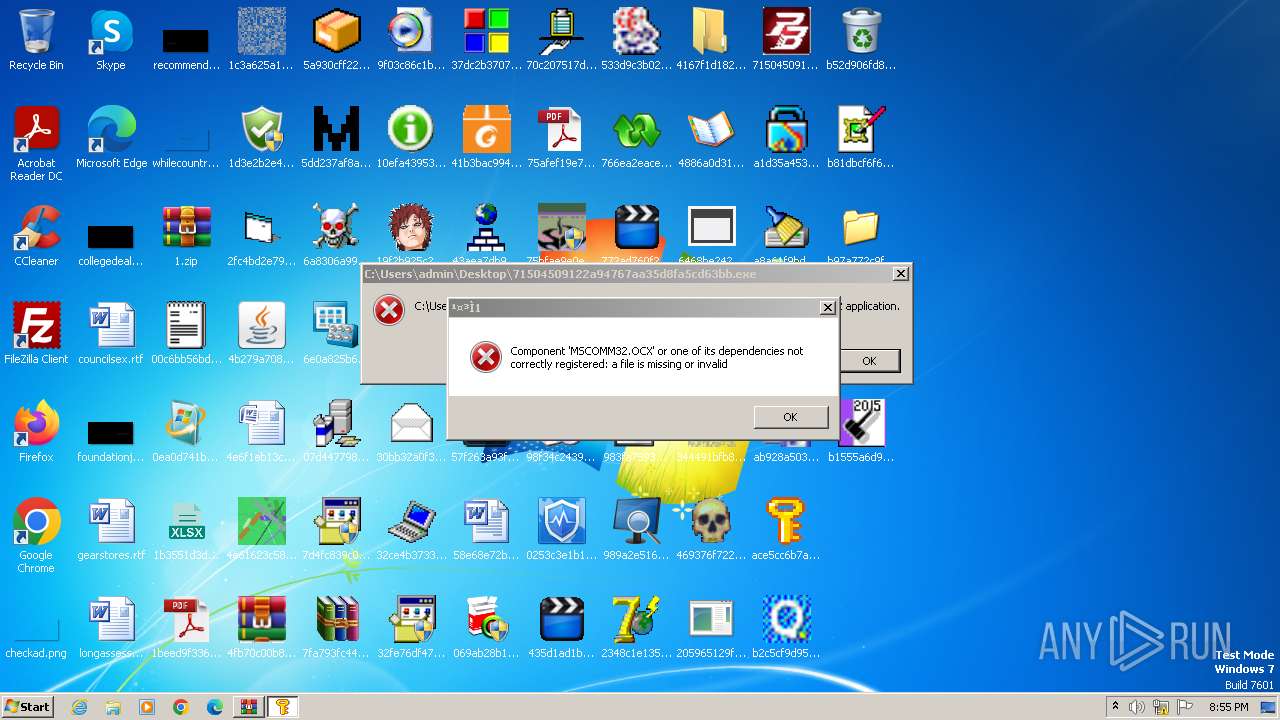
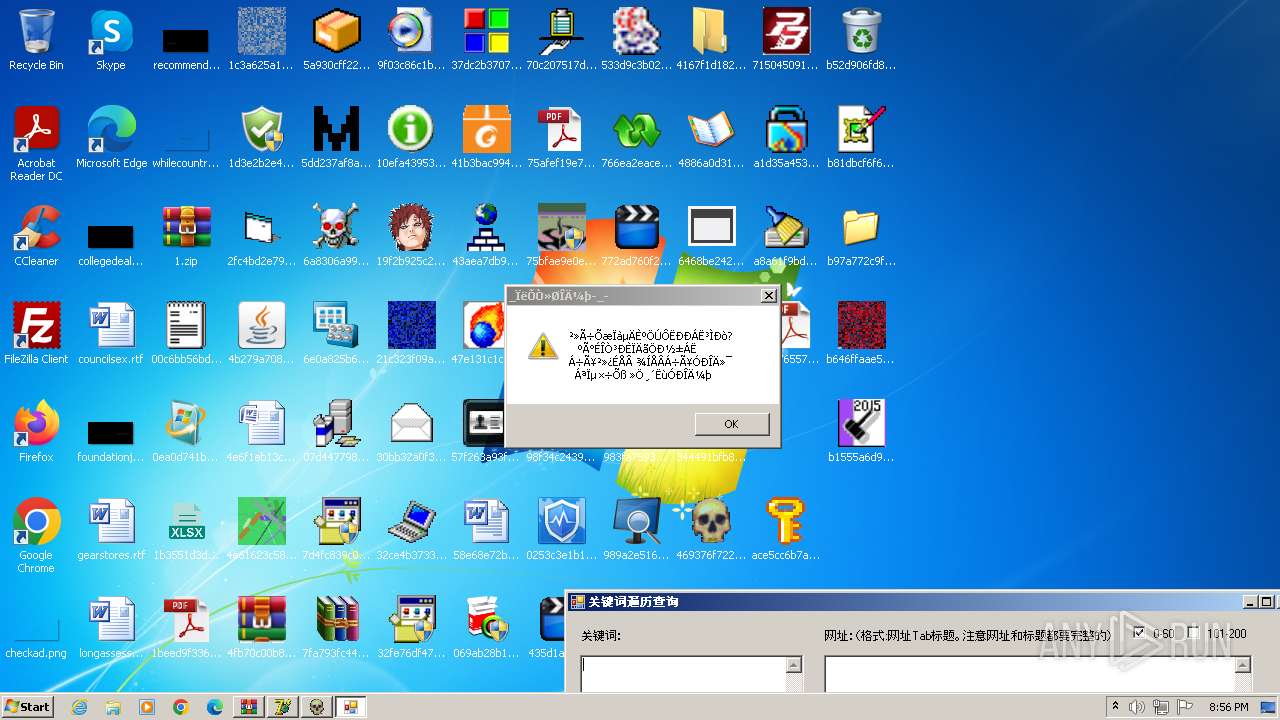
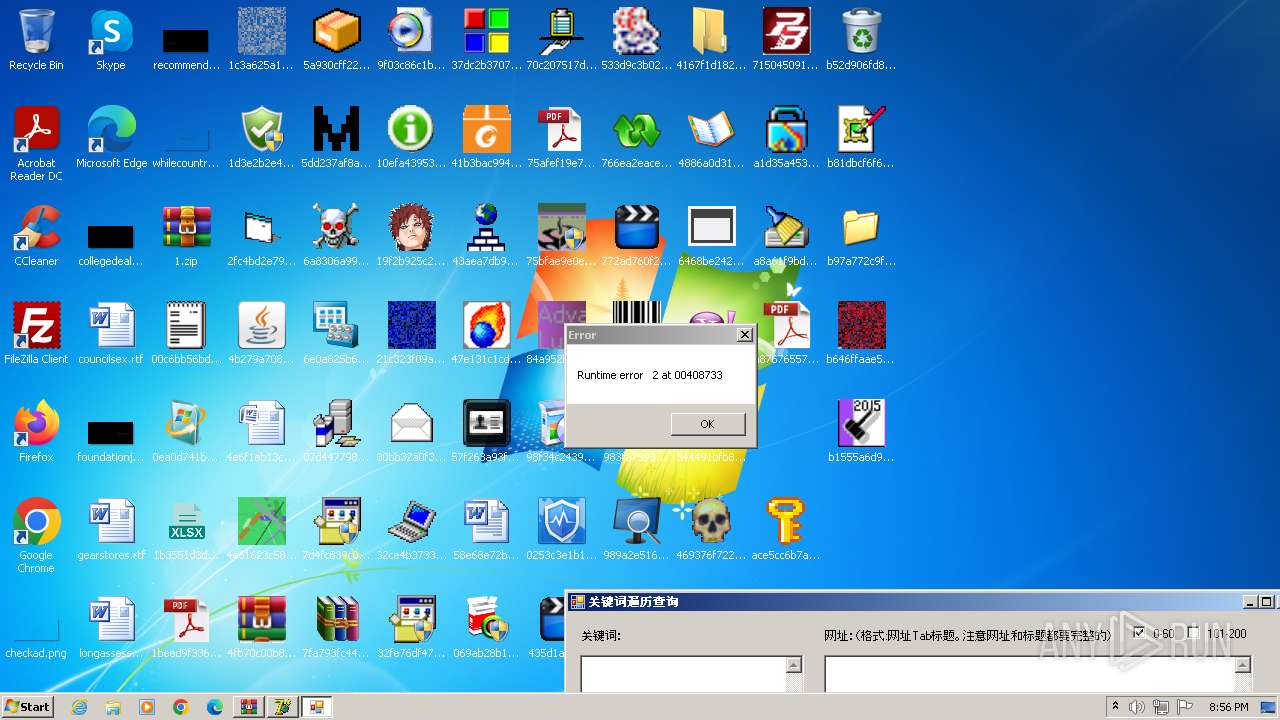
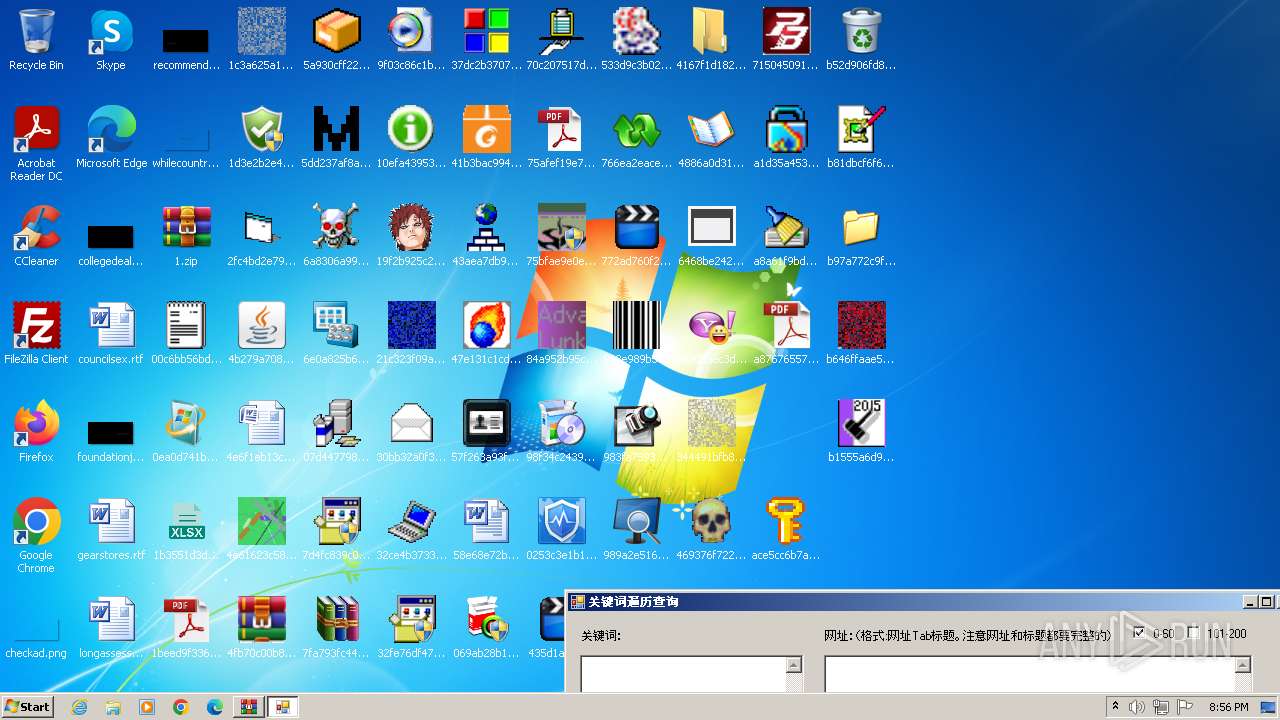
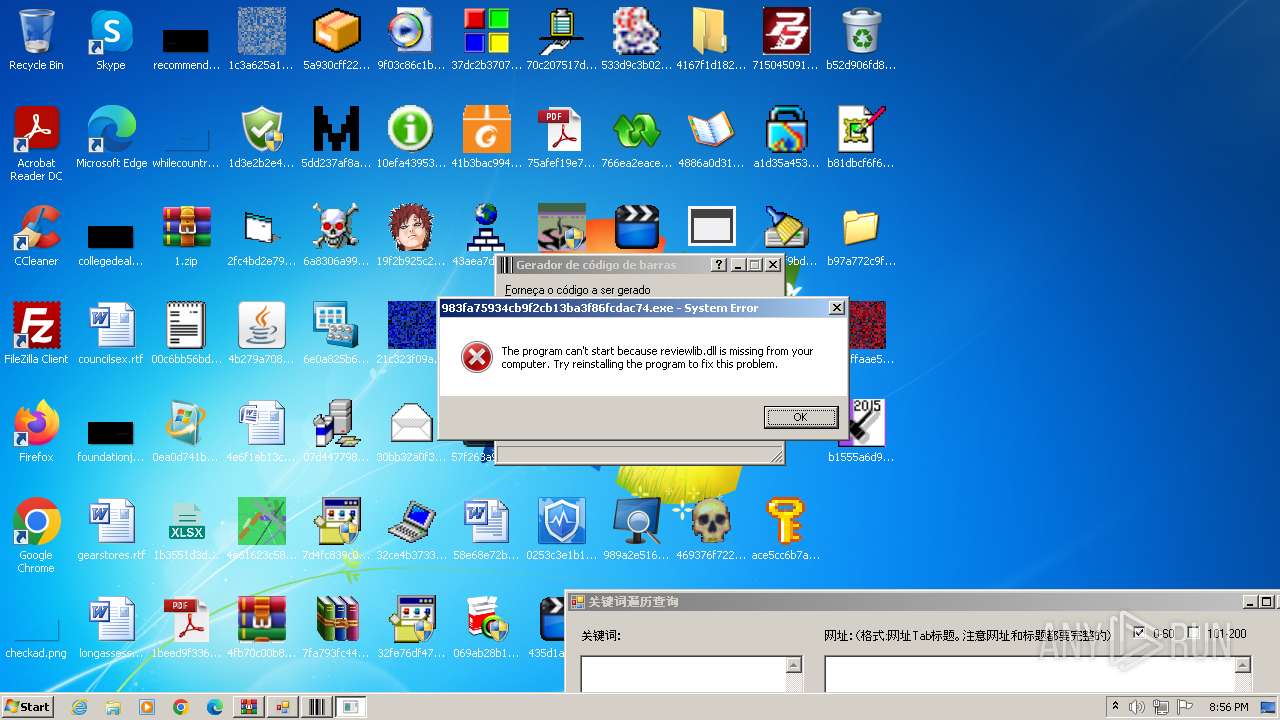
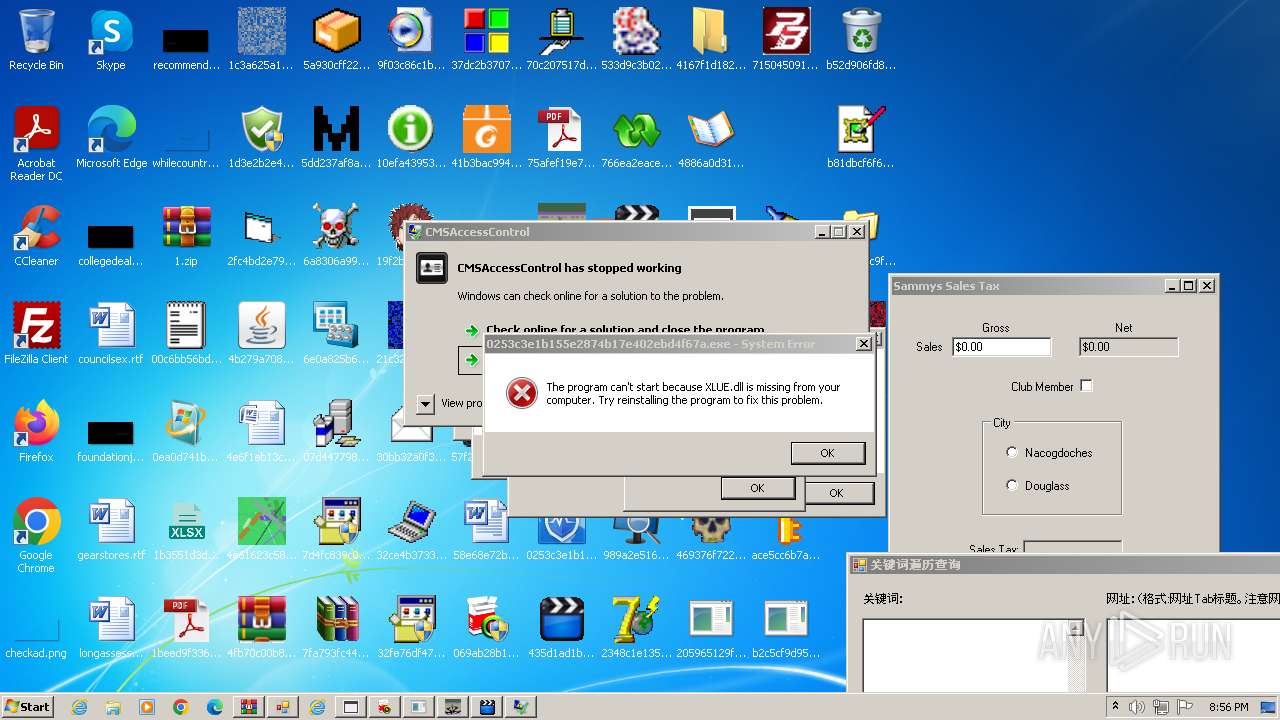
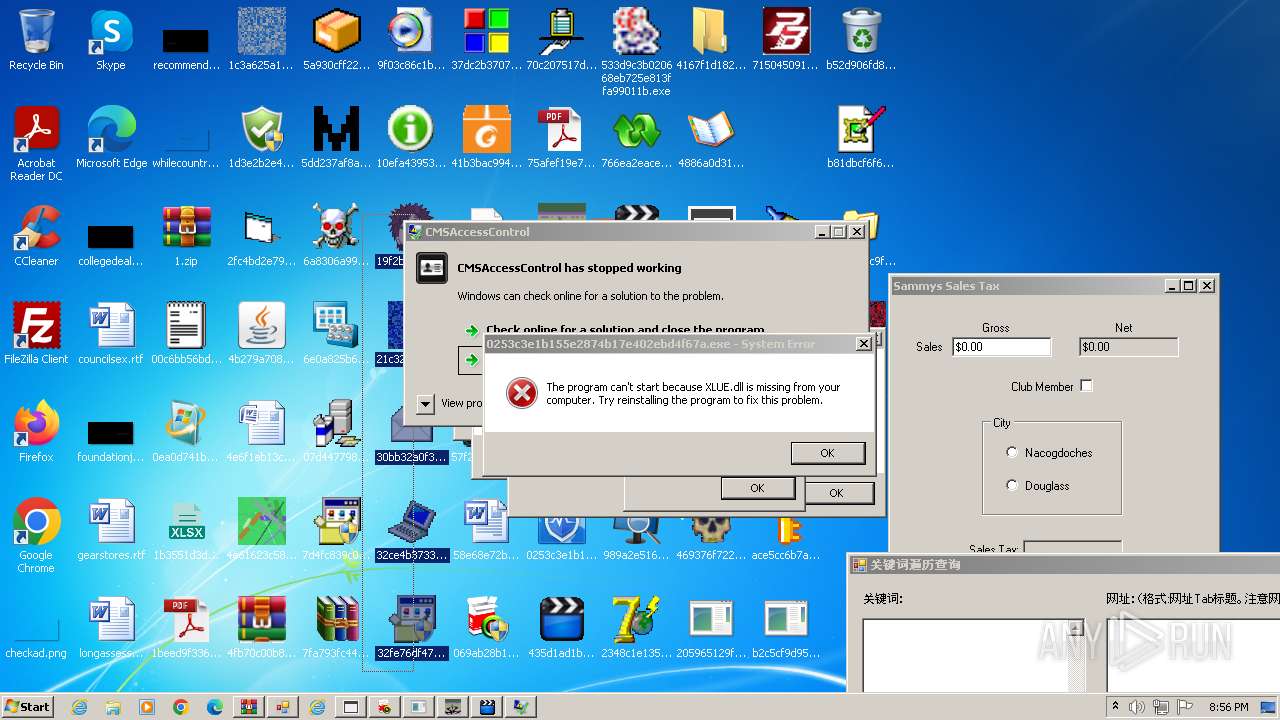
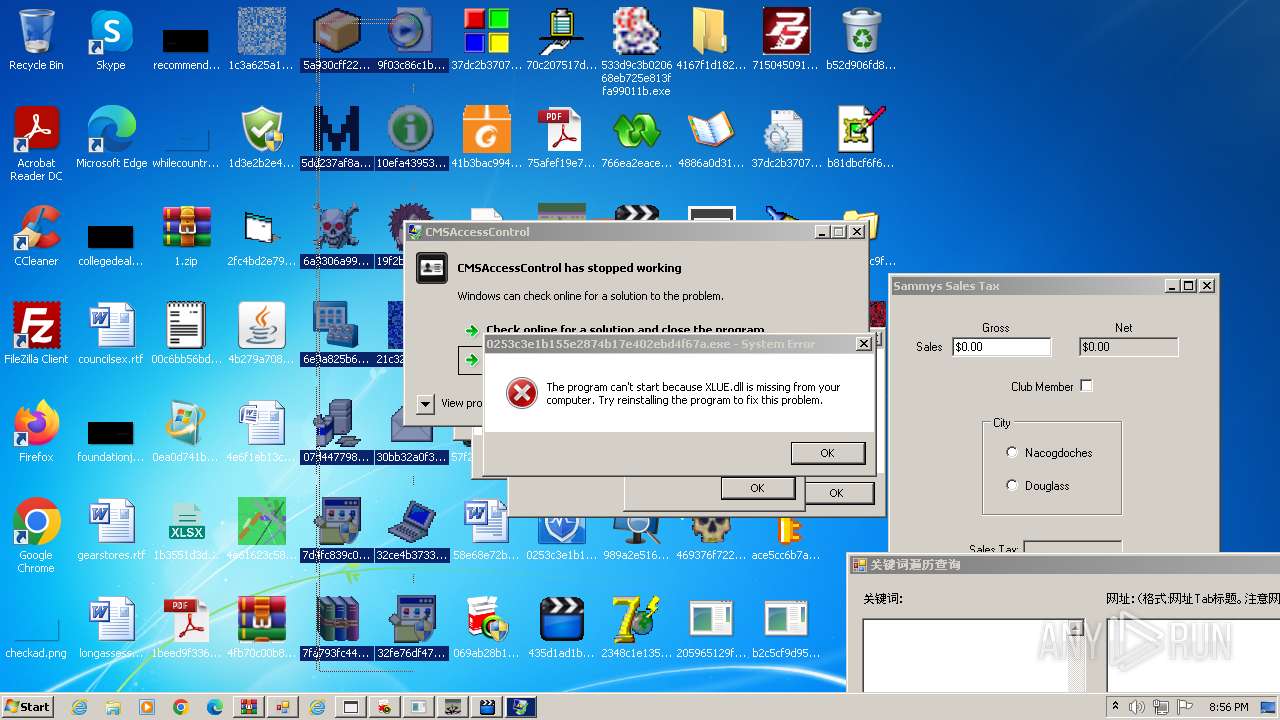
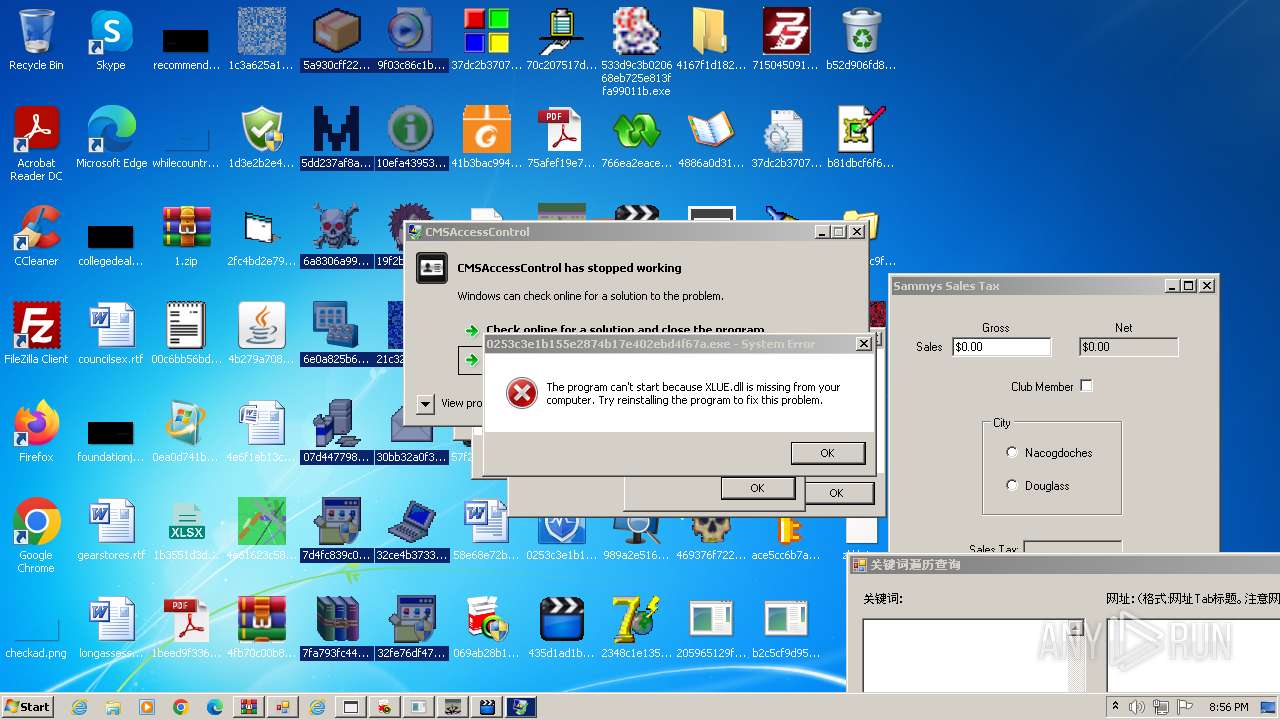
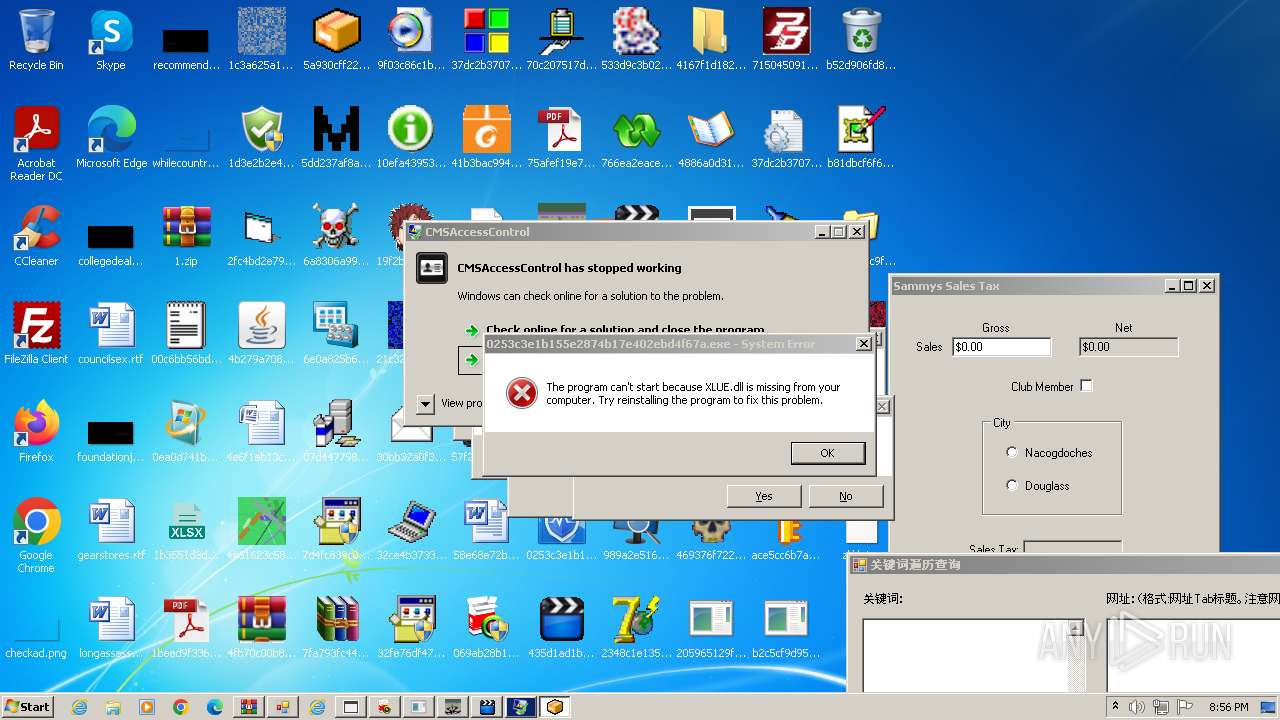
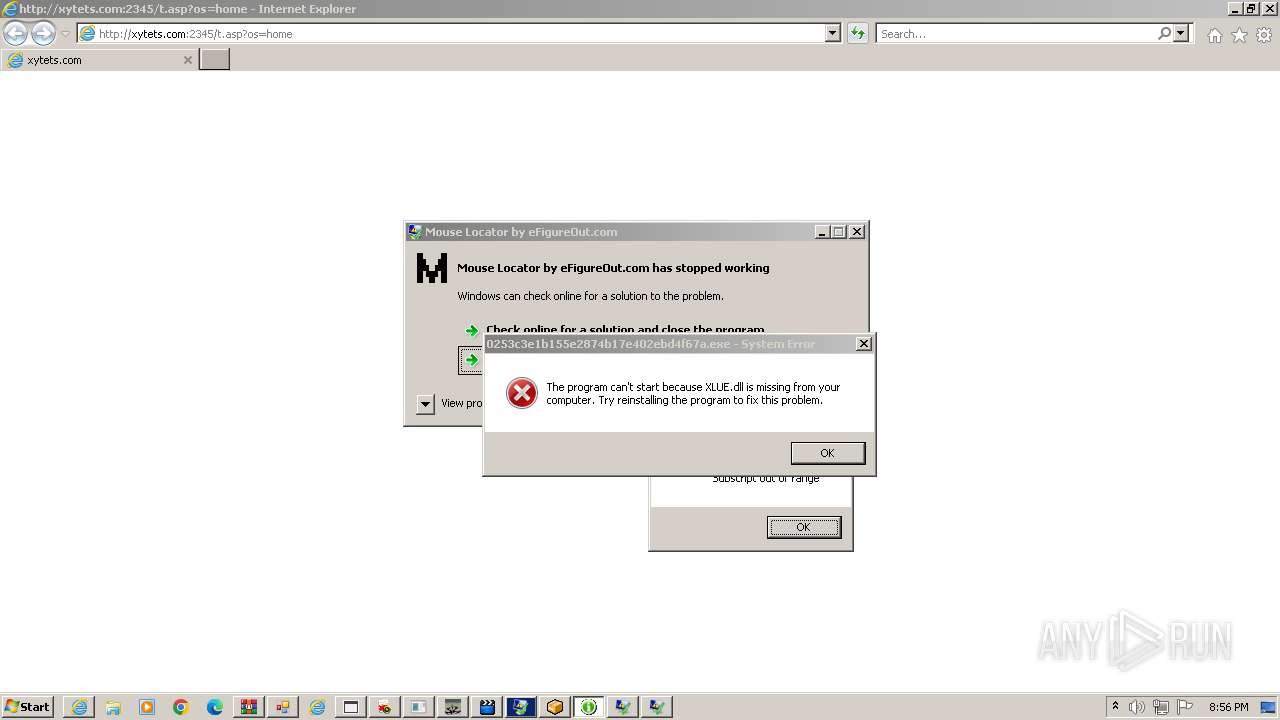
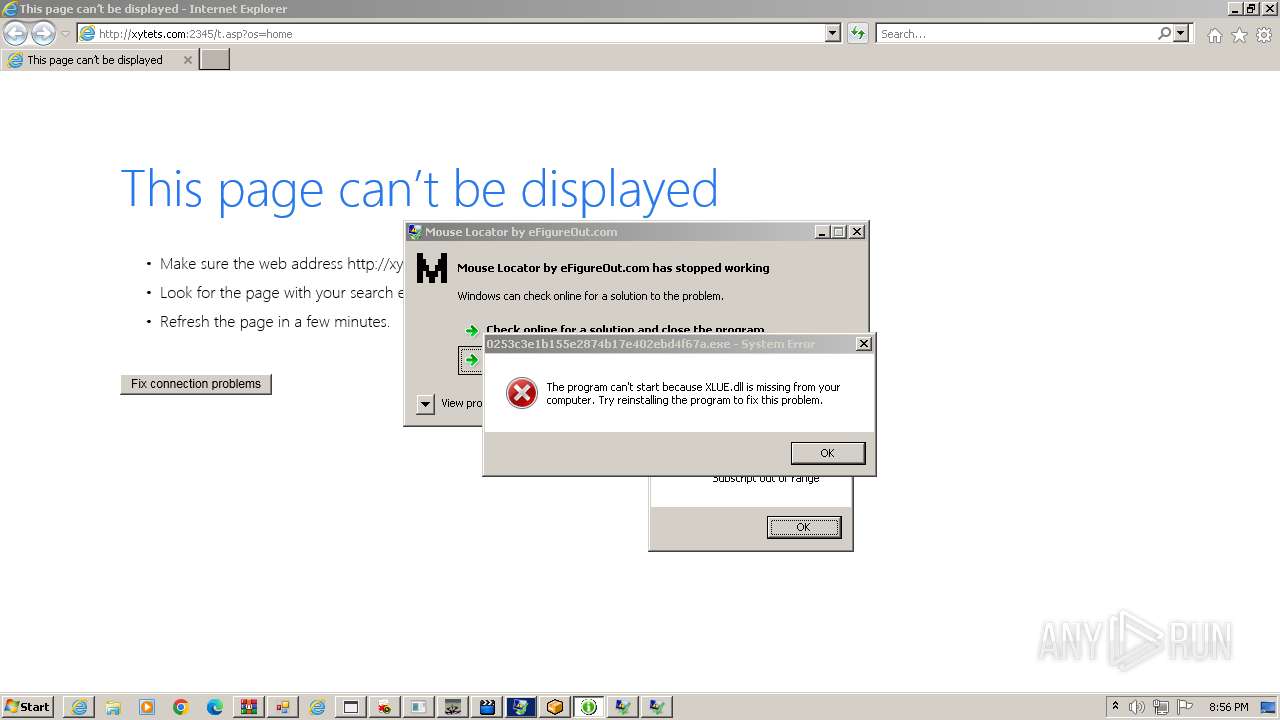
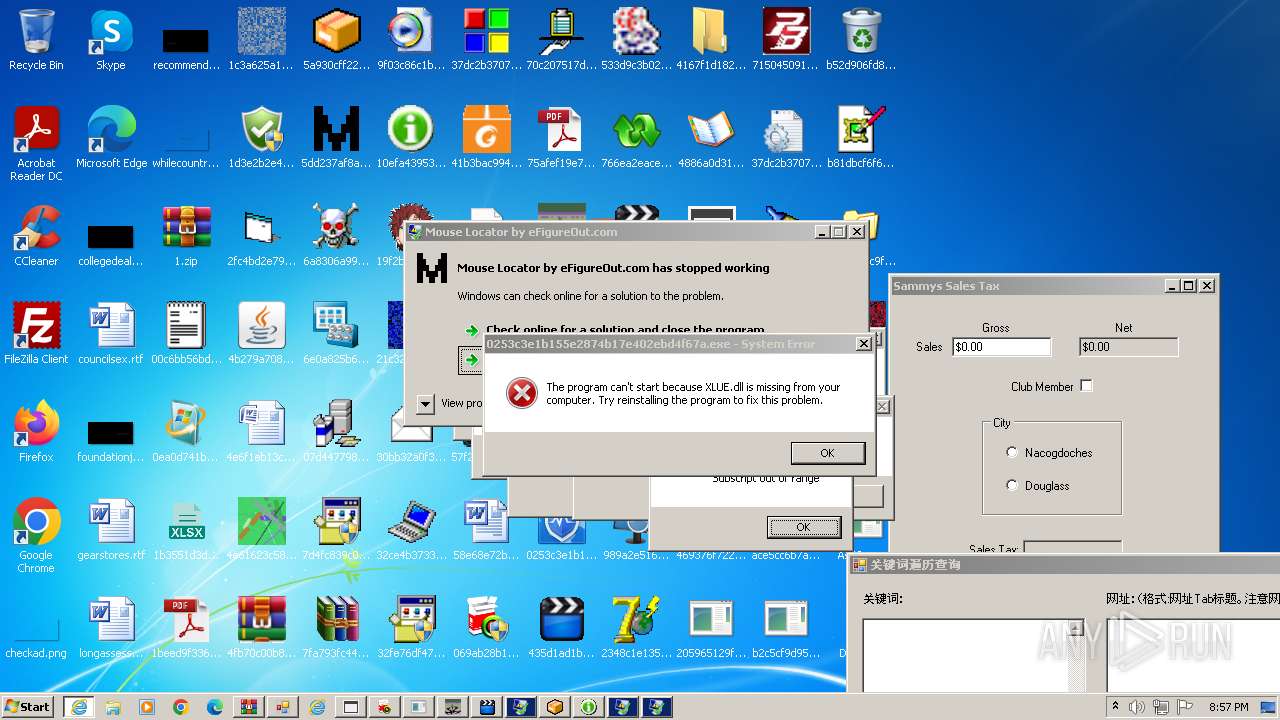
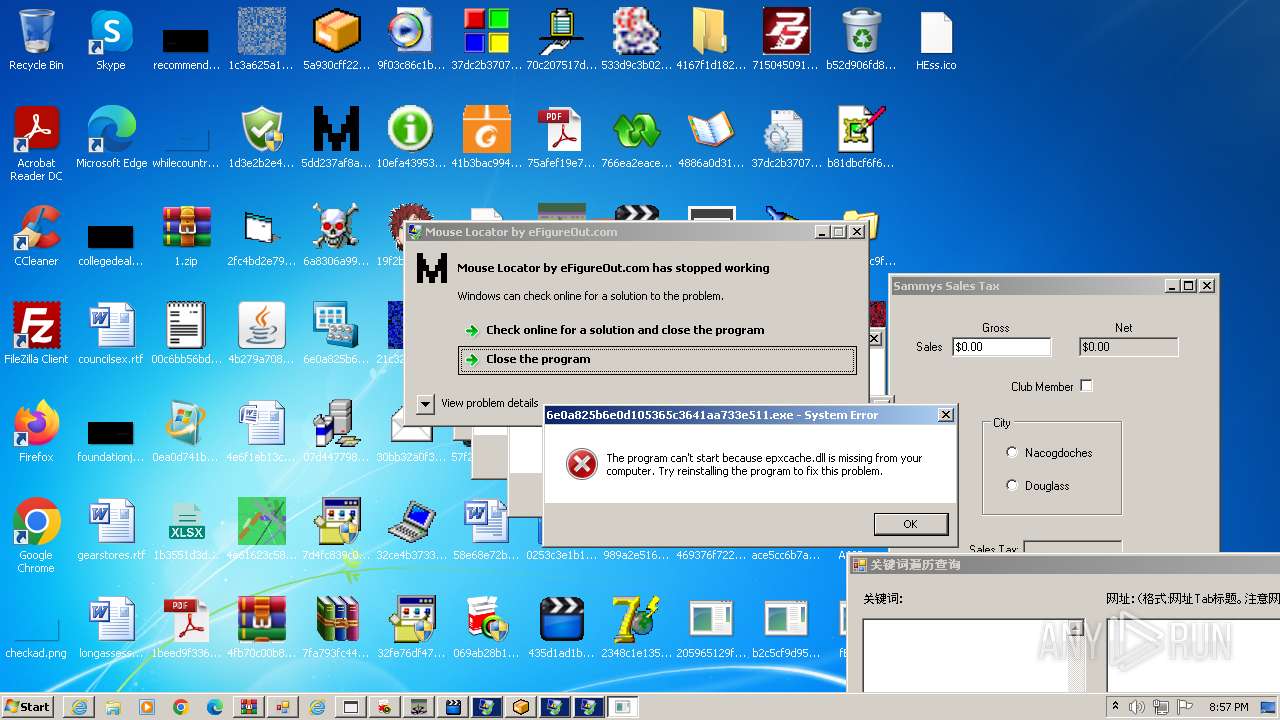
| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/10f78566-627e-4c1e-9889-b865ff0f1511 |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | December 02, 2023, 20:55:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6ECDCEEEEC01C7BA211B7E8E7B450924 |
| SHA1: | 215CE6912E1698D83E616B0F6EC71B06A9677E07 |
| SHA256: | 4AC88919133B624C40B0A650835337C801773DA77C052FCB2F0C3C33FD8DCDB2 |
| SSDEEP: | 98304:bCEIJ6aOLBqwihkip2yUSkpxXsN/LqgelHDKVYm2H4tH8miGAZGcHnkReCRGZl7D:cizYwBENy |
MALICIOUS
Drops the executable file immediately after the start
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- cmd.exe (PID: 2132)
- Au_.exe (PID: 2292)
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 98f34c24392acb67fb35b0ef87ed140d.exe (PID: 2028)
- QyswEEgY.exe (PID: 1756)
- 7d4fc839c0cc8f2a9bedf4d9d2bae755.exe (PID: 3472)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
- 7fa793fc444b9cab0dc02d8a0bb707a3.exe (PID: 3104)
- 51f574c70b4aa.exe (PID: 2404)
- 9f03c86c1b4c02bb2de070fd0a45ef49.exe (PID: 924)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- yikut.exe (PID: 2780)
- seiif.exe (PID: 4248)
- yuuax.exe (PID: 3524)
- yvdoey.exe (PID: 900)
- hxqav.exe (PID: 4560)
- wiiza.exe (PID: 5848)
- buuoxab.exe (PID: 5240)
- nuvik.exe (PID: 5552)
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 5388)
- ceaosa.exe (PID: 2736)
- 32ce4b3733014440d770a8d3b81544d2.exe (PID: 3268)
- hrzuaf.exe (PID: 5832)
Changes Security Center notification settings
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
Changes appearance of the Explorer extensions
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- yikut.exe (PID: 2780)
- seiif.exe (PID: 4248)
- yuuax.exe (PID: 3524)
- yvdoey.exe (PID: 900)
Runs injected code in another process
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- 344491bfb811ee82b644bc02e3287893.exe (PID: 3260)
- explorer.exe (PID: 1388)
Application was injected by another process
- explorer.exe (PID: 1388)
- taskeng.exe (PID: 288)
- dwm.exe (PID: 932)
- conhost.exe (PID: 2184)
- ctfmon.exe (PID: 1804)
- conhost.exe (PID: 300)
- conhost.exe (PID: 4252)
- WerFault.exe (PID: 4652)
- conhost.exe (PID: 4636)
- WerFault.exe (PID: 4740)
- conhost.exe (PID: 2476)
- conhost.exe (PID: 544)
UAC/LUA settings modification
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
Connects to the CnC server
- Au_.exe (PID: 2292)
- explorer.exe (PID: 1388)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1236)
Changes the autorun value in the registry
- nSoAoQMI.exe (PID: 2060)
- explorer.exe (PID: 1388)
Uses sleep, probably for evasion detection (SCRIPT)
- cscript.exe (PID: 968)
- cscript.exe (PID: 1016)
- cscript.exe (PID: 2740)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 3576)
- cscript.exe (PID: 1628)
- cscript.exe (PID: 2716)
- cscript.exe (PID: 1436)
- cscript.exe (PID: 3848)
- cscript.exe (PID: 2548)
- cscript.exe (PID: 2416)
- cscript.exe (PID: 3968)
- cscript.exe (PID: 1904)
- cscript.exe (PID: 448)
- cscript.exe (PID: 4340)
- cscript.exe (PID: 4144)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4532)
- cscript.exe (PID: 4940)
- cscript.exe (PID: 5136)
- cscript.exe (PID: 5308)
- cscript.exe (PID: 5520)
- cscript.exe (PID: 5696)
- cscript.exe (PID: 6096)
- cscript.exe (PID: 5980)
- cscript.exe (PID: 4496)
- cscript.exe (PID: 4148)
- cscript.exe (PID: 4708)
- cscript.exe (PID: 4924)
- cscript.exe (PID: 5152)
- cscript.exe (PID: 5224)
- cscript.exe (PID: 5384)
- cscript.exe (PID: 5892)
- cscript.exe (PID: 2224)
- cscript.exe (PID: 6124)
- cscript.exe (PID: 4728)
- cscript.exe (PID: 4964)
- cscript.exe (PID: 5544)
- cscript.exe (PID: 6060)
- cscript.exe (PID: 1436)
- cscript.exe (PID: 1212)
- cscript.exe (PID: 2316)
- cscript.exe (PID: 5928)
- cscript.exe (PID: 4720)
- cscript.exe (PID: 4712)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 5512)
- cscript.exe (PID: 2404)
- cscript.exe (PID: 608)
- cscript.exe (PID: 4628)
- cscript.exe (PID: 3760)
- cscript.exe (PID: 2696)
- cscript.exe (PID: 4568)
- cscript.exe (PID: 5060)
- cscript.exe (PID: 5736)
- cscript.exe (PID: 2716)
- cscript.exe (PID: 2828)
- cscript.exe (PID: 3000)
- cscript.exe (PID: 2468)
- cscript.exe (PID: 5164)
- cscript.exe (PID: 5296)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 4324)
- cscript.exe (PID: 5944)
- cscript.exe (PID: 3976)
- cscript.exe (PID: 2076)
- cscript.exe (PID: 2220)
- cscript.exe (PID: 4156)
- cscript.exe (PID: 2476)
- cscript.exe (PID: 4180)
- cscript.exe (PID: 6032)
- cscript.exe (PID: 5344)
- cscript.exe (PID: 4832)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 5080)
- cscript.exe (PID: 4484)
- cscript.exe (PID: 4360)
- cscript.exe (PID: 4296)
- cscript.exe (PID: 5240)
- cscript.exe (PID: 5720)
- cscript.exe (PID: 668)
- cscript.exe (PID: 2128)
- cscript.exe (PID: 3980)
- cscript.exe (PID: 5208)
- cscript.exe (PID: 4872)
- cscript.exe (PID: 5432)
- cscript.exe (PID: 4524)
- cscript.exe (PID: 3272)
- cscript.exe (PID: 6080)
- cscript.exe (PID: 6004)
- cscript.exe (PID: 4400)
- cscript.exe (PID: 4360)
- cscript.exe (PID: 4384)
- cscript.exe (PID: 4244)
- cscript.exe (PID: 5272)
- cscript.exe (PID: 5908)
- cscript.exe (PID: 2140)
- cscript.exe (PID: 3552)
- cscript.exe (PID: 4228)
- cscript.exe (PID: 5124)
- cscript.exe (PID: 4688)
- cscript.exe (PID: 5668)
- cscript.exe (PID: 2236)
Actions looks like stealing of personal data
- 51f574c70b4aa.exe (PID: 2404)
- QyswEEgY.exe (PID: 1756)
Steals credentials from Web Browsers
- 51f574c70b4aa.exe (PID: 2404)
Starts NET.EXE for service management
- 32ce4b3733014440d770a8d3b81544d2.exe (PID: 3268)
- net.exe (PID: 128)
- net.exe (PID: 4472)
Modifies files in the Chrome extension folder
- 51f574c70b4aa.exe (PID: 2404)
Changes the login/logoff helper path in the registry
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
Probably malicious OneNote attachment is found
- QyswEEgY.exe (PID: 1756)
SIMDA has been detected (SURICATA)
- explorer.exe (PID: 1388)
SHIZ has been detected (SURICATA)
- explorer.exe (PID: 1388)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 2980)
- explorer.exe (PID: 1388)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2980)
- explorer.exe (PID: 1388)
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- cmd.exe (PID: 2132)
- 98f34c24392acb67fb35b0ef87ed140d.exe (PID: 2028)
Starts itself from another location
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 5388)
Starts CMD.EXE for commands execution
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 43aea7db92460a8baf31acdcd1a3bb88.exe (PID: 2620)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2088)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2232)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3580)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1872)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2428)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1604)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3860)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4208)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5588)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5768)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4292)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5504)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5704)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4276)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4888)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5356)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3500)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4168)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5244)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5112)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5616)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2632)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4148)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2920)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1128)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3152)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5048)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5512)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4280)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4896)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4172)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2736)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3508)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2684)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5712)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5324)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1656)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3084)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4268)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4624)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5700)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5480)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3372)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3600)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5440)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4288)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3756)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5876)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 644)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5240)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5608)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3188)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2948)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4328)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3760)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5776)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2140)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3800)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6136)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3436)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4296)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4408)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4164)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 300)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4528)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5308)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3848)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3544)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5964)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2476)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6032)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5804)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 448)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5772)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5228)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2080)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5408)
Executing commands from a ".bat" file
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2088)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2232)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3580)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1872)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2428)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1604)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3860)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4208)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5588)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5768)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4292)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5504)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5704)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4276)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4888)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5356)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3500)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4168)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5112)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5616)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5244)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2632)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2920)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4148)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3152)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1128)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5048)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5512)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4280)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4172)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4896)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2736)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2684)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5712)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3508)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5324)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4268)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1656)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3084)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4624)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5700)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5480)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3372)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3600)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5440)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4288)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3756)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5876)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 644)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4328)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5608)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3188)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5240)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3760)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5776)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2948)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2140)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6136)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3800)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4408)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4296)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3436)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4164)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 300)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4528)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5308)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3848)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3544)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5964)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2476)
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6032)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 448)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5804)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5772)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5228)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5408)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2080)
Reads the Internet Settings
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- Au_.exe (PID: 2292)
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 43aea7db92460a8baf31acdcd1a3bb88.exe (PID: 2620)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- bkgrnd.exe (PID: 1528)
- 51f574c70b4aa.exe (PID: 2404)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
- 9f03c86c1b4c02bb2de070fd0a45ef49.exe (PID: 924)
- yikut.exe (PID: 2780)
- seiif.exe (PID: 4248)
- yuuax.exe (PID: 3524)
- yvdoey.exe (PID: 900)
Uses RUNDLL32.EXE to load library
- umwoe.exe (PID: 3632)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1036)
The process checks if it is being run in the virtual environment
- 344491bfb811ee82b644bc02e3287893.exe (PID: 3260)
- 21c323f09a68551f40c6d5e6cb74412b.exe (PID: 3000)
- explorer.exe (PID: 1388)
The process creates files with name similar to system file names
- Au_.exe (PID: 2292)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
Changes the title of the Internet Explorer window
- Au_.exe (PID: 2292)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
Malware-specific behavior (creating "System.dll" in Temp)
- Au_.exe (PID: 2292)
Changes the Home page of Internet Explorer
- Au_.exe (PID: 2292)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
Uses ATTRIB.EXE to modify file attributes
- 43aea7db92460a8baf31acdcd1a3bb88.exe (PID: 2620)
Uses REG/REGEDIT.EXE to modify registry
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2088)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2232)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3580)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1872)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2428)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1604)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4208)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3860)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5588)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5768)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4292)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5504)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5704)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4888)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4276)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5356)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3500)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4168)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5112)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5616)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5244)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2632)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2920)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4148)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1128)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3152)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5048)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5512)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4280)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4172)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4896)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2736)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2684)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5712)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3508)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5324)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1656)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4268)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4624)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3084)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5700)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5480)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3372)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3600)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5440)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4288)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3756)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3596)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5876)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 644)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5240)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4328)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3188)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5608)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2628)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3760)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5776)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2948)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5124)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3800)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2140)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6136)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4408)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4296)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3436)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4164)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5344)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 300)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4528)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5308)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3848)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3544)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5964)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2476)
- cmd.exe (PID: 1088)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6032)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 448)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5804)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5772)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5228)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5612)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2080)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5408)
The process executes VB scripts
- cmd.exe (PID: 1848)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 3244)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 3048)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 4444)
- cmd.exe (PID: 4644)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 4852)
- cmd.exe (PID: 5420)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 5620)
- cmd.exe (PID: 5820)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 2584)
- cmd.exe (PID: 4336)
- cmd.exe (PID: 4752)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 5540)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 5708)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 4168)
- cmd.exe (PID: 4908)
- cmd.exe (PID: 4516)
- cmd.exe (PID: 5828)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 4260)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 4136)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 6008)
- cmd.exe (PID: 5908)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 4340)
- cmd.exe (PID: 1840)
- cmd.exe (PID: 4432)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 5140)
- cmd.exe (PID: 5644)
- cmd.exe (PID: 752)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 3256)
- cmd.exe (PID: 4764)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 4676)
- cmd.exe (PID: 240)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 6092)
- cmd.exe (PID: 5576)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 5480)
- cmd.exe (PID: 4288)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 6000)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 3596)
- cmd.exe (PID: 3860)
- cmd.exe (PID: 4728)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 5860)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 4144)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 5224)
- cmd.exe (PID: 5108)
- cmd.exe (PID: 4140)
- cmd.exe (PID: 5616)
- cmd.exe (PID: 1436)
- cmd.exe (PID: 1604)
- cmd.exe (PID: 3440)
- cmd.exe (PID: 5520)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 668)
- cmd.exe (PID: 4532)
- cmd.exe (PID: 3808)
- cmd.exe (PID: 4828)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 5292)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 300)
- cmd.exe (PID: 952)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 5888)
- cmd.exe (PID: 2508)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 4388)
- cmd.exe (PID: 4404)
- cmd.exe (PID: 5432)
- cmd.exe (PID: 4388)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 3700)
- cmd.exe (PID: 4192)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 5284)
- cmd.exe (PID: 1656)
- cmd.exe (PID: 5164)
- cmd.exe (PID: 544)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 1876)
- cmd.exe (PID: 5340)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 4368)
- cmd.exe (PID: 368)
- cmd.exe (PID: 5908)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 4176)
- cmd.exe (PID: 5412)
- cmd.exe (PID: 4416)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 5440)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 3756)
- cmd.exe (PID: 3596)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 5820)
- cmd.exe (PID: 3116)
- cmd.exe (PID: 5832)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 5804)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 5712)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 6056)
- cmd.exe (PID: 5164)
- cmd.exe (PID: 4872)
- cmd.exe (PID: 5924)
- cmd.exe (PID: 5604)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 2364)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 5324)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 5760)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 5888)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 3520)
Reads security settings of Internet Explorer
- bkgrnd.exe (PID: 1528)
Reads settings of System Certificates
- bkgrnd.exe (PID: 1528)
Checks Windows Trust Settings
- bkgrnd.exe (PID: 1528)
Connects to unusual port
- nSoAoQMI.exe (PID: 2060)
- QyswEEgY.exe (PID: 1756)
- 9f03c86c1b4c02bb2de070fd0a45ef49.exe (PID: 924)
- yikut.exe (PID: 2780)
- yuuax.exe (PID: 3524)
- seiif.exe (PID: 4248)
Changes the desktop background image
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
The process verifies whether the antivirus software is installed
- 21c323f09a68551f40c6d5e6cb74412b.exe (PID: 3000)
The process executes via Task Scheduler
- IEMontior.exe (PID: 4716)
Uses TASKKILL.EXE to kill process
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
Application launched itself
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 3404)
INFO
Reads the Internet Settings
- explorer.exe (PID: 1388)
Manual execution by a user
- 71504509122a94767aa35d8fa5cd63bb.exe (PID: 1640)
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- a8a61f9bd2c23c6b2097f44199dc1685.exe (PID: 2956)
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- wmpnscfg.exe (PID: 4064)
- 205965129fc9e40e8c75ec62b28a32e7.exe (PID: 3504)
- 469376f722271ca46c61cd3d8e6734e5.exe (PID: 3500)
- 989a2e516088acff53c9b3b7bc01b1c2.exe (PID: 3516)
- 2348c1e1359506c785b9a37489abad8c.exe (PID: 1872)
- 962e989b5e7d18d9de1ed8c8434b8eff.exe (PID: 3576)
- 983fa75934cb9f2cb13ba3f86fcdac74.exe (PID: 2972)
- 344491bfb811ee82b644bc02e3287893.exe (PID: 3260)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2980)
- explorer.exe (PID: 1388)
- dwm.exe (PID: 932)
Checks supported languages
- 71504509122a94767aa35d8fa5cd63bb.exe (PID: 1640)
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- a8a61f9bd2c23c6b2097f44199dc1685.exe (PID: 2956)
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- guifx.exe (PID: 3264)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- Au_.exe (PID: 2292)
- Zlatowef.exe (PID: 2520)
- umwoe.exe (PID: 3632)
- 962e989b5e7d18d9de1ed8c8434b8eff.exe (PID: 3576)
- 989a2e516088acff53c9b3b7bc01b1c2.exe (PID: 3516)
- 469376f722271ca46c61cd3d8e6734e5.exe (PID: 3500)
- 2348c1e1359506c785b9a37489abad8c.exe (PID: 1872)
- 205965129fc9e40e8c75ec62b28a32e7.exe (PID: 3504)
- wmpnscfg.exe (PID: 4064)
- ckovo.exe (PID: 3192)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
- 344491bfb811ee82b644bc02e3287893.exe (PID: 3260)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
- 6468be24221d6546ff11f25f80f15a46.exe (PID: 2156)
- 4886a0d31ac52cc4431c7f8bbced0329.exe (PID: 2460)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 41b3bac994107f1387e41ecfce5b2cf6.exe (PID: 1116)
- 37dc2b37075ac8b7d7b0d7a64ce93cb1.exe (PID: 1852)
- 43aea7db92460a8baf31acdcd1a3bb88.exe (PID: 2620)
- 57f263a93fdc43468494e7fcfb092886.exe (PID: 3892)
- 47e131c1cd0e819ff5f5c7943797925b.exe (PID: 3784)
- 70c207517d92dcf0bf133f4bcaf30bbd.exe (PID: 1844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 069ab28b192fd0b755447ebbc6afb0d4.exe (PID: 3964)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- bkgrnd.exe (PID: 1528)
- QyswEEgY.exe (PID: 1756)
- nSoAoQMI.exe (PID: 2060)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3592)
- dw20.exe (PID: 3324)
- 75bfae9e0e3867cc21414005ae65821c.exe (PID: 3132)
- 84a952b95c84be7000171e6bb362c9c4.exe (PID: 3404)
- 98f34c24392acb67fb35b0ef87ed140d.exe (PID: 2028)
- 435d1ad1b5517baf8ad78f89d441e76a.exe (PID: 120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2232)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2088)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3580)
- 772ad760f25d5082f56fc51e00421db8.exe (PID: 3100)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1872)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2428)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1604)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3860)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4208)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5588)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5768)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4292)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5504)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5704)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4276)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4888)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5356)
- 5dd237af8a21c29fc2edc443c7f457d2.exe (PID: 5416)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 6a8306a9955ffbf527b4040bcd45eab1.exe (PID: 3080)
- 07d447798672ed80abae7b2c2fc2af90.exe (PID: 5652)
- 5a930cff22091983c9486391fd606660.exe (PID: 5492)
- 7d4fc839c0cc8f2a9bedf4d9d2bae755.exe (PID: 3472)
- 9f03c86c1b4c02bb2de070fd0a45ef49.exe (PID: 924)
- 7fa793fc444b9cab0dc02d8a0bb707a3.exe (PID: 3104)
- 21c323f09a68551f40c6d5e6cb74412b.exe (PID: 3000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6004)
- 10efa4395373062c24f47ab22520d4de.exe (PID: 2268)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- 32ce4b3733014440d770a8d3b81544d2.exe (PID: 3268)
- 51f574c70b4aa.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3500)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5112)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4168)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5244)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2632)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5616)
- CP.exe (PID: 3820)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 952)
- yikut.exe (PID: 2780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4148)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2920)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4120)
- IEMontior.exe (PID: 4716)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1128)
- CP.exe (PID: 2812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3152)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- seiif.exe (PID: 4248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5048)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5512)
- CP.exe (PID: 668)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4280)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4172)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4896)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3144)
- yuuax.exe (PID: 3524)
- CP.exe (PID: 300)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2736)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2684)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5712)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3508)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5324)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1656)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4268)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4624)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3084)
- CP.exe (PID: 5688)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- yvdoey.exe (PID: 900)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5700)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3064)
- CP.exe (PID: 5688)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5480)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3600)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3372)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5440)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4288)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
- hxqav.exe (PID: 4560)
- CP.exe (PID: 752)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
Creates files in the program directory
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 51f574c70b4aa.exe (PID: 2404)
- QyswEEgY.exe (PID: 1756)
Create files in a temporary directory
- 71504509122a94767aa35d8fa5cd63bb.exe (PID: 1640)
- ab928a5037d03eacaeedc9349f874e37.exe (PID: 280)
- b2c5cf9d9571823f712c98097d3806d0.exe (PID: 3592)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- Au_.exe (PID: 2292)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
- explorer.exe (PID: 1388)
- dwm.exe (PID: 932)
- 772ad760f25d5082f56fc51e00421db8.exe (PID: 3100)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
- 41b3bac994107f1387e41ecfce5b2cf6.exe (PID: 1116)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2988)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3592)
- 98f34c24392acb67fb35b0ef87ed140d.exe (PID: 2028)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2088)
- 435d1ad1b5517baf8ad78f89d441e76a.exe (PID: 120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2232)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1452)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3580)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1872)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1460)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2428)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1604)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3860)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4208)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4592)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4812)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5000)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5220)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5588)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5388)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5768)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2836)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4292)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4548)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4764)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4960)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5004)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5504)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5704)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4888)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4276)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5356)
- 7d4fc839c0cc8f2a9bedf4d9d2bae755.exe (PID: 3472)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5660)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6004)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- 10efa4395373062c24f47ab22520d4de.exe (PID: 2268)
- 51f574c70b4aa.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3500)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4992)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4168)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5244)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5112)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5616)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2632)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2920)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4120)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4148)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5520)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4376)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5952)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3152)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1128)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2524)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4844)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5972)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4396)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5048)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5512)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2404)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4780)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4280)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5224)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4896)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4172)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5216)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3144)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2736)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6076)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2684)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3508)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5712)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5828)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5324)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1656)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3084)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4268)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4624)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5984)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2248)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5700)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5480)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3064)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5284)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5108)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3372)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3600)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4492)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 5440)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4312)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 4288)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 2680)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 6092)
Reads the computer name
- a87676557bdf576b33070cd481a4026c.exe (PID: 1996)
- guifx.exe (PID: 3264)
- b52d906fd83240470fdc019a3554c08d.exe (PID: 2632)
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- Zlatowef.exe (PID: 2520)
- Au_.exe (PID: 2292)
- wmpnscfg.exe (PID: 4064)
- 95703aec3dbab49a4392981ea5b05a3c.exe (PID: 3268)
- ckovo.exe (PID: 3192)
- a1d35a4531c05d751a9868bfadb8176f.exe (PID: 2524)
- 344491bfb811ee82b644bc02e3287893.exe (PID: 3260)
- 962e989b5e7d18d9de1ed8c8434b8eff.exe (PID: 3576)
- 989a2e516088acff53c9b3b7bc01b1c2.exe (PID: 3516)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
- 6468be24221d6546ff11f25f80f15a46.exe (PID: 2156)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 43aea7db92460a8baf31acdcd1a3bb88.exe (PID: 2620)
- 41b3bac994107f1387e41ecfce5b2cf6.exe (PID: 1116)
- 70c207517d92dcf0bf133f4bcaf30bbd.exe (PID: 1844)
- 069ab28b192fd0b755447ebbc6afb0d4.exe (PID: 3964)
- 75afef19e7f9f799e2f353a970c3d207.exe (PID: 3452)
- QyswEEgY.exe (PID: 1756)
- nSoAoQMI.exe (PID: 2060)
- 75bfae9e0e3867cc21414005ae65821c.exe (PID: 3132)
- dw20.exe (PID: 3324)
- 98f34c24392acb67fb35b0ef87ed140d.exe (PID: 2028)
- bkgrnd.exe (PID: 1528)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 3980)
- 7fa793fc444b9cab0dc02d8a0bb707a3.exe (PID: 3104)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
- 51f574c70b4aa.exe (PID: 2404)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- 21c323f09a68551f40c6d5e6cb74412b.exe (PID: 3000)
- 9f03c86c1b4c02bb2de070fd0a45ef49.exe (PID: 924)
- CP.exe (PID: 3820)
- yikut.exe (PID: 2780)
- IEMontior.exe (PID: 4716)
- CP.exe (PID: 2812)
- seiif.exe (PID: 4248)
- CP.exe (PID: 668)
- CP.exe (PID: 300)
- yuuax.exe (PID: 3524)
- CP.exe (PID: 5688)
- 58e68e72b0c38587654c4877413dd6d0.exe (PID: 1664)
- yvdoey.exe (PID: 900)
- CP.exe (PID: 5688)
- CP.exe (PID: 752)
Reads the machine GUID from the registry
- 71504509122a94767aa35d8fa5cd63bb.exe (PID: 1640)
- ace5cc6b7a1cbc980dd1c8271cc7c8ad.exe (PID: 2464)
- Au_.exe (PID: 2292)
- 772ad760f25d5082f56fc51e00421db8.exe (PID: 3100)
- 6468be24221d6546ff11f25f80f15a46.exe (PID: 2156)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- 41b3bac994107f1387e41ecfce5b2cf6.exe (PID: 1116)
- bkgrnd.exe (PID: 1528)
- 435d1ad1b5517baf8ad78f89d441e76a.exe (PID: 120)
- 19f2b925c23f25e8b1ef3b632bc6d051.exe (PID: 2940)
- 10efa4395373062c24f47ab22520d4de.exe (PID: 2268)
- 51f574c70b4aa.exe (PID: 2404)
- IEMontior.exe (PID: 4716)
Checks proxy server information
- Au_.exe (PID: 2292)
- bkgrnd.exe (PID: 1528)
- 30bb32a0f3ab57854990cca5831dbb28.exe (PID: 2452)
The executable file from the user directory is run by the CMD process
- umwoe.exe (PID: 3632)
Changes appearance of the Explorer extensions
- dwm.exe (PID: 932)
- reg.exe (PID: 3632)
- reg.exe (PID: 3932)
- reg.exe (PID: 2092)
- reg.exe (PID: 752)
- reg.exe (PID: 1448)
- reg.exe (PID: 1208)
- reg.exe (PID: 2940)
- reg.exe (PID: 3104)
- reg.exe (PID: 2404)
- reg.exe (PID: 3268)
- reg.exe (PID: 1272)
- reg.exe (PID: 1232)
- reg.exe (PID: 2784)
- reg.exe (PID: 3436)
- reg.exe (PID: 3556)
- reg.exe (PID: 2828)
- reg.exe (PID: 1344)
- reg.exe (PID: 2904)
- reg.exe (PID: 3552)
- reg.exe (PID: 3700)
- reg.exe (PID: 1584)
- reg.exe (PID: 604)
- reg.exe (PID: 1612)
- reg.exe (PID: 668)
- reg.exe (PID: 552)
- reg.exe (PID: 680)
- reg.exe (PID: 3016)
- reg.exe (PID: 3136)
- reg.exe (PID: 3756)
- reg.exe (PID: 2128)
- reg.exe (PID: 4228)
- reg.exe (PID: 4236)
- reg.exe (PID: 4412)
- reg.exe (PID: 4420)
- reg.exe (PID: 4612)
- reg.exe (PID: 4604)
- reg.exe (PID: 4820)
- reg.exe (PID: 5012)
- reg.exe (PID: 5020)
- reg.exe (PID: 4828)
- reg.exe (PID: 5196)
- reg.exe (PID: 5404)
- reg.exe (PID: 5396)
- reg.exe (PID: 5204)
- reg.exe (PID: 5596)
- reg.exe (PID: 5604)
- reg.exe (PID: 5796)
- reg.exe (PID: 5932)
- reg.exe (PID: 5776)
- reg.exe (PID: 5940)
- reg.exe (PID: 4128)
- reg.exe (PID: 4332)
- reg.exe (PID: 4328)
- reg.exe (PID: 4104)
- reg.exe (PID: 4556)
- reg.exe (PID: 4560)
- reg.exe (PID: 1840)
- reg.exe (PID: 4776)
- reg.exe (PID: 4968)
- reg.exe (PID: 4984)
- reg.exe (PID: 5252)
- reg.exe (PID: 4992)
- reg.exe (PID: 5480)
- reg.exe (PID: 5728)
- reg.exe (PID: 5476)
- reg.exe (PID: 5904)
- reg.exe (PID: 6020)
- reg.exe (PID: 5684)
- reg.exe (PID: 6068)
- reg.exe (PID: 4124)
- reg.exe (PID: 4468)
- reg.exe (PID: 4416)
- reg.exe (PID: 2956)
- reg.exe (PID: 5056)
- reg.exe (PID: 5576)
- reg.exe (PID: 5668)
- reg.exe (PID: 5328)
- reg.exe (PID: 5360)
- reg.exe (PID: 1844)
- reg.exe (PID: 644)
- reg.exe (PID: 1152)
- reg.exe (PID: 3576)
- reg.exe (PID: 2744)
- reg.exe (PID: 4324)
- reg.exe (PID: 4296)
- reg.exe (PID: 2840)
- reg.exe (PID: 4528)
- reg.exe (PID: 5056)
- reg.exe (PID: 4432)
- reg.exe (PID: 5536)
- reg.exe (PID: 5456)
- reg.exe (PID: 4956)
- reg.exe (PID: 5680)
- reg.exe (PID: 5952)
- reg.exe (PID: 3312)
- reg.exe (PID: 3372)
- reg.exe (PID: 1232)
- reg.exe (PID: 3152)
- reg.exe (PID: 2128)
- reg.exe (PID: 4196)
- reg.exe (PID: 4132)
- reg.exe (PID: 4772)
- reg.exe (PID: 2084)
- reg.exe (PID: 5832)
- reg.exe (PID: 4224)
- reg.exe (PID: 4548)
- reg.exe (PID: 5040)
- reg.exe (PID: 4272)
- reg.exe (PID: 4876)
- reg.exe (PID: 4896)
- reg.exe (PID: 5744)
- reg.exe (PID: 2396)
- reg.exe (PID: 2948)
- reg.exe (PID: 3536)
- reg.exe (PID: 1460)
- reg.exe (PID: 5768)
- reg.exe (PID: 3860)
- reg.exe (PID: 296)
- reg.exe (PID: 5020)
- reg.exe (PID: 2836)
- reg.exe (PID: 4520)
- reg.exe (PID: 4296)
- reg.exe (PID: 4548)
- reg.exe (PID: 5092)
- reg.exe (PID: 4856)
- reg.exe (PID: 5832)
- reg.exe (PID: 4896)
- reg.exe (PID: 2812)
- reg.exe (PID: 4948)
- reg.exe (PID: 3740)
- reg.exe (PID: 1452)
- reg.exe (PID: 6008)
- reg.exe (PID: 3048)
- reg.exe (PID: 1376)
- reg.exe (PID: 1664)
- reg.exe (PID: 6076)
- reg.exe (PID: 4284)
- reg.exe (PID: 2744)
- reg.exe (PID: 5120)
- reg.exe (PID: 4924)
- reg.exe (PID: 2972)
- reg.exe (PID: 5004)
- reg.exe (PID: 5640)
- reg.exe (PID: 5736)
- reg.exe (PID: 6080)
- reg.exe (PID: 5324)
- reg.exe (PID: 968)
- reg.exe (PID: 644)
- reg.exe (PID: 952)
- reg.exe (PID: 1656)
- reg.exe (PID: 4400)
- reg.exe (PID: 1088)
- reg.exe (PID: 4228)
- reg.exe (PID: 4480)
- reg.exe (PID: 2344)
- reg.exe (PID: 2364)
- reg.exe (PID: 2728)
- reg.exe (PID: 4568)
- reg.exe (PID: 644)
- reg.exe (PID: 3932)
- reg.exe (PID: 5812)
- reg.exe (PID: 5780)
- reg.exe (PID: 3700)
- reg.exe (PID: 3540)
- reg.exe (PID: 4196)
- reg.exe (PID: 1128)
- reg.exe (PID: 4148)
- reg.exe (PID: 4356)
- reg.exe (PID: 4828)
- reg.exe (PID: 4772)
- reg.exe (PID: 4528)
- reg.exe (PID: 4288)
- reg.exe (PID: 5144)
- reg.exe (PID: 2348)
- reg.exe (PID: 5800)
- reg.exe (PID: 5352)
- reg.exe (PID: 2464)
- reg.exe (PID: 6008)
- reg.exe (PID: 3844)
- reg.exe (PID: 3116)
- reg.exe (PID: 3980)
- reg.exe (PID: 4268)
- reg.exe (PID: 4228)
- reg.exe (PID: 448)
- reg.exe (PID: 6056)
- reg.exe (PID: 4404)
- reg.exe (PID: 4160)
- reg.exe (PID: 4904)
- reg.exe (PID: 2236)
- reg.exe (PID: 5032)
- reg.exe (PID: 2608)
- reg.exe (PID: 1564)
- reg.exe (PID: 4036)
- reg.exe (PID: 5824)
- reg.exe (PID: 3700)
- reg.exe (PID: 5036)
- reg.exe (PID: 4960)
- reg.exe (PID: 4380)
- reg.exe (PID: 5776)
- reg.exe (PID: 2836)
- reg.exe (PID: 4508)
- reg.exe (PID: 4216)
- reg.exe (PID: 4948)
- reg.exe (PID: 4432)
- reg.exe (PID: 5712)
- reg.exe (PID: 5736)
Reads settings of System Certificates
- explorer.exe (PID: 1388)
Creates files or folders in the user directory
- explorer.exe (PID: 1388)
- Au_.exe (PID: 2292)
- 766ea2eaced5f8023fd52234af0fcb6d.exe (PID: 2684)
- 4167f1d1828a149544e695544b00be91.exe (PID: 1068)
- bkgrnd.exe (PID: 1528)
- 51f574c70b4aa.exe (PID: 2404)
- QyswEEgY.exe (PID: 1756)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1388)
- cscript.exe (PID: 968)
- cscript.exe (PID: 1016)
- cscript.exe (PID: 2740)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 3576)
- cscript.exe (PID: 2716)
- cscript.exe (PID: 1628)
- cscript.exe (PID: 1436)
- cscript.exe (PID: 3848)
- cscript.exe (PID: 2548)
- cscript.exe (PID: 3968)
- cscript.exe (PID: 2416)
- cscript.exe (PID: 448)
- cscript.exe (PID: 1904)
- cscript.exe (PID: 4340)
- cscript.exe (PID: 4144)
- cscript.exe (PID: 4532)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 5136)
- cscript.exe (PID: 4940)
- cscript.exe (PID: 5308)
- cscript.exe (PID: 5520)
- cscript.exe (PID: 5696)
- cscript.exe (PID: 6096)
- cscript.exe (PID: 5980)
- cscript.exe (PID: 4148)
- cscript.exe (PID: 4496)
- cscript.exe (PID: 4708)
- cscript.exe (PID: 5152)
- cscript.exe (PID: 4924)
- cscript.exe (PID: 5384)
- cscript.exe (PID: 5224)
- cscript.exe (PID: 5892)
- cscript.exe (PID: 2224)
- cscript.exe (PID: 6124)
- cscript.exe (PID: 4964)
- cscript.exe (PID: 4728)
- cscript.exe (PID: 5544)
- cscript.exe (PID: 6060)
- cscript.exe (PID: 1436)
- cscript.exe (PID: 1212)
- cscript.exe (PID: 5928)
- cscript.exe (PID: 2316)
- cscript.exe (PID: 4720)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 4712)
- cscript.exe (PID: 5512)
- cscript.exe (PID: 608)
- cscript.exe (PID: 2404)
- cscript.exe (PID: 3760)
- cscript.exe (PID: 4628)
- cscript.exe (PID: 2696)
- cscript.exe (PID: 5060)
- cscript.exe (PID: 4568)
- cscript.exe (PID: 5736)
- cscript.exe (PID: 2716)
- cscript.exe (PID: 2828)
- cscript.exe (PID: 3000)
- cscript.exe (PID: 2468)
- cscript.exe (PID: 5164)
- cscript.exe (PID: 4324)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 5296)
- cscript.exe (PID: 2076)
- cscript.exe (PID: 5944)
- cscript.exe (PID: 3976)
- cscript.exe (PID: 2220)
- cscript.exe (PID: 2476)
- cscript.exe (PID: 4156)
- cscript.exe (PID: 4180)
- cscript.exe (PID: 6032)
- cscript.exe (PID: 5344)
- cscript.exe (PID: 4832)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 4484)
- cscript.exe (PID: 5080)
- cscript.exe (PID: 5240)
- cscript.exe (PID: 4360)
- cscript.exe (PID: 4296)
- cscript.exe (PID: 5720)
- cscript.exe (PID: 668)
- cscript.exe (PID: 2128)
- cscript.exe (PID: 3980)
- cscript.exe (PID: 4872)
- cscript.exe (PID: 5208)
- cscript.exe (PID: 5432)
- cscript.exe (PID: 4524)
- cscript.exe (PID: 6080)
- cscript.exe (PID: 6004)
- cscript.exe (PID: 3272)
- cscript.exe (PID: 4400)
- cscript.exe (PID: 4384)
- cscript.exe (PID: 4360)
- cscript.exe (PID: 4244)
- cscript.exe (PID: 5908)
- cscript.exe (PID: 2140)
- cscript.exe (PID: 5272)
- cscript.exe (PID: 3552)
- cscript.exe (PID: 4228)
- cscript.exe (PID: 5124)
- cscript.exe (PID: 4688)
- cscript.exe (PID: 2236)
- cscript.exe (PID: 5668)
Reads Microsoft Office registry keys
- 10efa4395373062c24f47ab22520d4de.exe (PID: 2268)
Reads mouse settings
- 10efa4395373062c24f47ab22520d4de.exe (PID: 2268)
Application launched itself
- iexplore.exe (PID: 1208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:30 11:27:44 |
| ZipCRC: | 0x8232f6c7 |
| ZipCompressedSize: | 162548 |
| ZipUncompressedSize: | 307712 |
| ZipFileName: | 57f263a93fdc43468494e7fcfb092886.exe |
Total processes
2 268
Monitored processes
1 342
Malicious processes
91
Suspicious processes
289
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\435d1ad1b5517baf8ad78f89d441e76a.exe" | C:\Users\admin\Desktop\435d1ad1b5517baf8ad78f89d441e76a.exe | — | explorer.exe | |||||||||||
User: admin Company: REW is room acoustics analysis software for measuring Integrity Level: MEDIUM Description: REW is room acoustics analysis software for measuring Exit code: 0 Version: 1.00.0029 Modules
| |||||||||||||||
| 124 | C:\Windows\system32\cmd.exe /c "C:\Users\admin\Desktop\58e68e72b0c38587654c4877413dd6d0" | C:\Windows\System32\cmd.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 124 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /d 0 /t REG_DWORD /f | C:\Windows\System32\reg.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /d 0 /t REG_DWORD /f | C:\Windows\System32\reg.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 128 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /d 0 /t REG_DWORD /f | C:\Windows\System32\reg.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | net stop "Kingsoft AntiVirus Service" | C:\Windows\System32\net.exe | — | 32ce4b3733014440d770a8d3b81544d2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /d 0 /t REG_DWORD /f | C:\Windows\System32\reg.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\sGMgAcgU.bat" "C:\Users\admin\Desktop\58e68e72b0c38587654c4877413dd6d0.exe"" | C:\Windows\System32\cmd.exe | — | 58e68e72b0c38587654c4877413dd6d0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 280 | "C:\Users\admin\Desktop\ab928a5037d03eacaeedc9349f874e37.exe" | C:\Users\admin\Desktop\ab928a5037d03eacaeedc9349f874e37.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Shell Doc Object and Control Library Exit code: 4294967295 Version: 5.50.4807.2300 Modules
| |||||||||||||||
| 288 | taskeng.exe {713157D0-CA13-42EB-B692-3B7270C875D1} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
75 677
Read events
74 579
Write events
1 095
Delete events
3
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.zip |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
Executable files
909
Suspicious files
50
Text files
610
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:56B7F9BEF84A08B983394308C604929A | SHA256:E40AB49189EFD47A9D96D9F2023AF947DFE39AB276FB864D3B0C5425FC919A14 | |||
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\1.zip.lnk | binary | |
MD5:F7547789DF67D2ECD30E1A9F7F4C1B8F | SHA256:7FB1CD30A5E508666005DB449EAAE7A397A2351F5FB44AB82548F6EC434EDBFA | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\7d4fc839c0cc8f2a9bedf4d9d2bae755.exe | executable | |
MD5:7D4FC839C0CC8F2A9BEDF4D9D2BAE755 | SHA256:4EE074C2FD0F96143F8690DF640D6E609BBEAB6C080EB9955DB00DF7D595A31D | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\00c6bb56bd5037deb24159a6873a05b6.exe | executable | |
MD5:00C6BB56BD5037DEB24159A6873A05B6 | SHA256:8B91BFEBF5D2A438F788BA7A8F70A27757275324ECE1D3CB8022102987CC3B13 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\1d3e2b2e4d0ab4c1acb0a687b64943e5.exe | executable | |
MD5:1D3E2B2E4D0AB4C1ACB0A687B64943E5 | SHA256:2F582B021B5CCEBA1C7C25A7DC3B9C9300CD22BAAEAC56C78442AF35DDAD697A | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\5a930cff22091983c9486391fd606660.exe | executable | |
MD5:5A930CFF22091983C9486391FD606660 | SHA256:11CB0710137CFD8EE629EB0982A5C23255BF031ED9FB229906F10CC5203E34A8 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\983fa75934cb9f2cb13ba3f86fcdac74.exe | executable | |
MD5:983FA75934CB9F2CB13BA3F86FCDAC74 | SHA256:3BE9D14E9F4B4CCDEEDEDAA0A725572E96C58F3780C1486CA0E8586041EE6186 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\6a8306a9955ffbf527b4040bcd45eab1.exe | executable | |
MD5:6A8306A9955FFBF527B4040BCD45EAB1 | SHA256:987FEEB4B7968B3AE4D271A2E5F67C68978D6F895137219D89F7138F4A27CD25 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\2348c1e1359506c785b9a37489abad8c.exe | executable | |
MD5:2348C1E1359506C785B9A37489ABAD8C | SHA256:2DC8EC36B4EE698A2CB9B52FB2B5115F178BEA258A788E290B196C6CCF3DE5AD | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.2697\4b279a7081ce7020ffda0c7f074695e9.exe | executable | |
MD5:4B279A7081CE7020FFDA0C7F074695E9 | SHA256:3695500ACF513E118A00116766C205B4C095B5575D61CF7B6AC180A378EDE35B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
82
DNS requests
203
Threats
118
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | Au_.exe | GET | 301 | 222.73.33.250:80 | http://fxxz.com/show/push.txt | unknown | html | 178 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
2292 | Au_.exe | GET | 301 | 58.218.215.169:80 | http://www.fxxz.com/show/push.txt | unknown | html | 262 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3264 | guifx.exe | 165.194.123.67:443 | — | Chung-Ang University | KR | unknown |
2292 | Au_.exe | 222.73.33.250:80 | fxxz.com | China Telecom Group | CN | unknown |
2292 | Au_.exe | 58.218.215.169:80 | www.fxxz.com | Chinanet | CN | unknown |
1388 | explorer.exe | 104.126.37.128:80 | www.bing.com | Akamai International B.V. | DE | unknown |
1388 | explorer.exe | 34.90.130.132:80 | bloodguiltiness.com | GOOGLE-CLOUD-PLATFORM | NL | unknown |
1388 | explorer.exe | 85.215.44.41:80 | 88.broker | Strato AG | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fxxz.com |
| whitelisted |
www.fxxz.com |
| unknown |
www.bing.com |
| whitelisted |
bloodguiltiness.com |
| unknown |
88.broker |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
google.com |
| whitelisted |
gwentcarsales.co.uk |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
2292 | Au_.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Win32/Adware.Agent.NPP CnC Activity |
78 ETPRO signatures available at the full report