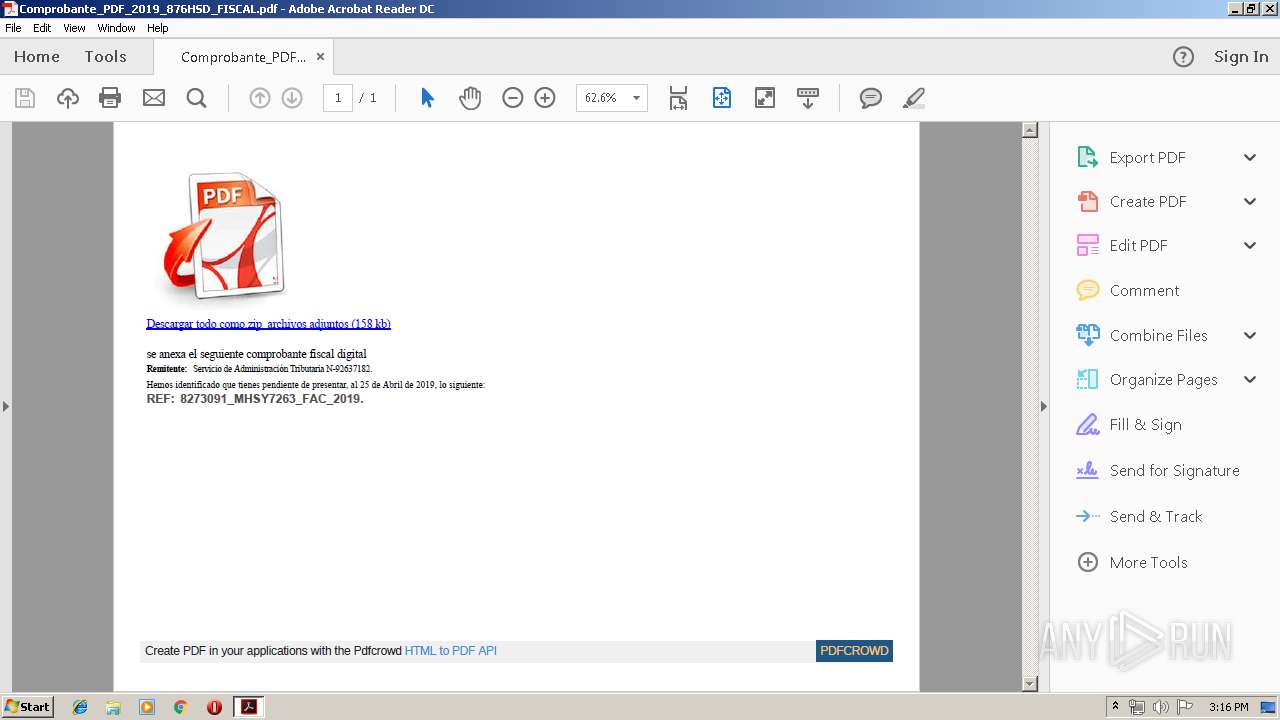
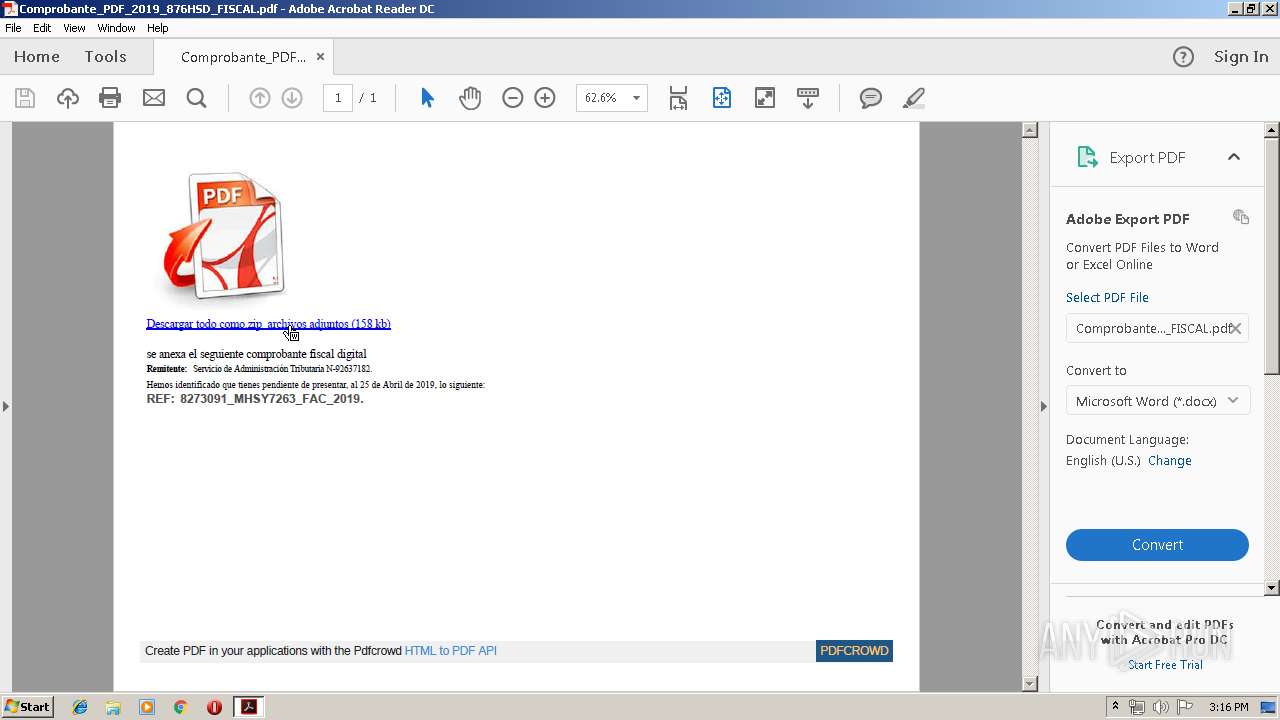
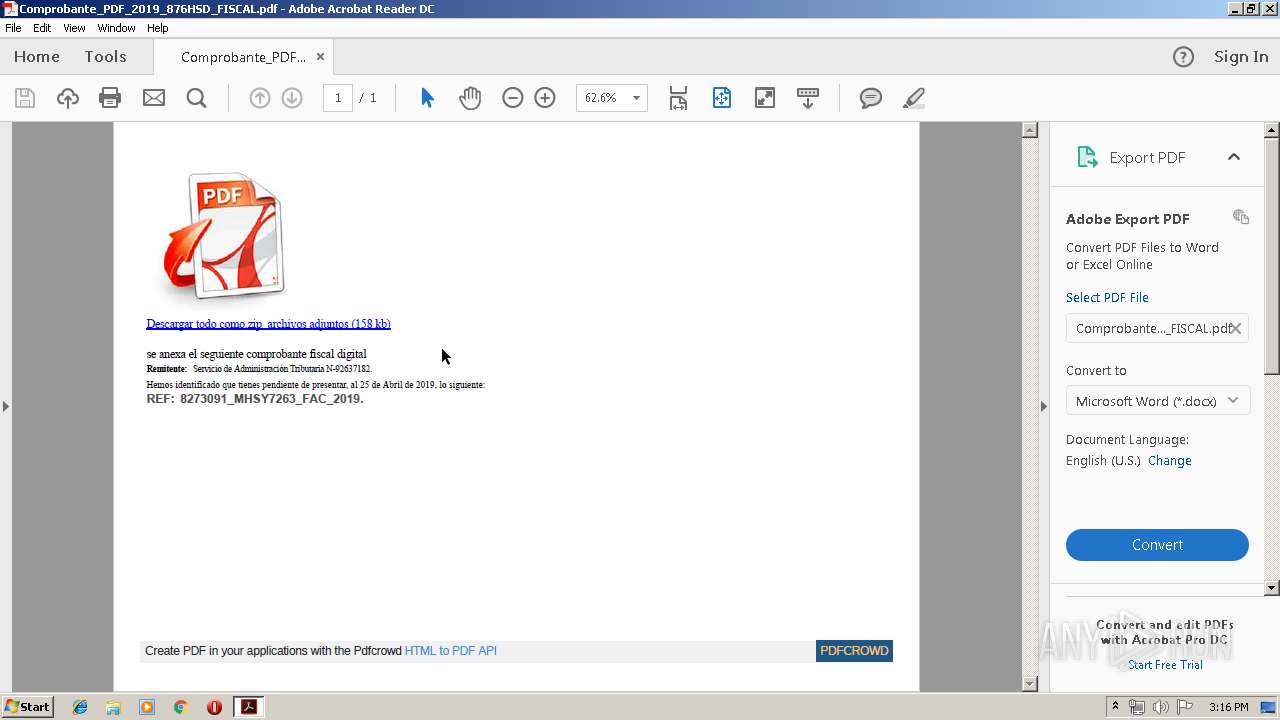
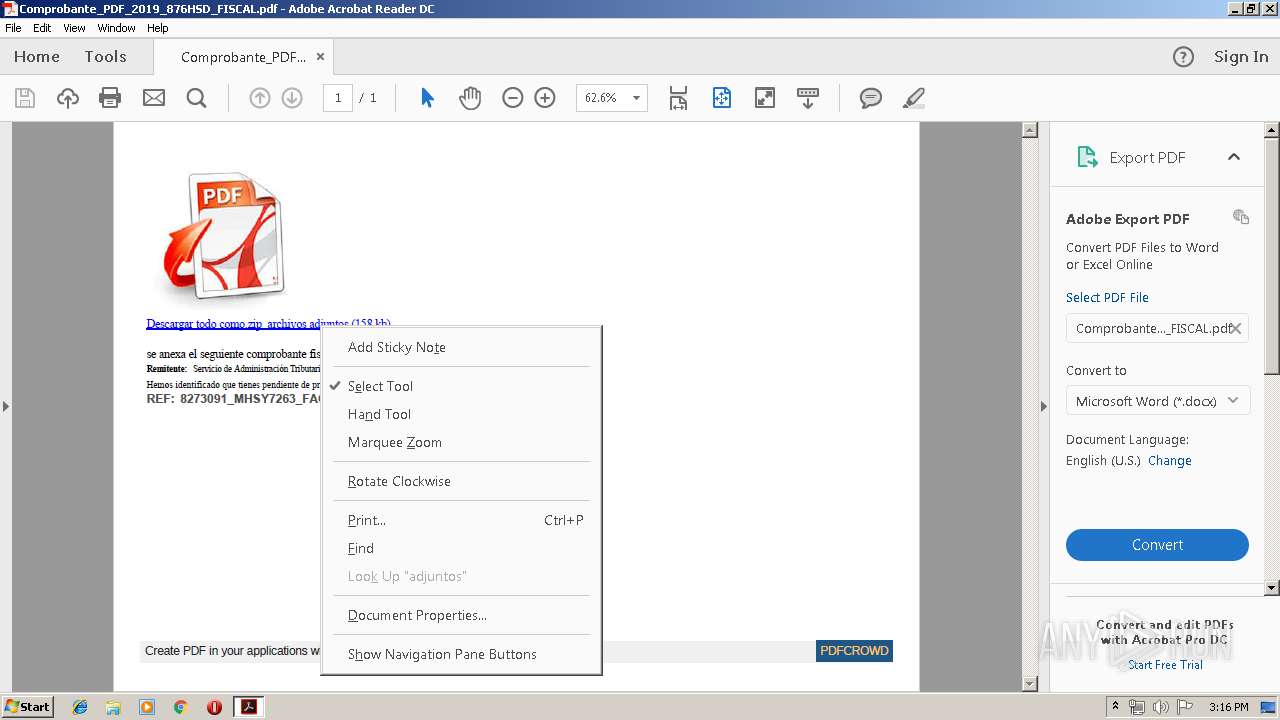
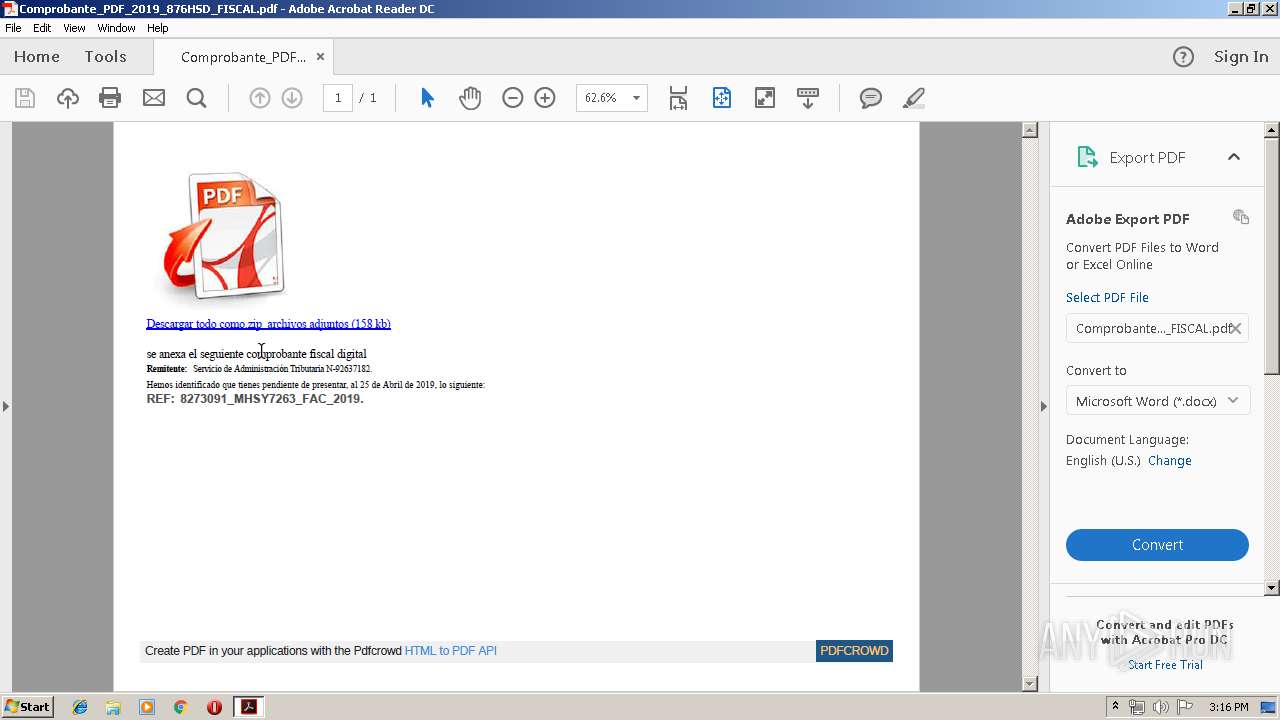
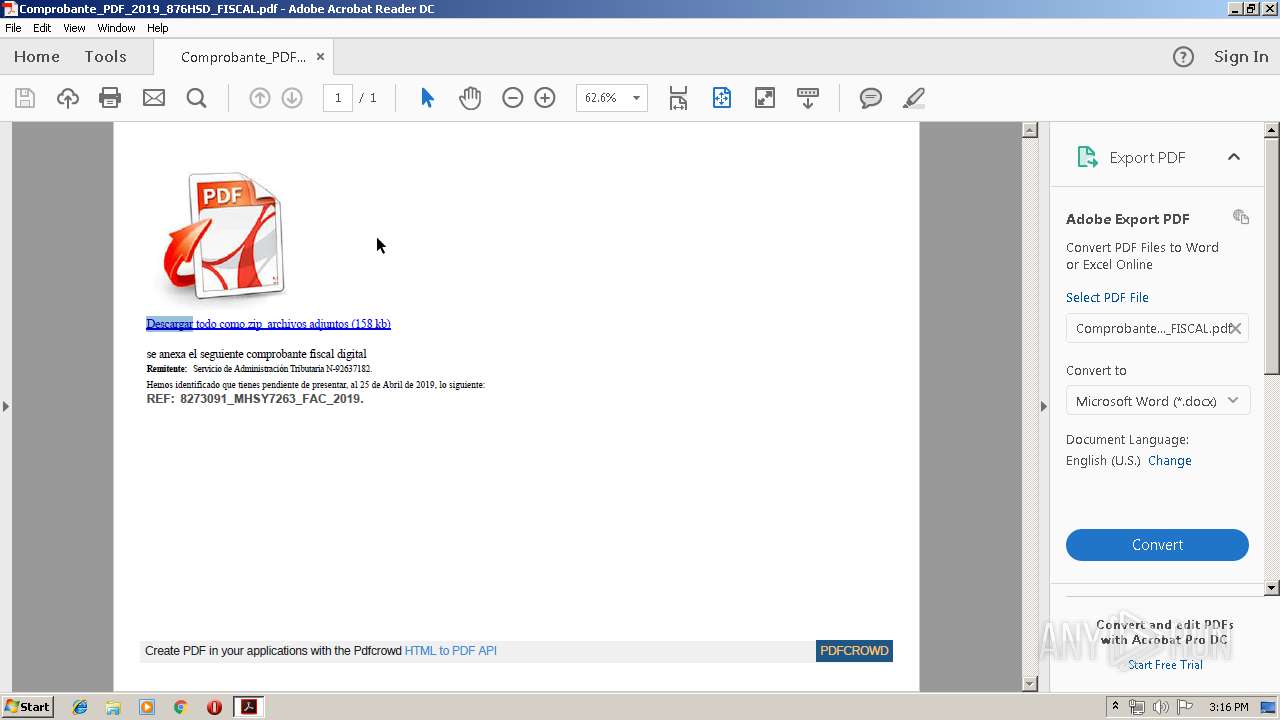
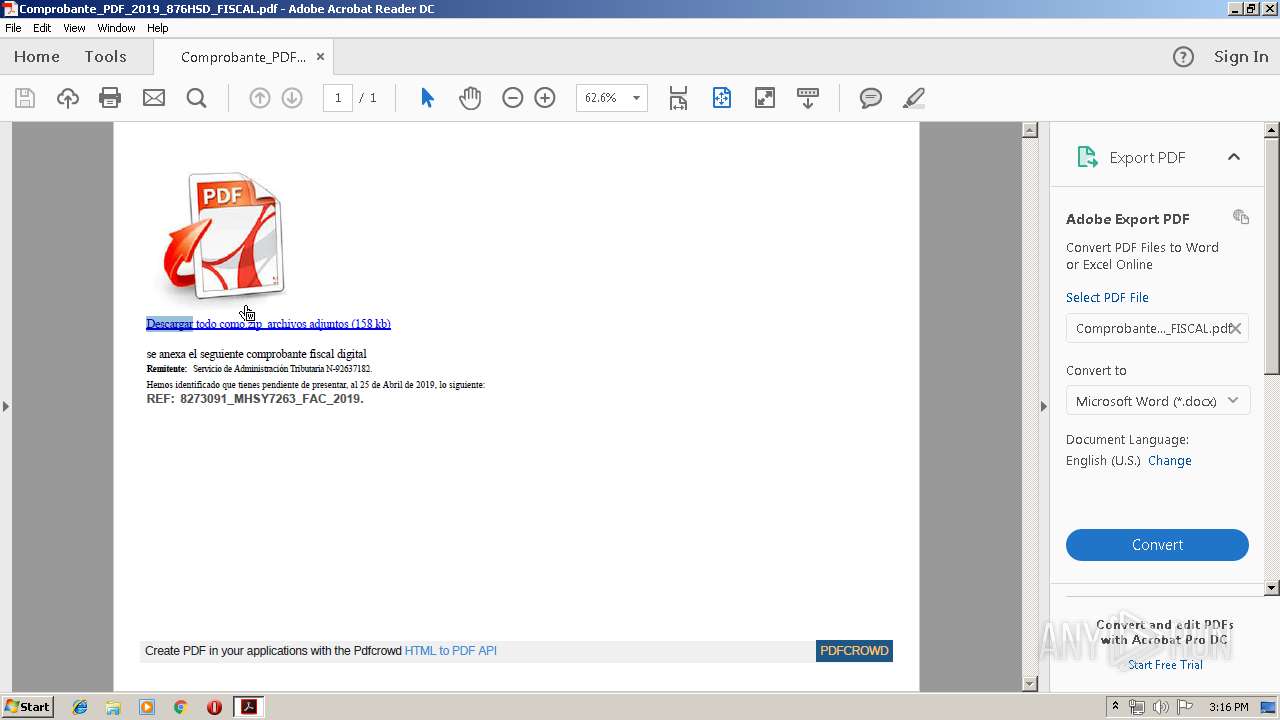
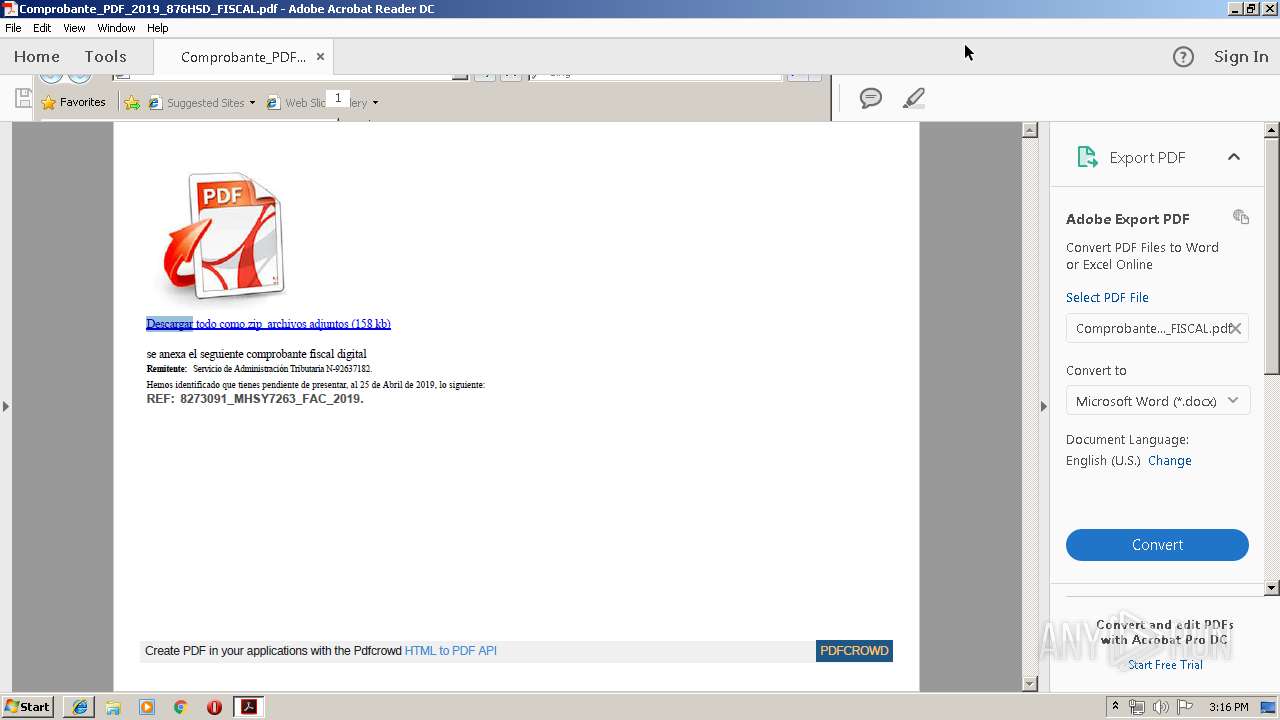
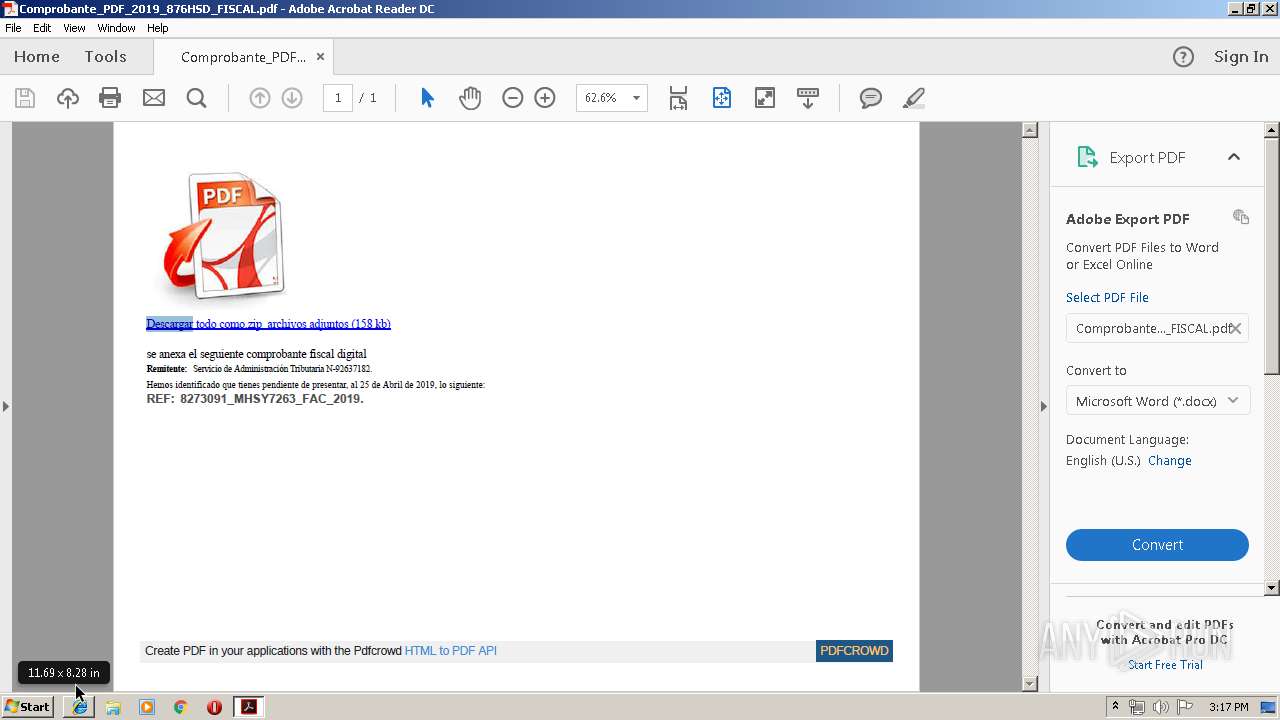
| File name: | Comprobante_PDF_2019_876HSD_FISCAL.pdf |
| Full analysis: | https://app.any.run/tasks/77021253-e4c4-45f5-99e2-81a233964634 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 14:15:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4 |
| MD5: | 1469015101698624835248264A9ED83E |
| SHA1: | CF37995D4423B4E554BA4879F34559564007C4F2 |
| SHA256: | 4B3FB82BEE0FB1F0847CDB450AF9FEBA96F5DCB3883E05EE8B77781C834A742A |
| SSDEEP: | 3072:nJVugdccj7NChLutktY5HmfpIx9T5VXnxp0nIhC:nJVugdbohgK29T3Xxp0IY |
MALICIOUS
No malicious indicators.SUSPICIOUS
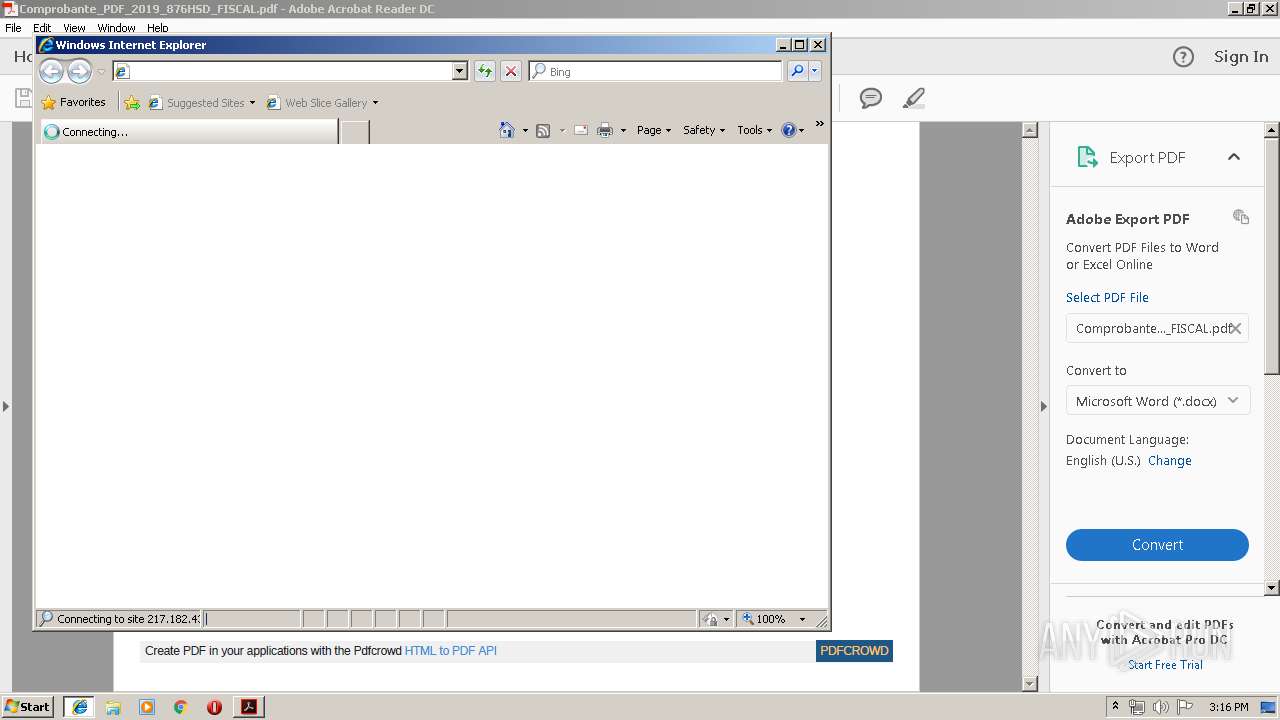
Starts Internet Explorer
- AcroRd32.exe (PID: 2184)
Creates files in the program directory
- AdobeARM.exe (PID: 3020)
INFO
Application launched itself
- AcroRd32.exe (PID: 2184)
- RdrCEF.exe (PID: 3152)
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 2980)
Creates files in the user directory
- AcroRd32.exe (PID: 2184)
- iexplore.exe (PID: 2620)
Changes internet zones settings
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 2980)
- iexplore.exe (PID: 3884)
Reads Internet Cache Settings
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 1972)
- iexplore.exe (PID: 2168)
Reads internet explorer settings
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 1972)
Reads settings of System Certificates
- iexplore.exe (PID: 4032)
Changes settings of System certificates
- iexplore.exe (PID: 4032)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Creator: | Pdfcrowd.com v20180221.063 |
| Producer: | Skia/PDF |
| ProductionLibrary: | Skia/PDF m63 |
| CreateDate: | 2019:04:25 03:26:42+00:00 |
| ModifyDate: | 2019:04:25 03:26:42+00:00 |
Total processes
44
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Comprobante_PDF_2019_876HSD_FISCAL.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3152.0.1311154407\1829991140" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2980 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3884 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Comprobante_PDF_2019_876HSD_FISCAL.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4032 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3152.1.1412478476\939305906" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
Total events
1 390
Read events
1 173
Write events
211
Delete events
6
Modification events
| (PID) Process: | (288) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (288) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (288) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {AD64D4B9-6764-11E9-A370-5254004A04AF} |
Value: 0 | |||
Executable files
0
Suspicious files
11
Text files
73
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 288 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9WX7QYYO\es-es[1].txt | — | |
MD5:— | SHA256:— | |||
| 288 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9WX7QYYO\social[1].txt | text | |
MD5:— | SHA256:— | |||
| 288 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9WX7QYYO\es-es[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
54
DNS requests
16
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2184 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2184 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2184 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
2184 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
2184 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3884 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2980 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
4032 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2620 | iexplore.exe | 217.182.43.136:443 | resortscancunv34zxweb.com.mx | OVH SAS | FR | unknown |
2620 | iexplore.exe | 2.18.233.62:443 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
2620 | iexplore.exe | 92.122.253.175:443 | c.s-microsoft.com | GTT Communications Inc. | — | suspicious |
2620 | iexplore.exe | 104.109.58.75:443 | mem.gfx.ms | Akamai International B.V. | NL | whitelisted |
2620 | iexplore.exe | 2.16.186.34:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
2620 | iexplore.exe | 104.111.243.146:443 | uhf.microsoft.com | Akamai International B.V. | NL | whitelisted |
4032 | iexplore.exe | 92.122.253.175:443 | c.s-microsoft.com | GTT Communications Inc. | — | suspicious |
2620 | iexplore.exe | 40.77.226.250:443 | web.vortex.data.microsoft.com | Microsoft Corporation | IE | whitelisted |
2184 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
1972 | iexplore.exe | 217.182.43.136:443 | resortscancunv34zxweb.com.mx | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
resortscancunv34zxweb.com.mx |
| unknown |
www.microsoft.com |
| whitelisted |
c.s-microsoft.com |
| whitelisted |
mem.gfx.ms |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
web.vortex.data.microsoft.com |
| whitelisted |
uhf.microsoft.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |