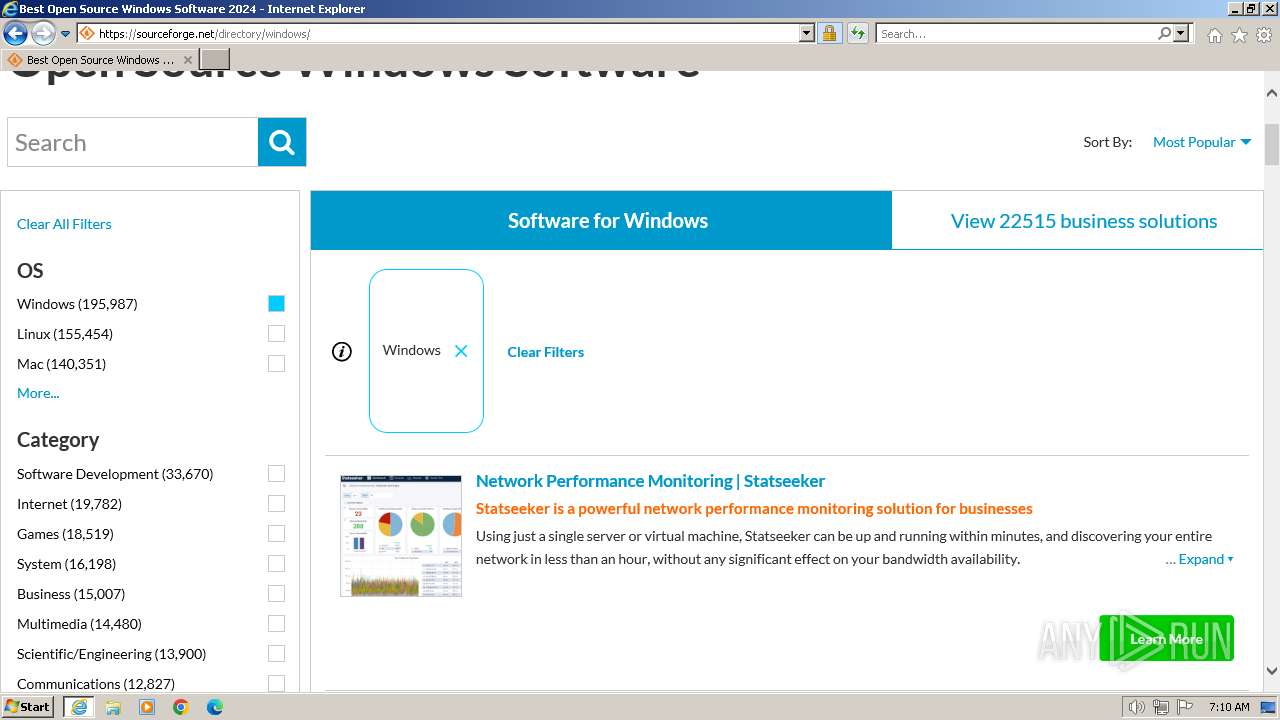
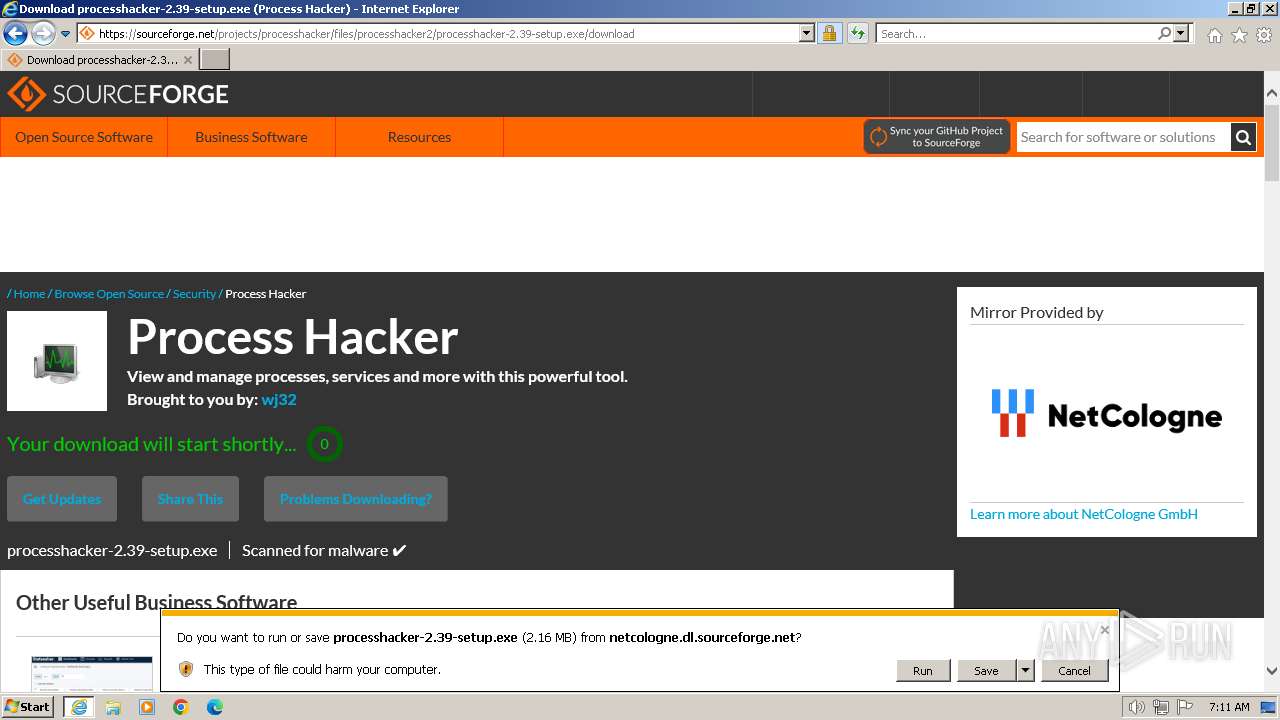
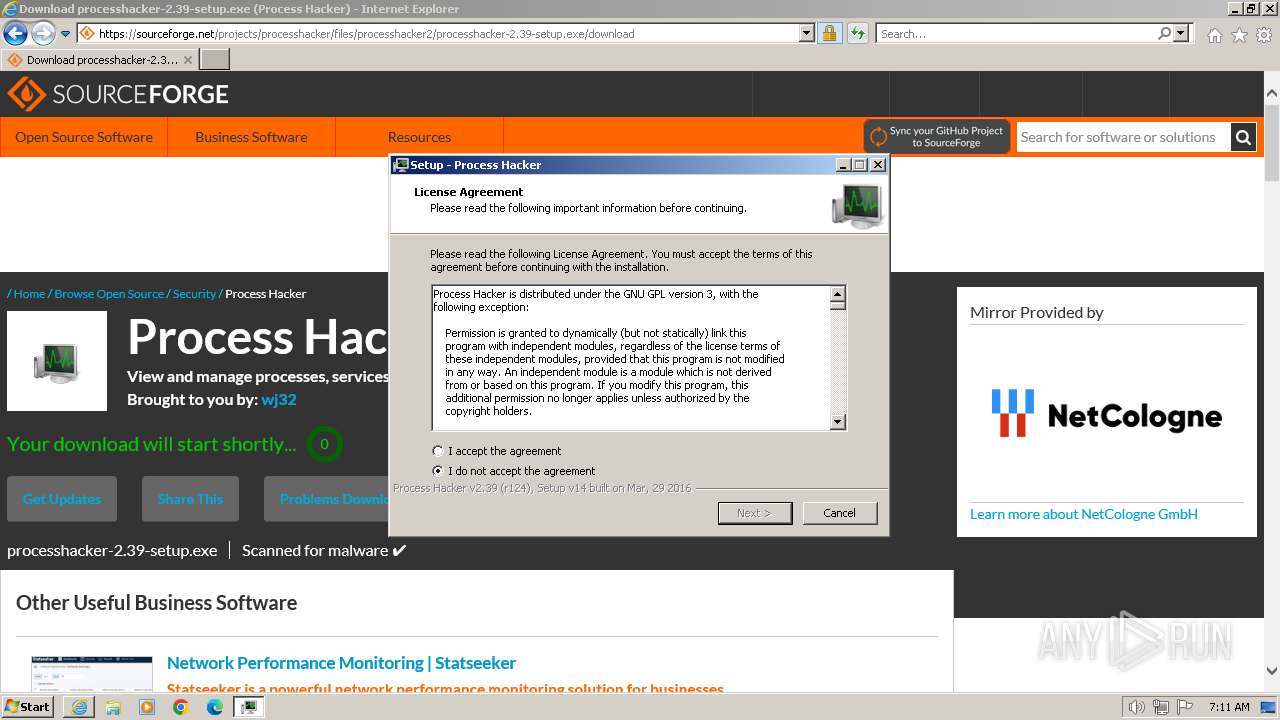
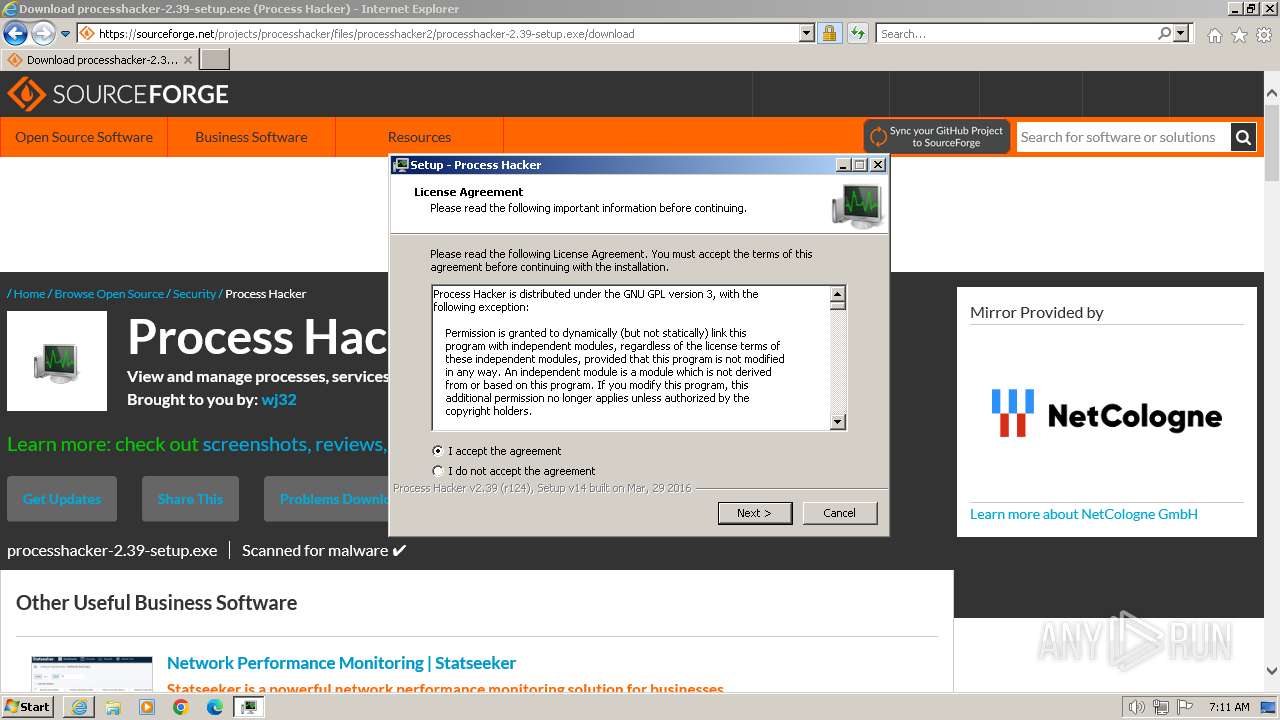
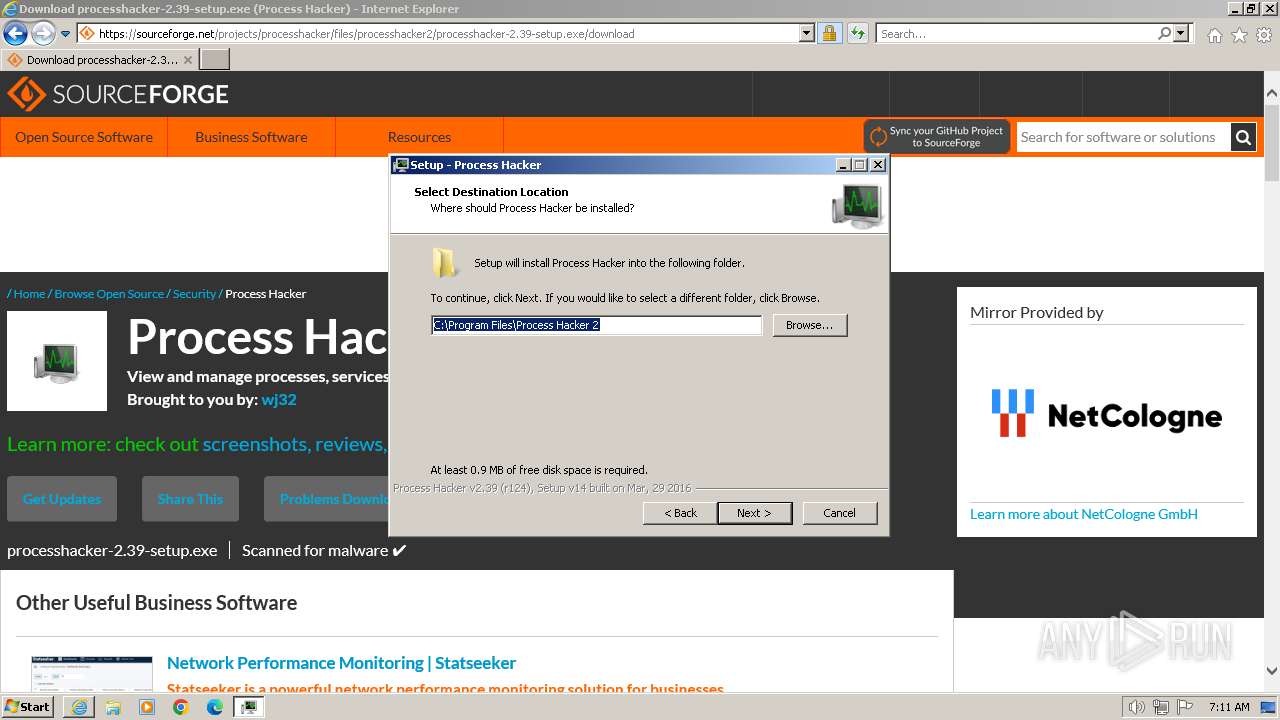
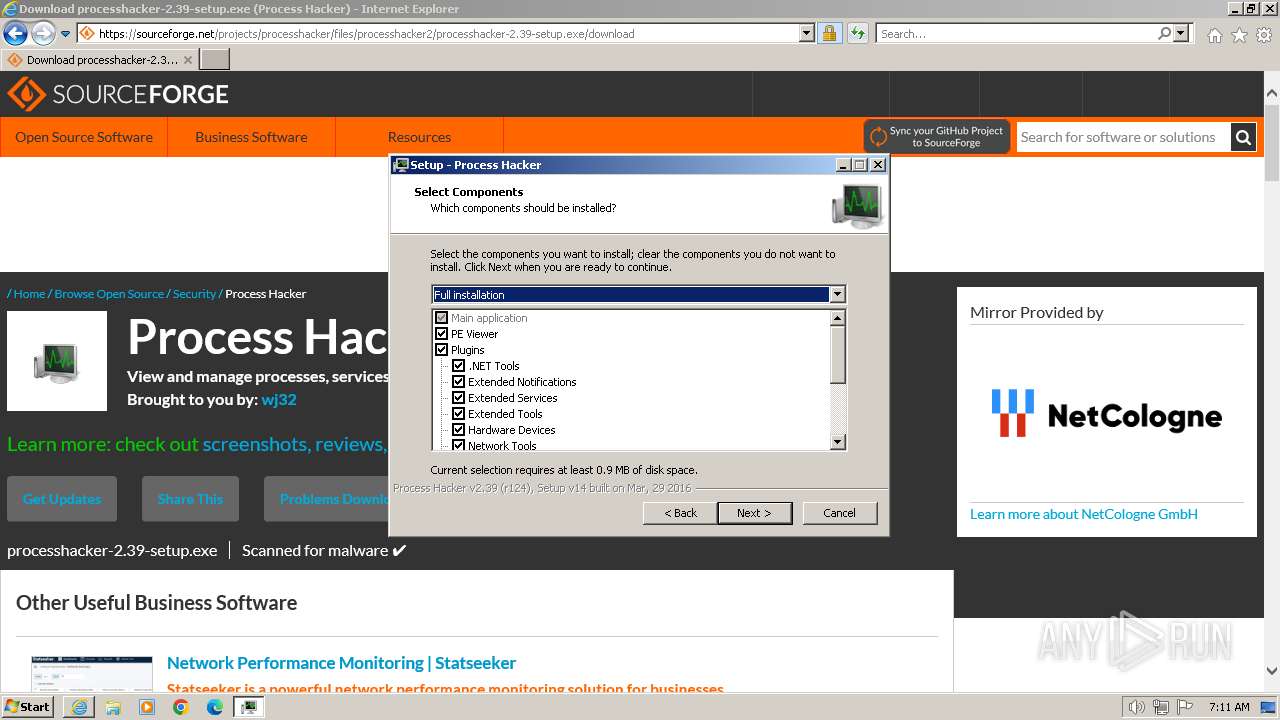
| URL: | https://sourceforge.net/projects/processhacker/files/processhacker2/processhacker-2.39-setup.exe/download |
| Full analysis: | https://app.any.run/tasks/cdde4b63-3405-4545-9ee9-0d57952c1aab |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2024, 07:08:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AD2610BB527018844065D32CB3B63136 |
| SHA1: | FB1AFD1628AB41BAF3FC2CD50A178DB34442089D |
| SHA256: | 4AE651B06A13AD6C3BE2D4A4B2710084B02B90BF86839A410D3E4AF3757C9874 |
| SSDEEP: | 3:N8HCGSuLAuUt6yAub1AuXKyA6i8VkvDLz:2iGnCt/915Pzi8VkvD/ |
MALICIOUS
Drops the executable file immediately after the start
- processhacker-2.39-setup.exe (PID: 876)
- processhacker-2.39-setup.exe (PID: 1956)
- processhacker-2.39-setup.tmp (PID: 2912)
SUSPICIOUS
Executable content was dropped or overwritten
- processhacker-2.39-setup.exe (PID: 876)
- processhacker-2.39-setup.exe (PID: 1956)
- processhacker-2.39-setup.tmp (PID: 2912)
Reads the Windows owner or organization settings
- processhacker-2.39-setup.tmp (PID: 2912)
Drops a system driver (possible attempt to evade defenses)
- processhacker-2.39-setup.tmp (PID: 2912)
Reads security settings of Internet Explorer
- ProcessHacker.exe (PID: 2856)
Reads the Internet Settings
- ProcessHacker.exe (PID: 2856)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 2856)
Process drops legitimate windows executable
- processhacker-2.39-setup.tmp (PID: 2912)
Checks Windows Trust Settings
- ProcessHacker.exe (PID: 2856)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 2040)
Application launched itself
- iexplore.exe (PID: 2040)
Executable content was dropped or overwritten
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 2040)
Create files in a temporary directory
- processhacker-2.39-setup.exe (PID: 876)
- processhacker-2.39-setup.exe (PID: 1956)
- processhacker-2.39-setup.tmp (PID: 2912)
Drops the executable file immediately after the start
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 2040)
Reads the computer name
- processhacker-2.39-setup.tmp (PID: 2316)
- ProcessHacker.exe (PID: 2856)
- processhacker-2.39-setup.tmp (PID: 2912)
Checks supported languages
- processhacker-2.39-setup.tmp (PID: 2316)
- processhacker-2.39-setup.exe (PID: 876)
- processhacker-2.39-setup.exe (PID: 1956)
- processhacker-2.39-setup.tmp (PID: 2912)
- ProcessHacker.exe (PID: 2856)
Creates files in the program directory
- processhacker-2.39-setup.tmp (PID: 2912)
Reads Environment values
- ProcessHacker.exe (PID: 2856)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 876 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe | iexplore.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Setup Exit code: 0 Version: 2.39 (r124) Modules
| |||||||||||||||
| 1956 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe" /SPAWNWND=$1023C /NOTIFYWND=$50204 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe | processhacker-2.39-setup.tmp | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Setup Exit code: 0 Version: 2.39 (r124) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://sourceforge.net/projects/processhacker/files/processhacker2/processhacker-2.39-setup.exe/download" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\AppData\Local\Temp\is-K043F.tmp\processhacker-2.39-setup.tmp" /SL5="$50204,1874675,150016,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-K043F.tmp\processhacker-2.39-setup.tmp | — | processhacker-2.39-setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
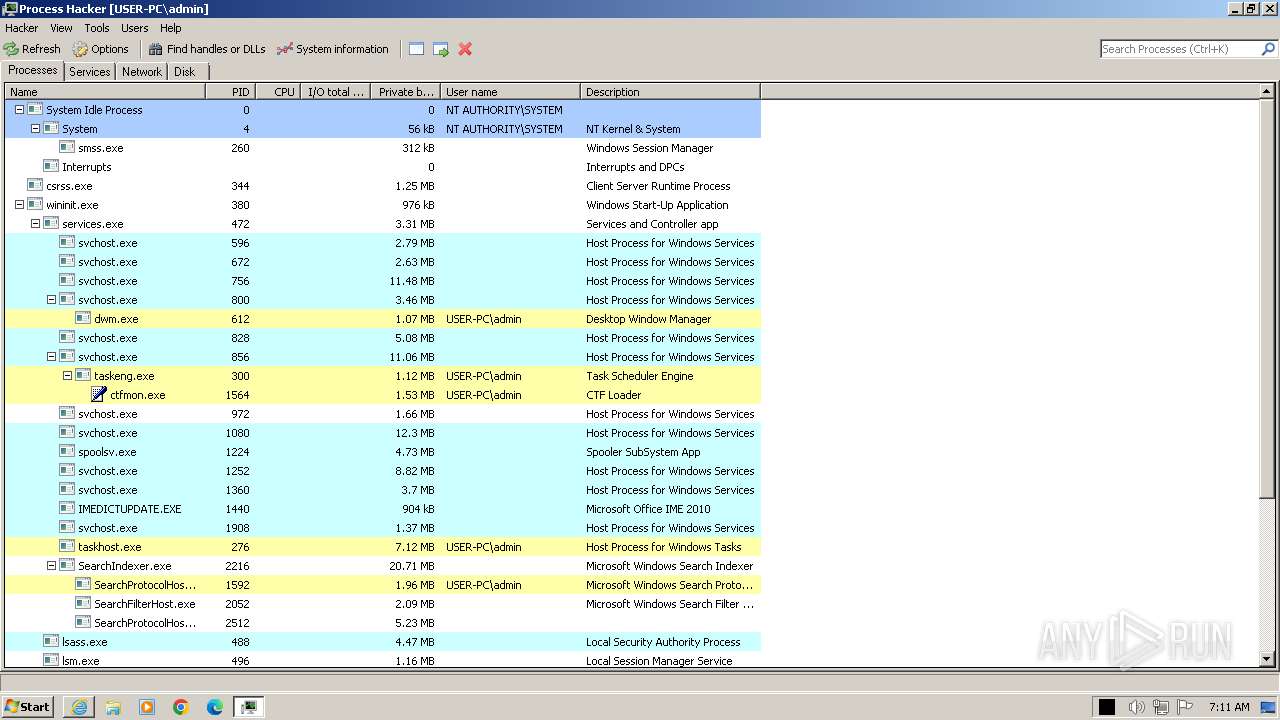
| 2856 | "C:\Program Files\Process Hacker 2\ProcessHacker.exe" | C:\Program Files\Process Hacker 2\ProcessHacker.exe | processhacker-2.39-setup.tmp | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 2912 | "C:\Users\admin\AppData\Local\Temp\is-2KHN9.tmp\processhacker-2.39-setup.tmp" /SL5="$2023E,1874675,150016,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\processhacker-2.39-setup.exe" /SPAWNWND=$1023C /NOTIFYWND=$50204 | C:\Users\admin\AppData\Local\Temp\is-2KHN9.tmp\processhacker-2.39-setup.tmp | processhacker-2.39-setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
36 656
Read events
36 514
Write events
134
Delete events
8
Modification events
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
38
Suspicious files
64
Text files
324
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:05C22BA005A9D97554BF65BF0E3629E7 | SHA256:B0600B1B82AB5F6829208C6B52869B2CDE962F93E4CD7608AFD350A2B8BECE8F | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\adsbanner[1].js | text | |
MD5:1A9F5B5D41007226049E6EF054C9F935 | SHA256:E3E69CC01AD15179EB67E1F90E1774ED5A5DA075F85420A1D9B01029B28B14DC | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\icon[1].png | image | |
MD5:2AE94FCF5B9699233B3D671BFB7EB0CD | SHA256:4853B6FB5D29D6D9DCCA39E796B1FCAEF057D592DA1BBDC9F068393E4EC5AAD9 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\download[1].htm | html | |
MD5:D6499B76E05FF672560708BD28A8A7BD | SHA256:61B2487CD39D76DB45D4B532A71DB5DA518232E38FA7FA8D2DD893DEB24061E7 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\lato[1].css | text | |
MD5:8F61F228AD51184B5F8BBBF14B436DF9 | SHA256:DA04907546EDDC4640039BB9EFBBB483D220B1E4EC553F9830A9510B7FF14899 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:DE13AF43765C4CD28AF824C3E81E2E5C | SHA256:C8B4A05D6F4AA251F6E238C94F568C2B05168B61F2267260BF0E601EF990BA39 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\L29VSDD5.txt | text | |
MD5:39CD3E135BB3F4CC1720BE5C6E92BFE0 | SHA256:515239D84F35D7A16D6CA429B6E2687FA8AA9614ADFBE46B2518570877A5193C | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\cmp[1].css | text | |
MD5:38C8ACF2B4EF7DEF65BACFB6E9A26E8E | SHA256:4BAAE150A27BC5716BA8F5160FBD2414F5B731C470D8EE0956612DAFA106E950 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:32EC33B0FB01AC1E9375DF20B52A52A9 | SHA256:BA5B977EC4C04062FB7DFD0540BE26F8B940B4C5193F26645B384D5F794AA5B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
141
DNS requests
49
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | iexplore.exe | GET | 200 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6f825234c2810feb | unknown | compressed | 4.66 Kb | unknown |
864 | iexplore.exe | GET | 200 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2f131cf452408714 | unknown | compressed | 4.66 Kb | unknown |
864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
864 | iexplore.exe | GET | 200 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1370d8f2dc7c184e | unknown | compressed | 65.2 Kb | unknown |
864 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
864 | iexplore.exe | GET | 200 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?02e66f896758e1a5 | unknown | compressed | 65.2 Kb | unknown |
864 | iexplore.exe | GET | 200 | 184.24.77.47:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgR%2B5rJNDRLPmf6wKNriwkmuQQ%3D%3D | unknown | binary | 503 b | unknown |
2040 | iexplore.exe | GET | 304 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?85105a2067e5fff2 | unknown | — | — | unknown |
2040 | iexplore.exe | GET | 304 | 23.32.238.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bb7a787b0c23a419 | unknown | — | — | unknown |
2040 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
864 | iexplore.exe | 172.64.150.145:443 | sourceforge.net | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
864 | iexplore.exe | 23.32.238.235:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
864 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
864 | iexplore.exe | 172.64.147.47:443 | a.fsdn.com | CLOUDFLARENET | US | unknown |
864 | iexplore.exe | 87.230.98.76:443 | d.delivery.consentmanager.net | PlusServer GmbH | DE | unknown |
864 | iexplore.exe | 212.102.56.181:443 | cdn.consentmanager.net | Datacamp Limited | DE | unknown |
864 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sourceforge.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a.fsdn.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
d.delivery.consentmanager.net |
| unknown |
cdn.consentmanager.net |
| malicious |
x1.c.lencr.org |
| whitelisted |
c.sf-syn.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
864 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
864 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |