| File name: | Auto System Care.exe |
| Full analysis: | https://app.any.run/tasks/d2818fd1-fdd8-434e-a1ed-a02ae63f98f1 |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2024, 02:39:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 844F27C28A2EEE84FB25AAD61C077790 |
| SHA1: | 8CDDBABFB306154B599A90029A36483D48AEDA70 |
| SHA256: | 4AFC95390AD33C320FD7D0F168AB8395F564BEA3EE880EFD9249879483094DC6 |
| SSDEEP: | 98304:59/culVFh4/tDwAjTPYxIGGddnT3+uz0UgEMmTtFAXOHLJgQ+aB7K6EY/dzwFnvp:t+3Wj0QqH9k+9qIrri3v |
MALICIOUS
Scans artifacts that could help determine the target
- iytr.exe (PID: 1608)
SUSPICIOUS
Drops the executable file immediately after the start
- Auto System Care.exe (PID: 6628)
- Auto System Care.exe (PID: 6720)
- Auto System Care.tmp (PID: 6744)
Reads security settings of Internet Explorer
- Auto System Care.tmp (PID: 6648)
- Auto System Care.tmp (PID: 6744)
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
Reads the date of Windows installation
- Auto System Care.tmp (PID: 6648)
- Auto System Care.tmp (PID: 6744)
Executable content was dropped or overwritten
- Auto System Care.exe (PID: 6628)
- Auto System Care.exe (PID: 6720)
- Auto System Care.tmp (PID: 6744)
Process drops legitimate windows executable
- Auto System Care.tmp (PID: 6744)
Reads the Windows owner or organization settings
- Auto System Care.tmp (PID: 6744)
Uses TASKKILL.EXE to kill process
- Auto System Care.tmp (PID: 6744)
Reads Internet Explorer settings
- iytr.exe (PID: 1608)
Reads Microsoft Outlook installation path
- iytr.exe (PID: 1608)
INFO
Checks supported languages
- Auto System Care.exe (PID: 6628)
- Auto System Care.tmp (PID: 6648)
- Auto System Care.exe (PID: 6720)
- Auto System Care.tmp (PID: 6744)
- iytr.exe (PID: 1608)
- iytr.exe (PID: 6420)
Process checks computer location settings
- Auto System Care.tmp (PID: 6648)
- Auto System Care.tmp (PID: 6744)
Reads the computer name
- Auto System Care.tmp (PID: 6648)
- Auto System Care.tmp (PID: 6744)
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
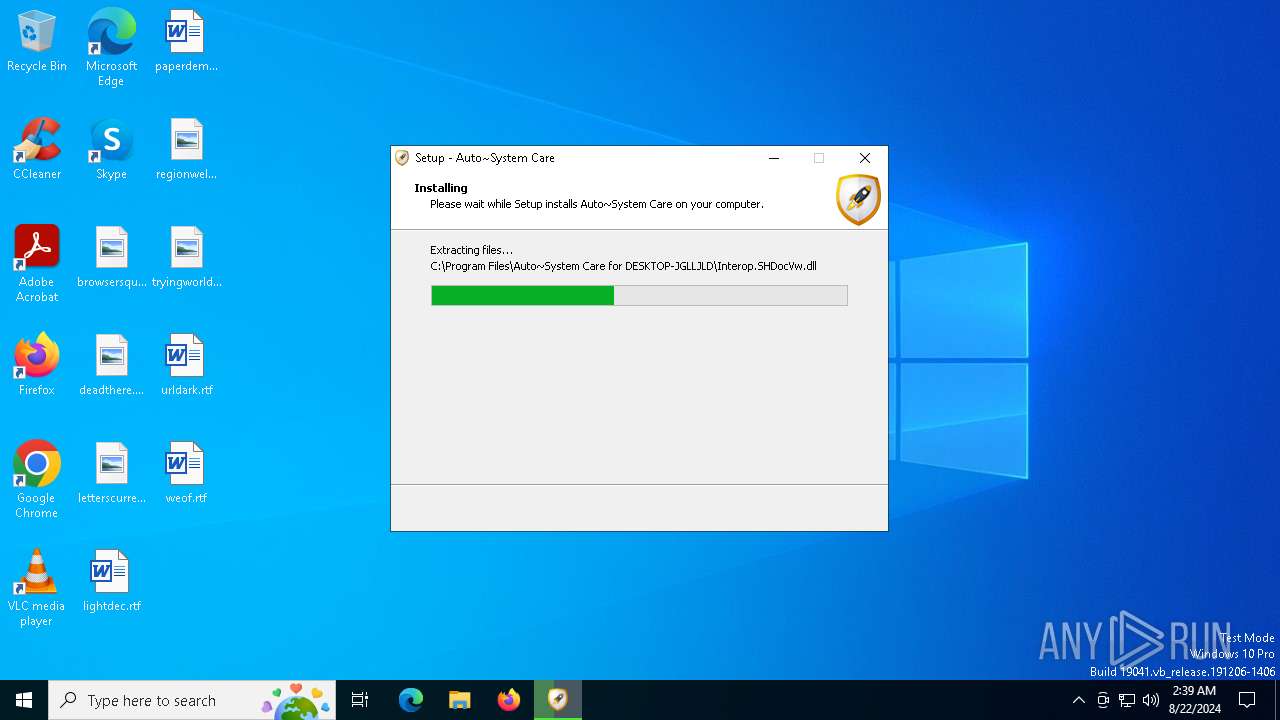
Create files in a temporary directory
- Auto System Care.exe (PID: 6628)
- Auto System Care.exe (PID: 6720)
- Auto System Care.tmp (PID: 6744)
Creates files in the program directory
- Auto System Care.tmp (PID: 6744)
Reads Environment values
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
Creates files or folders in the user directory
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
Reads the machine GUID from the registry
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
Disables trace logs
- iytr.exe (PID: 6420)
Checks proxy server information
- iytr.exe (PID: 6420)
- iytr.exe (PID: 1608)
Creates a software uninstall entry
- Auto System Care.tmp (PID: 6744)
Process checks Internet Explorer phishing filters
- iytr.exe (PID: 1608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:01:15 08:22:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 65024 |
| InitializedDataSize: | 104448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x113bc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.2 |
| ProductVersionNumber: | 1.0.0.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
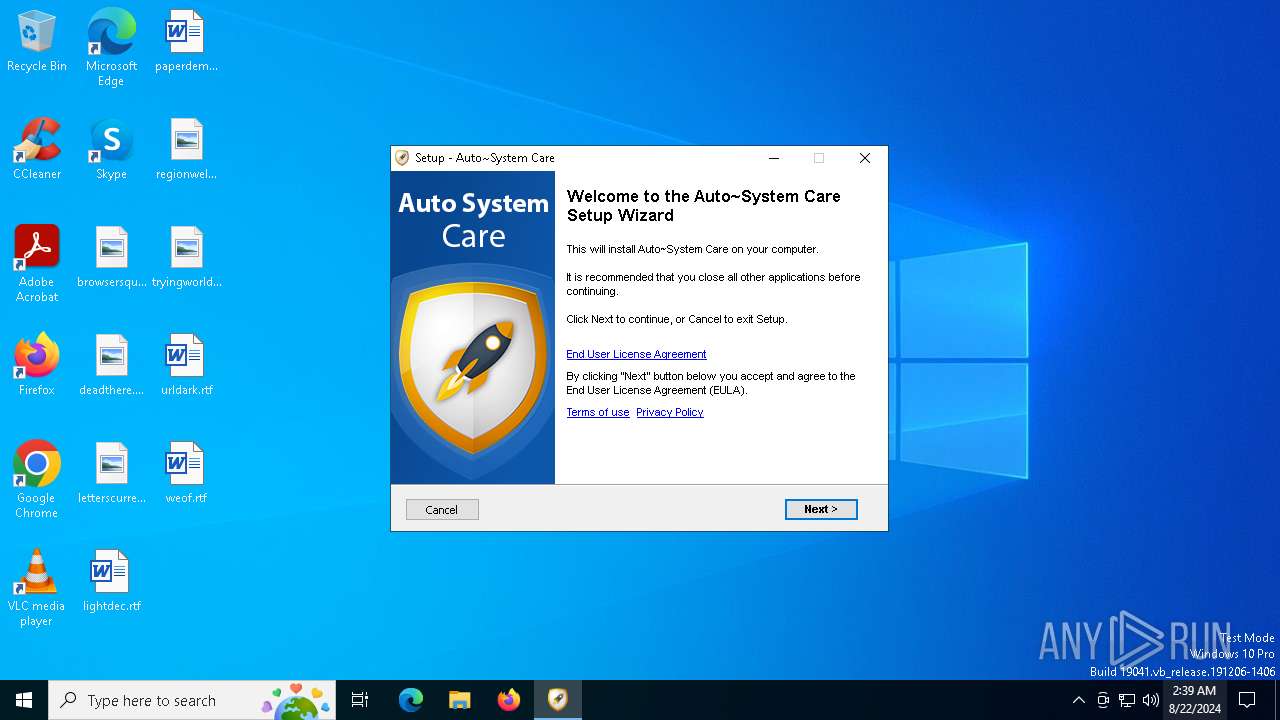
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Auto~System Care Setup |
| FileVersion: | 1.0.0.2 |
| LegalCopyright: | |
| ProductName: | Auto~System Care |
| ProductVersion: | 1.0.0.2 |
Total processes
135
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1608 | "C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\iytr.exe" firstshow | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\iytr.exe | Auto System Care.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: System Booster Version: 1.0.0.2 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\iytr.exe" getwebparam | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\iytr.exe | Auto System Care.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: System Booster Exit code: 1 Version: 1.0.0.2 Modules
| |||||||||||||||
| 6628 | "C:\Users\admin\AppData\Local\Temp\Auto System Care.exe" | C:\Users\admin\AppData\Local\Temp\Auto System Care.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Auto~System Care Setup Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\AppData\Local\Temp\is-11U3E.tmp\Auto System Care.tmp" /SL5="$503C8,7265007,170496,C:\Users\admin\AppData\Local\Temp\Auto System Care.exe" | C:\Users\admin\AppData\Local\Temp\is-11U3E.tmp\Auto System Care.tmp | — | Auto System Care.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6720 | "C:\Users\admin\AppData\Local\Temp\Auto System Care.exe" /SPAWNWND=$503A4 /NOTIFYWND=$503C8 | C:\Users\admin\AppData\Local\Temp\Auto System Care.exe | Auto System Care.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Auto~System Care Setup Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 6744 | "C:\Users\admin\AppData\Local\Temp\is-8CDE4.tmp\Auto System Care.tmp" /SL5="$603A8,7265007,170496,C:\Users\admin\AppData\Local\Temp\Auto System Care.exe" /SPAWNWND=$503A4 /NOTIFYWND=$503C8 | C:\Users\admin\AppData\Local\Temp\is-8CDE4.tmp\Auto System Care.tmp | Auto System Care.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6780 | "C:\Windows\System32\taskkill.exe" /f /im "iytr.exe" | C:\Windows\SysWOW64\taskkill.exe | — | Auto System Care.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6912 | "C:\Windows\System32\taskkill.exe" /f /im "ASCValidatorService.exe" | C:\Windows\SysWOW64\taskkill.exe | — | Auto System Care.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 443
Read events
11 272
Write events
161
Delete events
10
Modification events
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 581A0000058AD88A3CF4DA01 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 9A0E42B8C94124A3EE99C0E728EEA53A12390DD2B3FB3E2C9330603BE7AFE7D3 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\iytr.exe | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 837E13174D9B47388883BF67D562AEA721847057512FE60B4E9EB74727102B89 | |||
| (PID) Process: | (6744) Auto System Care.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Auto~System Care |
Value: | |||
Executable files
36
Suspicious files
7
Text files
30
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6744 | Auto System Care.tmp | C:\Users\admin\AppData\Local\Temp\is-36U6L.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6744 | Auto System Care.tmp | C:\Users\admin\AppData\Local\Temp\is-36U6L.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 6720 | Auto System Care.exe | C:\Users\admin\AppData\Local\Temp\is-8CDE4.tmp\Auto System Care.tmp | executable | |
MD5:5EA709C238E19609B581039ED605B75D | SHA256:030BF0EEF4DCC92C20F9873F9F46F585D00C4C7338E2A2C6566796FB09816388 | |||
| 6744 | Auto System Care.tmp | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\unins000.exe | executable | |
MD5:5EA709C238E19609B581039ED605B75D | SHA256:030BF0EEF4DCC92C20F9873F9F46F585D00C4C7338E2A2C6566796FB09816388 | |||
| 6744 | Auto System Care.tmp | C:\Users\admin\AppData\Local\Temp\is-36U6L.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6744 | Auto System Care.tmp | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\is-LOPE9.tmp | executable | |
MD5:590686DC89E051FDD89435CB74E291D7 | SHA256:F4B62962C800DF7410541D26B301B5E7CBC7E5EB513A1928933AE487BCB84AE7 | |||
| 6744 | Auto System Care.tmp | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\is-FL951.tmp | executable | |
MD5:E943BE64A2C359A32E3FEF8ADD9D245A | SHA256:319AF925E50DF13CE348A8B160E5264284C74A42E53AEEABA802FD1EACF7D34A | |||
| 6744 | Auto System Care.tmp | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\is-5LC5E.tmp | xml | |
MD5:7F2A41B4F6B7903D5D9F8611A0938FC6 | SHA256:472618FA4B8EC23E222FAA25D689E336C7B73F1334E3CB8EE43ECF983E52B714 | |||
| 6744 | Auto System Care.tmp | C:\Users\admin\AppData\Local\Temp\is-36U6L.tmp\setup_en.bmp | image | |
MD5:201296DBF6350096C191EFE1015C8B5D | SHA256:BCB734AB835112C8BB2624B5B648F51C86020FBF6EFD94949CC967CCE105E6D0 | |||
| 6744 | Auto System Care.tmp | C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\is-0DN33.tmp | executable | |
MD5:008419DC105F119B35C484D6B80CE051 | SHA256:6FD7C8D3DF96FBCDB52040CE75510BD1669F26F77FE4798862CE4EF84175FB45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5468 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1020 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2580 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5468 | svchost.exe | 40.126.35.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
5468 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cc.alfactiv.com |
| malicious |
www.alfactiv.com |
| unknown |
ins1.alfactiv.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
iytr.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\x64\SQLite.Interop.dll"...
|
iytr.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Auto~System Care for DESKTOP-JGLLJLD\x64\SQLite.Interop.dll"...
|