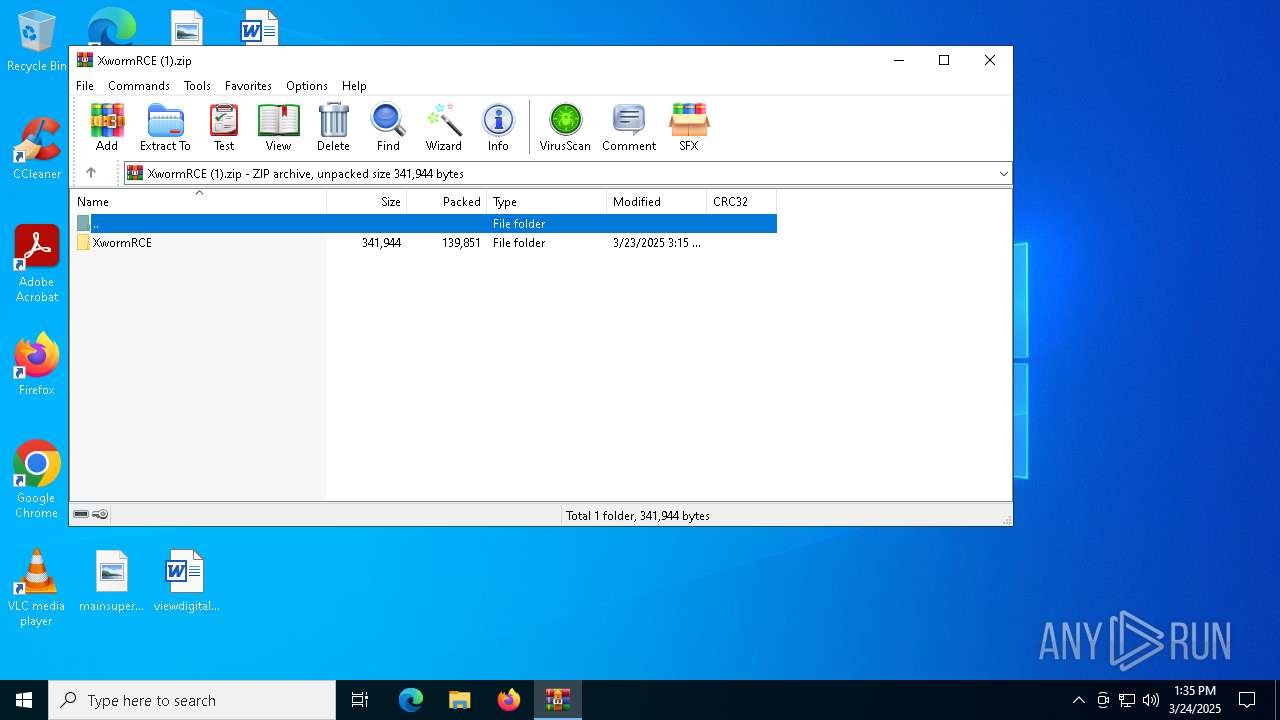
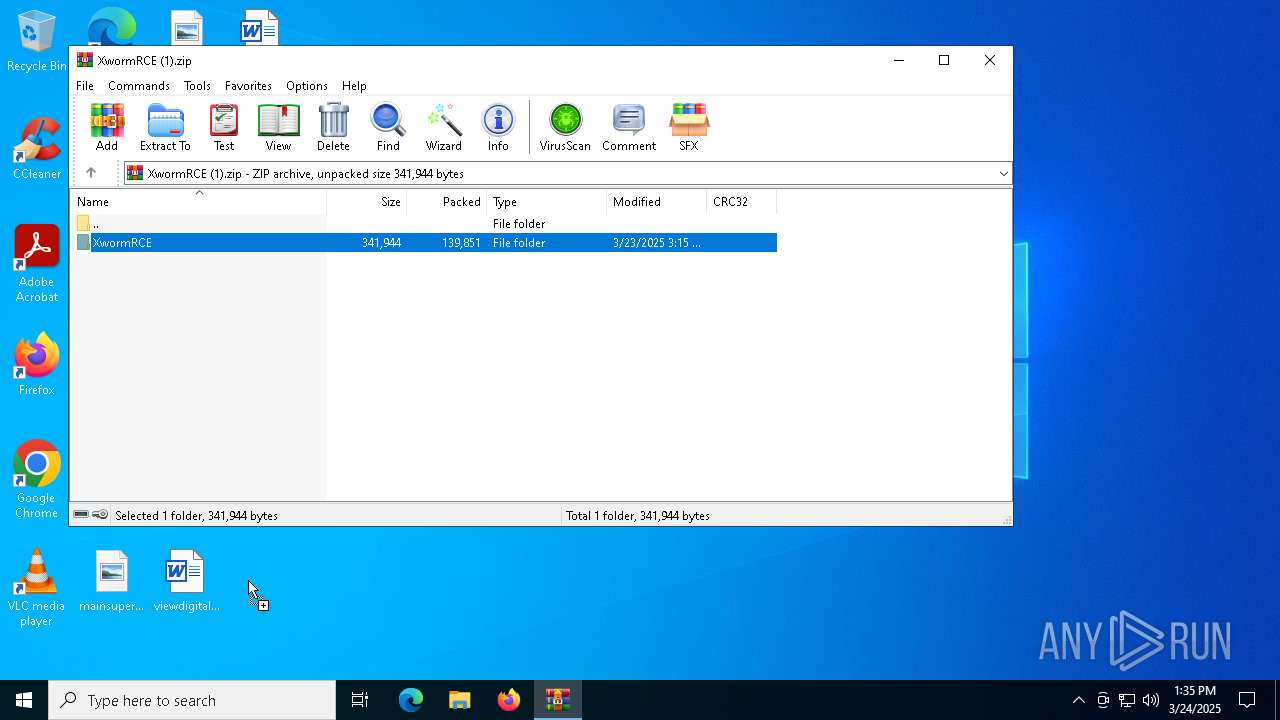
| File name: | XwormRCE (1).zip |
| Full analysis: | https://app.any.run/tasks/6f042887-e29d-499b-af33-ba4911607386 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 13:35:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | B42457EA6689557133BCD7AD17192B9A |
| SHA1: | 8FFA9D5C1EAA462C6A671FBB148BE65D073716FD |
| SHA256: | 4AC20696C22BB9DA3EF8AC36D44D85C4DF52255DB6AAC1328AD4E6602A5CEC30 |
| SSDEEP: | 3072:3QOrht7VnjlFg9JlHCl6fJrhoUeNNd7kht7VnjlFg9JlHCl6fJri5oFZaw:XJjA93Cl6fJrhKNNyJjA93Cl6fJrrZL |
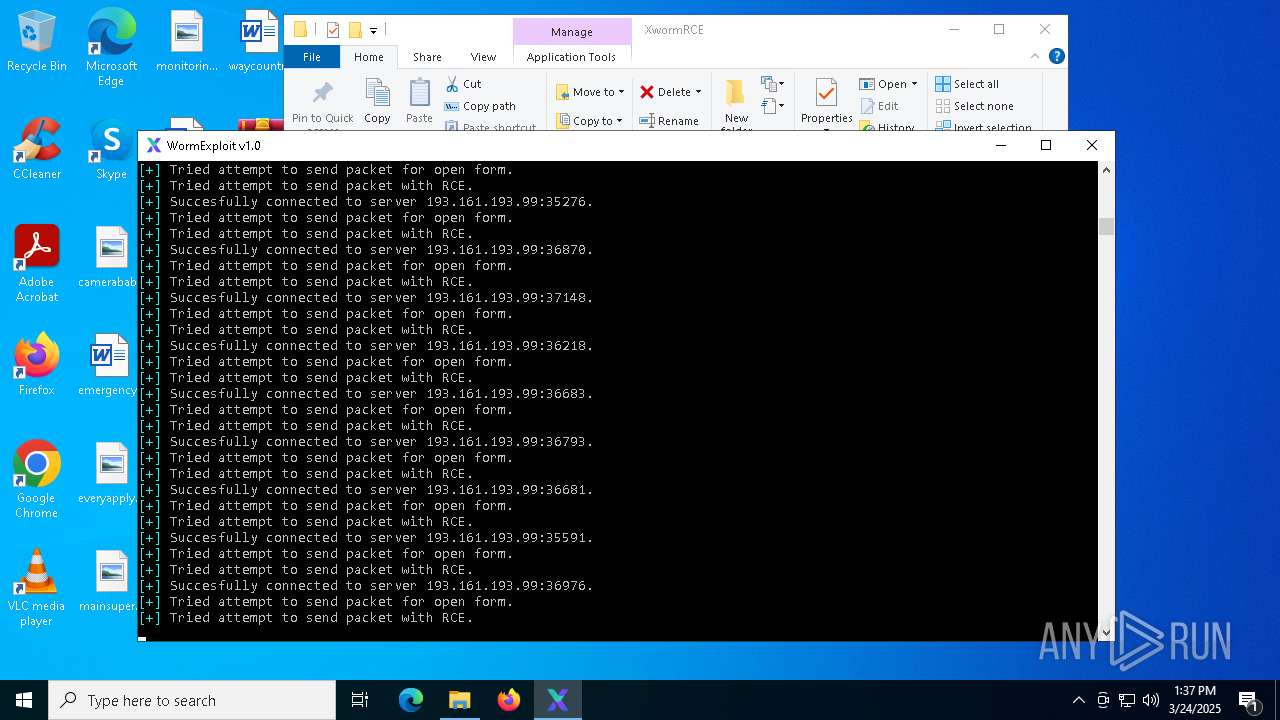
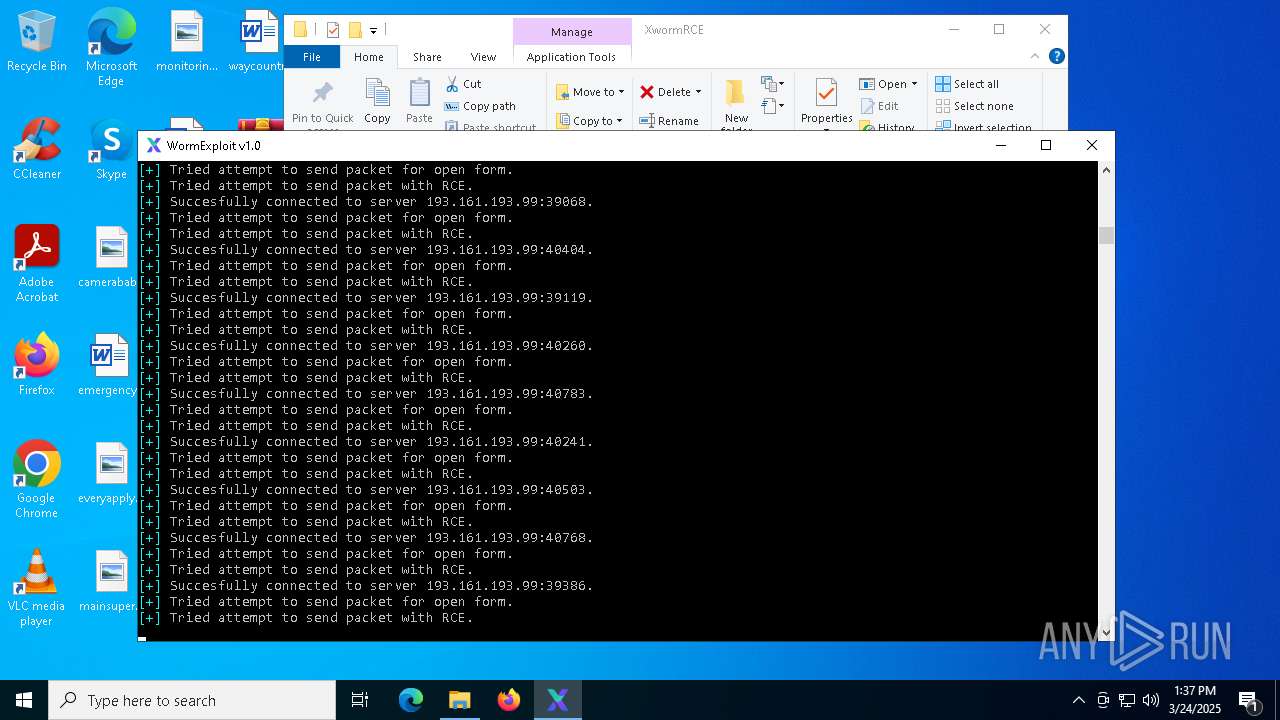
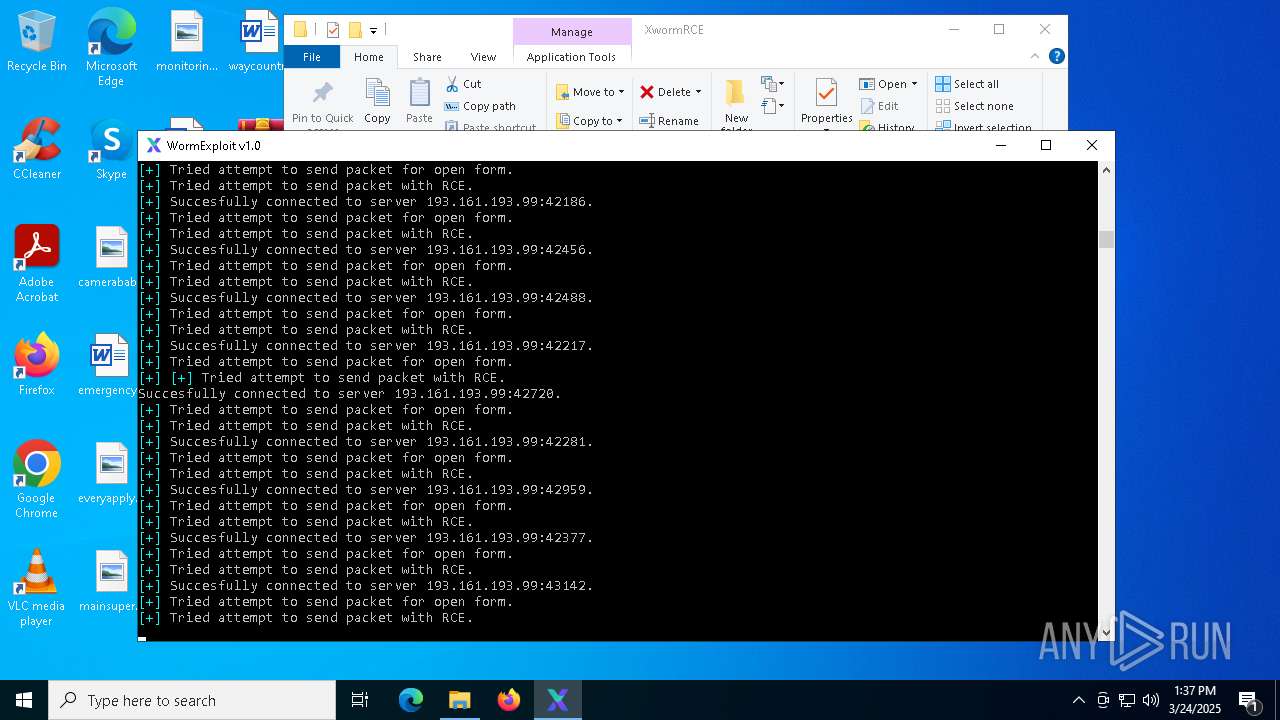
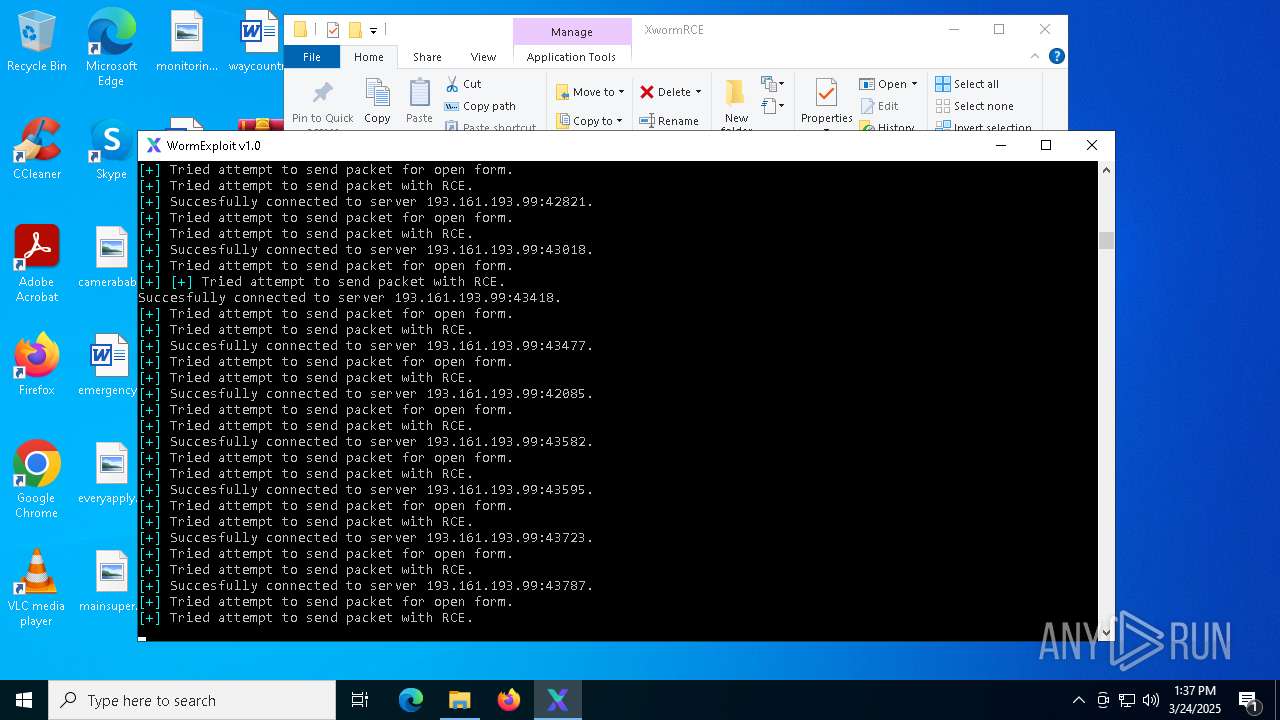
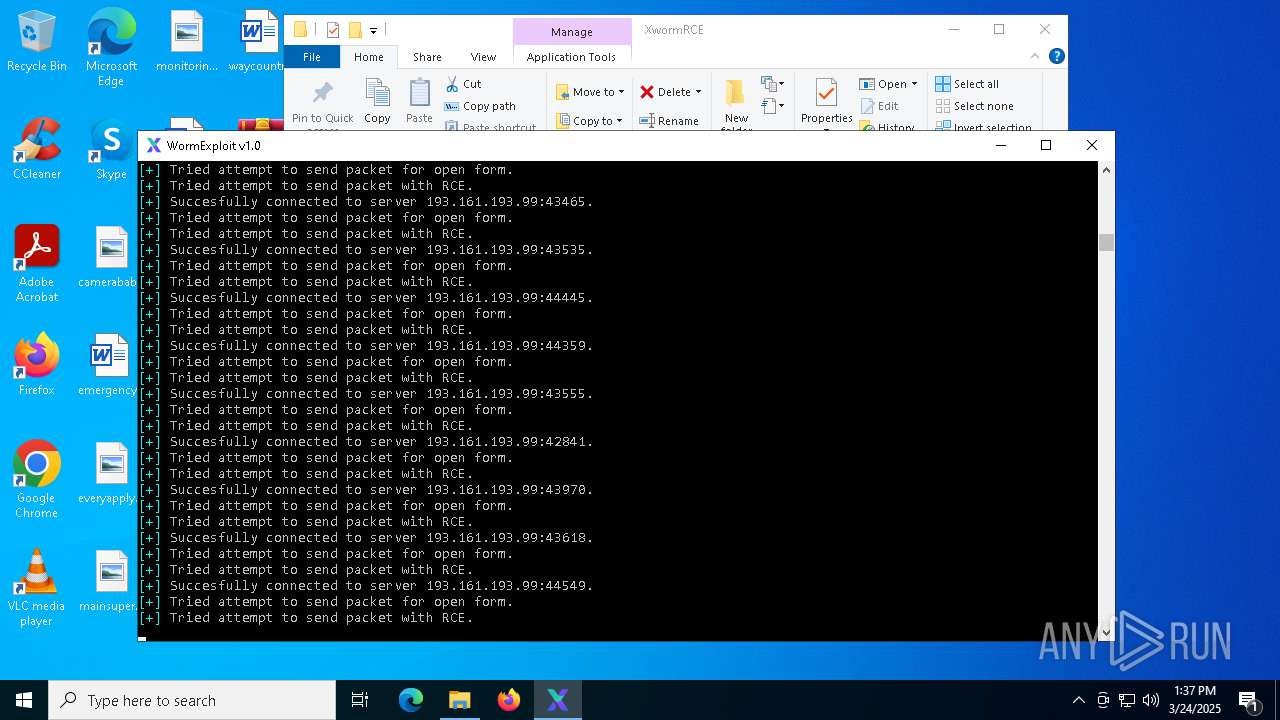
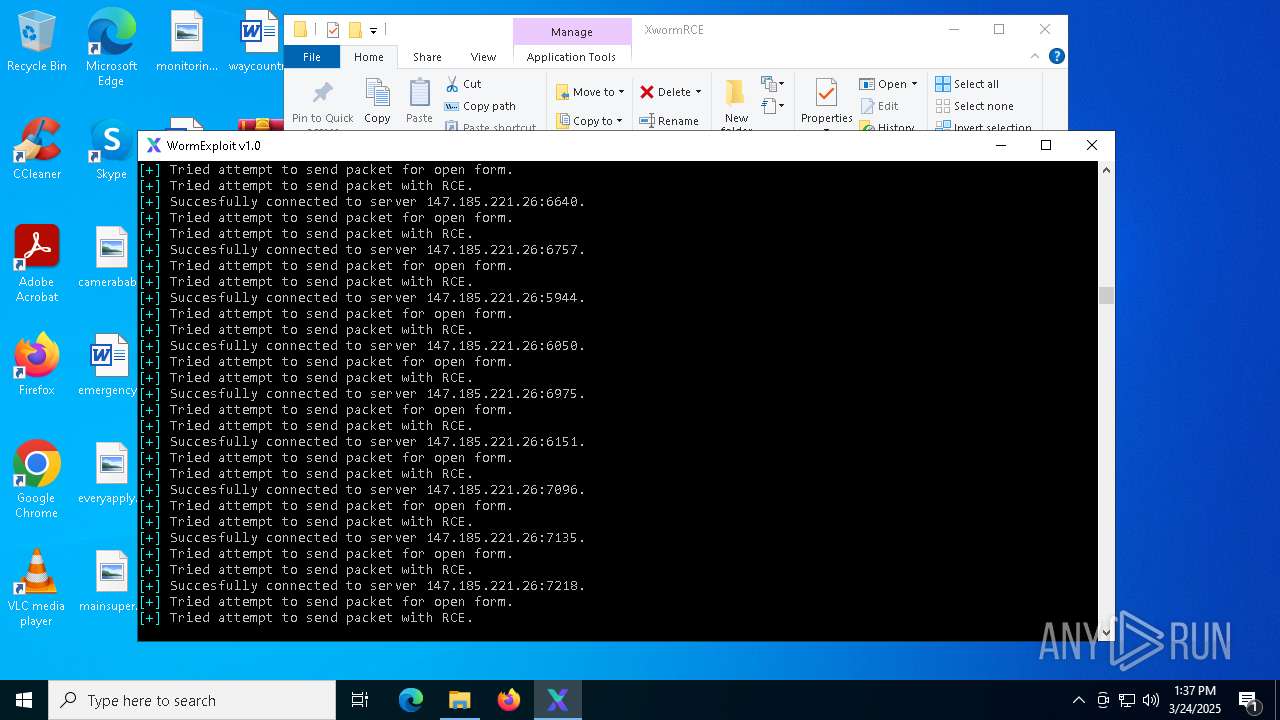
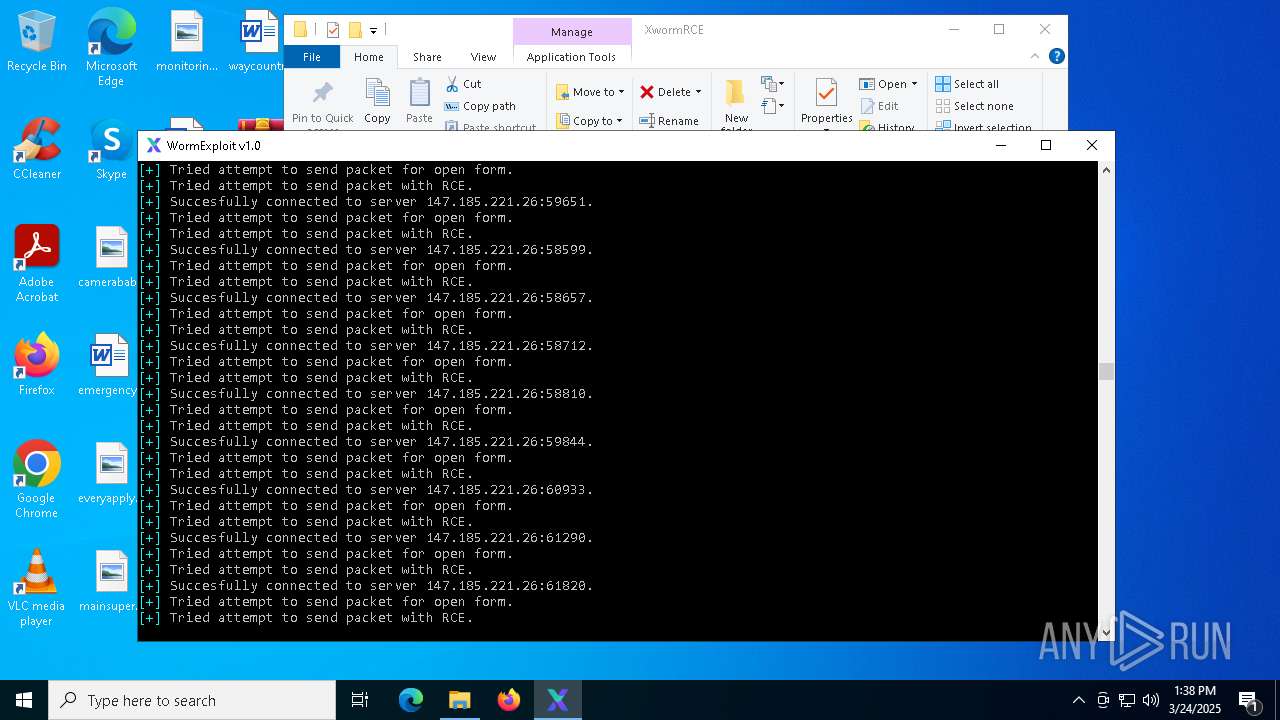
MALICIOUS
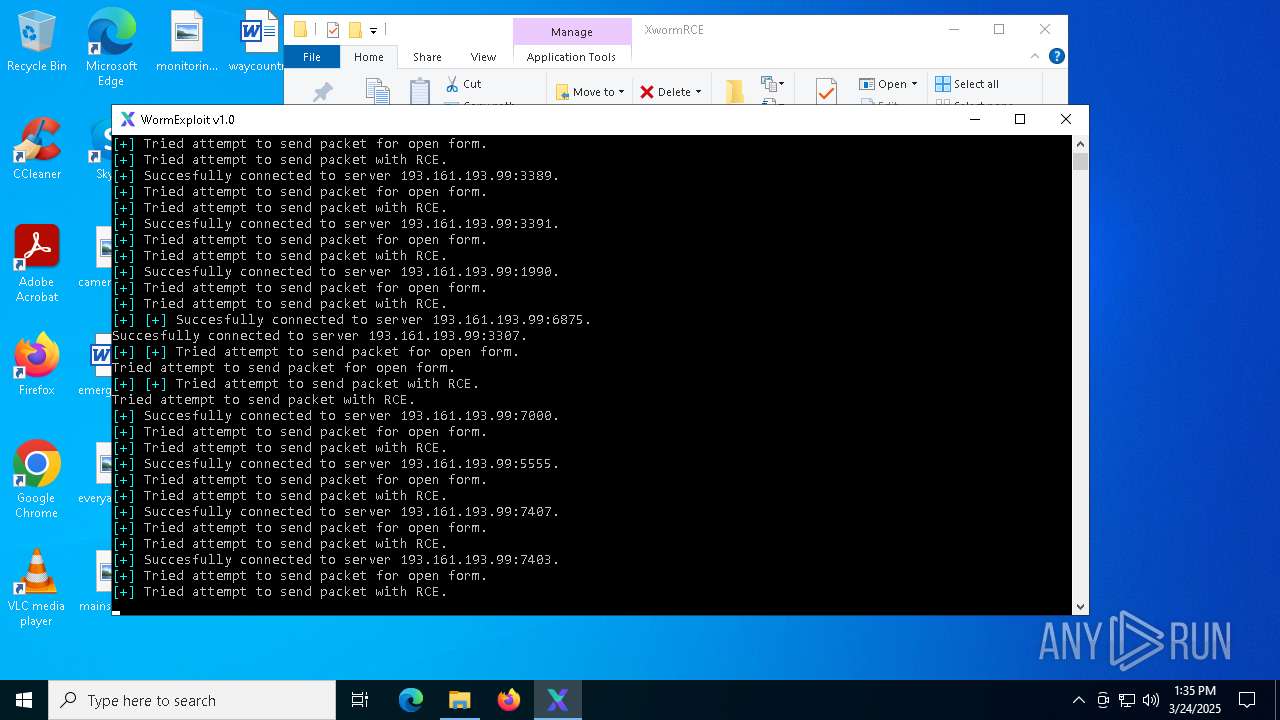
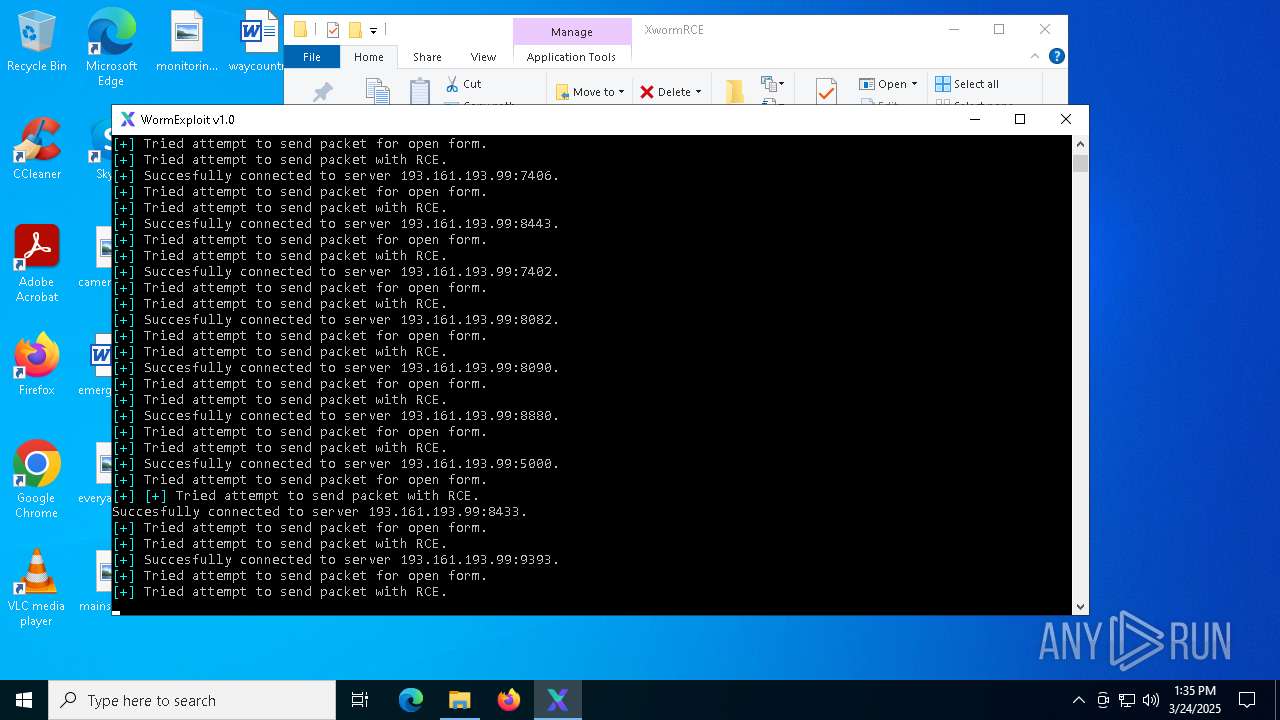
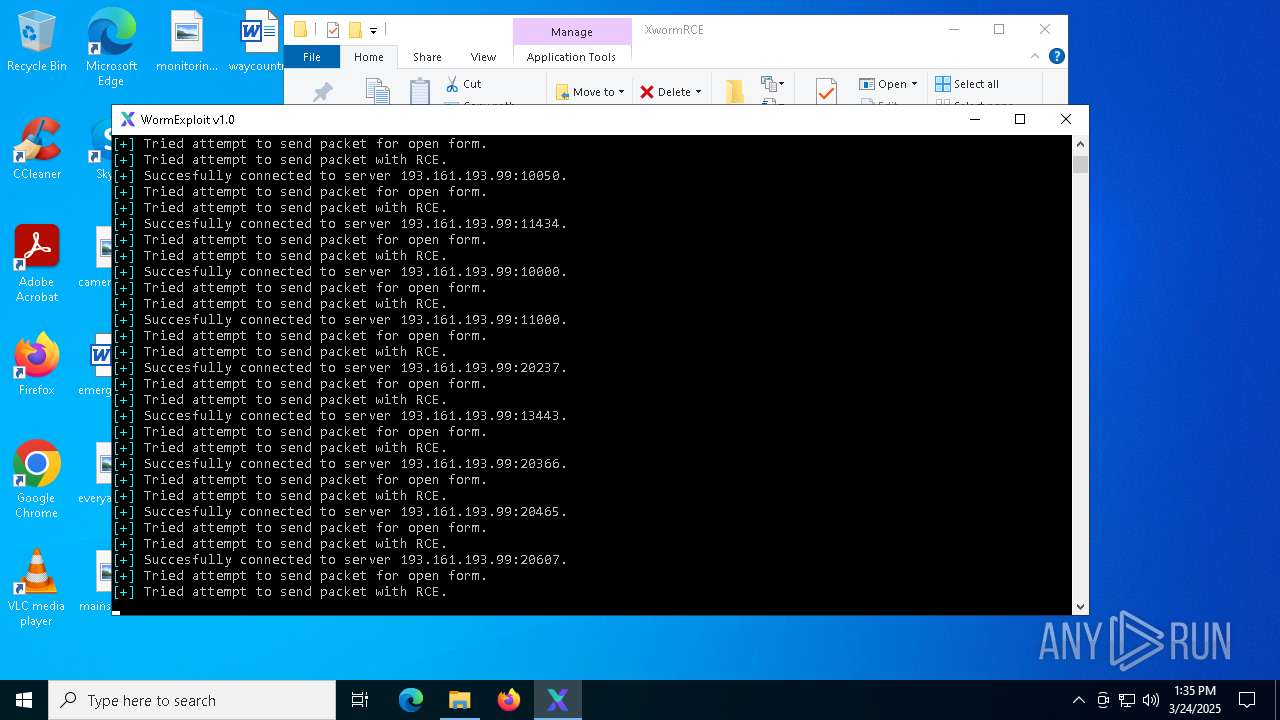
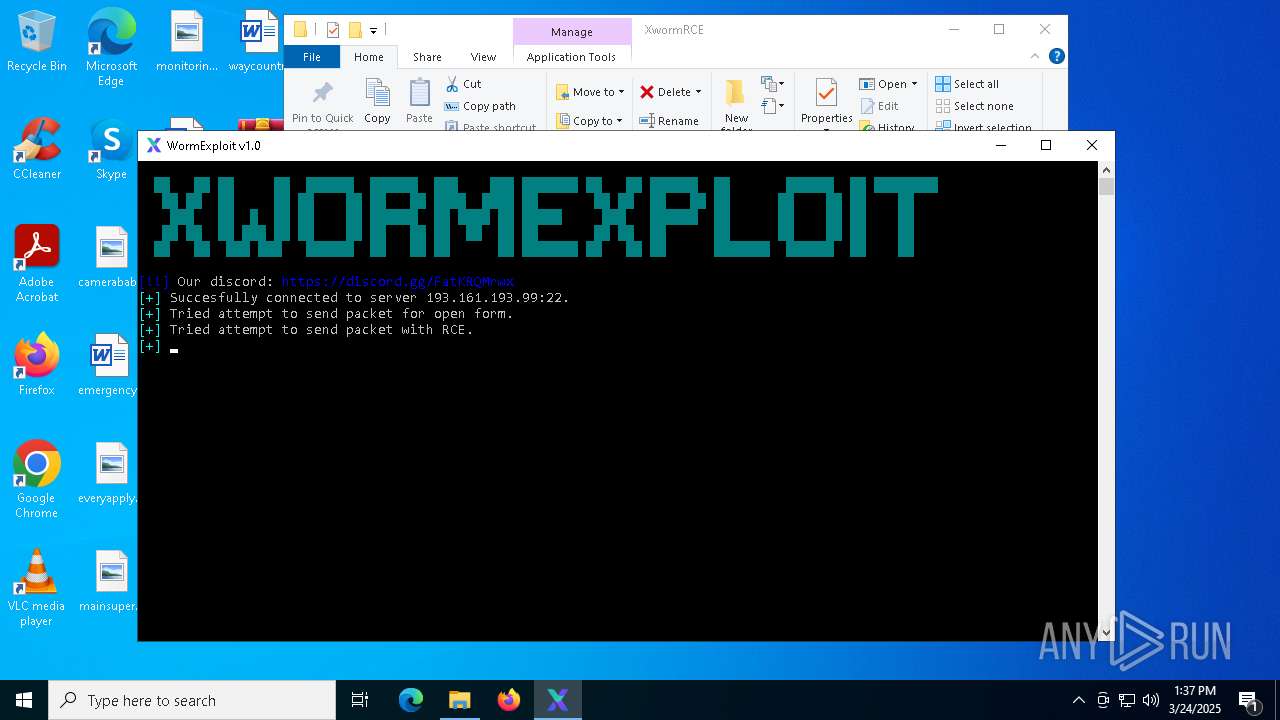
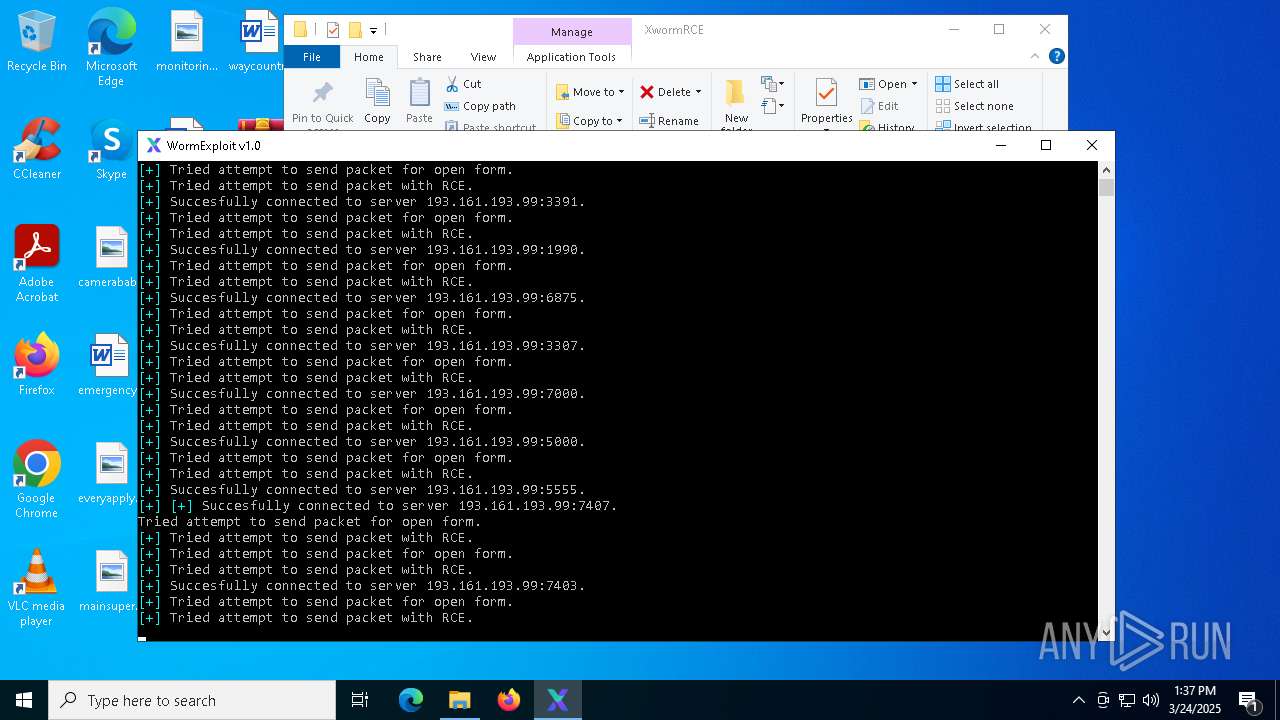
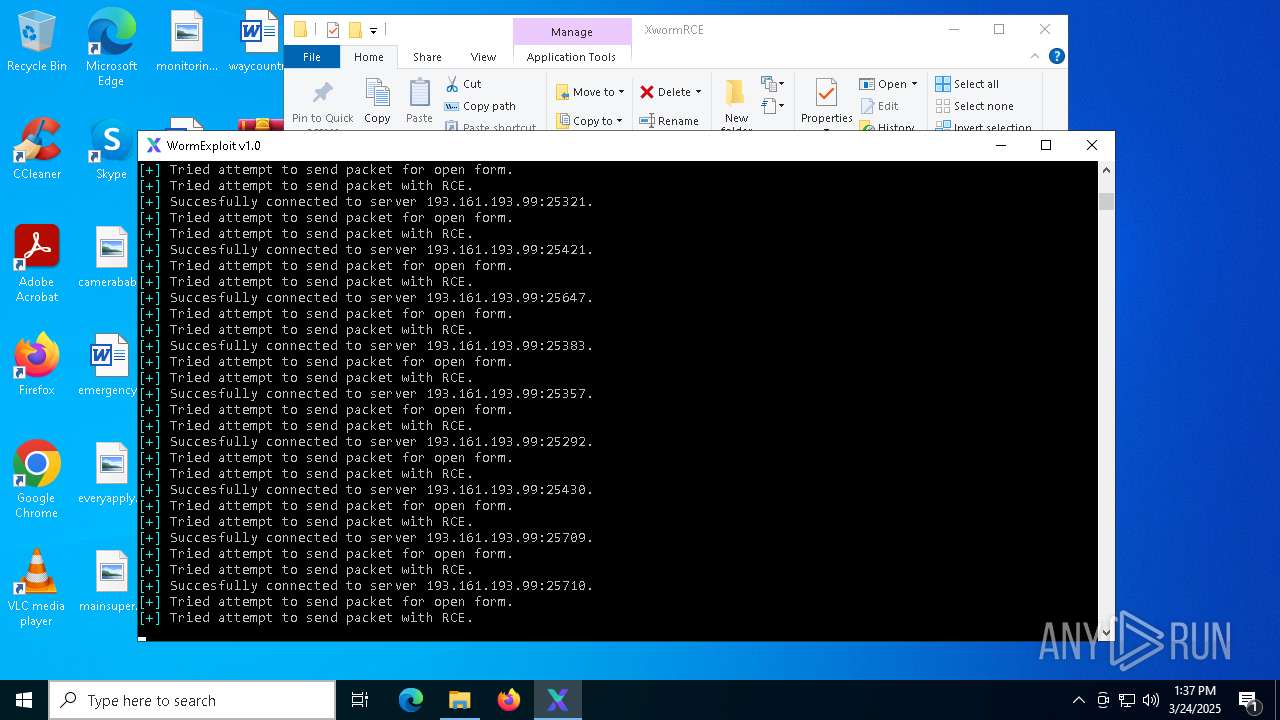
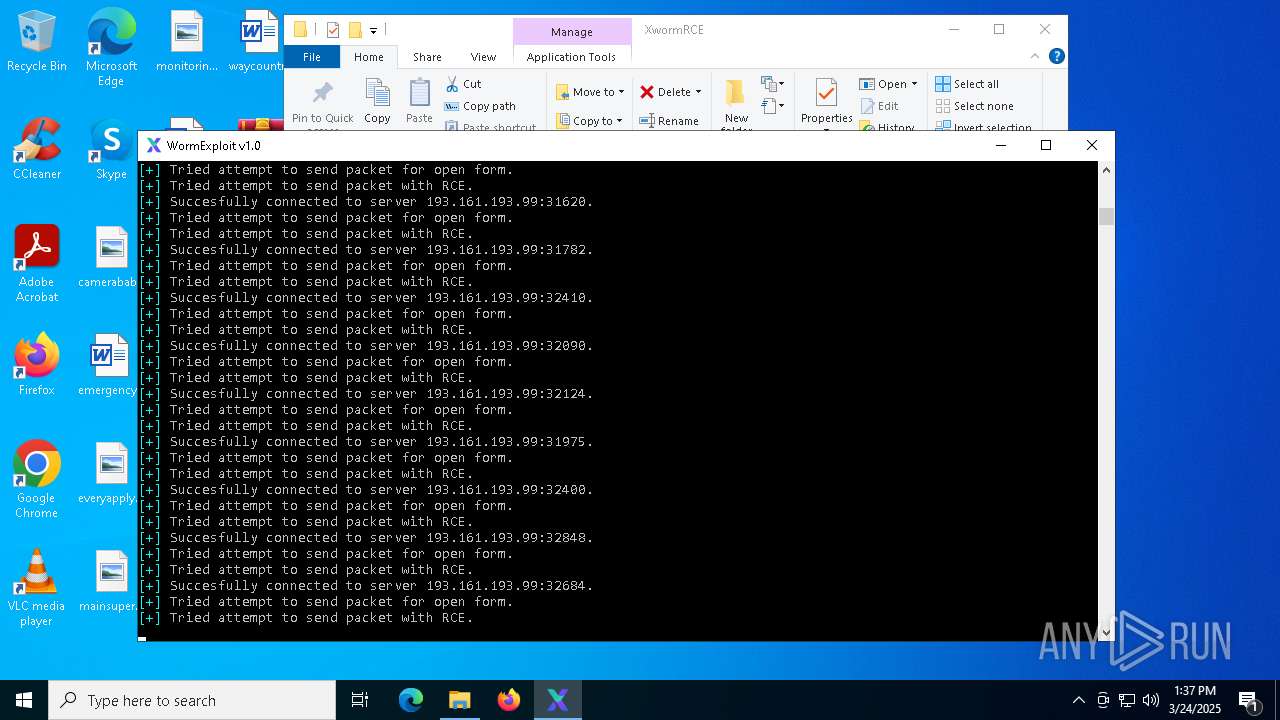
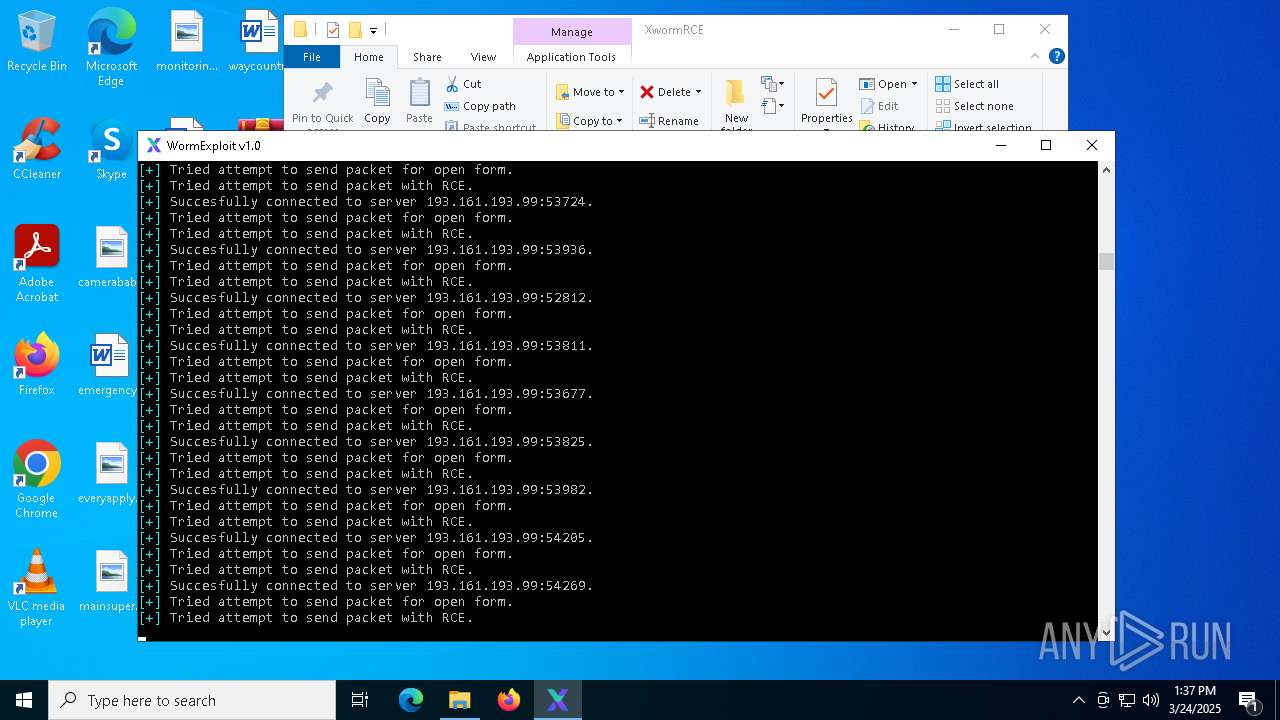
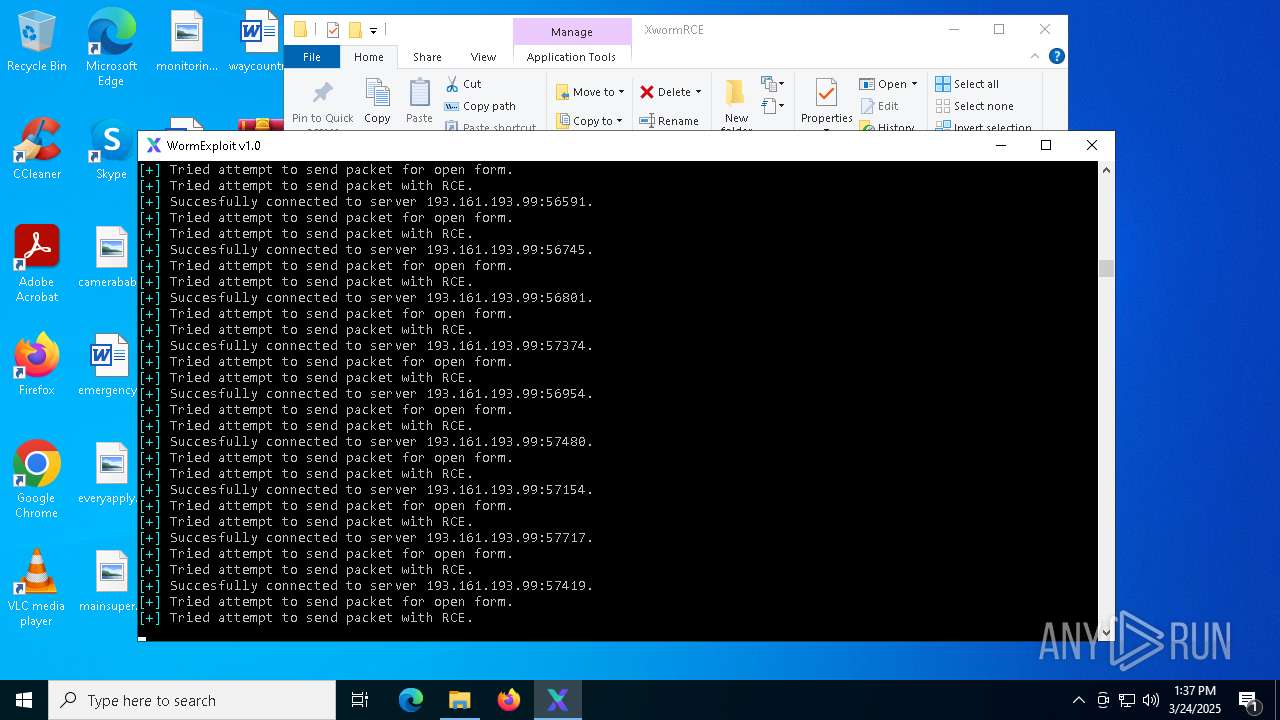
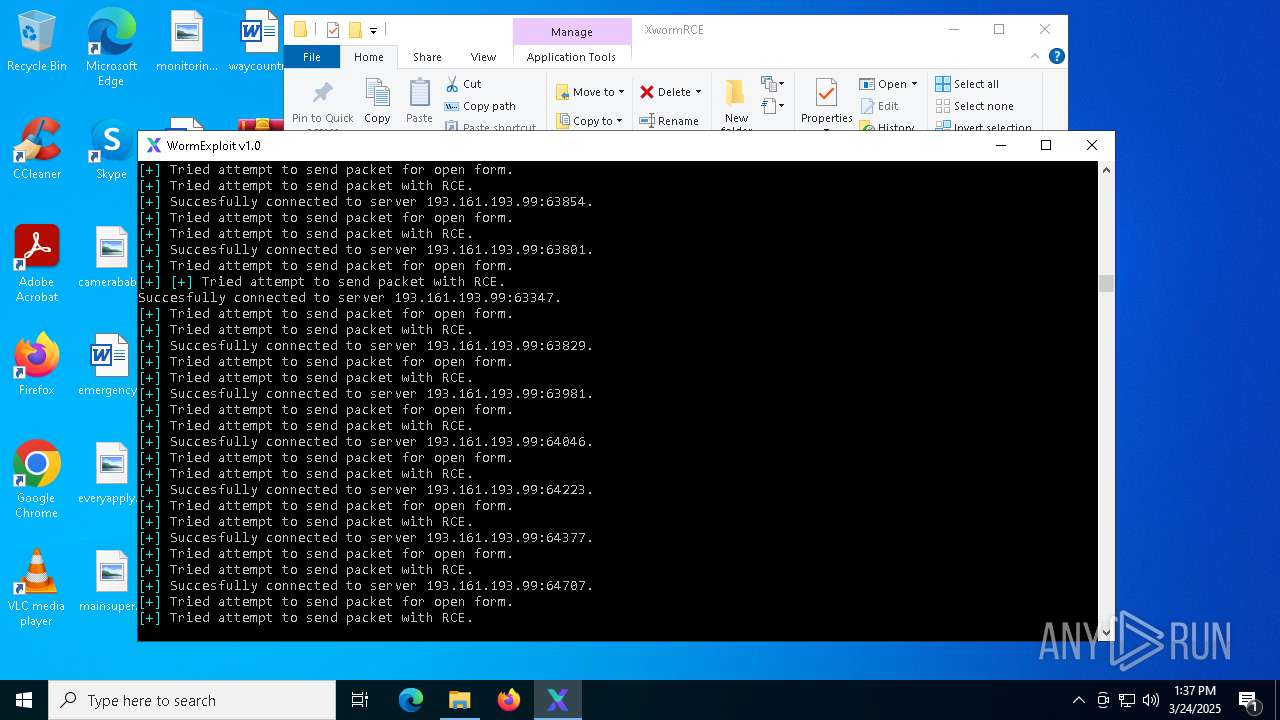
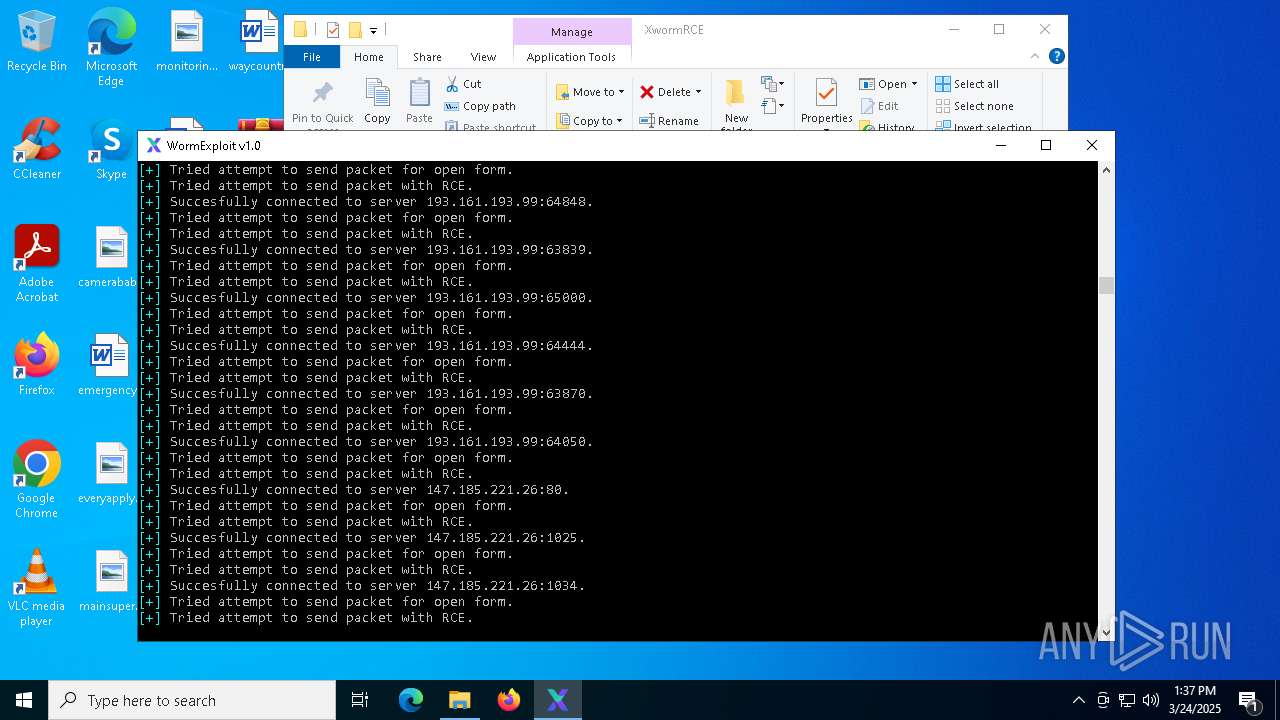
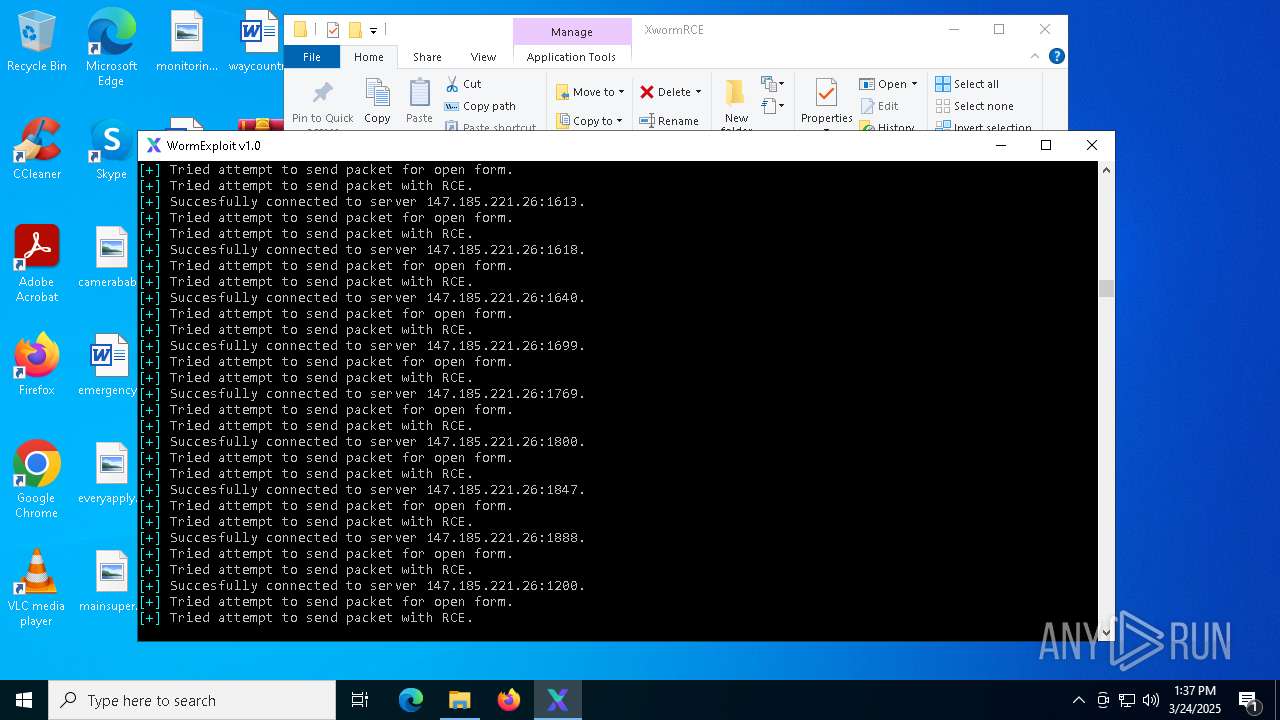
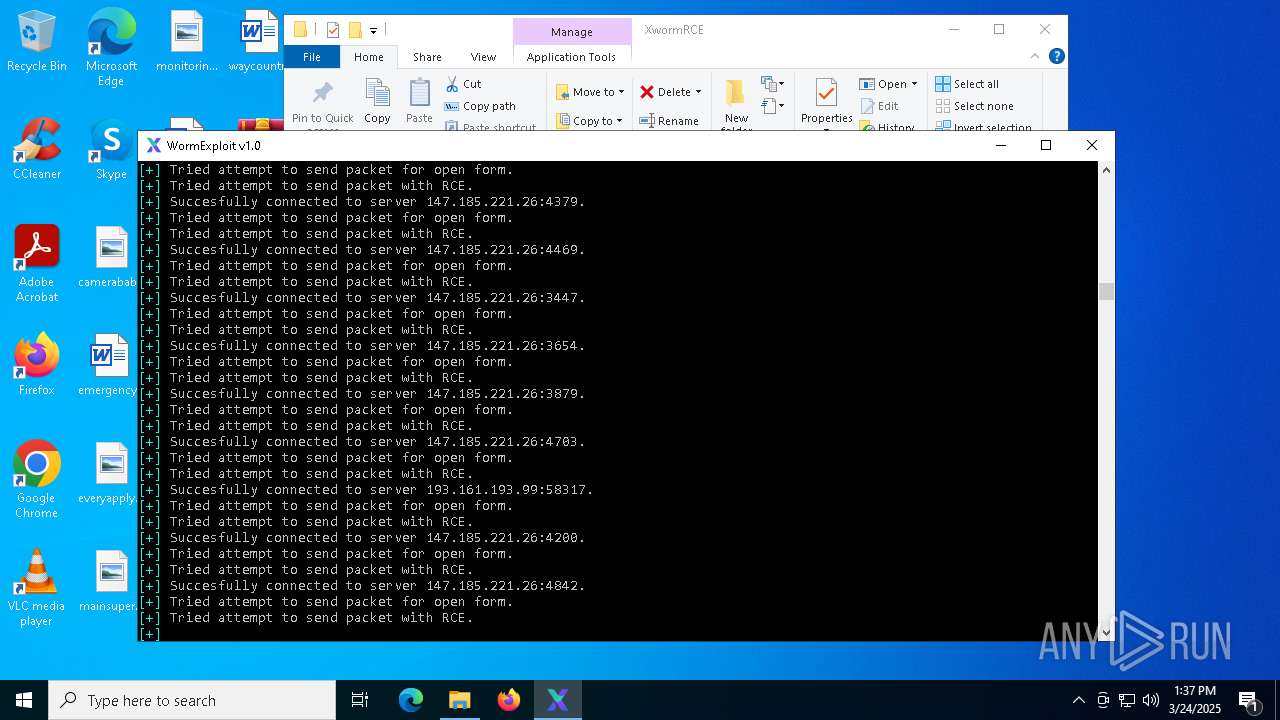
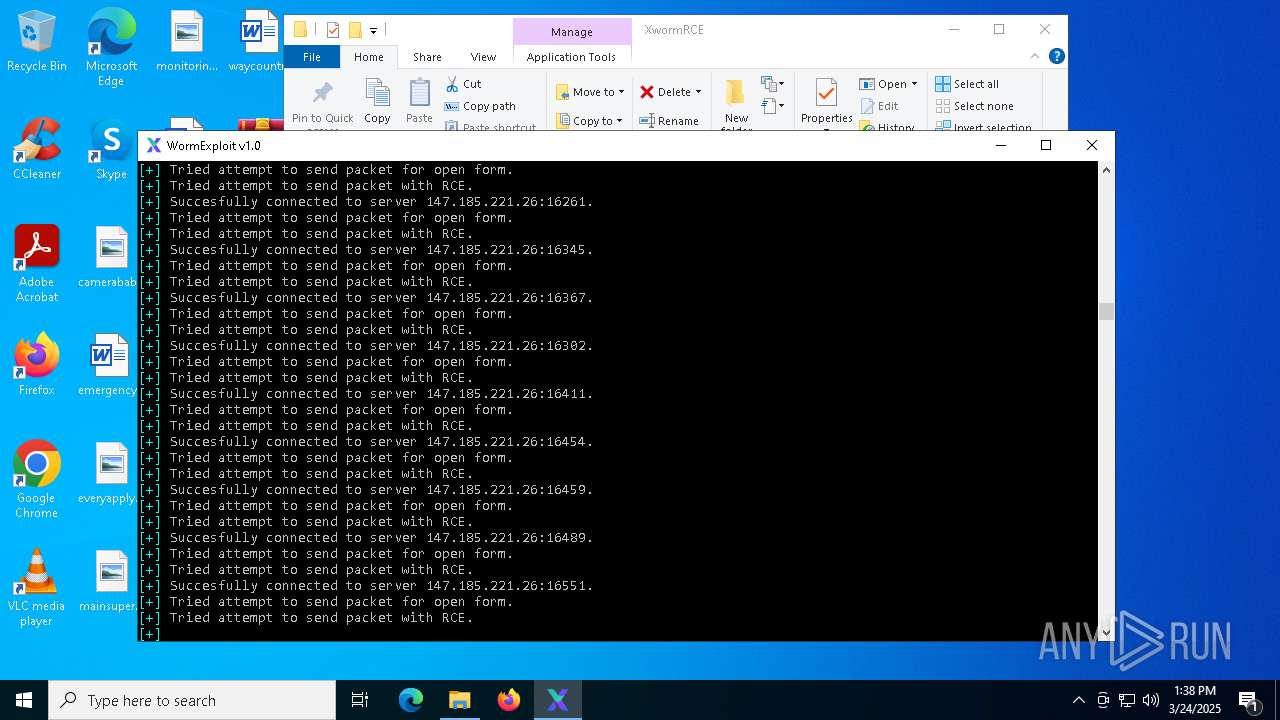
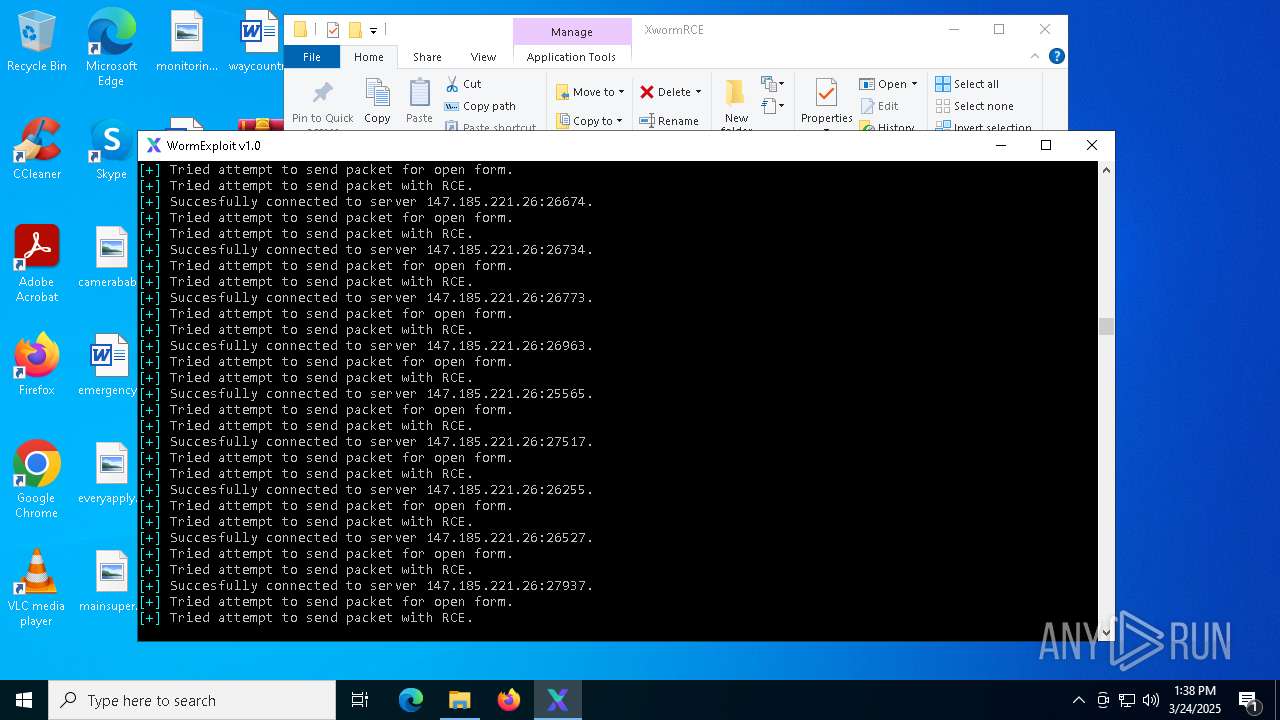
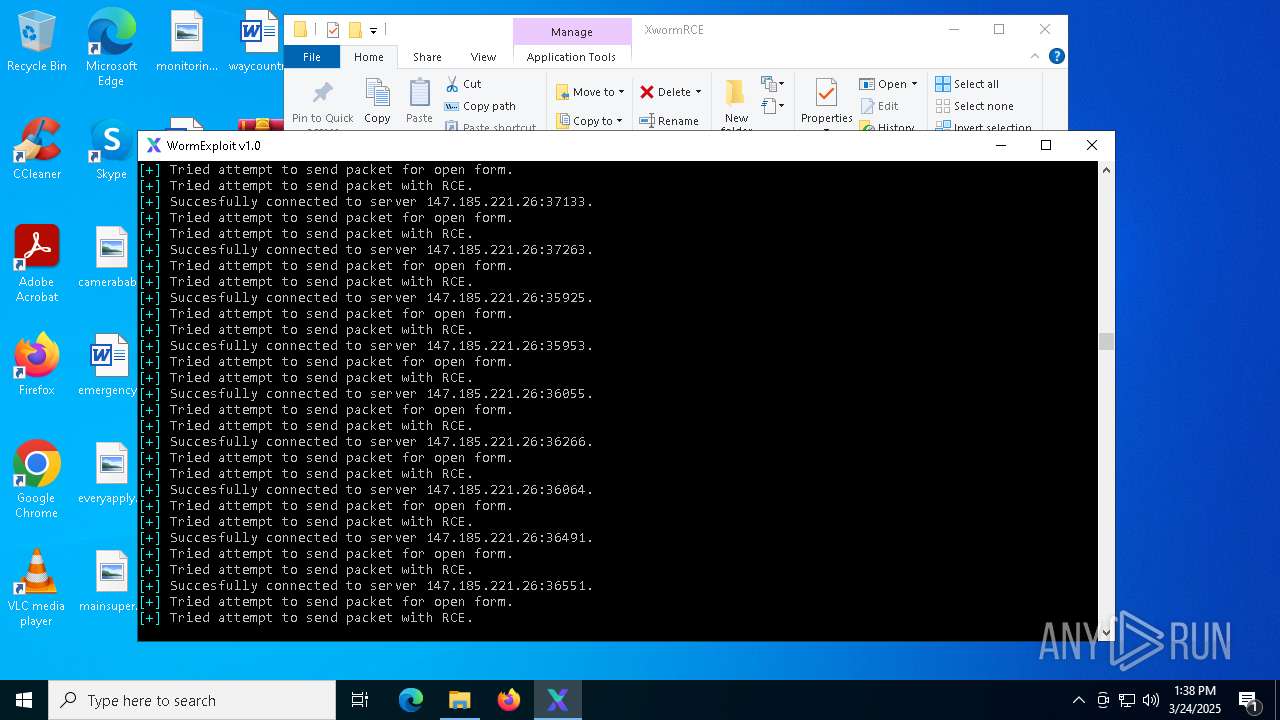
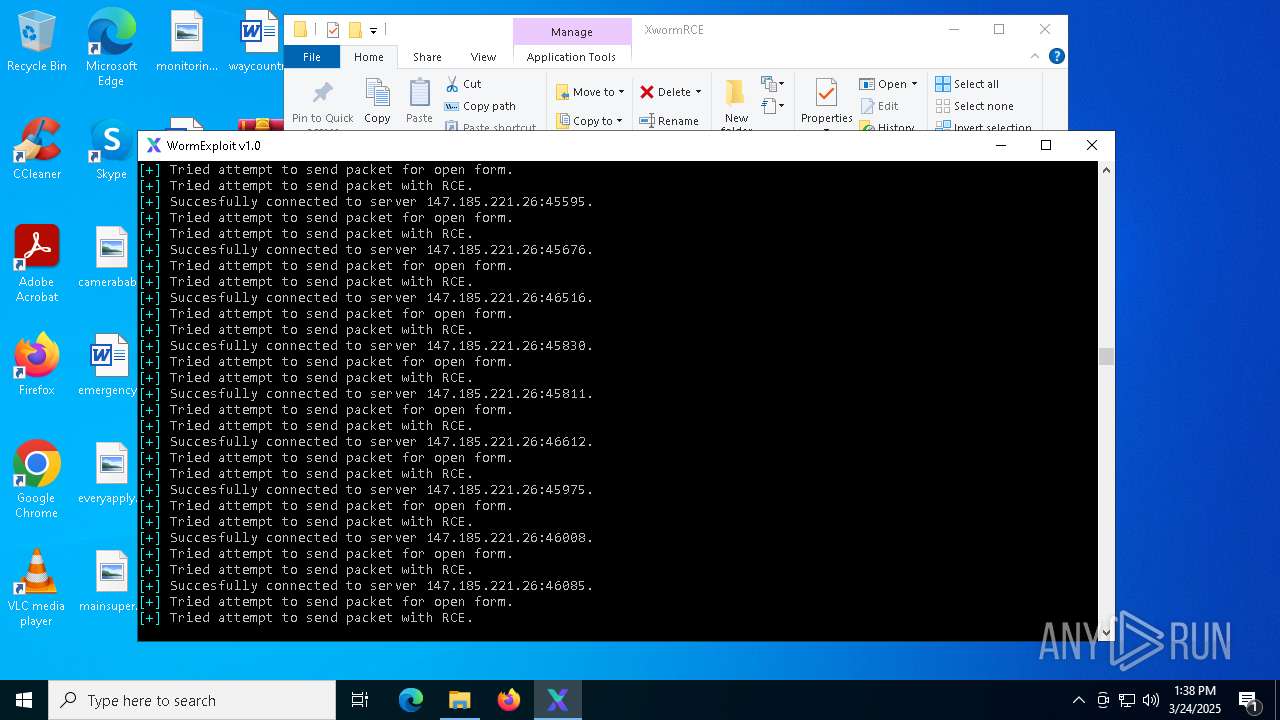
Attempting to connect via SSH
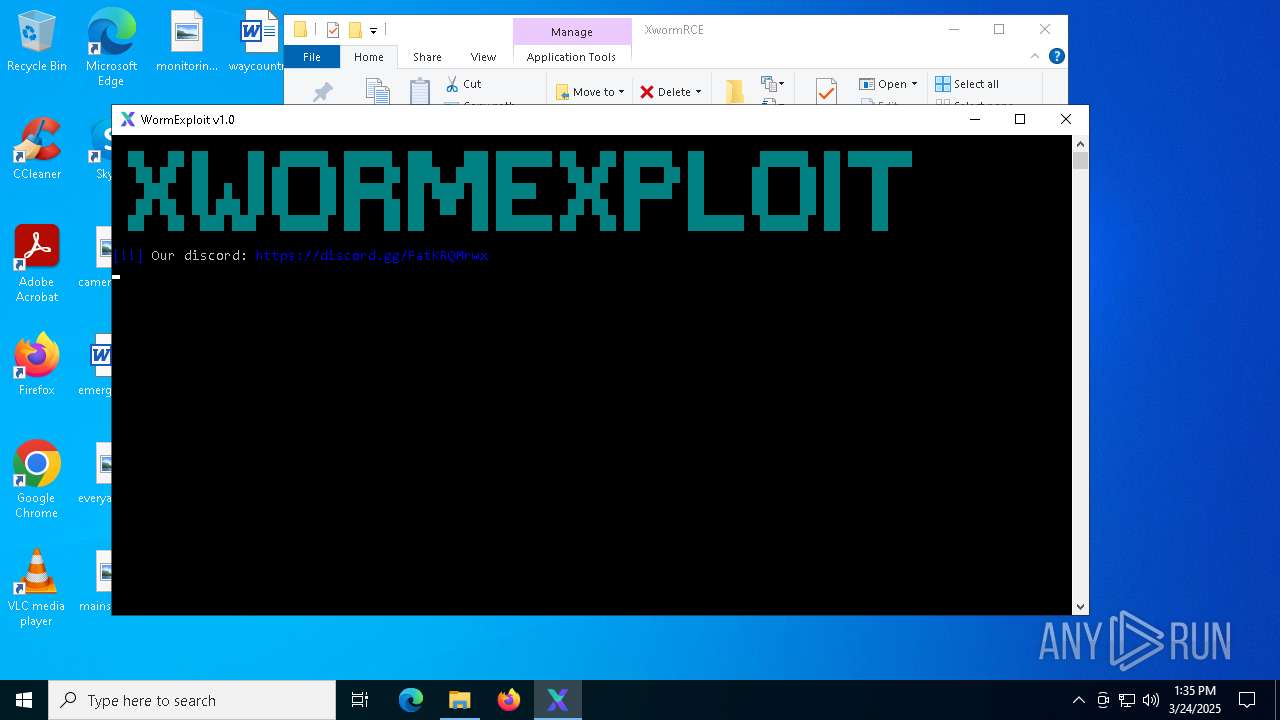
- Parser.exe (PID: 5936)
SUSPICIOUS
Connects to SSH
- Parser.exe (PID: 2096)
- Parser.exe (PID: 5936)
Potential Corporate Privacy Violation
- Parser.exe (PID: 2096)
- Parser.exe (PID: 5936)
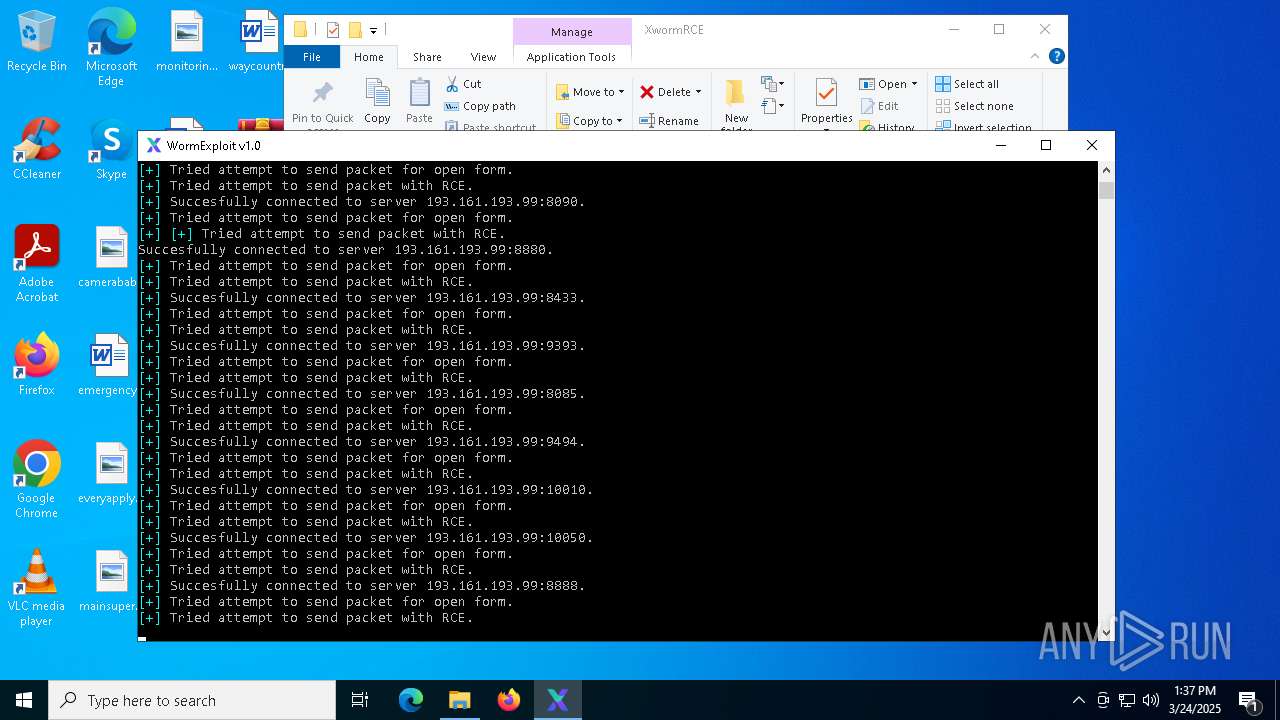
Connects to unusual port
- Parser.exe (PID: 2096)
- Parser.exe (PID: 5936)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7476)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 6876)
- BackgroundTransferHost.exe (PID: 7532)
- BackgroundTransferHost.exe (PID: 7820)
- notepad.exe (PID: 7452)
- BackgroundTransferHost.exe (PID: 5548)
- BackgroundTransferHost.exe (PID: 8128)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2136)
Checks supported languages
- Parser.exe (PID: 2096)
- ShellExperienceHost.exe (PID: 7476)
Manual execution by a user
- Parser.exe (PID: 2096)
- notepad.exe (PID: 7452)
- notepad.exe (PID: 7712)
- Parser.exe (PID: 5936)
Reads the machine GUID from the registry
- Parser.exe (PID: 2096)
Reads the computer name
- Parser.exe (PID: 2096)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7532)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7532)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:23 22:15:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | XwormRCE/ |
Total processes
153
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | "C:\Users\admin\Desktop\XwormRCE\Parser.exe" | C:\Users\admin\Desktop\XwormRCE\Parser.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WormExploit Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\XwormRCE (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Parser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5936 | "C:\Users\admin\Desktop\XwormRCE\Parser.exe" | C:\Users\admin\Desktop\XwormRCE\Parser.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WormExploit Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6876 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Parser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 026
Read events
5 991
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\XwormRCE (1).zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
2
Suspicious files
5
Text files
3
Unknown types
0
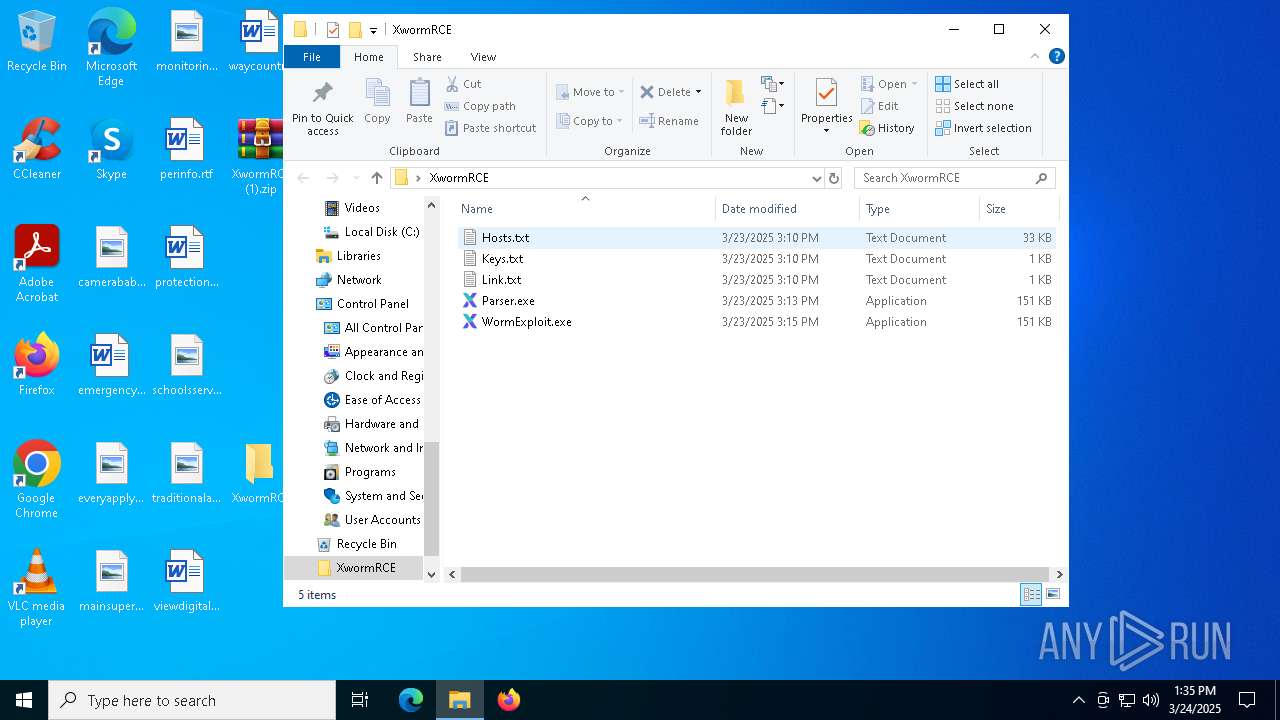
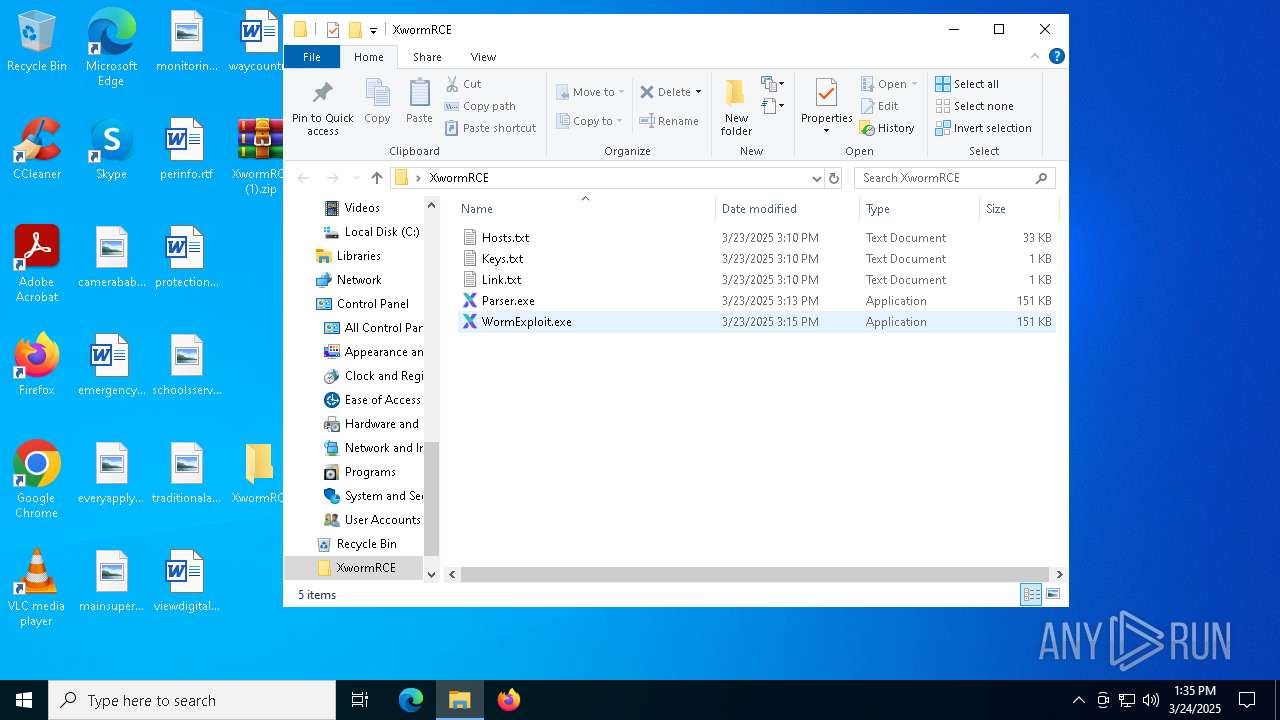
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\d2ae94d6-193f-49ad-b2f2-3ba9ea04de0d.down_data | — | |
MD5:— | SHA256:— | |||
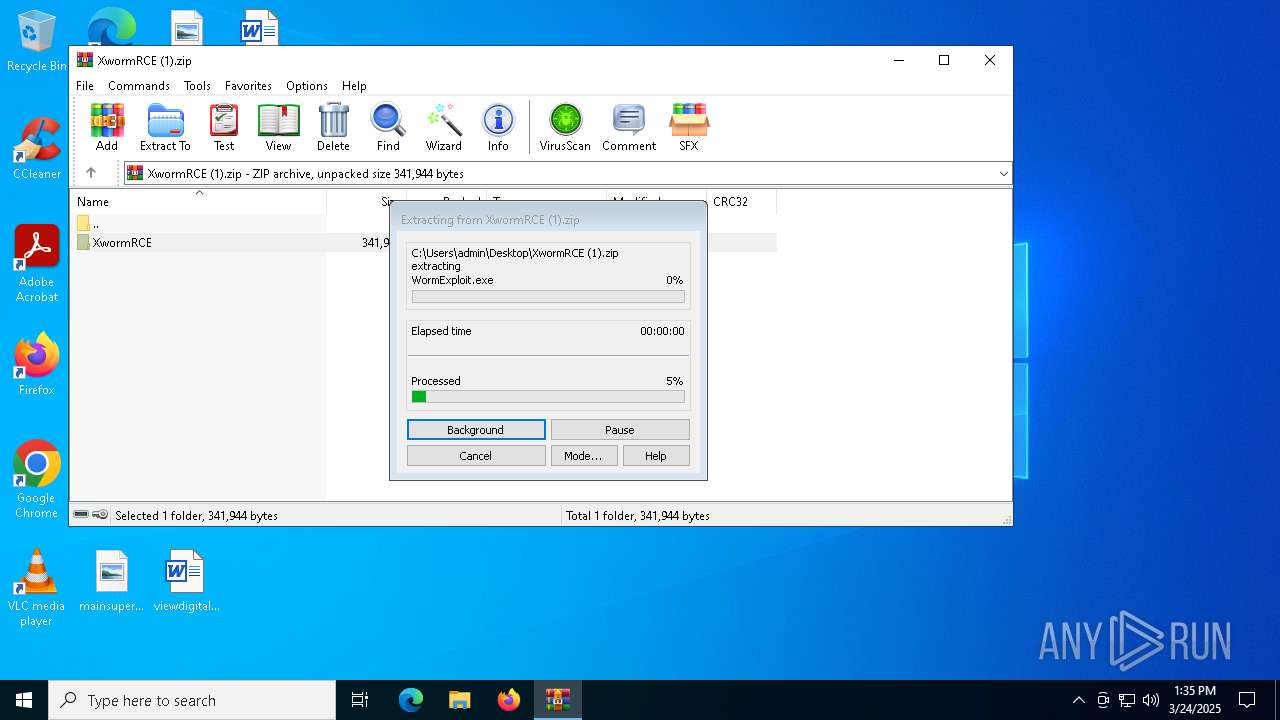
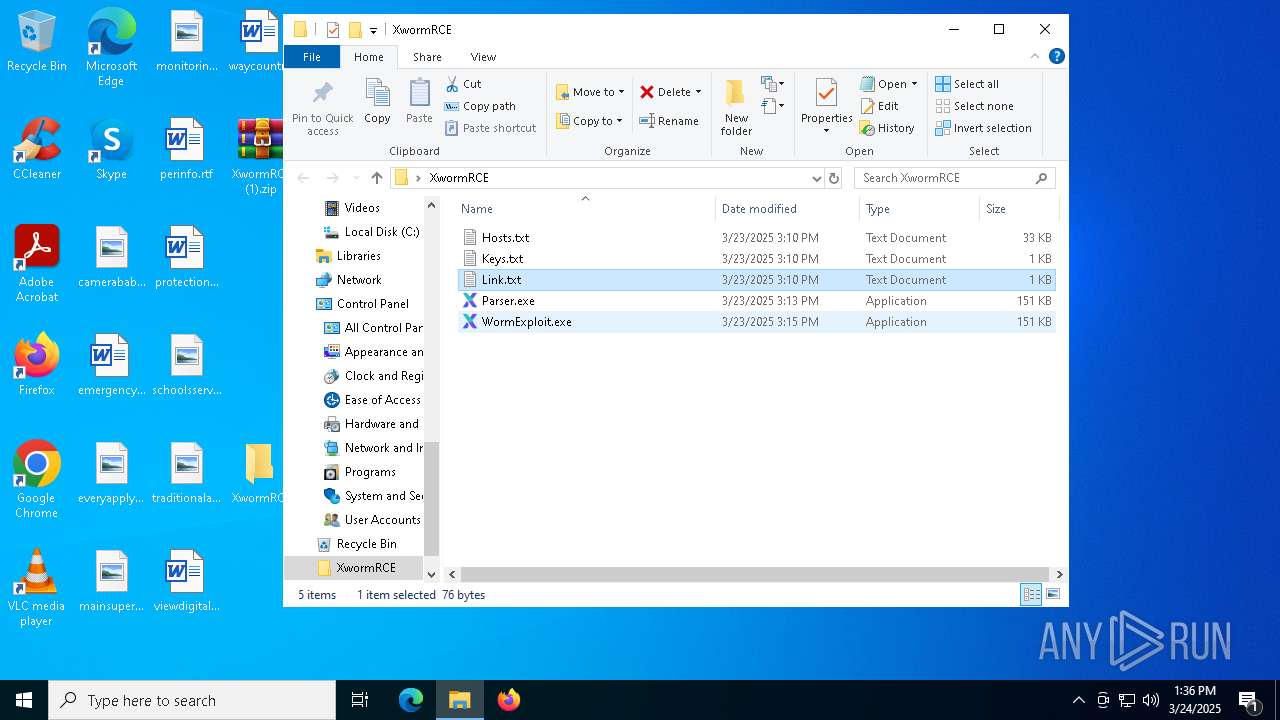
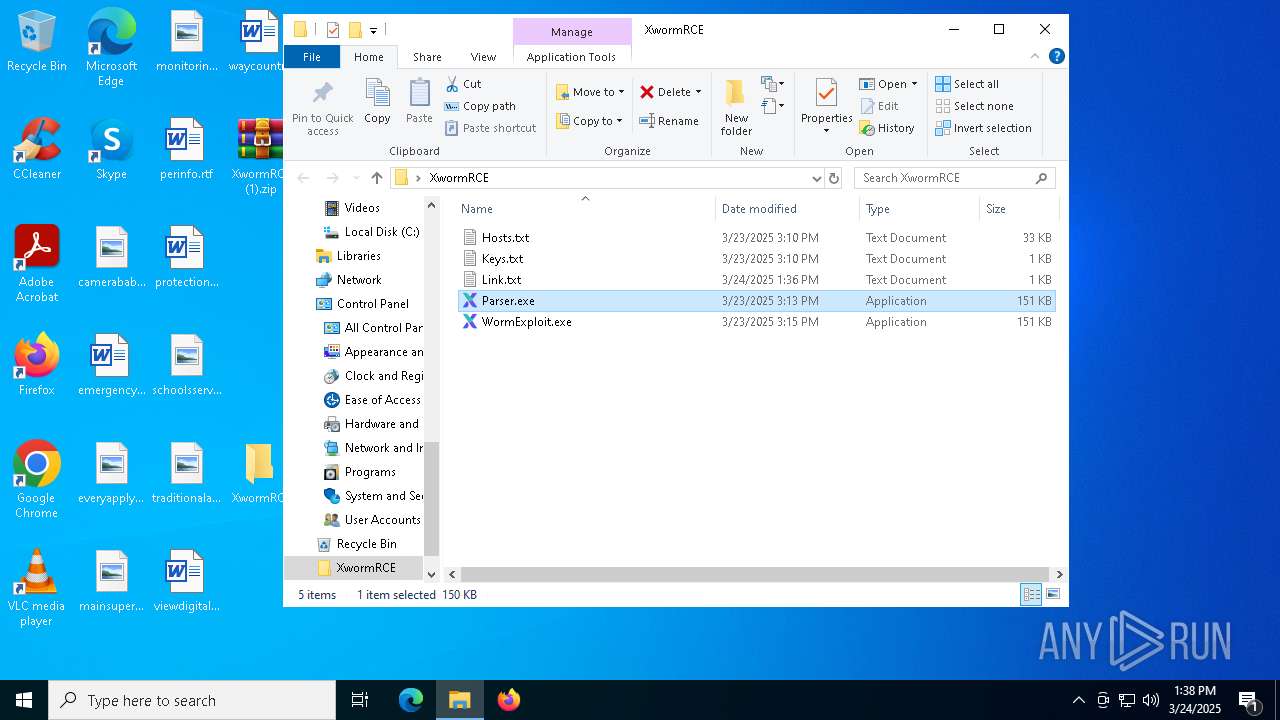
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.14392\XwormRCE\WormExploit.exe | executable | |
MD5:F58D26874C31720F73427619E91B422B | SHA256:661F61CCAA12D2618F19C3ACFDC370B481CECD1AFA491B4CCD8FF6AAEF85DFA7 | |||
| 7532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C1C4070B5680162ADBB25F96BDC30148 | SHA256:BDB8523F4D6B138A1A5BBCE35BAD43282CA8873F230879B120FB17A25B65C571 | |||
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.14392\XwormRCE\Hosts.txt | text | |
MD5:4017F359961D2DBFC8CF78ADF39E6935 | SHA256:C091A12783952DBB0CA2D533A51BD85599B30C4C3B723F0ADA25C70E0E91F8D5 | |||
| 7532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\03ad2484-8313-4b2c-97a0-06d73482de10.afb0cbf7-9553-455b-9c26-a8799f296624.down_meta | binary | |
MD5:76D3487639615213102D61BCE6E4B4D5 | SHA256:49E1BFC0A7B7AD83FA2EB74E1BEA2908552575CC87EE915A1FD7EAF4C6E9D673 | |||
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.14392\XwormRCE\Parser.exe | executable | |
MD5:173BD881FB873BCF16AD22059D56461A | SHA256:E5D5CCF8B1E629ED66D89DFF92F5689336D1AA3AA5551C0BEE3B658035DD820A | |||
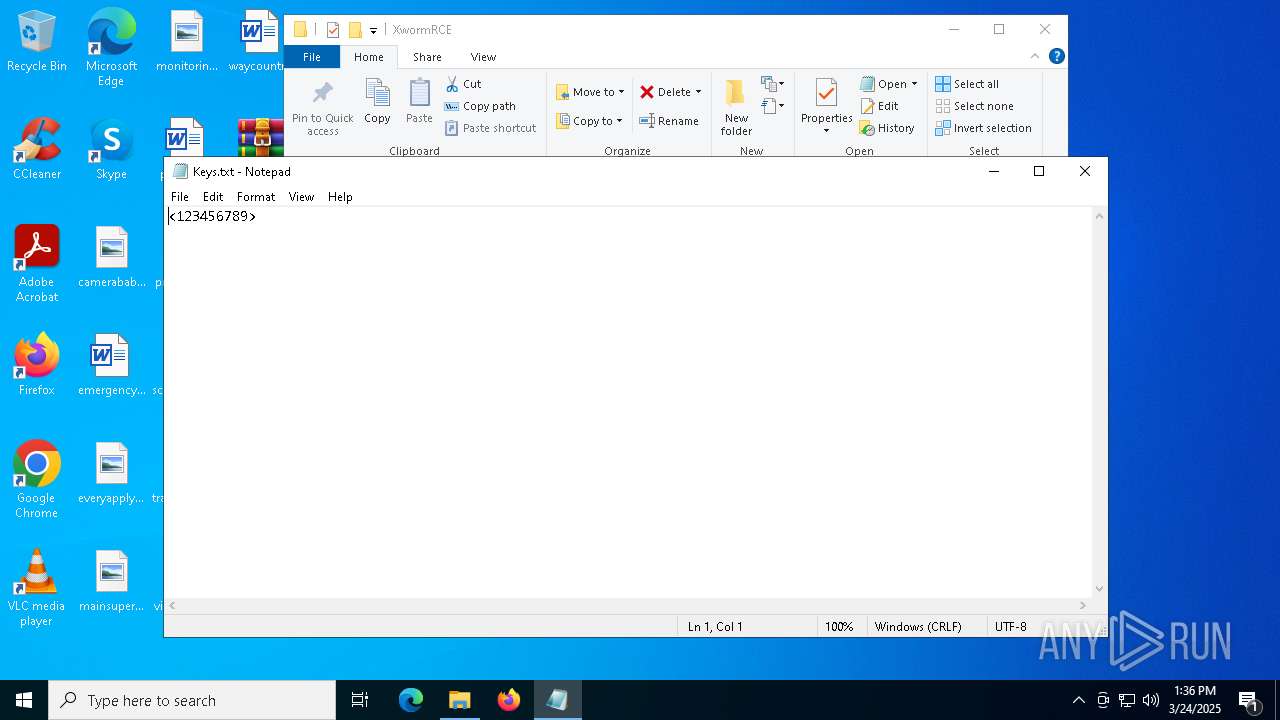
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.14392\XwormRCE\Keys.txt | text | |
MD5:DADEFDFD3DF5BA731438E7569F826962 | SHA256:D642578EED80496DBEDB64D1836A8319CA9AFDA202737D5B08211C6CB8E94EB1 | |||
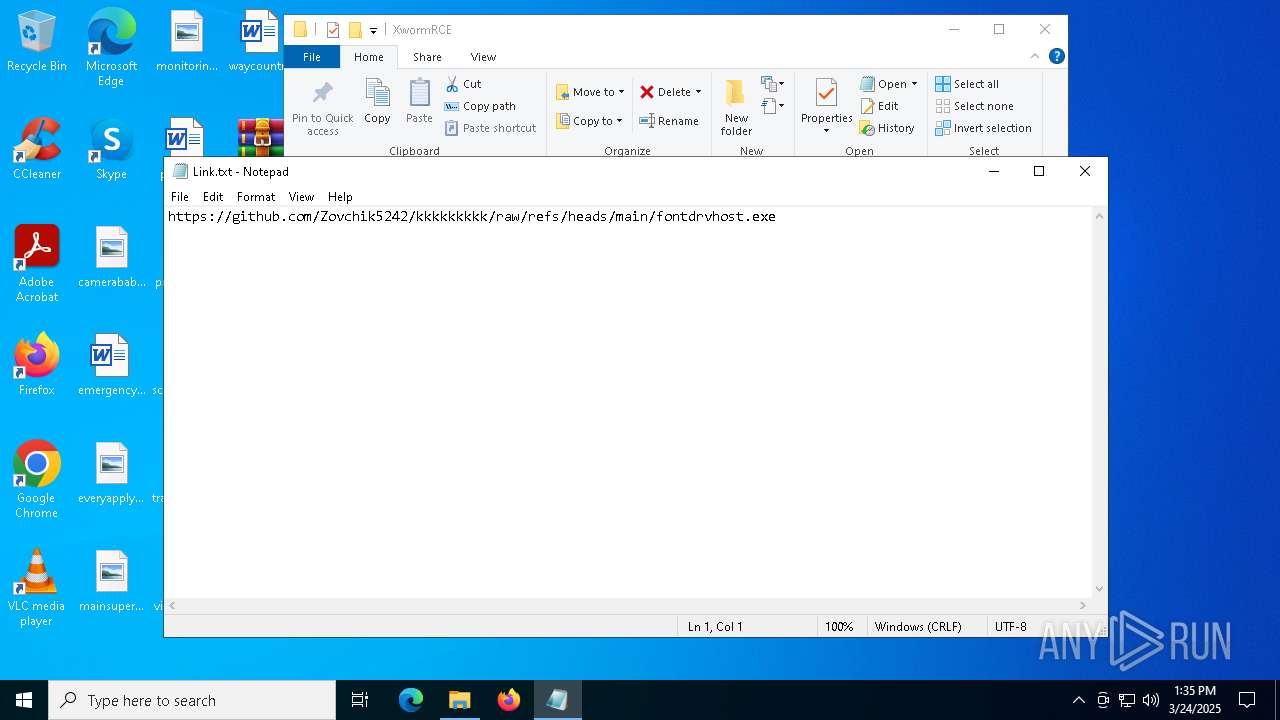
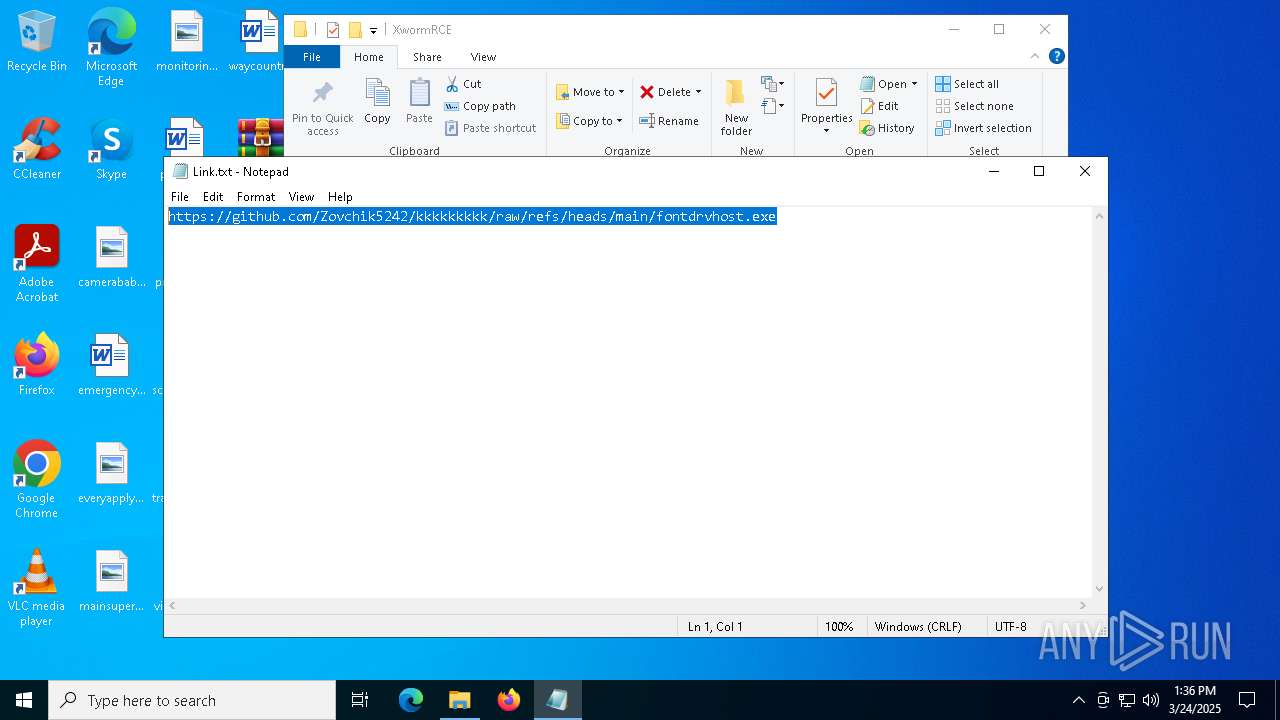
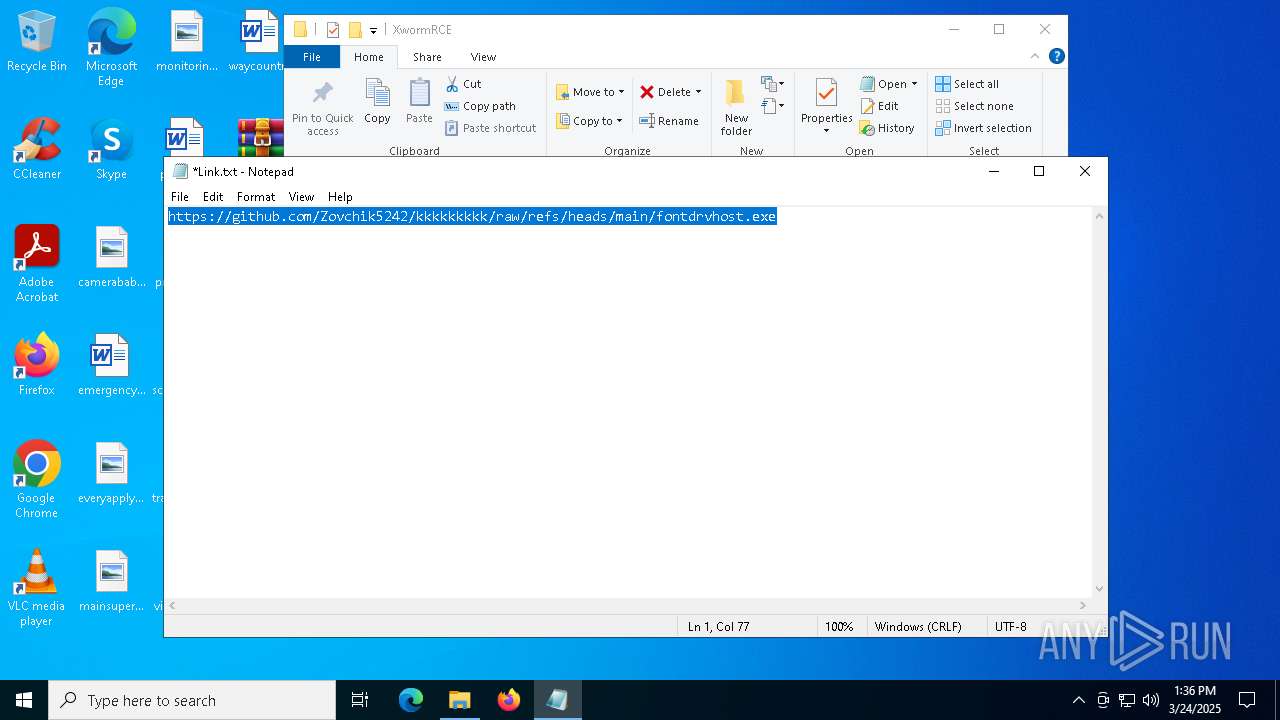
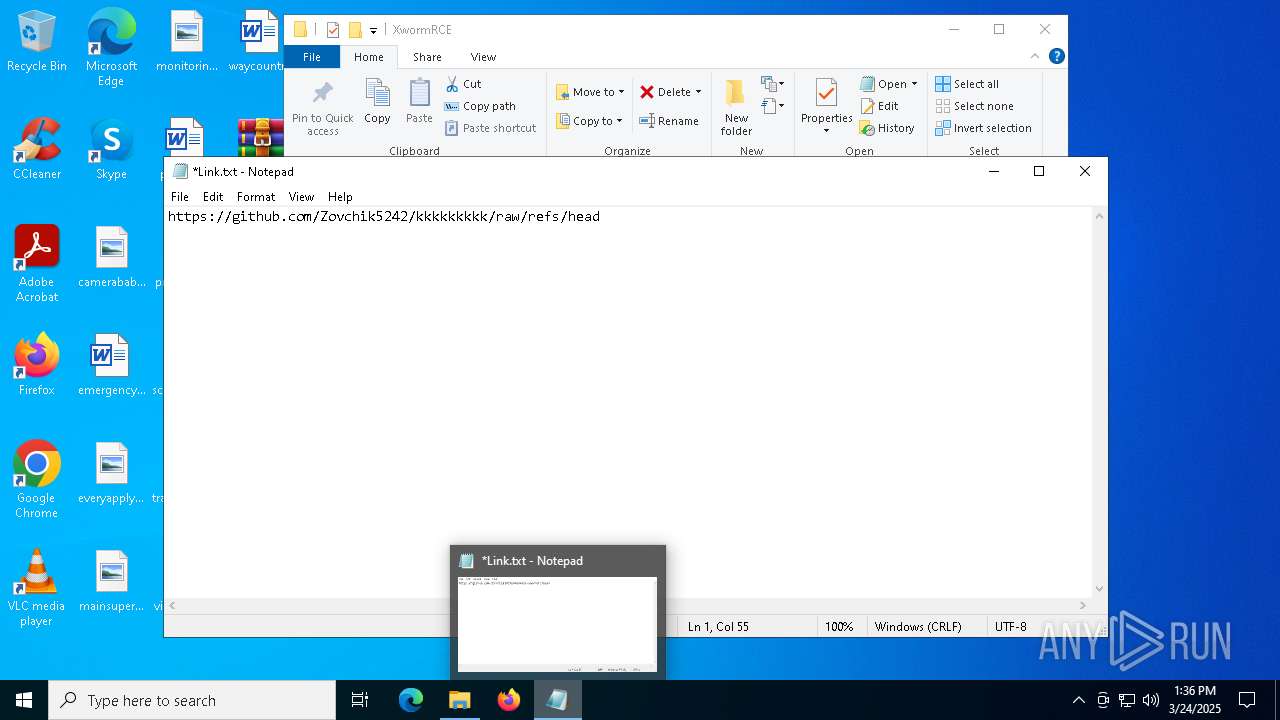
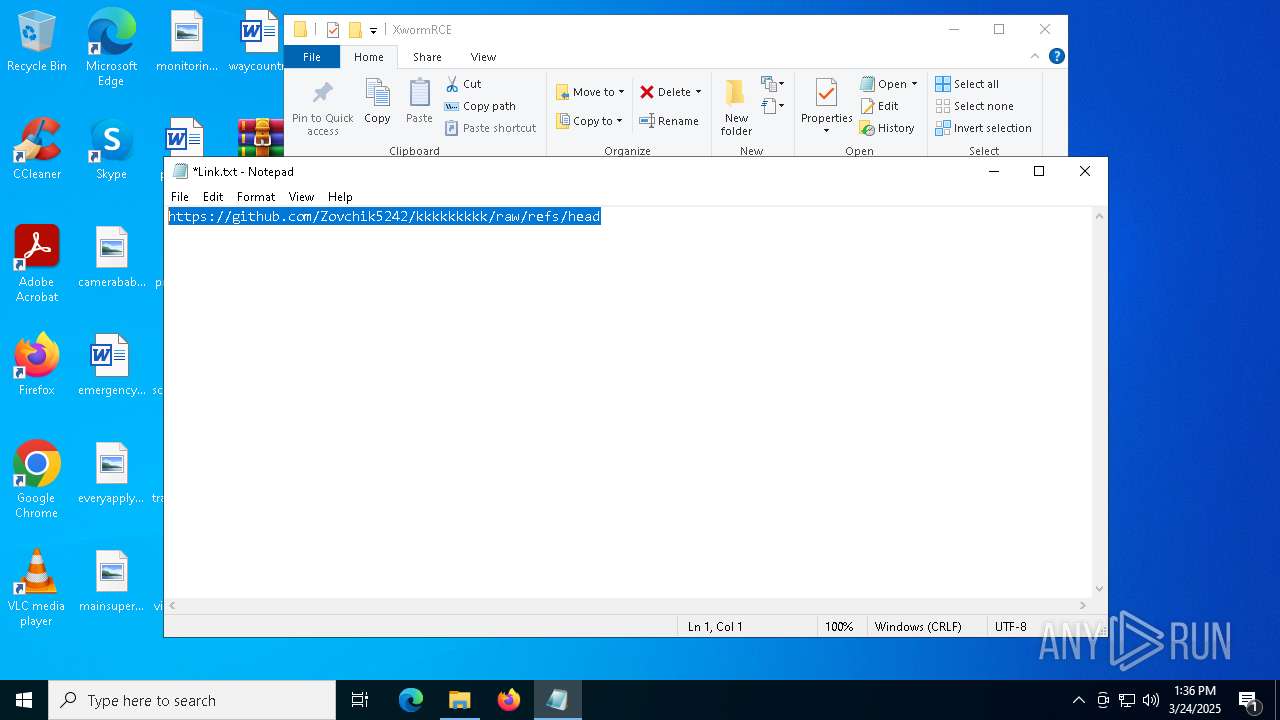
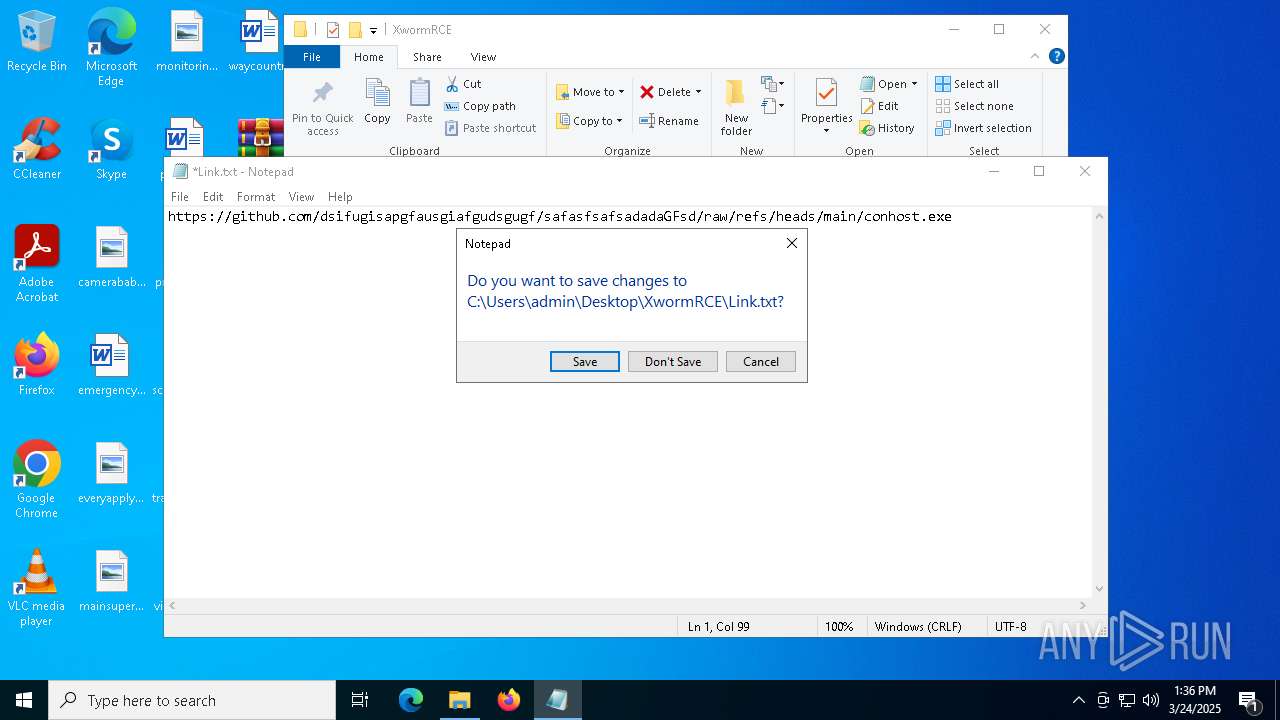
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.14392\XwormRCE\Link.txt | text | |
MD5:D91C5D75432012A1E599EBDFCDFF083C | SHA256:4AC9C91EE87E2978E5A2FA58B6BE229BC20BF69C64402A35ED867E44FA1A549D | |||
| 7532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\d2ae94d6-193f-49ad-b2f2-3ba9ea04de0d.afb0cbf7-9553-455b-9c26-a8799f296624.down_meta | binary | |
MD5:76D3487639615213102D61BCE6E4B4D5 | SHA256:49E1BFC0A7B7AD83FA2EB74E1BEA2908552575CC87EE915A1FD7EAF4C6E9D673 | |||
| 7532 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\03ad2484-8313-4b2c-97a0-06d73482de10.up_meta_secure | binary | |
MD5:1D3048378B20EE82FC1696F134A7A3C7 | SHA256:DA4B6F76B6C84D6CF91ECEEA106E63EFDB0B0C26D50900A7BD4646CD6413C7E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
1 956
DNS requests
17
Threats
71
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2088 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7532 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2088 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2088 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA HTTP METHOD terminated by non-compliant character |
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |
2096 | Parser.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A SSH banner has been detected |
2096 | Parser.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A SSH banner has been detected on a non-standard port number |
2096 | Parser.exe | Generic Protocol Command Decode | SURICATA SSH invalid banner |
2096 | Parser.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A SSH banner has been detected |
2096 | Parser.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A SSH banner has been detected on a non-standard port number |