| File name: | 000.exe |
| Full analysis: | https://app.any.run/tasks/c308c6b5-77dd-4b2f-9b8f-499086568e21 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 14:23:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | D5671758956B39E048680B6A8275E96A |
| SHA1: | 33C341130BF9C93311001A6284692C86FEC200EF |
| SHA256: | 4A900B344EF765A66F98CF39AC06273D565CA0F5D19F7EA4CA183786155D4A47 |
| SSDEEP: | 3072:V3LA1++iCeFj0im6X/AXpT8vVMCcHVcdhghUuzzo9YC:lLJlC6j0CX4XmvWHVcd62uo9P |
MALICIOUS
DARKROAD has been detected (YARA)
- 000.exe (PID: 6692)
SUSPICIOUS
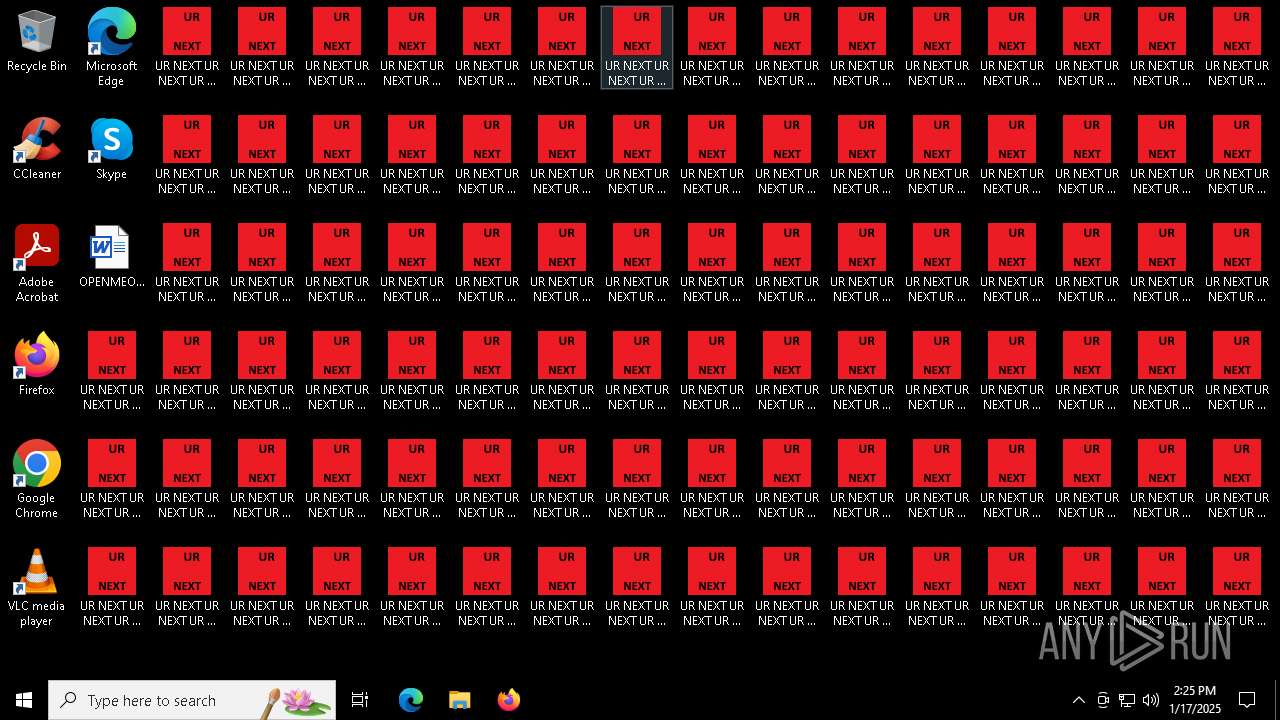
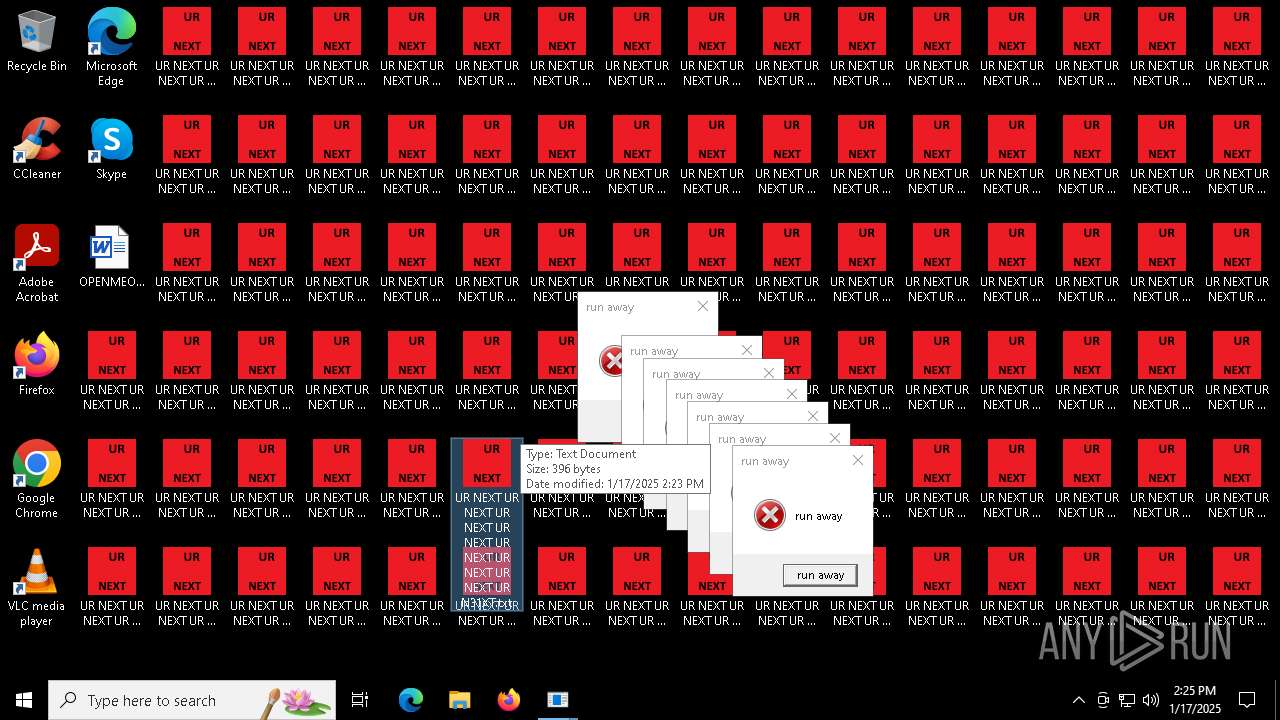
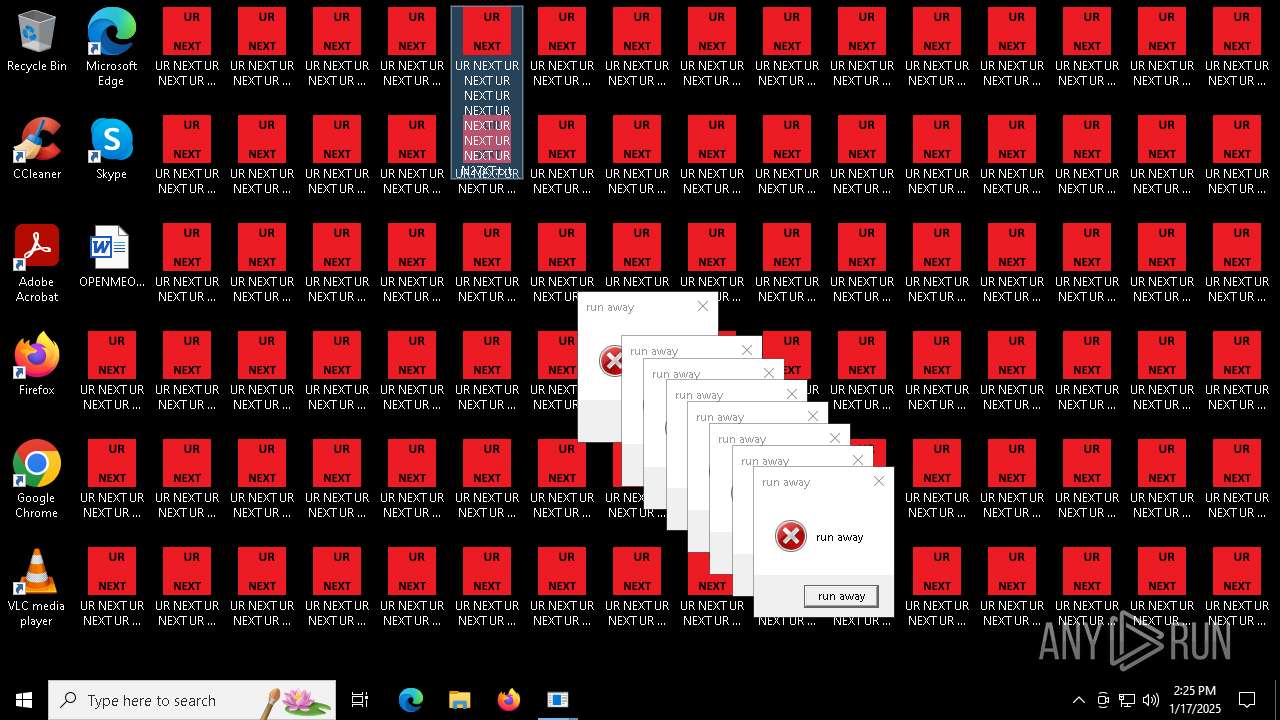
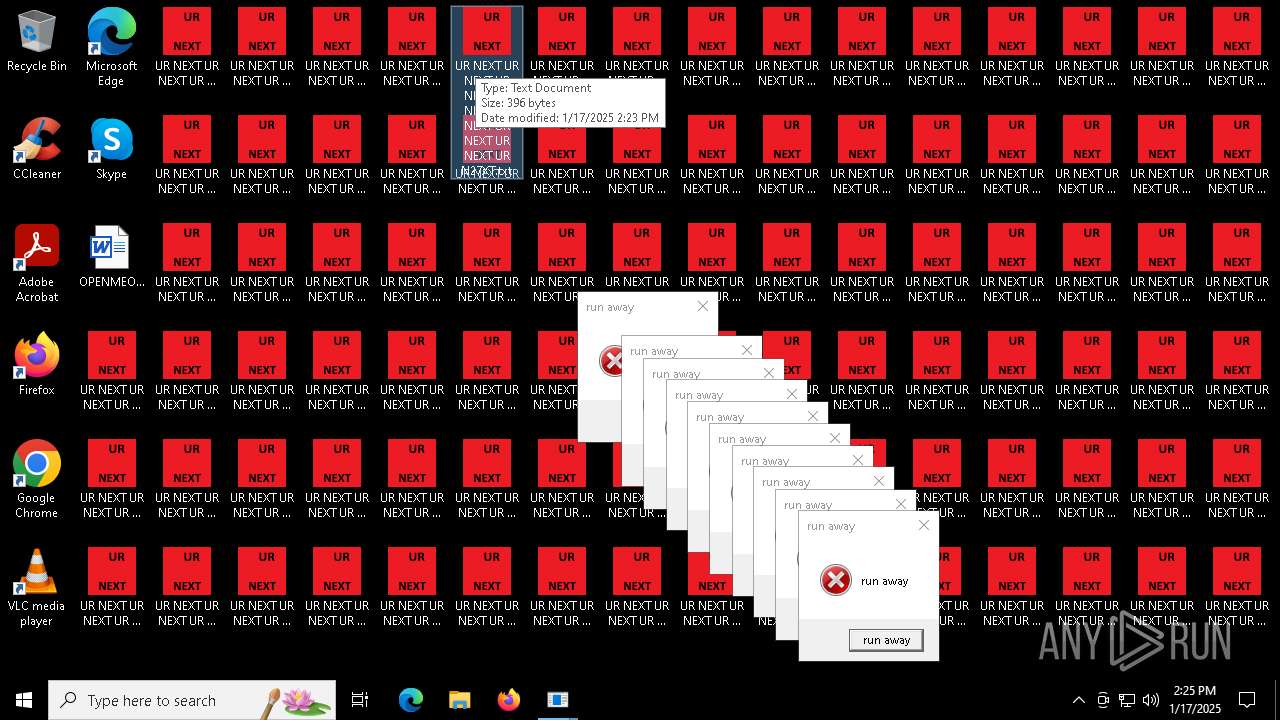
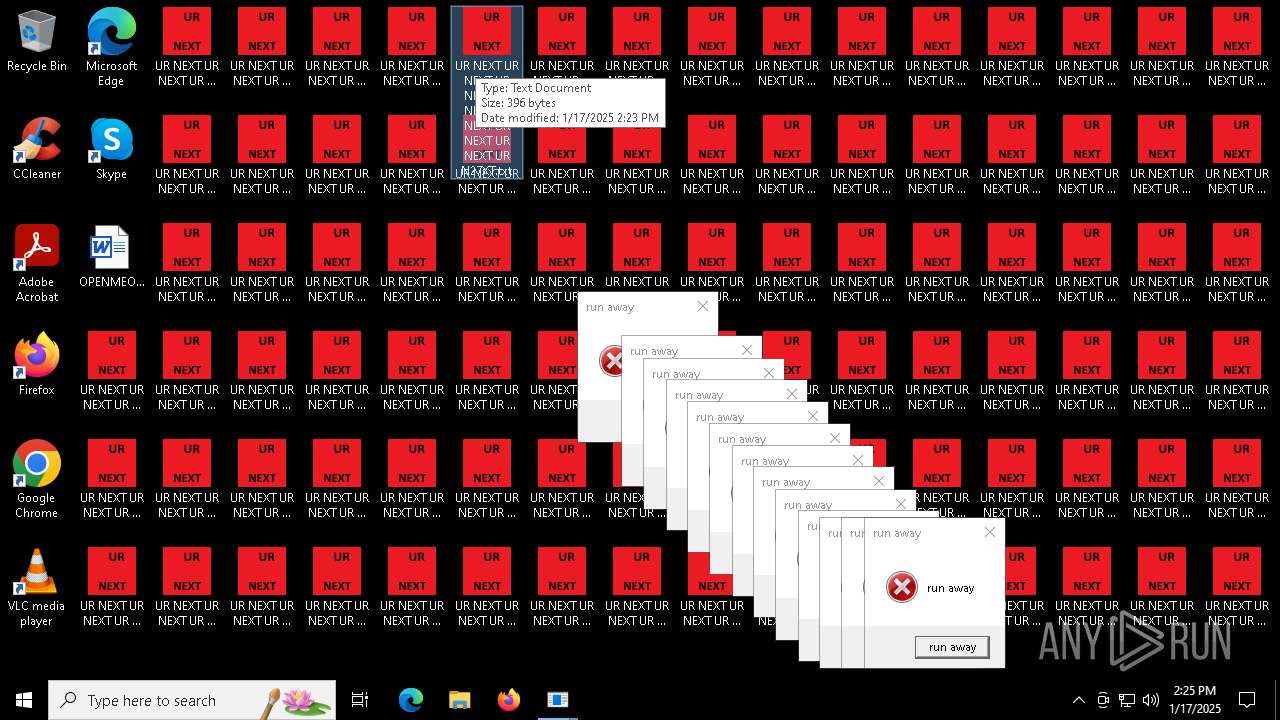
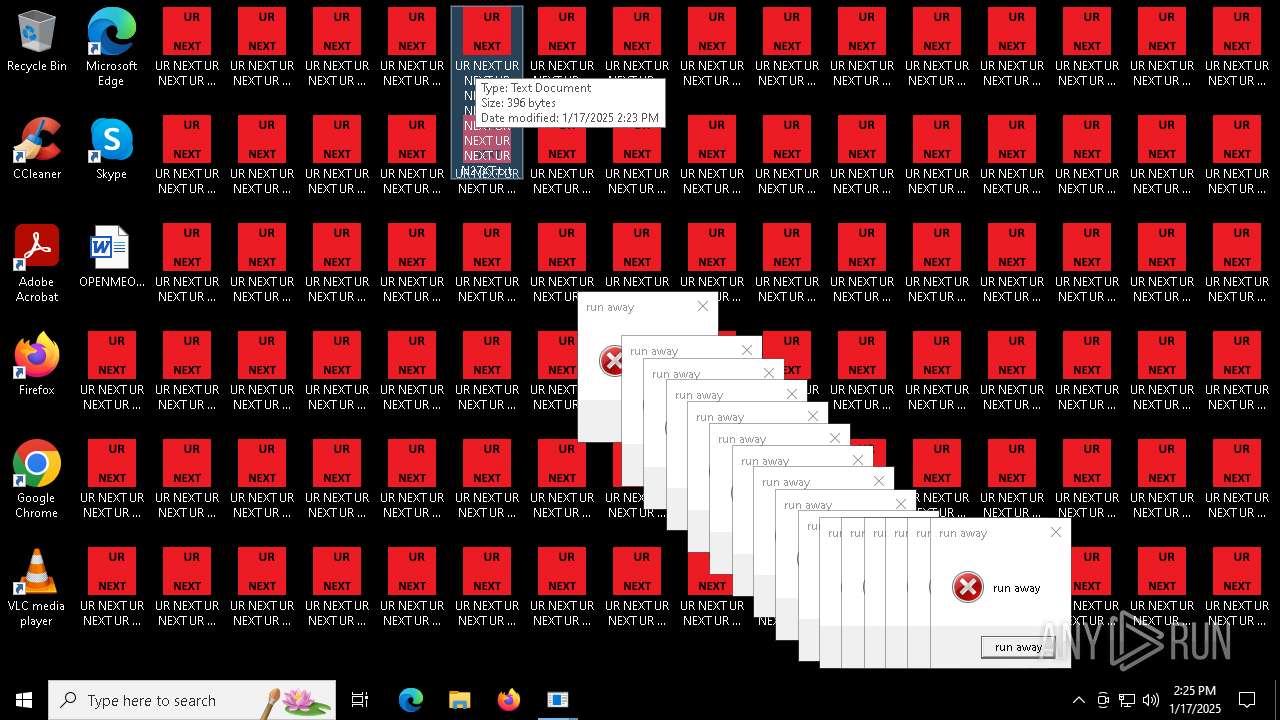
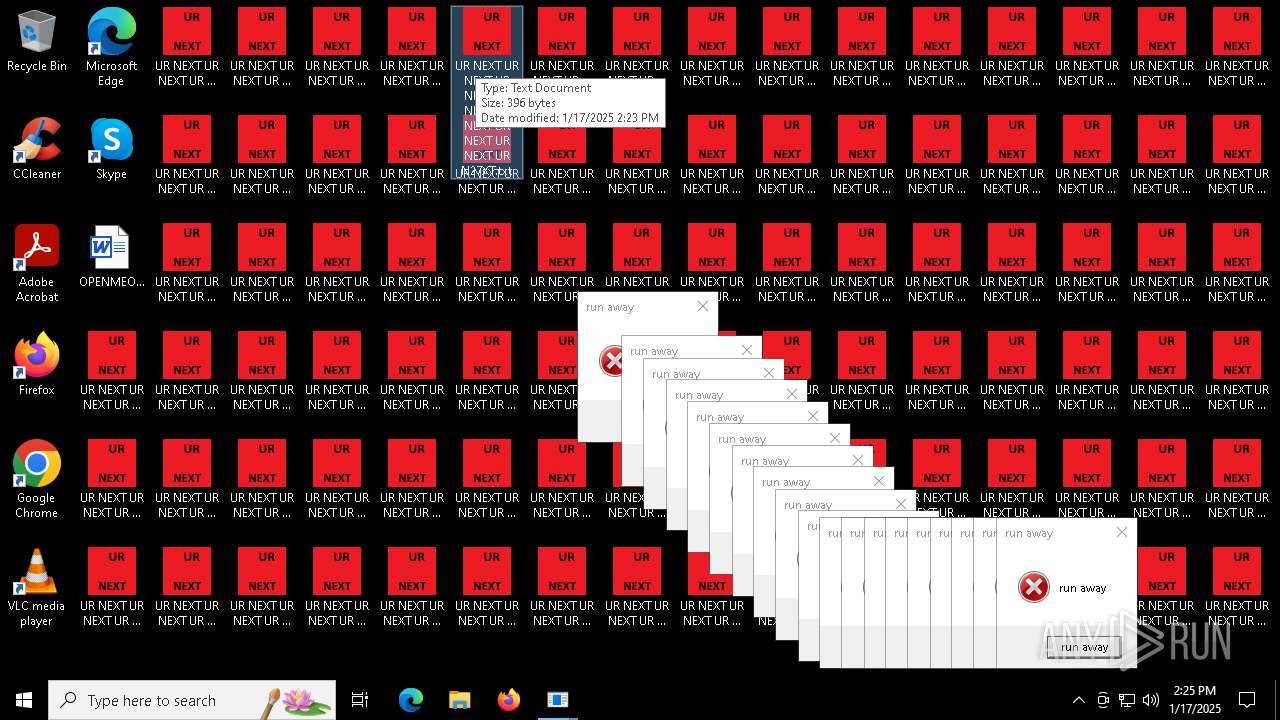
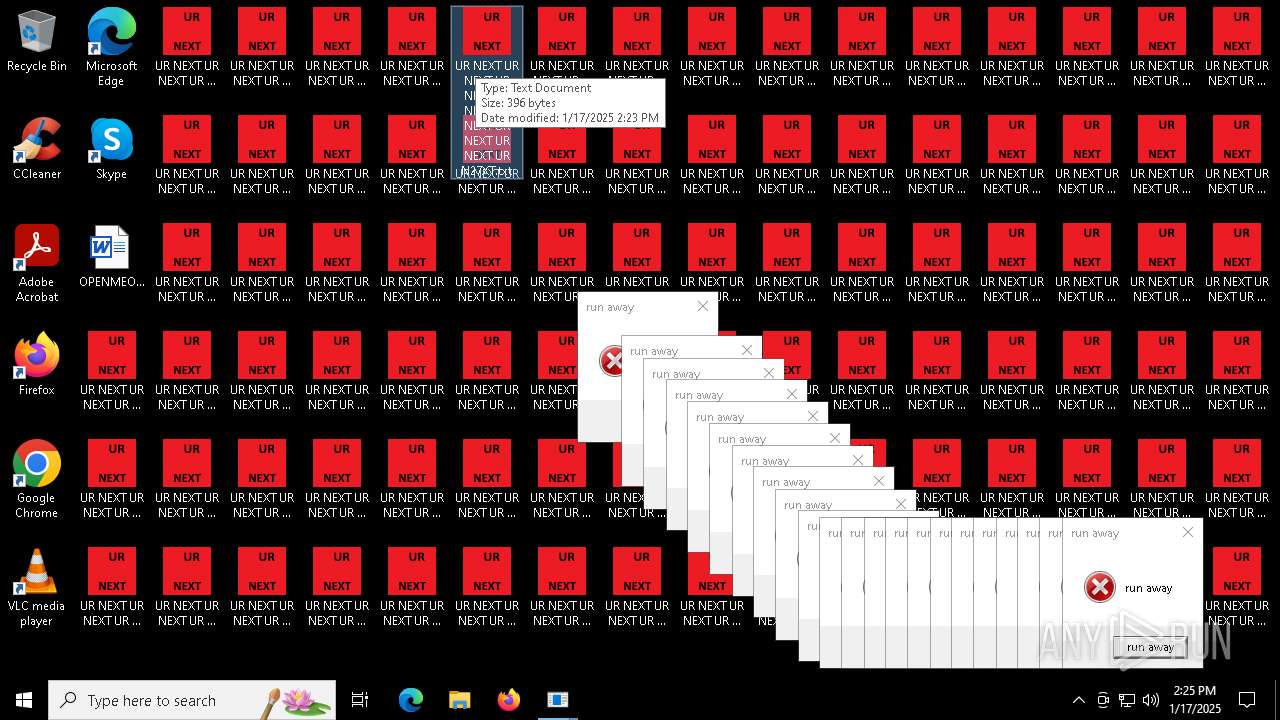
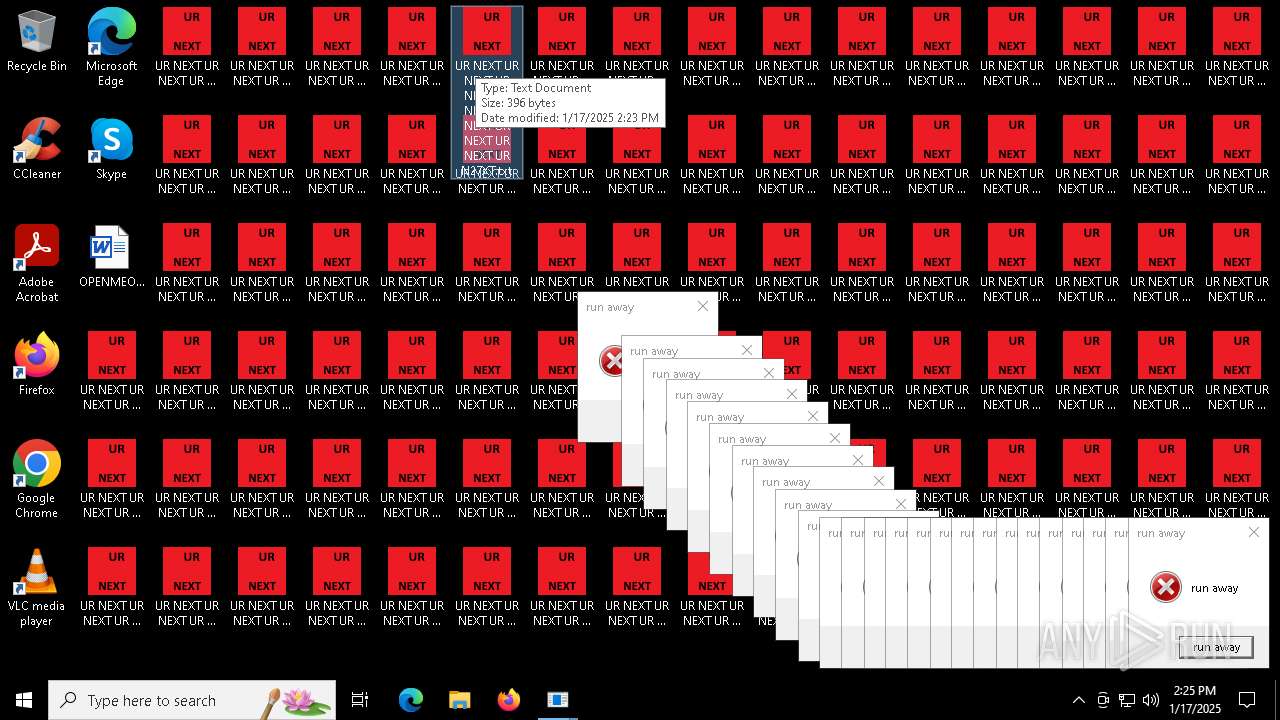
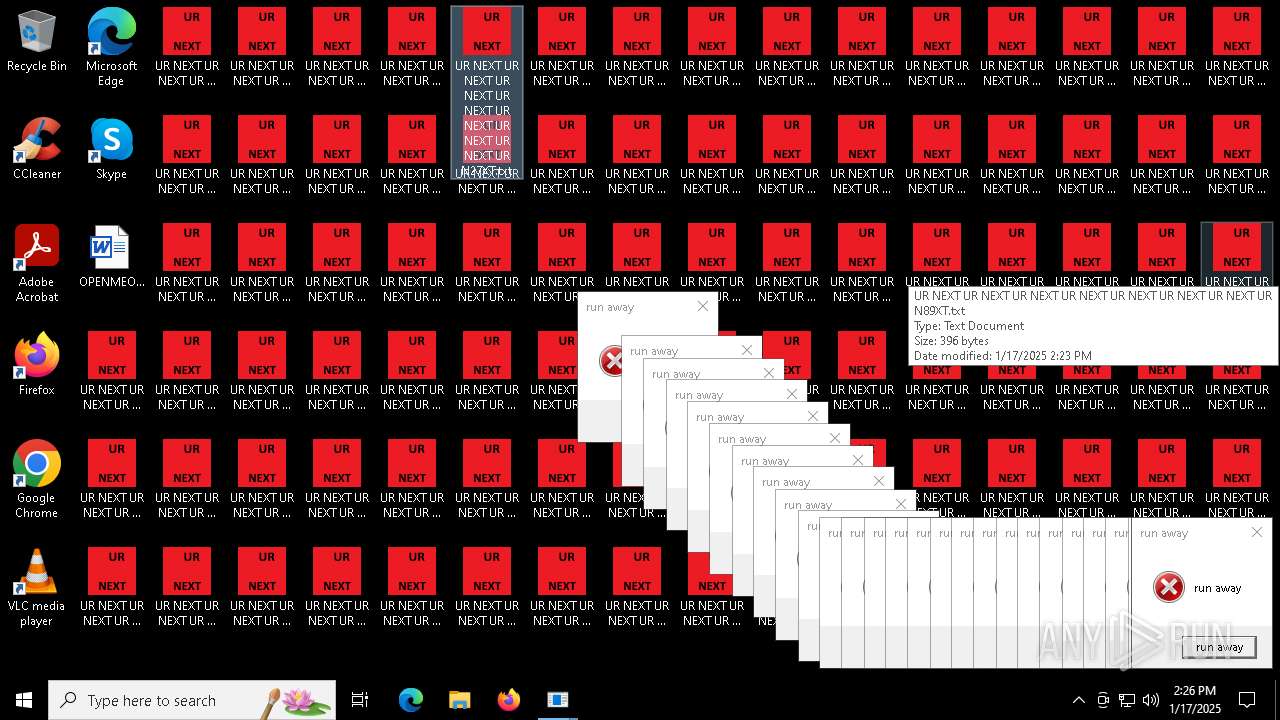
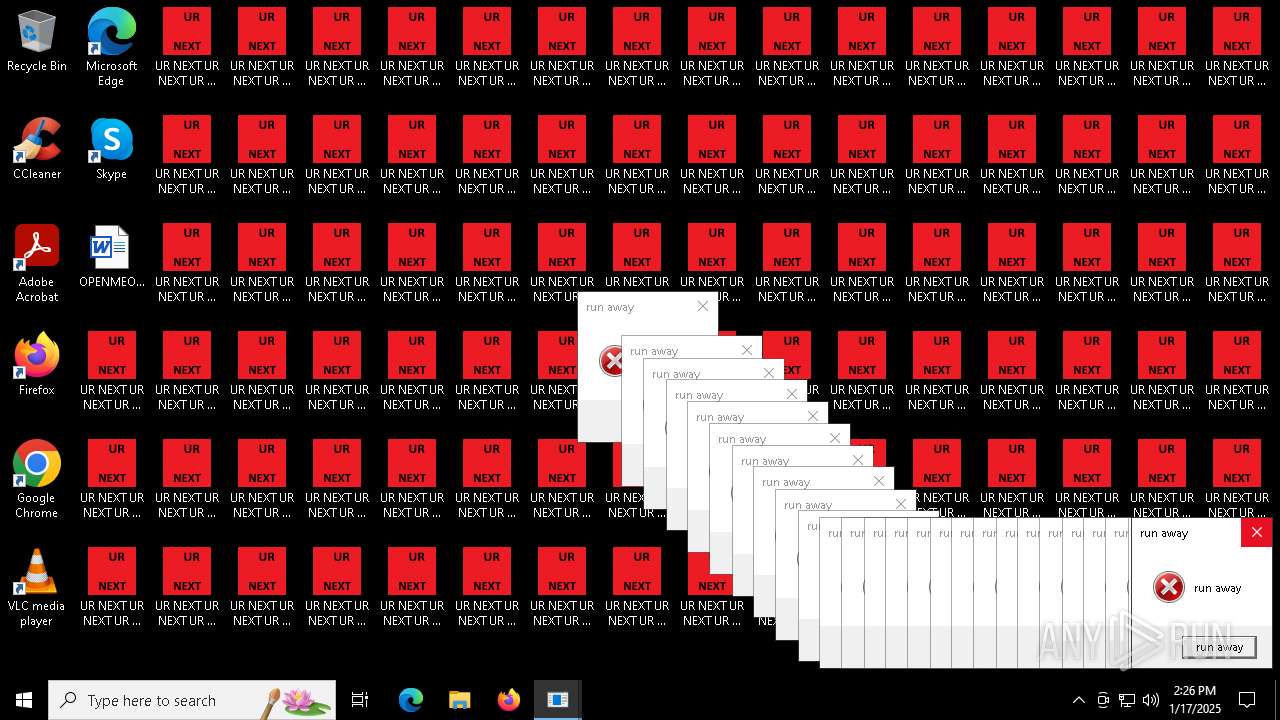
Changes the desktop background image
- 000.exe (PID: 6692)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 6840)
Starts CMD.EXE for commands execution
- 000.exe (PID: 6692)
- rniw.exe (PID: 5956)
Executable content was dropped or overwritten
- 000.exe (PID: 6692)
- cmd.exe (PID: 6840)
- rniw.exe (PID: 5956)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6840)
Executing commands from a ".bat" file
- 000.exe (PID: 6692)
- rniw.exe (PID: 5956)
Reads security settings of Internet Explorer
- 000.exe (PID: 6692)
SQL CE related mutex has been found
- 000.exe (PID: 6692)
There is functionality for taking screenshot (YARA)
- 000.exe (PID: 6692)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 908)
The system shut down or reboot
- cmd.exe (PID: 6840)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6012)
INFO
Reads the computer name
- 000.exe (PID: 6692)
Checks supported languages
- 000.exe (PID: 6692)
Creates files in the program directory
- cmd.exe (PID: 6840)
- 000.exe (PID: 6692)
Creates files or folders in the user directory
- 000.exe (PID: 6692)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7104)
- WMIC.exe (PID: 5340)
Create files in a temporary directory
- 000.exe (PID: 6692)
Reads the machine GUID from the registry
- 000.exe (PID: 6692)
Checks proxy server information
- 000.exe (PID: 6692)
Manual execution by a user
- rniw.exe (PID: 5956)
- chrome.exe (PID: 2228)
- notepad.exe (PID: 6032)
- chrome.exe (PID: 6468)
- chrome.exe (PID: 6372)
- chrome.exe (PID: 4672)
Application launched itself
- chrome.exe (PID: 2228)
- chrome.exe (PID: 6468)
- chrome.exe (PID: 6372)
- chrome.exe (PID: 4672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:16 13:26:30+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 6978560 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a9b16 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | 000 |
| FileVersion: | 0.0.0.0 |
| InternalName: | 000.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | 000.exe |
| ProductName: | 000 |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
390
Monitored processes
167
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | shutdown /f /r /t 0 | C:\Windows\SysWOW64\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x218,0x21c,0x220,0x1f4,0x224,0x7fff7193dc40,0x7fff7193dc4c,0x7fff7193dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: UR NEXT Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
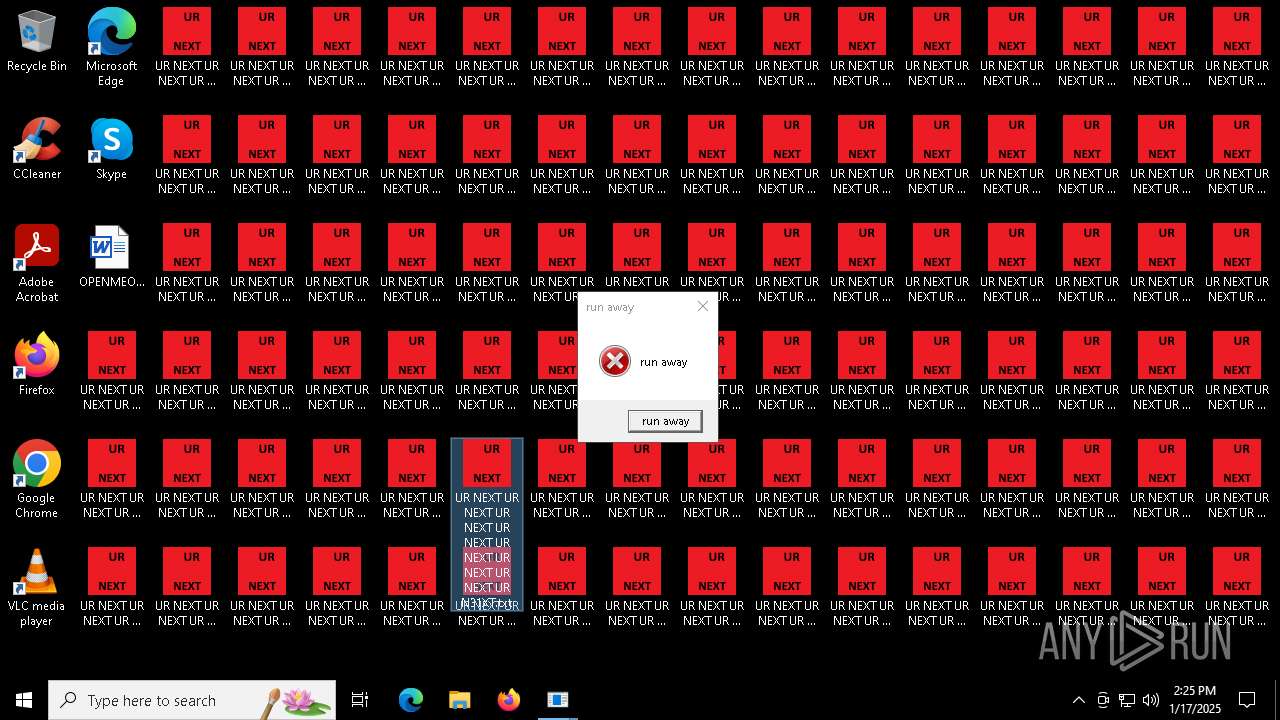
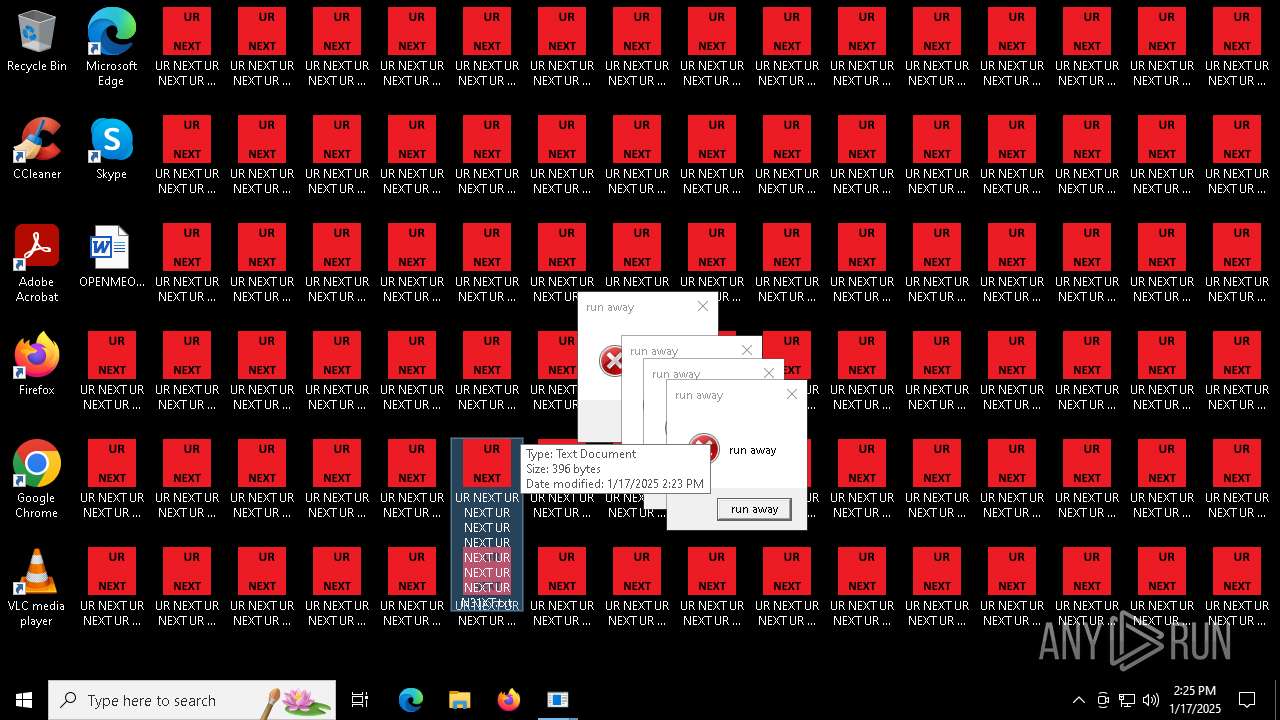
| 904 | runaway.exe | C:\Users\admin\AppData\Local\Temp\AEED.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 908 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 932 | runaway.exe | C:\Users\admin\AppData\Local\Temp\AEED.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 964 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 918
Read events
16 816
Write events
101
Delete events
1
Modification events
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalBase |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | DTDFile |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | RemoteDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSR.XML | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyStyle |
Value: 1 | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyName |
Value: | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyPort |
Value: 80 | |||
| (PID) Process: | (6692) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyBypass |
Value: 0 | |||
Executable files
3
Suspicious files
44
Text files
426
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
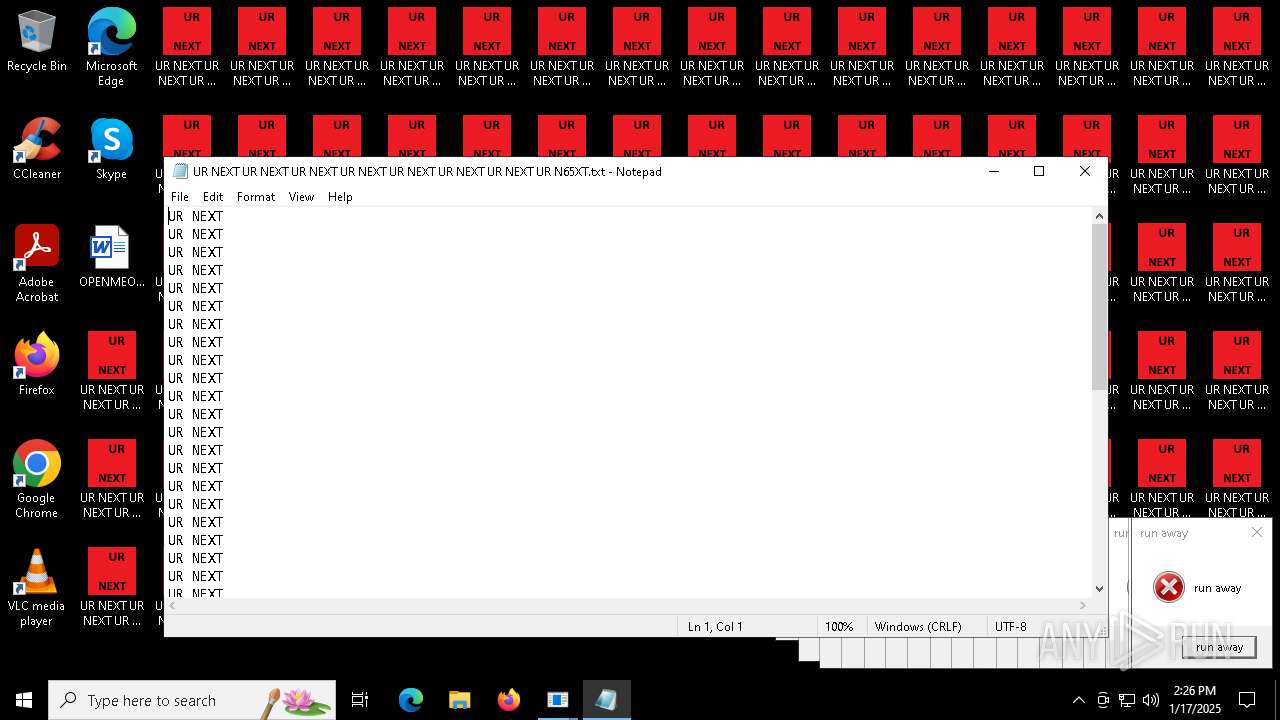
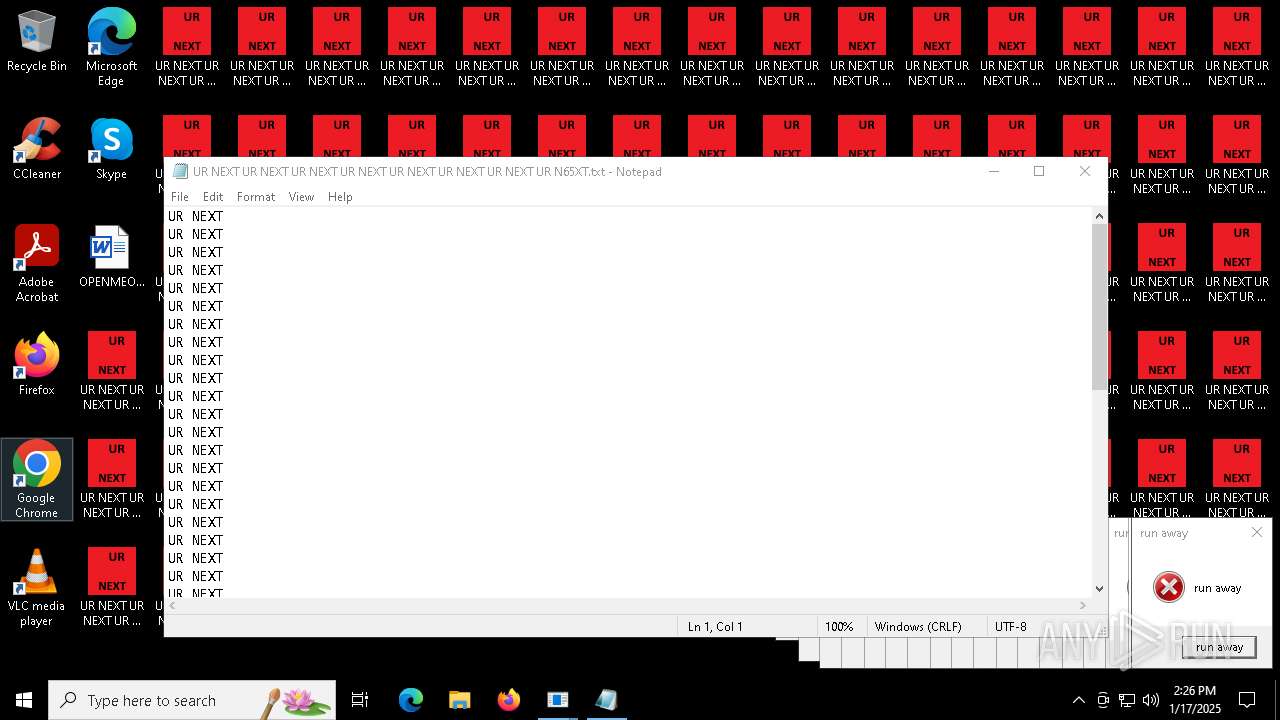
| 6692 | 000.exe | C:\Users\admin\AppData\Local\Temp\text.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 6692 | 000.exe | C:\Users\admin\AppData\Local\Temp\icon.ico | image | |
MD5:A4B9662CF3B6EA6626F6081C0D8C13F3 | SHA256:84A1C2713642090523F05D9FB015C537FD210D3200CADAF442BB67CF1834B356 | |||
| 6692 | 000.exe | C:\Users\admin\AppData\Local\Temp\rniw.exe | executable | |
MD5:9232120B6FF11D48A90069B25AA30ABC | SHA256:70FAA0E1498461731F873D3594F20CBF2BEAA6F123A06B66F9DF59A9CDF862BE | |||
| 6840 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\rniw.exe | executable | |
MD5:9232120B6FF11D48A90069B25AA30ABC | SHA256:70FAA0E1498461731F873D3594F20CBF2BEAA6F123A06B66F9DF59A9CDF862BE | |||
| 6692 | 000.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 6840 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N6XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 6840 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N1XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 6840 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N7XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 6840 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N4XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 6692 | 000.exe | C:\Users\admin\AppData\Local\Temp\v.mp4 | binary | |
MD5:D2774B188AB5DDE3E2DF5033A676A0B4 | SHA256:95374CF300097872A546D89306374E7CF2676F7A8B4C70274245D2DCCFC79443 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
29
DNS requests
9
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
720 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
2940 | OfficeClickToRun.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4856 | SearchApp.exe | 2.19.122.19:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
7236 | chrome.exe | 142.250.185.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
self.events.data.microsoft.com |
| unknown |
officeclient.microsoft.com |
| unknown |
ecs.office.com |
| unknown |
www.bing.com |
| unknown |
clientservices.googleapis.com |
| unknown |