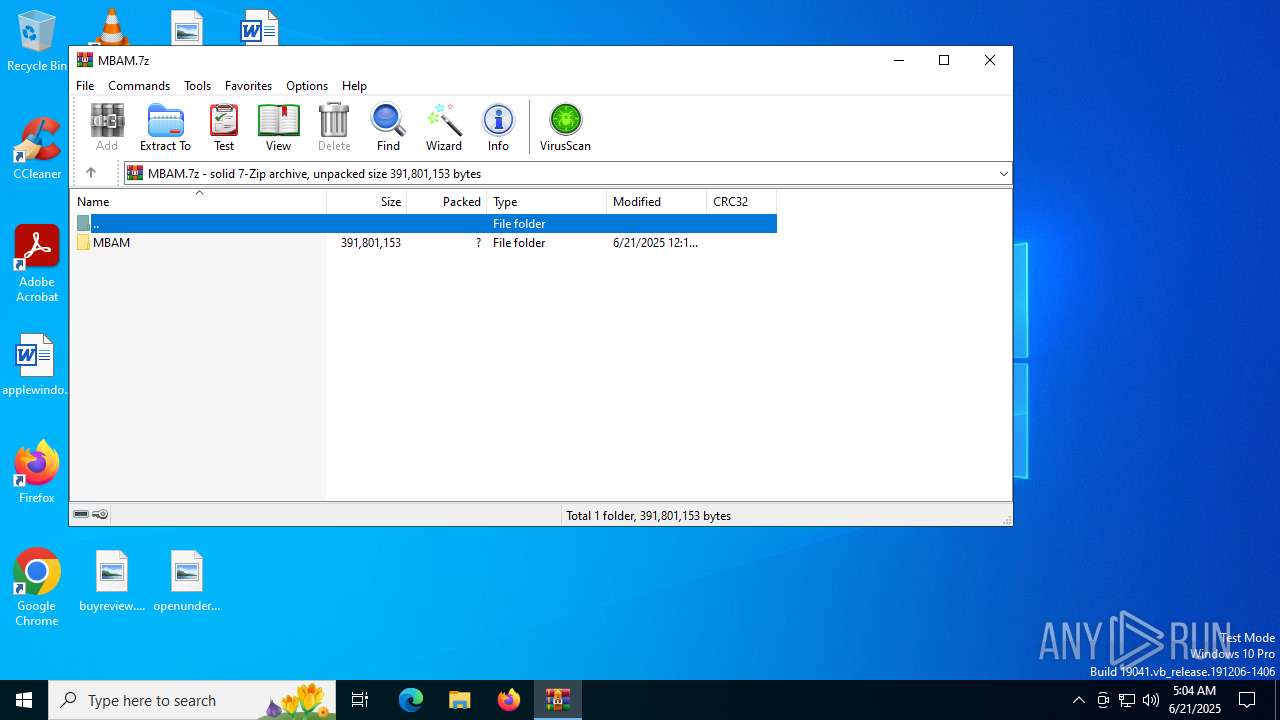
| File name: | MBAM.7z |
| Full analysis: | https://app.any.run/tasks/ee5eb951-9ae4-4329-be06-b9f35d2aebd4 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 05:04:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C7E0DECB7B8F740F3A1923D1A7028A31 |
| SHA1: | C380257DB7F25770A47C04EA7B5F9A4366D4FC31 |
| SHA256: | 4AB6F38D53D26DAEFD25602CFF15738D938B339FFE79504E64166CDFA1AD7E87 |
| SSDEEP: | 786432:iYvNojX3k8ueGzNgW9Sl6RfpZz98qJfZceKsZntO:iYlojX3klz79hfp9SqJfZceKs1o |
MALICIOUS
No malicious indicators.SUSPICIOUS
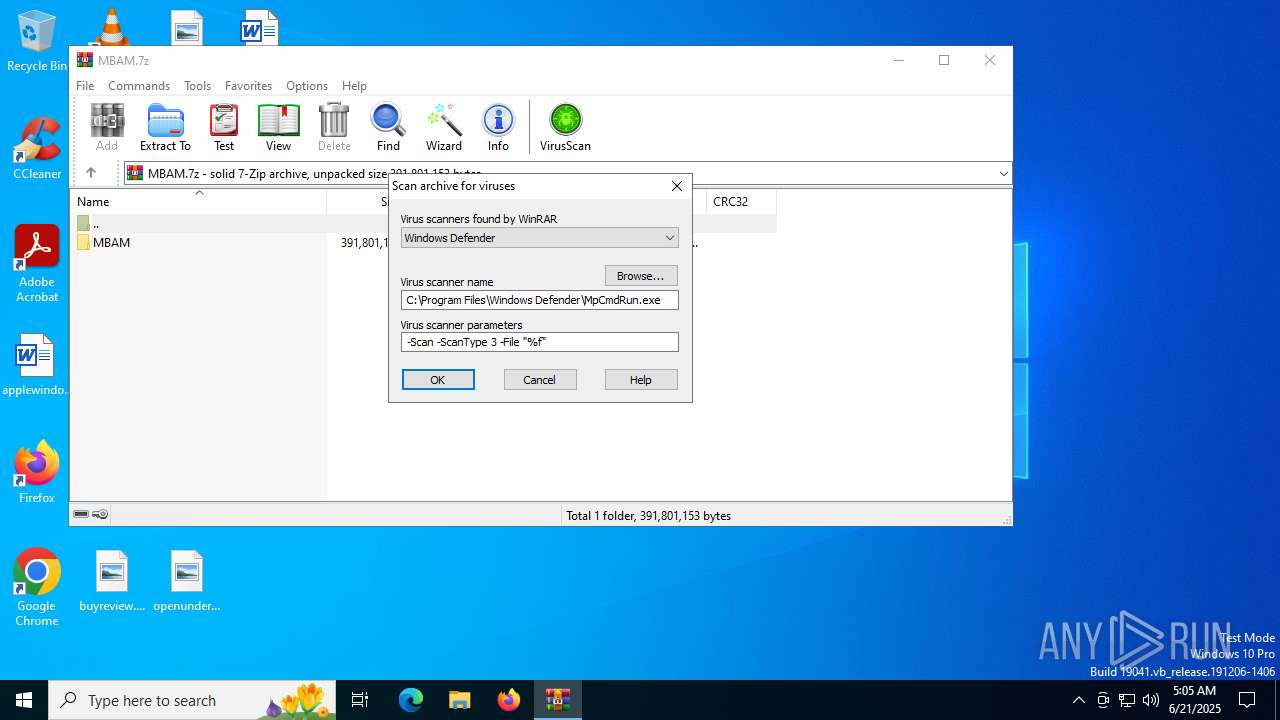
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 4860)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 4860)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4860)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4860)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4860)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4860)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4860)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4860)
The sample compiled with spanish language support
- WinRAR.exe (PID: 4860)
The sample compiled with english language support
- WinRAR.exe (PID: 4860)
Checks proxy server information
- slui.exe (PID: 1800)
Checks supported languages
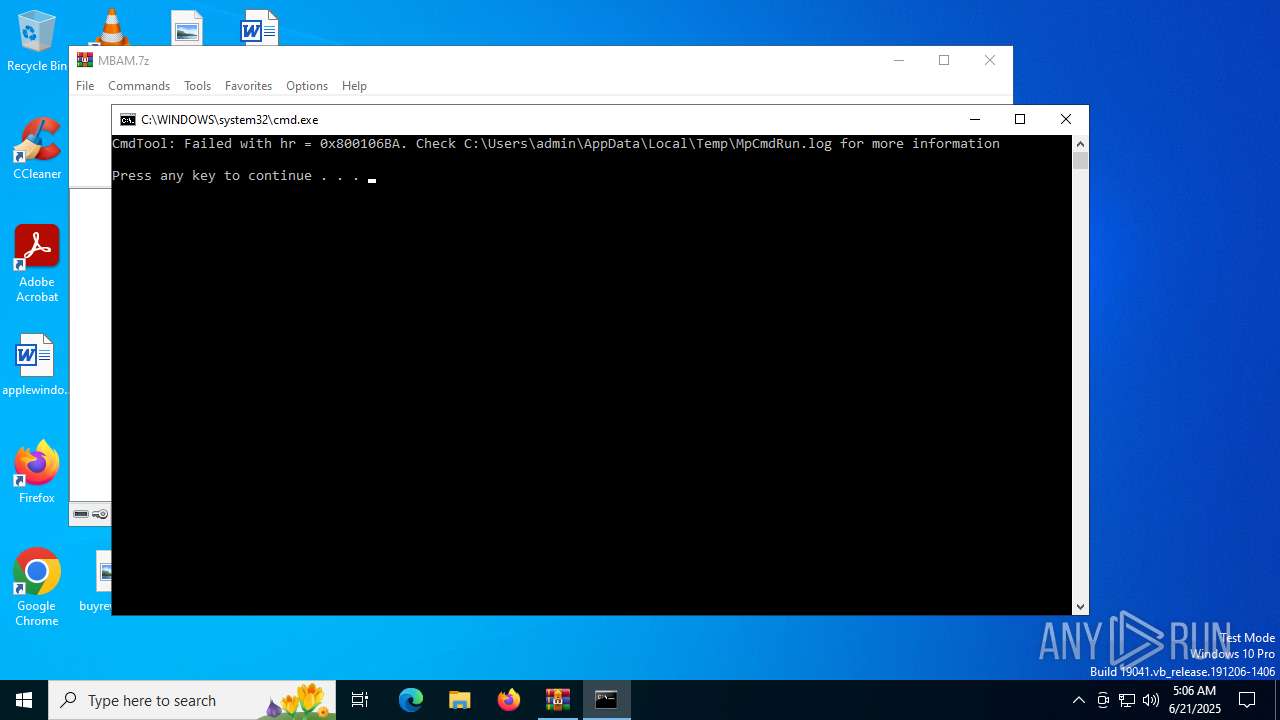
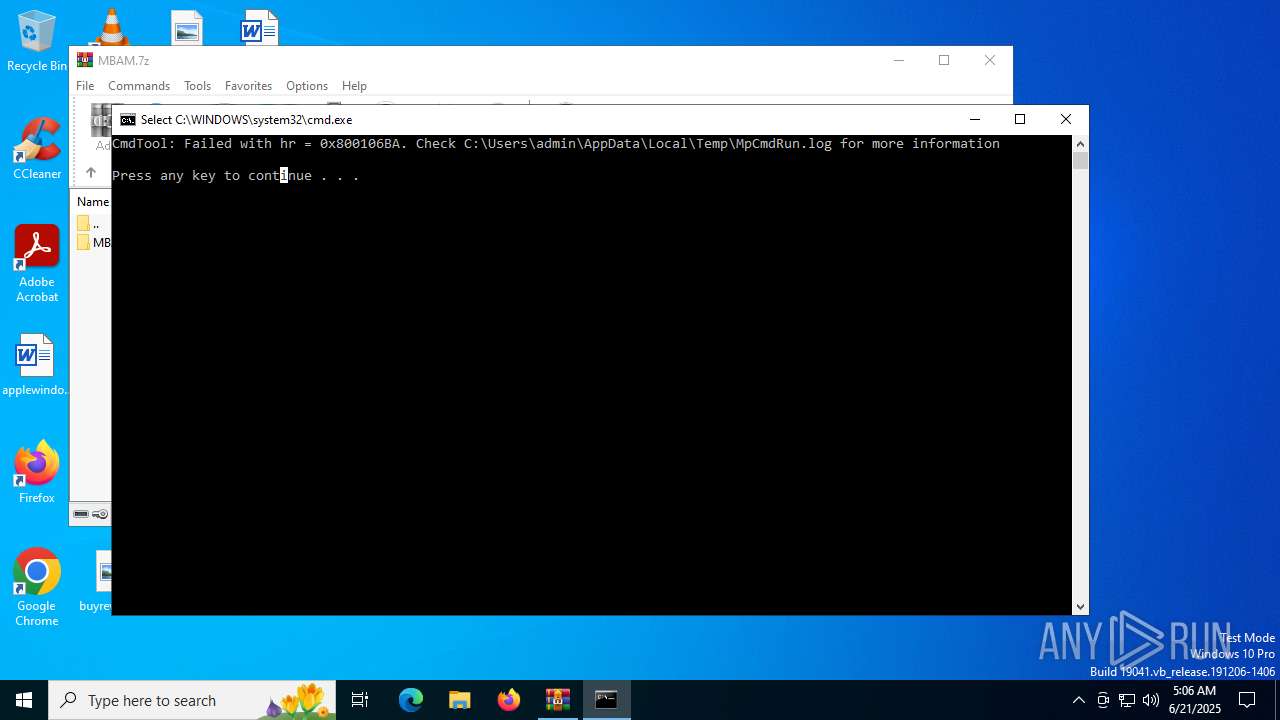
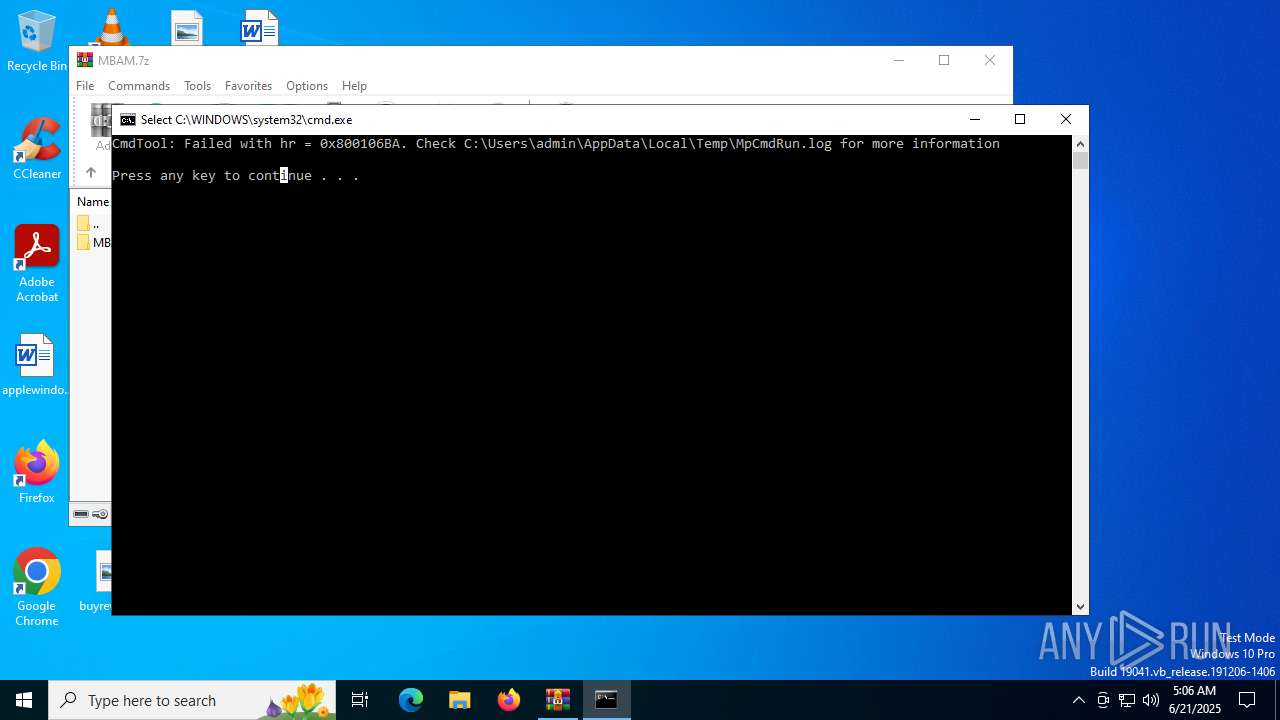
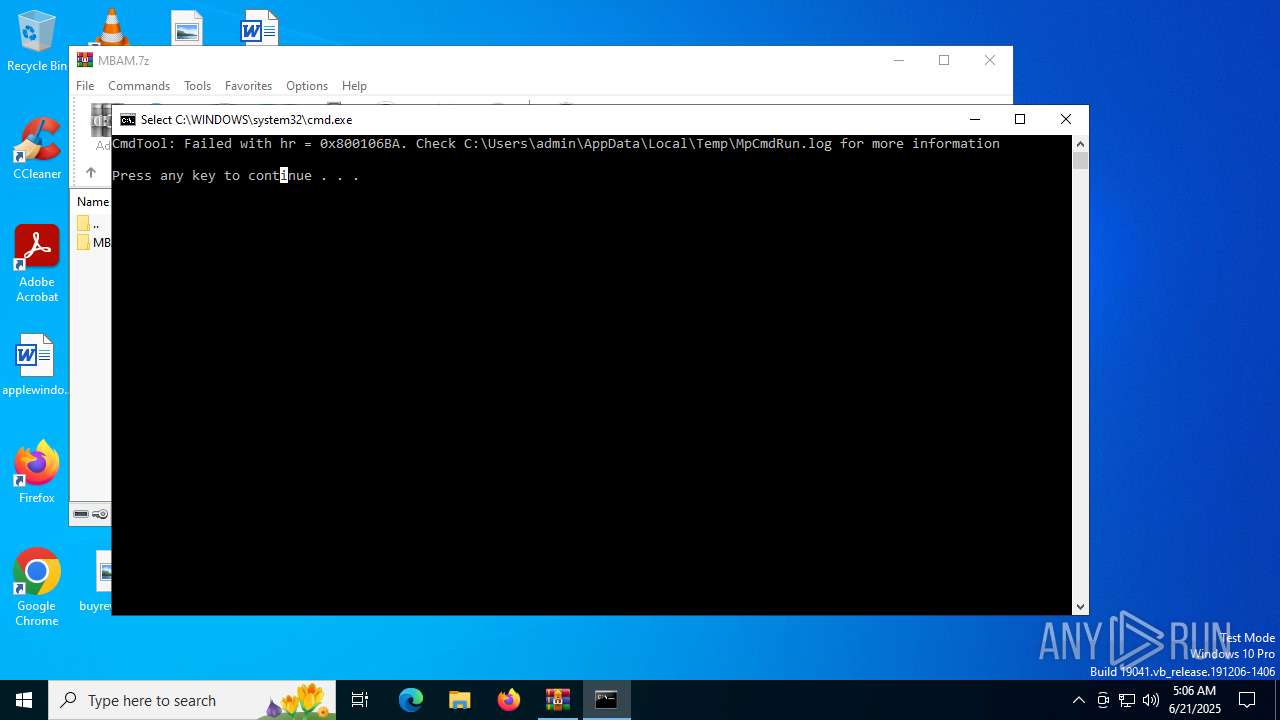
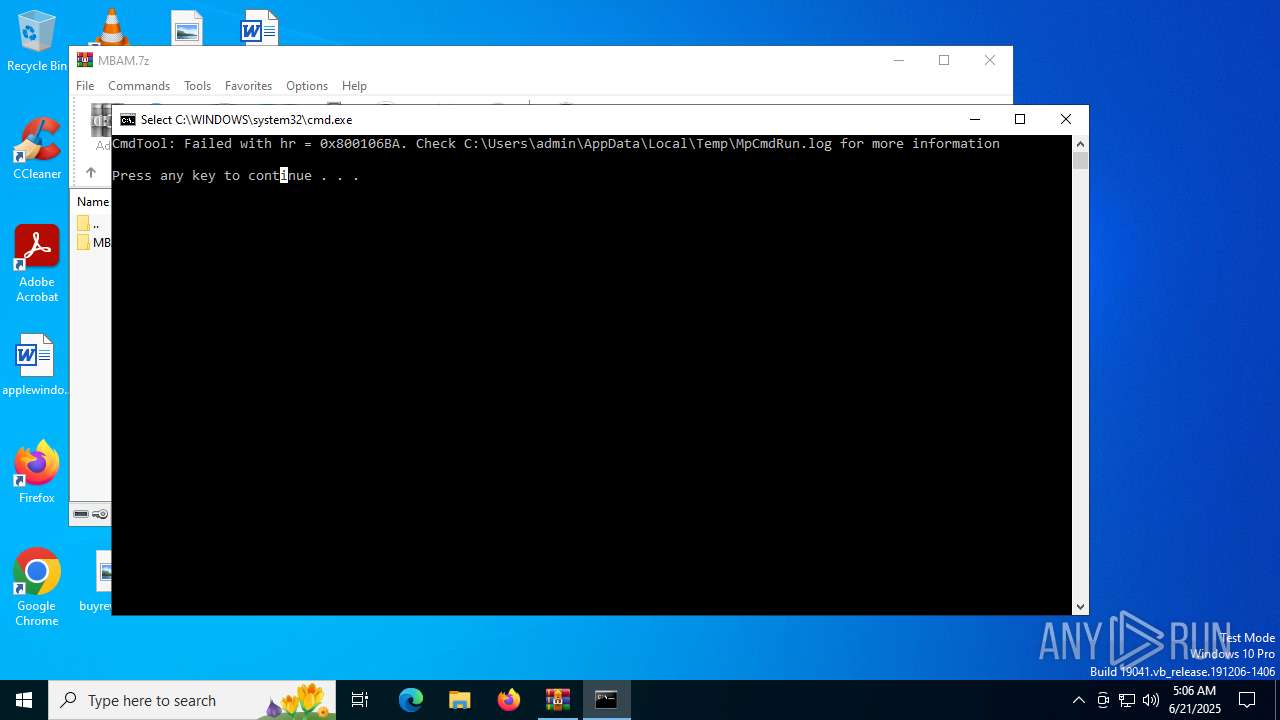
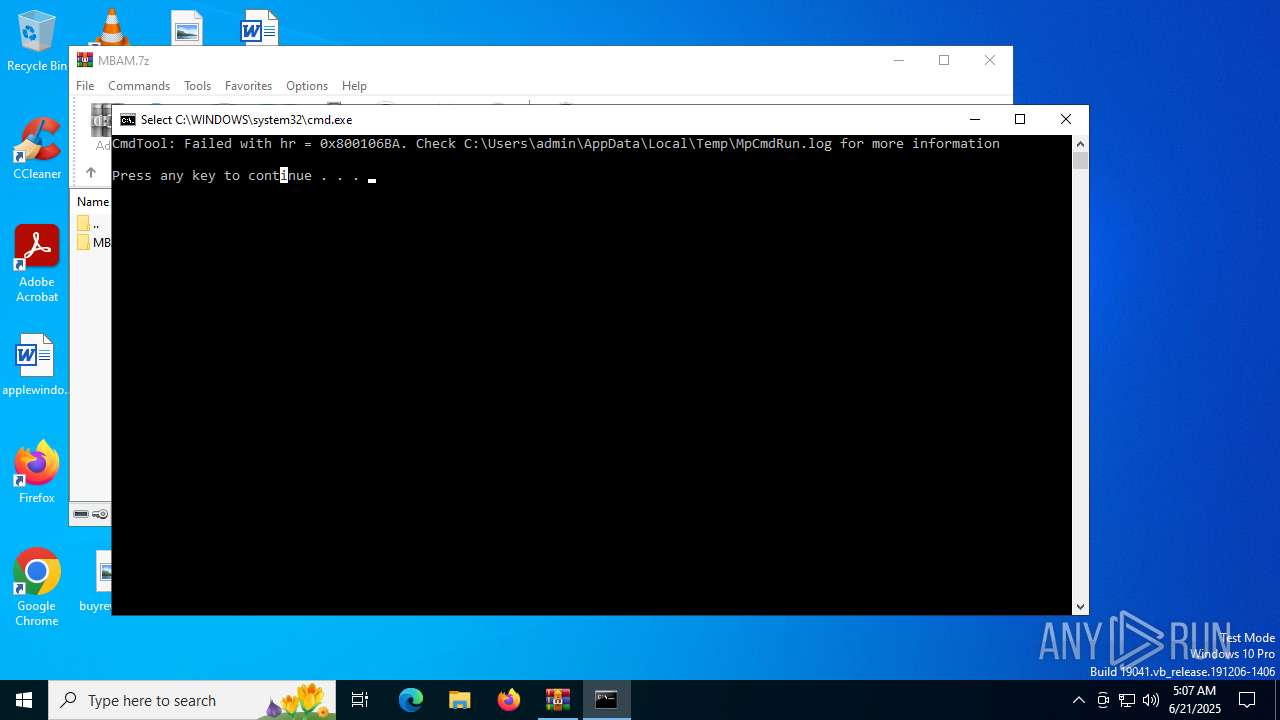
- MpCmdRun.exe (PID: 4748)
Reads the computer name
- MpCmdRun.exe (PID: 4748)
Reads the software policy settings
- slui.exe (PID: 1800)
Create files in a temporary directory
- MpCmdRun.exe (PID: 4748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:06:21 00:15:06+00:00 |
| ArchivedFileName: | MBAM |
Total processes
125
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1800 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2668 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\Rar$Scan108977.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4748 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4860 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\MBAM.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 082
Read events
7 071
Write events
11
Delete events
0
Modification events
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MBAM.7z | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4860) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
624
Suspicious files
27
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\assistant.deps.json | binary | |
MD5:26D5540F2674A1E33722EAF225EF7591 | SHA256:064A06E32F5A36F010A26737DEDEFD24CDBE5112FD08757B78449C3548447954 | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\ctlrvers.dat | text | |
MD5:A4A7B1372224AD52F4647180E3D8462F | SHA256:A2F604C40F2F3A0A54449271147B98152D8D9E620374478C646C3909393C3543 | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\assistant.runtimeconfig.json | binary | |
MD5:D94CF983FBA9AB1BB8A6CB3AD4A48F50 | SHA256:1ECA0F0C70070AA83BB609E4B749B26DCB4409784326032726394722224A098A | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\malwarebytes_assistant.runtimeconfig.json | binary | |
MD5:D94CF983FBA9AB1BB8A6CB3AD4A48F50 | SHA256:1ECA0F0C70070AA83BB609E4B749B26DCB4409784326032726394722224A098A | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\malwarebytes_assistant.deps.json | binary | |
MD5:0C0163F65B5457C15ABE97834ECA99D7 | SHA256:426998F682589E0700286C17D7FDC33125CE6B4334DD2DFDC505A4F3CC3C33A0 | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\mbamelam.inf | binary | |
MD5:5D8C05CC4F9B4304D57EA10B87F2DCF0 | SHA256:E26C2D3347E5F077DA92713C9DF3CD3EAE438FB7E29810BD5C3AFE567D2D3125 | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\mbam.firefox.manifest.json | binary | |
MD5:354B998C980FB0686E50C61D6C9253E6 | SHA256:4CEB660871A4338D6972369A0DE6DDF1933ADA81F280F8FD628972C0F65741C5 | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\MbamUI.Core.deps.json | binary | |
MD5:45A9FE186260252A3EDCB62DE202C86A | SHA256:BCFCD3C8C0BBB9CE17C41982B7D861ECA3B3B776EEEAB6C647CFAEFABC61D5FB | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\Malwarebytes.runtimeconfig.json | binary | |
MD5:EDAF04AFDA9B2C6D778D7042E7824A2F | SHA256:AE076CC42958355D8E061A4D3D020BED0EF3CD0C37C1851BDF84844503F9880C | |||
| 4860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4860.13150\MBAM.7z\MBAM\mbamelam.cat | binary | |
MD5:BD4CEAE54AF081D6B1DD91FF584C5D61 | SHA256:C3C4967B05CD00C31CAFC39B57000EC2E82CCF2CA295C72365F5CF6E5D191034 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.73:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
— | — | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |