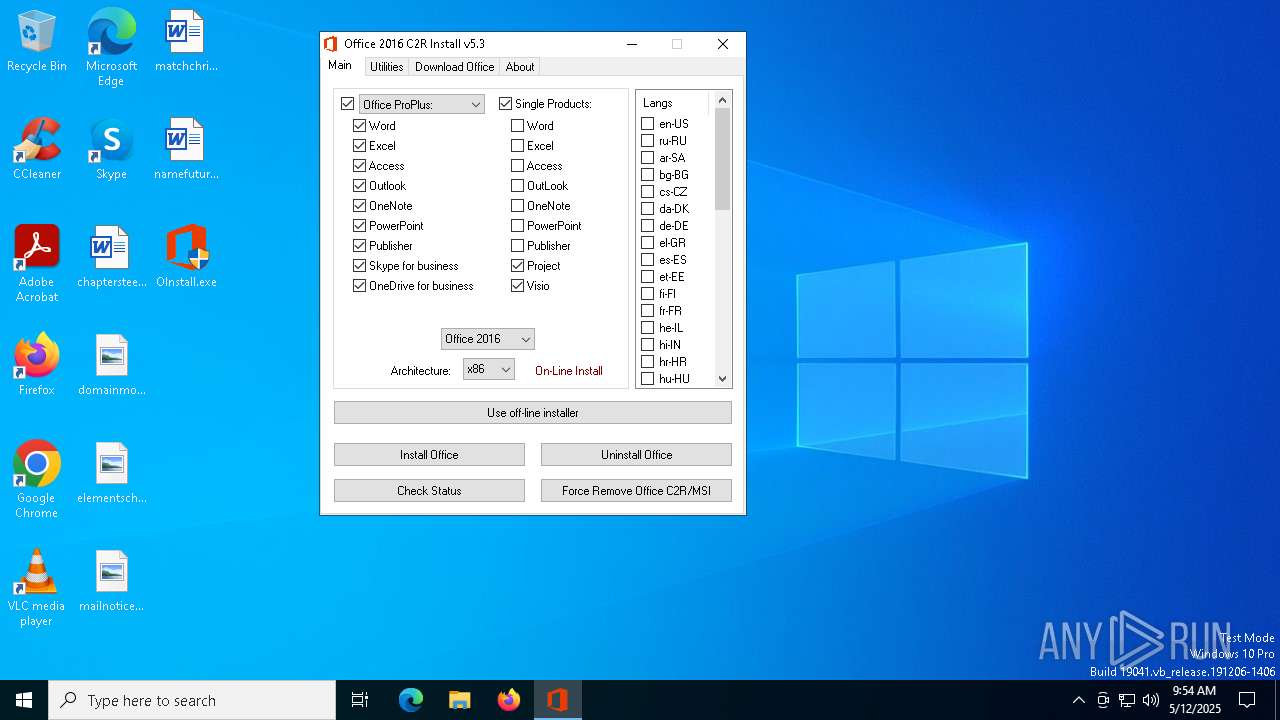
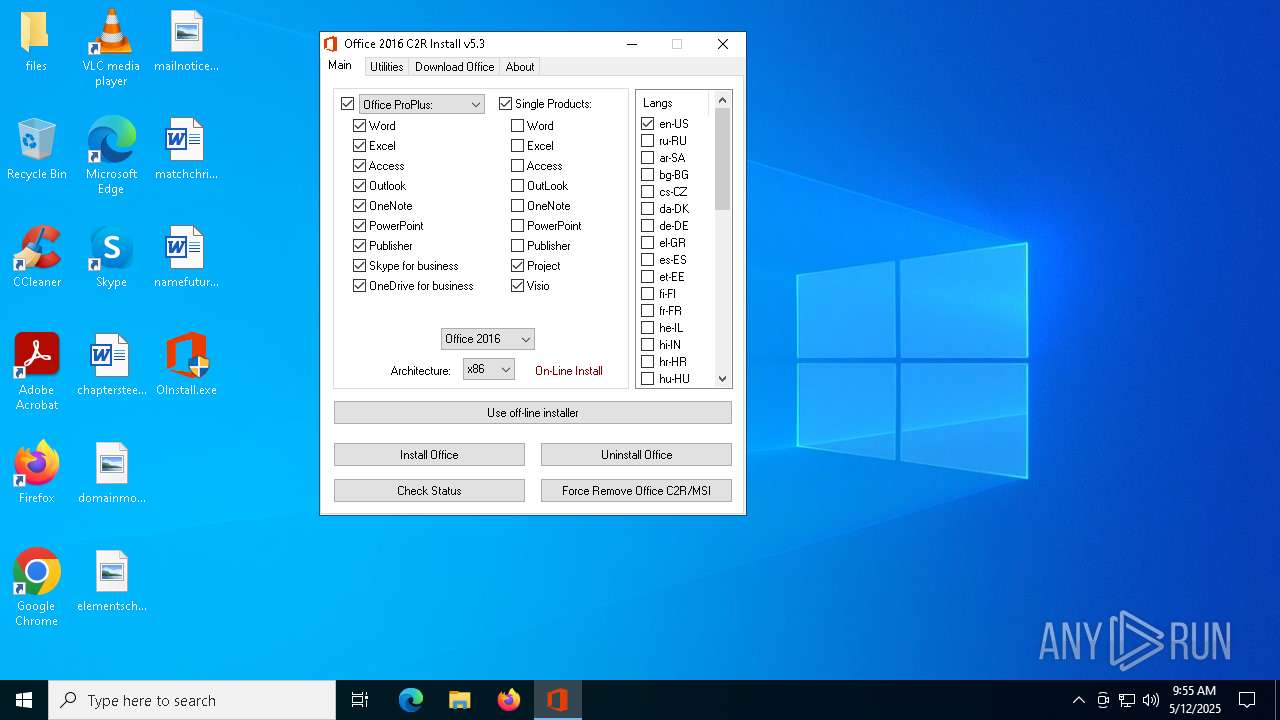
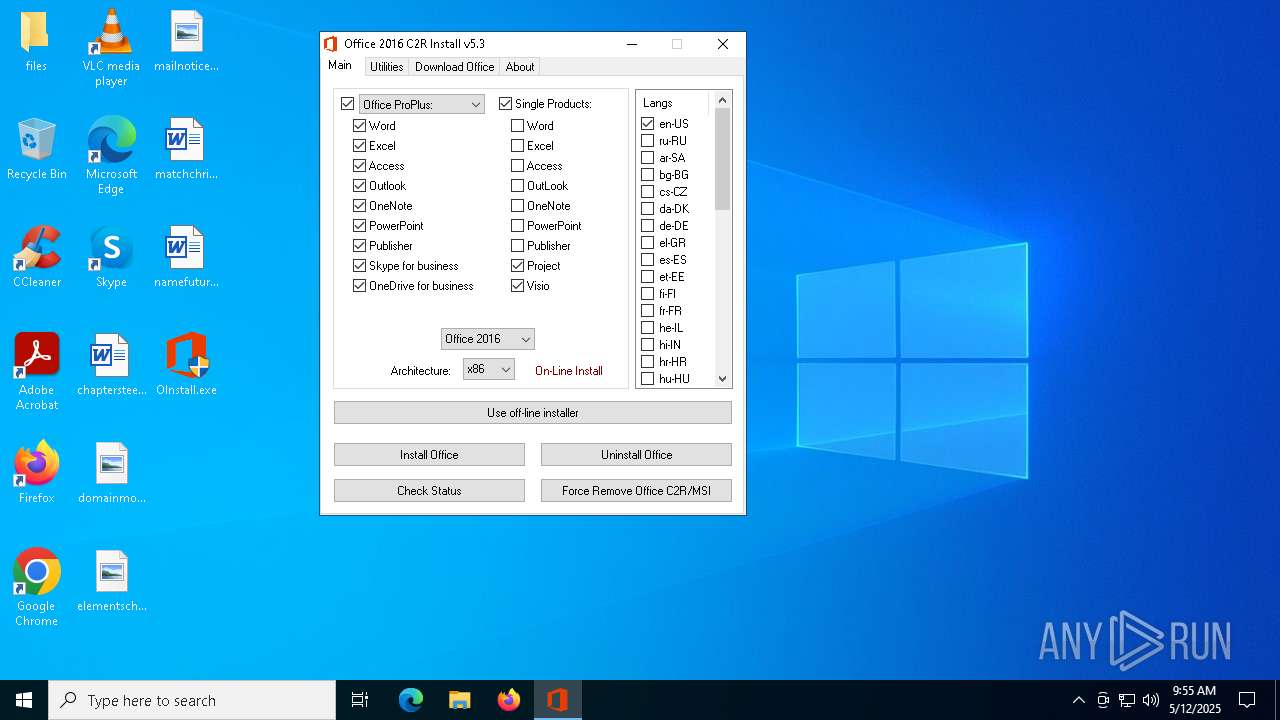
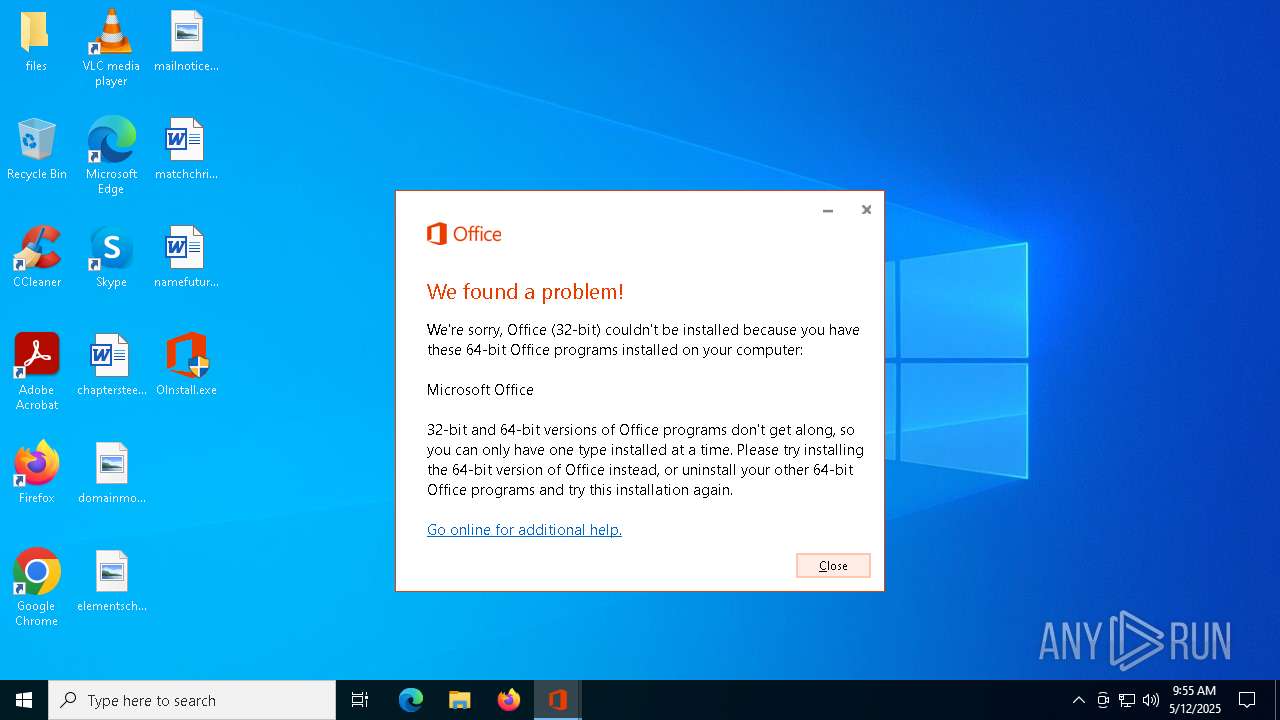
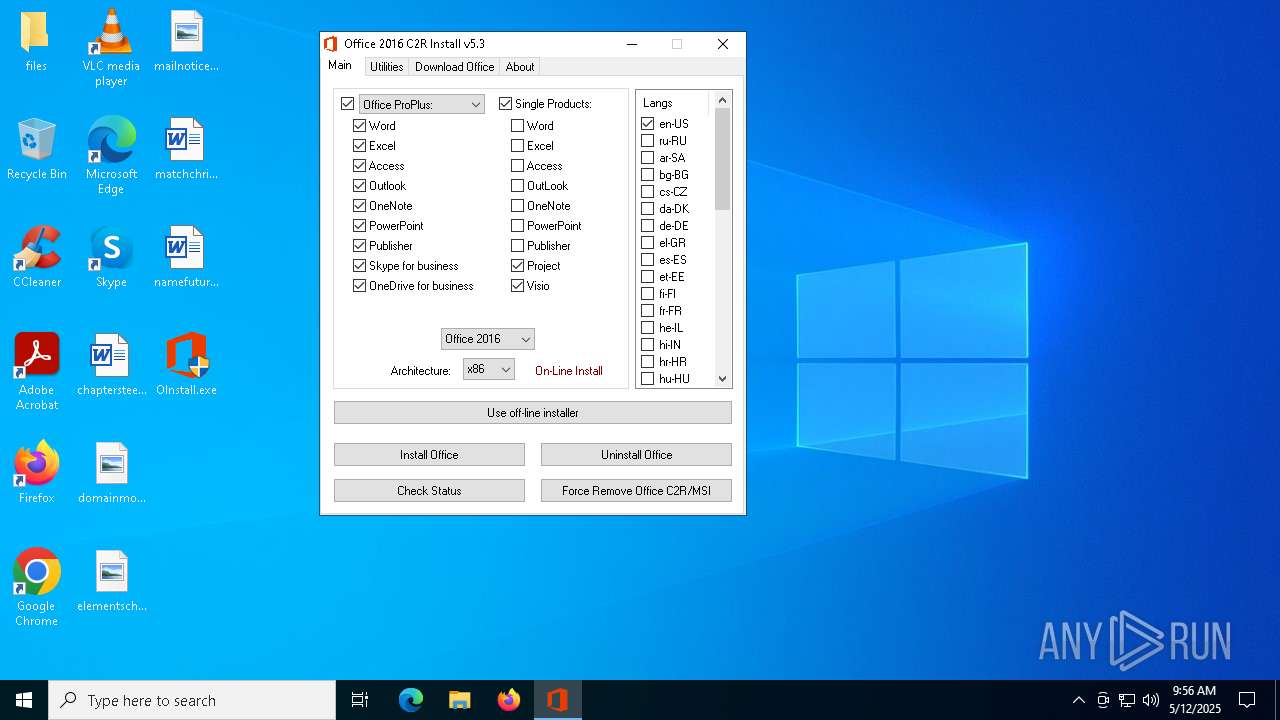
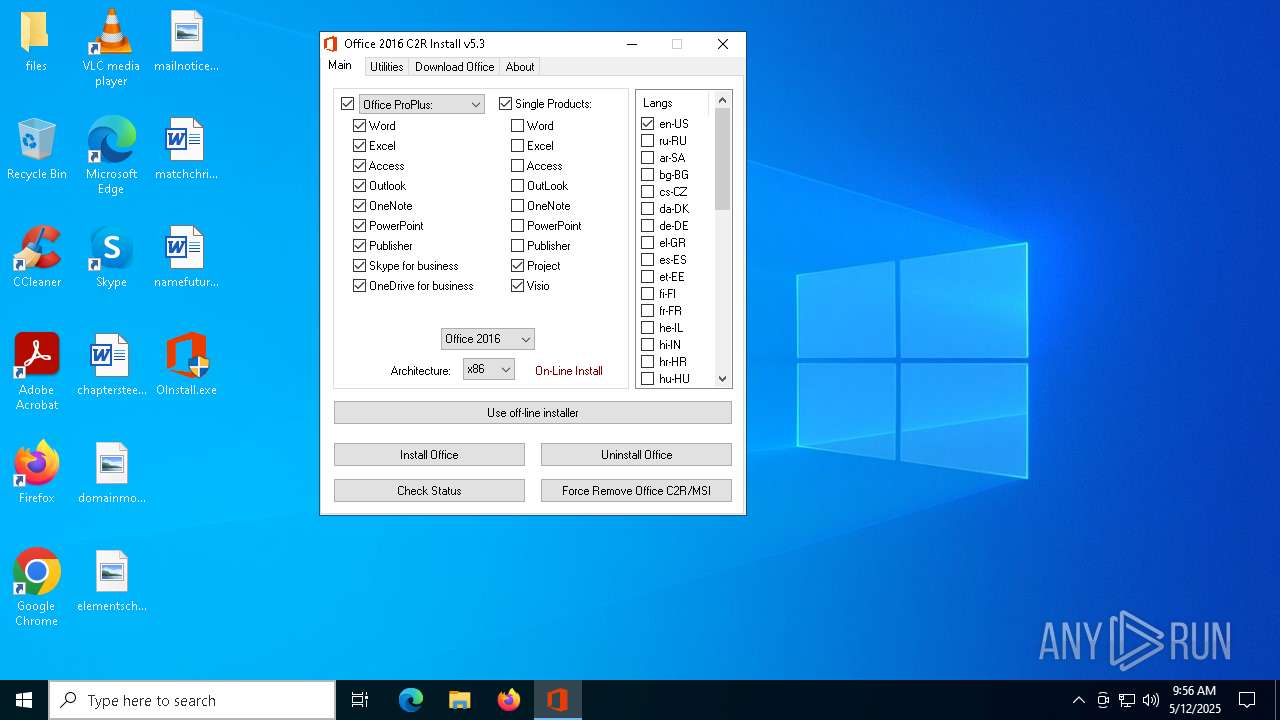
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/3ec6183e-e74c-4b72-9d13-a194e419577b |
| Verdict: | Malicious activity |
| Analysis date: | May 12, 2025, 09:54:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 7E58CAA6E6C089C1EA4FA69528B4433D |
| SHA1: | 4545993D5464A5270657F4A4009FE41CBDC758C5 |
| SHA256: | 4B1135F82C77D66CA0613988CF8C205F14D8A69F684A238CD51A4D7D3B058CAA |
| SSDEEP: | 98304:850t7G+WFwLSD9E0B819rIiPxhawKUrIxKjzmc9E035VkTv9E0somRnJTYMAezxN:Eq |
MALICIOUS
Executing a file with an untrusted certificate
- OInstall.exe (PID: 7200)
- OInstall.exe (PID: 5072)
- setup16.exe (PID: 8132)
SUSPICIOUS
Process drops legitimate windows executable
- OInstall.exe (PID: 7200)
- files.dat (PID: 7388)
Executable content was dropped or overwritten
- OInstall.exe (PID: 7200)
- files.dat (PID: 7388)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 7200)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 7200)
Starts application with an unusual extension
- cmd.exe (PID: 7332)
The process drops C-runtime libraries
- files.dat (PID: 7388)
Starts a Microsoft application from unusual location
- setup16.exe (PID: 8132)
Reads security settings of Internet Explorer
- setup16.exe (PID: 8132)
Searches for installed software
- setup16.exe (PID: 8132)
INFO
Checks supported languages
- OInstall.exe (PID: 7200)
- files.dat (PID: 7388)
- setup16.exe (PID: 8132)
Reads Environment values
- OInstall.exe (PID: 7200)
Reads the computer name
- OInstall.exe (PID: 7200)
- setup16.exe (PID: 8132)
The sample compiled with english language support
- OInstall.exe (PID: 7200)
- files.dat (PID: 7388)
UPX packer has been detected
- OInstall.exe (PID: 7200)
Process checks computer location settings
- setup16.exe (PID: 8132)
Reads Microsoft Office registry keys
- setup16.exe (PID: 8132)
Reads the software policy settings
- setup16.exe (PID: 8132)
- slui.exe (PID: 5392)
Checks proxy server information
- setup16.exe (PID: 8132)
- slui.exe (PID: 5392)
Create files in a temporary directory
- setup16.exe (PID: 8132)
Reads the machine GUID from the registry
- setup16.exe (PID: 8132)
Creates files or folders in the user directory
- setup16.exe (PID: 8132)
Reads CPU info
- setup16.exe (PID: 8132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (24) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .exe | | | UPX compressed Win32 Executable (20.8) |
| .exe | | | Win32 EXE Yoda's Crypter (20.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:29 12:45:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 719360 |
| InitializedDataSize: | 8532992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.3.0.0 |
| ProductVersionNumber: | 5.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
144
Monitored processes
10
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5072 | "C:\Users\admin\Desktop\OInstall.exe" | C:\Users\admin\Desktop\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5392 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7200 | "C:\Users\admin\Desktop\OInstall.exe" | C:\Users\admin\Desktop\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7240 | "C:\WINDOWS\Sysnative\cmd.exe" /D /c copy C:\WINDOWS\system32\Tasks\OInstall "\OInstall.tmp" /Y | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7248 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7332 | "C:\WINDOWS\Sysnative\cmd.exe" /D /c files.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7388 | files.dat -y -pkmsauto | C:\Users\admin\Desktop\files\files.dat | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 8132 | "C:\Users\admin\Desktop\files\Setup16.exe" /configure Configure.xml | C:\Users\admin\Desktop\files\setup16.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Exit code: 0 Version: 16.0.6831.5775 Modules
| |||||||||||||||
| 8148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | setup16.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 889
Read events
4 876
Write events
9
Delete events
4
Modification events
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Registration |
| Operation: | write | Name: | AcceptAllEulas |
Value: 1 | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Registration\DESKTOP-JGLLJLD |
| Operation: | write | Name: | none.AttemptGetKey |
Value: 1 | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesLastModified |
| Operation: | write | Name: | setup16.exe_queried |
Value: 96C5216800000000 | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesLastModified |
| Operation: | write | Name: | setup16.exe |
Value: Mon, 12 May 2025 09:55:34 GMT | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\setup16.exe |
| Operation: | write | Name: | RulesEndpoint |
Value: https://nexusrules.officeapps.live.com/nexus/rules?Application=C2R.exe&Version=16.0.6831.5775&ClientId={D61AB268-C26A-439D-BB15-2A0DEDFCA6A3}&OSEnvironment=10&MsoAppId=37&AudienceName=Unknown&AudienceGroup=Unknown&AppVersion=16.0.6831.5775& | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\setup16.exe |
| Operation: | delete value | Name: | RulesEndpoint |
Value: https://nexusrules.officeapps.live.com/nexus/rules?Application=C2R.exe&Version=16.0.6831.5775&ClientId={D61AB268-C26A-439D-BB15-2A0DEDFCA6A3}&OSEnvironment=10&MsoAppId=37&AudienceName=Unknown&AudienceGroup=Unknown&AppVersion=16.0.6831.5775& | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\setup16.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\setup16.exe\ULSMonitor |
| Operation: | write | Name: | ULSTagIds0 |
Value: 5601374,5601379,5804129,7202269,17102418,7168707,595174593,17962391,595174594,17962392,593359442,593359441,22929429 | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesEngineThrottling |
| Operation: | write | Name: | SpikeFactor |
Value: 12 | |||
| (PID) Process: | (8132) setup16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry |
| Operation: | write | Name: | ULSQueueSize |
Value: 20480 | |||
Executable files
6
Suspicious files
14
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7200 | OInstall.exe | C:\Users\admin\Desktop\files\setup16.exe | executable | |
MD5:C3CB16674CA1787AD44552766D93216F | SHA256:3EAA729D17BD14833B8E9B720F67F09C35735E13A4814E56B9DB0FD402629623 | |||
| 8132 | setup16.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:6872FAE8288DB34207D9E7EE350157F4 | SHA256:50795B027E2BC566D3B7ACB89913F8EFD23B70615C9DB9BF5B23323AD3132A7D | |||
| 7200 | OInstall.exe | C:\Users\admin\Desktop\files\files.dat | executable | |
MD5:BB81E763AB0E673B3C1AF2FEA2586A9A | SHA256:4D45C64B244C8F997358635C3B5CB9A65743FAC473D65C455D3BA8A25E50D5F9 | |||
| 7388 | files.dat | C:\Users\admin\Desktop\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 7388 | files.dat | C:\Users\admin\Desktop\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 7388 | files.dat | C:\Users\admin\Desktop\files\Configure.xml | text | |
MD5:AC6BE84084E31DBB0E08D188B6C86EC8 | SHA256:1879F7DE537C2AA70292C61EBEF9C6477D36E25B2E6A639E318B159E0A22B0FC | |||
| 7388 | files.dat | C:\Users\admin\Desktop\files\x86\cleanospp.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 8132 | setup16.exe | C:\Users\admin\AppData\Local\Temp\OfficeC2R614B8086-41CA-437B-8FC6-3E8FE9B62795\v32.cab | compressed | |
MD5:753724165DE60BD32C59A403062923B2 | SHA256:BA25514A2353C1FB8AAE0A03588D3C4859958E59BE06DAB32E8E2B5ABB63DA13 | |||
| 8132 | setup16.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:32D8FF85DEA1D0B2DC418F4708E0E85E | SHA256:470C6896C11CC566E4442DDD1F597A6A8E74FB36D1A1C4490D7A342C4AD674B1 | |||
| 8132 | setup16.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7396C420A8E1BC1DA97F1AF0D10BAD21 | binary | |
MD5:E07178901A4EAAC2816BB238EC3A80DB | SHA256:EEBD04C1272661E1091084108083CE44F7C961013791892D866B2F92EE3DEDA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
28
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8132 | setup16.exe | HEAD | 200 | 23.48.23.48:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | — | — | whitelisted |
8132 | setup16.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
8132 | setup16.exe | GET | 200 | 23.48.23.48:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | — | — | whitelisted |
8132 | setup16.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
8132 | setup16.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
8132 | setup16.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7988 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7988 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |