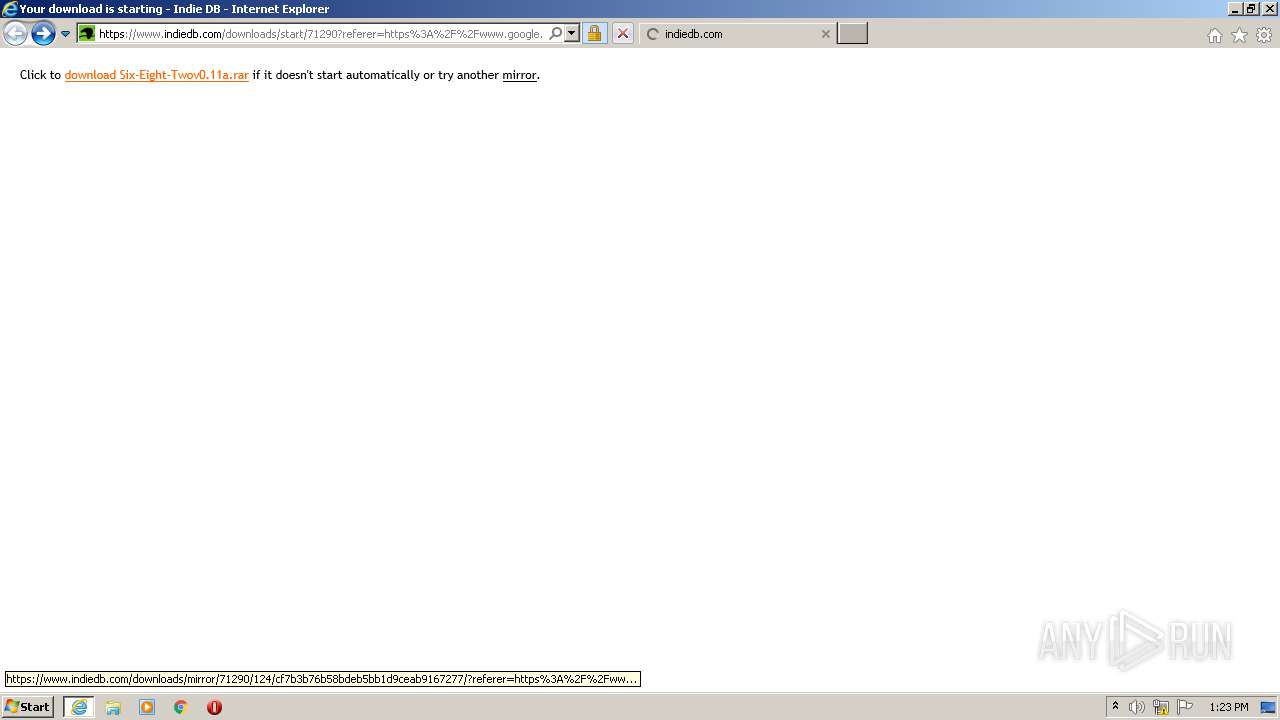
| URL: | https://www.indiedb.com/downloads/start/71290?referer=https%3A%2F%2Fwww.google.com%2F |
| Full analysis: | https://app.any.run/tasks/b429d284-1b79-4231-ba39-9185a2f00961 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 13:22:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 05334E78DF12329026516A2FF32A8236 |
| SHA1: | 22B16B0C571DB0CAB2A03F5BC38C961BAFA661EE |
| SHA256: | 4B5270F14F8A426D111ACC11ADCCA9ADA9257DB01BF065D6F84E01B1ABD57291 |
| SSDEEP: | 3:N8DSLaMO2aKXKWuJUXkRXU6AWCXjjP:2OLaMOmaWuaURXazjP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3452)
INFO
Application launched itself
- iexplore.exe (PID: 688)
Reads settings of System Certificates
- iexplore.exe (PID: 1700)
- iexplore.exe (PID: 688)
Reads internet explorer settings
- iexplore.exe (PID: 1700)
- iexplore.exe (PID: 2972)
Creates files in the user directory
- iexplore.exe (PID: 1700)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3452)
- iexplore.exe (PID: 688)
- iexplore.exe (PID: 2972)
Changes internet zones settings
- iexplore.exe (PID: 688)
Changes settings of System certificates
- iexplore.exe (PID: 688)
Adds / modifies Windows certificates
- iexplore.exe (PID: 688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 688 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.indiedb.com/downloads/start/71290?referer=https%3A%2F%2Fwww.google.com%2F | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1700 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:688 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:688 CREDAT:3544347 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3452 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
Total events
1 281
Read events
1 108
Write events
171
Delete events
2
Modification events
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3449642510 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30852690 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (688) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
72
Text files
111
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab36FC.tmp | — | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar36FD.tmp | — | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\RUU7Z85A.txt | — | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_ED4814D762306FD898B45E680A1C5D0C | der | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\QCTDJ3WO.txt | text | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | — | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 1700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_ED4814D762306FD898B45E680A1C5D0C | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
93
DNS requests
39
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1700 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEGTRSE7bbZvBAgAAAACAVY8%3D | US | der | 471 b | whitelisted |
1700 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEGTRSE7bbZvBAgAAAACAVY8%3D | US | der | 471 b | whitelisted |
1700 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCKcuDfDBqJ0QIAAAAAgFWT | US | der | 472 b | whitelisted |
1700 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDa2MTpyZrzlQgAAAAAYth4 | US | der | 472 b | whitelisted |
1700 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1700 | iexplore.exe | GET | 200 | 65.9.70.118:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
1700 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
1700 | iexplore.exe | GET | 200 | 65.9.70.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
1700 | iexplore.exe | GET | 200 | 65.9.70.118:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
1700 | iexplore.exe | GET | 200 | 65.9.70.156:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1700 | iexplore.exe | 104.26.13.36:443 | www.indiedb.com | Cloudflare Inc | US | unknown |
1700 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 65.9.68.113:443 | gamernetwork.mainroll.com | AT&T Services, Inc. | US | unknown |
1700 | iexplore.exe | 65.9.68.113:443 | gamernetwork.mainroll.com | AT&T Services, Inc. | US | unknown |
— | — | 65.9.70.195:80 | o.ss2.us | AT&T Services, Inc. | US | malicious |
— | — | 65.9.70.156:80 | o.ss2.us | AT&T Services, Inc. | US | unknown |
1700 | iexplore.exe | 65.9.70.118:80 | ocsp.rootg2.amazontrust.com | AT&T Services, Inc. | US | whitelisted |
1700 | iexplore.exe | 65.9.68.9:443 | cdn.bluebillywig.com | AT&T Services, Inc. | US | suspicious |
1700 | iexplore.exe | 65.9.70.213:80 | ocsp.rootg2.amazontrust.com | AT&T Services, Inc. | US | whitelisted |
— | — | 172.217.22.102:443 | s0.2mdn.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.indiedb.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
gamernetwork.mainroll.com |
| whitelisted |
static.indiedb.com |
| unknown |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
cdn.bluebillywig.com |
| whitelisted |
s0.2mdn.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1700 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1700 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1700 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1700 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2972 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2972 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2972 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |