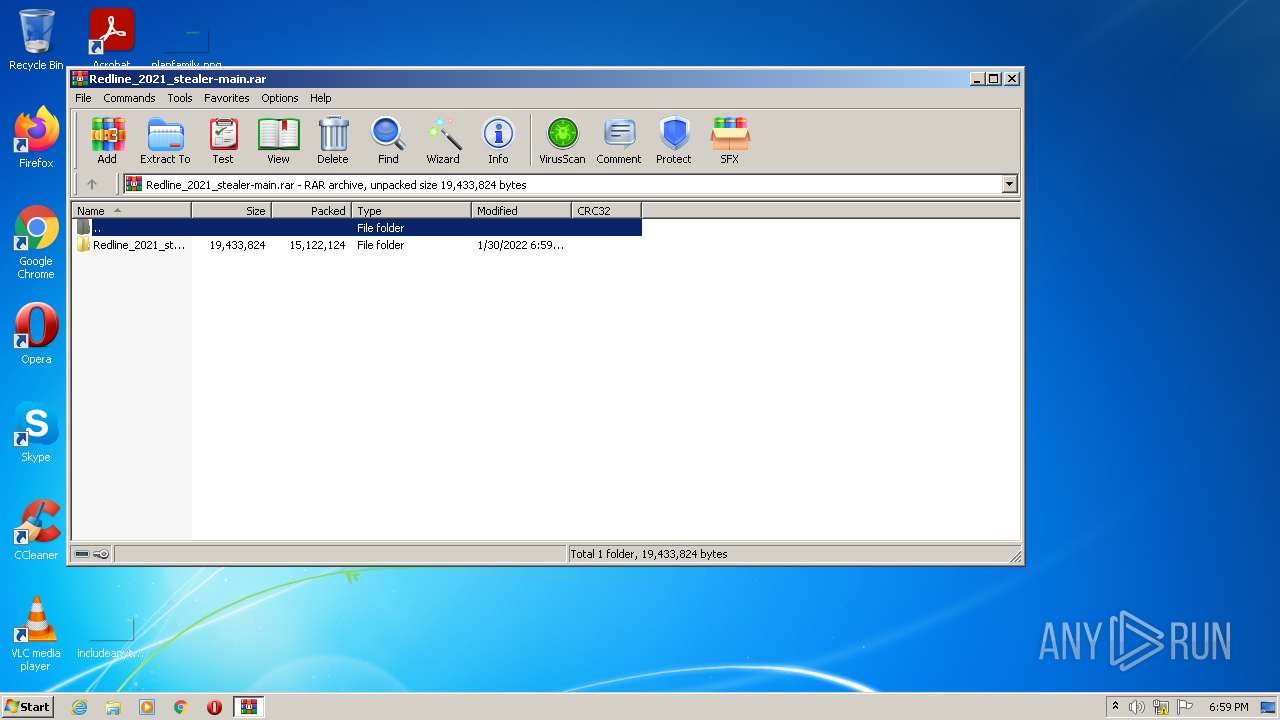
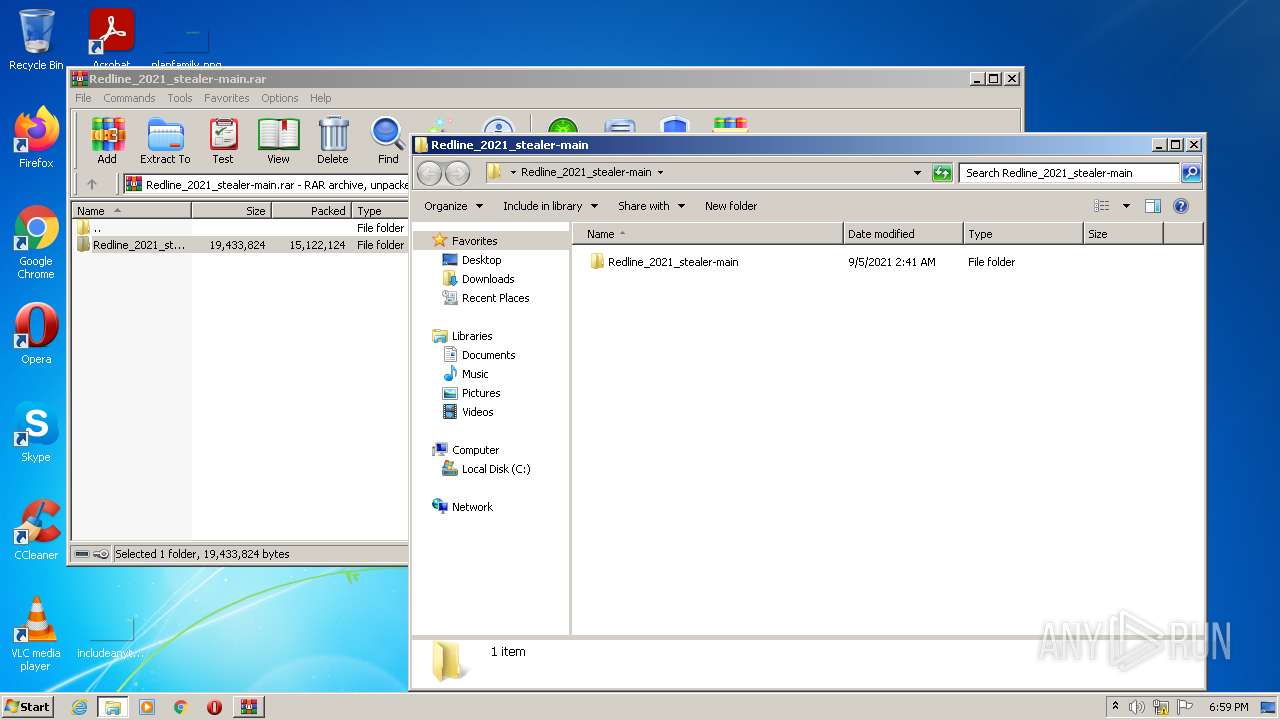
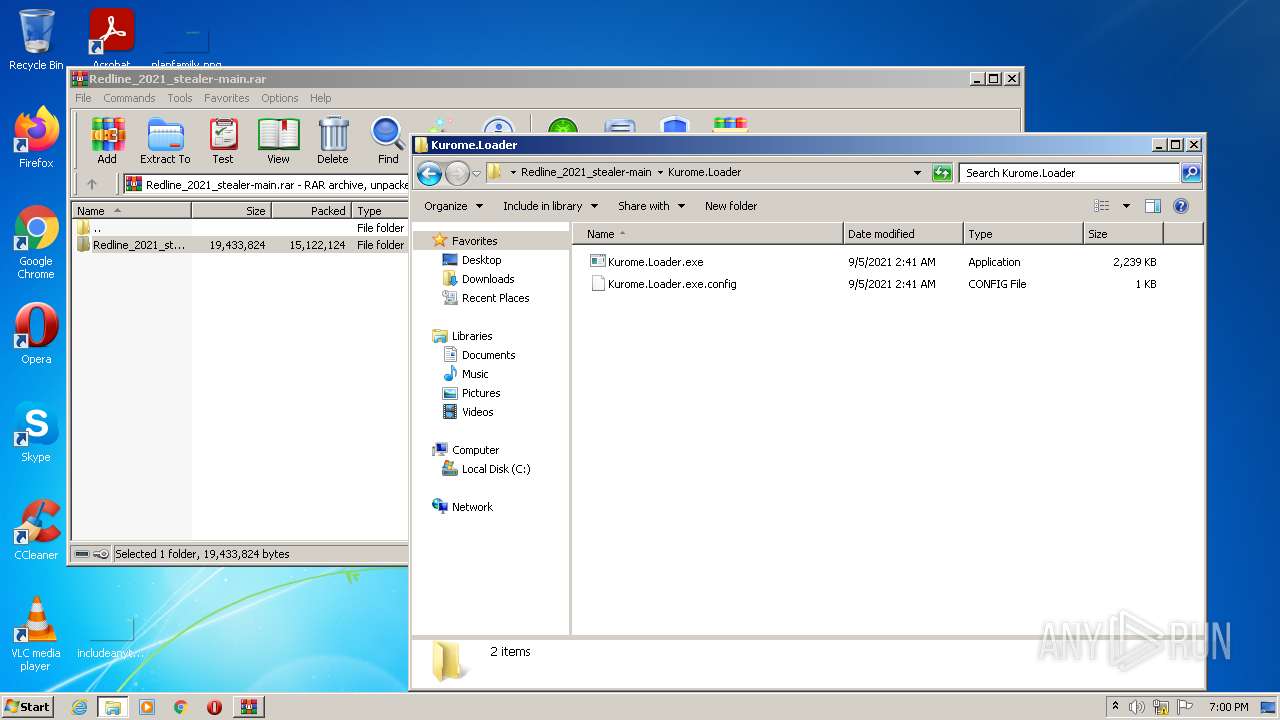
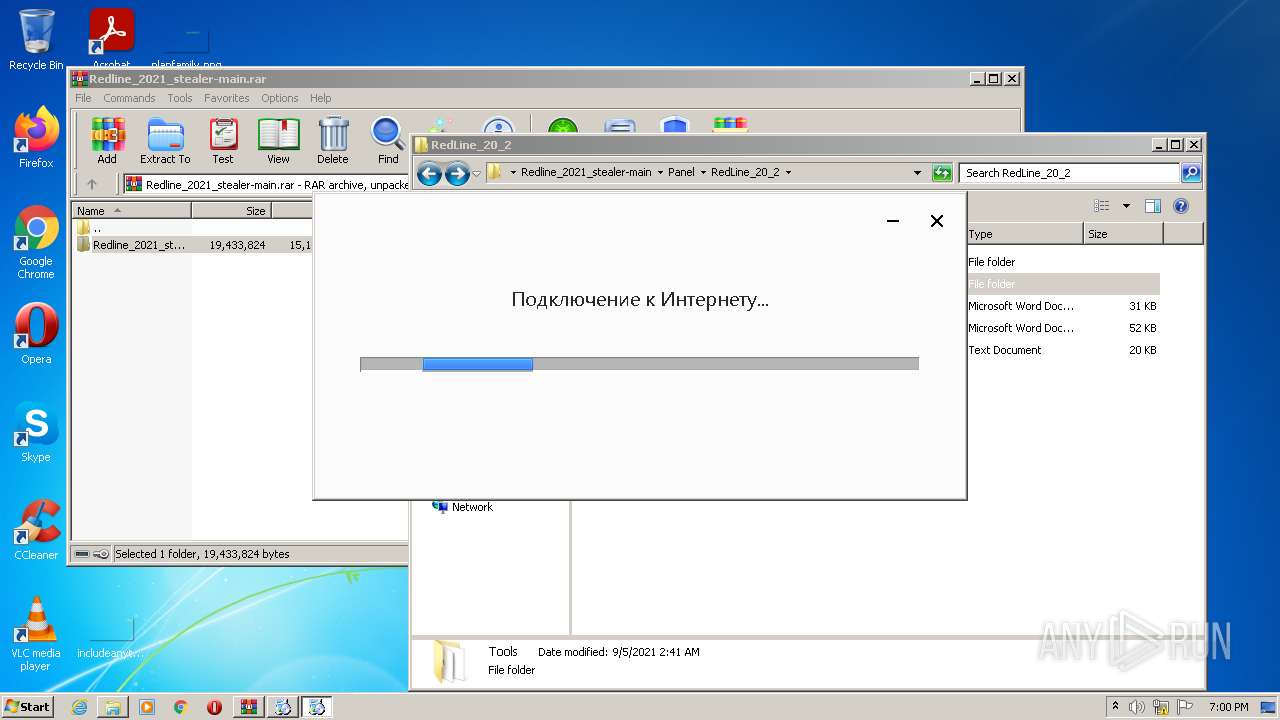
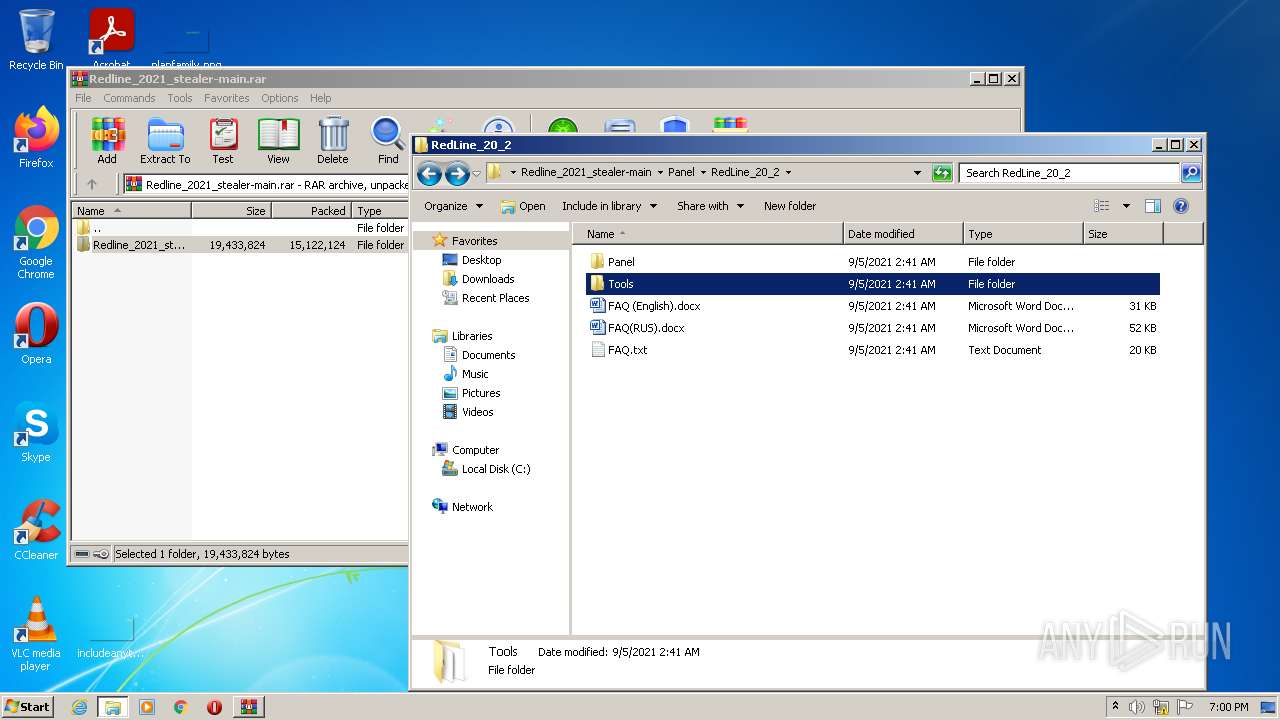
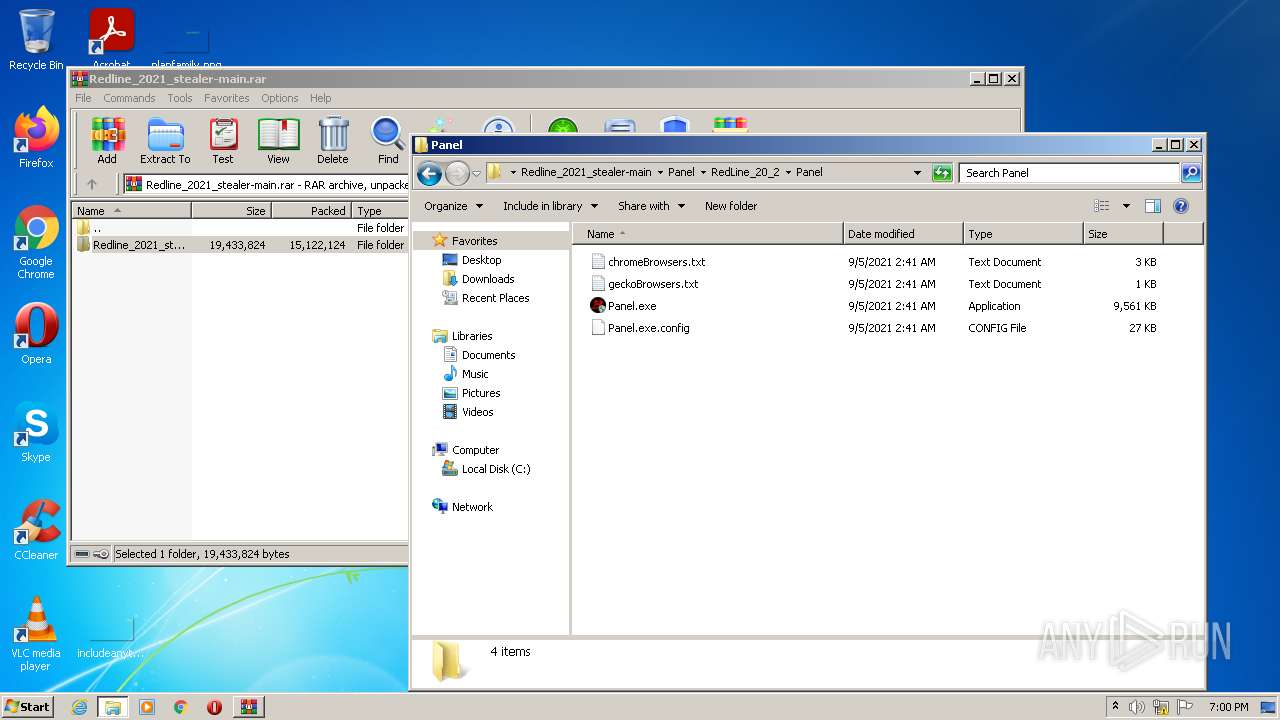
| File name: | Redline_2021_stealer-main.rar |
| Full analysis: | https://app.any.run/tasks/0c7adbcd-2be8-4dc9-94e9-1b893d779395 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2022, 18:59:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5834A2F9DD05A8FBF390B133D618CF77 |
| SHA1: | 1F9DEC6D14B58878024C5360E4A3F013CD019866 |
| SHA256: | 4B0BCA466528875369A4934E92A1156F68F4919A0B99872788B65A0315881873 |
| SSDEEP: | 393216:VoIxpiFTnpx1eJ/p4kZZc9RosoKm6NMaEcqpHVtckzM:ZpGnv0JptZc9RoymgMaEcqeJ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3032)
- Explorer.EXE (PID: 1656)
- GoogleUpdate.exe (PID: 2676)
- GoogleUpdate.exe (PID: 2168)
Application was dropped or rewritten from another process
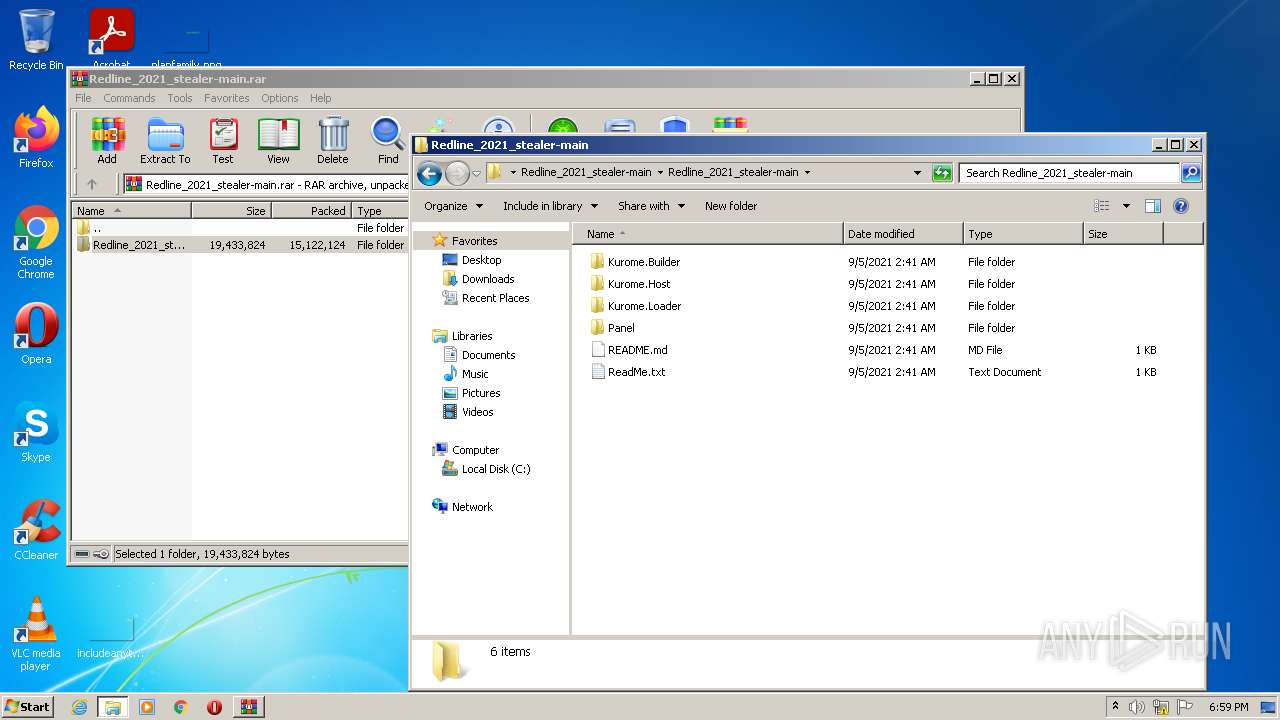
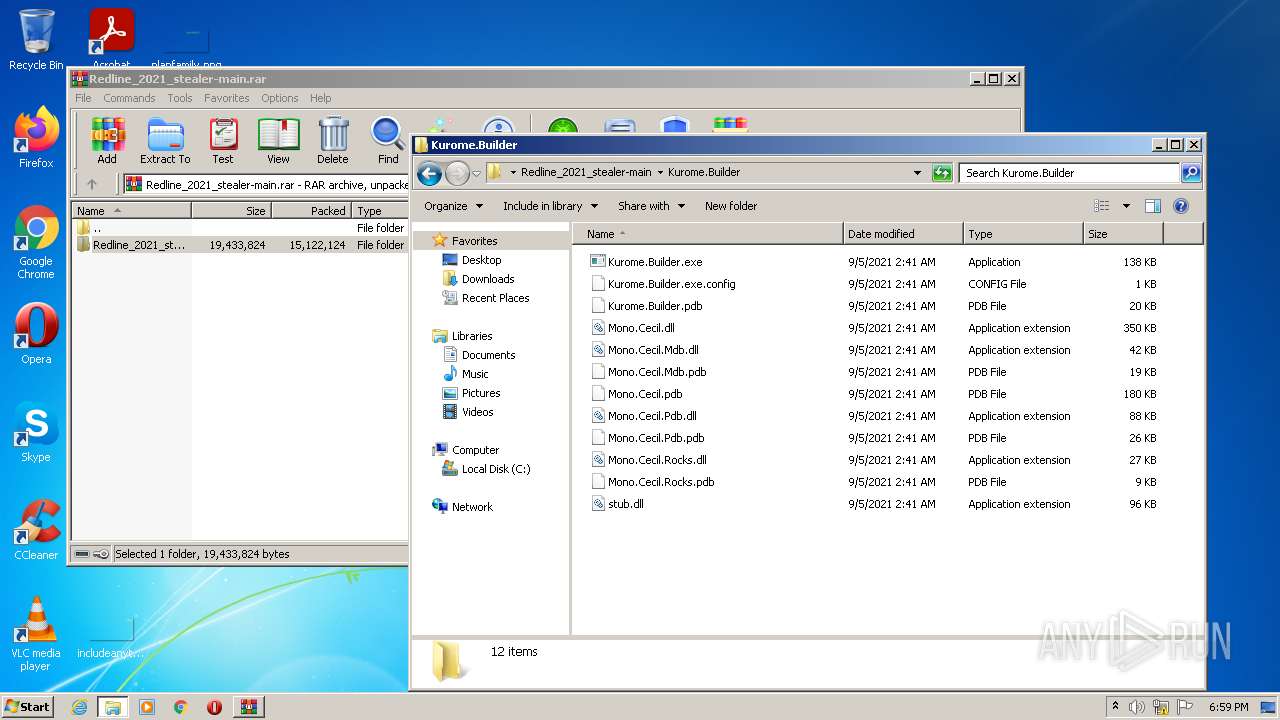
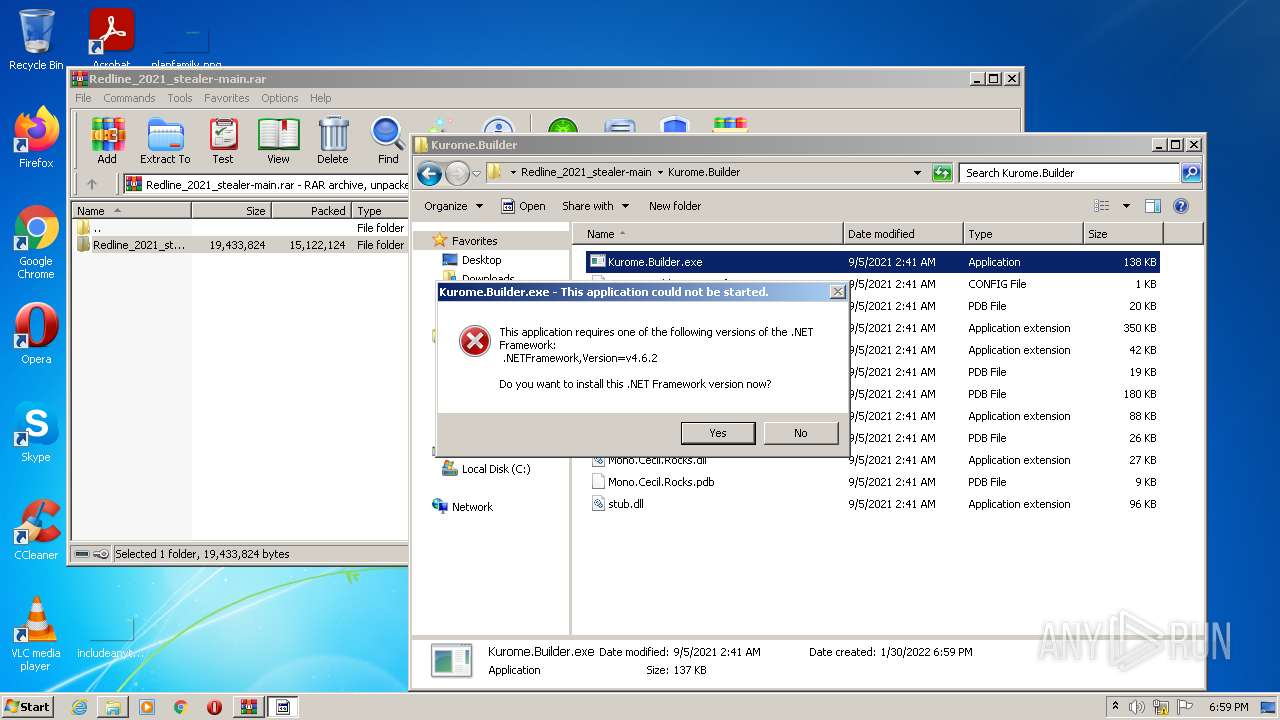
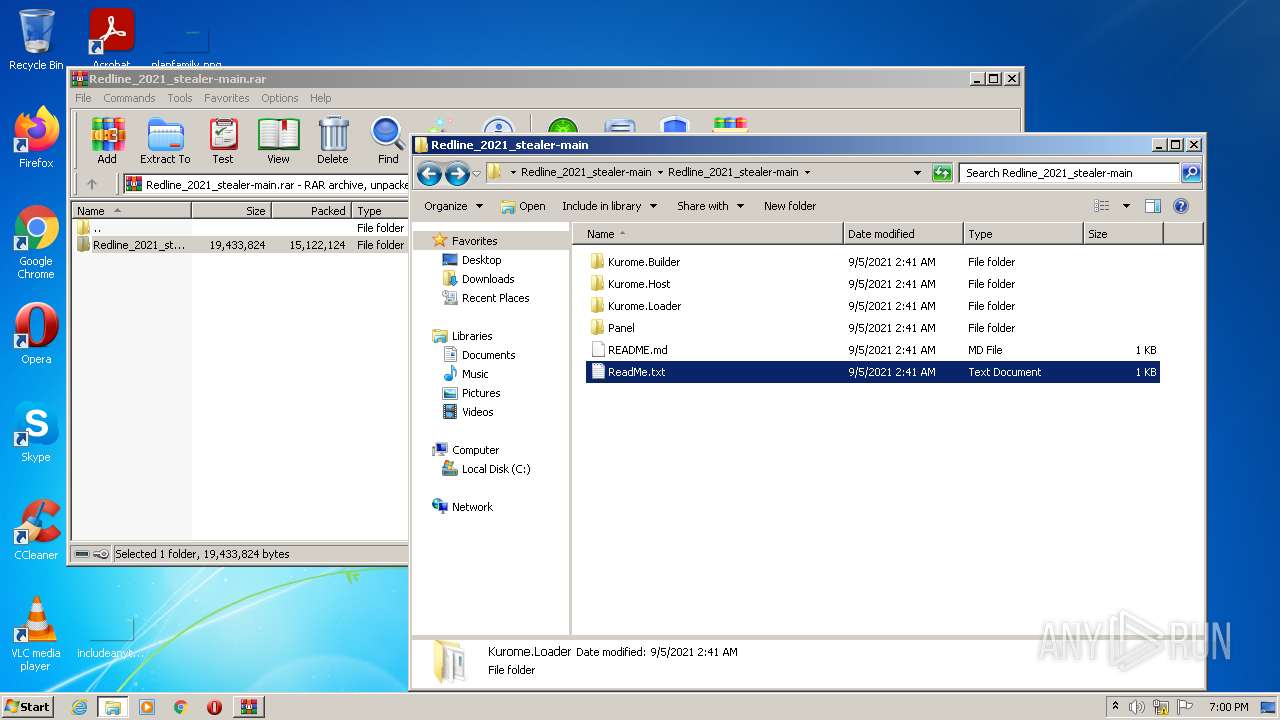
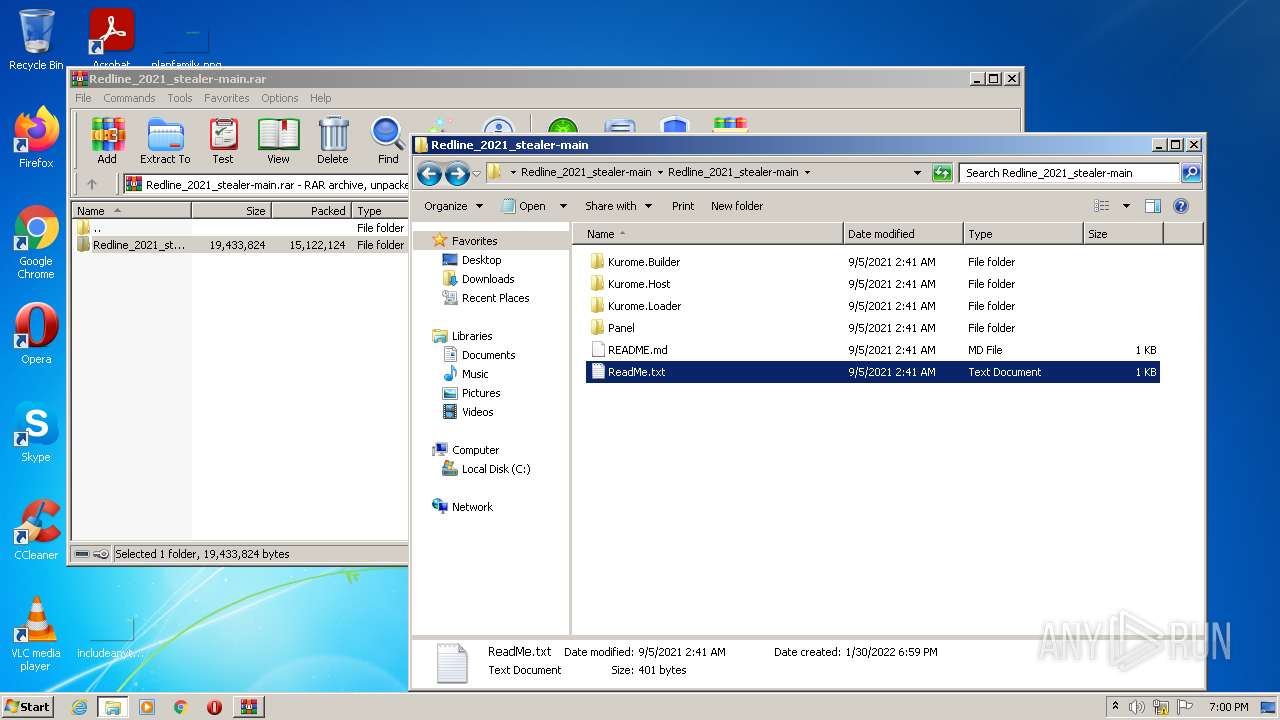
- Kurome.Builder.exe (PID: 576)
- Kurome.Host.exe (PID: 2580)
- Kurome.Loader.exe (PID: 496)
- Chrome.exe (PID: 2696)
- GoogleUpdateSetup.exe (PID: 3080)
- GoogleUpdate.exe (PID: 2676)
- GoogleUpdate.exe (PID: 2168)
Drops executable file immediately after starts
- Chrome.exe (PID: 2696)
- GoogleUpdateSetup.exe (PID: 3080)
Changes settings of System certificates
- GoogleUpdate.exe (PID: 3364)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 1604)
- Kurome.Builder.exe (PID: 576)
- Kurome.Host.exe (PID: 2580)
- Kurome.Loader.exe (PID: 496)
- Chrome.exe (PID: 2696)
- GoogleUpdate.exe (PID: 2168)
- GoogleUpdateSetup.exe (PID: 3080)
- GoogleUpdate.exe (PID: 2676)
- GoogleUpdate.exe (PID: 3268)
- GoogleUpdate.exe (PID: 3364)
- GoogleUpdate.exe (PID: 2508)
- GoogleUpdate.exe (PID: 3576)
Reads the computer name
- WinRAR.exe (PID: 1604)
- GoogleUpdate.exe (PID: 2168)
- GoogleUpdate.exe (PID: 2676)
- GoogleUpdate.exe (PID: 2508)
- GoogleUpdate.exe (PID: 3364)
- GoogleUpdate.exe (PID: 3576)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1604)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1604)
- Chrome.exe (PID: 2696)
- GoogleUpdateSetup.exe (PID: 3080)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1604)
- Chrome.exe (PID: 2696)
- GoogleUpdateSetup.exe (PID: 3080)
Creates files in the user directory
- Explorer.EXE (PID: 1656)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1656)
Creates files in the program directory
- GoogleUpdateSetup.exe (PID: 3080)
Creates a directory in Program Files
- GoogleUpdateSetup.exe (PID: 3080)
Adds / modifies Windows certificates
- GoogleUpdate.exe (PID: 3364)
Application launched itself
- GoogleUpdate.exe (PID: 2508)
INFO
Manual execution by user
- Kurome.Builder.exe (PID: 576)
Checks supported languages
- NOTEPAD.EXE (PID: 652)
- Explorer.EXE (PID: 1656)
Reads settings of System Certificates
- GoogleUpdate.exe (PID: 3364)
- GoogleUpdate.exe (PID: 2508)
- GoogleUpdate.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
56
Monitored processes
15
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
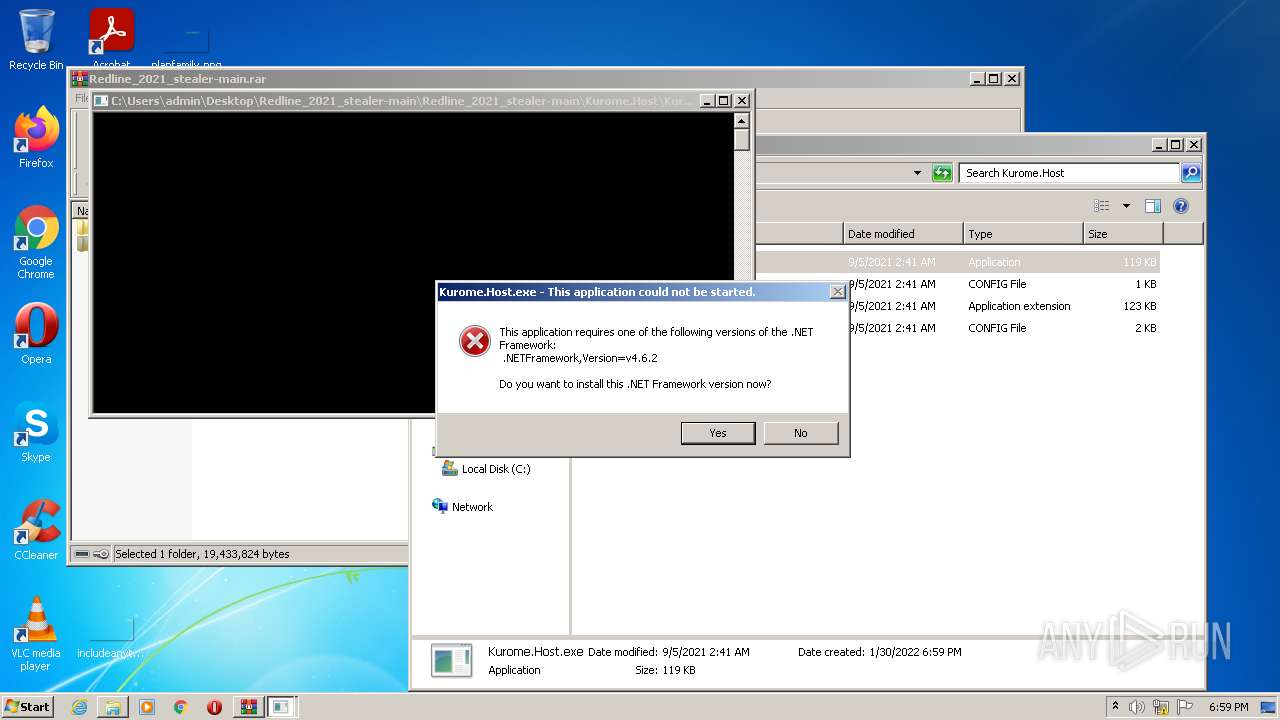
| 496 | "C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Loader\Kurome.Loader.exe" | C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Loader\Kurome.Loader.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kurome.Loader Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 576 | "C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Kurome.Builder.exe" | C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Kurome.Builder.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kurome.Builder Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
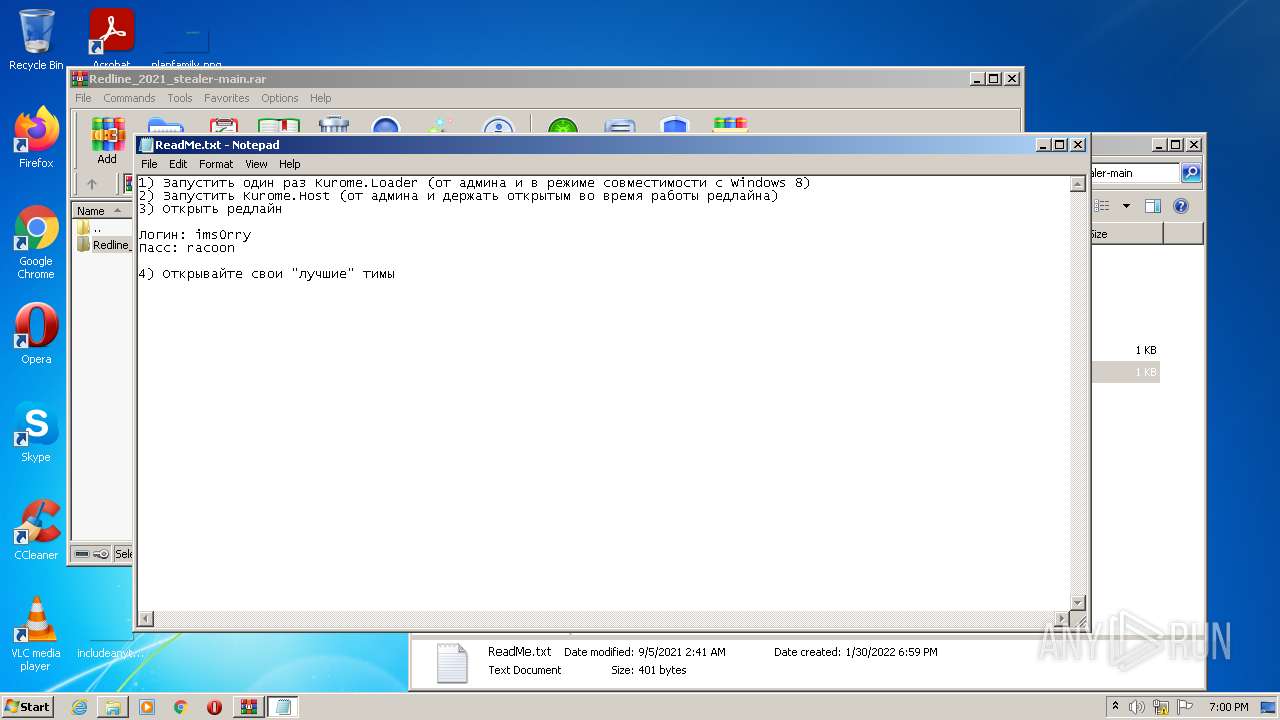
| 652 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\ReadMe.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Redline_2021_stealer-main.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1656 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | C:\Users\admin\AppData\Local\Temp\GUM8CCD.tmp\GoogleUpdate.exe /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={147E1A31-5E49-ACD4-7646-E2EE6FA22B56}&lang=ru&browser=3&usagestats=0&appname=Google%20Chrome&needsadmin=prefers&ap=x64-stable-statsdef_1&installdataindex=empty" | C:\Users\admin\AppData\Local\Temp\GUM8CCD.tmp\GoogleUpdate.exe | — | Chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Installer Exit code: 2147747856 Version: 1.3.34.11 Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /handoff "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={147E1A31-5E49-ACD4-7646-E2EE6FA22B56}&lang=ru&browser=3&usagestats=0&appname=Google%20Chrome&needsadmin=prefers&ap=x64-stable-statsdef_1&installdataindex=empty" /installsource taggedmi /sessionid "{DAB74A2B-F34A-4039-B13C-15F044EE0030}" | C:\Program Files\Google\Update\GoogleUpdate.exe | GoogleUpdate.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 2147747856 Version: 1.3.33.23 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Host\Kurome.Host.exe" | C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Host\Kurome.Host.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kurome.Host Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2676 | "C:\Program Files\GUM9161.tmp\GoogleUpdate.exe" /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={147E1A31-5E49-ACD4-7646-E2EE6FA22B56}&lang=ru&browser=3&usagestats=0&appname=Google%20Chrome&needsadmin=prefers&ap=x64-stable-statsdef_1&installdataindex=empty" /installelevated | C:\Program Files\GUM9161.tmp\GoogleUpdate.exe | — | GoogleUpdateSetup.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Installer Exit code: 2147747856 Version: 1.3.34.11 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Panel\RedLine_20_2\Tools\Chrome.exe" | C:\Users\admin\Desktop\Redline_2021_stealer-main\Redline_2021_stealer-main\Panel\RedLine_20_2\Tools\Chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Update Setup Exit code: 2147747856 Version: 1.3.34.11 Modules
| |||||||||||||||
Total events
21 890
Read events
21 137
Write events
748
Delete events
5
Modification events
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Redline_2021_stealer-main.rar | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
155
Suspicious files
6
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
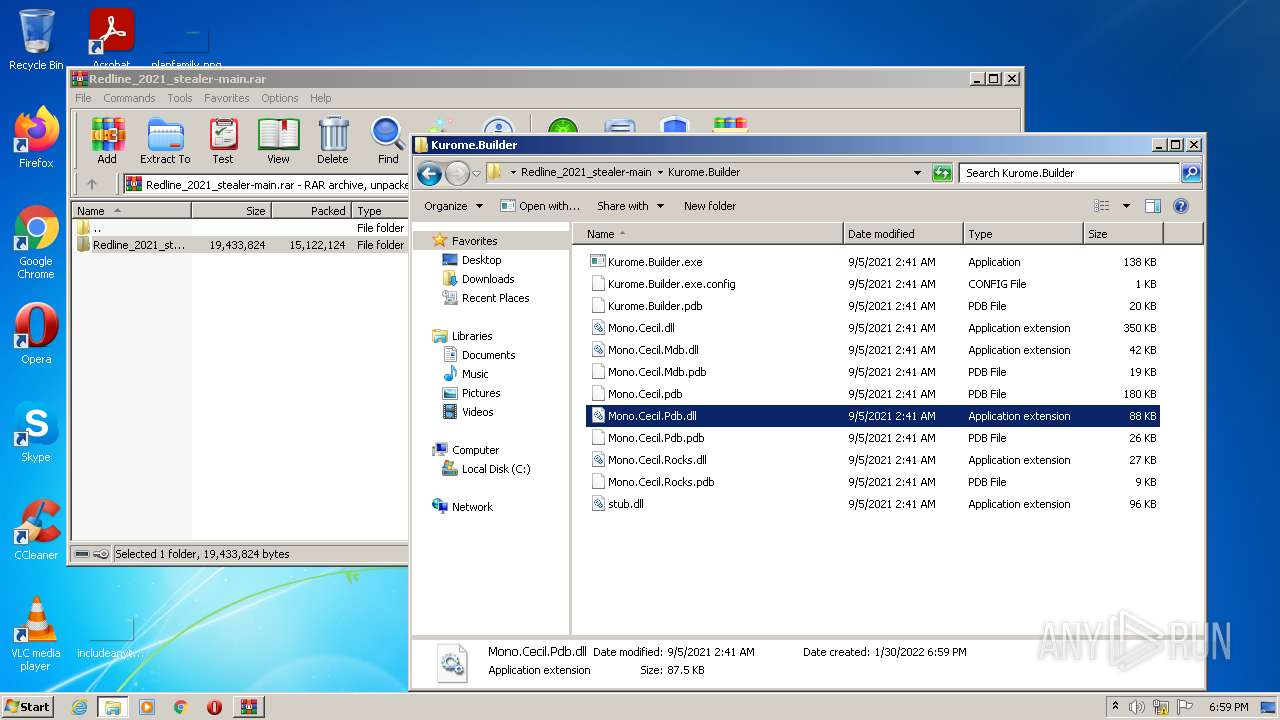
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Kurome.Builder.exe.config | xml | |
MD5:5A7F52D69E6FCA128023469AE760C6D5 | SHA256:498C7F8E872F9CEF0CF04F7D290CF3804C82A007202C9B484128C94D03040FD0 | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Mdb.dll | executable | |
MD5:1C6ACA0F1B1FA1661FC1E43C79334F7C | SHA256:411F8ED8C49738FA38A56ED8F991D556227D13602E83186E66AE1C4F821C940B | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Pdb.dll | executable | |
MD5:6D5EB860C2BE5DBEB470E7D3F3E7DDA4 | SHA256:447EDE1984BB4ACD73BD97C0EC57A11C079CEE8301C91FB199CA98C1906D3CC4 | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Mdb.pdb | binary | |
MD5:073D9D6C9C71F66151B84A376EDE4A9D | SHA256:891251514AA16F94485263C52FABA51BB5BB3495B9FAD382C74F6C9DA78718DD | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Pdb.pdb | binary | |
MD5:711C5F65BD140E72EE30B33F14FBF100 | SHA256:7C3A6B12EF0676D3DC80A4E2B790F3DEC4D7FDAA182B2181C3F6EE283B118A9E | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.pdb | binary | |
MD5:9A345FCE8746876DB39AA5622A771163 | SHA256:ECF13638359A5A9FE271966924CF543C4B440C2DC274E9D94069EF50BBC95482 | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Rocks.dll | executable | |
MD5:6E7F0F4FFF6C49E3F66127C23B7F1A53 | SHA256:2E2623319BDC362974A78EA4A43F4893011EC257884D24267F4594142FCD436E | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Builder\Mono.Cecil.Rocks.pdb | binary | |
MD5:4C98B54BF658DB95DFB4D1AE6BED2565 | SHA256:5FCF9491B8D73F1F90A83EE7BDA9097043903BA18822F1F22EACF92338B0D619 | |||
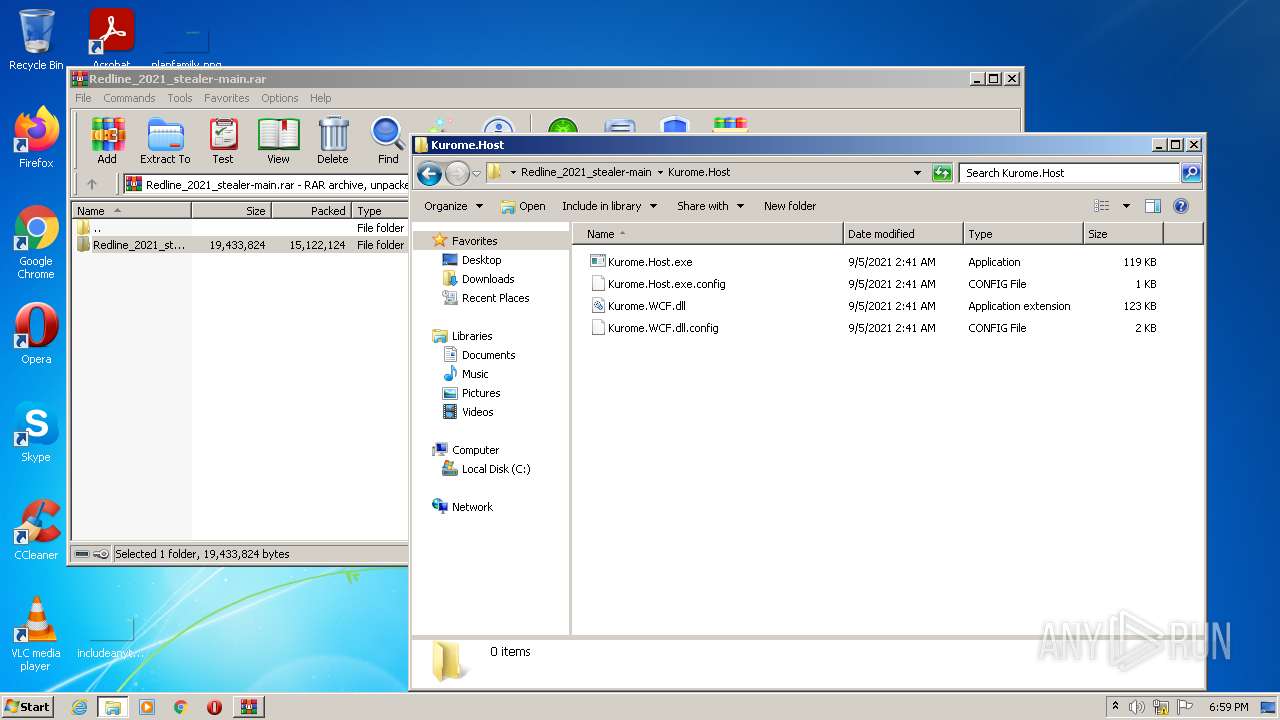
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Loader\Kurome.Loader.exe | executable | |
MD5:A3EC05D5872F45528BBD05AEECF0A4BA | SHA256:D4797B2E4957C9041BA32454657F5D9A457851C6B5845A57E0E5397707E7773E | |||
| 1604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1604.33445\Redline_2021_stealer-main\Redline_2021_stealer-main\Kurome.Host\Kurome.WCF.dll | executable | |
MD5:E3D39E30E0CDB76A939905DA91FE72C8 | SHA256:4BFA493B75361920E6403C3D85D91A454C16DDDA89A97C425257E92B352EDD74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 142.250.186.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe | US | — | — | whitelisted |
2508 | GoogleUpdate.exe | GET | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe | US | text | 37 b | whitelisted |
2508 | GoogleUpdate.exe | GET | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe | US | text | 37 b | whitelisted |
924 | svchost.exe | HEAD | 200 | 173.194.5.203:80 | http://r5---sn-aigl6n76.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe?cms_redirect=yes&mh=Pg&mip=185.217.117.59&mm=28&mn=sn-aigl6n76&ms=nvh&mt=1643568539&mv=u&mvi=5&pl=25&rmhost=r3---sn-aigl6n76.gvt1.com&shardbypass=yes&smhost=r3---sn-aigl6ns6.gvt1.com | US | — | — | whitelisted |
924 | svchost.exe | GET | — | 173.194.5.203:80 | http://r5---sn-aigl6n76.gvt1.com/edgedl/release2/chrome/jskl2vqav7llvnpswum2rlzxee_97.0.4692.99/97.0.4692.99_chrome_installer.exe?cms_redirect=yes&mh=Pg&mip=185.217.117.59&mm=28&mn=sn-aigl6n76&ms=nvh&mt=1643568539&mv=u&mvi=5&pl=25&rmhost=r3---sn-aigl6n76.gvt1.com&shardbypass=yes&smhost=r3---sn-aigl6ns6.gvt1.com | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2508 | GoogleUpdate.exe | 142.250.185.99:443 | update.googleapis.com | Google Inc. | US | whitelisted |
924 | svchost.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2508 | GoogleUpdate.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
924 | svchost.exe | 142.250.186.142:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
3576 | GoogleUpdate.exe | 142.250.185.99:443 | update.googleapis.com | Google Inc. | US | whitelisted |
3364 | GoogleUpdate.exe | 142.250.185.99:443 | update.googleapis.com | Google Inc. | US | whitelisted |
924 | svchost.exe | 173.194.5.203:80 | r5---sn-aigl6n76.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r5---sn-aigl6n76.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
924 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
924 | svchost.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1 ETPRO signatures available at the full report