| File name: | PatchCleaner.zip |
| Full analysis: | https://app.any.run/tasks/b8f29c8d-d061-4bcf-88c6-3a22a2fd774e |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2024, 07:18:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 7FC853224EAFE62F87647074472DD021 |
| SHA1: | 80E50FEB7490B0B1AE49CD9EDC8101328282618F |
| SHA256: | 4A9B727FF9837D13DBFB8332C4E7C2B3BE56E39FF2865BA91640A791EEC86C13 |
| SSDEEP: | 24576:Qp6+7eSjpT1LinUqcqml5VDYHBZsZPj1SCAg81wp9OgUs53Ut016Eb05EDNUIJob:Qp6+7eSjpT1LinUqcqmlzDYHBZsZPj1G |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3972)
Reads security settings of Internet Explorer
- PatchCleaner.exe (PID: 372)
The process executes VB scripts
- PatchCleaner.exe (PID: 372)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 316)
- cscript.exe (PID: 1796)
- cscript.exe (PID: 1596)
Adds/modifies Windows certificates
- PatchCleaner.exe (PID: 372)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 316)
- cscript.exe (PID: 1796)
- cscript.exe (PID: 1596)
Reads settings of System Certificates
- PatchCleaner.exe (PID: 372)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 316)
- cscript.exe (PID: 1796)
- cscript.exe (PID: 1596)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 316)
- cscript.exe (PID: 1596)
- cscript.exe (PID: 1796)
Creates file in the systems drive root
- PatchCleaner.exe (PID: 372)
Reads the Internet Settings
- PatchCleaner.exe (PID: 372)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Manual execution by a user
- PatchCleaner.exe (PID: 372)
- wmpnscfg.exe (PID: 1424)
- PatchCleaner.exe (PID: 2072)
Reads the software policy settings
- PatchCleaner.exe (PID: 372)
Reads Environment values
- PatchCleaner.exe (PID: 372)
Disables trace logs
- PatchCleaner.exe (PID: 372)
Reads security settings of Internet Explorer
- cscript.exe (PID: 316)
- cscript.exe (PID: 1796)
- cscript.exe (PID: 1596)
Checks supported languages
- wmpnscfg.exe (PID: 1424)
- PatchCleaner.exe (PID: 372)
Reads the computer name
- wmpnscfg.exe (PID: 1424)
- PatchCleaner.exe (PID: 372)
Reads the machine GUID from the registry
- PatchCleaner.exe (PID: 372)
Creates files or folders in the user directory
- PatchCleaner.exe (PID: 372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2016:11:16 18:01:28 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PatchCleaner/ |
Total processes
46
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Windows\System32\cscript.exe" //B //Nologo WMIProducts.vbs | C:\Windows\System32\cscript.exe | — | PatchCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
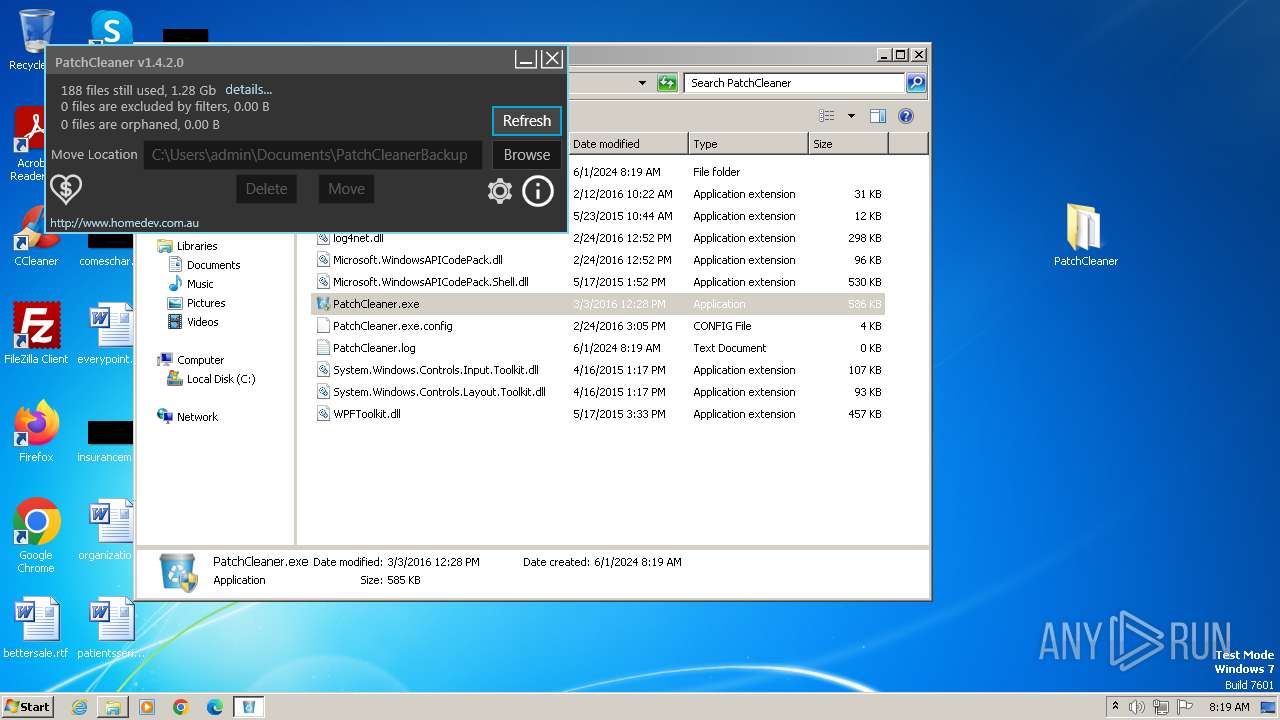
| 372 | "C:\Users\admin\Desktop\PatchCleaner\PatchCleaner.exe" | C:\Users\admin\Desktop\PatchCleaner\PatchCleaner.exe | explorer.exe | ||||||||||||
User: admin Company: HomeDev Integrity Level: HIGH Description: PatchCleaner Version: 1.4.2.0 Modules
| |||||||||||||||
| 1424 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | "C:\Windows\System32\cscript.exe" //B //Nologo WMIProducts.vbs | C:\Windows\System32\cscript.exe | — | PatchCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1796 | "C:\Windows\System32\cscript.exe" //B //Nologo WMIProducts.vbs | C:\Windows\System32\cscript.exe | — | PatchCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\Desktop\PatchCleaner\PatchCleaner.exe" | C:\Users\admin\Desktop\PatchCleaner\PatchCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: HomeDev Integrity Level: MEDIUM Description: PatchCleaner Exit code: 3221226540 Version: 1.4.2.0 Modules
| |||||||||||||||
| 3972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\PatchCleaner.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
18 807
Read events
18 676
Write events
124
Delete events
7
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PatchCleaner.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
0
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\AppData\WMIProducts.vbs | text | |
MD5:73D4F340C8523C46915CE32E175C0EDA | SHA256:59D2B20E6FFEC82EA9FB9735DD8265E8FE37D51F74BE34EEC6DBE30DDA326925 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\PatchCleaner.exe.config | xml | |
MD5:5CBEBE6CFAFBEE5251EC24E7D71DD2FC | SHA256:0184DB13C199C31012AC282F3D4DD1F74A9C414A78012D96D326E9B4C3D05877 | |||
| 316 | cscript.exe | C:\Users\admin\Desktop\PatchCleaner\AppData\products.txt | text | |
MD5:D1AB7D48C528ED63F42144B174897F9F | SHA256:CA841BB7404DDF4519C61F78308F79C3294743A21353A4B8E6E2D4B368D1DC5B | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\PatchCleaner.exe | executable | |
MD5:70C39AC8C162955E3A2DBC4798FE6BD4 | SHA256:9E6181874BB298A2222B5A7077EFB1365664060A494E2BFDC04C9BE8A894F7F1 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\HomeDev.Software.dll | executable | |
MD5:4F4D6D18ADD67CF09FF4F1B241B2AB85 | SHA256:6AF0BD80E5CB1922E4E71CCB7A4AB59E7B0A42EE712AF8536F8A35154C3034E3 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\WPFToolkit.dll | executable | |
MD5:195ED09E0B4F3B09EA4A3B67A0D3F396 | SHA256:AEF9FCBB874FC82E151E32279330061F8F22A77C05F583A0CB5E5696654AC456 | |||
| 1796 | cscript.exe | C:\Users\admin\Desktop\PatchCleaner\AppData\products.txt | text | |
MD5:D1AB7D48C528ED63F42144B174897F9F | SHA256:CA841BB7404DDF4519C61F78308F79C3294743A21353A4B8E6E2D4B368D1DC5B | |||
| 372 | PatchCleaner.exe | C:\Users\admin\AppData\Local\HomeDev\PatchCleaner.exe_Url_j3bnab4s0fdhyhblskuk0wgdiwtwj1t0\1.4.2.0\xahpjygb.newcfg | xml | |
MD5:8205F537CCF408D9A9C372846EB340BB | SHA256:39920187070DA1EDC5BCA3F462C633F5B27DBF78B51BE24CF5CDC03CF269DEC7 | |||
| 372 | PatchCleaner.exe | C:\Users\admin\AppData\Local\HomeDev\PatchCleaner.exe_Url_j3bnab4s0fdhyhblskuk0wgdiwtwj1t0\1.4.2.0\user.config | xml | |
MD5:471A89B7EB58CA4E703F456DA01A9F31 | SHA256:6E76F167E24B7E02386E79794015A5FEDB5EFE9AB5D25C60C6FE0A6F0013A048 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.15447\PatchCleaner\System.Windows.Controls.Input.Toolkit.dll | executable | |
MD5:9722713E648F42B57299E9D2CF3D5C1A | SHA256:BC3A78EB4DF2FD5B39244FA0586CC0A82FE3D0E185D151E6C340C53072A61872 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
372 | PatchCleaner.exe | GET | 301 | 45.76.119.238:80 | http://www.homedev.com.au/Common/CurrentVersion/727da176-50bb-452c-8db5-96ee0a573ed4 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
372 | PatchCleaner.exe | 45.76.119.238:80 | www.homedev.com.au | AS-CHOOPA | AU | unknown |
372 | PatchCleaner.exe | 45.76.119.238:443 | www.homedev.com.au | AS-CHOOPA | AU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.homedev.com.au |
| unknown |