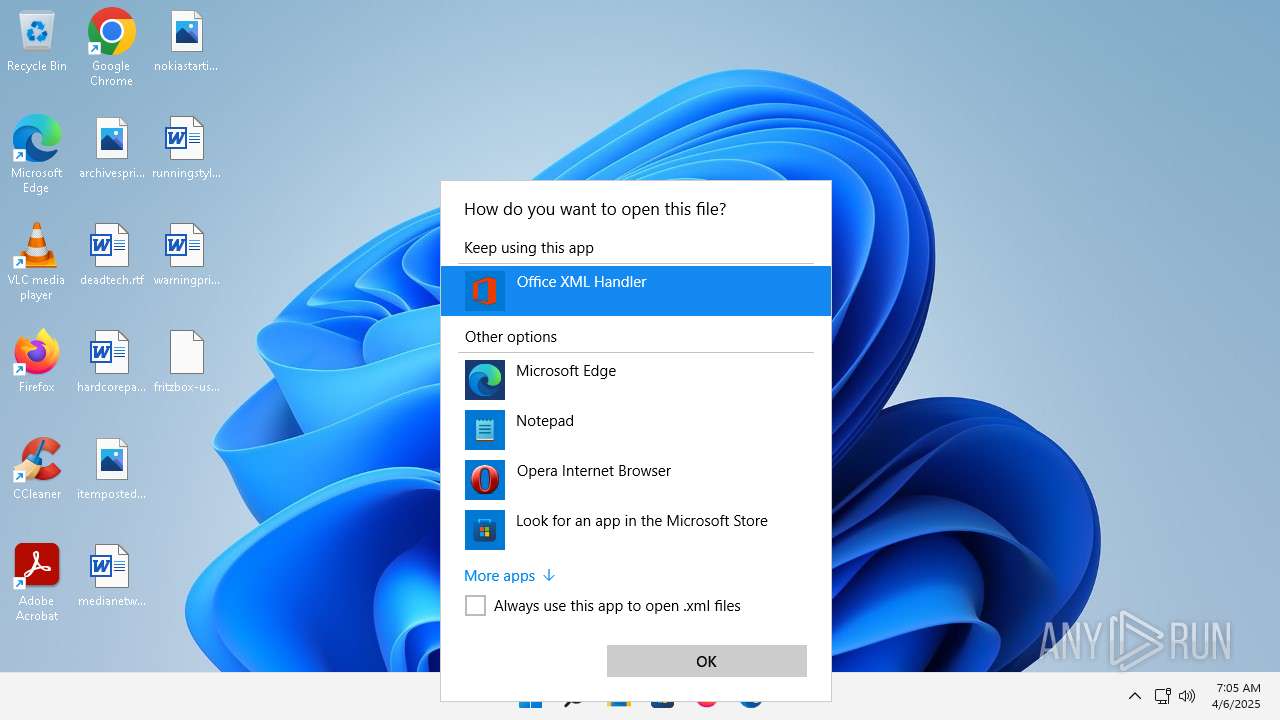
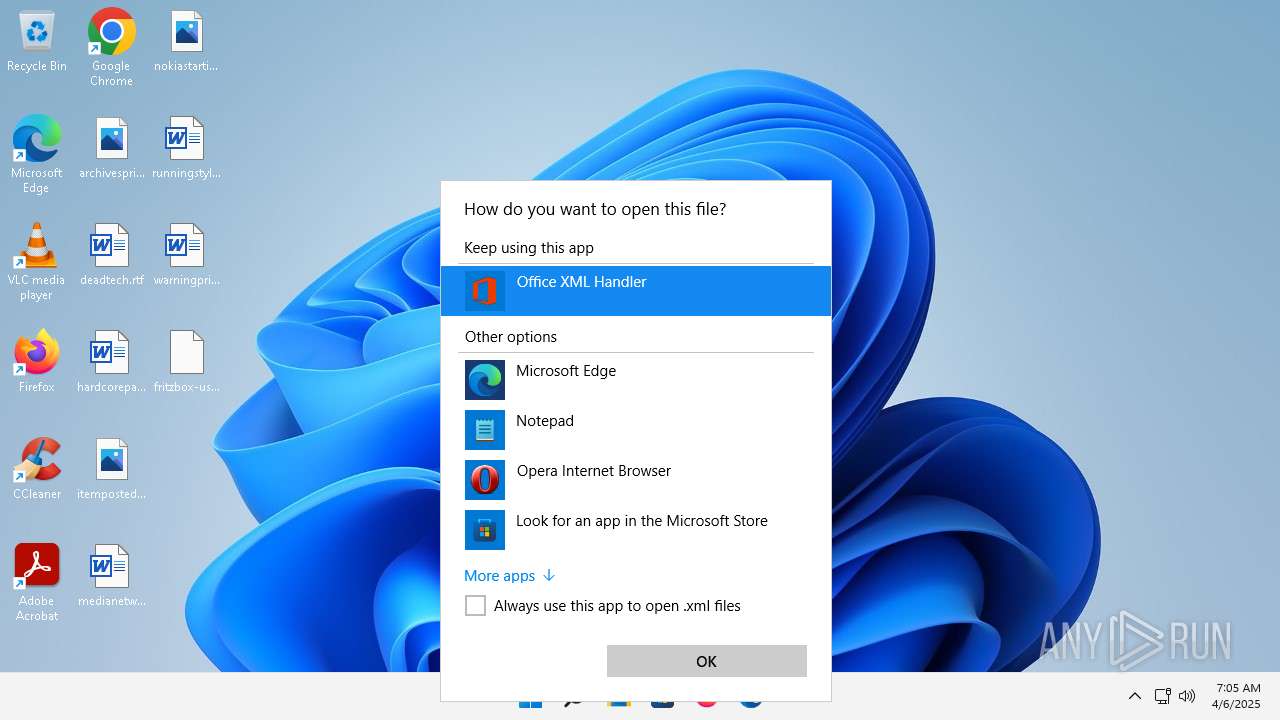
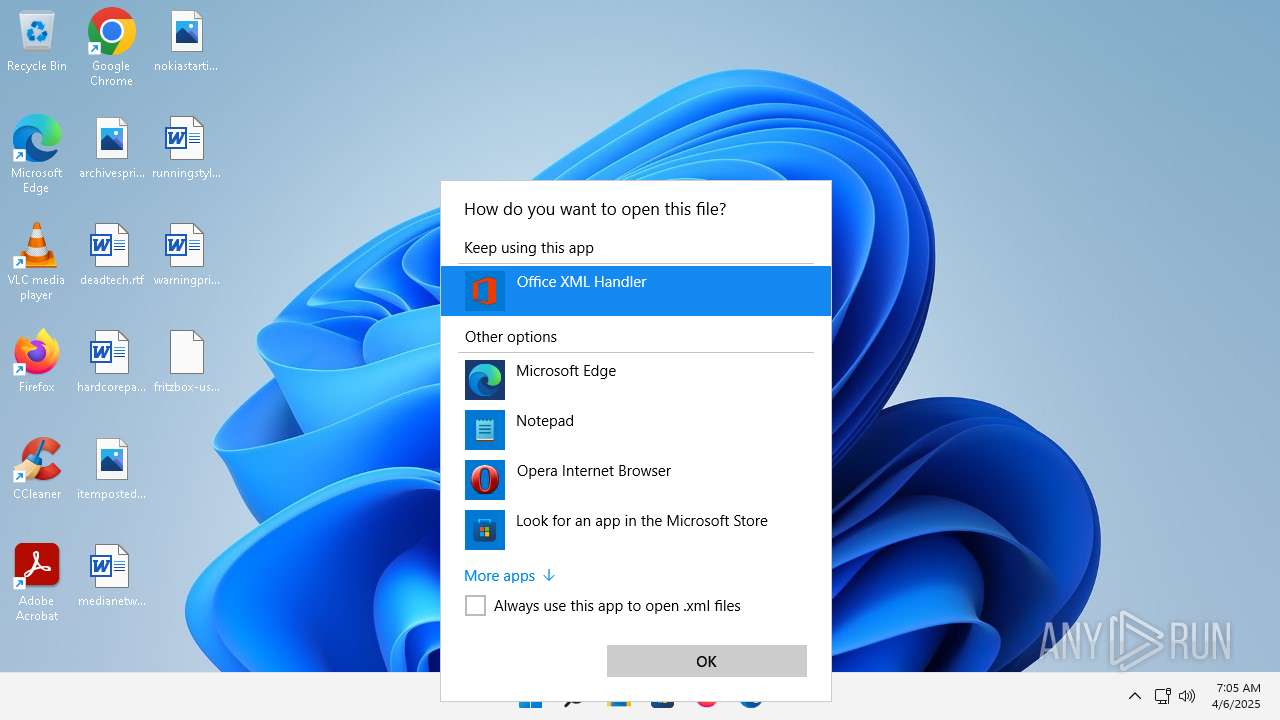
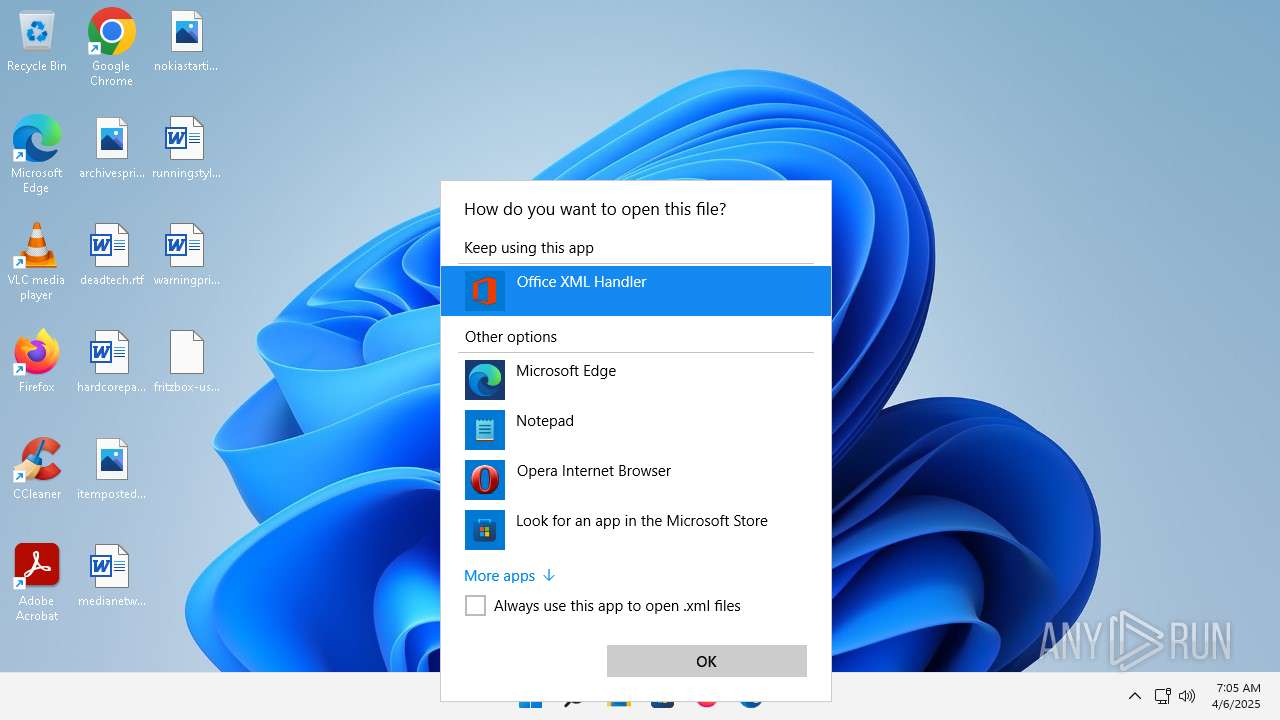
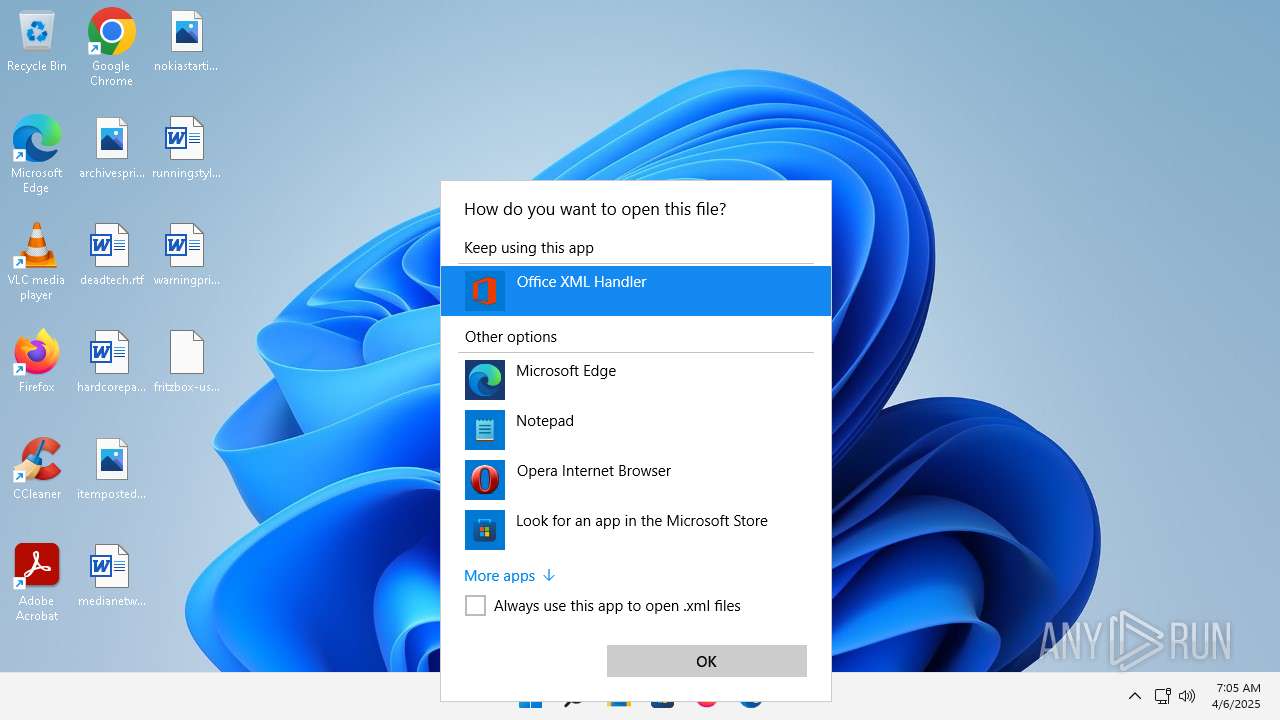
| File name: | fritzbox-usb-fernanschluss.application |
| Full analysis: | https://app.any.run/tasks/fc989e38-c75b-4b11-8589-87bc4869a62d |
| Verdict: | Malicious activity |
| Analysis date: | April 06, 2025, 07:03:59 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, Unicode text, UTF-8 (with BOM) text, with very long lines (7341), with CRLF line terminators |
| MD5: | 74D6B0D34A8E2B533BBDA4E069F38987 |
| SHA1: | 9DDEF37661748DB107A1E12DEAE4312E27A87E3F |
| SHA256: | 4B2E4C6F55833AA3F25EA0DB349EAB2D20D70E08518E75CF3C1D833540FBA791 |
| SSDEEP: | 192:okWbTWvUxMTn5Z8dp7YJAZ8dpIFJNBZDRjHfhwYT3qs35bZlZ07A:7wagdpMfdpUJNBZdjJwYTas3pZlKc |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- MSOXMLED.EXE (PID: 4812)
- OpenWith.exe (PID: 2864)
- MSOXMLED.EXE (PID: 4176)
- OpenWith.exe (PID: 3324)
- OpenWith.exe (PID: 1404)
- OpenWith.exe (PID: 1872)
- MSOXMLED.EXE (PID: 4204)
- MSOXMLED.EXE (PID: 5928)
- MSOXMLED.EXE (PID: 5080)
- OpenWith.exe (PID: 1604)
- MSOXMLED.EXE (PID: 3616)
- OpenWith.exe (PID: 2664)
- OpenWith.exe (PID: 4184)
- MSOXMLED.EXE (PID: 1752)
- OpenWith.exe (PID: 1152)
- MSOXMLED.EXE (PID: 3568)
- MSOXMLED.EXE (PID: 3404)
- MSOXMLED.EXE (PID: 2560)
- OpenWith.exe (PID: 3584)
- OpenWith.exe (PID: 5876)
- MSOXMLED.EXE (PID: 4460)
- MSOXMLED.EXE (PID: 3432)
- OpenWith.exe (PID: 1812)
- OpenWith.exe (PID: 4940)
- MSOXMLED.EXE (PID: 3416)
- OpenWith.exe (PID: 4452)
- MSOXMLED.EXE (PID: 2368)
- OpenWith.exe (PID: 508)
- MSOXMLED.EXE (PID: 2864)
- OpenWith.exe (PID: 3220)
- OpenWith.exe (PID: 2028)
- MSOXMLED.EXE (PID: 3392)
- OpenWith.exe (PID: 952)
- MSOXMLED.EXE (PID: 1868)
- MSOXMLED.EXE (PID: 3032)
- OpenWith.exe (PID: 2276)
- OpenWith.exe (PID: 3532)
- MSOXMLED.EXE (PID: 1688)
- MSOXMLED.EXE (PID: 436)
- MSOXMLED.EXE (PID: 2308)
- OpenWith.exe (PID: 4288)
- OpenWith.exe (PID: 3996)
- MSOXMLED.EXE (PID: 2736)
- OpenWith.exe (PID: 1800)
- OpenWith.exe (PID: 5324)
- MSOXMLED.EXE (PID: 4564)
- MSOXMLED.EXE (PID: 2552)
- OpenWith.exe (PID: 5088)
- MSOXMLED.EXE (PID: 3296)
- OpenWith.exe (PID: 4588)
- OpenWith.exe (PID: 2280)
- OpenWith.exe (PID: 1904)
- MSOXMLED.EXE (PID: 1696)
- MSOXMLED.EXE (PID: 4472)
- OpenWith.exe (PID: 6032)
- MSOXMLED.EXE (PID: 2568)
- OpenWith.exe (PID: 4780)
- MSOXMLED.EXE (PID: 5876)
- MSOXMLED.EXE (PID: 3116)
- OpenWith.exe (PID: 4104)
- MSOXMLED.EXE (PID: 4068)
- OpenWith.exe (PID: 3784)
- OpenWith.exe (PID: 1600)
- MSOXMLED.EXE (PID: 3216)
- MSOXMLED.EXE (PID: 5200)
- OpenWith.exe (PID: 3684)
- MSOXMLED.EXE (PID: 5104)
- OpenWith.exe (PID: 1620)
- MSOXMLED.EXE (PID: 1800)
- MSOXMLED.EXE (PID: 3068)
- OpenWith.exe (PID: 4196)
- OpenWith.exe (PID: 5260)
- MSOXMLED.EXE (PID: 1468)
- OpenWith.exe (PID: 1684)
- MSOXMLED.EXE (PID: 508)
- OpenWith.exe (PID: 5892)
- MSOXMLED.EXE (PID: 356)
- OpenWith.exe (PID: 1740)
- MSOXMLED.EXE (PID: 2176)
- MSOXMLED.EXE (PID: 832)
- OpenWith.exe (PID: 4708)
- OpenWith.exe (PID: 1516)
Reads security settings of Internet Explorer
- MSOXMLED.EXE (PID: 4812)
- MSOXMLED.EXE (PID: 4176)
- MSOXMLED.EXE (PID: 4204)
- MSOXMLED.EXE (PID: 5928)
- MSOXMLED.EXE (PID: 3616)
- MSOXMLED.EXE (PID: 5080)
- MSOXMLED.EXE (PID: 1752)
- MSOXMLED.EXE (PID: 3568)
- MSOXMLED.EXE (PID: 3404)
- MSOXMLED.EXE (PID: 2560)
- MSOXMLED.EXE (PID: 4460)
- MSOXMLED.EXE (PID: 3432)
- MSOXMLED.EXE (PID: 3416)
- MSOXMLED.EXE (PID: 2368)
- MSOXMLED.EXE (PID: 2864)
- MSOXMLED.EXE (PID: 3392)
- MSOXMLED.EXE (PID: 3032)
- MSOXMLED.EXE (PID: 1868)
- MSOXMLED.EXE (PID: 1688)
- MSOXMLED.EXE (PID: 436)
- MSOXMLED.EXE (PID: 2308)
- MSOXMLED.EXE (PID: 2736)
- MSOXMLED.EXE (PID: 4564)
- MSOXMLED.EXE (PID: 2552)
- MSOXMLED.EXE (PID: 3296)
- MSOXMLED.EXE (PID: 1696)
- MSOXMLED.EXE (PID: 4472)
- MSOXMLED.EXE (PID: 2568)
- MSOXMLED.EXE (PID: 5876)
- MSOXMLED.EXE (PID: 4068)
- MSOXMLED.EXE (PID: 3116)
- MSOXMLED.EXE (PID: 3216)
- MSOXMLED.EXE (PID: 5200)
- MSOXMLED.EXE (PID: 1800)
- MSOXMLED.EXE (PID: 3068)
- MSOXMLED.EXE (PID: 5104)
- MSOXMLED.EXE (PID: 1468)
- MSOXMLED.EXE (PID: 508)
- MSOXMLED.EXE (PID: 356)
- MSOXMLED.EXE (PID: 2176)
- MSOXMLED.EXE (PID: 832)
INFO
Checks supported languages
- MSOXMLED.EXE (PID: 4812)
- MSOXMLED.EXE (PID: 4176)
- MSOXMLED.EXE (PID: 4204)
- MSOXMLED.EXE (PID: 5928)
- MSOXMLED.EXE (PID: 3616)
- MSOXMLED.EXE (PID: 5080)
- MSOXMLED.EXE (PID: 1752)
- MSOXMLED.EXE (PID: 3568)
- MSOXMLED.EXE (PID: 3404)
- MSOXMLED.EXE (PID: 2560)
- MSOXMLED.EXE (PID: 4460)
- MSOXMLED.EXE (PID: 3416)
- MSOXMLED.EXE (PID: 3432)
- MSOXMLED.EXE (PID: 2368)
- MSOXMLED.EXE (PID: 3392)
- MSOXMLED.EXE (PID: 2864)
- MSOXMLED.EXE (PID: 1868)
- MSOXMLED.EXE (PID: 2308)
- MSOXMLED.EXE (PID: 3032)
- MSOXMLED.EXE (PID: 1688)
- MSOXMLED.EXE (PID: 436)
- MSOXMLED.EXE (PID: 4564)
- MSOXMLED.EXE (PID: 2736)
- MSOXMLED.EXE (PID: 3296)
- MSOXMLED.EXE (PID: 4472)
- MSOXMLED.EXE (PID: 2552)
- MSOXMLED.EXE (PID: 1696)
- MSOXMLED.EXE (PID: 5876)
- MSOXMLED.EXE (PID: 2568)
- MSOXMLED.EXE (PID: 4068)
- MSOXMLED.EXE (PID: 3116)
- MSOXMLED.EXE (PID: 3216)
- MSOXMLED.EXE (PID: 1800)
- MSOXMLED.EXE (PID: 5200)
- MSOXMLED.EXE (PID: 5104)
- MSOXMLED.EXE (PID: 3068)
- MSOXMLED.EXE (PID: 1468)
- MSOXMLED.EXE (PID: 508)
- MSOXMLED.EXE (PID: 356)
- MSOXMLED.EXE (PID: 832)
- MSOXMLED.EXE (PID: 2176)
Reads Microsoft Office registry keys
- MSOXMLED.EXE (PID: 4812)
- OpenWith.exe (PID: 2864)
- MSOXMLED.EXE (PID: 4176)
- OpenWith.exe (PID: 3324)
- MSOXMLED.EXE (PID: 5928)
- OpenWith.exe (PID: 1872)
- MSOXMLED.EXE (PID: 4204)
- OpenWith.exe (PID: 1404)
- OpenWith.exe (PID: 1604)
- MSOXMLED.EXE (PID: 3616)
- OpenWith.exe (PID: 2664)
- MSOXMLED.EXE (PID: 5080)
- MSOXMLED.EXE (PID: 3404)
- OpenWith.exe (PID: 4184)
- OpenWith.exe (PID: 1152)
- MSOXMLED.EXE (PID: 1752)
- MSOXMLED.EXE (PID: 3568)
- OpenWith.exe (PID: 5876)
- MSOXMLED.EXE (PID: 2560)
- OpenWith.exe (PID: 3584)
- MSOXMLED.EXE (PID: 4460)
- OpenWith.exe (PID: 1812)
- MSOXMLED.EXE (PID: 3432)
- OpenWith.exe (PID: 4940)
- MSOXMLED.EXE (PID: 3416)
- OpenWith.exe (PID: 4452)
- MSOXMLED.EXE (PID: 2368)
- OpenWith.exe (PID: 508)
- MSOXMLED.EXE (PID: 2864)
- OpenWith.exe (PID: 3220)
- MSOXMLED.EXE (PID: 3392)
- OpenWith.exe (PID: 2028)
- OpenWith.exe (PID: 2276)
- MSOXMLED.EXE (PID: 1868)
- OpenWith.exe (PID: 952)
- MSOXMLED.EXE (PID: 3032)
- OpenWith.exe (PID: 3532)
- MSOXMLED.EXE (PID: 1688)
- OpenWith.exe (PID: 4288)
- MSOXMLED.EXE (PID: 436)
- MSOXMLED.EXE (PID: 2308)
- OpenWith.exe (PID: 3996)
- OpenWith.exe (PID: 1800)
- MSOXMLED.EXE (PID: 2736)
- OpenWith.exe (PID: 5324)
- MSOXMLED.EXE (PID: 4564)
- MSOXMLED.EXE (PID: 2552)
- OpenWith.exe (PID: 5088)
- MSOXMLED.EXE (PID: 3296)
- OpenWith.exe (PID: 4588)
- MSOXMLED.EXE (PID: 1696)
- OpenWith.exe (PID: 1904)
- MSOXMLED.EXE (PID: 4472)
- OpenWith.exe (PID: 2280)
- OpenWith.exe (PID: 6032)
- MSOXMLED.EXE (PID: 2568)
- OpenWith.exe (PID: 4780)
- MSOXMLED.EXE (PID: 5876)
- OpenWith.exe (PID: 3784)
- OpenWith.exe (PID: 4104)
- MSOXMLED.EXE (PID: 4068)
- MSOXMLED.EXE (PID: 3116)
- OpenWith.exe (PID: 1600)
- MSOXMLED.EXE (PID: 3216)
- OpenWith.exe (PID: 1620)
- MSOXMLED.EXE (PID: 5200)
- MSOXMLED.EXE (PID: 5104)
- MSOXMLED.EXE (PID: 1800)
- OpenWith.exe (PID: 3684)
- MSOXMLED.EXE (PID: 1468)
- MSOXMLED.EXE (PID: 3068)
- OpenWith.exe (PID: 4196)
- OpenWith.exe (PID: 5260)
- OpenWith.exe (PID: 1684)
- MSOXMLED.EXE (PID: 508)
- OpenWith.exe (PID: 5892)
- MSOXMLED.EXE (PID: 356)
- OpenWith.exe (PID: 1740)
- MSOXMLED.EXE (PID: 832)
- MSOXMLED.EXE (PID: 2176)
- OpenWith.exe (PID: 1516)
- OpenWith.exe (PID: 4708)
Reads the computer name
- MSOXMLED.EXE (PID: 4812)
- MSOXMLED.EXE (PID: 4176)
- MSOXMLED.EXE (PID: 4204)
- MSOXMLED.EXE (PID: 5928)
- MSOXMLED.EXE (PID: 3616)
- MSOXMLED.EXE (PID: 5080)
- MSOXMLED.EXE (PID: 1752)
- MSOXMLED.EXE (PID: 3568)
- MSOXMLED.EXE (PID: 3404)
- MSOXMLED.EXE (PID: 2560)
- MSOXMLED.EXE (PID: 4460)
- MSOXMLED.EXE (PID: 3432)
- MSOXMLED.EXE (PID: 3416)
- MSOXMLED.EXE (PID: 2368)
- MSOXMLED.EXE (PID: 3032)
- MSOXMLED.EXE (PID: 3392)
- MSOXMLED.EXE (PID: 2864)
- MSOXMLED.EXE (PID: 1868)
- MSOXMLED.EXE (PID: 1688)
- MSOXMLED.EXE (PID: 436)
- MSOXMLED.EXE (PID: 2308)
- MSOXMLED.EXE (PID: 4564)
- MSOXMLED.EXE (PID: 2736)
- MSOXMLED.EXE (PID: 3296)
- MSOXMLED.EXE (PID: 2552)
- MSOXMLED.EXE (PID: 1696)
- MSOXMLED.EXE (PID: 5876)
- MSOXMLED.EXE (PID: 4472)
- MSOXMLED.EXE (PID: 2568)
- MSOXMLED.EXE (PID: 3116)
- MSOXMLED.EXE (PID: 5200)
- MSOXMLED.EXE (PID: 4068)
- MSOXMLED.EXE (PID: 3216)
- MSOXMLED.EXE (PID: 5104)
- MSOXMLED.EXE (PID: 1800)
- MSOXMLED.EXE (PID: 3068)
- MSOXMLED.EXE (PID: 1468)
- MSOXMLED.EXE (PID: 356)
- MSOXMLED.EXE (PID: 508)
- MSOXMLED.EXE (PID: 2176)
- MSOXMLED.EXE (PID: 832)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 2864)
- OpenWith.exe (PID: 1872)
- OpenWith.exe (PID: 1404)
- OpenWith.exe (PID: 3324)
- OpenWith.exe (PID: 1604)
- OpenWith.exe (PID: 2664)
- OpenWith.exe (PID: 4184)
- OpenWith.exe (PID: 1152)
- OpenWith.exe (PID: 5876)
- OpenWith.exe (PID: 3584)
- OpenWith.exe (PID: 1812)
- OpenWith.exe (PID: 4940)
- OpenWith.exe (PID: 4452)
- OpenWith.exe (PID: 508)
- OpenWith.exe (PID: 3220)
- OpenWith.exe (PID: 2028)
- OpenWith.exe (PID: 2276)
- OpenWith.exe (PID: 952)
- OpenWith.exe (PID: 4288)
- OpenWith.exe (PID: 3532)
- OpenWith.exe (PID: 3996)
- OpenWith.exe (PID: 1800)
- OpenWith.exe (PID: 5324)
- OpenWith.exe (PID: 5088)
- OpenWith.exe (PID: 4588)
- OpenWith.exe (PID: 2280)
- OpenWith.exe (PID: 1904)
- OpenWith.exe (PID: 4780)
- OpenWith.exe (PID: 6032)
- OpenWith.exe (PID: 4104)
- OpenWith.exe (PID: 3784)
- OpenWith.exe (PID: 1620)
- OpenWith.exe (PID: 1600)
- OpenWith.exe (PID: 3684)
- OpenWith.exe (PID: 1684)
- OpenWith.exe (PID: 4196)
- OpenWith.exe (PID: 5260)
- OpenWith.exe (PID: 5892)
- OpenWith.exe (PID: 1740)
- OpenWith.exe (PID: 1516)
- OpenWith.exe (PID: 4708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xml | | | Generic XML (UTF-8) (72.7) |
|---|---|---|
| .txt | | | Text - UTF-8 encoded (27.2) |
EXIF
XMP
| AssemblySchemaLocation: | urn:schemas-microsoft-com:asm.v1 assembly.adaptive.xsd |
|---|---|
| AssemblyManifestVersion: | 1 |
| AssemblyXmlns: | urn:schemas-microsoft-com:asm.v2 |
| AssemblyAssemblyIdentityName: | fritzbox-usb-fernanschluss.application |
| AssemblyAssemblyIdentityVersion: | 2.3.5.1 |
| AssemblyAssemblyIdentityPublicKeyToken: | 4b253d3c7789a3f0 |
| AssemblyAssemblyIdentityLanguage: | de |
| AssemblyAssemblyIdentityProcessorArchitecture: | x86 |
| AssemblyAssemblyIdentityXmlns: | urn:schemas-microsoft-com:asm.v1 |
| AssemblyDescriptionPublisher: | FRITZ!Box |
| AssemblyDescriptionProduct: | FRITZ!Box USB-Fernanschluss |
| AssemblyDescriptionSupportUrl: | https://avm.de/ |
| AssemblyDescriptionXmlns: | urn:schemas-microsoft-com:asm.v1 |
| AssemblyDeploymentInstall: | |
| AssemblyDeploymentTrustURLParameters: | |
| AssemblyDeploymentSubscriptionUpdateExpirationMaximumAge: | 2 |
| AssemblyDeploymentSubscriptionUpdateExpirationUnit: | weeks |
| AssemblyDeploymentDeploymentProviderCodebase: | https://clickonce.avm.de/usb-fernanschluss2/deutsch/fritzbox-usb-fernanschluss.application |
| AssemblyDependencyDependentAssemblyDependencyType: | install |
| AssemblyDependencyDependentAssemblyCodebase: | Application%20Files\fritzbox-usb-fernanschluss_2_3_5_1\fritzbox-usb-fernanschluss.exe.manifest |
| AssemblyDependencyDependentAssemblySize: | 22028 |
| AssemblyDependencyDependentAssemblyAssemblyIdentityName: | fritzbox-usb-fernanschluss.exe |
| AssemblyDependencyDependentAssemblyAssemblyIdentityVersion: | 2.3.5.1 |
| AssemblyDependencyDependentAssemblyAssemblyIdentityPublicKeyToken: | 4b253d3c7789a3f0 |
| AssemblyDependencyDependentAssemblyAssemblyIdentityLanguage: | de |
| AssemblyDependencyDependentAssemblyAssemblyIdentityProcessorArchitecture: | x86 |
| AssemblyDependencyDependentAssemblyAssemblyIdentityType: | win32 |
| AssemblyDependencyDependentAssemblyHashTransformsTransformAlgorithm: | urn:schemas-microsoft-com:HashTransforms.Identity |
| AssemblyDependencyDependentAssemblyHashDigestMethodAlgorithm: | http://www.w3.org/2000/09/xmldsig#sha1 |
| AssemblyDependencyDependentAssemblyHashDigestValue: | iJ5FYZMogtZS5d9e1HLZRwBYs9w= |
| AssemblyCompatibleFrameworksXmlns: | urn:schemas-microsoft-com:clickonce.v2 |
| AssemblyCompatibleFrameworksFrameworkTargetVersion: | 4 |
| AssemblyCompatibleFrameworksFrameworkProfile: | Full |
| AssemblyCompatibleFrameworksFrameworkSupportedRuntime: | 4.0.30319 |
| AssemblyPublisherIdentityName: | CN=W10-JDG\jdg |
| AssemblyPublisherIdentityIssuerKeyHash: | 5fd636342c920388293d294e9f886f92478a2a4c |
| AssemblySignatureId: | StrongNameSignature |
| AssemblySignatureXmlns: | http://www.w3.org/2000/09/xmldsig# |
| AssemblySignatureSignedInfoCanonicalizationMethodAlgorithm: | http://www.w3.org/2001/10/xml-exc-c14n# |
| AssemblySignatureSignedInfoSignatureMethodAlgorithm: | http://www.w3.org/2000/09/xmldsig#rsa-sha1 |
| AssemblySignatureSignedInfoReferenceUri: | - |
| AssemblySignatureSignedInfoReferenceTransformsTransformAlgorithm: | http://www.w3.org/2000/09/xmldsig#enveloped-signature |
| AssemblySignatureSignedInfoReferenceDigestMethodAlgorithm: | http://www.w3.org/2000/09/xmldsig#sha1 |
| AssemblySignatureSignedInfoReferenceDigestValue: | JopWxOCFiO4cYzZ1iaYZbyAVPc8= |
| AssemblySignatureSignatureValue: | JWjhBME19joa5d631Ch43WWzCiLQmI+EhUNfvac0BDsR5zyriiFkCvdVWMbAilJEMhWrzCzbkP0HAMl3Ov8MyfnKrKv0oEdTROPv+7ctTxtatstyoOF/qUW28MSLLF+PlGrFvRIZTqgLwfkuLyM5su6lUkMCFx4cVQ3o0FXwScYua3JI+N8q9iwY0nhW1J0QQdudT0Q9BSCtztYG7BmW71fh6+SkEdAZvxZnnAEX+MVAG+keke27E3+ROgPX//3pjoybX2ORQr5XbZF1+iOEiUtT+f+S64Et/Kjy5YRqkXo/4k4voZfGPuGV7iHJNFDoV3RPXjY5EE0F0glrJmvmjg== |
| AssemblySignatureKeyInfoId: | StrongNameKeyInfo |
| AssemblySignatureKeyInfoKeyValueRSAKeyValueModulus: | otkS1lql1dJS/VbBFcnkGZxi8Fc98feoEEyb+qeOWruAHA6IFhxk2bieXAHSepYOzfnaKjp++rZ4eLmyFad1IHODL4/jfyK7oODMPDLEDArpeJO8p1iABeRm3+nBAMmagyZapyMv/CiWjs87++qv9H6CyINl4E997plM8GTKTz1hEp7SGjSUwLW72UKeJsXk3To1A+QLmZb8qeSuE7cG1jMLeGaRGn49j9HtjgzMKuxqyA0YJJe6PloJ9PRhHKHqvBCQ+dMTEHmxnHbXPdbZfwB3Qe665HeVVPjAc9Jlxg+dJIFDA0j5XdpF3larRSTvEwQ+q1cN5TH549O6FFWJ4w== |
| AssemblySignatureKeyInfoKeyValueRSAKeyValueExponent: | AQAB |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationHash: | cf3d15206f19a6897536631cee8885e0c4568a26 |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationDescription: | - |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationUrl: | - |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityName: | fritzbox-usb-fernanschluss.application |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityVersion: | 2.3.5.1 |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityPublicKeyToken: | 4b253d3c7789a3f0 |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityLanguage: | de |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityProcessorArchitecture: | x86 |
| AssemblySignatureKeyInfoRelDataLicenseGrantManifestInformationAssemblyIdentityXmlns: | urn:schemas-microsoft-com:asm.v1 |
| AssemblySignatureKeyInfoRelDataLicenseGrantSignedBy: | - |
| AssemblySignatureKeyInfoRelDataLicenseGrantAuthenticodePublisherX509SubjectName: | CN=AVM Computersysteme Vertriebs GmbH, O=AVM Computersysteme Vertriebs GmbH, L=Berlin, C=DE |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureId: | AuthenticodeSignature |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureXmlns: | http://www.w3.org/2000/09/xmldsig# |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoCanonicalizationMethodAlgorithm: | http://www.w3.org/2001/10/xml-exc-c14n# |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoSignatureMethodAlgorithm: | http://www.w3.org/2000/09/xmldsig#rsa-sha1 |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoReferenceUri: | - |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoReferenceTransformsTransformAlgorithm: | http://www.w3.org/2000/09/xmldsig#enveloped-signature |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoReferenceDigestMethodAlgorithm: | http://www.w3.org/2000/09/xmldsig#sha1 |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignedInfoReferenceDigestValue: | kBT0/tPcCDpxOD76qDZiVaruz9I= |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureSignatureValue: | aKP1GaDyduD+B7y3dUHg0eC+a9dzWiJRhACA8Zh0ol0EmuAGCAKW+0gsE7SRmV1ypgiE+ICTwf6OJkjhvg9nizILcZgTvOeON4/IQDliS6jPMGdELmeT4qNsz+DDYgzvzbOyYIEpWLyzvXVYZRWSyxZXIWO07M7jVVtSd1uOU3lwgGI6Tus+wEO5TBRr8WFUAG8NOjJpf8wMQMhCAO8h2mo6Yp2XA1g3K49EeBSsCQwkIOrjzWDYnLJPNA4FmzC3wf82WDJKX/j63ZLos9mYY4VuHx0+mHR9NsZCRS2Ypi+LRKkKjFtgnhqN6SlXb3Tx5Tzz8tx8M4HFC4/OWIf/iA== |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureKeyInfoKeyValueRSAKeyValueModulus: | otkS1lql1dJS/VbBFcnkGZxi8Fc98feoEEyb+qeOWruAHA6IFhxk2bieXAHSepYOzfnaKjp++rZ4eLmyFad1IHODL4/jfyK7oODMPDLEDArpeJO8p1iABeRm3+nBAMmagyZapyMv/CiWjs87++qv9H6CyINl4E997plM8GTKTz1hEp7SGjSUwLW72UKeJsXk3To1A+QLmZb8qeSuE7cG1jMLeGaRGn49j9HtjgzMKuxqyA0YJJe6PloJ9PRhHKHqvBCQ+dMTEHmxnHbXPdbZfwB3Qe665HeVVPjAc9Jlxg+dJIFDA0j5XdpF3larRSTvEwQ+q1cN5TH549O6FFWJ4w== |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureKeyInfoKeyValueRSAKeyValueExponent: | AQAB |
| AssemblySignatureKeyInfoRelDataLicenseIssuerSignatureKeyInfoX509DataX509Certificate: | MIIFOzCCBCOgAwIBAgIQCQq+YJiO4lLi8bMF/dUrGDANBgkqhkiG9w0BAQsFADByMQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3d3cuZGlnaWNlcnQuY29tMTEwLwYDVQQDEyhEaWdpQ2VydCBTSEEyIEFzc3VyZWQgSUQgQ29kZSBTaWduaW5nIENBMB4XDTIwMDcxNTAwMDAwMFoXDTIyMDcyMDEyMDAwMFoweDELMAkGA1UEBhMCREUxDzANBgNVBAcTBkJlcmxpbjErMCkGA1UEChMiQVZNIENvbXB1dGVyc3lzdGVtZSBWZXJ0cmllYnMgR21iSDErMCkGA1UEAxMiQVZNIENvbXB1dGVyc3lzdGVtZSBWZXJ0cmllYnMgR21iSDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKLZEtZapdXSUv1WwRXJ5BmcYvBXPfH3qBBMm/qnjlq7gBwOiBYcZNm4nlwB0nqWDs352io6fvq2eHi5shWndSBzgy+P438iu6DgzDwyxAwK6XiTvKdYgAXkZt/pwQDJmoMmWqcjL/wolo7PO/vqr/R+gsiDZeBPfe6ZTPBkyk89YRKe0ho0lMC1u9lCnibF5N06NQPkC5mW/KnkrhO3BtYzC3hmkRp+PY/R7Y4MzCrsasgNGCSXuj5aCfT0YRyh6rwQkPnTExB5sZx21z3W2X8Ad0HuuuR3lVT4wHPSZcYPnSSBQwNI+V3aRd5Wq0Uk7xMEPqtXDeUx+ePTuhRVieMCAwEAAaOCAcUwggHBMB8GA1UdIwQYMBaAFFrEuXsqCqOl6nEDwGD5LfZldQ5YMB0GA1UdDgQWBBTge6SOLJZ4wT7MTeNTHXU9IJdYtzAOBgNVHQ8BAf8EBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwMwdwYDVR0fBHAwbjA1oDOgMYYvaHR0cDovL2NybDMuZGlnaWNlcnQuY29tL3NoYTItYXNzdXJlZC1jcy1nMS5jcmwwNaAzoDGGL2h0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9zaGEyLWFzc3VyZWQtY3MtZzEuY3JsMEwGA1UdIARFMEMwNwYJYIZIAYb9bAMBMCowKAYIKwYBBQUHAgEWHGh0dHBzOi8vd3d3LmRpZ2ljZXJ0LmNvbS9DUFMwCAYGZ4EMAQQBMIGEBggrBgEFBQcBAQR4MHYwJAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBOBggrBgEFBQcwAoZCaHR0cDovL2NhY2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0U0hBMkFzc3VyZWRJRENvZGVTaWduaW5nQ0EuY3J0MAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcNAQELBQADggEBAHiUuRbAwfuXknRwNTgqmzz93BBOA57dZh3L06eTtxRFqWguja/IlR0IDmHuKXn7+K78hQlELNCP7iPRQu2Y4nKxMOg6EGBiTYCsc8vu0HOPWSE8lpzaHVgp5ijEmR0odkOOdFKTOLyyXiYS/PaJspHFXoHomVI+wJ6RtKN+xL8mVY8KsVrkrroC7YswH9uRNY6E5BVbrMxDirQ2ewfJ4VKcGulCWumpJ06Meh5cCdNQRUEguhaK9xkp6o6kXvxocmhgfguNV5glRbFVPi/ABYCn5CXLutO+ReSYFEPiOq1cdLW8GfFnW7ogAfIKE5yefsofXaQoDEMCUxsd44t4KIA= |
Total processes
182
Monitored processes
82
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
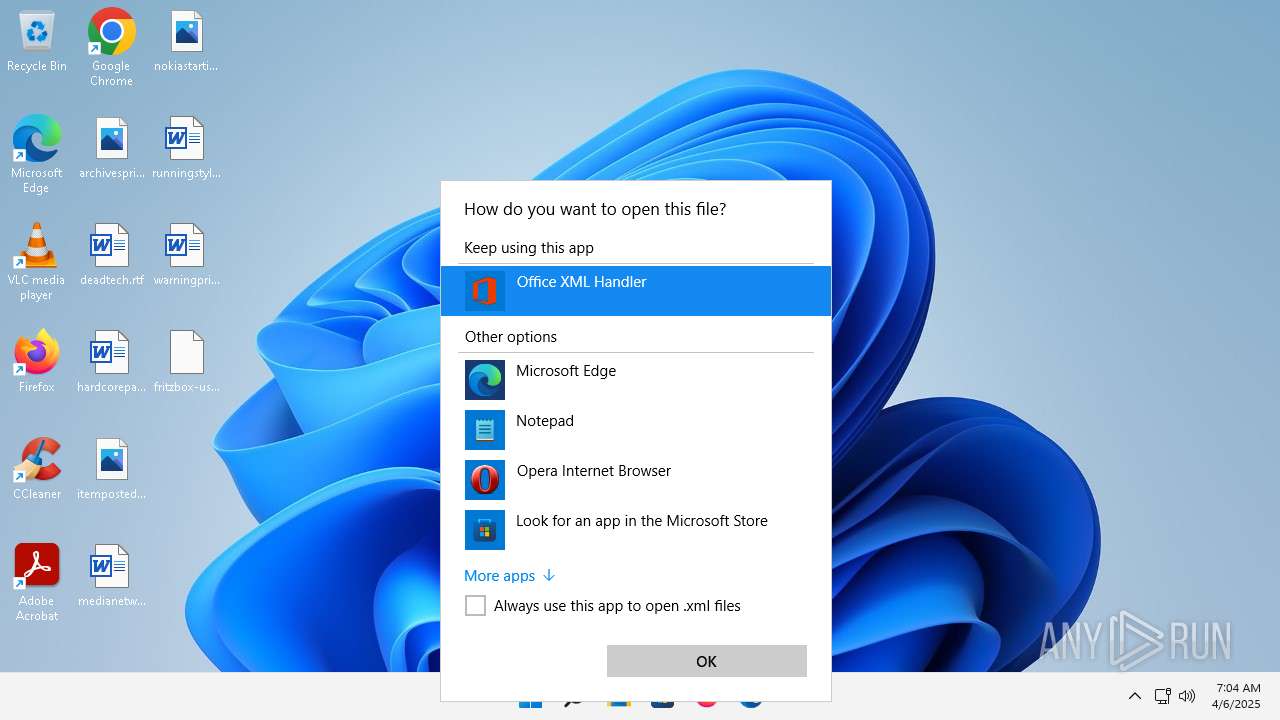
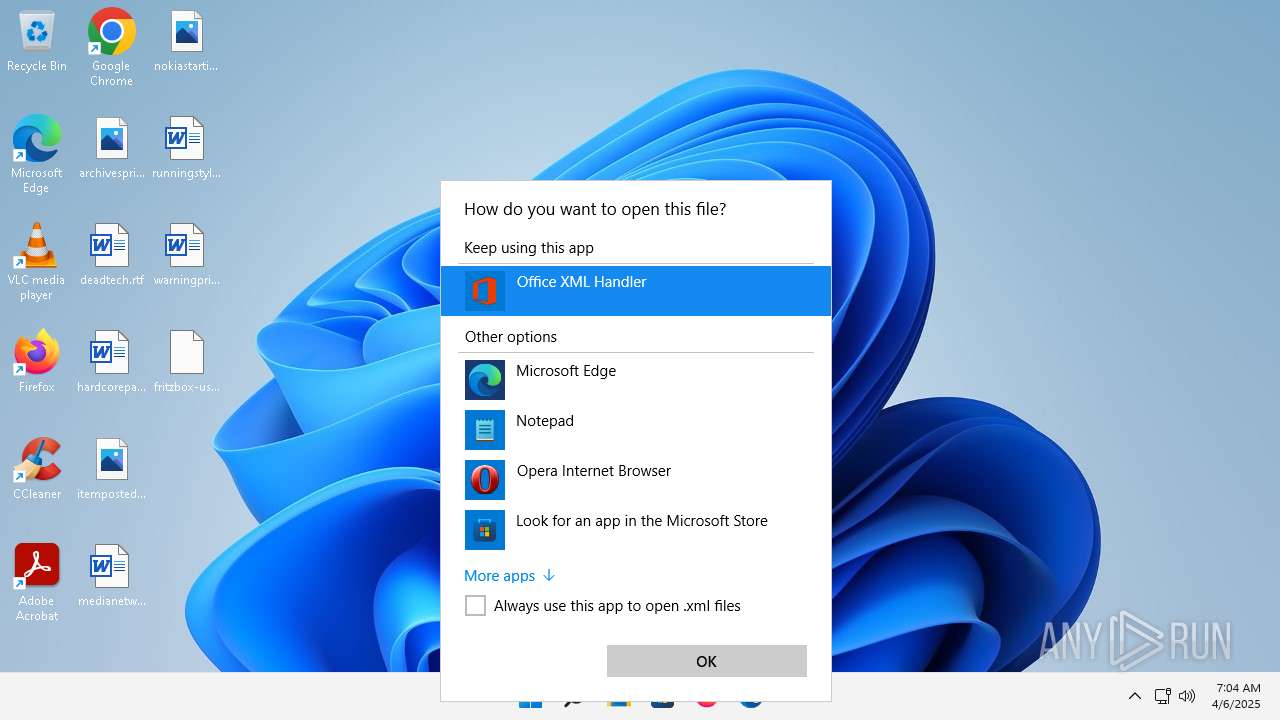
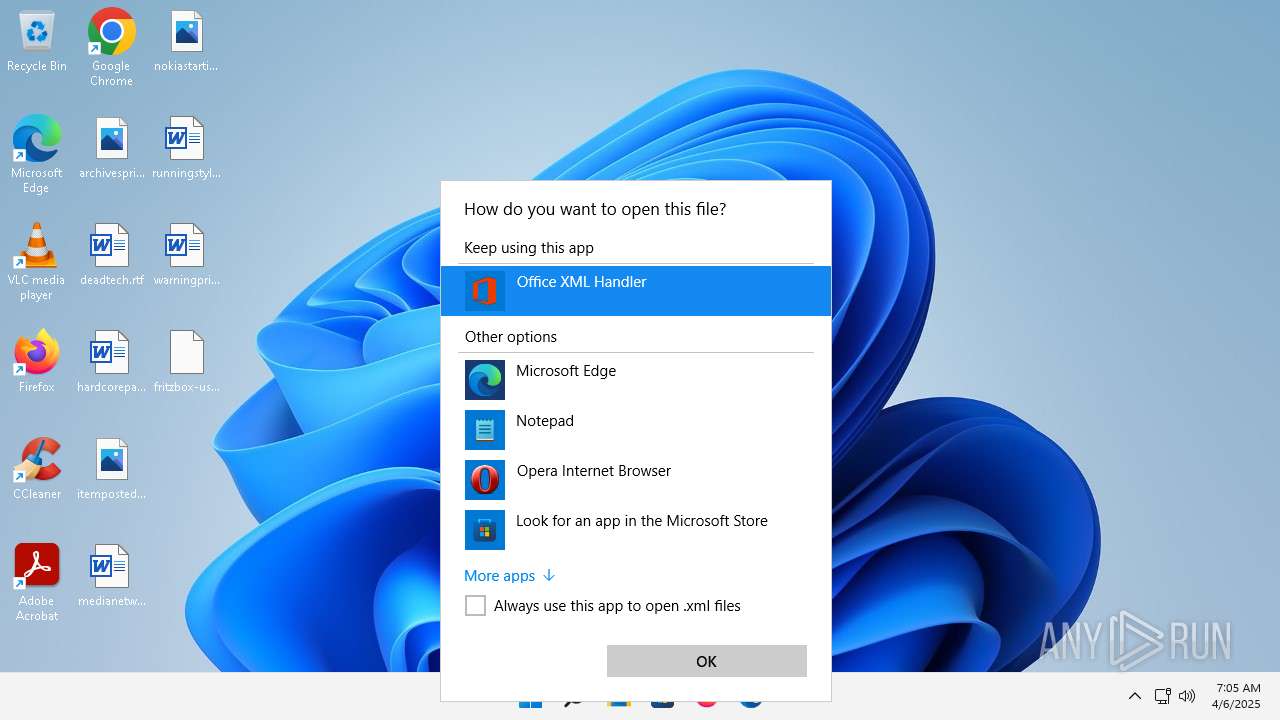
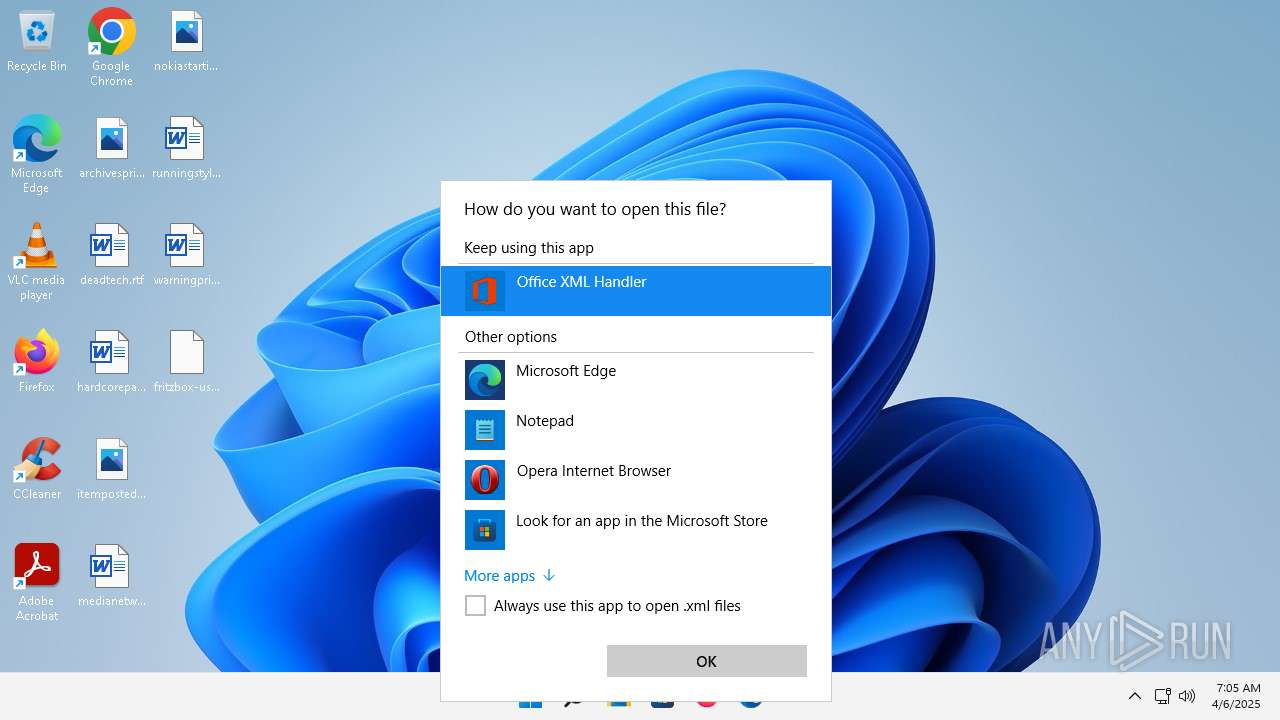
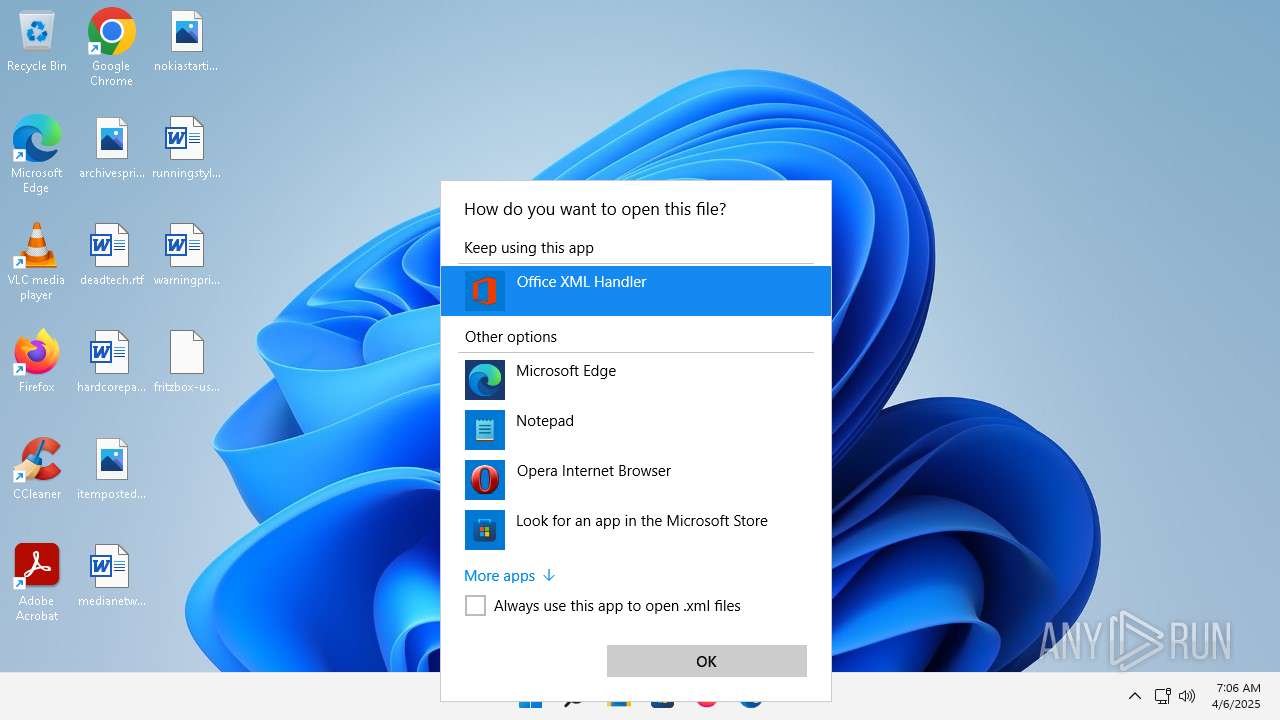
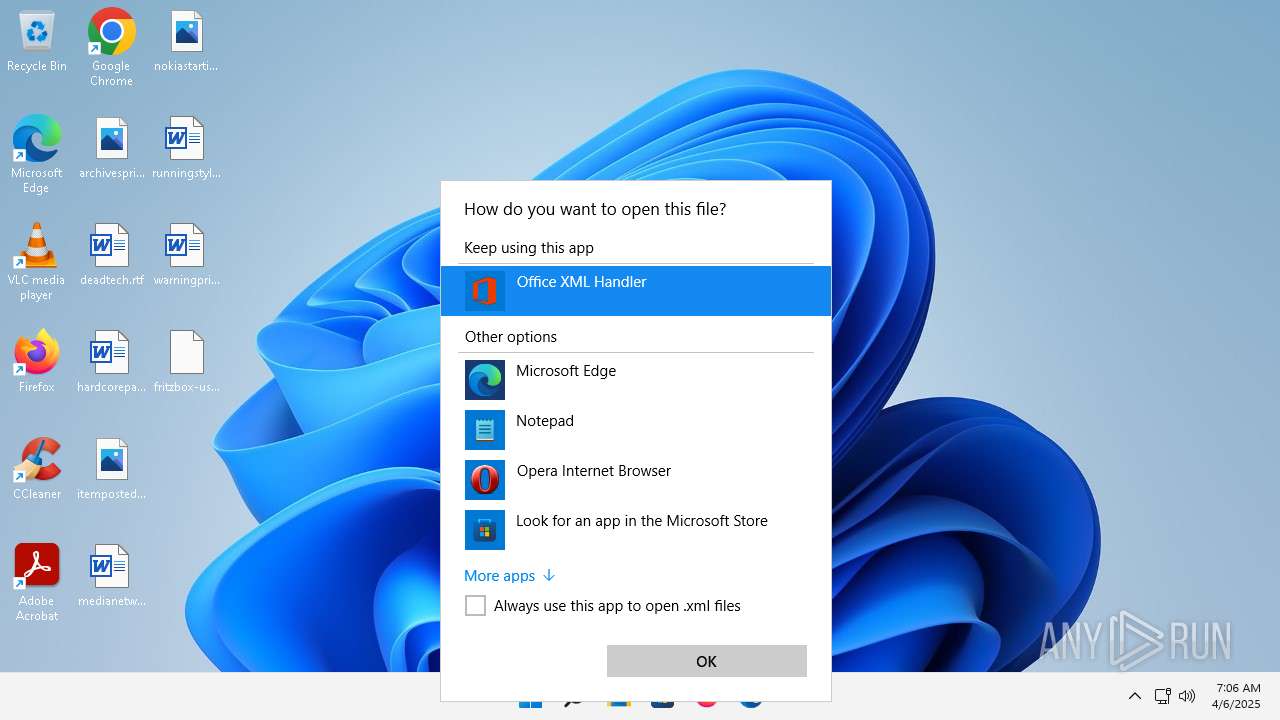
| 356 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\fritzbox-usb-fernanschluss.application.xml" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\MSOXMLED.EXE | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Office XML Handler Exit code: 0 Version: 16.0.16626.20118 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\fritzbox-usb-fernanschluss.application.xml" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\MSOXMLED.EXE | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Office XML Handler Exit code: 0 Version: 16.0.16626.20118 Modules
| |||||||||||||||
| 508 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\fritzbox-usb-fernanschluss.application.xml" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\MSOXMLED.EXE | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Office XML Handler Exit code: 0 Version: 16.0.16626.20118 Modules
| |||||||||||||||
| 832 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\fritzbox-usb-fernanschluss.application.xml" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\MSOXMLED.EXE | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Office XML Handler Exit code: 0 Version: 16.0.16626.20118 Modules
| |||||||||||||||
| 952 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1404 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\fritzbox-usb-fernanschluss.application.xml" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\MSOXMLED.EXE | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Office XML Handler Exit code: 0 Version: 16.0.16626.20118 Modules
| |||||||||||||||
| 1516 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
111 162
Read events
110 385
Write events
777
Delete events
0
Modification events
| (PID) Process: | (4812) MSOXMLED.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4812) MSOXMLED.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4812) MSOXMLED.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4812) MSOXMLED.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.xml\OpenWithProgids |
| Operation: | write | Name: | xmlfile |
Value: | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.xml\OpenWithProgids |
| Operation: | write | Name: | xmlfile |
Value: | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | Opera.HTML_.xml |
Value: 0 | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2864) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
14
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1352 | svchost.exe | GET | 200 | 2.21.20.155:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 104.102.63.189:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
5336 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2be8f428262e73fa | unknown | — | — | whitelisted |
3156 | smartscreen.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b96910a8d575f9cb | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b5c209eb39f9a373 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?74f19306e9a7f92f | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?ae0cec35f73e7201 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e0b4dd42efe063e | unknown | — | — | whitelisted |
— | — | POST | 200 | 172.205.25.163:443 | https://checkappexec.microsoft.com/windows/shell/actions | unknown | binary | 182 b | whitelisted |
— | — | GET | 200 | 104.102.63.189:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | binary | 55 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
1352 | svchost.exe | 2.21.20.155:80 | — | Akamai International B.V. | DE | unknown |
3156 | smartscreen.exe | 4.231.66.184:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3156 | smartscreen.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
5336 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5336 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
4824 | svchost.exe | 104.102.63.189:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
2768 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2988 | OfficeClickToRun.exe | 52.168.112.67:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |