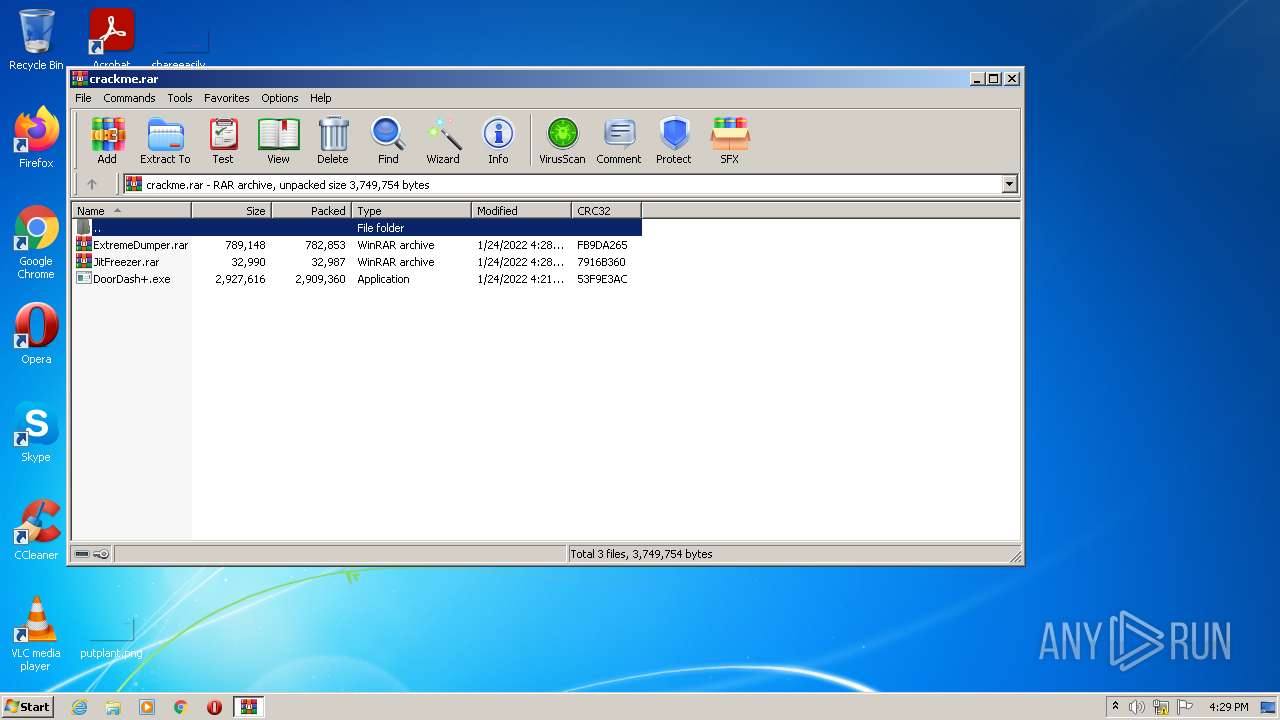
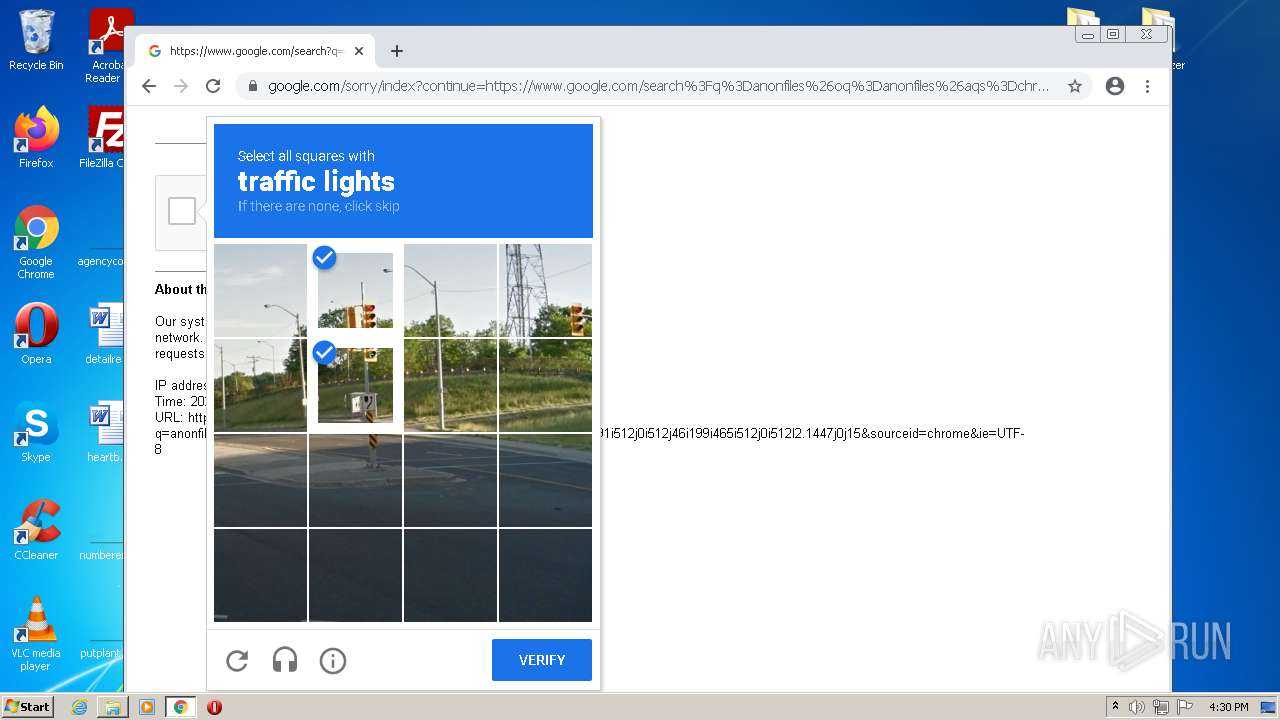
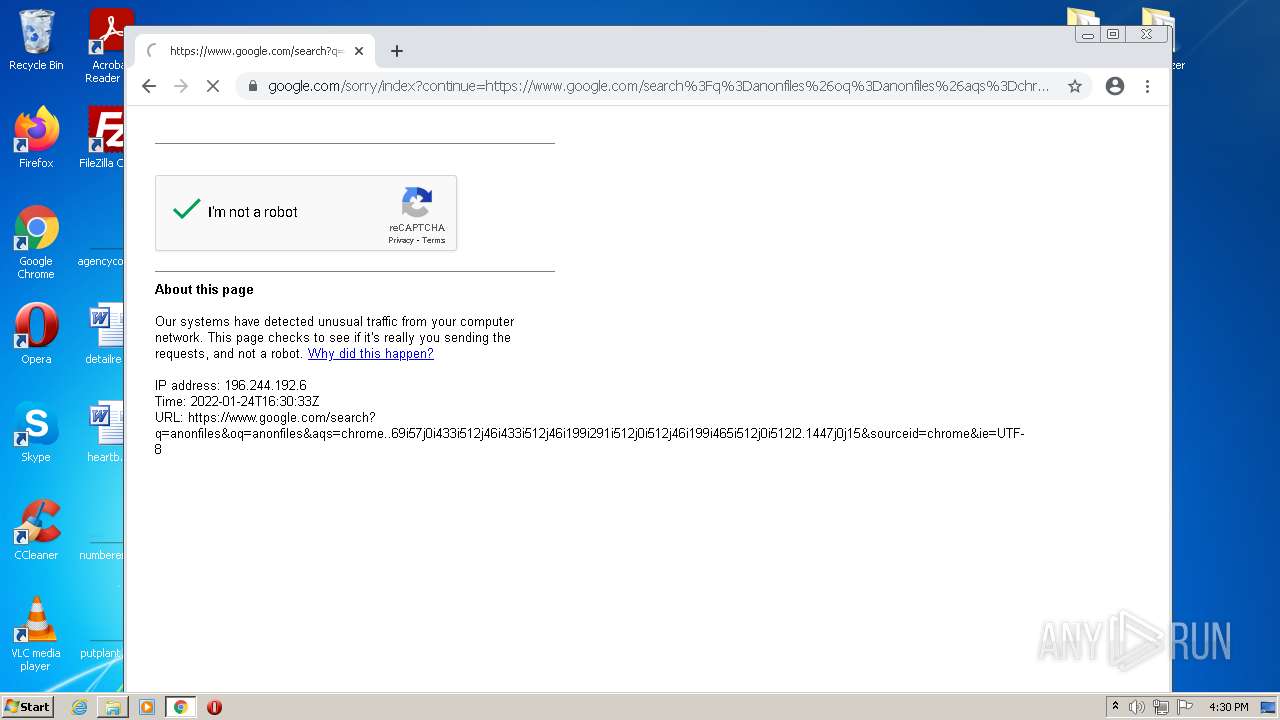
| File name: | crackme.rar |
| Full analysis: | https://app.any.run/tasks/b71b34e0-6407-4870-8eea-d4e827bc21ae |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:29:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 166C01AB866BFFF958BEF046099DC419 |
| SHA1: | DEEB854FD1B627AFD58FD63F30826A94FC20C82F |
| SHA256: | 4AFFA3CBA261DDC21A5372DF3E413E7E0EF827BA3012F317D1CDEB8ED5DF5A79 |
| SSDEEP: | 98304:6rXp0m4slBCleht0LxO3hLpEeORFSPhOFbA8pCS0Qk:2XpLnComORLpE1whae8k |
MALICIOUS
Loads dropped or rewritten executable
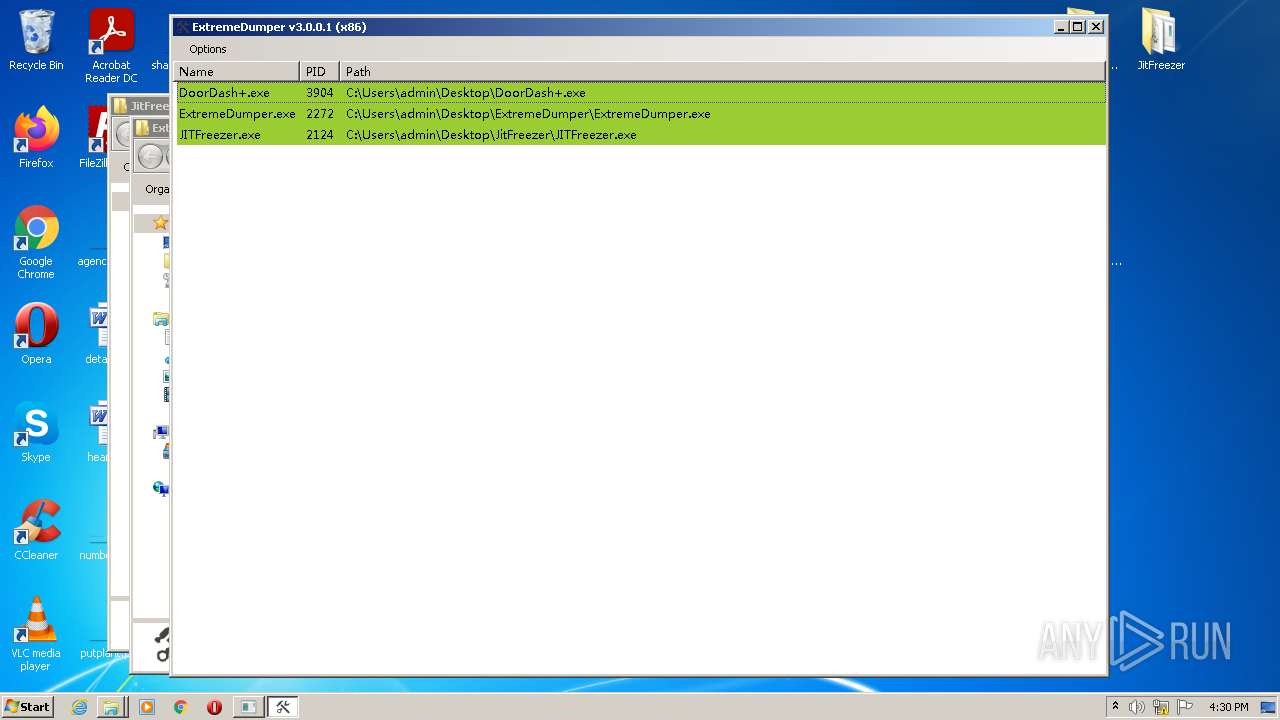
- SearchProtocolHost.exe (PID: 2248)
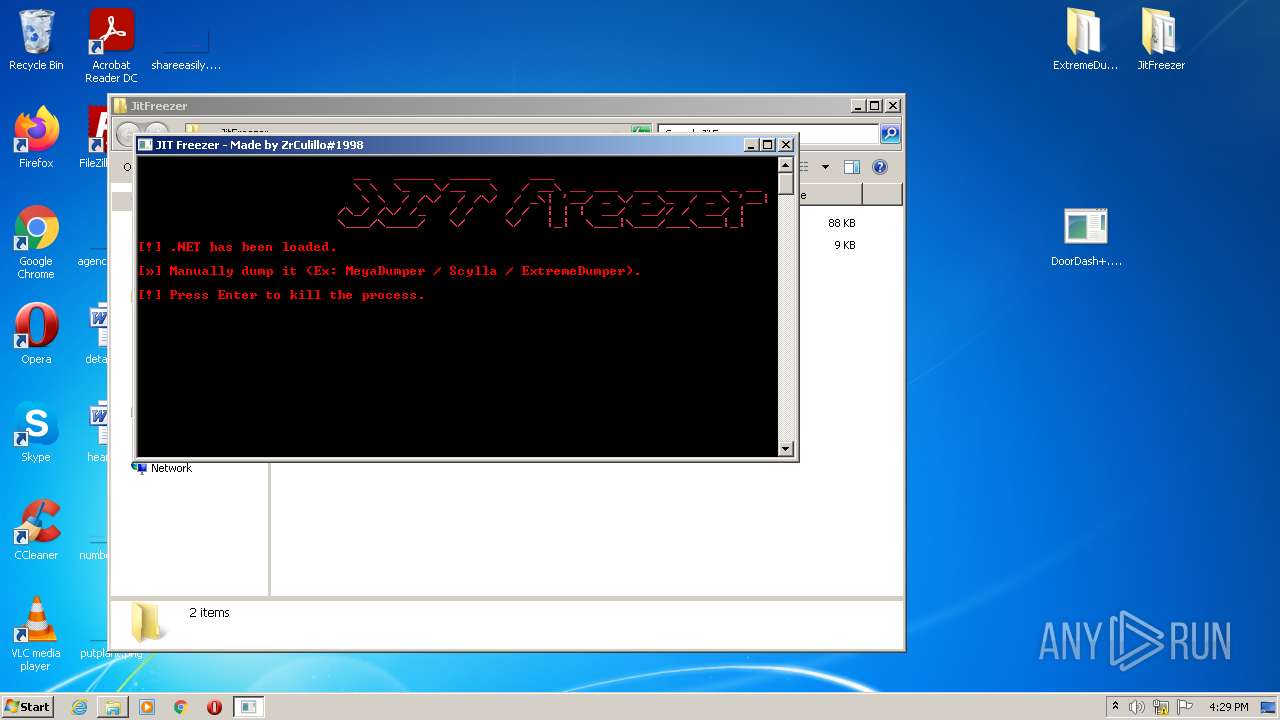
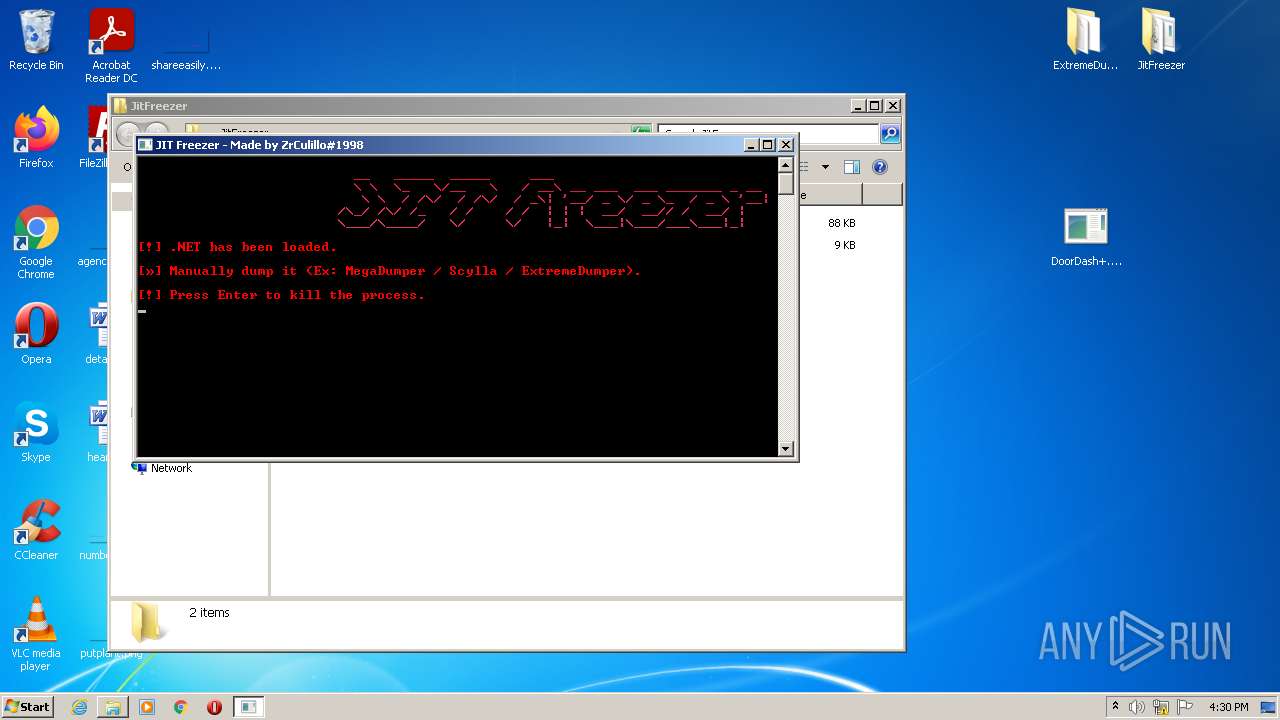
- JITFreezer.exe (PID: 2124)
Application was dropped or rewritten from another process
- JITFreezer.exe (PID: 2124)
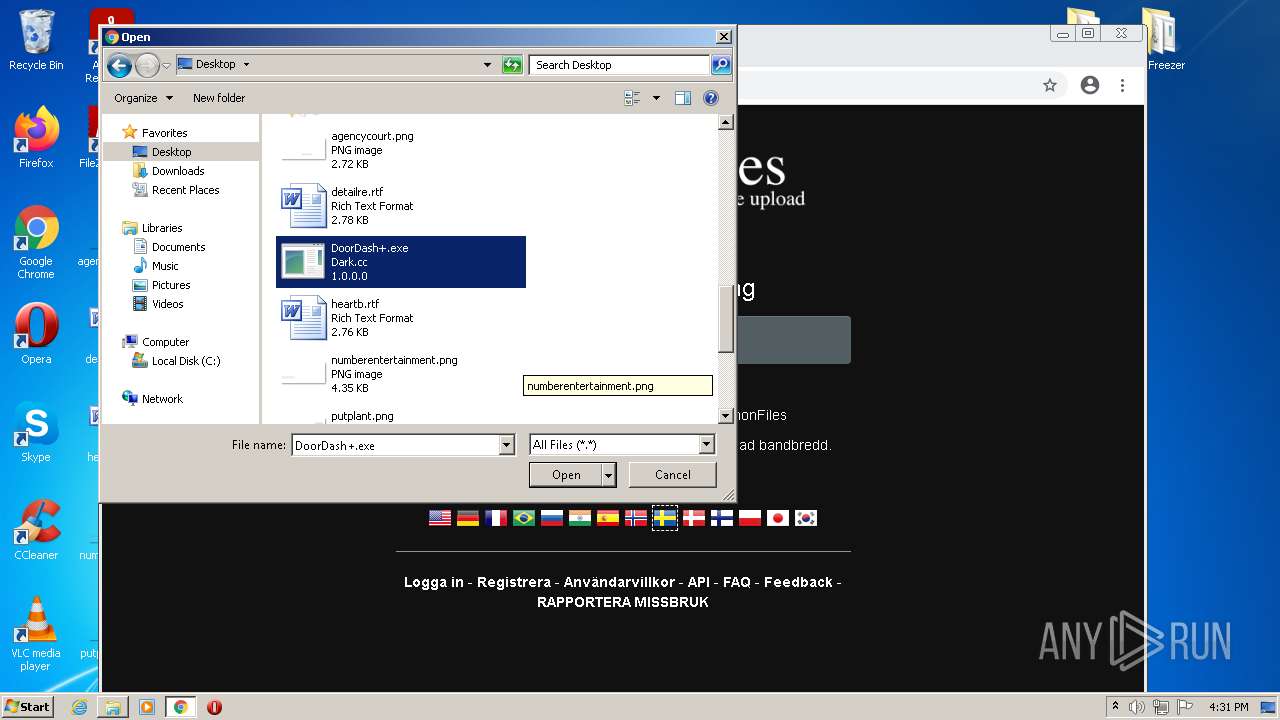
- DoorDash+.exe (PID: 3904)
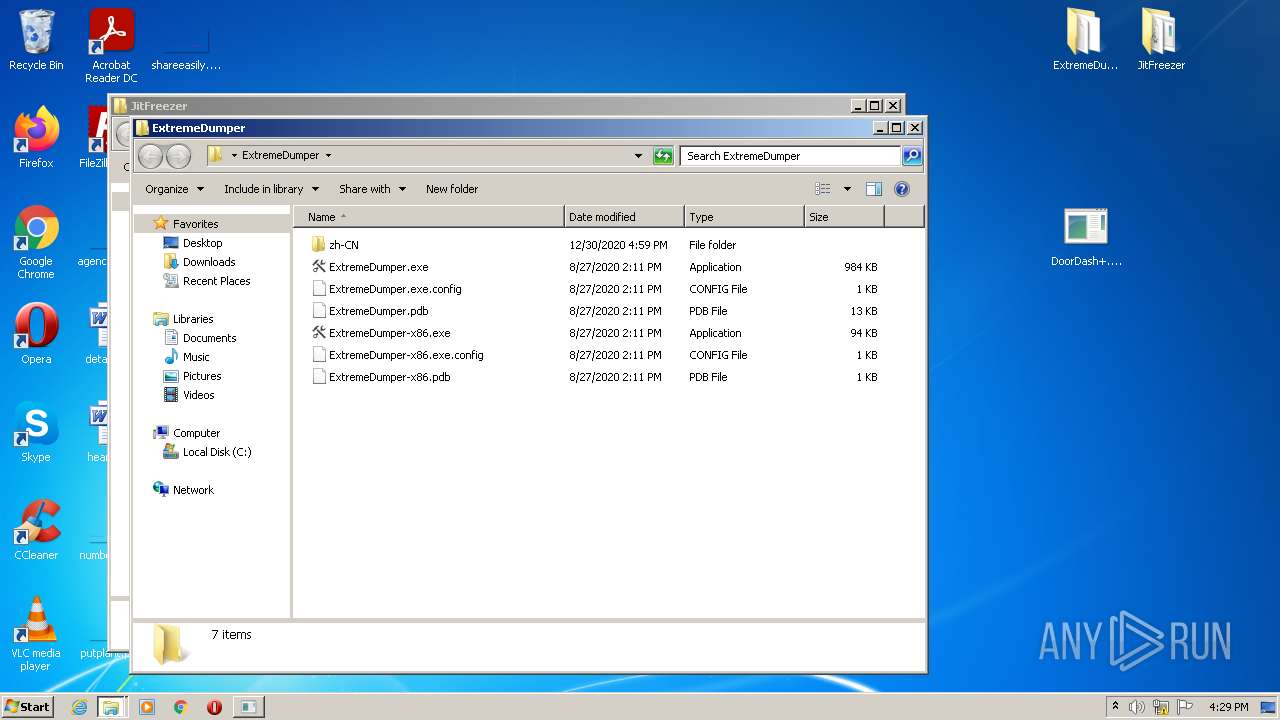
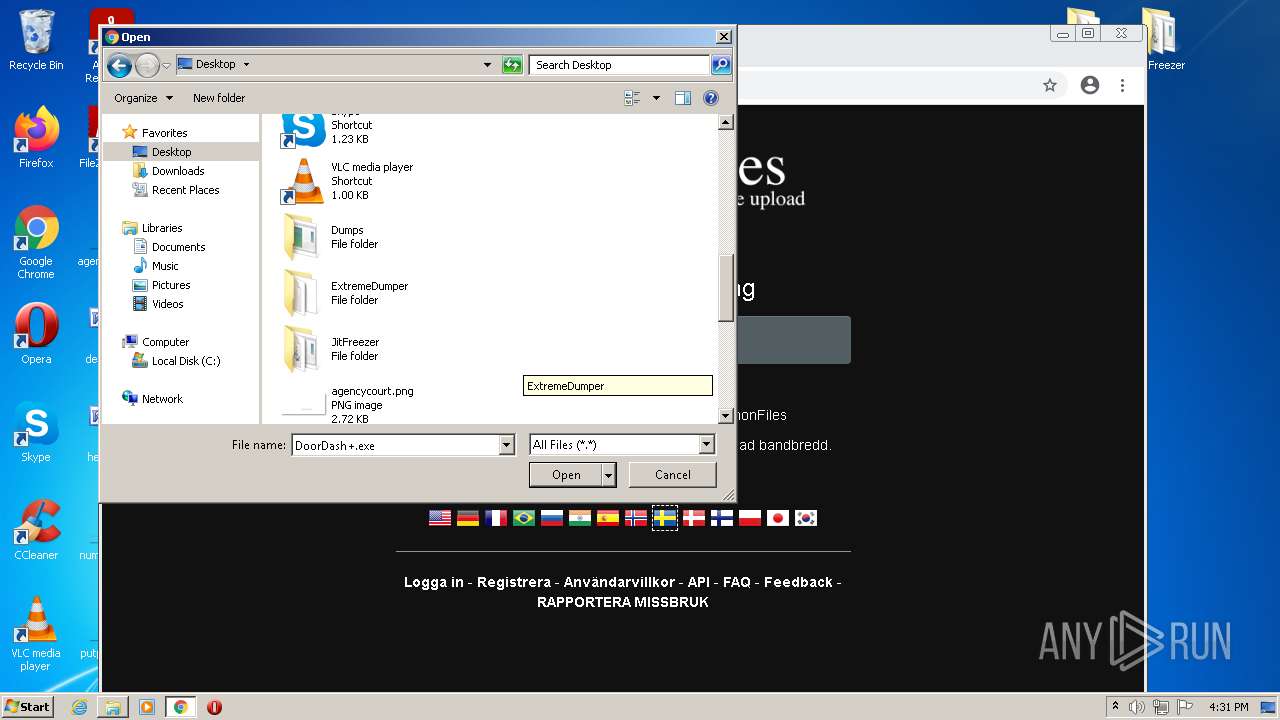
- ExtremeDumper.exe (PID: 2272)
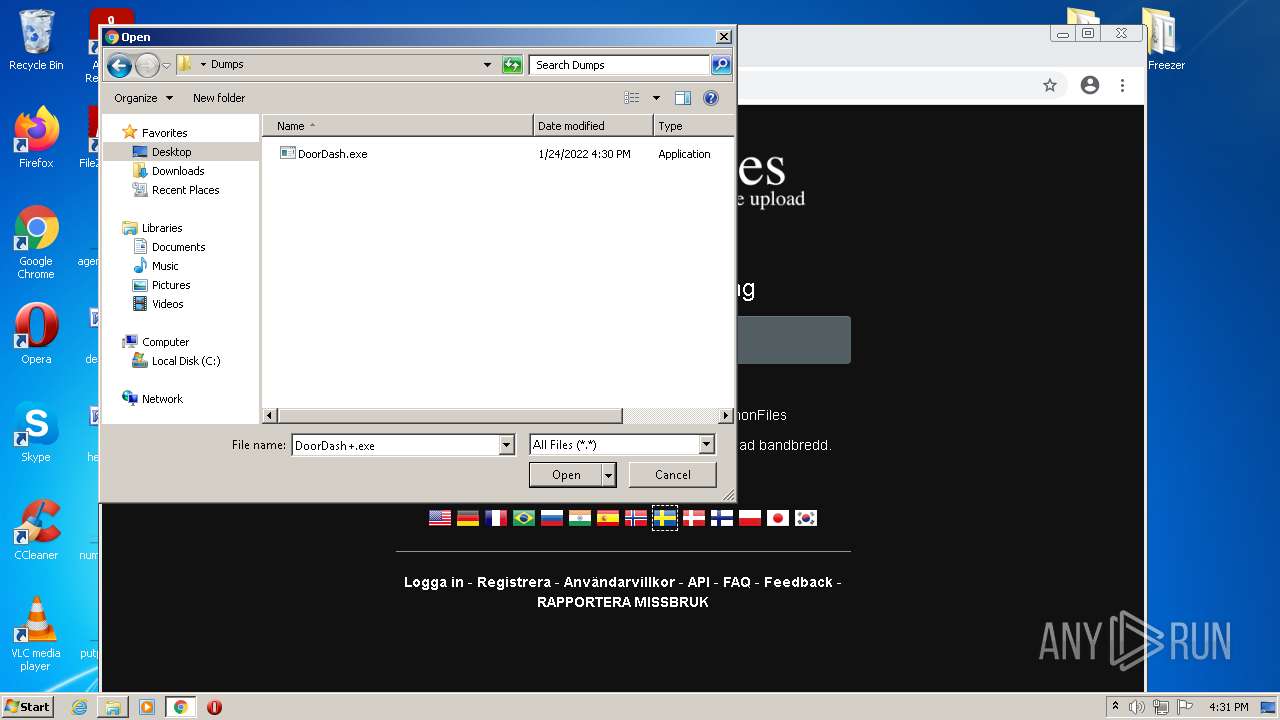
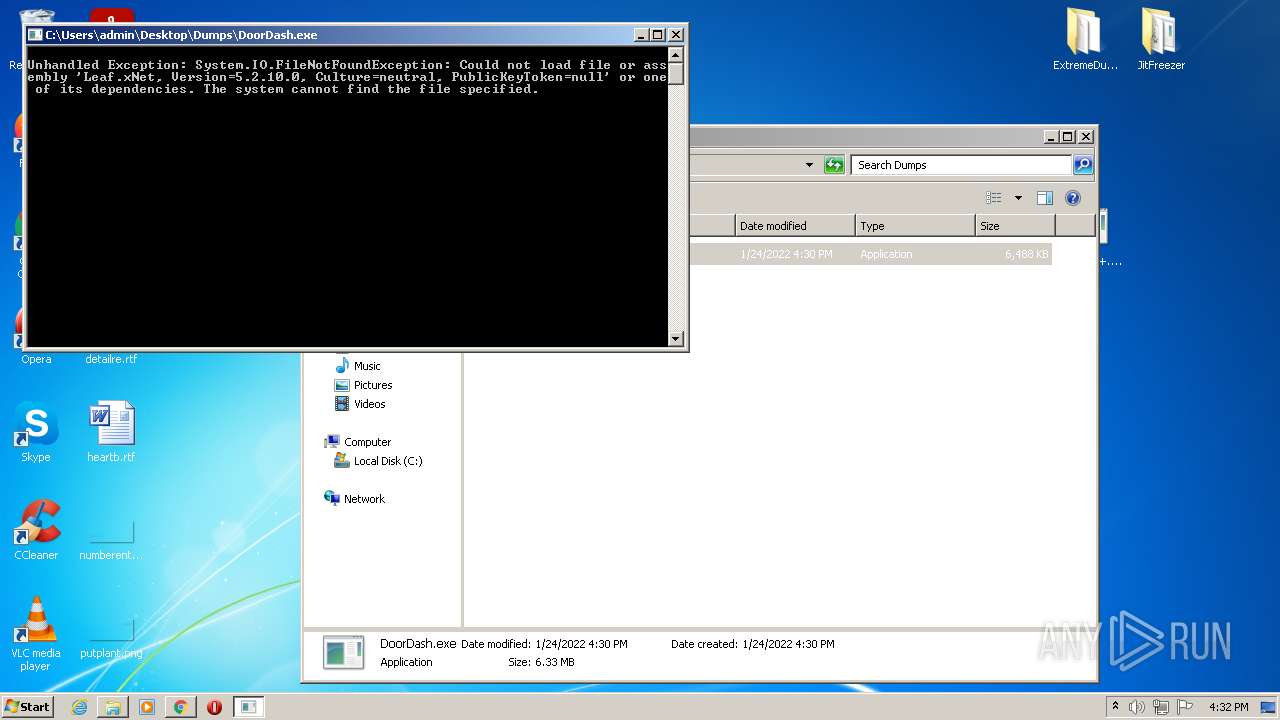
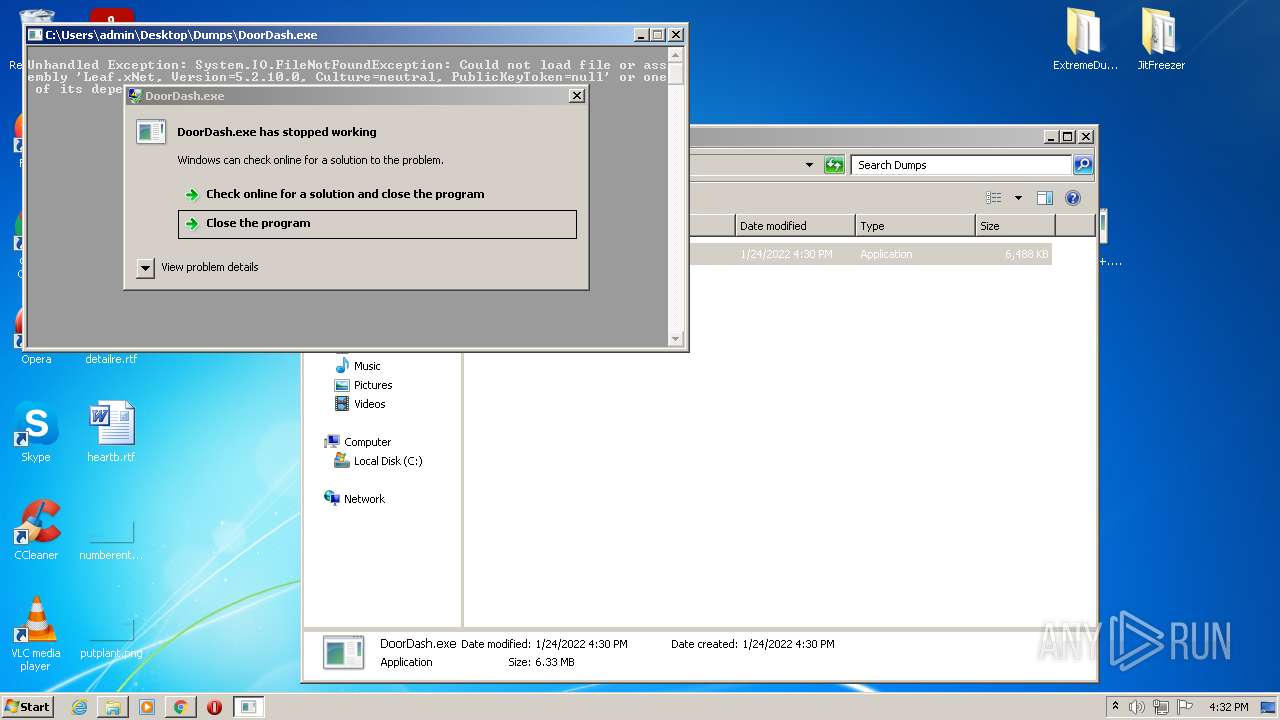
- DoorDash.exe (PID: 2916)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 1304)
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
- JITFreezer.exe (PID: 2124)
- ExtremeDumper.exe (PID: 2272)
- DoorDash+.exe (PID: 3904)
- DoorDash.exe (PID: 2916)
Reads the computer name
- WinRAR.exe (PID: 1304)
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
- JITFreezer.exe (PID: 2124)
- DoorDash+.exe (PID: 3904)
- ExtremeDumper.exe (PID: 2272)
- DoorDash.exe (PID: 2916)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1304)
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
- ExtremeDumper.exe (PID: 2272)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1304)
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
- ExtremeDumper.exe (PID: 2272)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2384)
Reads default file associations for system extensions
- chrome.exe (PID: 4024)
INFO
Manual execution by user
- WinRAR.exe (PID: 3244)
- WinRAR.exe (PID: 2680)
- JITFreezer.exe (PID: 2124)
- ExtremeDumper.exe (PID: 2272)
- chrome.exe (PID: 2384)
- DoorDash.exe (PID: 2916)
Checks supported languages
- chrome.exe (PID: 744)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 1808)
- chrome.exe (PID: 688)
- chrome.exe (PID: 700)
- chrome.exe (PID: 3804)
- chrome.exe (PID: 3260)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 1500)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 1228)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 2756)
- chrome.exe (PID: 744)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 1176)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 2348)
- chrome.exe (PID: 1368)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 2964)
- chrome.exe (PID: 2808)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 1592)
- chrome.exe (PID: 1696)
- chrome.exe (PID: 1436)
- chrome.exe (PID: 3076)
- chrome.exe (PID: 1220)
- chrome.exe (PID: 3588)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 4024)
- chrome.exe (PID: 2752)
Reads the computer name
- chrome.exe (PID: 744)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 688)
- chrome.exe (PID: 700)
- chrome.exe (PID: 2808)
- chrome.exe (PID: 3076)
- chrome.exe (PID: 1220)
- chrome.exe (PID: 3588)
- chrome.exe (PID: 1696)
- chrome.exe (PID: 4024)
Reads the hosts file
- chrome.exe (PID: 688)
- chrome.exe (PID: 2384)
Application launched itself
- chrome.exe (PID: 2384)
Reads settings of System Certificates
- chrome.exe (PID: 688)
Reads the date of Windows installation
- chrome.exe (PID: 1220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
86
Monitored processes
42
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 688 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1280 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1040 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3580 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4176 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3444 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1304 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\crackme.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8323294518213923766,2855609962579994729,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2400 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
18 486
Read events
18 124
Write events
353
Delete events
9
Modification events
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\crackme.rar | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
172
Text files
126
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EED41F-950.pma | — | |
MD5:— | SHA256:— | |||
| 1304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1304.43261\JitFreezer.rar | compressed | |
MD5:— | SHA256:— | |||
| 1304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1304.43261\DoorDash+.exe | executable | |
MD5:— | SHA256:— | |||
| 1304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1304.43261\ExtremeDumper.rar | compressed | |
MD5:— | SHA256:— | |||
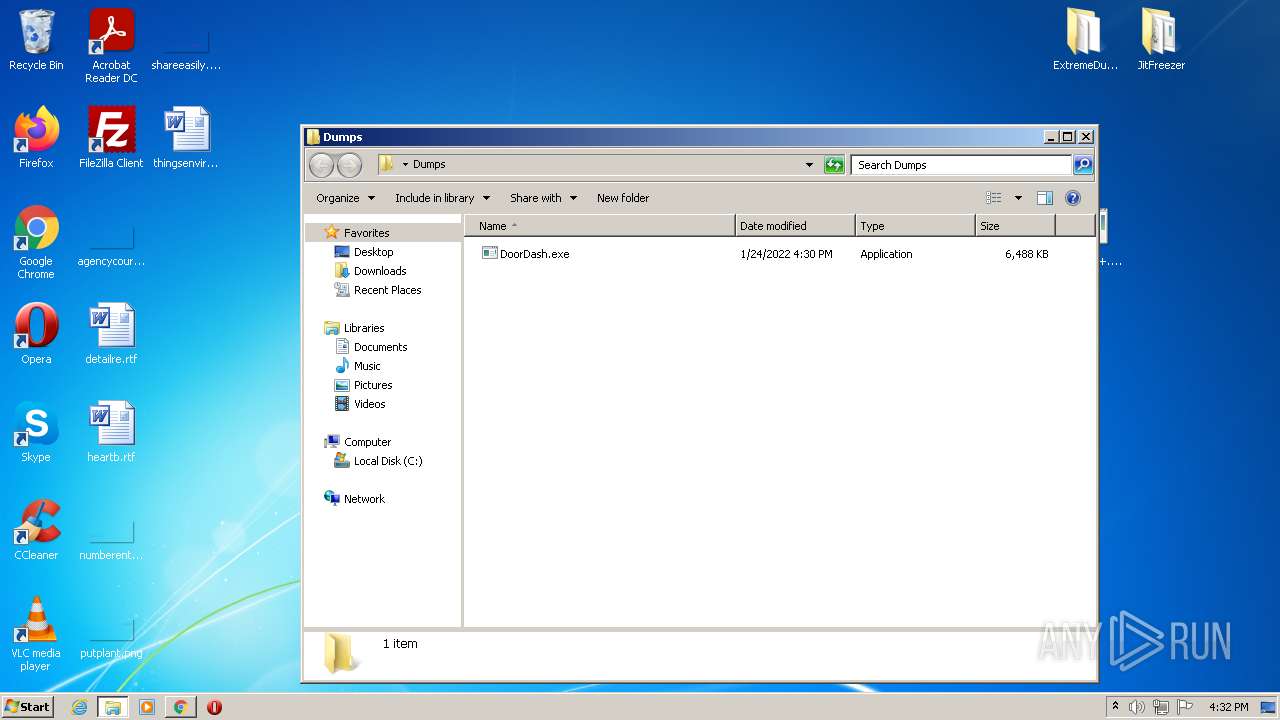
| 2272 | ExtremeDumper.exe | C:\Users\admin\Desktop\Dumps\DoorDash.exe | executable | |
MD5:— | SHA256:— | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3244.43624\ExtremeDumper\ExtremeDumper.exe | executable | |
MD5:C140AFA0E76EF5A0688A2DA551D2F079 | SHA256:F05784CC1A8754D3CB45164A97BB4FFC7111E251D7E612D86CCB40E386676196 | |||
| 2680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2680.44352\JitFreezer\Colorful.Console.dll | executable | |
MD5:AC4267B870699A799E05B2BE2D2956DA | SHA256:309C616209120EE751DF11612A8EADD06E8C86E68510D0B31BA21290782516FC | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3244.43624\ExtremeDumper\extremedumper-x86.exe� | executable | |
MD5:45ABED5C5E470D978BC2BD480F41AFBC | SHA256:55DBABA42703C41EDE1A349BDA4936BD129F36AF14B2E035EF7BA276B07D64D8 | |||
| 3244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3244.43624\ExtremeDumper\ExtremeDumper-x86.exe | executable | |
MD5:45ABED5C5E470D978BC2BD480F41AFBC | SHA256:55DBABA42703C41EDE1A349BDA4936BD129F36AF14B2E035EF7BA276B07D64D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
64
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | svchost.exe | GET | — | 74.125.104.231:80 | http://r2---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1643041702&mv=m&mvi=2&pl=27&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
924 | svchost.exe | HEAD | 200 | 74.125.104.231:80 | http://r2---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1643041462&mv=m&mvi=2&pl=27&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
688 | chrome.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 556 b | whitelisted |
924 | svchost.exe | GET | 206 | 74.125.104.231:80 | http://r2---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1643041462&mv=m&mvi=2&pl=27&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 5.63 Kb | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 206 | 74.125.104.231:80 | http://r2---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1643041462&mv=m&mvi=2&pl=27&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 9.50 Kb | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
688 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
688 | chrome.exe | 216.58.212.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.186.100:443 | www.google.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.186.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.184.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.181.238:443 | apis.google.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 216.58.212.142:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.186.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
688 | chrome.exe | 142.250.186.161:443 | lh5.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |