1B57E871B154282EB43DE9CEE5B5FDF4FD7723410997DB4C50A7110366F3B10F1A635D45F3968F74D9A990877A560756698E5EC8A59391ABDB583C6BC26FA36810B3448C3599B369F85526F6DD4D3D18D6F95DF03636FA47BB12BF142CFFC13A97BA5106FDCFAA64FFDC6AF85AC8887BCA0F99A586735798851A810C83CBD93A177D0BCE469A3B07448CBC747769412B8B5EC5B890AD14104DB8F24E990549E277ED21CCDD4B7AFEE6C5494344C22F95F4DFA65C0D66D947BA05A54452477BF01B7D30B6EADC66DE823749BE5E57C70B4A42641AD0E14A71A78F50184D5E3B5B7A4 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 940400008EE96FE892EDE921F825A3EE096E740F32D9CECFFC0B7D4DC99F73850F393562E4021FD71B7515B07BA7FEA386EF28C208CA3C2BE68B4581377F5C0C6A071F146B2C85F04F61FAE5FB65BDE0747CB4FBCC6739A26B545998B283D778733394677BF830A2906120562DDBA4D193AC411FC94CD7B576B0655E85D9B90B2B89CC75E27CCC8711A636B229C26F163956F88888A078AC0D5F0136E7E4A54C7CABB3BE4EDE3E8DA130CC597F2777E102BEE8F4CBD44CB468CB5AF15426FD20D38C3746BE1E22D672BB5D0D53396797400F26D8D81BAB2AAA86B141B2A2F2D823F48F78C46756BF77AE8A99453E6866673D813E27D3326C2C837D87D162461A703FB601981E587C4F25DA51E252193126EC2FA41164DAB8BC556D4C3A50D2F6541397F501BF3351443A1AEBA80156212F8C54822040AD33ACF26087393B84692BE6A7365BBDC5E8EB78FED4A3C27B54E39E9AC1A7B8C7F7DCC8E65DA4516C57D21BF3D4A587E2B6AD398FC54616EF856DBAD29FBEC74C31C8137D775D54B32D2FFF2490A182514F2082A9400D9A5D04BE974399441D24E76F1BB80113A97F908CC7CDBAB7252C7E6A09DF6589E16CFF43F8362EC83E90C285189B35F48F57FC521E4C2BD1AD2A8084596EE7FD317FD9D95FB300570976D656F5D58C3F65C6D8276EEF4C1C68BFD66B2C6698DFF1A6AF688CB58C8ACACB8C2E7B1AAD517A972798372C4AD6AD34C2394FDE4F292CD7221071B21DF58CCDC09F5F4EF0F2B3465438C9D4F10E124AAD6683B0E2580CF444703E7705B1E72575DCCDB6C166899332D75117837EAFCECEA7FBF39997853A17282E6E49F4455D22F0DCC29B87EE2DD7217A9EFF05C5DE71017042A1F186C0AAF120EC69D2E5DCA978FD0B66F0DB262CE1BA288214C8335A3C72AB7089C91C40BD17A41030424B9AE15A41657C36CBC66F1452D2BB5B4B340D954810154405EC150AD1DCD7583F1EFEC2235CF2DF51CE525A5E7E737823B37AC41B90920C0DF70EA3E208219FB172371B9CEAA40F738F13468213E6D6EA062399AB06ED820AD988B4CACA998F9E799A1404618830C1A5F0A0425DF4E2A8DE6553DA7F30CECBDE1572109FA2E3AC375972C80700C958E126BE6CEC4C4550756886C1EA9F02B8D58304BAFD26FD2835C135F11D0217CD5754786D51791429CD9E58BF5CE20504EEAD3AE47569181FED55CE4CD7C02F1FF9330351C61561F7EABD0C2DF8156FD59B5ECFD0329DCF53F687A7E8DDF752AE206C65AC7B003E0863FEB10B36C3AB069515487685185AF0C48517DEE6574B5C6953E0A1E64F58D05448CBE40FCBE87B7085412BF8B8781EB6BA9A69E202AED1FE3D712F655F7D5373C052F5E5E45A495823812015B32D794FD842BBC4A43282231905C36A6047AAD2D419B9CDDF56221A6E249FE16CAAB2AEF33584B2534EE9FEE73B89348633ED138230D8CDD731D94397A040552DF7362483835147931836BF7BB24DCA4029E1B5AEB56D7EC547E65A8E95F4E8F406BBDB53C4F4CE1B149FB393A5B5A52EAEAC08AC3144CB693D050BE84B2C7F9E977B27DFB07A9C615006C939E5AE58E5263B54981195564E04534F723DB1F0915115DA6F54A1D0BE5D2BAF5A13318C20F2ADA736630A287D1C8C72BE86598AD8EA5F99B1D57A1C7A2E3ABF97F7D92C0BAE6FBD2DD8AEC7126680603A5C05DD7A2094ECDD3F01036EDA80D04F2C58C3B9D88DA91F6D4513AECDC4C2AA32F9FFA4B90E6A410C66948CE9758244DA79834716B071F49F56EF767A4EA42F10B4E8E1BB08934E34BFAD922F808961F91E07E85947EF7FED2D2C366A31F5E7F359773526E95C50820CF62ED74180108CB1FB3A2628B07C741A9A0F8B0261FCAD032D02E2FBC12C66E2A798AC41B5D604A8316DF46E5413FC21833BB94011B55A050448439384E78E9DDC960697A5FA0B885BC3939C038BD78D18F57E949E40A00D96C4DB790C73DC3DAA8446709E185D71F59FF1DBE86D76EC1887A34F5D4AB72E9182BE28CA73E57B4906175117A184ECB39A367B9D43ABA07B2386F2235DF55FCC5358B971BAAE1188218BFFF5C9F6C6F577BF09E9514F11BA9B6FCC087E60ED90284641CA2C4B3CC3EBECFFF60DC8F77B00F22ACA90B3A9C4677E7FEDE91BC6570693DC69CD1C7FE942DCB1AD331526091B9D18F17A3C9295DE5F1E90B81CE040FE3C4692BFC9F0AD87394C2C4E1E5FC3B43722CFE3623BA90BB51C615A044408801EE2328F1FBF3F4B292393CAE5D09288C44B6BFB8A8E2A6291B9D88E56E981D9AC73CABEA4C959270CB1CAE1B8DD5B613CCEE61FF25599E907C01E1FD5B57F0C9EC9578AEA177120D9EAC96D611E9054E8CCB1BA70988CA234698FB21708429B5635A6 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\c_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\c_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\c_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\c_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3092) c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\c_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
0
Suspicious files
275
Text files
207
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | c.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\YUZCTRJX-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.yuzctrjx | binary | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\YUZCTRJX-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3092 | c.exe | C:\Users\admin\AppData\Roaming\Adobe\YUZCTRJX-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
38
DNS requests
19
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3092 | c.exe | GET | — | 74.220.215.73:80 | http://www.bizziniinfissi.com/ | US | — | — | malicious |
3092 | c.exe | GET | — | 217.26.53.161:80 | http://www.haargenau.biz/ | CH | — | — | malicious |
3092 | c.exe | GET | 301 | 83.138.82.107:80 | http://www.swisswellness.com/ | DE | — | — | whitelisted |
3092 | c.exe | GET | — | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
3092 | c.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
3092 | c.exe | GET | — | 104.24.23.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
3092 | c.exe | GET | 301 | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
3092 | c.exe | GET | — | 217.26.53.37:80 | http://www.hrk-ramoz.com/ | CH | — | — | malicious |
3092 | c.exe | GET | — | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
3092 | c.exe | GET | 200 | 136.243.13.215:80 | http://www.holzbock.biz/ | DE | html | 1.78 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3092 | c.exe | 104.24.23.22:80 | www.belvedere-locarno.com | Cloudflare Inc | US | shared |
3092 | c.exe | 80.244.187.247:80 | www.hotelfarinet.com | UKfastnet Ltd | GB | suspicious |
3092 | c.exe | 80.244.187.247:443 | www.hotelfarinet.com | UKfastnet Ltd | GB | suspicious |
3092 | c.exe | 212.59.186.61:443 | www.hotelweisshorn.com | green.ch AG | CH | malicious |
3092 | c.exe | 217.26.53.37:80 | www.hrk-ramoz.com | Hostpoint AG | CH | malicious |
3092 | c.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3092 | c.exe | 78.46.77.98:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3092 | c.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
3092 | c.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
3092 | c.exe | 136.243.13.215:80 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3092 | c.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3092 | c.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
3092 | c.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3092 | c.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
3092 | c.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3092 | c.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
3092 | c.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3092 | c.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
3092 | c.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3092 | c.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |