| File name: | hdd-capacity-restore_softradar-com.exe |
| Full analysis: | https://app.any.run/tasks/51399536-c16d-4c5a-be53-016ddcb4292c |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2024, 12:26:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B8DA7010CB85E1CDB84D5912017A9565 |
| SHA1: | AD8643815233CAE0444FEB830F88C2689AC434F6 |
| SHA256: | 4AC4B12998235BE95F030AB9C1002ABEEC045A23E8331A58B13809D203C846FE |
| SSDEEP: | 24576:vRSci8zxWatSgisgohEkXam601tL/e6X1h+gQgE:vRSci8zxWatSDsgohEkqm601tL/e6X1q |
MALICIOUS
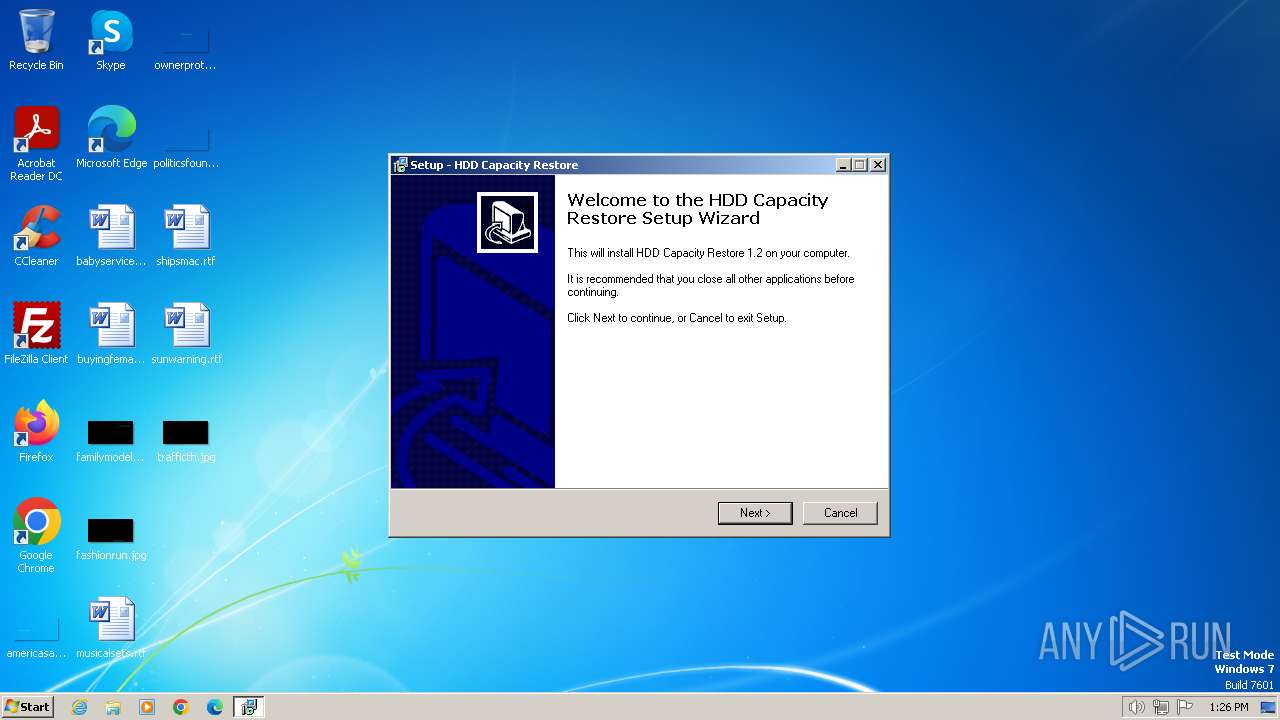
Drops the executable file immediately after the start
- hdd-capacity-restore_softradar-com.exe (PID: 3216)
- is-V3LUD.tmp (PID: 3200)
Creates a writable file in the system directory
- is-V3LUD.tmp (PID: 3200)
SUSPICIOUS
Executable content was dropped or overwritten
- hdd-capacity-restore_softradar-com.exe (PID: 3216)
- is-V3LUD.tmp (PID: 3200)
Process drops legitimate windows executable
- is-V3LUD.tmp (PID: 3200)
Reads the Windows owner or organization settings
- is-V3LUD.tmp (PID: 3200)
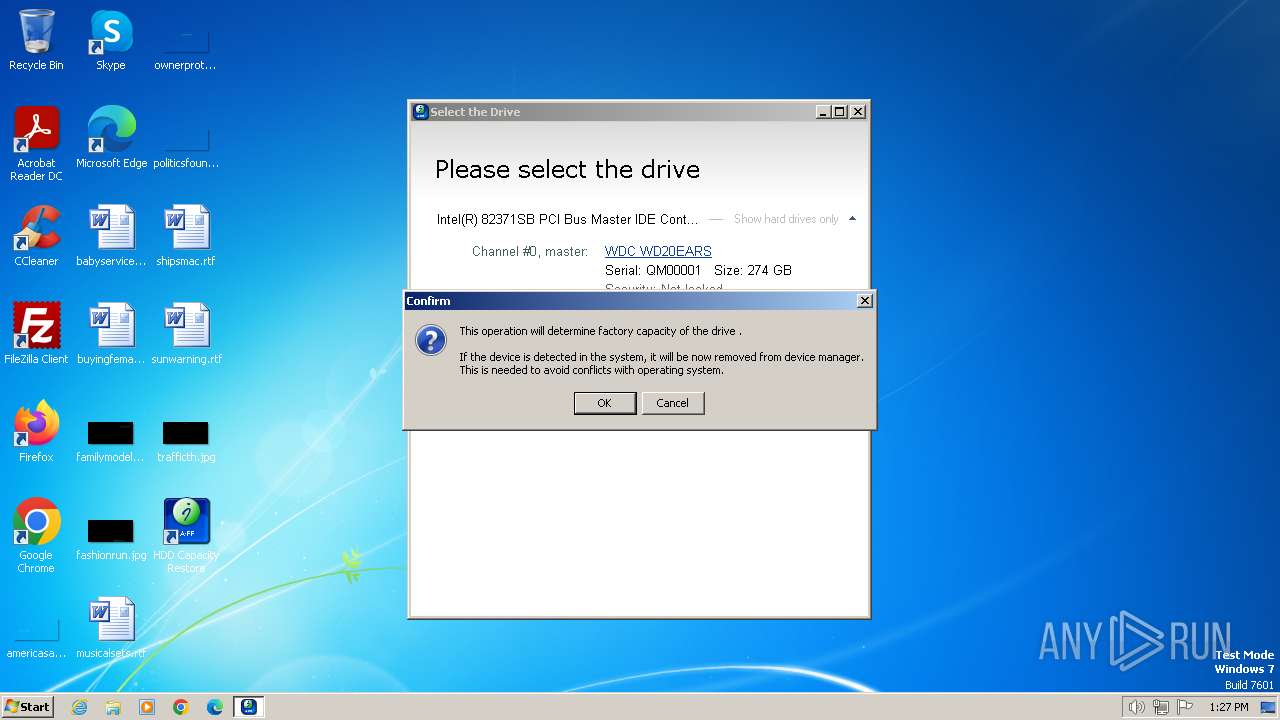
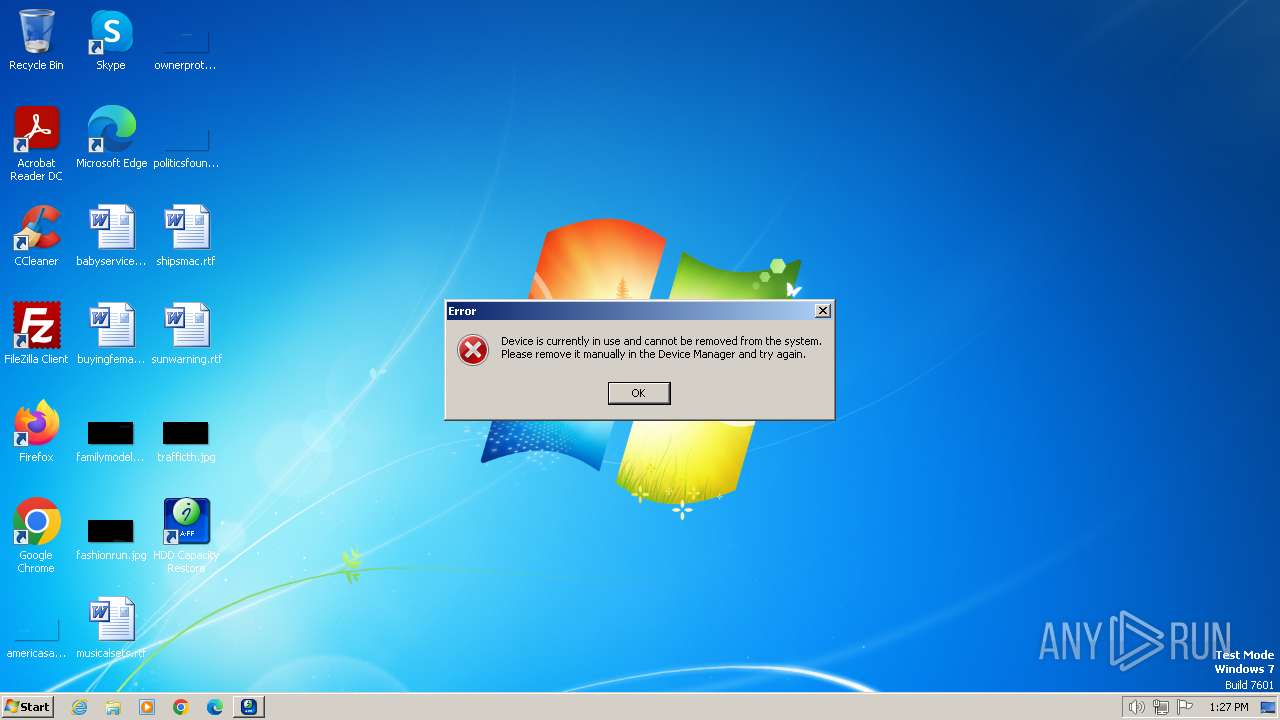
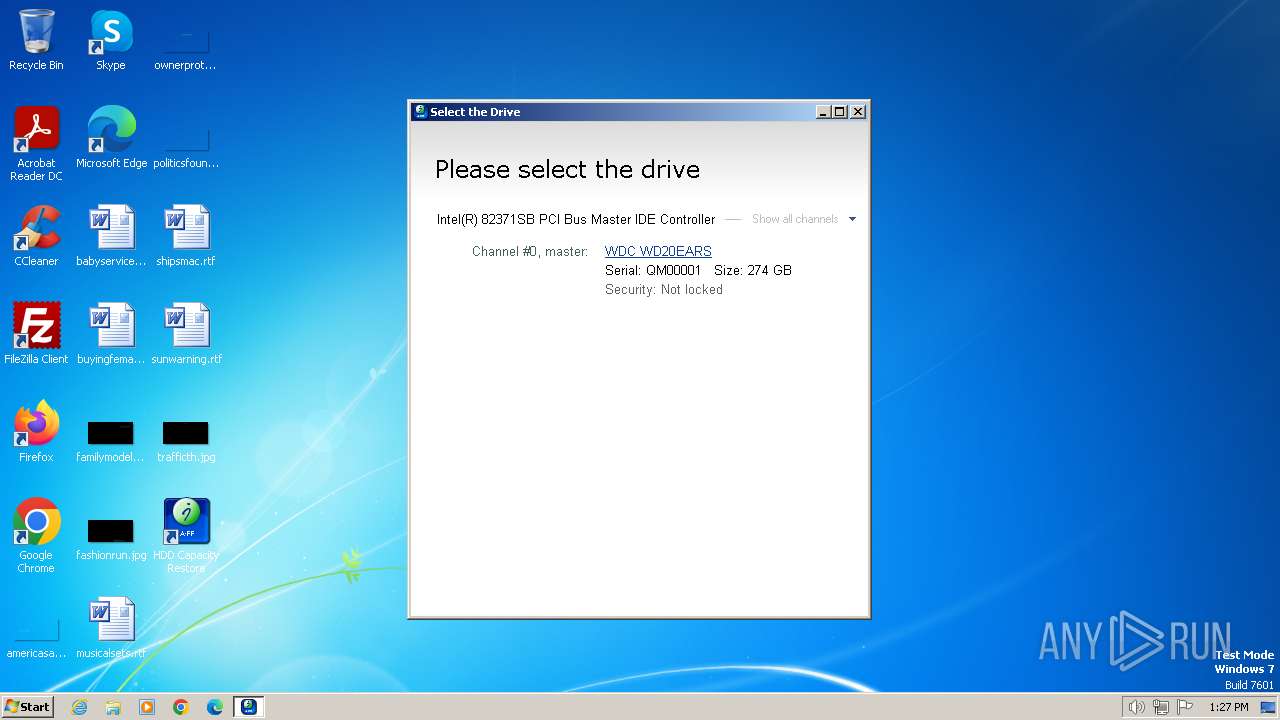
Drops a system driver (possible attempt to evade defenses)
- is-V3LUD.tmp (PID: 3200)
INFO
Create files in a temporary directory
- hdd-capacity-restore_softradar-com.exe (PID: 3216)
- is-V3LUD.tmp (PID: 3200)
Checks supported languages
- hdd-capacity-restore_softradar-com.exe (PID: 3216)
- is-V3LUD.tmp (PID: 3200)
- CapacityRestore.exe (PID: 2348)
Creates files in the program directory
- is-V3LUD.tmp (PID: 3200)
Reads the computer name
- is-V3LUD.tmp (PID: 3200)
- CapacityRestore.exe (PID: 2348)
Creates a software uninstall entry
- is-V3LUD.tmp (PID: 3200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable PowerBASIC/Win 9.x (51.2) |
|---|---|---|
| .exe | | | Inno Setup installer (37.9) |
| .exe | | | Win32 Executable Delphi generic (4.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.2) |
| .exe | | | Win32 Executable (generic) (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 36864 |
| InitializedDataSize: | 17408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x98d8 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Atola Technology |
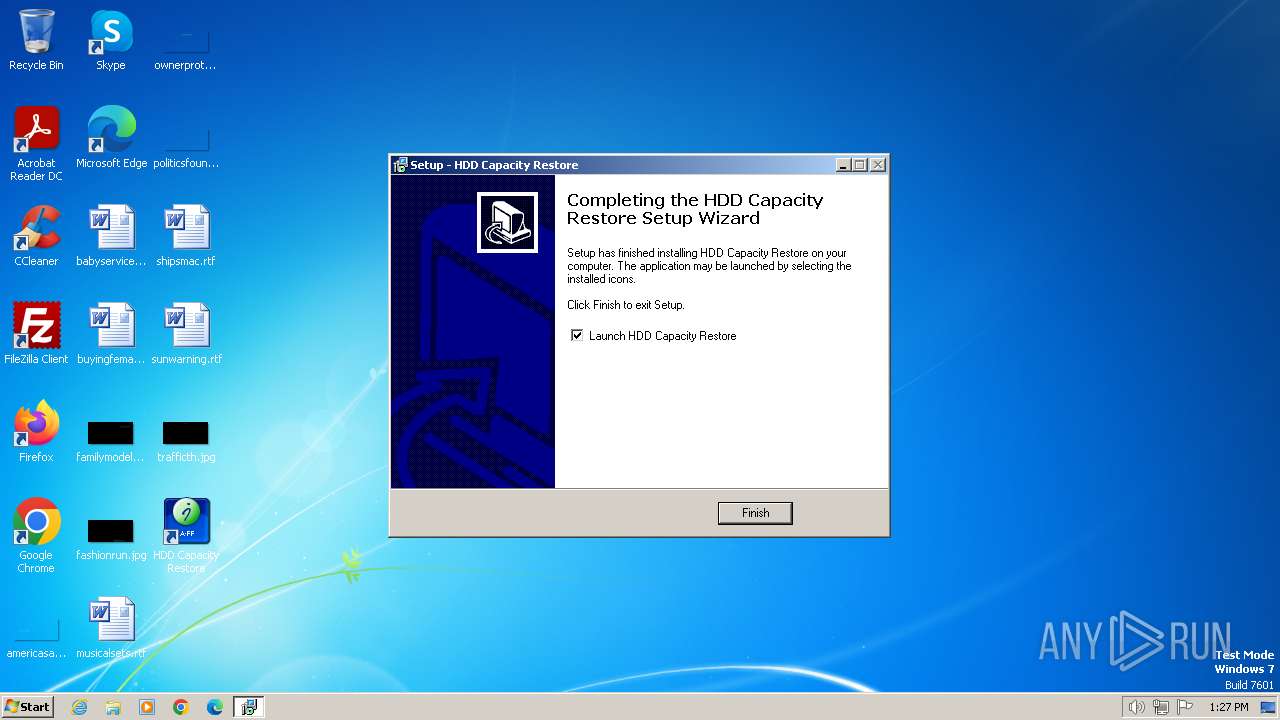
| FileDescription: | HDD Capacity Restore Setup |
| FileVersion: | |
| LegalCopyright: | Copyright (C) 2003-2007 A-FF.COM Data Recovery |
Total processes
45
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2348 | "C:\Program Files\HDD Capacity Restore\CapacityRestore.exe" | C:\Program Files\HDD Capacity Restore\CapacityRestore.exe | — | is-V3LUD.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\AppData\Local\Temp\is-PNQ75.tmp\is-V3LUD.tmp" /SL4 $80198 "C:\Users\admin\AppData\Local\Temp\hdd-capacity-restore_softradar-com.exe" 255575 52736 | C:\Users\admin\AppData\Local\Temp\is-PNQ75.tmp\is-V3LUD.tmp | hdd-capacity-restore_softradar-com.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.46.0.0 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\AppData\Local\Temp\hdd-capacity-restore_softradar-com.exe" | C:\Users\admin\AppData\Local\Temp\hdd-capacity-restore_softradar-com.exe | explorer.exe | ||||||||||||
User: admin Company: Atola Technology Integrity Level: HIGH Description: HDD Capacity Restore Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3348 | "C:\Users\admin\AppData\Local\Temp\hdd-capacity-restore_softradar-com.exe" | C:\Users\admin\AppData\Local\Temp\hdd-capacity-restore_softradar-com.exe | — | explorer.exe | |||||||||||
User: admin Company: Atola Technology Integrity Level: MEDIUM Description: HDD Capacity Restore Setup Exit code: 3221226540 Version: Modules
| |||||||||||||||
Total events
2 556
Read events
2 537
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.1.12 | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
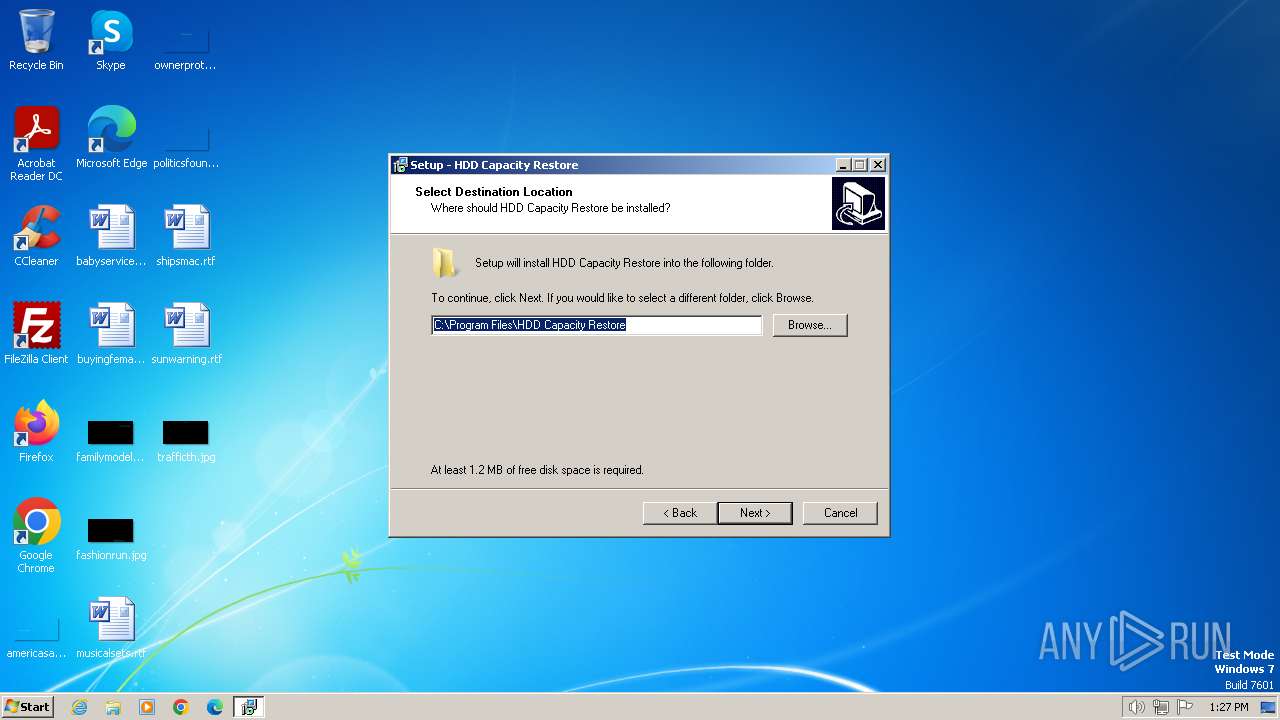
Value: C:\Program Files\HDD Capacity Restore | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\HDD Capacity Restore\ | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: HDD Capacity Restore | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: desktopicon | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | DisplayName |
Value: HDD Capacity Restore 1.2 | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\HDD Capacity Restore\CapacityRestore.exe | |||
| (PID) Process: | (3200) is-V3LUD.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HDD Capacity Restore_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\HDD Capacity Restore\unins000.exe" | |||
Executable files
9
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3200 | is-V3LUD.tmp | C:\Windows\system32\is-27KLK.tmp | executable | |
MD5:E914838D71C5937A841BABEFD59B1483 | SHA256:EB5F2FD9F4505CB9109B8C8F262DCEB784F01BA2EE315C02A3C02FE9C312BCD6 | |||
| 3200 | is-V3LUD.tmp | C:\Users\admin\AppData\Local\Temp\is-76AAH.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3200 | is-V3LUD.tmp | C:\Program Files\HDD Capacity Restore\unins000.exe | executable | |
MD5:1DC0B6066C8EF024699219FFA4C0854B | SHA256:6EBED4FA80E633A9F28057A8C84BBE92789628A1E3D316525CD6BE4F26D6724C | |||
| 3200 | is-V3LUD.tmp | C:\Program Files\HDD Capacity Restore\is-LCNT1.tmp | executable | |
MD5:E00FEECAF2816851DB18239C5C494DBC | SHA256:9745E8DB0CC7F6681AA8745EA6FCBB3F92C5AC36CB1132B77F54123757A26900 | |||
| 3200 | is-V3LUD.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\HDD Capacity Restore\HDD Capacity Restore.lnk | binary | |
MD5:EAE1CAC5C845E6C14D30332CBE3069E0 | SHA256:25CC30179CF5971EACCEA76045E81582DD5A0A801EEBE81BE0645E1720814400 | |||
| 3200 | is-V3LUD.tmp | C:\Program Files\HDD Capacity Restore\is-CVUVI.tmp | executable | |
MD5:1DC0B6066C8EF024699219FFA4C0854B | SHA256:6EBED4FA80E633A9F28057A8C84BBE92789628A1E3D316525CD6BE4F26D6724C | |||
| 3200 | is-V3LUD.tmp | C:\Program Files\HDD Capacity Restore\unins000.dat | binary | |
MD5:2690898E0AD6E92966AA214C5F76E55F | SHA256:FF53648C8638DDEE5267C8A22A01FD90FB3CE403A2738412E0E16E4251C48D8D | |||
| 3216 | hdd-capacity-restore_softradar-com.exe | C:\Users\admin\AppData\Local\Temp\is-PNQ75.tmp\is-V3LUD.tmp | executable | |
MD5:F627721A34C13A5307779A498E8F6519 | SHA256:13C6A795A259A9731D5C00F35E6EEEEAE840423D3E1783FD6C75509A3B7CB348 | |||
| 3200 | is-V3LUD.tmp | C:\Users\admin\AppData\Local\Temp\is-76AAH.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:C594B792B9C556EA62A30DE541D2FB03 | SHA256:5DCC1E0A197922907BCA2C4369F778BD07EE4B1BBBDF633E987A028A314D548E | |||
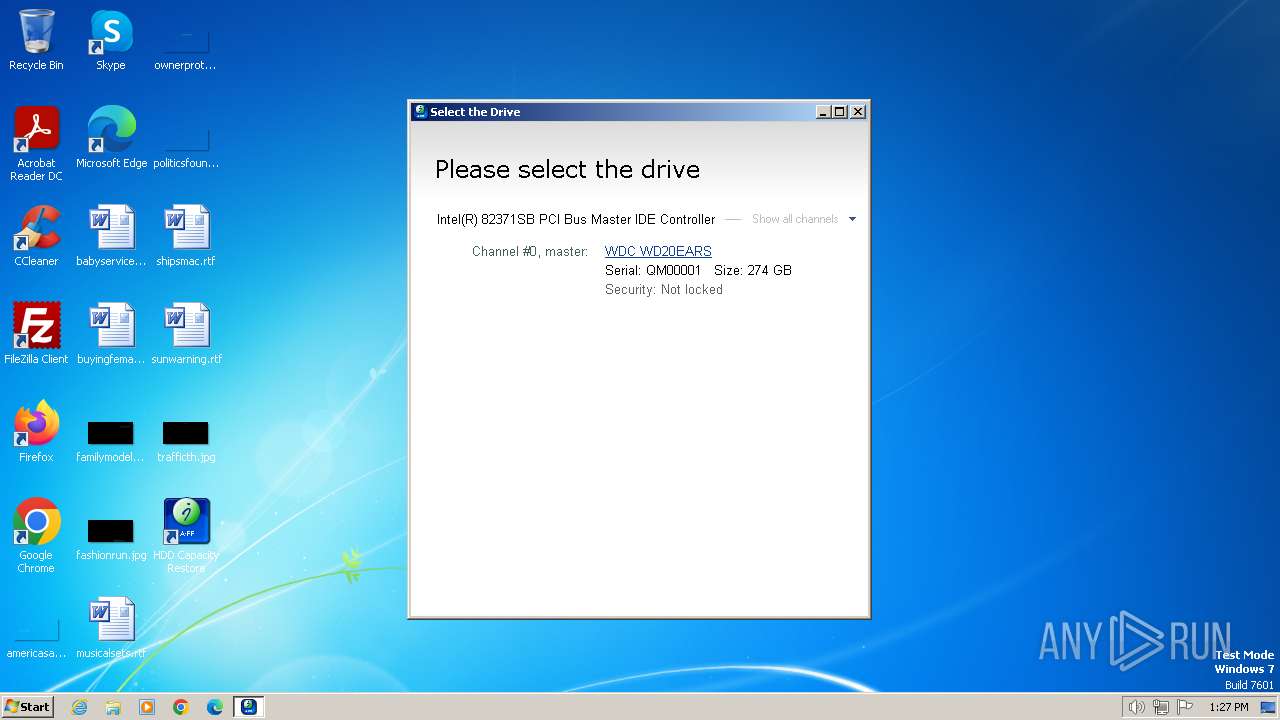
| 3200 | is-V3LUD.tmp | C:\Windows\System32\affhdd.sys | executable | |
MD5:E914838D71C5937A841BABEFD59B1483 | SHA256:EB5F2FD9F4505CB9109B8C8F262DCEB784F01BA2EE315C02A3C02FE9C312BCD6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |